Deck 15: Service Provider Routing and Switching, Professional (JNCIP-SP)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/30
Play
Full screen (f)
Deck 15: Service Provider Routing and Switching, Professional (JNCIP-SP)
1
Referring to the exhibit, each node in the IP fabric is peering to its directly attached neighbor using EBGP. Each node is peering using physical interface IP addresses. Leaf 2 and Leaf 3 are advertising the 10.1.1/24 network into EBGP. Spine 2 must be configured so that it can load-share traffic destined to the 10 1.1/24 network over both next-hop A and next-hop B. 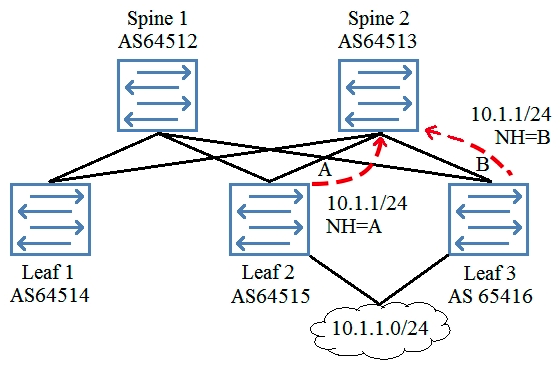 Which two actions must be performed to accomplish this task? (Choose two.)
Which two actions must be performed to accomplish this task? (Choose two.)
A) Use a load-balancing policy applied to the forwarding table.
B) Use multipath multiple-AS.
C) Use advertise-inactive.
D) Use multihop.
 Which two actions must be performed to accomplish this task? (Choose two.)
Which two actions must be performed to accomplish this task? (Choose two.)A) Use a load-balancing policy applied to the forwarding table.
B) Use multipath multiple-AS.
C) Use advertise-inactive.
D) Use multihop.
Use a load-balancing policy applied to the forwarding table.
Use multipath multiple-AS.
Use multipath multiple-AS.
2
You want to configure redundant Layer 3 gateways. In this scenario, which two Juniper best practices would accomplish this task? (Choose two.)
A) configuring both IRB interfaces manually with the same MAC address.
B) allowing Junos to dynamically create the virtual IP address of the IRB interface.
C) configuring both IRB interfaces manually with the same IP address.
D) allowing Junos to dynamically create the virtual MAC address of the IRB interface.
A) configuring both IRB interfaces manually with the same MAC address.
B) allowing Junos to dynamically create the virtual IP address of the IRB interface.
C) configuring both IRB interfaces manually with the same IP address.
D) allowing Junos to dynamically create the virtual MAC address of the IRB interface.
configuring both IRB interfaces manually with the same IP address.
allowing Junos to dynamically create the virtual MAC address of the IRB interface.
allowing Junos to dynamically create the virtual MAC address of the IRB interface.
3
You are logged in to Leaf 1. When examining the routing table, you notice that you have no routes from Leaf 2. 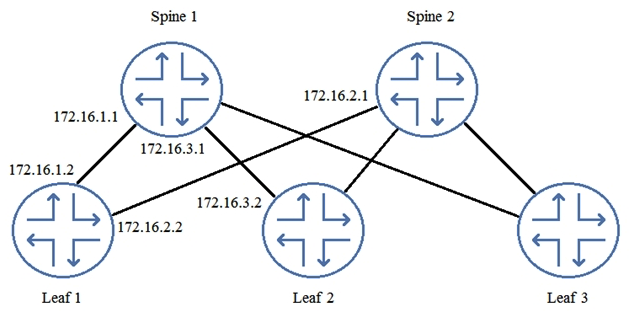 Referring to the exhibit, which two commands would you use to troubleshoot the problem? (Choose two.)
Referring to the exhibit, which two commands would you use to troubleshoot the problem? (Choose two.)
A) From Leaf 2, issue the show route advertising-protocol bgp 172.16.1.2 command. From Leaf 2, issue the show route advertising-protocol bgp 172.16.1.2 command.
B) From Spine 1, issue the show route advertising-protocol bgp 172.16.1.1 command. From Spine 1, issue the show route advertising-protocol bgp 172.16.1.1
C) From Spine 1, issue the show route advertising-protocol bgp 172.16.1.2 command.
D) From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command. From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command.
 Referring to the exhibit, which two commands would you use to troubleshoot the problem? (Choose two.)
Referring to the exhibit, which two commands would you use to troubleshoot the problem? (Choose two.)A) From Leaf 2, issue the show route advertising-protocol bgp 172.16.1.2 command. From Leaf 2, issue the show route advertising-protocol bgp 172.16.1.2 command.
B) From Spine 1, issue the show route advertising-protocol bgp 172.16.1.1 command. From Spine 1, issue the show route advertising-protocol bgp 172.16.1.1
C) From Spine 1, issue the show route advertising-protocol bgp 172.16.1.2 command.
D) From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command. From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command.
From Spine 1, issue the show route advertising-protocol bgp 172.16.1.2 command.
From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command. From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command.
From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command. From Leaf 1, issue the show route receive-protocol bgp 172.16.1.1 command.
4
Host1 and host2 are connected to an EVPN signaled VXLAN overlay, and must have Layer 3 connectivity. The VNI and VLAN assignments are shown in the exhibit. 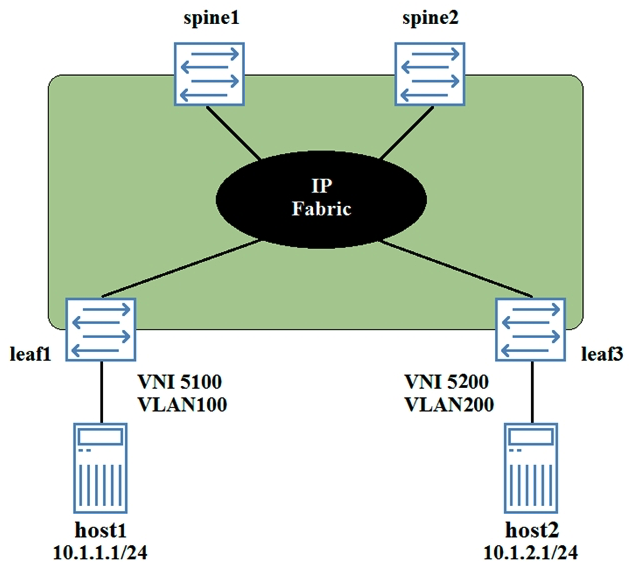 In this scenario, which two statements are true? (Choose two.)
In this scenario, which two statements are true? (Choose two.)
A) The ESI assigned to the host1 link will be different from the ESI assigned to the host2 link.
B) The VNI assigned to the host1 link must be the same as the VNI assigned to the host2 link.
C) A Layer 3 gateway can be configured on the spine devices.
D) A Layer 3 gateway can be configured on the leaf devices.
 In this scenario, which two statements are true? (Choose two.)
In this scenario, which two statements are true? (Choose two.)A) The ESI assigned to the host1 link will be different from the ESI assigned to the host2 link.
B) The VNI assigned to the host1 link must be the same as the VNI assigned to the host2 link.
C) A Layer 3 gateway can be configured on the spine devices.
D) A Layer 3 gateway can be configured on the leaf devices.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
5
What are three advantages of using MPLS for data center interconnects? (Choose three.)
A) dedicated MPLS backbones for Layer 2 and Layer 3 DCIs
B) any-to-any connectivity
C) traffic engineering
D) dedicated connections between customer sites
E) sub 50 ms failover times
A) dedicated MPLS backbones for Layer 2 and Layer 3 DCIs
B) any-to-any connectivity
C) traffic engineering
D) dedicated connections between customer sites
E) sub 50 ms failover times

