Deck 4: LPIC-1 Exam 101
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/105
Play
Full screen (f)
Deck 4: LPIC-1 Exam 101
1
When is the content of the kernel ring buffer reset?
A) When the ring buffer is explicitly reset using the command dmesg --clear When the ring buffer is explicitly reset using the command dmesg --clear
B) When the ring buffer is read using dmesg without any additional parameters When the ring buffer is read using dmesg without any additional parameters
C) When a configurable amount of time, 15 minutes by default, has passed
D) When the kernel loads a previously unloaded kernel module
E) When the system is shut down or rebooted
A) When the ring buffer is explicitly reset using the command dmesg --clear When the ring buffer is explicitly reset using the command dmesg --clear
B) When the ring buffer is read using dmesg without any additional parameters When the ring buffer is read using dmesg without any additional parameters
C) When a configurable amount of time, 15 minutes by default, has passed
D) When the kernel loads a previously unloaded kernel module
E) When the system is shut down or rebooted
When the ring buffer is explicitly reset using the command dmesg --clear When the ring buffer is explicitly reset using the command dmesg --clear
When the system is shut down or rebooted
When the system is shut down or rebooted
2
Which of the following commands installs GRUB 2 into the master boot record on the third hard disk?
A) grub2 install /dev/sdc
B) grub-mkrescue /dev/sdc
C) grub-mbrinstall /dev/sdc
D) grub-setup /dev/sdc
E) grub-install /dev/sdc
A) grub2 install /dev/sdc
B) grub-mkrescue /dev/sdc
C) grub-mbrinstall /dev/sdc
D) grub-setup /dev/sdc
E) grub-install /dev/sdc
grub-install /dev/sdc
3
Which of the following commands changes the number of days before the ext3 filesystem on /dev/sda1 has to run through a full filesystem check while booting?
A) tune2fs -d 200 /dev/sda1
B) tune2fs -i 200 /dev/sda1
C) tune2fs -c 200 /dev/sda1
D) tune2fs -n 200 /dev/sda1
E) tune2fs --days 200 /dev/sda1
A) tune2fs -d 200 /dev/sda1
B) tune2fs -i 200 /dev/sda1
C) tune2fs -c 200 /dev/sda1
D) tune2fs -n 200 /dev/sda1
E) tune2fs --days 200 /dev/sda1
tune2fs -i 200 /dev/sda1
4
Which daemon handles power management events on a Linux system?
A) acpid
B) batteryd
C) pwrmgntd
D) psd
E) inetd
A) acpid
B) batteryd
C) pwrmgntd
D) psd
E) inetd

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
5
Consider the following directory: drwxrwxr-x 2 root sales 4096 Jan 1 15:21 sales Which command ensures new files created within the directory sales are owned by the group ?
A) chmod g+s sales chmod g+s
B) setpol -R newgroup=sales sales
C) chgrp -p sales sales
D) chown --persistent *.sales sales
E) chmod 2775 sales
A) chmod g+s sales chmod g+s
B) setpol -R newgroup=sales sales
C) chgrp -p sales sales
D) chown --persistent *.sales sales
E) chmod 2775 sales

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
6
What does the command mount --bind do?
A) It makes the contents of one directory available in another directory
B) It mounts all available filesystems to the current directory
C) It mounts all user mountable filesystems to the user's home directory
D) It mounts all file systems listed in /etc/fstab which have the option userbind set It mounts all file systems listed in /etc/fstab which have the option userbind set
E) It permanently mounts a regular file to a directory
A) It makes the contents of one directory available in another directory
B) It mounts all available filesystems to the current directory
C) It mounts all user mountable filesystems to the user's home directory
D) It mounts all file systems listed in /etc/fstab which have the option userbind set It mounts all file systems listed in /etc/fstab which have the option userbind set
E) It permanently mounts a regular file to a directory

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
7
Which umask value ensures that new directories can be read, written and listed by their owning user, read and listed by their owning group and are not accessible at all for everyone else?
A) 0750
B) 0027
C) 0036
D) 7640
E) 0029
A) 0750
B) 0027
C) 0036
D) 7640
E) 0029

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
8
What is true regarding UEFI firmware?
A) It can read and interpret partition tables
B) It can use and read certain file systems
C) It stores its entire configuration on the /boot/ partition
D) It is stored in a special area within the GPT metadata
E) It is loaded from a fixed boot disk position
A) It can read and interpret partition tables
B) It can use and read certain file systems
C) It stores its entire configuration on the /boot/ partition
D) It is stored in a special area within the GPT metadata
E) It is loaded from a fixed boot disk position

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
9
In order to display all currently mounted filesystems, which of the following commands could be used?
A) cat /proc/self/mounts
B) free
C) lsmounts
D) mount
E) cat /proc/filesystems
A) cat /proc/self/mounts
B) free
C) lsmounts
D) mount
E) cat /proc/filesystems

