Deck 10: Planning for Contingencies
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/29
Play
Full screen (f)
Deck 10: Planning for Contingencies
1
What is the most widely accepted biometric authorization technology? Why?
IRIS scanning is the most widely accepted authorization technology.
The reasons for the same are as mentioned below:
1. Equipment required in this technology are in-expensive.
2. Technology is widely acceptable.
3. Only the snapshot of the eye serve the purpose, and it is quite easy to use.
The reasons for the same are as mentioned below:
1. Equipment required in this technology are in-expensive.
2. Technology is widely acceptable.
3. Only the snapshot of the eye serve the purpose, and it is quite easy to use.
2
Why is TCP port 80 always of critical importance when securing an organization's network?
Port 80 is default port number of the web server. It has been designed to listens the request from the web client using http daemon to the authorised user.
Web Server listen the inbound connection requested from the browser or from web applications, and in return web browsers or the applications receive the responses from the port 80. It is always open by default, and thus, there is always a fear of intrusion from hackers. They can try to expose the vulnerable information related to the configuration of web server to the network. To prevent this, port 80 requires strong Web Security.
Web Server listen the inbound connection requested from the browser or from web applications, and in return web browsers or the applications receive the responses from the port 80. It is always open by default, and thus, there is always a fear of intrusion from hackers. They can try to expose the vulnerable information related to the configuration of web server to the network. To prevent this, port 80 requires strong Web Security.
3


How should RWW go about notifying its peers? What other procedures should Iris have the technician perform?
Following ways can be adopted by RWW to notify to its peers:
1. An email can be sent
2. News can be broadcasted using BBS site.
3. Alerts can be transmitted to various social, technical, discussion forums, etc.
Ms. I 's technician should perform the following procedures:
• Update in filter algorithms of server
• Run a pattern of virus to study its effect on computers, possible harms to system, data, etc.
• Development of algorithm, tool, utility to remove the virus.
• Solutions/suggestion to other vendors to incorporate in their anti-virus firewalls
• Warning and awareness to the users that how it spreads and its symptoms and remedial action to be taken if such symptoms are confirmed.
• User community- FAQ's pages on company's web site should be immediately formed, and helpline should be started.
1. An email can be sent
2. News can be broadcasted using BBS site.
3. Alerts can be transmitted to various social, technical, discussion forums, etc.
Ms. I 's technician should perform the following procedures:
• Update in filter algorithms of server
• Run a pattern of virus to study its effect on computers, possible harms to system, data, etc.
• Development of algorithm, tool, utility to remove the virus.
• Solutions/suggestion to other vendors to incorporate in their anti-virus firewalls
• Warning and awareness to the users that how it spreads and its symptoms and remedial action to be taken if such symptoms are confirmed.
• User community- FAQ's pages on company's web site should be immediately formed, and helpline should be started.
4
What kind of data and information can be found using a packet sniffer?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
5
Go to the Web site of VeriSign, one of the market leaders in digital certificates. Determine whether VeriSign serves as a registration authority, certificate authority, or both. Download its free guide to PKI and summarize VeriSign's services.

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
6
What are the main components of cryptology?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
7
What is the most effective biometric authorization technology? Why?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
8
Explain the relationship between plaintext and ciphertext.

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
9


When would be the appropriate time to begin the forensic data collection process to analyze the root cause of this incident? Why?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
10
Define asymmetric encryption. Why would it be of interest to information security professionals?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
11
Go to csrc.nist.gov and locate "Federal Information Processing Standard (FIPS) 197." What encryption standard does this address use? Examine the contents of this publication and describe the algorithm discussed. How strong is it? How does it encrypt plaintext?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
12
One tenet of cryptography is that increasing the work factor to break a code increases the security of that code. Why is that true?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
13
What is the typical relationship between the untrusted network, the firewall, and the trusted network?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
14
Explain the key differences between symmetric and asymmetric encryption. Which can the computer process faster? Which lowers the costs associated with key management?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
15
Search the Internet for vendors of biometric products. Find one vendor with a product designed to examine each characteristic mentioned in Figure 10-4. What is the crossover error rate (CER) associated with each product? Which would be more acceptable to users? Which would be preferred by security administrators?
Reference: Figure 10-4
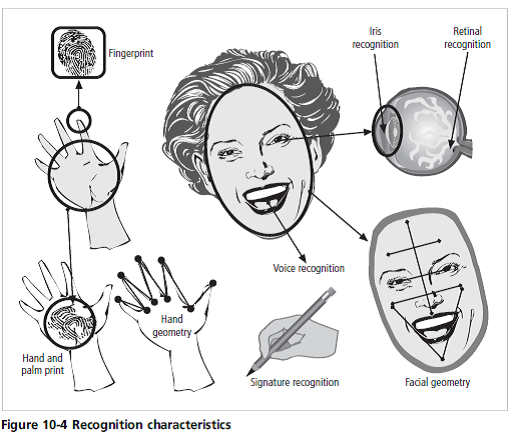
Reference: Figure 10-4


Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
16
What is a VPN? Why are VPNs widely used?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
17
How is an application-layer firewall different from a packet filtering firewall? Why is an application-layer firewall sometimes called a proxy server?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
18
What special function does a cache server perform? Why does this function have value for larger organizations?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
19
How does screened-host firewall architecture differ from screened-subnet firewall architecture? Which offers more security for the information assets that remain on the trusted network?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
20


What can be done to minimize the risk of this situation recurring? Can these types of situations be completely avoided?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
21
What is a DMZ? Is this really a good name for the function that this type of subnet performs?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
22
Create a spreadsheet that takes eight values input into eight different cells and then applies a transposition cipher to them. Next, create a row that takes the results and applies a substitution cipher to them (substitute 0 for 5, 1 for 6, 2 for 7, 3 for 8, 4 for 9, and vice versa).

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
23
What is RADIUS? What advantage does it have over TACACS?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
24
What is the difference between authentication and authorization? Can a system permit authorization without authentication? Why or why not?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
25
How does a network-based IDPS differ from a host-based IDPS?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
26
Iris's smartphone beeped. Frowning, she glanced at the screen, expecting to see another junk e-mail. "We've really got to do something about the spam!" she muttered to herself. She scanned the header of the message.
"Uh-oh!" She glanced at her watch, and while looking at her incident response pocket card, dialed the home number of the on-call systems administrator. When he answered, she asked
"Seen the alert yet? What's up?"
"Wish I knew-some sort of virus," he replied. "A user must have opened an infected attachment."
Iris made a mental note to remind the awareness program manager to restart the refresher training program for virus control. Her users should know better, but some new employees had not been trained yet.
"Why didn't the firewall catch it?" Iris asked.
"It must be a new one," he replied. "It slipped by the pattern filters."
"What are we doing now?" Iris was growing more nervous by the minute.
"I'm ready to cut our Internet connection remotely, then drive down to the office and start our planned recovery operations-shut down infected systems, clean up any infected servers, recover data from tape backups, and notify our peers that they may receive this virus from us in our e-mail. I just need your go-ahead." The admin sounded uneasy. This was not a trivial operation, and he was facing a long night of intense work.
"Do it. I'll activate the incident response plan and start working the notification call list to get some extra hands in to help." Iris knew this situation would be the main topic at the weekly CIO's meeting. She just hoped her colleagues would be able to restore the systems to safe operation quickly. She looked at her watch: 12:35 a.m.
If you were in Iris's position, how would you approach your interaction with the second-shift operator?
"Uh-oh!" She glanced at her watch, and while looking at her incident response pocket card, dialed the home number of the on-call systems administrator. When he answered, she asked
"Seen the alert yet? What's up?"
"Wish I knew-some sort of virus," he replied. "A user must have opened an infected attachment."
Iris made a mental note to remind the awareness program manager to restart the refresher training program for virus control. Her users should know better, but some new employees had not been trained yet.
"Why didn't the firewall catch it?" Iris asked.
"It must be a new one," he replied. "It slipped by the pattern filters."
"What are we doing now?" Iris was growing more nervous by the minute.
"I'm ready to cut our Internet connection remotely, then drive down to the office and start our planned recovery operations-shut down infected systems, clean up any infected servers, recover data from tape backups, and notify our peers that they may receive this virus from us in our e-mail. I just need your go-ahead." The admin sounded uneasy. This was not a trivial operation, and he was facing a long night of intense work.
"Do it. I'll activate the incident response plan and start working the notification call list to get some extra hands in to help." Iris knew this situation would be the main topic at the weekly CIO's meeting. She just hoped her colleagues would be able to restore the systems to safe operation quickly. She looked at her watch: 12:35 a.m.
If you were in Iris's position, how would you approach your interaction with the second-shift operator?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
27
What is network footprinting? What is network fingerprinting? How are they related?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
28
Search the Internet for information about a technology called personal or home office firewalls. Examine the various alternatives, select three of the options, and compare their functionalities, cost, features, and types of protection.

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck
29
Why do many organizations ban port scanning activities on their internal networks? Why would ISPs ban outbound port scanning by their customers?

Unlock Deck
Unlock for access to all 29 flashcards in this deck.
Unlock Deck
k this deck


