Deck 26: Communications and Collaboration
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/46
Play
Full screen (f)
Deck 26: Communications and Collaboration
1
The most widely used one-to-one communication on the Internet is e-mail.
True
2
You can attach any number of files to an e-mail message, regardless of the size.
False
3
The best way to protect data on a computer is to effectively control access.
True
4
____ is the process of selecting paths in a network along which to send network traffic.
A) Forwarding
B) Routing
C) Tagging
D) Phishing
A) Forwarding
B) Routing
C) Tagging
D) Phishing

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
5
A worm is a type of virus that has to attach itself to other files in order to spread.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
6
Most e-mail users report that their biggest problem is spam.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
7
E-mail is the best communication method to use when correspondence needs to be accessed in real time.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
8
Generally the communications media for teleconferencing is a telephone line.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
9
Which of the following allows people to use voice, full-motion video, and interactive desktop sharing?
A) Community building
B) Collaborative communication
C) History tracking
D) Tagging
A) Community building
B) Collaborative communication
C) History tracking
D) Tagging

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
10
Instant messaging should be short and to the point.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
11
Google Docs is an example of what type of program?
A) Anti-virus
B) History tracking
C) Online document sharing
D) Collaborative communication
A) Anti-virus
B) History tracking
C) Online document sharing
D) Collaborative communication

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
12
Temporary Internet Files (TIF) increase the amount of time it takes for a browser to load and display a Web site.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
13
Windows Mail provides two formatting options: HTML and RDF Summary .

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
14
A(n) time bomb is a type of virus that is triggered by the appearance or disappearance of specified data.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
15
It is possible to add a hyperlink to a message rather than attaching a file.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
16
Users may need a(n) password in order to log on to a computer system or to specific parts of it.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
17
In most instances, electronic communications use voice rather than text or graphics.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
18
Which type of correspondence is possible with electronic communication?
A) One to one
B) One to many
C) Many to many
D) Any of the above
A) One to one
B) One to many
C) Many to many
D) Any of the above

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
19
Software routing is one process that can be used to cut down or eliminate most junk mail.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
20
Which of the following was originally developed to facilitate the syndication of news articles?
A) Phishing
B) Teleconferencing
C) RDF Summary
D) Google Docs
A) Phishing
B) Teleconferencing
C) RDF Summary
D) Google Docs

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
21
The Vmyths Web site can help people identify ____.
A) pyramid schemes
B) hoaxes
C) Trojan horses
D) worms
A) pyramid schemes
B) hoaxes
C) Trojan horses
D) worms

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
22
A "bounced" e-mail refers to a message that ____.
A) has an attachment
B) has a virus
C) gets returned because of delivery failure
D) is sent in rich text format and gets garbled
A) has an attachment
B) has a virus
C) gets returned because of delivery failure
D) is sent in rich text format and gets garbled

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
23
If a customer needs immediate assistance or has a complaint, then the reply should be within ____.
A) 5 minutes
B) 30 minutes to 3 hours
C) 5 to 10 hours
D) 24 hours
A) 5 minutes
B) 30 minutes to 3 hours
C) 5 to 10 hours
D) 24 hours

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
24
Mistyping an e-mail address can cause the message to ____.
A) fail to be delivered
B) spread a virus
C) get caught in the spam filter
D) get sorted into the Junk folder
A) fail to be delivered
B) spread a virus
C) get caught in the spam filter
D) get sorted into the Junk folder

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
25
What is a paper trail?
A) A written record created in the course of activities
B) A message that gets garbled during transmission
C) An attachment that gets blocked by your e-mail program
D) Notification that an e-mail message was not delivered properly
A) A written record created in the course of activities
B) A message that gets garbled during transmission
C) An attachment that gets blocked by your e-mail program
D) Notification that an e-mail message was not delivered properly

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
26
____________________ uses a telecommunications system to serve groups, permitting the live exchange and sharing of information between two or more people.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
27
Case 26-1 Gilbert uses Windows Mail as his e-mail program. He has been getting a lot of junk e-mail in his inbox and wants to take steps to help prevent the number of unsolicited messages that he receives. The type of junk e-mail that Gilbert is receiving is called ____.
A) fraud
B) hoax
C) worm
D) spam
A) fraud
B) hoax
C) worm
D) spam

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
28
Which is an integrated security system that prevents unauthorized electronic access to a network computer system while permitting outward communication?
A) Firewall
B) Electronic identification cards
C) Antivirus software
D) Biometric security measures
A) Firewall
B) Electronic identification cards
C) Antivirus software
D) Biometric security measures

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
29
Encryption technologies can help keep ____ information secure.
A) anti-virus
B) instant messaging
C) teleconferencing
D) credit card
A) anti-virus
B) instant messaging
C) teleconferencing
D) credit card

