Deck 11: Computer Crime and Information Technology Security
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/63
Play
Full screen (f)
Deck 11: Computer Crime and Information Technology Security
1
The risk of disclosure of confidential information is most closely related to which category in Carter's taxonomy?
A)Target
B)Instrumentality
C)Both A and B
D)Neither A nor B
A)Target
B)Instrumentality
C)Both A and B
D)Neither A nor B
A
2
According to Carter's taxonomy, use of a computer to further a criminal end refers to which of the following categories?
A)Target
B)Instrumentality
C)Incidental
D)Associated
A)Target
B)Instrumentality
C)Incidental
D)Associated
B
3
A bank's information system was hacked in an effort to obtain clients' personal financial information. Which category of computer crime best describes that situation?
A)Target
B)Instrumentality
C)Incidental
D)Associated
A)Target
B)Instrumentality
C)Incidental
D)Associated
A
4
The terms target, instrumentality, incidental and associated from Carter's taxonomy are most closely associated with which form of risk from Brown's taxonomy?
A)Human error
B)Liquidity
C)Systems
D)Market
A)Human error
B)Liquidity
C)Systems
D)Market

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
5
George received an e-mail that threatened to release his personal financial data unless he paid a fee. That situation is an example of:
A)Extortion
B)Intrusion
C)Information manipulation
D)Error
A)Extortion
B)Intrusion
C)Information manipulation
D)Error

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
6
Which of the following types of computer criminal is least likely to be motivated by financial gain?
A)Script kiddie
B)Cyber-criminal
C)Corporate spies
D)Organized crime
A)Script kiddie
B)Cyber-criminal
C)Corporate spies
D)Organized crime

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
7
Business risks and threats to information systems include all of the following except:
A)Error
B)Intrusions
C)Malicious software
D)Instrumentality
A)Error
B)Intrusions
C)Malicious software
D)Instrumentality

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
8
Disclosure of confidential information is one risk associated with information technology. Which of the following would be considered confidential information?
A)The stock price of Microsoft
B)The book value of Disney Corporation's fixed assets
C)The social security numbers of GE's board of directors
D)All of the above are examples of confidential information.
A)The stock price of Microsoft
B)The book value of Disney Corporation's fixed assets
C)The social security numbers of GE's board of directors
D)All of the above are examples of confidential information.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
9
Consider the following examples of computer crime as you answer the next question: i. Social Security numbers are stolen from a company's database.ii. A fraudster uses a computer to identify people over the age of 80 with annual incomes of $250,000 or more
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following statements is most true?
A)The list includes examples of all four categories.
B)The list includes examples of all categories except associated.
C)The list includes examples of all categories except target.
D)The list includes examples of all categories except incidental.
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following statements is most true?
A)The list includes examples of all four categories.
B)The list includes examples of all categories except associated.
C)The list includes examples of all categories except target.
D)The list includes examples of all categories except incidental.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
10
George received an e-mail that threatened to release his personal financial data unless he paid a fee. Which category of computer crime best describes that situation?
A)Target
B)Instrumentality
C)Incidental
D)Associated
A)Target
B)Instrumentality
C)Incidental
D)Associated

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
11
Consider the following examples of computer crime as you answer the next question: i. Social Security numbers are stolen from a company's database.ii. A fraudster uses a computer to identify people over the age of 80 with annual incomes of $250,000 or more
Iii) A supervisor receives threats from a worker via e-mail; the worker demands promotion as a condition of not exposing the supervisor's illegal acts
Iv) An unhappy customer launches a denial-of-service attack
Which of the following pairs an item from the list with an appropriate description of a business risk?
A)Extortion, i
B)Service interruption, ii
C)Extortion, iii
D)None of the above
Iii) A supervisor receives threats from a worker via e-mail; the worker demands promotion as a condition of not exposing the supervisor's illegal acts
Iv) An unhappy customer launches a denial-of-service attack
Which of the following pairs an item from the list with an appropriate description of a business risk?
A)Extortion, i
B)Service interruption, ii
C)Extortion, iii
D)None of the above

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
12
Malicious software, such as a logic bomb, is most closely related to which generic element of the accounting information system?
A)Inputs
B)Processing
C)Outputs
D)Storage
A)Inputs
B)Processing
C)Outputs
D)Storage

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
13
Consider the following examples of computer crime as you answer the next question: i. Social Security numbers are stolen from a company's database.ii. A fraudster uses a computer to identify people over the age of 80 with annual incomes of $250,000 or more
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following pairs includes two items from the same category?
A)I and II
B)II and III
C)II and IV
D)I and IV
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following pairs includes two items from the same category?
A)I and II
B)II and III
C)II and IV
D)I and IV

