Deck 8: LPIC-2 Exam 202
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/99
Play
Full screen (f)
Deck 8: LPIC-2 Exam 202
1
When using mod_authz_core, which of the following strings can be used as an argument to Require in an Apache HTTPD configuration file to specify the authentication provider?
A) method
B) all
C) regex
D) header
E) expr
A) method
B) all
C) regex
D) header
E) expr
method
all
expr
all
expr
2
FILL BLANK Which directive in a Nginx server configuration block defines the TCP ports on which the virtual host will be available, and which protocols it will use? (Specify ONLY the option name without any values.)
listen
3
When trying to reverse proxy a web server through Nginx, what keyword is missing from the following configuration sample? 
A) remote_proxy
B) reverse_proxy
C) proxy_reverse
D) proxy_pass
E) forward_to

A) remote_proxy
B) reverse_proxy
C) proxy_reverse
D) proxy_pass
E) forward_to
proxy_pass
4
Which http_access directive for Squid allows users in the ACL named sales_net to only access the Internet at times specified in the time_acl named sales_time ?
A) http_access deny sales_time sales_net
B) http_access allow sales_net sales_time
C) http_access allow sales_net and sales-time
D) allow http_access sales_net sales_time
E) http_access sales_net sales_time
A) http_access deny sales_time sales_net
B) http_access allow sales_net sales_time
C) http_access allow sales_net and sales-time
D) allow http_access sales_net sales_time
E) http_access sales_net sales_time

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
5
Performing a DNS lookup with dig results in this response: 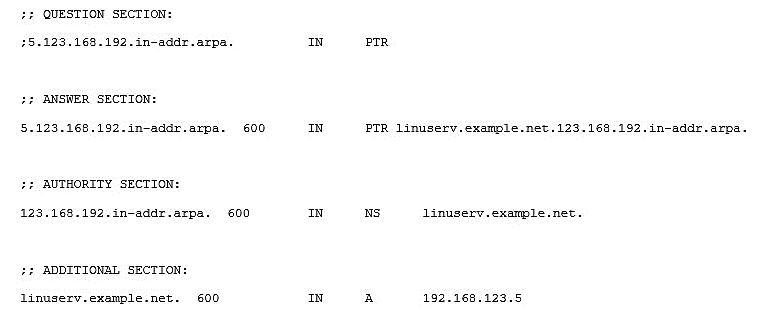
A) There is no . after linuserv.example.net in the PTR record in the forward lookup zone file There is no . after linuserv.example.net in the PTR record in the forward lookup zone file
B) There is no . after linuserv in the PTR record in the forward lookup zone file . after linuserv
C) There is no . after linuserv.example.net in the PTR record in the reverse lookup zone file in the PTR record in the reverse lookup zone file
D) The . in the NS definition in the reverse lookup zone has to be removed The . in the NS definition in the reverse lookup zone has to be removed

A) There is no . after linuserv.example.net in the PTR record in the forward lookup zone file There is no . after linuserv.example.net in the PTR record in the forward lookup zone file
B) There is no . after linuserv in the PTR record in the forward lookup zone file . after linuserv
C) There is no . after linuserv.example.net in the PTR record in the reverse lookup zone file in the PTR record in the reverse lookup zone file
D) The . in the NS definition in the reverse lookup zone has to be removed The . in the NS definition in the reverse lookup zone has to be removed

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
6
In a BIND zone file, what does the @ character indicate?
A) It's the fully qualified host name of the DNS server
B) It's an alias for the e-mail address of the zone master
C) It's the name of the zone as defined in the zone statement in named.conf It's the name of the zone as defined in the zone statement in named.conf
D) It's used to create an alias between two CNAME entries
A) It's the fully qualified host name of the DNS server
B) It's an alias for the e-mail address of the zone master
C) It's the name of the zone as defined in the zone statement in named.conf It's the name of the zone as defined in the zone statement in named.conf
D) It's used to create an alias between two CNAME entries

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
7
In order to protect a directory on an Apache HTTPD web server with a password, this configuration was added to an .htaccess file in the respective directory: 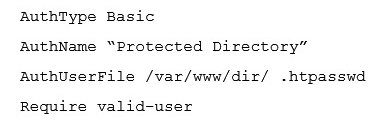 Furthermore, a file /var/www/dir/ .htpasswd was created with the following content: usera:S3cr3t Given that all these files were correctly processed by the web server processes, which of the following statements is true about requests to the directory?
Furthermore, a file /var/www/dir/ .htpasswd was created with the following content: usera:S3cr3t Given that all these files were correctly processed by the web server processes, which of the following statements is true about requests to the directory?
A) The user usera can access the site using the password s3cr3t The user usera can access the site using the password s3cr3t
B) Accessing the directory as usera raises HTTP error code 442 (User Not Existent) Accessing the directory as raises HTTP error code 442 (User Not Existent)
C) Requests are respond with HTTP error code 500 (Internal Server Error)
D) The browser prompts the visitor for a username and password but logins for usera do not seem to work The browser prompts the visitor for a username and password but logins for do not seem to work
E) The web server delivers the content of the directory without requesting authentication
 Furthermore, a file /var/www/dir/ .htpasswd was created with the following content: usera:S3cr3t Given that all these files were correctly processed by the web server processes, which of the following statements is true about requests to the directory?
Furthermore, a file /var/www/dir/ .htpasswd was created with the following content: usera:S3cr3t Given that all these files were correctly processed by the web server processes, which of the following statements is true about requests to the directory?A) The user usera can access the site using the password s3cr3t The user usera can access the site using the password s3cr3t
B) Accessing the directory as usera raises HTTP error code 442 (User Not Existent) Accessing the directory as raises HTTP error code 442 (User Not Existent)
C) Requests are respond with HTTP error code 500 (Internal Server Error)
D) The browser prompts the visitor for a username and password but logins for usera do not seem to work The browser prompts the visitor for a username and password but logins for do not seem to work
E) The web server delivers the content of the directory without requesting authentication