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
6
Which two statements describe EVPN-based VXLAN implementations? (Choose two.)
A) The movement of a virtual host requires a manual reconfiguration of the VTEP.
B) The movement of a virtual host results in the dynamic remapping of the VTEP.
C) MAC addresses are learned using multicast flooding.
D) MAC addresses are propagated using BGP updates.
A) The movement of a virtual host requires a manual reconfiguration of the VTEP.
B) The movement of a virtual host results in the dynamic remapping of the VTEP.
C) MAC addresses are learned using multicast flooding.
D) MAC addresses are propagated using BGP updates.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
7
You have configured a new MC-LAG connection to a host. After committing the configuration, the MC-LAG link is not functioning properly. 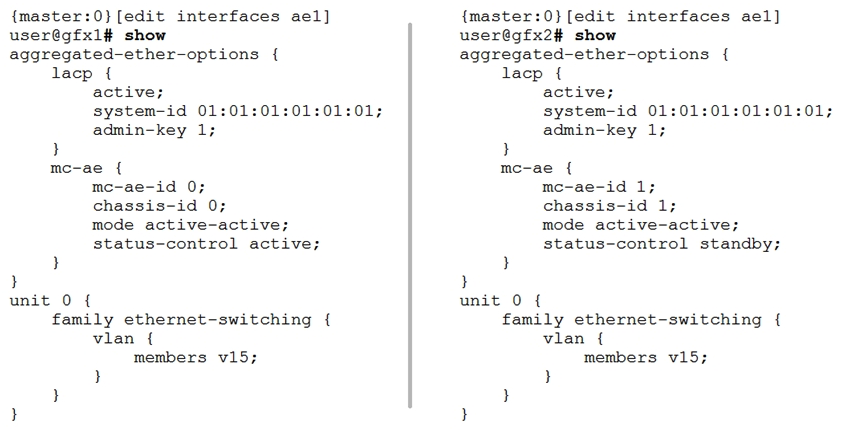 Referring to the exhibit, how would you solve this problem?
Referring to the exhibit, how would you solve this problem?
A) Change the chassis-id on qfx1 to 1. Change the chassis-id on qfx1 to 1.
B) Configure a system-id on qfx1 that is different from the system-id on qfx2. Configure a system-id on qfx1 that is different from the on qfx2.
C) Configure the status-control on qfx2 to active. Configure the status-control on qfx2 to active.
D) Change the mc-ae-id on qfx1 to 1. mc-ae-id
 Referring to the exhibit, how would you solve this problem?
Referring to the exhibit, how would you solve this problem?A) Change the chassis-id on qfx1 to 1. Change the chassis-id on qfx1 to 1.
B) Configure a system-id on qfx1 that is different from the system-id on qfx2. Configure a system-id on qfx1 that is different from the on qfx2.
C) Configure the status-control on qfx2 to active. Configure the status-control on qfx2 to active.
D) Change the mc-ae-id on qfx1 to 1. mc-ae-id

