Deck 19: Networks
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/75
Play
Full screen (f)
Deck 19: Networks
1
A communications protocol is a set of rules for efficiently transmitting data from one network device to another.
True
2
Social networking services, such as Facebook and LinkedIn, are designed for people to reconnect with old friends and coworkers, and make new social or professional contacts.
True
3
Forum rooms provide a synchronous environment in which a group of participants share text-based information.
False
4
Ethernet is a wireless network technology and does not require a cable to connect network devices.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
5
A built-in referral system in the social network helps participants contact other participants with similar interests.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
6
When communication is synchronous , messages are held until the recipient is ready to view them.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
7
Software for accessing files stored in the cloud storage can only be built into software applications and browsers.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
8
Packets traveling on a single line always go to a single destination.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
9
Internet connections are classified as always-on connections if they remain active even when you are not online.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
10
In a network configured with a router, all network data travels to the router before continuing to its destination.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
11
A Wi-Fi hotspot is basically a wireless local area network that provides access to guests using laptop computers or mobile devices.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
12
All networks are secured.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
13
Homegroups are designed for computers with either the Windows operating system or Apple's OS X operating system.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
14
Cyberfraud is the repeated use of Internet-based communications technologies to deliberately harm other people through intimidation, humiliation, or embarrassment.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
15
A computer can have a permanently assigned dynamic IP address.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
16
NSP equipment and links are tied together by network service points.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
17
If your password is strong enough, do not change it.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
18
Text messaging is an asynchronous service; messages are delivered to a mobile device, where they are stored, and the recipient should delete them after they are viewed.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
19
A domain name ends with an extension that indicates its bottom-level domain.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
20
You always can assign a unique IP address to your computer.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
21
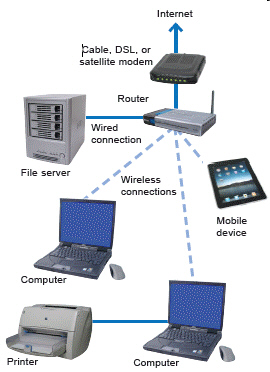 Referring to the accompanying figure, the connection point between the printer and the network is referred to as a _____.
Referring to the accompanying figure, the connection point between the printer and the network is referred to as a _____.A) link
B) point
C) device
D) node

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
22
The Internet is a global network that connects millions of smaller networks, computers, and other devices that exchange data using a standard communications protocol called _____.
A) IP/TCP
B) TPC/IP
C) TCP/IP
D) TCP
A) IP/TCP
B) TPC/IP
C) TCP/IP
D) TCP

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
23
The first time you want to connect to a secured network, you are required to enter the correct _____.
A) decryption key
B) user name and password
C) password
D) encryption key
A) decryption key
B) user name and password
C) password
D) encryption key

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
24
Your computer acts as a _____ that receives data or services.
A) network server
B) client
C) destination computer
D) data processing unit
A) network server
B) client
C) destination computer
D) data processing unit

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
25
Early communications networks, such as the telephone system, used a technology called _____ switching, which essentially established a dedicated, private link between two telephones for the duration of a call.
A) circuit
B) packet
C) connection
D) line
A) circuit
B) packet
C) connection
D) line

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following Internet Protocol addresses are divided into eight segments?
A) IPv6
B) IPv8
C) IPv4
D) IPv10
A) IPv6
B) IPv8
C) IPv4
D) IPv10

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
27
NSP stands for _____.
A) Network System Provider
B) Network Support Provider
C) Network Service Protocol
D) Network Service Provider
A) Network System Provider
B) Network Support Provider
C) Network Service Protocol
D) Network Service Provider

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
28
Packets can originate from _____ sources.
A) only one
B) not more than two
C) several
D) not more than five
A) only one
B) not more than two
C) several
D) not more than five

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
29
Discoverable network devices are listed under the _____ heading of File Explorer.
A) Homegroup
B) Network
C) Computer
D) Shared
A) Homegroup
B) Network
C) Computer
D) Shared

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
30
A router's wired _____ port can connect to a modem for Internet access.
A) uplink
B) outlink
C) inlink
D) onlink
A) uplink
B) outlink
C) inlink
D) onlink

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
31
The most popular type of wireless network is called _____.
A) Bluetooth
B) Ethernet
C) VPN
D) Wi-Fi
A) Bluetooth
B) Ethernet
C) VPN
D) Wi-Fi

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
32
A _____ network typically connects personal computers within a very limited geographical area.
A) local area
B) wide area
C) virtual
D) private
A) local area
B) wide area
C) virtual
D) private

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
33
Homegroups are designed for computers with the _____ operating system.
A) Windows
B) OS X
C) iOS
D) Android
A) Windows
B) OS X
C) iOS
D) Android