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
8
Which Apache HTTPD directive enables HTTPS protocol support?
A) HTTPSEngine on
B) SSLEngine on
C) SSLEnable on
D) HTTPSEnable on
E) StartTLS on
A) HTTPSEngine on
B) SSLEngine on
C) SSLEnable on
D) HTTPSEnable on
E) StartTLS on

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
9
Which BIND option should be used to limit the IP addresses from which slave name servers may connect?
A) allow-zone-transfer
B) allow-transfer
C) allow-secondary
D) allow-slaves
E) allow-queries
A) allow-zone-transfer
B) allow-transfer
C) allow-secondary
D) allow-slaves
E) allow-queries

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
10
In response to a certificate signing request, a certification authority sent a web server certificate along with the certificate of an intermediate certification authority that signed the web server certificate. What should be done with the intermediate certificate in order to use the web server certificate with Apache HTTPD?
A) The intermediate certificate should be merged with the web server's certificate into one file that is specified in SSLCertificateFile The intermediate certificate should be merged with the web server's certificate into one file that is specified in SSLCertificateFile
B) The intermediate certificate should be used to verify the certificate before its deployment on the web server and can be deleted
C) The intermediate certificate should be stored in its own file which is referenced in SSLCaCertificateFile The intermediate certificate should be stored in its own file which is referenced in SSLCaCertificateFile
D) The intermediate certificate should be improved into the certificate store of the web browser used to test the correct operation of the web server
E) The intermediate certificate should be archived and resent to the certification authority in order to request a renewal of the certificate
A) The intermediate certificate should be merged with the web server's certificate into one file that is specified in SSLCertificateFile The intermediate certificate should be merged with the web server's certificate into one file that is specified in SSLCertificateFile
B) The intermediate certificate should be used to verify the certificate before its deployment on the web server and can be deleted
C) The intermediate certificate should be stored in its own file which is referenced in SSLCaCertificateFile The intermediate certificate should be stored in its own file which is referenced in SSLCaCertificateFile
D) The intermediate certificate should be improved into the certificate store of the web browser used to test the correct operation of the web server
E) The intermediate certificate should be archived and resent to the certification authority in order to request a renewal of the certificate

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
11
What word is missing from the following excerpt of a named.conf file? 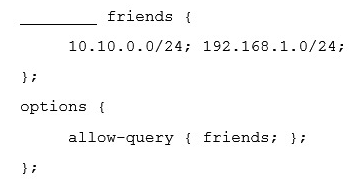
A) networks
B) net
C) list
D) acl
E) group

A) networks
B) net
C) list
D) acl
E) group

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
12
Which global option in squid.conf sets the port number or numbers that Squid will use to listen for client requests?
A) port
B) client_port
C) http_port
D) server_port
E) squid_port
A) port
B) client_port
C) http_port
D) server_port
E) squid_port

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
13
A host, called lpi , with the MAC address 08:00:2b:4c:59:23 should always be given the IP address of 192.168.1.2 by a DHCP server running ISC DHCPD. Which of the following configurations will achieve this?
A)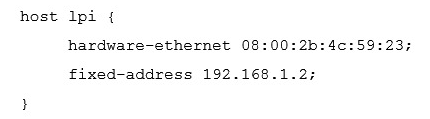
B)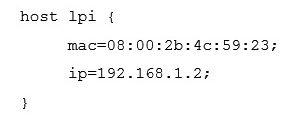
C) host lpi = 08:00:2b:4c:59:23 192.168.1.2
D)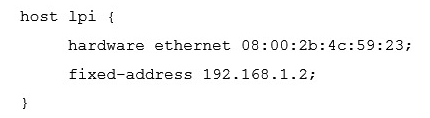
E)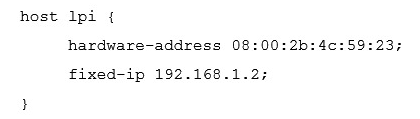
A)

B)

C) host lpi = 08:00:2b:4c:59:23 192.168.1.2
D)

E)


Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
14
Which tool creates a Certificate Signing Request (CSR) for serving HTTPS with Apache HTTPD?
A) apachect1
B) certgen
C) cartool
D) httpsgen
E) openssl
A) apachect1
B) certgen
C) cartool
D) httpsgen
E) openssl

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
15
What option for BIND is required in the global options to disable recursive queries on the DNS server by default?
A) allow-recursive-query ( none; );
B) allow-recursive-query off;
C) recursion { disabled; };
D) recursion { none; };
E) recursion no;
A) allow-recursive-query ( none; );
B) allow-recursive-query off;
C) recursion { disabled; };
D) recursion { none; };
E) recursion no;