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
8
You are troubleshooting an L3VPN that is part of an EVPN/MPLS DCI. You notice that the EVPN overlay BGP session toward 10.29.50.4 is unable to establish. 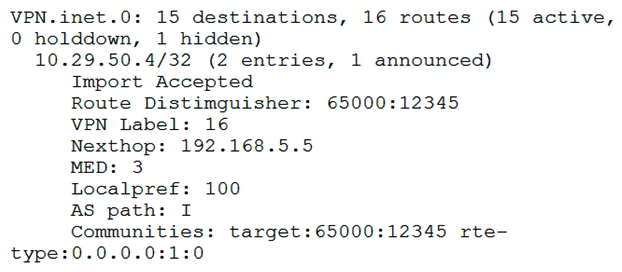 Why is the BGP session failing to establish?
Why is the BGP session failing to establish?
A) The vrf-table-label value is not configured in the remote PE. The vrf-table-label value is not configured in the remote PE.
B) The route-distinguisher value on the local PE is incorrect. route-distinguisher value on the local PE is incorrect.
C) There is no route for 192.168.5.5 in inet.3.
D) There is no route for 192.168.5.5 in VPN.inet.0.
 Why is the BGP session failing to establish?
Why is the BGP session failing to establish?A) The vrf-table-label value is not configured in the remote PE. The vrf-table-label value is not configured in the remote PE.
B) The route-distinguisher value on the local PE is incorrect. route-distinguisher value on the local PE is incorrect.
C) There is no route for 192.168.5.5 in inet.3.
D) There is no route for 192.168.5.5 in VPN.inet.0.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
9
A company wants to expand their hosting business and is seeking solutions to support multiple tenants. Each tenant should be able to configure their own logical interfaces. Also, based on customer needs, all routing features must be supported. What will satisfy the customer's requirements?
A) routing instances
B) tenant systems
C) logical systems
D) bridge domains
A) routing instances
B) tenant systems
C) logical systems
D) bridge domains