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
10
Which command uninstalls a package but keeps its configuration files in case the package is re-installed?
A) dpkg -s pkgname
B) dpkg -L pkgname
C) dpkg -P pkgname
D) dpkg -v pkgname
E) dpkg -r pkgname
A) dpkg -s pkgname
B) dpkg -L pkgname
C) dpkg -P pkgname
D) dpkg -v pkgname
E) dpkg -r pkgname

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
11
What is the maximum niceness value that a regular user can assign to a process with the nice command when executing a new process?
A) 9
B) 15
C) 19
D) 49
E) 99
A) 9
B) 15
C) 19
D) 49
E) 99

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following files exist in a standard GRUB 2 installation?
A) /boot/grub/stages/stage0
B) /boot/grub/i386-pc/lvm.mod
C) /boot/grub/fstab
D) /boot/grub/grub.cfg
E) /boot/grub/linux/vmlinuz
A) /boot/grub/stages/stage0
B) /boot/grub/i386-pc/lvm.mod
C) /boot/grub/fstab
D) /boot/grub/grub.cfg
E) /boot/grub/linux/vmlinuz

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
13
When considering the use of hard links, what are valid reasons not to use hard links?
A) Hard links are not available on all Linux systems because traditional filesystems, such as ext4, do not support them
B) Each hard link has individual ownership, permissions and ACLs which can lead to unintended disclosure of file content
C) Hard links are specific to one filesystem and cannot point to files on another filesystem
D) If users other than root should be able to create hard links, suln has to be installed and configured If users other than root should be able to create hard links, suln has to be installed and configured
E) When a hard linked file is changed, a copy of the file is created and consumes additional space
A) Hard links are not available on all Linux systems because traditional filesystems, such as ext4, do not support them
B) Each hard link has individual ownership, permissions and ACLs which can lead to unintended disclosure of file content
C) Hard links are specific to one filesystem and cannot point to files on another filesystem
D) If users other than root should be able to create hard links, suln has to be installed and configured If users other than root should be able to create hard links, suln has to be installed and configured
E) When a hard linked file is changed, a copy of the file is created and consumes additional space

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
14
A Debian package creates several files during its installation. Which of the following commands searches for packages owning the file /etc/debian_version ?
A) apt-get search /etc/debian_version
B) apt -r /etc/debian_version
C) find /etc/debian_version -dpkg
D) dpkg -S /etc/debian_version
E) apt-file /etc/debian_version
A) apt-get search /etc/debian_version
B) apt -r /etc/debian_version
C) find /etc/debian_version -dpkg
D) dpkg -S /etc/debian_version
E) apt-file /etc/debian_version

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
15
Which is the default percentage of reserved space for the root user on new ext4 filesystems?
A) 10%
B) 3%
C) 15%
D) 0%
E) 5%
A) 10%
B) 3%
C) 15%
D) 0%
E) 5%

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following statements are true about the boot sequence of a PC using a BIOS?
A) Some parts of the boot process can be configured from the BIOS
B) Linux does not require the assistance of the BIOS to boot a computer
C) The BIOS boot process starts only if secondary storage, such as the hard disk, is functional
D) The BIOS initiates the boot process after turning the computer on
E) The BIOS is started by loading hardware drivers from secondary storage, such as the hard disk
A) Some parts of the boot process can be configured from the BIOS
B) Linux does not require the assistance of the BIOS to boot a computer
C) The BIOS boot process starts only if secondary storage, such as the hard disk, is functional
D) The BIOS initiates the boot process after turning the computer on
E) The BIOS is started by loading hardware drivers from secondary storage, such as the hard disk

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
17
Which of the following partition types is used for Linux swap spaces when partitioning hard disk drives?
A) 7
B) 82
C) 83
D) 8e
E) fd
A) 7
B) 82
C) 83
D) 8e
E) fd

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
18
Which chown command changes the ownership to dave and the group to staff on a file named data.txt ?
A) chown dave/staff data.txt
B) chown -u dave -g staff data.txt
C) chown --user dave --group staff data.txt
D) chown dave+staff data.txt
E) chown dave:staff data.txt
A) chown dave/staff data.txt
B) chown -u dave -g staff data.txt
C) chown --user dave --group staff data.txt
D) chown dave+staff data.txt
E) chown dave:staff data.txt

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
19
Which of the following apt-get subcommands installs the newest versions of all currently installed packages?
A) auto-update
B) dist-upgrade
C) full-upgrade
D) install
E) update
A) auto-update
B) dist-upgrade
C) full-upgrade
D) install
E) update

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
20
What is contained on the EFI System Partition?
A) The Linux root file system
B) The first stage boot loader
C) The default swap space file
D) The Linux default shell binaries
E) The user home directories
A) The Linux root file system
B) The first stage boot loader
C) The default swap space file
D) The Linux default shell binaries
E) The user home directories