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
14
An information systems development company routinely creates a password that they do not disclose to their clients. In that way, the development company can bypass any security the client adds on later if the system needs maintenance. The client's information system is therefore at greatest risk for:
A)Error
B)Intrusion
C)Web site defacement
D)Extortion
A)Error
B)Intrusion
C)Web site defacement
D)Extortion

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
15
Consider the following examples of computer crime as you answer the next question: i. Social Security numbers are stolen from a company's database.ii. A fraudster uses a computer to identify people over the age of 80 with annual incomes of $250,000 or more
Iii) A supervisor receives threats from a worker via e-mail; the worker demands promotion as a condition of not exposing the supervisor's illegal acts
Iv) An unhappy customer launches a denial-of-service attack
Which two items represent the same category of risk from the list discussed in the chapter?
A)I and II
B)I and III
C)II and IV
D)None of the above
Iii) A supervisor receives threats from a worker via e-mail; the worker demands promotion as a condition of not exposing the supervisor's illegal acts
Iv) An unhappy customer launches a denial-of-service attack
Which two items represent the same category of risk from the list discussed in the chapter?
A)I and II
B)I and III
C)II and IV
D)None of the above

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
16
The difference between "error" and "information manipulation" as business risks associated with information technology is:
A)The person's intent
B)The kind of information involved
C)The potential dollar amount of the loss
D)The classification on Carter's taxonomy
A)The person's intent
B)The kind of information involved
C)The potential dollar amount of the loss
D)The classification on Carter's taxonomy

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
17
___ are ___ driven by financial gain.
A)Hackers, cyber-criminals
B)Cyber-criminals, hackers
C)Corporate spies, terrorists
D)Terrorists, corporate spies
A)Hackers, cyber-criminals
B)Cyber-criminals, hackers
C)Corporate spies, terrorists
D)Terrorists, corporate spies

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
18
Consider the following examples of computer crime as you answer the next question: i. Social Security numbers are stolen from a company's database.ii. A fraudster uses a computer to identify people over the age of 80 with annual incomes of $250,000 or more
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following pairs includes items from different categories?
A)I and IV
B)II and III
C)Both A and B
D)Neither A nor B
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following pairs includes items from different categories?
A)I and IV
B)II and III
C)Both A and B
D)Neither A nor B

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
19
Which category of computer crime in Carter's taxonomy recognizes that the presence of computers has generated new versions of traditional crimes?
A)Target
B)Instrumentality
C)Incidental
D)Associated
A)Target
B)Instrumentality
C)Incidental
D)Associated

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
20
Computer crimes that fall under Carter's "target" category are most closely associated with which generic element of an accounting information system?
A)Processing
B)Storage
C)Both A and B
D)Neither A nor B
A)Processing
B)Storage
C)Both A and B
D)Neither A nor B

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
21
A firewall is an example of which type of control?
A)Physical security
B)Technical security
C)Administrative security
D)Enterprise security
A)Physical security
B)Technical security
C)Administrative security
D)Enterprise security

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
22
Consider the following list as you respond to the next question: i. An individual broke into a retail store's information system, stealing sensitive employee information
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which of the following statements is most true?
A)Examples i and ii describe two different types of computer criminals.
B)Examples iii and iv describe the same type of computer criminal.
C)Both A and B are true.
D)Neither A nor B is true.
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which of the following statements is most true?
A)Examples i and ii describe two different types of computer criminals.
B)Examples iii and iv describe the same type of computer criminal.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
23
Consider the following short case as you respond to the next question: Melissa is an internal auditor for the County of Bufflufia. Her job responsibilities include providing training on information systems security and checking the work of data entry clerks. Melissa is also part of a team that responds to denial-of-service attacks on the county's information system. Her co-worker, Eugene, ensures that all the county's computers have the most up-to-date antivirus software; he also enforces the county's policy of backing up sensitive data, such as employee social security numbers and other payroll information, at least once a day. The back-ups are dated and stored in a locked filing cabinet.Which employee has responsibilities related to technical security controls?
A)Melissa only
B)Eugene only
C)Both Melissa and Eugene
D)Neither Melissa nor Eugene
A)Melissa only
B)Eugene only
C)Both Melissa and Eugene
D)Neither Melissa nor Eugene