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following DNS records could be a glue record?
A) ns1.lab A 198.51.100.53
B) lab NS 198.51.100.53
C) ns1.lab NS 198.51.100.53
D) ns1. A 198.51.100.53
E) ns1.lab GLUE 198.51.100.53
A) ns1.lab A 198.51.100.53
B) lab NS 198.51.100.53
C) ns1.lab NS 198.51.100.53
D) ns1. A 198.51.100.53
E) ns1.lab GLUE 198.51.100.53

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
17
What is DNSSEC used for?
A) Encrypted DNS queries between nameservers
B) Cryptographic authentication of DNS zones
C) Secondary DNS queries for local zones
D) Authentication of the user that initiated the DNS query
E) Encrypting DNS queries and response
A) Encrypted DNS queries between nameservers
B) Cryptographic authentication of DNS zones
C) Secondary DNS queries for local zones
D) Authentication of the user that initiated the DNS query
E) Encrypting DNS queries and response

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
18
If there is no access directive, what is the default setting for OpenLDAP?
A)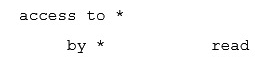
B)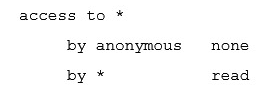
C)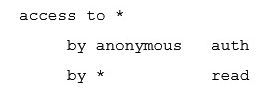
D)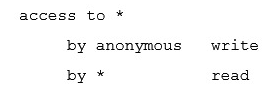
A)
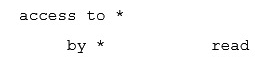
B)

C)

D)


Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
19
FILL BLANK What configuration directive of the Apache HTTPD server defines where log files are stored? (Specify ONE of the directives without any other options.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
20
Which statements about the Alias and Redirect directives in Apache HTTPD's configuration file are true?
A) Alias can only reference files under DocumentRoot Alias can only reference files under DocumentRoot
B) Redirect works with regular expressions Redirect works with regular expressions
C) Redirect is handled on the client side is handled on the client side
D) Alias is handled on the server side is handled on the server side
E) Alias is not a valid configuration directive is not a valid configuration directive
A) Alias can only reference files under DocumentRoot Alias can only reference files under DocumentRoot
B) Redirect works with regular expressions Redirect works with regular expressions
C) Redirect is handled on the client side is handled on the client side
D) Alias is handled on the server side is handled on the server side
E) Alias is not a valid configuration directive is not a valid configuration directive

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
21
To allow X connections to be forwarded from or through an SSH server, what configuration keyword must be set to yes in the sshd configuration file?
A) AllowForwarding
B) ForwardingAllow
C) XllForwardingAllow
D) XllForwarding
A) AllowForwarding
B) ForwardingAllow
C) XllForwardingAllow
D) XllForwarding

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
22
What is the standard port used by OpenVPN?
A) 1723
B) 4500
C) 500
D) 1194
A) 1723
B) 4500
C) 500
D) 1194

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
23
FILL BLANK What is the path to the global Postfix configuration file? (Specify the full name of the file, including path .)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
24
FILL BLANK According to this LDIF excerpt, which organizational unit is Robert Smith part of? (Specify only the organizational unit.) 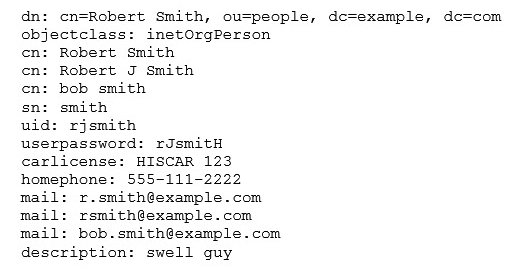


Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
25
Using its standard configuration, how does fail2ban block offending SSH clients?
A) By rejecting connections due to its role as a proxy in front of SSHD.
B) By modifying and adjusting the SSHD configuration.
C) By creating and maintaining netfilter rules.
D) By creating null routes that drop any response packets sent to the client.
E) By modifying and adjusting the TCP Wrapper configuration for SSHD.
A) By rejecting connections due to its role as a proxy in front of SSHD.
B) By modifying and adjusting the SSHD configuration.
C) By creating and maintaining netfilter rules.
D) By creating null routes that drop any response packets sent to the client.
E) By modifying and adjusting the TCP Wrapper configuration for SSHD.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
26
How is the LDAP administrator account configured when the rootdn and rootpw directives are not present in the slapd.conf file?
A) The default account admin with the password admin are used
B) The account is defined by an ACL in slapd.conf The account is defined by an ACL in
C) The default account admin is used without a password
D) The account is defined in the file /etc/ldap.secret The account is defined in the file /etc/ldap.secret
E) The account is defined in the file /etc/ldap.root.conf /etc/ldap.root.conf
A) The default account admin with the password admin are used
B) The account is defined by an ACL in slapd.conf The account is defined by an ACL in
C) The default account admin is used without a password
D) The account is defined in the file /etc/ldap.secret The account is defined in the file /etc/ldap.secret
E) The account is defined in the file /etc/ldap.root.conf /etc/ldap.root.conf