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
21
When removing a package on a system using dpkg package management, which dpkg option ensures configuration files are removed as well?
A) --clean
B) --purge
C) --vacuum
D) --remove
E) --declare
A) --clean
B) --purge
C) --vacuum
D) --remove
E) --declare

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
22
Which of the following commands displays the contents of a gzip compressed tar archive?
A) gzip archive.tgz | tar xvf -
B) tar -fzt archive.tgz
C) gzip -d archive.tgz | tar tvf -
D) tar cf archive.tgz
E) tar ztf archive.tgz
A) gzip archive.tgz | tar xvf -
B) tar -fzt archive.tgz
C) gzip -d archive.tgz | tar tvf -
D) tar cf archive.tgz
E) tar ztf archive.tgz

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following statements are correct when comparing Linux containers with traditional virtual machines (e.g. LXC vs. KVM)?
A) Containers are a lightweight virtualization method where the kernel controls process isolation and resource management.
B) Fully virtualized machines can run any operating system for a specific hardware architecture within the virtual machine.
C) Containers are completely decoupled from the host system's physical hardware and can only use emulated virtual hardware devices.
D) The guest environment for fully virtualized machines is created by a hypervisor which provides virtual and emulated hardware devices.
E) Containers on the same host can use different operating systems, as the container hypervisor creates separate kernel execution.
A) Containers are a lightweight virtualization method where the kernel controls process isolation and resource management.
B) Fully virtualized machines can run any operating system for a specific hardware architecture within the virtual machine.
C) Containers are completely decoupled from the host system's physical hardware and can only use emulated virtual hardware devices.
D) The guest environment for fully virtualized machines is created by a hypervisor which provides virtual and emulated hardware devices.
E) Containers on the same host can use different operating systems, as the container hypervisor creates separate kernel execution.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following commands changes all CR-LF line breaks in the text file userlist.txt to Linux standard LF line breaks and stores the result in newlist.txt ?
A) tr -d '\r' < userlist.txt > newlist.txt
B) tr -c '\n\r' '' userlist.txt
C) tr '\r\n' '' newlist.txt
D) tr '\r' '\n' userlist.txt newlist.txt
E) tr -s '/^M/^J/' userlist.txt newlist.txt
A) tr -d '\r' < userlist.txt > newlist.txt
B) tr -c '\n\r' ''
C) tr '\r\n' ''
D) tr '\r' '\n' userlist.txt newlist.txt
E) tr -s '/^M/^J/' userlist.txt newlist.txt

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
25
Which command must be entered before exiting vi to save the current file as filea.txt ?
A) %s filea.txt
B) %w filea.txt
C) :save filea.txt
D) :w filea.txt
E) :s filea.txt
A) %s filea.txt
B) %w filea.txt
C) :save filea.txt
D) :w filea.txt
E) :s filea.txt

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following commands displays the path to the executable file that would be executed when the command foo is invoked?
A) lsattr foo
B) apropos foo
C) locate foo
D) whatis foo
E) which foo
A) lsattr foo
B) apropos foo
C) locate foo
D) whatis foo
E) which foo

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
27
Which of the following vi commands deletes two lines, the current and the following line?
A) d2
B) 2d
C) 2dd
D) dd2
E) de12
A) d2
B) 2d
C) 2dd
D) dd2
E) de12

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
28
The installation of a local Debian package failed due to unsatisfied dependencies. Which of the following commands installs missing dependencies and completes the interrupted package installation?
A) dpkg --fix --all
B) apt-get autoinstall
C) dpkg-reconfigure --all
D) apt-get all
E) apt-get install -f
A) dpkg --fix --all
B) apt-get autoinstall
C) dpkg-reconfigure --all
D) apt-get all
E) apt-get install -f

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following commands list all files and directories within the /tmp/ directory and its subdirectories which are owned by the user root?
A) find /tmp -user root -print
B) find -path /tmp -uid root
C) find /tmp -uid root -print
D) find /tmp -user root
E) find -path /tmp -user root -print
A) find /tmp -user root -print
B) find -path /tmp -uid root
C) find /tmp -uid root -print
D) find /tmp -user root
E) find -path /tmp -user root -print

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
30
Which of the following commands installs the GRUB boot files into the currently active file systems and the boot loader into the first partition of the first disk?
A) grub-install /dev/sda
B) grub-install /dev/sda1
C) grub-install current /dev/sda0
D) grub-install /dev/sda0
E) grub-install current /dev/sda1
A) grub-install /dev/sda
B) grub-install /dev/sda1
C) grub-install current /dev/sda0
D) grub-install /dev/sda0
E) grub-install current /dev/sda1

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following commands prints a list of usernames (first column) and their primary group (fourth column) from the /etc/passwd file?
A) fmt -f 1,4 /etc/passwd
B) cut -d : -f 1,4 /etc/passwd
C) sort -t : -k 1,4 /etc/passwd
D) paste -f 1,4 /etc/passwd
E) split -c 1,4 /etc/passwd
A) fmt -f 1,4 /etc/passwd
B) cut -d : -f 1,4 /etc/passwd
C) sort -t : -k 1,4 /etc/passwd
D) paste -f 1,4 /etc/passwd
E) split -c 1,4 /etc/passwd