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
24
Based on the CoBIT accountability framework, which of the following statements is most true?
A)Julie, an employee of SNB Corporation, is accountable to SNB's board of directors.
B)Mark, a member of SNB Corporation's board of directors, is accountable to SNB's information security management employees.
C)Both A and B are true.
D)Neither A nor B is true.
A)Julie, an employee of SNB Corporation, is accountable to SNB's board of directors.
B)Mark, a member of SNB Corporation's board of directors, is accountable to SNB's information security management employees.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
25
Randall works in the information security department of RDN Corporation; Felix is on the board of directors of RDN. Which of the following statements is most true?
A)Randall should inform Felix about information governance control.
B)Felix should inform Randall about information governance control.
C)Only Felix is accountable to RDN's shareholders.
D)Felix can never interact with RDN's external auditors.
A)Randall should inform Felix about information governance control.
B)Felix should inform Randall about information governance control.
C)Only Felix is accountable to RDN's shareholders.
D)Felix can never interact with RDN's external auditors.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
26
All of the following are elements of the CIA triad except:
A)Clarity
B)Confidentiality
C)Availability
D)Data integrity
A)Clarity
B)Confidentiality
C)Availability
D)Data integrity

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
27
At HCK Corporation, only employees in the information systems department can install new software on a computer. Which type of security control best describes that practice?
A)Physical
B)Technical
C)Administrative
D)Practice
A)Physical
B)Technical
C)Administrative
D)Practice

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
28
The CoBIT framework discusses seven information criteria. Consider the pairs of items below; which one violates the criterion indicated?
A)Effectiveness: market value of short-term investments
B)Confidentiality: employee payroll data are kept in a locked filing cabineta
C)Integrity: variances between expected sales and actual sales
D)Compliance: general-purpose financial statements included in a 10-K filing
A)Effectiveness: market value of short-term investments
B)Confidentiality: employee payroll data are kept in a locked filing cabineta
C)Integrity: variances between expected sales and actual sales
D)Compliance: general-purpose financial statements included in a 10-K filing

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
29
BSD Corporation developed an internal control plan using the COSO framework. Based on the CoBIT accountability framework, which of the following statements is most true?
A)External auditors are responsible to all organizational stakeholders for communicating information from the plan.
B)The board of directors is responsible to all organizational stakeholders for communicating information from the plan.
C)Both A and B are true.
D)Neither A nor B is true.
A)External auditors are responsible to all organizational stakeholders for communicating information from the plan.
B)The board of directors is responsible to all organizational stakeholders for communicating information from the plan.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
30
Consider the following list as you respond to the next question: i. An individual broke into a retail store's information system, stealing sensitive employee information
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which of the following statements is most true?
A)Examples i and ii describe the same type of computer criminal.
B)Examples iii and iv describe the same type of computer criminal.
C)Both A and B is true.
D)Neither A nor B is true.
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which of the following statements is most true?
A)Examples i and ii describe the same type of computer criminal.
B)Examples iii and iv describe the same type of computer criminal.
C)Both A and B is true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
31
Consider the following short case as you respond to the next question: Melissa is an internal auditor for the County of Bufflufia. Her job responsibilities include providing training on information systems security and checking the work of data entry clerks. Melissa is also part of a team that responds to denial-of-service attacks on the county's information system. Her co-worker, Eugene, ensures that all the county's computers have the most up-to-date antivirus software; he also enforces the county's policy of backing up sensitive data, such as employee social security numbers and other payroll information, at least once a day. The back-ups are dated and stored in a locked filing cabinet.Which employee has responsibilities related to all three elements of the CIA triad?
A)Melissa only
B)Eugene only
C)Both Melissa and Eugene
D)Neither Melissa nor Eugene
A)Melissa only
B)Eugene only
C)Both Melissa and Eugene
D)Neither Melissa nor Eugene

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
32
WER Corporation forces its employees to change their system password every six months. Which type of security control best describes the company's policy?
A)Physical
B)Technical
C)Administrative
D)Hacking
A)Physical
B)Technical
C)Administrative
D)Hacking

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
33
Organized crime and hackers are most likely to be included in which element of an enterprise risk management plan based on the COSO framework?
A)Internal environment
B)Event identification
C)Objective setting
D)Control activities
A)Internal environment
B)Event identification
C)Objective setting
D)Control activities

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
34
Which type of computer criminal is likely to launch a denial-of-service attack?
A)Terrorist
B)Hacker
C)Both A and B
D)Neither A nor B
A)Terrorist
B)Hacker
C)Both A and B
D)Neither A nor B