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
34
Which of the following is the domain name of the following Web address: www.msu.edu/infotech?
A) www.msu.edu
B) msu.edu
C) edu
D) msu.edu/infotech
A) www.msu.edu
B) msu.edu
C) edu
D) msu.edu/infotech

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
35
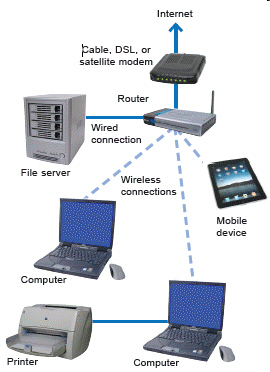 Referring to the accompanying figure, the _____ is serving the purpose of linking two or more nodes of the network.
Referring to the accompanying figure, the _____ is serving the purpose of linking two or more nodes of the network.A) file server
B) printer
C) router
D) modem

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
36
All of the following are secure network icons, except _____.
A)
B)
C)
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
37
SSID stands for _____.
A) service set identifier
B) service system identifier
C) system set identifier
D) single service identifier
A) service set identifier
B) service system identifier
C) system set identifier
D) single service identifier

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
38
To see a list of available networks when using Windows 7 or 8, click the _____ network icon, located in the notification area of the desktop.
A)
B)
C)
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following links devices within an organization?
A) Internet
B) intranet
C) extranet
D) virtual network
A) Internet
B) intranet
C) extranet
D) virtual network

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
40
A virtual private network (VPN) is a type of _____ that allows remote users to connect to a private network using a public communications system such as the Internet.
A) local area network
B) intranet
C) extranet
D) wide area network
A) local area network
B) intranet
C) extranet
D) wide area network

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following is the newest instant messaging platform?
A) AOL's AIM
B) Google Talk
C) Windows Messenger
D) ICQ
A) AOL's AIM
B) Google Talk
C) Windows Messenger
D) ICQ

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
42
A series of entries posted online similar to the entries in a diary is called a(n) _____.
A) blog
B) podcast
C) chat room
D) Facebook
A) blog
B) podcast
C) chat room
D) Facebook

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
43
Which of the following is Microsoft's cloud storage service?
A) SkyDrive
B) iCloud
C) Dropbox
D) Just Cloud
A) SkyDrive
B) iCloud
C) Dropbox
D) Just Cloud

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
44
_____ provides a way to transfer files from one computer to another over a network.
A) TCP
B) FTP
C) IPv6
D) IP
A) TCP
B) FTP
C) IPv6
D) IP

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
45
Which of the following is a video conferencing application?
A) Pinterest
B) Google Talk
C) Windows Messenger
D) GoToMeeting
A) Pinterest
B) Google Talk
C) Windows Messenger
D) GoToMeeting

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
46
Fast Internet connections, called broadband, blaze away at _____ or more.
A) 200 Mbps
B) 100 Mbps
C) 100Kbps
D) 50 Mbps
A) 200 Mbps
B) 100 Mbps
C) 100Kbps
D) 50 Mbps

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following top-level domains is designed for unrestricted use?
A) gov
B) edu
C) int
D) net
A) gov
B) edu
C) int
D) net

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
48
Which of the following top-level domains is restricted to organizations established by international treaties?
A) gov
B) info
C) int
D) biz
A) gov
B) info
C) int
D) biz

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
49
Which of the following is the most common Internet connection?
A) symmetrical
B) always-on
C) asymmetrical
D) downstream
A) symmetrical
B) always-on
C) asymmetrical
D) downstream

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
50
Which of the following is a broadband Internet access technology that works over standard phone lines?
A) cable Internet service
B) dial-up Internet service
C) satellite Internet service
D) DSL
A) cable Internet service
B) dial-up Internet service
C) satellite Internet service
D) DSL

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
51
Which of the following types of communications tools is used for social networking (Facebook)?
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following types of communications tools is used for chat rooms?
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
53
All of the Internet's domain names and corresponding IP addresses are stored on a system of computers called the _____.
A) Domain Name System
B) Domain Name Server
C) Domain Name Service
D) Domain Name Database
A) Domain Name System
B) Domain Name Server
C) Domain Name Service
D) Domain Name Database

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following types of communications tools is used for forums and discussion groups?
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following is LEAST likely related to a slow Internet connection?
A) the number of users logged in to your Internet service
B) the amount of traffic that is circulating on the Internet
C) environmental factors that affect the speed of wireless connections
D) the speed of your computer's processor
A) the number of users logged in to your Internet service
B) the amount of traffic that is circulating on the Internet
C) environmental factors that affect the speed of wireless connections
D) the speed of your computer's processor