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
32
Given the following input stream: txt1.txt atxt.txt txtB.txt Which of the following regular expressions turns this input stream into the following output stream? txt1.bak.txt atxt.bak.txt txtB.bak.txt
A) s/^.txt/.bak/
B) s/txt/bak.txt/
C) s/txt$/bak.txt/
D) s/^txt$/.bak^/
E) s/[.txt]/.bak$1/
A) s/^.txt/.bak/
B) s/txt/bak.txt/
C) s/txt$/bak.txt/
D) s/^txt$/.bak^/
E) s/[.txt]/.bak$1/

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
33
The command dbmaint & was used to run dbmaint in the background. However, is terminated after logging out of the system. Which alternative invocation lets continue to run even when the user running the program logs out?
A) job -b dmaint
B) dbmaint &>/dev/pts/null
C) nohup dbmaint &
D) bg dbmaint
E) wait dbmaint
A) job -b dmaint
B) dbmaint &>/dev/pts/null
C) nohup dbmaint &
D) bg dbmaint
E) wait dbmaint

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
34
Immediately after deleting 3 lines of text in vi and moving the cursor to a different line, which single character command will insert the deleted content below the current line?
A) i (lowercase)
B) p (lowercase)
C) P (uppercase)
D) U (uppercase)
E) u (lowercase)
A) i (lowercase)
B) p (lowercase)
C) P (uppercase)
D) U (uppercase)
E) u (lowercase)

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
35
Which of the following commands can be used to determine how long the system has been running?
A) uptime
B) up
C) time --up
D) uname -u
E) top
A) uptime
B) up
C) time --up
D) uname -u
E) top

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
36
Which of the following files, located in a user's home directory, contains the Bash history?
A) .b ashrc_history .b ashrc_history
B) .bash _histfile .bash _histfile
C) .history
D) .bash_history
E) .history_bash
A) .b ashrc_history .b ashrc_history
B) .bash _histfile .bash _histfile
C) .history
D) .bash_history
E) .history_bash

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
37
When redirecting the output of find to the xargs command, what option to is useful if the filenames contain spaces?
A) -rep-space
B) -printnul
C) -nospace
D) -ignore-space
E) -print0
A) -rep-space
B) -printnul
C) -nospace
D) -ignore-space
E) -print0

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
38
Which wildcards will match the following filenames? ttyS0 ttyS1 ttyS2
A) ttyS[1-5]
B) tty?[0-5]
C) tty*2
D) tty[A-Z][012]
E) tty[Ss][02]
A) ttyS[1-5]
B) tty?[0-5]
C) tty*2
D) tty[A-Z][012]
E) tty[Ss][02]

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following files are found in the /boot/ file system?
A) Linux kernel images
B) Bash shell binaries
C) systemd target and service units
D) Initial ramdisk images
E) fsck binaries
A) Linux kernel images
B) Bash shell binaries
C) systemd target and service units
D) Initial ramdisk images
E) fsck binaries

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
40
Which of the following are valid stream redirection operators within Bash?
A) <
B) #>
C) %>
D) >>>
E) 2>&1
A) <
B) #>
C) %>
D) >>>
E) 2>&1

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
41
Where is the bootloader stored on the hard disk of a UEFI system?
A) In the EFI Boot Record (EBR).
B) In the Master Boot Record (MBR).
C) On the EFI System Partition (ESP).
D) On the partition labeled boot . On the partition labeled boot .
E) On the partition number 127 . On the partition number 127
A) In the EFI Boot Record (EBR).
B) In the Master Boot Record (MBR).
C) On the EFI System Partition (ESP).
D) On the partition labeled boot . On the partition labeled boot .
E) On the partition number 127 . On the partition number 127

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
42
Which of the following commands sets the SetUID permission on the executable /bin/foo ?
A) chmod 4755 /bin/foo
B) chmod 1755 /bin/foo
C) chmod u-s /bin/foo
D) chmod 755+s /bin/foo
E) chmod 2755 /bin/foo
A) chmod 4755 /bin/foo
B) chmod 1755 /bin/foo
C) chmod u-s /bin/foo
D) chmod 755+s /bin/foo
E) chmod 2755 /bin/foo

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
43
Which of the following commands lists all currently installed packages when using RPM package management?
A) yum --query --all
B) yum --list --installed
C) rpm --query --list
D) rpm --list --installed
E) rpm --query --all
A) yum --query --all
B) yum --list --installed
C) rpm --query --list
D) rpm --list --installed
E) rpm --query --all