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
35
Consider the following short case as you respond to the next question: Melissa is an internal auditor for the County of Bufflufia. Her job responsibilities include providing training on information systems security and checking the work of data entry clerks. Melissa is also part of a team that responds to denial-of-service attacks on the county's information system. Her co-worker, Eugene, ensures that all the county's computers have the most up-to-date antivirus software; he also enforces the county's policy of backing up sensitive data, such as employee social security numbers and other payroll information, at least once a day. The back-ups are dated and stored in a locked filing cabinet.Melissa's responsibilities relate to which elements of the CIA triad?
A)Confidentiality and availability
B)Confidentiality and data integrity
C)Availability and data integrity
D)None of the above
A)Confidentiality and availability
B)Confidentiality and data integrity
C)Availability and data integrity
D)None of the above

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
36
Based on the CoBIT accountability framework, which of the following statements is most true?
A)Maria, a member of the Board of Directors, should give information on information governance control to any corporate stakeholder who asks for it.
B)Erin, the lead partner on a corporation's external audit team, should share information only with the board of directors.
C)Both A and B are true.
D)Neither A nor B is true.
A)Maria, a member of the Board of Directors, should give information on information governance control to any corporate stakeholder who asks for it.
B)Erin, the lead partner on a corporation's external audit team, should share information only with the board of directors.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
37
Consider the following list as you respond to the next question: i. An individual broke into a retail store's information system, stealing sensitive employee information
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which items in the list are examples of organized crime?
A)iii only
B)iv only
C)Both iii and iv
D)Neither iii nor iv
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which items in the list are examples of organized crime?
A)iii only
B)iv only
C)Both iii and iv
D)Neither iii nor iv

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
38
CoBIT's information criteria include all of the following except:
A)The elements of the CIA triad.
B)Effectiveness and efficiency.
C)Truthfulness.
D)Compliance and reliability.
A)The elements of the CIA triad.
B)Effectiveness and efficiency.
C)Truthfulness.
D)Compliance and reliability.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
39
Consider the following list as you respond to the next question: i. An individual broke into a retail store's information system, stealing sensitive employee information
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which items in the list are examples of cyber-criminals?
A)ii only
B)iii only
C)Both ii and iii
D)Neither ii nor iii
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which items in the list are examples of cyber-criminals?
A)ii only
B)iii only
C)Both ii and iii
D)Neither ii nor iii

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
40
Consider the following short case as you respond to the next question: Melissa is an internal auditor for the County of Bufflufia. Her job responsibilities include providing training on information systems security and checking the work of data entry clerks. Melissa is also part of a team that responds to denial-of-service attacks on the county's information system. Her co-worker, Eugene, ensures that all the county's computers have the most up-to-date antivirus software; he also enforces the county's policy of backing up sensitive data, such as employee social security numbers and other payroll information, at least once a day. The back-ups are dated and stored in a locked filing cabinet.Which of the following statements is most true?
A)Eugene's responsibilities span both physical and technical controls.
B)Melissa's responsibilities are related to at least one element of the CIA triad.
C)Both A and B are true.
D)Neither A nor B is true.
A)Eugene's responsibilities span both physical and technical controls.
B)Melissa's responsibilities are related to at least one element of the CIA triad.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
41
The CoBIT framework identifies seven information criteria; the FASB conceptual framework includes four qualitative characteristics of accounting information, as well as several assumptions, principles and constraints. Which of the following statements about them is most true?
A)The "confidentiality" criterion in CoBIT contradicts the "full disclosure" principle in the FASB conceptual framework.
B)The "reliability of information" criterion in CoBIT is most closely related to one of the secondary qualitative characteristics in the FASB conceptual framework.
C)Both A and B are true.
D)Neither A nor B is true.
A)The "confidentiality" criterion in CoBIT contradicts the "full disclosure" principle in the FASB conceptual framework.
B)The "reliability of information" criterion in CoBIT is most closely related to one of the secondary qualitative characteristics in the FASB conceptual framework.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
42
Fill in the blanks below with appropriate terminology from CoBIT.
A. ______ auditors exchange information with one another to maintain strong corporate and IT governance.
B. ______ is directly responsible for choosing a public accounting firm to do external audits.
C. _______ holds IT and information security management accountable for value delivery, an element of IT governance.
D. __________ should provide information about risk management, an element of IT governance, to the board of directors.
E. Information about internal control flows two ways between the audit committee and ______.
F. Internal auditors exchange various kinds of information with corporate employees in ______.
G. Stakeholders rely on _____ for assurance about various forms of control.
H. The board of directors provides information about _____ to shareholders and employees.
I. Through the ___, external auditors interact with the corporate board of directors.j. Ultimately, ____ hold the board of directors accountable with respect to corporate governance.
A. internal and externalb. the audit committeec. the board of directorsd. information technology and information security managemente. external auditorsf. information technology and information security managementg. external auditorsh. financial a
A. ______ auditors exchange information with one another to maintain strong corporate and IT governance.
B. ______ is directly responsible for choosing a public accounting firm to do external audits.
C. _______ holds IT and information security management accountable for value delivery, an element of IT governance.
D. __________ should provide information about risk management, an element of IT governance, to the board of directors.
E. Information about internal control flows two ways between the audit committee and ______.
F. Internal auditors exchange various kinds of information with corporate employees in ______.
G. Stakeholders rely on _____ for assurance about various forms of control.
H. The board of directors provides information about _____ to shareholders and employees.
I. Through the ___, external auditors interact with the corporate board of directors.j. Ultimately, ____ hold the board of directors accountable with respect to corporate governance.
A. internal and externalb. the audit committeec. the board of directorsd. information technology and information security managemente. external auditorsf. information technology and information security managementg. external auditorsh. financial a