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
10
You are asked to manage the oversubscription ratio of your spine and leaf IP fabric. You determine that you are at a 3:1 ratio of downstream to upstream traffic and must achieve a 1:1 ratio. In this scenario, which two actions would you take to achieve this goal? (Choose two.)
A) Increase the number of server-facing ports that each leaf node uses to carry traffic.
B) Reduce the number of server-facing ports that each leaf node uses to carry traffic.
C) Increase the number of spine nodes in your design.
D) Reduce the number of leaf nodes in your design.
A) Increase the number of server-facing ports that each leaf node uses to carry traffic.
B) Reduce the number of server-facing ports that each leaf node uses to carry traffic.
C) Increase the number of spine nodes in your design.
D) Reduce the number of leaf nodes in your design.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
11
You need to add perimeter security to the network shown in the exhibit. All traffic must be inspected for attacks. The edge routers are using all available ports. Your solution must maintain both port and device resiliency. 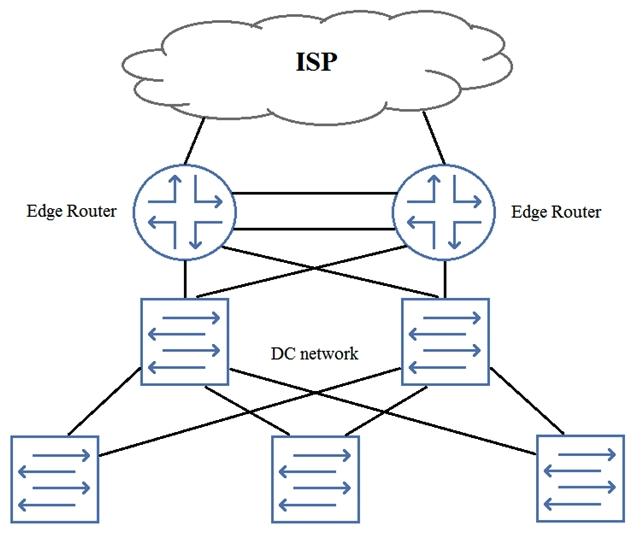 In this scenario, which design would satisfy these requirements?
In this scenario, which design would satisfy these requirements?
A) one-arm SRX Series device using LAG
B) one-arm SRX Series chassis cluster
C) inline SRX Series chassis cluster
D) inline SPX Series device using LAG
 In this scenario, which design would satisfy these requirements?
In this scenario, which design would satisfy these requirements?A) one-arm SRX Series device using LAG
B) one-arm SRX Series chassis cluster
C) inline SRX Series chassis cluster
D) inline SPX Series device using LAG

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
12
Which two statements describe an IP fabric? (Choose two.)
A) Open standards allow for vendor interoperability.
B) Each leaf should have a connection to each spine.
C) xSTP protocols should be used to prevent loops.
D) Traffic should always follow a single path.
A) Open standards allow for vendor interoperability.
B) Each leaf should have a connection to each spine.
C) xSTP protocols should be used to prevent loops.
D) Traffic should always follow a single path.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
13
Referring to the exhibit, not all routes are being exchanged by EBGP peers. 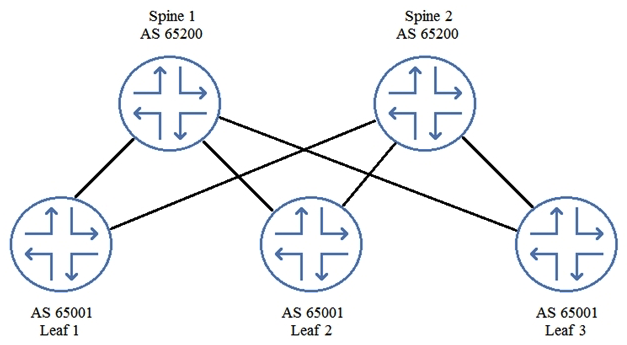 In this scenario, which BGP parameter would solve this problem?
In this scenario, which BGP parameter would solve this problem?
A) multihop
B) multipath
C) multipath multiple-as
D) as-override
 In this scenario, which BGP parameter would solve this problem?
In this scenario, which BGP parameter would solve this problem?A) multihop
B) multipath
C) multipath multiple-as
D) as-override