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
44
What are the main differences between GPT and MBR partition tables regarding maximum number and size of partitions?
A) MBR can handle partition sizes up to 4 TB, whereas GPT supports partition sizes up to 128 ZB.
B) By default, GPT can manage up to 128 partitions while MBR only supports four primary partitions.
C) By default, GPT can manage up to 64 partitions while MBR only supports 16 primary partitions.
D) MBR can handle partition sizes up to 2.2 TB, whereas GPT supports sizes up to 9.4 ZB.
E) Both GPT and MBR support up to four primary partitions, each with up to 4096 TB.
A) MBR can handle partition sizes up to 4 TB, whereas GPT supports partition sizes up to 128 ZB.
B) By default, GPT can manage up to 128 partitions while MBR only supports four primary partitions.
C) By default, GPT can manage up to 64 partitions while MBR only supports 16 primary partitions.
D) MBR can handle partition sizes up to 2.2 TB, whereas GPT supports sizes up to 9.4 ZB.
E) Both GPT and MBR support up to four primary partitions, each with up to 4096 TB.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
45
Running chmod 640 filea.txt as a regular user doesn't update filea.txt' s permission. What might be a reason why chmod cannot modify the permissions?
A) filea.txt is owned by another user and a regular user cannot change the permissions of another user's file. filea.txt is owned by another user and a regular user cannot change the permissions of another user's file.
B) filea.txt is a symbolic link whose permissions are a fixed value which cannot be charged. is a symbolic link whose permissions are a fixed value which cannot be charged.
C) filea.txt has the sticky bit set and a regular user cannot remove this permission. has the sticky bit set and a regular user cannot remove this permission.
D) filea.txt is a hard link whose permissions are inherited from the target and cannot be set directly. is a hard link whose permissions are inherited from the target and cannot be set directly.
E) filea.txt has the SetUID bit set which imposes the restriction that only the root user can make changes to the file. has the SetUID bit set which imposes the restriction that only the root user can make changes to the file.
A) filea.txt is owned by another user and a regular user cannot change the permissions of another user's file. filea.txt is owned by another user and a regular user cannot change the permissions of another user's file.
B) filea.txt is a symbolic link whose permissions are a fixed value which cannot be charged. is a symbolic link whose permissions are a fixed value which cannot be charged.
C) filea.txt has the sticky bit set and a regular user cannot remove this permission. has the sticky bit set and a regular user cannot remove this permission.
D) filea.txt is a hard link whose permissions are inherited from the target and cannot be set directly. is a hard link whose permissions are inherited from the target and cannot be set directly.
E) filea.txt has the SetUID bit set which imposes the restriction that only the root user can make changes to the file. has the SetUID bit set which imposes the restriction that only the root user can make changes to the file.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following Linux filesystems preallocate a fixed number of inodes when creating a new filesystem instead of generating them as needed?
A) JFS
B) ext3
C) XFS
D) ext2
E) procfs
A) JFS
B) ext3
C) XFS
D) ext2
E) procfs

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following commands show how the shell handles a specific command?
A) where
B) type
C) stat
D) case
E) fileinfo
A) where
B) type
C) stat
D) case
E) fileinfo

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
48
What is the effect of the -v option for the grep command?
A) It enables color to highlight matching parts.
B) It shows the command's version information.
C) It only outputs non-matching lines.
D) It changes the output order showing the last matching line first.
E) It outputs all lines and prefixes matching lines with a+.
A) It enables color to highlight matching parts.
B) It shows the command's version information.
C) It only outputs non-matching lines.
D) It changes the output order showing the last matching line first.
E) It outputs all lines and prefixes matching lines with a+.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
49
Which of the following commands print the current working directory when using a Bash shell?
A) echo "${PWD}"
B) echo "${WD}"
C) printwd
D) pwd
E) echo "${pwd}"
A) echo "${PWD}"
B) echo "${WD}"
C) printwd
D) pwd
E) echo "${pwd}"

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
50
Which of the following signals is sent to a process when the key combination Ctrl+Z is pressed on the keyboard?
A) SIGTERM
B) SIGCONT
C) SIGSTOP
D) SIGKILL
E) SIGINT
A) SIGTERM
B) SIGCONT
C) SIGSTOP
D) SIGKILL
E) SIGINT

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
51
In the vi editor, how can commands such as moving the cursor or copying lines into the buffer be issued multiple times or applied to multiple rows?
A) By using the command :repeat followed by the number and the command By using the command :repeat followed by the number and the command
B) By specifying the number right in front of a command such as 41 or 2yj. By specifying the number right in front of a command such as 41 or 2yj.
C) By selecting all affected lines using the shit and cursor keys before applying the command.
D) By issuing a command such as :set repetition=4 with repeats every subsequent command 4 times. By issuing a command such as :set repetition=4 with repeats every subsequent command 4 times.
E) By specifying the number after a command such as 14 or yj2 followed by escape. By specifying the number after a command such as 14 yj2 followed by escape.
A) By using the command :repeat followed by the number and the command By using the command :repeat followed by the number and the command
B) By specifying the number right in front of a command such as 41 or 2yj. By specifying the number right in front of a command such as 41 or 2yj.
C) By selecting all affected lines using the shit and cursor keys before applying the command.
D) By issuing a command such as :set repetition=4 with repeats every subsequent command 4 times. By issuing a command such as :set repetition=4 with repeats every subsequent command 4 times.
E) By specifying the number after a command such as 14 or yj2 followed by escape. By specifying the number after a command such as 14 yj2 followed by escape.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following commands loads a kernel module along with any required dependency modules?
A) depmod
B) modprobe
C) module_install
D) insmod
E) loadmod
A) depmod
B) modprobe
C) module_install
D) insmod
E) loadmod

