Deck 9: Network and Internet Security
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/90
Play
Full screen (f)
Deck 9: Network and Internet Security
1
It is important to select strong passwords and change them frequently.
True
2
Antispam programs are used to detect and remove any viruses or worms that find their way onto your computer.
False
3
Like a computer virus, a computer worm infects other computer files to replicate itself.
False
4
A fingerprint recognition system is typically used to protect access to office computers, to automatically supply Web site passwords on home computers, and to pay for products or services.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
5
Private key encryption is also called symmetric key encryption.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
6
Biometric authentication uses information that an individual should know or can easily remember.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
7
Wi-Fi security features work by default.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
8
The Fair and Accurate Credit Transactions Act (FACTA) enables all Americans to get a free copy of their credit report, upon request, each year from the three major consumer credit bureaus.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
9
Botnets are a major security threat since criminals are increasingly creating botnets to use for computer sabotage.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
10
A relatively new type of scam involves posting fake job listings on job search sites to elicit personal information (such as Social Security numbers) from job seekers.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
11
Many Internet security concerns today can be categorized as cybercrimes.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
12
Denial of service attacks are usually of insignificant cost in terms of business lost.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
13
Possessed knowledge access systems use physical objects for identification purposes and are frequently used to access facilities and computer systems.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
14
Information used in identity theft can be obtained by skimming or via social engineering.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
15
Unauthorized use involves using a computer resource for unauthorized activities.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
16
While two-factor authentication systems are common in the United States, they are not widely used in other countries.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
17
Writing a computer virus or other type of malware or even posting the malware code on the Internet is not illegal, but it is considered highly unethical and irresponsible behavior.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
18
When you send someone an encrypted message using public key encryption, only a public key is necessary to decrypt it.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
19
A firewall is a security system that essentially creates a barrier between a computer or network and the Internet in order to protect against unauthorized access.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
20
Fortunately, identity theft is declining and poses a much smaller danger to individuals today.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
21
A type of computer infection occurs when a hacker breaches a computer system in order to delete data, change data, modify programs, or otherwise alter the data and programs located there. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
22
Advocates of ____ state that, unless individuals or businesses protect their access points, they are welcoming others to use them.
A) spoofing
B) phishing
C) spamming
D) war driving
A) spoofing
B) phishing
C) spamming
D) war driving

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
23
Strong passwords are passwords that are at least eight characters long. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
24
____ refers to the act of breaking into a computer or network.
A) Spamming
B) Phishing
C) Hacking
D) Spoofing
A) Spamming
B) Phishing
C) Hacking
D) Spoofing

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
25
A computer that is controlled by a hacker or other computer criminal is referred to as a(n) botherder or zombie computer. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
26
In spoofing, terrorists launch attacks via the Internet. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
27
Cuts or other changes to a finger may prevent access via a(n) keystroke reader. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
28
Phishing schemes use legitimate-looking e-mails to trick users into providing private information. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
29
Spear phishing e-mails are directly targeted to a specific individual and typically appear to come from an organization or person that the targeted individual has an association with. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
30
To avoid the need to obtain the recipient's public key before sending that person an encrypted e-mail, proprietary encrypted e-mail can be used. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
31
According to a recent study, the total cost per data breach in ____ is $5.4 million-the highest of any country.
A) India
B) China
C) Russia
D) the United States
A) India
B) China
C) Russia
D) the United States

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
32
A(n) denial of service (DoS) attack is an act of sabotage that attempts to flood a network server or Web server with so many requests for action that it cannot handle legitimate requests any longer. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
33
Packetsniffing systems determine whether or not the person attempting access is actually who he or she claims to be. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
34
Online auction spam occurs when an item purchased through an online auction is never delivered after payment, or the item is not as specified by the seller. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
35
AntiDoS software is used to detect and eliminate computer viruses and other types of malware. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
36
Computer spyware includes any illegal act involving a computer. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
37
To explain acceptable computer use to their employees, students, or other users, many organizations and educational institutions publish guidelines for behavior, often called ____.
A) cybercrime protocols
B) codes of conduct
C) anithacking rules
D) school rules
A) cybercrime protocols
B) codes of conduct
C) anithacking rules
D) school rules

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
38
Numeric passwords are referred to passcodes. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
39
Computer crime is sometimes referred to as ____.
A) hacking
B) cybercrime
C) cyberstalking
D) spoofing
A) hacking
B) cybercrime
C) cyberstalking
D) spoofing