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
14
What happens when a packet is encapsulated by a VXLAN before being placed in the overlay?
A) The QoS markings are placed in the VXLAN header.
B) The VLAN-ID is placed in the VXLAN header.
C) A VNI that maps to the VLAN-ID is placed in the VXLAN header.
D) The TTL is decremented by two and placed in the VXLAN header.
A) The QoS markings are placed in the VXLAN header.
B) The VLAN-ID is placed in the VXLAN header.
C) A VNI that maps to the VLAN-ID is placed in the VXLAN header.
D) The TTL is decremented by two and placed in the VXLAN header.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
15
Which statement is true about a Data Center Interconnect over an IP network?
A) Layer 2 data must traverse a point-to-point link.
B) Layer 2 data must traverse an MPLS LSP.
C) Layer 2 data must be encapsulated.
D) Layer 3 data must be encapsulated.
A) Layer 2 data must traverse a point-to-point link.
B) Layer 2 data must traverse an MPLS LSP.
C) Layer 2 data must be encapsulated.
D) Layer 3 data must be encapsulated.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
16
Referring to the exhibit, Host 1 and Host 3 have exchanged traffic. 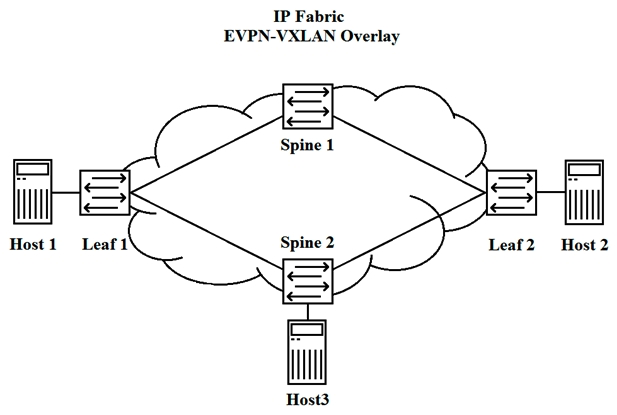 ` In this scenario, which statement is true?
` In this scenario, which statement is true?
A) Leaf 2 does not learn Host 1's MAC address until Host 1 and Host 2 send traffic to each other.
B) Leaf 2 learns Host 1's MAC address through periodic updates from Spine 2.
C) Leaf 2 learns Host 1's MAC address when Host 3 learns Host 1's MAC address.
D) Leaf 2 learns Host 1's MAC address when Leaf 1 queries Host 1.
 ` In this scenario, which statement is true?
` In this scenario, which statement is true?A) Leaf 2 does not learn Host 1's MAC address until Host 1 and Host 2 send traffic to each other.
B) Leaf 2 learns Host 1's MAC address through periodic updates from Spine 2.
C) Leaf 2 learns Host 1's MAC address when Host 3 learns Host 1's MAC address.
D) Leaf 2 learns Host 1's MAC address when Leaf 1 queries Host 1.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
17
After configuring an IP fabric using EBGP as your routing protocol, you notice that not all of the routes are showing up in the routing tables. You have verified that all adjacencies have formed, and that all policies are in place and configured properly. In this scenario, which statement is true?
A) The routers have not been configured with the multipath multiple-as parameter. The routers have not been configured with the multipath multiple-as parameter.
B) The routers have not been configured using the add-path parameter. The routers have not been configured using the add-path
C) The routers have not been configured using the bfd-liveness-detection parameter. bfd-liveness-detection
D) The routers have not been configured using the multihop parameter. multihop
A) The routers have not been configured with the multipath multiple-as parameter. The routers have not been configured with the multipath multiple-as parameter.
B) The routers have not been configured using the add-path parameter. The routers have not been configured using the add-path
C) The routers have not been configured using the bfd-liveness-detection parameter. bfd-liveness-detection
D) The routers have not been configured using the multihop parameter. multihop

