Deck 2: Data Center Design, Specialist (JNCDS-DC)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/74
Play
Full screen (f)
Deck 2: Data Center Design, Specialist (JNCDS-DC)
1
Your data center uses a Virtual Chassis Fabric. The ToR switches have 48 ports and each rack supports 20 servers. Each server has two ports that are configured as a LAG. You need to implement link level redundancy but you cannot use two ports on the same device for this redundancy. Which type of connection should you use to complete this task?
A) MC-LAG
B) RTG
C) LAG
D) ESI
A) MC-LAG
B) RTG
C) LAG
D) ESI
LAG
2
You are designing a Layer 2 fabric implementation for a small data center and have chosen to implement a Virtual Chassis Fabric. You must accommodate two racks of servers with 1 Gbps connectivity, 10 racks of servers with 10 Gbps connectivity, and maintain a single management interface. Which device would satisfy the requirements in this implementation?
A) QFX5110
B) QFX10002
C) EX4600
D) EX4300
A) QFX5110
B) QFX10002
C) EX4600
D) EX4300
QFX5110
3
Click the Exhibit button. Traffic congestion is noticed when sending traffic from S1 to S2. You must design a CoS deployment to address the traffic congestion issue. Referring to the exhibit, which two statements are true? (Choose two.) 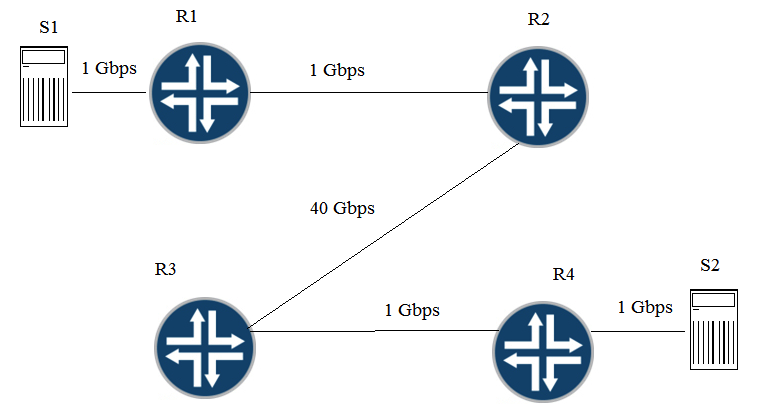
A) You should use BA classifiers on R1.
B) You should use multifield classifiers on R2, R3, and R4.
C) You should use multifield classifiers on R1.
D) You should use BA classifiers on R2, R3, and R4.

A) You should use BA classifiers on R1.
B) You should use multifield classifiers on R2, R3, and R4.
C) You should use multifield classifiers on R1.
D) You should use BA classifiers on R2, R3, and R4.
You should use BA classifiers on R1.
You should use multifield classifiers on R2, R3, and R4.
You should use multifield classifiers on R2, R3, and R4.
4
Which two statements about data center design are correct? (Choose two.)
A) The most efficient traffic flow pattern is 50% east-west and 50% north-south.
B) A data center that provides hosted services should scale based on customer demands.
C) A multitier design provides better performance as the number of applications increase.
D) An application may query several resources in response to a single user request.
A) The most efficient traffic flow pattern is 50% east-west and 50% north-south.
B) A data center that provides hosted services should scale based on customer demands.
C) A multitier design provides better performance as the number of applications increase.
D) An application may query several resources in response to a single user request.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
5
Click the Exhibit button. Referring to the exhibit, you want the vSRX device to inspect inter-VM traffic. Which two actions must you take to accomplish this task? (Choose two.) 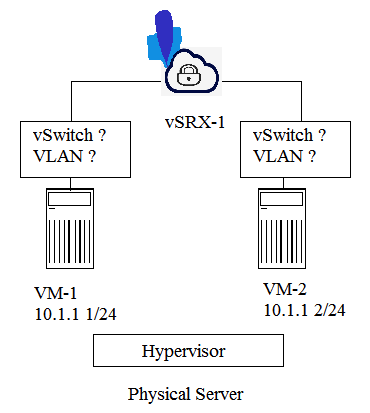
A) You must put the connections between the VMs and the vSRX device in separate VLANs.
B) You must put the connections between the VMs and the vSRX device in separate vSwitches.
C) You must put the connection between the VMs and the vSRX device in the same VLAN.
D) You must put the connection between the VMs and the vSRX device in the same vSwitch.