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
40
USB security keys are also called USB security tokens. _________________________

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
41
____ uses a single secret key to both encrypt and decrypt the file or message.
A) Private key encryption
B) Asymmetric key encryption
C) Public key encryption
D) Synchronous key encryption
A) Private key encryption
B) Asymmetric key encryption
C) Public key encryption
D) Synchronous key encryption

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
42
____ identify users by a particular unique biological characteristic.
A) Possessed object access systems
B) Password access systems
C) Possessed knowledge access systems
D) Biometric access systems
A) Possessed object access systems
B) Password access systems
C) Possessed knowledge access systems
D) Biometric access systems

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
43
Like a computer virus, a ____ is a malicious program designed to cause damage.
A) computer worm
B) scam
C) phish
D) computer bug
A) computer worm
B) scam
C) phish
D) computer bug

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
44
Antivirus programs are usually set up to automatically download new ____ from their associated Web site on a regular basis.
A) threat definitions
B) viruses
C) fraud tips
D) virus reports
A) threat definitions
B) viruses
C) fraud tips
D) virus reports

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
45
____, the most commonly used type of possessed knowledge, are secret words or character combinations associated with an individual.
A) Usernames
B) PINs
C) Passwords
D) Codes
A) Usernames
B) PINs
C) Passwords
D) Codes

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
46
____ is a generic term that refers to any type of malicious software.
A) Spamware
B) Malware
C) Spyware
D) Badware
A) Spamware
B) Malware
C) Spyware
D) Badware

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
47
____ includes any acts of malicious destruction to a computer or computer resource.
A) Phishing attacks
B) Blocking attacks
C) Computer sabotage
D) Spoofing attacks
A) Phishing attacks
B) Blocking attacks
C) Computer sabotage
D) Spoofing attacks

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
48
Some Web-based encrypted e-mail systems-such as the popular free ____ service-require both the sender and recipient to have accounts through that system.
A) CryptMail
B) QuietMail
C) HushMail
D) PrivateMail
A) CryptMail
B) QuietMail
C) HushMail
D) PrivateMail

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
49
The term ____ refers to accessing someone else's unsecured Wi-Fi network from the hacker's current location (such as inside his or her home, outside a Wi-Fi hotspot location, or near a local business).
A) war driving
B) Wi-Fi piggybacking
C) Wi-Fi worming
D) denial of service
A) war driving
B) Wi-Fi piggybacking
C) Wi-Fi worming
D) denial of service

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
50
A booming area of computer crime involves online fraud, theft, scams, and related activities collectively referred to as ____.
A) e-cons
B) e-scams
C) dot frauds
D) dot cons
A) e-cons
B) e-scams
C) dot frauds
D) dot cons

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
51
A ____ is a security system that essentially creates a wall between a computer or network and the Internet in order to protect against unauthorized access.
A) Trojan horse
B) firewall
C) hub
D) bridge
A) Trojan horse
B) firewall
C) hub
D) bridge

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
52
A computer ____ spreads by creating copies of its code and sending those copies to other computers via a network.
A) virus
B) software
C) worm
D) hacker
A) virus
B) software
C) worm
D) hacker

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
53
____ access systems use physical objects for identification purposes and they are frequently used to control access to facilities and computer systems.
A) Touch object
B) Possessed object
C) Two-factor
D) Biometric
A) Touch object
B) Possessed object
C) Two-factor
D) Biometric

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
54
A computer that is controlled by a hacker or other computer criminal is referred to as a ____.
A) spider
B) server
C) client
D) bot
A) spider
B) server
C) client
D) bot

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
55
Increasingly, USB security keys, also called USB security ____-USB flash drives that are inserted into a computer to grant access to a network, to supply Web site usernames and passwords, or to provide other security features-are being used.
A) botherders
B) botnets
C) passes
D) tokens
A) botherders
B) botnets
C) passes
D) tokens

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
56
____ software can control which devices can be connected to an employee's computer.
A) Data-leakage prevention
B) Device authentication
C) Professional firewall
D) Network quarantine
A) Data-leakage prevention
B) Device authentication
C) Professional firewall
D) Network quarantine

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
57
A ____ provides a secure private tunnel from the user's computer through the Internet to another destination and is most often used to provide remote employees with secure access to a company network.
A) laptop private network
B) USB private network
C) tunnel private network
D) virtual private network
A) laptop private network
B) USB private network
C) tunnel private network
D) virtual private network