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
18
You are configuring an IP Fabric in your data center and you are trying to load-balance traffic across multiple equal-cost BGP routes. You have enabled multipath, but the traffic is not being load-balanced. 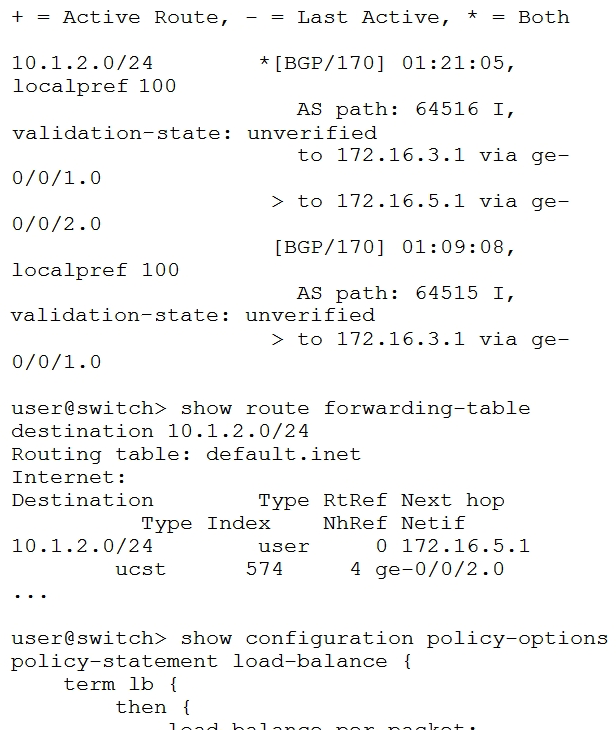 Referring to the exhibit, what will solve this problem?
Referring to the exhibit, what will solve this problem?
A) You should apply the load-balance policy as an import policy to the forwarding table. You should apply the load-balance policy as an import policy to the forwarding table.
B) You should apply the load-balance policy as an import policy for the BGP neighbor. policy as an import policy for the BGP neighbor.
C) You should apply the load-balance policy as an export policy to the forwarding table. policy as an export policy to the forwarding table.
D) You should apply the load-balance policy as an export policy to the BGP neighbor. policy as an export policy to the BGP neighbor.
 Referring to the exhibit, what will solve this problem?
Referring to the exhibit, what will solve this problem?A) You should apply the load-balance policy as an import policy to the forwarding table. You should apply the load-balance policy as an import policy to the forwarding table.
B) You should apply the load-balance policy as an import policy for the BGP neighbor. policy as an import policy for the BGP neighbor.
C) You should apply the load-balance policy as an export policy to the forwarding table. policy as an export policy to the forwarding table.
D) You should apply the load-balance policy as an export policy to the BGP neighbor. policy as an export policy to the BGP neighbor.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
19
Which two statements define the use of route targets and route distinguishers in an EVPN? (Choose two.)
A) Route targets ensure that routes from different clients remain unique within the data center domain.
B) Route targets identify the VRF into which the route should be placed.
C) Route distinguishers ensure that routes from different clients remain unique within the data center domain.
D) Route distinguishers identify the VRF into which the route should be placed.
A) Route targets ensure that routes from different clients remain unique within the data center domain.
B) Route targets identify the VRF into which the route should be placed.
C) Route distinguishers ensure that routes from different clients remain unique within the data center domain.
D) Route distinguishers identify the VRF into which the route should be placed.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
20
You are designing a network for a small data center. In this scenario, which underlay protocol allows for the simplest implementation?
A) OSPF
B) IBGP
C) EBGP
D) MPLS
A) OSPF
B) IBGP
C) EBGP
D) MPLS