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
27
Which of the following information has to be submitted to a certification authority in order to request a web server certificate?
A) The web server's private key.
B) The IP address of the web server.
C) The list of ciphers supported by the web server.
D) The web server's SSL configuration file.
E) The certificate signing request.
A) The web server's private key.
B) The IP address of the web server.
C) The list of ciphers supported by the web server.
D) The web server's SSL configuration file.
E) The certificate signing request.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
28
For what purpose is TCP/IP stack fingerprinting used by nmap?
A) It is used to determine the remote operating system.
B) It is used to filter out responses from specific servers.
C) It is used to identify duplicate responses from the same remote server.
D) It is used to masquerade the responses of remote servers.
E) It is used to uniquely identify servers on the network for forensics.
A) It is used to determine the remote operating system.
B) It is used to filter out responses from specific servers.
C) It is used to identify duplicate responses from the same remote server.
D) It is used to masquerade the responses of remote servers.
E) It is used to uniquely identify servers on the network for forensics.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
29
FILL BLANK What is the name of the root element of the LDAP tree holding the configuration of an OpenLDAP server that is using directory based configuration? (Specify ONLY the element's name without any additional information.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
30
FILL BLANK Which OpenLDAP client command can be used to change the password for an LDAP entry? (Specify ONLY the command without any path or parameters.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following PAM modules allows the system administrator to use an arbitrary file containing a list of user and group names with restrictions on the system resources available to them?
A) pam_filter
B) pam_limits
C) pam_listfile
D) pam_unix
A) pam_filter
B) pam_limits
C) pam_listfile
D) pam_unix

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
32
How are PAM modules organized and stored?
A) As plain text files in /etc/security/ As plain text files in /etc/security/
B) A statically linked binaries in /etc/pam.d/bin/ A statically linked binaries in /etc/pam.d/bin/
C) As Linux kernel modules within the respective sub directory of /lib/modules/ As Linux kernel modules within the respective sub directory of /lib/modules/
D) As shared object files within the /lib/ directory hierarchy As shared object files within the /lib/ directory hierarchy
E) As dynamically linked binaries in /usr/lib/pam/sbin/ As dynamically linked binaries in /usr/lib/pam/sbin/
A) As plain text files in /etc/security/ As plain text files in /etc/security/
B) A statically linked binaries in /etc/pam.d/bin/ A statically linked binaries in /etc/pam.d/bin/
C) As Linux kernel modules within the respective sub directory of /lib/modules/ As Linux kernel modules within the respective sub directory of /lib/modules/
D) As shared object files within the /lib/ directory hierarchy As shared object files within the /lib/ directory hierarchy
E) As dynamically linked binaries in /usr/lib/pam/sbin/ As dynamically linked binaries in /usr/lib/pam/sbin/

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
33
In a PAM configuration file, which of the following is true about the required control flag?
A) If the module returns success, no more modules of the same type will be invoked
B) The success of the module is needed for the module-type facility to succeed. If it returns a failure, control is returned to the calling application
C) The success of the module is needed for the module-type facility to succeed. However, all remaining modules of the same type will be invoked
D) The module is not critical and whether it returns success or failure is not important
E) If the module returns failure, no more modules of the same type will be invoked
A) If the module returns success, no more modules of the same type will be invoked
B) The success of the module is needed for the module-type facility to succeed. If it returns a failure, control is returned to the calling application
C) The success of the module is needed for the module-type facility to succeed. However, all remaining modules of the same type will be invoked
D) The module is not critical and whether it returns success or failure is not important
E) If the module returns failure, no more modules of the same type will be invoked

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
34
What does the samba-tool testparm command confirm regarding the Samba configuration?
A) The configuration loads successfully.
B) The service operates as expected.
C) The Samba services are started automatically when the system boots.
D) The netfilter configuration on the Samba server does not block any access to the services defined in the configuration.
E) All running Samba processes use the most recent configuration version.
A) The configuration loads successfully.
B) The service operates as expected.
C) The Samba services are started automatically when the system boots.
D) The netfilter configuration on the Samba server does not block any access to the services defined in the configuration.
E) All running Samba processes use the most recent configuration version.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
35
Select the Samba option below that should be used if the main intention is to setup a guest printer service?
A) security = cups
B) security = ldap
C) security = pam
D) security = share
E) security = printing
A) security = cups
B) security = ldap
C) security = pam
D) security = share
E) security = printing

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
36
FILL BLANK In order to specify alterations to an LDAP entry, what keyword is missing from the following LDIF file excerpt? 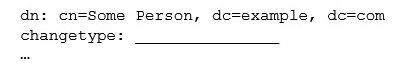 Specify the keyword only and no other information.
Specify the keyword only and no other information.
 Specify the keyword only and no other information.
Specify the keyword only and no other information.
Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
37
Which FTP names are recognized as anonymous users in vsftp when the option anonymous_enable is set to yes in the configuration files?
A) anonymous
B) ftp
C) In the described configuration, any username which neither belongs to an existing user nor has another special meaning is treated as anonymous user.
D) nobody
E) guest
A) anonymous
B) ftp
C) In the described configuration, any username which neither belongs to an existing user nor has another special meaning is treated as anonymous user.
D) nobody
E) guest