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
43
Based on the list provided in the text, indicate the type of computer criminal described in each of the following.
A. A young, inexperienced hacker who uses tools written by others for the purpose of attacking systems
b. Could seriously disrupt power grids, telecommunications and transportation
c. Hackers driven by financial gain
d. Recruit talented hackers to handle the technical aspects of crime
e. Someone who invades an information system for malicious purposes
f. Take advantage of networked systems by turning to computer intrusion techniques to gather the information they desire
g. The largest threat to a company's information systems
A. A young, inexperienced hacker who uses tools written by others for the purpose of attacking systems
b. Could seriously disrupt power grids, telecommunications and transportation
c. Hackers driven by financial gain
d. Recruit talented hackers to handle the technical aspects of crime
e. Someone who invades an information system for malicious purposes
f. Take advantage of networked systems by turning to computer intrusion techniques to gather the information they desire
g. The largest threat to a company's information systems

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
44
PCA Corporation maintains its fixed asset records in an Excel spreadsheet, as well as in its general ledger software. An internal auditor for PCA downloaded the Excel spreadsheet, then verified the information in it against both the general ledger software and the actual fixed assets in use. Which of the following statements is most true?
A)Internal auditors should not be viewed as a form of internal control.
B)PCA is legally required to follow the CoBIT accountability framework, which includes internal auditors, to meet the information criterion of compliance.
C)The internal auditor's actions help PCA achieve integrity in its information.
D)Information about fixed assets is confidential; the internal auditor's actions conflict with the information criterion of confidentiality.
A)Internal auditors should not be viewed as a form of internal control.
B)PCA is legally required to follow the CoBIT accountability framework, which includes internal auditors, to meet the information criterion of compliance.
C)The internal auditor's actions help PCA achieve integrity in its information.
D)Information about fixed assets is confidential; the internal auditor's actions conflict with the information criterion of confidentiality.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
45
An organization that uses the CoBIT framework to strengthen internal controls wants to improve the confidentiality of its information. Which of the following internal controls will best help achieve that goal?
A)Encryption
B)Security guards
C)Use of the COSO internal control framework
D)Adherence to the steps in the systems development life cycle
A)Encryption
B)Security guards
C)Use of the COSO internal control framework
D)Adherence to the steps in the systems development life cycle