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
21
Which protocol is used between VCF member devices to create a loop-free topology?
A) LLDP
B) MSTP
C) RSTP
D) VCCP
A) LLDP
B) MSTP
C) RSTP
D) VCCP

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
22
You are asked to configure VXLAN for your data center using multicast to exchange VTEP information. In this scenario, which two configuration parameters must match on the VTEPs in the same VXLAN segment? (Choose two.)
A) multicast group
B) VLAN ID
C) routing instance name
D) VNI
A) multicast group
B) VLAN ID
C) routing instance name
D) VNI

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
23
Which two statements are true about Virtual Chassis? (Choose two.)
A) The request virtual-chassis mode fabric reboot command will set the Virtual Chassis to fabric mode with similar devices. The request virtual-chassis mode fabric reboot command will set the Virtual Chassis to fabric mode with similar devices.
B) The request virtual-chassis mode fabric reboot command will set the Virtual Chassis to mixed mode. command will set the Virtual Chassis to mixed mode.
C) By default, Junos switches are in a non-mixed mode Virtual Chassis.
D) By default, Junos switches are in mixed mode Virtual Chassis.
A) The request virtual-chassis mode fabric reboot command will set the Virtual Chassis to fabric mode with similar devices. The request virtual-chassis mode fabric reboot command will set the Virtual Chassis to fabric mode with similar devices.
B) The request virtual-chassis mode fabric reboot command will set the Virtual Chassis to mixed mode. command will set the Virtual Chassis to mixed mode.
C) By default, Junos switches are in a non-mixed mode Virtual Chassis.
D) By default, Junos switches are in mixed mode Virtual Chassis.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
24
What are two methods used to scale an IBGP IP Fabric? (Choose two.)
A) spanning tree
B) redundant trunk groups
C) route reflection
D) confederations
A) spanning tree
B) redundant trunk groups
C) route reflection
D) confederations

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
25
Your manager asks you to secure ARP and DHCP traffic across your local Ethernet links. In this scenario, which technology will accomplish this task?
A) SSL
B) a firewall filter
C) IPsec
D) MACsec
A) SSL
B) a firewall filter
C) IPsec
D) MACsec

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
26
You have configured MP-IBGP to support EVPN for your overlay network. However, you are not seeing the expected routes on your edge devices. 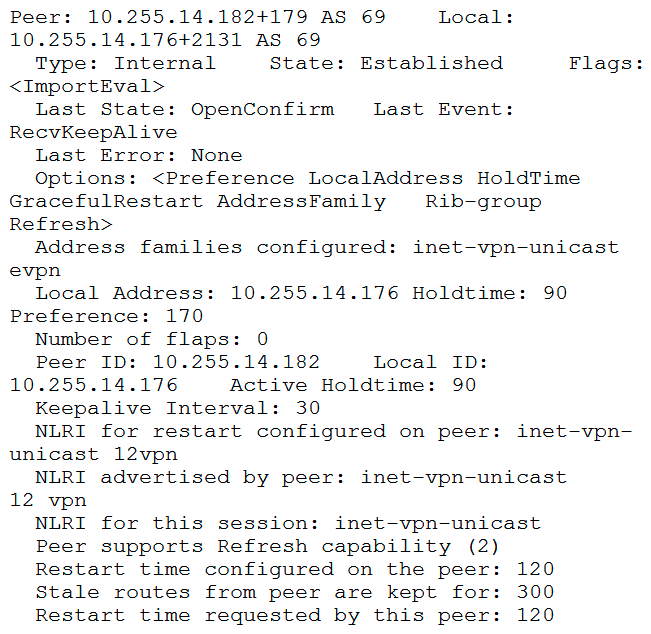 Referring to the exhibit, how would you solve this problem?
Referring to the exhibit, how would you solve this problem?
A) The family evpn signaling parameter must be configured on the remote peer. The family evpn signaling parameter must be configured on the remote peer.
B) Graceful restart must be disabled for this session.
C) The group types on both devices should be set to external . The group types on both devices should be set to external .
D) The family 12vpn signaling must be configured on the local peer. The family 12vpn signaling must be configured on the local peer.
 Referring to the exhibit, how would you solve this problem?
Referring to the exhibit, how would you solve this problem?A) The family evpn signaling parameter must be configured on the remote peer. The family evpn signaling parameter must be configured on the remote peer.
B) Graceful restart must be disabled for this session.
C) The group types on both devices should be set to external . The group types on both devices should be set to external .
D) The family 12vpn signaling must be configured on the local peer. The family 12vpn signaling must be configured on the local peer.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
27
What are two valid types of VXLAN signaling? (Choose two.)
A) EVPN
B) RSVP
C) RSTP
D) MPLS
A) EVPN
B) RSVP
C) RSTP
D) MPLS