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following statements in the ISC DHCPD configuration is used to specify whether or not an address pool can be used by nodes which have a corresponding host section in the configuration?
A) identified-nodes
B) unconfigured-hosts
C) missing-peers
D) unmatched-hwaddr
E) unknown-clients
A) identified-nodes
B) unconfigured-hosts
C) missing-peers
D) unmatched-hwaddr
E) unknown-clients

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
39
FILL BLANK What option in the sshd configuration file instructs to permit only specific user names to log in to a system? (Specify ONLY the option name without any values.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
40
A company is transitioning to a new DNS domain name and wants to accept e-mail for both domains for all of its users on a Postfix server. Which configuration option should be updated to accomplish this?
A) mydomain
B) mylocations
C) mydestination
D) myhosts
E) mydomains
A) mydomain
B) mylocations
C) mydestination
D) myhosts
E) mydomains

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
41
Which command is used to administer IPv6 netfilter rules?
A) iptables
B) iptablesv6
C) iptables6
D) ip6tables
E) ipv6tables
A) iptables
B) iptablesv6
C) iptables6
D) ip6tables
E) ipv6tables

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
42
Which rdnc sub command can be used in conjunction with the name of a zone in order to make BIND reread the content of the specific zone file without reloading other zones as well?
A) lookup
B) reload
C) fileupdate
D) reread
E) zoneupdate
A) lookup
B) reload
C) fileupdate
D) reread
E) zoneupdate

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
43
Which of the following Samba configuration parameters is functionally identical to the parameter read only=yes ?
A) browseable=no
B) read write=no
C) writeable=no
D) write only=no
E) write access=no
A) browseable=no
B) read write=no
C) writeable=no
D) write only=no
E) write access=no

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
44
Which of the following DNS record types is used for reverse DNS queries?
A) CNAME
B) IN
C) PTR
D) REV
E) RIN
A) CNAME
B) IN
C) PTR
D) REV
E) RIN

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
45
Fill in the blank. What command creates a SSH key pair? (Specify ONLY the command without any path or parameters)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
46
With fail2ban, what is a 'jail'?
A) A netfilter rules chain blocking offending IP addresses for a particular service
B) A group of services on the server which should be monitored for similar attack patterns in the log files
C) A filter definition and a set of one or more actions to take when the filter is matched
D) The chroot environment in which fail2ban runs
A) A netfilter rules chain blocking offending IP addresses for a particular service
B) A group of services on the server which should be monitored for similar attack patterns in the log files
C) A filter definition and a set of one or more actions to take when the filter is matched
D) The chroot environment in which fail2ban runs

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following OpenVPN configuration options makes OpenVPN forward network packets between VPN clients itself instead of passing the packets on to the Linux host which runs the OpenVPN server for further processing?
A) inter-client-traffic
B) client-to-client
C) client-router
D) client-pass
E) grant-client-traffic
A) inter-client-traffic
B) client-to-client
C) client-router
D) client-pass
E) grant-client-traffic

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
48
The program vsftpd, running in a chroot jail, gives the following error:  Which of the following actions would fix the error?
Which of the following actions would fix the error?
A) The file /etc/ld.so.conf in the root filesystem must contain the path to the appropriate lib directory in the chroot jail The file /etc/ld.so.conf in the root filesystem must contain the path to the appropriate lib directory in the chroot jail
B) Create a symbolic link that points to the required library outside the chroot jail
C) Copy the required library to the appropriate lib directory in the chroot jail Copy the required library to the appropriate
D) Run the program using the command chroot and the option --static_libs Run the program using the command chroot and the option --static_libs
 Which of the following actions would fix the error?
Which of the following actions would fix the error?A) The file /etc/ld.so.conf in the root filesystem must contain the path to the appropriate lib directory in the chroot jail The file /etc/ld.so.conf in the root filesystem must contain the path to the appropriate lib directory in the chroot jail
B) Create a symbolic link that points to the required library outside the chroot jail
C) Copy the required library to the appropriate lib directory in the chroot jail Copy the required library to the appropriate
D) Run the program using the command chroot and the option --static_libs Run the program using the command chroot and the option --static_libs

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
49
Which of the following commands can be used to connect and interact with remote TCP network services?
A) nettalk
B) nc
C) telnet
D) cat
E) netmap
A) nettalk
B) nc
C) telnet
D) cat
E) netmap

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
50
What is the name of the network security scanner project which, at the core, is a server with a set of network vulnerability tests?
A) NetMap
B) OpenVAS
C) Smartscan
D) Wireshark
A) NetMap
B) OpenVAS
C) Smartscan
D) Wireshark

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
51
Which of these tools provides DNS information in the following format? 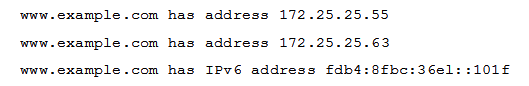
A) dig
B) nslookup
C) host
D) named-checkconf
E) named-checkzone

A) dig
B) nslookup
C) host
D) named-checkconf
E) named-checkzone

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following Samba services handles the membership of a file server in an Active Directory domain?
A) winbindd
B) nmbd
C) msadd
D) admemb
E) samba
A) winbindd
B) nmbd
C) msadd
D) admemb
E) samba