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
53
What is the default nice level when a process is started using the nice command?
A) -10
B) 0
C) 10
D) 15
E) 20
A) -10
B) 0
C) 10
D) 15
E) 20

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
54
What is the purpose of the ldd command?
A) It lists which shared libraries a binary needs to run.
B) It installs and updates installed shared libraries.
C) It turns a dynamically linked binary into a static binary.
D) It defines which version of a library should be used by default.
E) It runs a binary with an alternate library search path.
A) It lists which shared libraries a binary needs to run.
B) It installs and updates installed shared libraries.
C) It turns a dynamically linked binary into a static binary.
D) It defines which version of a library should be used by default.
E) It runs a binary with an alternate library search path.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
55
When booting from the hard disk, a computer successfully loads the Linux kernel and initramfs but hangs during the subsequent startup tasks. The system is booted using a Linux based rescue CD to investigate the problem. Which of the following methods helps to identify the root cause of the problem?
A) Using the dmesg command from the rescue CD's shell to view the original system's boot logs. Using the dmesg command from the rescue CD's shell to view the original system's boot logs.
B) Investigating the file /proc/kmsg on the computer's hard disk for possible errors. Investigating the file /proc/kmsg on the computer's hard disk for possible errors.
C) Investigating the file /var/log on the computer's hard disk for possible errors. /var/log
D) Using chroot to switch to the file system on the hard disk and use dmesg to view the logs. Using chroot to switch to the file system on the hard disk and use to view the logs.
E) Rebooting again from the hard drive since the system successfully booted from the rescue CD.
A) Using the dmesg command from the rescue CD's shell to view the original system's boot logs. Using the dmesg command from the rescue CD's shell to view the original system's boot logs.
B) Investigating the file /proc/kmsg on the computer's hard disk for possible errors. Investigating the file /proc/kmsg on the computer's hard disk for possible errors.
C) Investigating the file /var/log on the computer's hard disk for possible errors. /var/log
D) Using chroot to switch to the file system on the hard disk and use dmesg to view the logs. Using chroot to switch to the file system on the hard disk and use to view the logs.
E) Rebooting again from the hard drive since the system successfully booted from the rescue CD.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
56
What is the correct way to set the default systemd boot target to multi-user ?
A) systemctl isolate multi-user.target
B) systemctl set-runlevel multi-user.target
C) systemctl set-boot multi-user.target
D) systemctl set-default multi-user.target
E) systemctl boot -p multi-user.target
A) systemctl isolate multi-user.target
B) systemctl set-runlevel multi-user.target
C) systemctl set-boot multi-user.target
D) systemctl set-default multi-user.target
E) systemctl boot -p multi-user.target

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
57
Which of the following commands is used to change options and positional parameters within a running Bash shell?
A) history
B) setsh
C) bashconf
D) set
E) envsetup
A) history
B) setsh
C) bashconf
D) set
E) envsetup

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
58
When in Normal mode in vi , which character can be used to begin a reverse search of the text?
A) r
B) /
C) F
D) ?
E) s
A) r
B) /
C) F
D) ?
E) s

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following commands display the IDs of all processes owned by root?
A) pgrep -c root
B) pgrep -u root
C) pgrep -f root
D) pgrep -U 0
E) pgrep -c 0
A) pgrep -c root
B) pgrep -u root
C) pgrep -f root
D) pgrep -U 0
E) pgrep -c 0

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
60
In Bash, inserting 1>&2 after a command redirects…
A) …standard error to standard input.
B) …standard output to standard error.
C) …standard input to standard error.
D) …standard error to standard output.
E) …standard output to standard input.
A) …standard error to standard input.
B) …standard output to standard error.
C) …standard input to standard error.
D) …standard error to standard output.
E) …standard output to standard input.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
61
What is the process ID number of the init process on a System V init based system?
A) -1
B) 0
C) 1
D) It is different with each reboot
E) It is set to the current run level
A) -1
B) 0
C) 1
D) It is different with each reboot
E) It is set to the current run level

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
62
What is the first program the Linux kernel starts at boot time when using System V init?
A) /lib/init.so
B) /proc/sys/kernel/init
C) /etc/rc.d/rcinit
D) /sbin/init
E) /boot/init
A) /lib/init.so
B) /proc/sys/kernel/init
C) /etc/rc.d/rcinit
D) /sbin/init
E) /boot/init