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
28
You want to ensure high availability of the Junos devices in your data center. In this scenario, which three features would accomplish this task? (Choose three.)
A) Virtual Router Redundancy Protocol
B) Multiple Spanning Tree Protocol
C) dual Routing Engines
D) virtual private LAN service
E) graceful Routing Engine switchover
A) Virtual Router Redundancy Protocol
B) Multiple Spanning Tree Protocol
C) dual Routing Engines
D) virtual private LAN service
E) graceful Routing Engine switchover

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
29
A VXLAN has been created between devices leaf1 and leaf3. 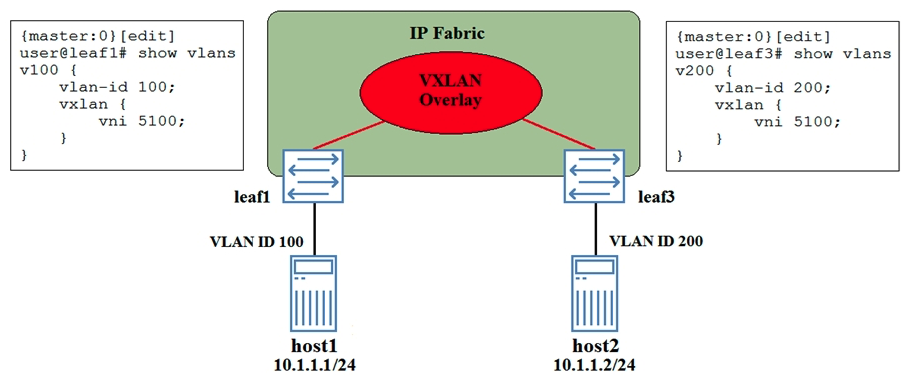 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
A) Traffic sent from host1 to host2 will be tagged with VLAN ID 200 when exiting leaf3.
B) Traffic sent from leaf1 to host2 will he dropped on leaf1.
C) Traffic sent from host1 to host2 will be tagged with VLAN ID 100 when exiting leaf3.
D) Traffic sent from leaf1 to host2 will he dropped on leaf3.
 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?A) Traffic sent from host1 to host2 will be tagged with VLAN ID 200 when exiting leaf3.
B) Traffic sent from leaf1 to host2 will he dropped on leaf1.
C) Traffic sent from host1 to host2 will be tagged with VLAN ID 100 when exiting leaf3.
D) Traffic sent from leaf1 to host2 will he dropped on leaf3.

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck
30
You have a site with thousands of MAC addresses multihomed to two leaf nodes in an EVPN VXLAN. In this scenario, which EVPN feature provides fast network convergence in the event of a leaf node link failure?
A) BGP Additional Paths
B) Bidirectional Forwarding Detection
C) Ethernet Autodiscovery
D) Fast reroute
A) BGP Additional Paths
B) Bidirectional Forwarding Detection
C) Ethernet Autodiscovery
D) Fast reroute

Unlock Deck
Unlock for access to all 30 flashcards in this deck.
Unlock Deck
k this deck