A) You must put the connections between the VMs and the vSRX device in separate VLANs.
B) You must put the connections between the VMs and the vSRX device in separate vSwitches.
C) You must put the connection between the VMs and the vSRX device in the same VLAN.
D) You must put the connection between the VMs and the vSRX device in the same vSwitch.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
6
You are implementing a new financial application in your data center. You must ensure Web traffic to this server is secure. Which Junos feature would you use to accomplish this task?
A) graceful restart
B) antispam
C) AppSecure
D) Virtual Chassis
A) graceful restart
B) antispam
C) AppSecure
D) Virtual Chassis

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
7
Click the Exhibit button. You are creating a resilient IP fabric for a data center based on a Clos architecture. Referring to the exhibit, which statement is true? 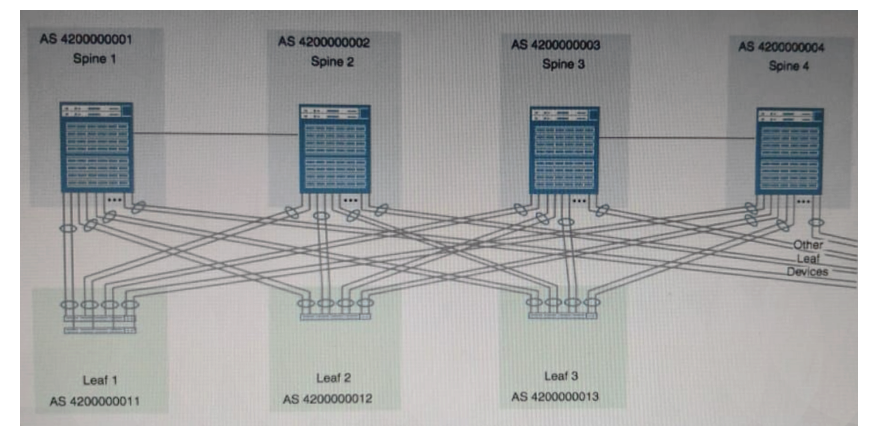
A) A physical link must be added between spine 2 and spine 3 and between spine 1 and spine 4.
B) Additional physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be added for resiliency.
C) No physical links need to be added or removed.
D) The physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be removed.

A) A physical link must be added between spine 2 and spine 3 and between spine 1 and spine 4.
B) Additional physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be added for resiliency.
C) No physical links need to be added or removed.
D) The physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be removed.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
8
You are designing an IP fabric using EBGP. In this scenario, what are two ways of designing the ASN scheme for the IP fabric? (Choose two.)
A) Assign the same ASN to all devices.
B) Assign the ASN to all leaf devices and a separate ASN to all spine devices.
C) Assign a unique ASN to each individual device.
D) Assign the same ASN used by the WAN service provider to the spine devices.
A) Assign the same ASN to all devices.
B) Assign the ASN to all leaf devices and a separate ASN to all spine devices.
C) Assign a unique ASN to each individual device.
D) Assign the same ASN used by the WAN service provider to the spine devices.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
9
What are two methods used to protect the data center perimeter? (Choose two.)
A) session authentication
B) DDoS protection
C) asset classification
D) network subnetting
A) session authentication
B) DDoS protection
C) asset classification
D) network subnetting