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
46
List the elements of Carter's taxonomy of computer crime.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
47
CoBIT can be used to strengthen internal controls against computer crime by:
A)Ensuring that information produced by the AIS conforms to the framework's seven information criteria.
B)Clarifying reporting relationships and responsibilities via the accountability framework.
C)Both A and B are true.
D)Neither A nor B is true.
A)Ensuring that information produced by the AIS conforms to the framework's seven information criteria.
B)Clarifying reporting relationships and responsibilities via the accountability framework.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
48
The CoBIT framework can be used to strengthen internal controls against computer crime in various ways. Indicate whether each statement below is
(a) always true,
(b) sometimes true or
(c) never true.
a. As a form of internal control, each step of the systems development life cycle focuses on one of CoBIT's information criteria.
b. CoBIT can be used in conjunction with the COSO internal control framework to identify appropriate control activities.
c. CoBIT provides standards for evaluating information inputs and outputs that can help strengthen internal control.
d. The board of directors, as part of the CoBIT accountability framework, helps create a strong environment that values internal control and risk management.
e. The COSO enterprise risk management framework requires the use of CoBIT to identify risks.
(a) always true,
(b) sometimes true or
(c) never true.
a. As a form of internal control, each step of the systems development life cycle focuses on one of CoBIT's information criteria.
b. CoBIT can be used in conjunction with the COSO internal control framework to identify appropriate control activities.
c. CoBIT provides standards for evaluating information inputs and outputs that can help strengthen internal control.
d. The board of directors, as part of the CoBIT accountability framework, helps create a strong environment that values internal control and risk management.
e. The COSO enterprise risk management framework requires the use of CoBIT to identify risks.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
49
Jack conducted an Internet search for examples of computer crime that resulted in the items listed below. Which type of computer criminal is described in each? Be as specific as possible in your responses.
A. Boris and Natasha coordinated ten people who sent out e-mails asking the recipients to purchase fake lottery tickets.
B. Gil, an IT consultant for DMM Corporation, stole personal information about corporate executives and sold it to tabloid newspapers.
C. Marie, the chief information officer of RBC Corporation, planted a logic bomb in case she ever lost her job.
D. Timothy shut down traffic lights on a major street in his city in an effort to cause serious traffic accidents.
E. Zachary used a computer program he found on the Internet to "kill" characters in an online game.
A. Boris and Natasha coordinated ten people who sent out e-mails asking the recipients to purchase fake lottery tickets.
B. Gil, an IT consultant for DMM Corporation, stole personal information about corporate executives and sold it to tabloid newspapers.
C. Marie, the chief information officer of RBC Corporation, planted a logic bomb in case she ever lost her job.
D. Timothy shut down traffic lights on a major street in his city in an effort to cause serious traffic accidents.
E. Zachary used a computer program he found on the Internet to "kill" characters in an online game.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
50
The CoBIT framework looks at the issue of internal control from three points of view. An organization's hardware and software configuration is most closely related to:
A)Business objectives.
B)Information technology resources.
C)Information technology processes.
D)Information criteria.
A)Business objectives.
B)Information technology resources.
C)Information technology processes.
D)Information criteria.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
51
The CoBIT framework identifies seven information criteria; the FASB conceptual framework includes four qualitative characteristics of accounting information, as well as several assumptions, principles and constraints. Which of the following statements about them is most true?
A)The "effectiveness" criterion in CoBIT is related to the primary qualitative characteristic of "relevance" in the FASB conceptual framework.
B)The "cost effectiveness" constraint in the FASB conceptual framework and the "effectiveness" criterion in CoBIT express the same idea in different ways.
C)Both A and B are true.
D)Neither A nor B is true.
A)The "effectiveness" criterion in CoBIT is related to the primary qualitative characteristic of "relevance" in the FASB conceptual framework.
B)The "cost effectiveness" constraint in the FASB conceptual framework and the "effectiveness" criterion in CoBIT express the same idea in different ways.
C)Both A and B are true.
D)Neither A nor B is true.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
52
The chapter discussed the four elements of Carter's taxonomy of computer crime, eleven business risks / threats to information systems and seven common types of computer criminals. Classify each item below using each of them. 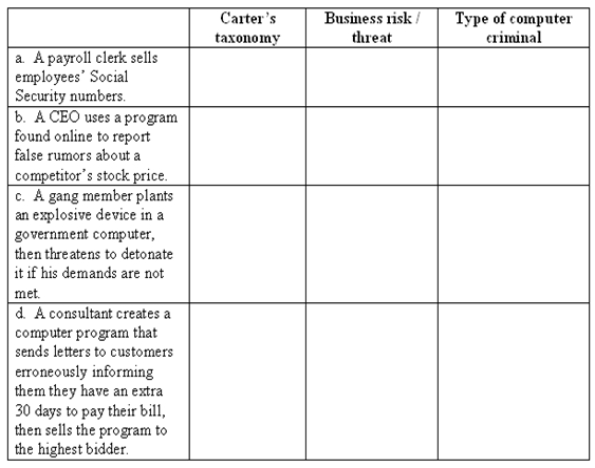


Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
53
Information technology controls can be classified as physical, technical or administrative. Consider each independent situation below; suggest one control from the indicated classification that would address (prevent / detect / correct) the risk.a) A bank's customer database is hacked.Administrative: _____________________________________________
b) A careless employee spills coffee on a network server.Physical: _____________________________________________
c) A corporation's sales data are manipulated by a member of the sales staff. Technical: _____________________________________________
d) A former employee introduces a logic bomb to a company's payroll system.Administrative: _____________________________________________
e) A political candidate's web site is defaced.Technical: _____________________________________________
f) A senior citizen sends money to a fake religious organization based on a fraudulent e-mail.Administrative: _____________________________________________
g) A waitress steals a customer's credit card number.Physical: _____________________________________________
h) An employee uses work time to shop online using the company's computer. Administrative: _____________________________________________
i) Corporate spies steal research and development information. Technical: _____________________________________________
j) Fake compromising photos of a corporate CEO are posted to a social networking site. Technical: _____________________________________________
A. regular security auditsb. encase the server in a cabinetc. system access logd. policy to remove employees from the system when they leave the companye. password rotationf. security trainingg. customers pay at the registerh. appropriate use poli
b) A careless employee spills coffee on a network server.Physical: _____________________________________________
c) A corporation's sales data are manipulated by a member of the sales staff. Technical: _____________________________________________
d) A former employee introduces a logic bomb to a company's payroll system.Administrative: _____________________________________________
e) A political candidate's web site is defaced.Technical: _____________________________________________
f) A senior citizen sends money to a fake religious organization based on a fraudulent e-mail.Administrative: _____________________________________________
g) A waitress steals a customer's credit card number.Physical: _____________________________________________
h) An employee uses work time to shop online using the company's computer. Administrative: _____________________________________________
i) Corporate spies steal research and development information. Technical: _____________________________________________
j) Fake compromising photos of a corporate CEO are posted to a social networking site. Technical: _____________________________________________
A. regular security auditsb. encase the server in a cabinetc. system access logd. policy to remove employees from the system when they leave the companye. password rotationf. security trainingg. customers pay at the registerh. appropriate use poli

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
54
The CoBIT framework looks at the issue of internal control from three points of view. If NTS Corporation's strategic plan includes a statement about planned increases in sales, which of the following statements is most true?
A)The statement is unrelated to any of the three points of view.
B)The statement is related to the "business objective" point of view.
C)The statement is meaningful only if the planned increases were predicted with a computer model.
D)The statement ensures that sales figures conform to all seven information criteria in the CoBIT framework.
A)The statement is unrelated to any of the three points of view.
B)The statement is related to the "business objective" point of view.
C)The statement is meaningful only if the planned increases were predicted with a computer model.
D)The statement ensures that sales figures conform to all seven information criteria in the CoBIT framework.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
55
The CoBIT framework identifies seven information criteria. In each example below, indicate one criterion that is met AND one that is not met in the space provided. 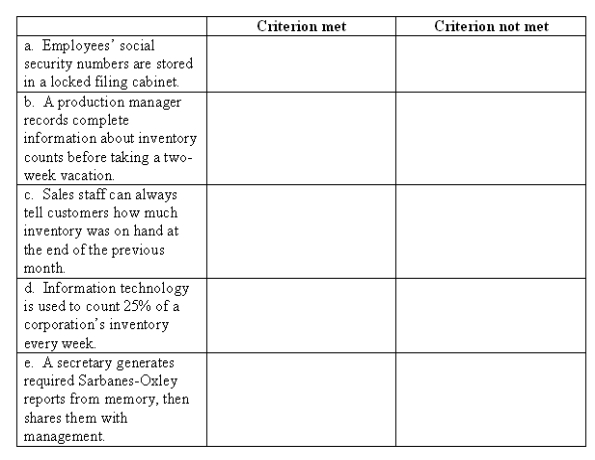


Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
56
Which element of Carter's taxonomy of computer crime is associated with each item below?
A. Computer is not required for the crime but is related to the criminal act
b. Computer is used to commit the crime
c. Computer use may make a crime more difficult to trace
d. Growth of the Internet creates new ways of reaching victims
e. Objective is to impact the confidentiality, availability and / or integrity of data
f. Presence of computers has generated new versions of fairly traditional crimes
g. Targets the system or its data
h. Technological growth creates new crime targets
i. Use of the computer simplifies criminal actions
j. Uses the computer to further a criminal end
A. Computer is not required for the crime but is related to the criminal act
b. Computer is used to commit the crime
c. Computer use may make a crime more difficult to trace
d. Growth of the Internet creates new ways of reaching victims
e. Objective is to impact the confidentiality, availability and / or integrity of data
f. Presence of computers has generated new versions of fairly traditional crimes
g. Targets the system or its data
h. Technological growth creates new crime targets
i. Use of the computer simplifies criminal actions
j. Uses the computer to further a criminal end