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
58
One emerging type of Trojan horse is called a ____-Access Trojan.
A) Demote
B) Remote
C) Control
D) Hacker
A) Demote
B) Remote
C) Control
D) Hacker

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
59
A ____ is a malicious program that masquerades as something else-usually as some type of application program.
A) Trojan horse
B) computer worm
C) computer insect
D) computer bug
A) Trojan horse
B) computer worm
C) computer insect
D) computer bug

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
60
A computer ____ is a software program that is installed without the permission or knowledge of the computer user, that is designed to alter the way a computer operates, and that can replicate itself to infect any new media it has access to.
A) phish
B) virus
C) bot
D) link
A) phish
B) virus
C) bot
D) link

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
61
____ occurs when someone obtains enough information about a person to be able to masquerade as that person for a variety of activities-usually to buy products or services in that person's name.
A) Data theft
B) Information theft
C) Identity theft
D) Database theft
A) Data theft
B) Information theft
C) Identity theft
D) Database theft

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
62
The best protection against many dot cons is ____.
A) contacting your ISP
B) updating the operating system
C) installing an antivirus program
D) common sense
A) contacting your ISP
B) updating the operating system
C) installing an antivirus program
D) common sense

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
63
A computer virus that activates when it detects a certain condition, such as when a particular keystroke is pressed, is called a(n) ____________________.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
64
In businesses, access control systems are often integrated into a comprehensive ____________________ system designed to manage users' access to enterprise systems.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
65
Phishing schemes may use a technique called ____, which is setting up spoofed Web sites with addresses slightly different from legitimate sites.
A) typosquatting
B) spamming
C) DoS attacks
D) identity theft
A) typosquatting
B) spamming
C) DoS attacks
D) identity theft

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
66
Once installed, ____________________ are designed to record every keystroke made on the infected computer and transmit account numbers, passwords, and other related information to criminals.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
67
Public key encryption is also called ____________________ encryption.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
68
Online fraud, theft, scams, and other related activities are collectively referred to as ____________________.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
69
When a digitally signed document is received, the recipient's computer uses the sender's ____ key to verify the digital signature.
A) private
B) public
C) organizational
D) token
A) private
B) public
C) organizational
D) token

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
70
____________________ access refers to individuals gaining access to a computer, network, file, or other resource without permission.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
71
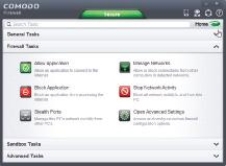
A(n) ____________________, such as the one shown in the accompanying figure, is a security system that essentially creates a barrier between a computer or a network and the Internet in order to protect against unauthorized access.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
72
A(n) ____________________ access system is an identification system that requires the individual requesting access to provide information that only the authorized user is supposed to know.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
73
Biometric access systems use a(n) ____________________ in conjunction with software and a database to match the supplied biometric data with the biometric data previously stored in the database to identify and authenticate an individual.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
74
____ is a type of scam that uses spoofed domain names to obtain personal information for use in fraudulent activities.
A) Framing
B) Fishing
C) Pharming
D) Farming
A) Framing
B) Fishing
C) Pharming
D) Farming

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
75
Typically, ____________________ begins with obtaining a person's name and Social Security number, often from a credit application, rental application, or similar form.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
76
The ____ includes provisions to combat cyberterrorism, including protecting ISPs against lawsuits from customers for revealing private information to law enforcement agencies.
A) Heath Insurance Portability and Accountability Act (HIPAA)
B) PROTECT Act
C) Homeland Security Act of 2002
D) National Information Infrastructure Protection Act
A) Heath Insurance Portability and Accountability Act (HIPAA)
B) PROTECT Act
C) Homeland Security Act of 2002
D) National Information Infrastructure Protection Act

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
77
Older 40-bit encryption (which can only use keys that are 40 bits or 5 characters long) is considered ____________________.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
78
A group of bots that are controlled by one individual and can work together in a coordinated fashion is called a(n) ____________________.

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
79
____ can be extremely distressing for victims, can take years to straighten out, and can be very expensive.
A) Spams
B) Identity theft
C) Remote access
D) Software theft
A) Spams
B) Identity theft
C) Remote access
D) Software theft

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck
80
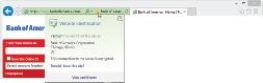
The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
A) EV
B) SK
C) SQL
D) HTTPS

Unlock Deck
Unlock for access to all 90 flashcards in this deck.
Unlock Deck
k this deck