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
30
GlobalSign and VeriSign are commercial digital ID groups that can help you ____.
A) encrypt an e-mail message
B) control unsolicited e-mail
C) prevent viruses
D) add hyperlinks to an e-mail message
A) encrypt an e-mail message
B) control unsolicited e-mail
C) prevent viruses
D) add hyperlinks to an e-mail message

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
31
If you are having trouble configuring your e-mail account with Windows Mail, you might consider using ____.
A) the Network Repair Tool
B) Windows Live Mail
C) rich text format (RTF)
D) HTML formatting
A) the Network Repair Tool
B) Windows Live Mail
C) rich text format (RTF)
D) HTML formatting

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
32
What is the estimated yearly cost of spam for U.S. businesses?
A) $20 thousand
B) $20 million
C) $20 billion
D) $20 trillion
A) $20 thousand
B) $20 million
C) $20 billion
D) $20 trillion

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the following is not a sort option for displaying the History list in Internet Explorer?
A) By Total Time
B) By Date
C) By Site
D) By Most Visited
A) By Total Time
B) By Date
C) By Site
D) By Most Visited

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
34
Radio listeners believing that invaders from Mars were attacking the world is an example of a(n) ____.
A) hoax
B) virus
C) urban legend
D) pyramid scheme
A) hoax
B) virus
C) urban legend
D) pyramid scheme

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
35
If the reply message is not applicable to other recipients, which is the best response option?
A) Reply
B) Reply All
C) Cc
D) Bcc
A) Reply
B) Reply All
C) Cc
D) Bcc

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
36
Case 26-2 Wanda has just been hired to work for a Web design company. As part of her new employee training, her supervisor reviews the company's list of guidelines for the use of electronic communications. Wanda's supervisor explains that she is expected to follow the rules of ____ when communicating through electronic media.
A) netiquette
B) phishing
C) tagging
D) filtering
A) netiquette
B) phishing
C) tagging
D) filtering

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
37
FIGURE 26-1  Figure 26-1 above shows an example of ____.
Figure 26-1 above shows an example of ____.
A) encryption technology
B) a firewall
C) biometric security measures
D) virus protection
 Figure 26-1 above shows an example of ____.
Figure 26-1 above shows an example of ____.A) encryption technology
B) a firewall
C) biometric security measures
D) virus protection

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
38
Case 26-1 Gilbert uses Windows Mail as his e-mail program. He has been getting a lot of junk e-mail in his inbox and wants to take steps to help prevent the number of unsolicited messages that he receives. To display the Junk E-mail Options dialog box, Gilbert would click ____ on the menu bar and then click Junk E-mail Options.
A) File
B) Tools
C) Internet
D) Filter
A) File
B) Tools
C) Internet
D) Filter

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
39
Case 26-2 Wanda has just been hired to work for a Web design company. As part of her new employee training, her supervisor reviews the company's list of guidelines for the use of electronic communications. Wanda learns that when the correspondence requires a paper trail, the best communication method is ____.
A) instant messaging
B) teleconferencing
C) cell phone
D) e-mail
A) instant messaging
B) teleconferencing
C) cell phone
D) e-mail

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
40
FIGURE 26-2 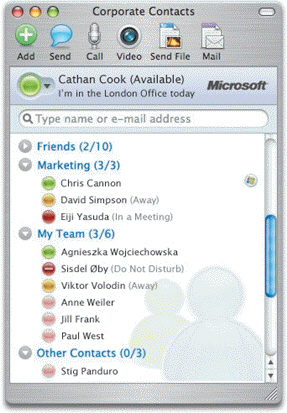 The interface shown in Figure 26-2 above would be used for ____.
The interface shown in Figure 26-2 above would be used for ____.
A) teleconferencing
B) instant messaging
C) sharing the content of blogs
D) tagging
 The interface shown in Figure 26-2 above would be used for ____.
The interface shown in Figure 26-2 above would be used for ____.A) teleconferencing
B) instant messaging
C) sharing the content of blogs
D) tagging

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
41
Match between columns

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
42
What is a virus? How can a virus spread? What are some things you can do to help prevent a virus from infecting your computer?

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
43
A(n) ____________________ is a virus that does not cause its damage until a certain date or until the system has been booted a certain number of times.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
44
A(n) ____________________ is a virus that makes many copies of itself, resulting in the consumption of system resources that slows down or actually halts the task.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
45
____________________ is used in blogs and other informational sites to simplify the search process.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
46
E-mail ____________________ is a computer crime that involves the manipulation of a computer or computer data in order to dishonestly obtain money, property, information, or other things of value, or to cause loss.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck