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
57
The CoBIT framework is divided into four domains of knowledge. Suppose TPC Corporation uses the systems development life cycle for new IT projects. Which of the following statements is most true?
A)The systems development life cycle cannot be used as a form of internal control; it is therefore unrelated to the CoBIT framework.
B)The seven steps in the systems development life cycle span all four domains of knowledge from the CoBIT framework.
C)The CoBIT framework requires the use of the systems development life cycle as a form of internal control.
D)Using the systems development life cycle prohibits TPC from using CoBIT.
A)The systems development life cycle cannot be used as a form of internal control; it is therefore unrelated to the CoBIT framework.
B)The seven steps in the systems development life cycle span all four domains of knowledge from the CoBIT framework.
C)The CoBIT framework requires the use of the systems development life cycle as a form of internal control.
D)Using the systems development life cycle prohibits TPC from using CoBIT.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
58
The CoBIT framework is divided into four domains of knowledge; the text discussed three types of controls related to information security. Which of the following statements is most true?
A)In the "plan and organize" domain, systems designers should think about all three types of controls.
B)Only technical security controls are relevant in the "deliver and support" domain.
C)Administrative security controls are relevant only in the "plan and organize" domain.
D)No controls are necessary in the "monitor and evaluate" domain.
A)In the "plan and organize" domain, systems designers should think about all three types of controls.
B)Only technical security controls are relevant in the "deliver and support" domain.
C)Administrative security controls are relevant only in the "plan and organize" domain.
D)No controls are necessary in the "monitor and evaluate" domain.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
59
In each statement that follows, circle the business risk or threat that most clearly applies based on the list provided in the text.
A. Disclosure of confidential information or intrusion: Employee data are made available on the Internet.
B. DOS attacks or extortion: Prevent computer systems from functioning in accordance with their intended purpose.
C. Error or web site defacement: Digital graffiti
d. Fraud or error: Losses can vary widely depending on where the problem originated.
E. Information theft or information manipulation: An employee creates fake refunds to benefit a family member.
F. Intrusion or extortion: Main objective is to gain access to a network.
G. Intrusion or service interruption: Classified as accidental, willful neglect or malicious behavior.
H. Malicious software or information theft: Logic bombs, replicating worm, Trojan horse.
I. Service interruption or disclosure of confidential information: Can lead to missed deadlines for receivables or payables.j. Web site defacement or extortion: Criminal contacts an organization after successfully stealing information.
A. Disclosure of confidential information or intrusion: Employee data are made available on the Internet.
B. DOS attacks or extortion: Prevent computer systems from functioning in accordance with their intended purpose.
C. Error or web site defacement: Digital graffiti
d. Fraud or error: Losses can vary widely depending on where the problem originated.
E. Information theft or information manipulation: An employee creates fake refunds to benefit a family member.
F. Intrusion or extortion: Main objective is to gain access to a network.
G. Intrusion or service interruption: Classified as accidental, willful neglect or malicious behavior.
H. Malicious software or information theft: Logic bombs, replicating worm, Trojan horse.
I. Service interruption or disclosure of confidential information: Can lead to missed deadlines for receivables or payables.j. Web site defacement or extortion: Criminal contacts an organization after successfully stealing information.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
60
A denial-of-service attack prevents computer systems from functioning in accordance with their intended purpose. Thus, a denial-of-service attack is most closely related to which information criterion from the CoBIT framework?
A)Availability
B)Confidentiality
C)Compliance
D)Information governance
A)Availability
B)Confidentiality
C)Compliance
D)Information governance

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
61
Ethan is an information technology security consultant. He has been asked to speak to a local professional organization about ways to strengthen internal controls against computer crime, and wants to relate his comments to the CoBIT framework. Prepare a short summary of the key points Ethan should make in his presentation; ensure that each one has a clear relationship to the CoBIT framework.

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
62
The chapter discussed seven types of computer criminals and eleven examples of risks and threats to information systems. Consider the items below, each of which pairs a type of computer criminal with a risk; provide a specific example based on both items.
A. Organized crime, extortion
b. Terrorist, service interruption / delay
c. Insider, error
d. Cyber-criminal, information theft
A. Organized crime, extortion
b. Terrorist, service interruption / delay
c. Insider, error
d. Cyber-criminal, information theft

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck
63
In your own words, explain the relationship between each of the following groups found in the CoBIT accountability framework:
A. Audit committee, external audit
b. Board of directors, IT and information security management
c. Employees, board of directors
A. Audit committee, external audit
b. Board of directors, IT and information security management
c. Employees, board of directors

Unlock Deck
Unlock for access to all 63 flashcards in this deck.
Unlock Deck
k this deck