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
10
A customer asks you if they should implement nonstop active routing (NSR) in some cases to replace graceful restart in their data center. In this scenario, which two statements are true? (Choose two.)
A) NSR saves routing protocol information by running the routing protocol process (rpd) on the backup Routing Engine.
B) NSR is self-contained and does not rely on helper routers (or switches) to assist the routing platform in restoring routing protocol information.
C) NSR accounts for large and small traffic flows to ensure coherent forwarding path selection during failover.
D) NSR delivers TCP/UDP stream status reducing control plane stress for other networking devices through concatenated announcements from the routing protocol process (rpd)
A) NSR saves routing protocol information by running the routing protocol process (rpd) on the backup Routing Engine.
B) NSR is self-contained and does not rely on helper routers (or switches) to assist the routing platform in restoring routing protocol information.
C) NSR accounts for large and small traffic flows to ensure coherent forwarding path selection during failover.
D) NSR delivers TCP/UDP stream status reducing control plane stress for other networking devices through concatenated announcements from the routing protocol process (rpd)

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
11
You plan to deploy a set of SRX Series devices in an active/active chassis cluster with an active/active network infrastructure. Which two statements are true in this scenario? (Choose two.)
A) This deployment scenario is recommended when firewall services are used extensively for east-west traffic.
B) End-host traffic is services through one SRX node during non-failure conditions.
C) This deployment scenario is recommended when firewall services are used extensively for north-south traffic.
D) End-host traffic is serviced through both SRX nodes during non-failure conditions.
A) This deployment scenario is recommended when firewall services are used extensively for east-west traffic.
B) End-host traffic is services through one SRX node during non-failure conditions.
C) This deployment scenario is recommended when firewall services are used extensively for north-south traffic.
D) End-host traffic is serviced through both SRX nodes during non-failure conditions.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
12
Click the Exhibit button. You are designing a Layer 2 Ethernet fabric. Your customer wants to know which protocol in your design will ensure a loop-free topology. Referring to the exhibit, which protocol meets this requirement? 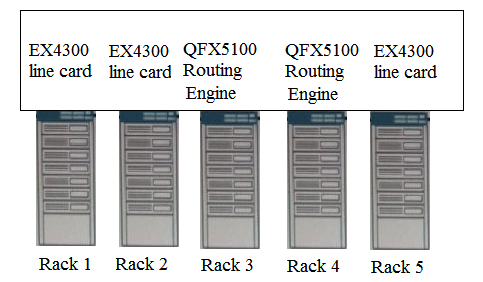
A) STP
B) VCCP
C) BGP
D) EVPN

A) STP
B) VCCP
C) BGP
D) EVPN

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
13
Clos architectures are based on which network topology?
A) ring
B) VLANs
C) hybrid
D) spine and leaf
A) ring
B) VLANs
C) hybrid
D) spine and leaf

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
14
You need a security management solution for your data center that will support centralized network visibility and control, J-Flow collection from existing perimeter devices, and SIEM. In this scenario, which two products should you choose for your data center design? (Choose two.)
A) vSRX
B) Security Director
C) JSA
D) Sky ATP
A) vSRX
B) Security Director
C) JSA
D) Sky ATP

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
15
A large multinational corporation wants to implement SDN for rapid deployment of application environments. You are asked to define SDN service chaining for a presentation to execute management. In this scenario, which statement would satisfy the requirement?
A) Integrated software is used to insert a software widget into the flow of network traffic.
B) Stacked hardware is used to insert a software widget into the flow of network traffic.
C) Software is used to virtually insert services into the flow of network traffic.
D) Hardware is used to virtually insert services into the flow of network traffic.
A) Integrated software is used to insert a software widget into the flow of network traffic.
B) Stacked hardware is used to insert a software widget into the flow of network traffic.
C) Software is used to virtually insert services into the flow of network traffic.
D) Hardware is used to virtually insert services into the flow of network traffic.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
16
Which Junos NFV device is used to provide security in virtualized environments?
A) TCX1000
B) SSG20
C) IC6500
D) vSRX
A) TCX1000
B) SSG20
C) IC6500
D) vSRX

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
17
You have included in your data center design an SRX1500 chassis cluster. The RFP requires a documented upgrade process for the cluster that minimizes downtime. What satisfies this requirement in this scenario?
A) an in-service software upgrade
B) a topology-independent in-service software upgrade
C) a manual device upgrade
D) a nonstop software upgrade
A) an in-service software upgrade
B) a topology-independent in-service software upgrade
C) a manual device upgrade
D) a nonstop software upgrade