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
63
Consider the following output from the command ls -i: 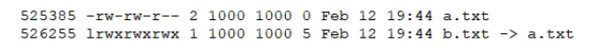 How would a new file named c.txt be created with the same inode number as a.txt (Inode 525385)?
How would a new file named c.txt be created with the same inode number as a.txt (Inode 525385)?
A) ln -h a.txt c.txt
B) ln c.txt a.txt
C) ln a.txt c.txt
D) ln -f c.txt a.txt
E) ln -i 525385 c.txt
 How would a new file named c.txt be created with the same inode number as a.txt (Inode 525385)?
How would a new file named c.txt be created with the same inode number as a.txt (Inode 525385)?A) ln -h a.txt c.txt
B) ln c.txt a.txt
C) ln a.txt c.txt
D) ln -f c.txt a.txt
E) ln -i 525385 c.txt

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
64
Which file defines the network locations from where the Debian package manager downloads software packages?
A) /etc/dpkg/dpkg.cfg
B) /etc/apt/apt.conf.d
C) /etc/apt/apt.conf
D) /etc/dpkg/dselect.cfg
E) /etc/apt/sources.list
A) /etc/dpkg/dpkg.cfg
B) /etc/apt/apt.conf.d
C) /etc/apt/apt.conf
D) /etc/dpkg/dselect.cfg
E) /etc/apt/sources.list

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
65
Which type of file system is created by mkfs when it is executed with the block device name only and without any additional parameters?
A) XFS
B) VFAT
C) ext2
D) ext3
E) ext4
A) XFS
B) VFAT
C) ext2
D) ext3
E) ext4

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
66
Which of the following commands installs all packages with a name ending with the string foo ?
A) zypper get "*foo"
B) zypper update "foo?"
C) zypper force "foo*"
D) zypper install "*foo"
E) zypper add ".*foo"
A) zypper get "*foo"
B) zypper update "foo?"
C) zypper force "foo*"
D) zypper install "*foo"
E) zypper add ".*foo"

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
67
A backup software heavily uses hard links between files which have not been changed in between two backup runs. Which benefits are realized due to these hard links?
A) The old backups can be moved to slow backup media, such as tapes, while still serving as hard link target in new backups.
B) The backup runs faster because hard links are asynchronous operations, postponing the copy operation to a later point in time.
C) The backup is guaranteed to be uncharged because a hard linked file cannot be modified after its creation.
D) The backup consumes less space because the hard links point to the same data on disk instead of storing redundant copies.
E) The backup runs faster because, instead of copying the data of each file, hard links only change file system meta data.
A) The old backups can be moved to slow backup media, such as tapes, while still serving as hard link target in new backups.
B) The backup runs faster because hard links are asynchronous operations, postponing the copy operation to a later point in time.
C) The backup is guaranteed to be uncharged because a hard linked file cannot be modified after its creation.
D) The backup consumes less space because the hard links point to the same data on disk instead of storing redundant copies.
E) The backup runs faster because, instead of copying the data of each file, hard links only change file system meta data.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
68
A yum repository can declare sets of related packages. Which yum command installs all packages belonging to the group admintools ?
A) yum pkgsel --install admintools
B) yum install admintools/*
C) yum groupinstall admintools
D) yum taskinstall admintools
E) yum collection install admintools
A) yum pkgsel --install admintools
B) yum install admintools/*
C) yum groupinstall admintools
D) yum taskinstall admintools
E) yum collection install admintools

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
69
Which of the following commands redirects the output of ls to standard error?
A) ls >-1
B) ls <C) ls >&2
D) ls >>2
E) ls |error
A) ls >-1
B) ls <
D) ls >>2
E) ls |error

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
70
Which of the following commands lists the dependencies of the RPM package file foo.rpm ?
A) rpm -qpR foo.rpm
B) rpm -dep foo
C) rpm -ld foo.rpm
D) rpm -R foo.rpm
E) rpm -pD foo
A) rpm -qpR foo.rpm
B) rpm -dep foo
C) rpm -ld foo.rpm
D) rpm -R foo.rpm
E) rpm -pD foo

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
71
Which of the following commands displays the output of the foo command on the screen and also writes it to a file called /tmp/foodata ?
A) foo | less /tmp/foodata
B) foo | cp /tmp/foodata
C) foo > /tmp/foodata
D) foo | tee /tmp/foodata
E) foo > stdout >> /tmp/foodata
A) foo | less /tmp/foodata
B) foo | cp /tmp/foodata
C) foo > /tmp/foodata
D) foo | tee /tmp/foodata
E) foo > stdout >> /tmp/foodata

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
72
Which of the following signals is sent to a process when the key combination Ctrl+C is pressed on the keyboard?
A) SIGTERM
B) SIGCONT
C) SIGSTOP
D) SIGKILL
E) SIGINT
A) SIGTERM
B) SIGCONT
C) SIGSTOP
D) SIGKILL
E) SIGINT