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
56
Window's network troubleshooter provides a set of utilities to identify and fix all of the following problems, EXCEPT _____.
A) Internet connections
B) Windows registry
C) shared folders
D) network circuitry
A) Internet connections
B) Windows registry
C) shared folders
D) network circuitry

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
57
Mobile broadband service is offered by the following wireless cellular phone service providers, EXCEPT _____.
A) Comcast
B) Verizon
C) AT&T
D) Sprint
A) Comcast
B) Verizon
C) AT&T
D) Sprint

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
58
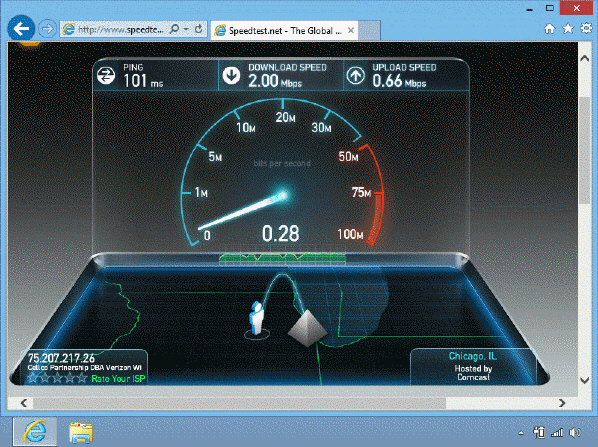 The tool shown in the accompanying figure allows you _____.
The tool shown in the accompanying figure allows you _____.A) to check the speed of your computer
B) to check the speed of your Internet connection
C) both a and b
D) neither a nor b

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following types of communications tools is used for voice over IP (Skype)?
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous
A) Public Asynchronous
B) Private Asynchronous
C) Public Synchronous
D) Private Synchronous

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
60
If your network fails and you cannot get an e-mail or browse the Internet, you should check that _____.
A) airplane mode is enabled
B) the router is functioning correctly
C) the wireless signal is strong enough
D) All of the above
A) airplane mode is enabled
B) the router is functioning correctly
C) the wireless signal is strong enough
D) All of the above

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
61
Each connection point on a network is referred to as a network ____________________.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
62
Network data is often stored on a network ____________________, such as one that handles e-mail or movie downloads.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
63
Case-Based Critical Thinking Questions Case 19-1 Leon made a presentation about netiquette. His presentation was followed by a very useful discussion. Answer the following questions that the audience asked him. Which of the following is among the most important rules of netiquette?
A) Distinguish between business and personal
B) Proofread messages before you send them
C) Respond promptly
D) All of the above
A) Distinguish between business and personal
B) Proofread messages before you send them
C) Respond promptly
D) All of the above

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
64
____________________ is online jargon for "Internet etiquette."

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
65
The ____________________ is maintained by network service providers (NSPs).

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
66
A Wi-Fi ____________________ is basically a wireless local area network that provides access to guests using laptop computers or mobile devices.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
67
A(n) ____________________ name is a key component of e-mail addresses and Web site addresses.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
68
Case-Based Critical Thinking Questions Case 19-1 Leon made a presentation about netiquette. His presentation was followed by a very useful discussion. Answer the following questions that the audience asked him. Which of the following is not appropriate etiquete for e-mail communications?
A) Promptly respond to messages
B) Type important messages in all uppercase
C) Be careful with wording
D) Do not spread false information
A) Promptly respond to messages
B) Type important messages in all uppercase
C) Be careful with wording
D) Do not spread false information

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
69
Please briefly describe the following three ways of connecting to the Internet: Cable Internet service, digital subscriber line, and dial-up Internet service.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
70
When a communications tool is ____________________, interchanges happen in real time and all parties must be online at the same time.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
71
The capacity of an Internet connection is sometimes referred to as ____________________ and can be measured in bits per second.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
72
A(n) ____________________ area network is one that covers a large geographical area and typically consists of several smaller networks.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
73
The chapter listed nine of the most commonly used top-level domains. Please name five of the nine and include a description of who can use each domain.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
74
When your computer is connected to a local area network, you have access to files designated as "____________________" on other network computers.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
75
Case-Based Critical Thinking Questions Case 19-1 Leon made a presentation about netiquette. His presentation was followed by a very useful discussion. Answer the following questions that the audience asked him. Which of the following should be avoided when communicating with businesses?
A) Use of smileys
B) Use of uppercase and lowercase letters
C) Use of more formal language
D) Tailoring your message
A) Use of smileys
B) Use of uppercase and lowercase letters
C) Use of more formal language
D) Tailoring your message

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck