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
18
What are two requirements for a VXLAN tunnel endpoint (VTEP)? (Choose two.)
A) TCP session tracking
B) MAC address learning
C) IGMP filtering
D) IP address learning of interested VTEPs
A) TCP session tracking
B) MAC address learning
C) IGMP filtering
D) IP address learning of interested VTEPs

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
19
You are designing a DCI strategy. You must provide a solution that meets the requirements shown below: -sub 50 ms failover to alternate path -supports L2 and L3 VPNs -supports traffic engineered paths Which technology would satisfy the requirements?
A) MPLS
B) GRE
C) BGP
D) IPsec
A) MPLS
B) GRE
C) BGP
D) IPsec

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
20
Which two statements are correct about current data center designs? (Choose two.)
A) Network functions are being virtualized.
B) Public IP addresses are easy to obtain but not manage.
C) There is a proliferation of distributed applications.
D) There is a proliferation of monolithic applications.
A) Network functions are being virtualized.
B) Public IP addresses are easy to obtain but not manage.
C) There is a proliferation of distributed applications.
D) There is a proliferation of monolithic applications.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
21
You want to provide Layer 2 connectivity to a backup data center or to a disaster recovery site. What would you use to accomplish this task?
A) Data Center Interconnect
B) network redundancy
C) SDN
D) SAN protocols
A) Data Center Interconnect
B) network redundancy
C) SDN
D) SAN protocols

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
22
A customer is using EVPN to maximize their Data Center Interconnect and provide a stretched Layer 2 network to support VM mobility. What are two benefits in this scenario? (Choose two.)
A) Load balancing is used across the WAN per flow
B) Layer 2 MAC tables are populated using the control plane
C) Load balancing is used across the WAN per packet
D) Layer 2 MAC tables are populated using the data plane
A) Load balancing is used across the WAN per flow
B) Layer 2 MAC tables are populated using the control plane
C) Load balancing is used across the WAN per packet
D) Layer 2 MAC tables are populated using the data plane

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
23
Your company is deploying a private cloud based on OpenStack and has selected Contrail Networking as their SDN controller. Which statement is true in this scenario?
A) All bare-metal servers must run a vSRX instance for overlay tunneling.
B) All virtualized servers must run a vSRX instance for overlay tunneling
C) All bare-metal serer must run a vRouter for overlay tunneling
D) All virtualized servers must run a vRouter for overlay tunneling
A) All bare-metal servers must run a vSRX instance for overlay tunneling.
B) All virtualized servers must run a vSRX instance for overlay tunneling
C) All bare-metal serer must run a vRouter for overlay tunneling
D) All virtualized servers must run a vRouter for overlay tunneling

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
24
You are designing an IP fabric using EVPN with VXLAN and must ensure that all links between the leaf and spine nodes are used as efficiently as possible. Which two design considerations are important to achieve this task? (Choose two.)
A) Load balancing is automatic in an IP fabric design.
B) Load balancing must be managed by an SDN controller in an IP fabric design.
C) The overlay network needs to support load balancing.
D) The underlay network needs to support load balancing.
A) Load balancing is automatic in an IP fabric design.
B) Load balancing must be managed by an SDN controller in an IP fabric design.
C) The overlay network needs to support load balancing.
D) The underlay network needs to support load balancing.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
25
How many inches does one RU equal?
A) 1.000
B) 1.251
C) 1.527
D) 1.752
A) 1.000
B) 1.251
C) 1.527
D) 1.752

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
26
Which devices are recommended by Juniper Networks as edge routers in a data center?
A) EX Series
B) QFX Series
C) MX Series
D) CTP Series
A) EX Series
B) QFX Series
C) MX Series
D) CTP Series