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
73
Instead of supplying an explicit device in /etc/fstab for mounting, what other options may be used to identify the intended partition?
A) LABEL
B) ID
C) FIND
D) NAME
E) UUID
A) LABEL
B) ID
C) FIND
D) NAME
E) UUID

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
74
Which of the following regular expressions represents a single upper-case letter?
A) :UPPER:
B) [A-Z]
C) !a-z
D) %C
E) {AZ}
A) :UPPER:
B) [A-Z]
C) !a-z
D) %C
E) {AZ}

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
75
In compliance with the FHS, in which of the directories are man pages found?
A) /opt/man/
B) /usr/doc/
C) /usr/share/man/
D) /var/pkg/man
E) /var/man/
A) /opt/man/
B) /usr/doc/
C) /usr/share/man/
D) /var/pkg/man
E) /var/man/

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
76
Which of the following directories on a 64 bit Linux system typically contain shared libraries?
A) ~/.lib64/
B) /usr/lib64/
C) /var/lib64/
D) /lib64/
E) /opt/lib64/
A) ~/.lib64/
B) /usr/lib64/
C) /var/lib64/
D) /lib64/
E) /opt/lib64/

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
77
A faulty kernel module is causing issues with a network interface card. Which of the following actions ensures that this module is not loaded automatically when the system boots?
A) Using lsmod --remove --autoclean without specifying the name of a specific module Using lsmod --remove --autoclean without specifying the name of a specific module
B) Using modinfo -k followed by the name of the offending module modinfo -k followed by the name of the offending module
C) Using modprobe -r followed by the name of the offending module modprobe -r
D) Adding a blacklist line including the name of the offending module to the file /etc/modprobe.d/blacklist.conf Adding a blacklist line including the name of the offending module to the file /etc/modprobe.d/blacklist.conf
E) Deleting the kernel module's directory from the file system and recompiling the kernel, including its modules
A) Using lsmod --remove --autoclean without specifying the name of a specific module Using lsmod --remove --autoclean without specifying the name of a specific module
B) Using modinfo -k followed by the name of the offending module modinfo -k followed by the name of the offending module
C) Using modprobe -r followed by the name of the offending module modprobe -r
D) Adding a blacklist line including the name of the offending module to the file /etc/modprobe.d/blacklist.conf Adding a blacklist line including the name of the offending module to the file /etc/modprobe.d/blacklist.conf
E) Deleting the kernel module's directory from the file system and recompiling the kernel, including its modules

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
78
Given a log file loga.log with timestamps of the format DD/MM/YYYY:hh:mm:ss , which command filters out all log entries in the time period between 8:00 am and 8:59 am?
A) grep -E ':08:[09]+:[09]+' loga.log
B) grep -E ':08:[00]+' loga.log
C) grep -E loga.log ':08:[0-9]+:[0-9]+'
D) grep loga.log ':08:[0-9]:[0-9]'
E) grep -E ':08:[0-9]+:[0-9]+' loga.log
A) grep -E ':08:[09]+:[09]+' loga.log
B) grep -E ':08:[00]+' loga.log
C) grep -E loga.log ':08:[0-9]+:[0-9]+'
D) grep loga.log ':08:[0-9]:[0-9]'
E) grep -E ':08:[0-9]+:[0-9]+' loga.log

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
79
Given the following two symbolic links in a System V init configuration: /etc/rc1.d/K01apache2 /etc/rc2.d/S02apache2 When are the scripts executed that are referenced by these links?
A) S02apache2 is run when runlevel 2 is entered. S02apache2 is run when runlevel 2 is entered.
B) S02apache2 is run when runlevel 2 is left. is run when runlevel 2 is left.
C) K01apache2 is never run because K indicates a deactivated service. K01apache2 is never run because K indicates a deactivated service.
D) Both S02apache2 and K01apache2 are run during a system shutdown. Both and are run during a system shutdown.
E) K01apache2 is run when runlevel 1 is entered. is run when runlevel 1 is entered.
A) S02apache2 is run when runlevel 2 is entered. S02apache2 is run when runlevel 2 is entered.
B) S02apache2 is run when runlevel 2 is left. is run when runlevel 2 is left.
C) K01apache2 is never run because K indicates a deactivated service. K01apache2 is never run because K indicates a deactivated service.
D) Both S02apache2 and K01apache2 are run during a system shutdown. Both and are run during a system shutdown.
E) K01apache2 is run when runlevel 1 is entered. is run when runlevel 1 is entered.

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck
80
Which of the following commands can be used to display the inode number of a given file?
A) inode
B) ln
C) ls
D) cp
E) stat
A) inode
B) ln
C) ls
D) cp
E) stat

Unlock Deck
Unlock for access to all 105 flashcards in this deck.
Unlock Deck
k this deck