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
53
The content of which local file has to be transmitted to a remote SSH server in order to be able to log into the remote server using SSH keys?
A) ~ /.ssh/authorized_keys ~ /.ssh/authorized_keys
B) ~ /.ssh/config /.ssh/config
C) ~ /.ssh/id_rsa.pub /.ssh/id_rsa.pub
D) ~ /.ssh/id_rsa /.ssh/id_rsa
E) ~ ./ssh/known_hosts ./ssh/known_hosts
A) ~ /.ssh/authorized_keys ~ /.ssh/authorized_keys
B) ~ /.ssh/config /.ssh/config
C) ~ /.ssh/id_rsa.pub /.ssh/id_rsa.pub
D) ~ /.ssh/id_rsa /.ssh/id_rsa
E) ~ ./ssh/known_hosts ./ssh/known_hosts

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
54
To which destination will a route appear in the Linux routing table after activating IPv6 on a router's network interface, even when no global IPv6 addresses have been assigned to the interface?
A) fe80::/10
B) 0::/128
C) 0::/0
D) fe80::/64
E) 2000::/3
A) fe80::/10
B) 0::/128
C) 0::/0
D) fe80::/64
E) 2000::/3

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
55
After running ssh-keygen and accepting the default values, which of the following files are changed or created?
A) ~/.ssh/id_rsa.key
B) ~/.ssh/id_rsa.pub
C) ~/.ssh/id_rsa.prv
D) ~/.ssh/id_rsa.crt
E) ~/.ssh/id_rsa
A) ~/.ssh/id_rsa.key
B) ~/.ssh/id_rsa.pub
C) ~/.ssh/id_rsa.prv
D) ~/.ssh/id_rsa.crt
E) ~/.ssh/id_rsa

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
56
Which netfilter table contains built-in chains called INPUT , OUTPUT and FORWARD ?
A) ipconn
B) filter
C) nat
D) default
E) masq
A) ipconn
B) filter
C) nat
D) default
E) masq

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
57
In order to prevent all anonymous FTP users from listing uploaded file names, what security precaution can be taken when creating an upload directory?
A) The directory must not have the execute permission set.
B) The directory must not have the read permission set.
C) The directory must not have the read or execute permission set.
D) The directory must not have the write permission set.
E) The directory must not contain other directories.
A) The directory must not have the execute permission set.
B) The directory must not have the read permission set.
C) The directory must not have the read or execute permission set.
D) The directory must not have the write permission set.
E) The directory must not contain other directories.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
58
In which CIFS share must printer drivers be placed to allow Point'n'Print driver deployment on Windows?
A) winx64drv$
B) print$
C) The name of the share is specified in the option print driver share within each printable share in smb.conf The name of the share is specified in the option print driver share within each printable share in smb.conf
D) pnpdrivers$
E) NETLOGON
A) winx64drv$
B) print$
C) The name of the share is specified in the option print driver share within each printable share in smb.conf The name of the share is specified in the option print driver share within each printable share in smb.conf
D) pnpdrivers$
E) NETLOGON

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
59
How must Samba be configured such that it can check CIFS passwords against those found in /etc/passwd and /etc/ shadow?
A) Set the parameters "encrypt passwords = yes" and "password file = /etc/passwd" Set the parameters "encrypt passwords = yes" "password file = /etc/passwd"
B) Set the parameters "encrypt passwords = yes" , "password file = /etc/passwd" and "password algorithm = crypt" , "password algorithm = crypt"
C) Delete the smbpasswd file and create a symbolic link to the passwd and shadow file Delete the smbpasswd file and create a symbolic link to the passwd shadow file
D) It is not possible for Samba to use /etc/passwd and /etc/shadow directly
E) Run smbpasswd to convert /etc/passwd and /etc/shadow to a Samba password file Run to convert /etc/shadow to a Samba password file
A) Set the parameters "encrypt passwords = yes" and "password file = /etc/passwd" Set the parameters "encrypt passwords = yes" "password file = /etc/passwd"
B) Set the parameters "encrypt passwords = yes" , "password file = /etc/passwd" and "password algorithm = crypt" , "password algorithm = crypt"
C) Delete the smbpasswd file and create a symbolic link to the passwd and shadow file Delete the smbpasswd file and create a symbolic link to the passwd shadow file
D) It is not possible for Samba to use /etc/passwd and /etc/shadow directly
E) Run smbpasswd to convert /etc/passwd and /etc/shadow to a Samba password file Run to convert /etc/shadow to a Samba password file