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
27
Which two security components are inherent in a Contrail vRouter? (Choose two.)
A) basic tenant separation directional control for Layer 3 and Layer 4 traffic
B) Layer 7 traffic filters
C) security groups
D) encapsulation around each VM residing on the compute node
A) basic tenant separation directional control for Layer 3 and Layer 4 traffic
B) Layer 7 traffic filters
C) security groups
D) encapsulation around each VM residing on the compute node

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
28
You are designing an IP fabric using IBGP as your underlay. In this scenario, which statement is correct?
A) Confederations are not allowed in an IBGP IP traffic.
B) Route reflectors should be implemented on your spine devices.
C) IBGP ensures that traffic will be load balanced by default.
D) You must ensure that you have a full mesh with all devices.
A) Confederations are not allowed in an IBGP IP traffic.
B) Route reflectors should be implemented on your spine devices.
C) IBGP ensures that traffic will be load balanced by default.
D) You must ensure that you have a full mesh with all devices.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
29
Which two statements describe the Contrail vRouter? (Choose two.)
A) It is forwarding plane that runs software on a virtualized server.
B) It extends the network form physical routers and switches into an overlay network hosted in virtual server.
C) It is responsible for providing the management, control, and analytics functions of the virtualized network.
D) It provides the logically centralized control plane and management plane of the system.
A) It is forwarding plane that runs software on a virtualized server.
B) It extends the network form physical routers and switches into an overlay network hosted in virtual server.
C) It is responsible for providing the management, control, and analytics functions of the virtualized network.
D) It provides the logically centralized control plane and management plane of the system.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
30
You are designing a Control-based SDN overlay network. IP filtering and tenant separation for Layer 3 and Layer 4 traffic is required for this installation. In this scenario, which Contrail component performs this function?
A) vSwitch
B) control node
C) vRouter
D) compute node
A) vSwitch
B) control node
C) vRouter
D) compute node

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
31
Which protocol is used on the VPCs of a Virtual Chassis Fabric?
A) IEEE 802.1BR
B) MPLS
C) VCCP
D) IS-IS
A) IEEE 802.1BR
B) MPLS
C) VCCP
D) IS-IS

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
32
Two data centers need to be connected for application and server mobility. An MPLS pseudowire is going to facilitate the necessary connectivity. This pseudowire will extend between which two types of network devices?
A) PE to CE
B) PE to P
C) PE to PE
D) CE to CE
A) PE to CE
B) PE to P
C) PE to PE
D) CE to CE

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
33
You are seeking a server-virtualization security solution that is lightweight and will protect virtual machines from a variety of threats. Which platform should you choose in this scenario?
A) vSRX
B) vRR
C) vEPC
D) TCX
A) vSRX
B) vRR
C) vEPC
D) TCX

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
34
A customer has selected QFX5110 switches. The initial installation will contain two switches located in racks about two meters apart. What is the most cost-effective way to interconnect these switches?
A) Use SMF between the racks and interconnect the switches with LX4 transceivers.
B) Use a Virtual Chassis cable between the VCP cards.
C) Use MMF between the racks and interconnect the switches with SR4 transceivers.
D) Use a three-meter passive DAC cable between the racks and interconnect the switches with it.
A) Use SMF between the racks and interconnect the switches with LX4 transceivers.
B) Use a Virtual Chassis cable between the VCP cards.
C) Use MMF between the racks and interconnect the switches with SR4 transceivers.
D) Use a three-meter passive DAC cable between the racks and interconnect the switches with it.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
35
You are designing a data center network with a combination of KVM virtual machines and physical QFX Series devices. You require a single Juniper Networks solution for monitoring resource utilization across all devices. In this scenario, which product would satisfy this requirement?
A) AppFormix
B) Contrail
C) JTI
D) Junos Space
A) AppFormix
B) Contrail
C) JTI
D) Junos Space

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
36
Your SAN team must transmit FC between multiple locations in a data center. To keep the cost of the project to a minimum, your management decides that using FCoE would be the most cost-effective approach. In this scenario, which architecture will support FCoE losslessly?
A) Layer 3 Clos
B) Virtual Chassis
C) Virtual Chassis Fabric
D) VXLAN overlay
A) Layer 3 Clos
B) Virtual Chassis
C) Virtual Chassis Fabric
D) VXLAN overlay