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
60
A zone file contains the following lines: 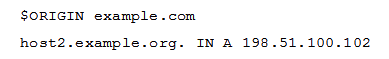 and is included in the BIND configuration using this configuration stanza:
and is included in the BIND configuration using this configuration stanza: 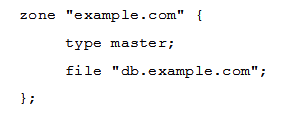 Which problem is contained in this configuration?
Which problem is contained in this configuration?
A) The zone statement is the BIND configuration must contain the cross-zone-data yes ; statement. The zone statement is the BIND configuration must contain the cross-zone-data yes ; statement.
B) The zone cannon contain records for a name which is outside the zone's hierarchy.
C) The $ORIGIN declaration cannot be used in zone files that are included for a specific zone name in the BIND configuration. $ORIGIN declaration cannot be used in zone files that are included for a specific zone name in the BIND configuration.
D) An A record cannot contain an IPv4 address because its value is supposed to be a reverse DNS name.
E) Names of records in a zone file cannot be fully qualified domain names.
 and is included in the BIND configuration using this configuration stanza:
and is included in the BIND configuration using this configuration stanza:  Which problem is contained in this configuration?
Which problem is contained in this configuration?A) The zone statement is the BIND configuration must contain the cross-zone-data yes ; statement. The zone statement is the BIND configuration must contain the cross-zone-data yes ; statement.
B) The zone cannon contain records for a name which is outside the zone's hierarchy.
C) The $ORIGIN declaration cannot be used in zone files that are included for a specific zone name in the BIND configuration. $ORIGIN declaration cannot be used in zone files that are included for a specific zone name in the BIND configuration.
D) An A record cannot contain an IPv4 address because its value is supposed to be a reverse DNS name.
E) Names of records in a zone file cannot be fully qualified domain names.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
61
Which command is used to configure which file systems a NFS server makes available to clients?
A) exportfs
B) mkfs.nfs
C) mount
D) nfsservct1
E) telinit
A) exportfs
B) mkfs.nfs
C) mount
D) nfsservct1
E) telinit

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
62
Fill in the blank. What configuration directive of the Apache HTTPD server defines where log files are stored? (Specify ONE of the directives without any other options.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
63
When are Sieve filters usually applied to an email?
A) When the email is delivered to a mailbox
B) When the email is relayed by an SMTP server
C) When the email is received by an SMTP smarthost
D) When the email is sent to the first server by an MUA
E) When the email is retrieved by an MUA
A) When the email is delivered to a mailbox
B) When the email is relayed by an SMTP server
C) When the email is received by an SMTP smarthost
D) When the email is sent to the first server by an MUA
E) When the email is retrieved by an MUA

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
64
Which of the following statements is true regarding the NFSv4 pseudo file system on the NFS server?
A) It must be called /exports It must be called /exports
B) It usually contains bind mounts of the directory trees to be exported
C) It must be a dedicated partition on the server
D) It is defined in the option Nfsv4-Root in /etc/pathmapd.conf It is defined in the option Nfsv4-Root in /etc/pathmapd.conf
E) It usually contains symlinks to the directory trees to be exported
A) It must be called /exports It must be called /exports
B) It usually contains bind mounts of the directory trees to be exported
C) It must be a dedicated partition on the server
D) It is defined in the option Nfsv4-Root in /etc/pathmapd.conf It is defined in the option Nfsv4-Root in /etc/pathmapd.conf
E) It usually contains symlinks to the directory trees to be exported

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
65
Fill in the blank. In order to specify alterations to an LDAP entry, what keyword is missing from the following LDIF file excerpt? 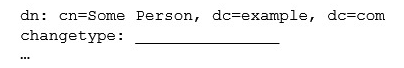 Specify the keyword only and no other information.
Specify the keyword only and no other information.
 Specify the keyword only and no other information.
Specify the keyword only and no other information.
Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
66
A user requests a "hidden" Samba share, named confidential , similar to the Windows Administration Share. How can this be configured?
A)
B)
C)
D)
E)
A)

B)

C)

D)

E)


Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
67
What option in the client configuration file would tell OpenVPN to use a dynamic source port when making a connection to a peer?
A) src-port
B) remote
C) source-port
D) nobind
E) dynamic-bind
A) src-port
B) remote
C) source-port
D) nobind
E) dynamic-bind

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
68
Fill in the blank. Which directive in a Nginx server configuration block defines the TCP ports on which the virtual host will be available, and which protocols it will use? (Specify ONLY the option name without any values.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
69
Fill in the blank. Which OpenLDAP client command can be used to change the password for an LDAP entry? (Specify ONLY the command without any path or parameters.)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
70
Fill in the blank. What is the path to the global Postfix configuration file? (Specify the full name of the file, including path .)

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
71
Which keyword is used in the Squid configuration to define networks and times used to limit access to the service?
A) acl
B) allow
C) http_allow
D) permit
A) acl
B) allow
C) http_allow
D) permit

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
72
Which of the following options are valid in /etc/exports ?
A) rw
B) ro
C) rootsquash
D) norootsquash
E) uid
A) rw
B) ro
C) rootsquash
D) norootsquash
E) uid

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
73
Which Linux user is used by vsftpd to perform file system operations for anonymous FTP users?
A) The Linux user which runs the vsftpd process
B) The Linux user that owns the root FTP directory served by vsftpd
C) The Linux user with the same user name that was used to anonymously log into the FTP server
D) The Linux user root, but vsftpd grants access to anonymous users only to globally read-/writeable files
E) The Linux user specified in the configuration option ftp_username
A) The Linux user which runs the vsftpd process
B) The Linux user that owns the root FTP directory served by vsftpd
C) The Linux user with the same user name that was used to anonymously log into the FTP server
D) The Linux user root, but vsftpd grants access to anonymous users only to globally read-/writeable files
E) The Linux user specified in the configuration option ftp_username

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
74
Which of the following lines in the sshd configuration file should, if present, be changed in order to increase the security of the server?
A) Protocol 2, 1
B) PermitEmptyPasswords no
C) Port 22
D) PermitRootLogin yes
E) IgnoreRhosts yes
A) Protocol 2, 1
B) PermitEmptyPasswords no
C) Port 22
D) PermitRootLogin yes
E) IgnoreRhosts yes

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
75
Which of these tools, without any options, provides the most information when performing DNS queries?
A) dig
B) nslookup
C) host
D) named-checkconf
E) named-checkzone
A) dig
B) nslookup
C) host
D) named-checkconf
E) named-checkzone

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
76
The following Apache HTTPD configuration has been set up to create a virtual host available at www.example.com and www2.example.com: 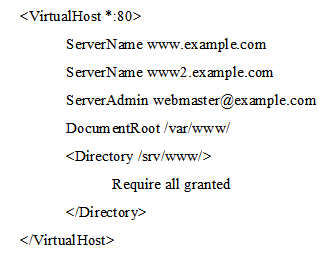 Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?
Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?
A) The configuration must be split into two VirtualHost sections since each virtual host may only have one name. The configuration must be split into two VirtualHost sections since each virtual host may only have one name.
B) The port mentioned in opening VirtualHost tag has to be appended to the ServerName declaration's values. The port mentioned in opening tag has to be appended to the ServerName declaration's values.
C) Both virtual host names have to be placed as comma separated values in one ServerName declaration. Both virtual host names have to be placed as comma separated values in one declaration.
D) Both virtual host names have to be mentioned in the opening VirtualHost tag. Both virtual host names have to be mentioned in the opening tag.
E) Only one Server name declaration may exist, but additional names can be declared in ServerAlias options. Only one Server name declaration may exist, but additional names can be declared in ServerAlias options.
 Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?
Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?A) The configuration must be split into two VirtualHost sections since each virtual host may only have one name. The configuration must be split into two VirtualHost sections since each virtual host may only have one name.
B) The port mentioned in opening VirtualHost tag has to be appended to the ServerName declaration's values. The port mentioned in opening tag has to be appended to the ServerName declaration's values.
C) Both virtual host names have to be placed as comma separated values in one ServerName declaration. Both virtual host names have to be placed as comma separated values in one declaration.
D) Both virtual host names have to be mentioned in the opening VirtualHost tag. Both virtual host names have to be mentioned in the opening tag.
E) Only one Server name declaration may exist, but additional names can be declared in ServerAlias options. Only one Server name declaration may exist, but additional names can be declared in ServerAlias options.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
77
Which of the following actions synchronizes UNIX passwords with the Samba passwords when the encrypted Samba password is changed using smbpasswd ?
A) There are no actions to accomplish this since is not possible.
B) Run netvamp regularly, to convert the passwords. Run netvamp regularly, to convert the passwords.
C) Run winbind -sync , to synchronize the passwords. winbind -sync , to synchronize the passwords.
D) Add unix password sync = yes to smb.conf Add unix password sync = yes to smb.conf
E) Add smb unix password = sync to smb.conf smb unix password = sync
A) There are no actions to accomplish this since is not possible.
B) Run netvamp regularly, to convert the passwords. Run netvamp regularly, to convert the passwords.
C) Run winbind -sync , to synchronize the passwords. winbind -sync , to synchronize the passwords.
D) Add unix password sync = yes to smb.conf Add unix password sync = yes to smb.conf
E) Add smb unix password = sync to smb.conf smb unix password = sync

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
78
It has been discovered that the company mail server is configured as an open relay. Which of the following actions would help prevent the mail server from being used as an open relay while maintaining the possibility to receive company mails?
A) Restrict Postfix to only accept e-mail for domains hosted on this server
B) Configure Dovecot to support IMAP connectivity
C) Configure netfilter to not permit port 25 traffic on the public network
D) Restrict Postfix to only relay outbound SMTP from the internal network
E) Upgrade the mailbox format from mbox to maildir
A) Restrict Postfix to only accept e-mail for domains hosted on this server
B) Configure Dovecot to support IMAP connectivity
C) Configure netfilter to not permit port 25 traffic on the public network
D) Restrict Postfix to only relay outbound SMTP from the internal network
E) Upgrade the mailbox format from mbox to maildir

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
79
Which of the following nmap parameters scans a target for open TCP ports?
A) -sO
B) -sZ
C) -sT
D) -sU
E) -sS
A) -sO
B) -sZ
C) -sT
D) -sU
E) -sS

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
80
The Samba configuration file contains the following lines: 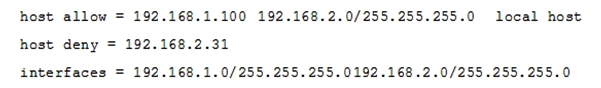 A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server. Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server. Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
A) host allow = 192.168.1.1-255
B) host allow = 192.168.1.100 192.168.2.200 localhost
C) host deny = 192.168.1.100/255.255.255.0 192.168.2.31 localhost
D) host deny = 192.168.2.200/255.255.255.0 192.168.2.31 localhost
E) host allow = 192.168.1.0/255.255.255.0 192.168.2.0/255.255.255.0 localhost
 A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server. Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server. Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?A) host allow = 192.168.1.1-255
B) host allow = 192.168.1.100 192.168.2.200 localhost
C) host deny = 192.168.1.100/255.255.255.0 192.168.2.31 localhost
D) host deny = 192.168.2.200/255.255.255.0 192.168.2.31 localhost
E) host allow = 192.168.1.0/255.255.255.0 192.168.2.0/255.255.255.0 localhost

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck