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
37
You are designing a Junos-based Ethernet Fabric for a data center that has a combination of 60 EX Series and QFX Series devices. In this scenario, which solution would you choose?
A) Junos Fusion Provider Edge
B) Virtual Chassis
C) Junos Fusion Data Center
D) Virtual Chassis Fabric
A) Junos Fusion Provider Edge
B) Virtual Chassis
C) Junos Fusion Data Center
D) Virtual Chassis Fabric

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
38
Click the Exhibit button. Referring to the exhibit, what must you change to make the topology a supported Virtual Chassis Fabric design? 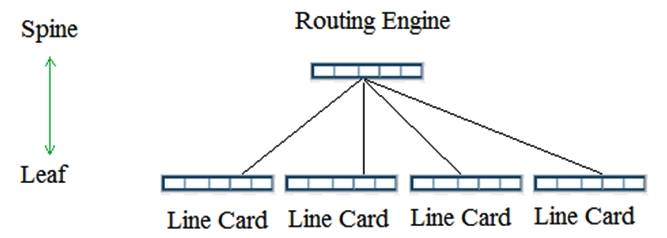
A) Change the Routing Engine to a line card.
B) Remove one leaf node.
C) Add a second spine node.
D) Change one of the line cards to a VCP master instance.

A) Change the Routing Engine to a line card.
B) Remove one leaf node.
C) Add a second spine node.
D) Change one of the line cards to a VCP master instance.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
39
Which two statements are correct about a VCF deployment? (Choose two.)
A) You are allowed up to four spine devices.
B) The fabric is managed as a single logical device.
C) An EX4300 switch must be deployed as a spine device.
D) You must deploy a QFX5100 as a leaf device.
A) You are allowed up to four spine devices.
B) The fabric is managed as a single logical device.
C) An EX4300 switch must be deployed as a spine device.
D) You must deploy a QFX5100 as a leaf device.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
40
You are re-designing a traditional multitiered data center into a modern spine-and-leaf data center architecture. In this scenario, which two tiers are collapsed? (Choose two.)
A) distribution
B) WAN
C) access
D) core
A) distribution
B) WAN
C) access
D) core

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
41
Clos architectures are based on which network topology?
A) ring
B) VLANs
C) hybrid
D) spine and leaf
A) ring
B) VLANs
C) hybrid
D) spine and leaf

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
42
What are two methods used to protect the data center perimeter? (Choose two.)
A) session authentication
B) DDoS protection
C) asset classification
D) network subnetting
A) session authentication
B) DDoS protection
C) asset classification
D) network subnetting

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
43
Click the Exhibit button. Referring to the exhibit, you want the vSRX device to inspect inter-VM traffic. Which two actions must you take to accomplish this task? (Choose two.) 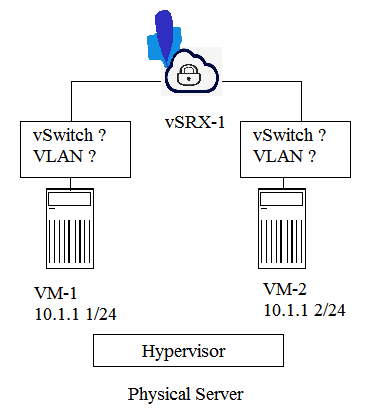
A) You must put the connections between the VMs and the vSRX device in separate VLANs.
B) You must put the connections between the VMs and the vSRX device in separate vSwitches.
C) You must put the connection between the VMs and the vSRX device in the same VLAN.
D) You must put the connection between the VMs and the vSRX device in the same vSwitch.

A) You must put the connections between the VMs and the vSRX device in separate VLANs.
B) You must put the connections between the VMs and the vSRX device in separate vSwitches.
C) You must put the connection between the VMs and the vSRX device in the same VLAN.
D) You must put the connection between the VMs and the vSRX device in the same vSwitch.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
44
Click the Exhibit button. Traffic congestion is noticed when sending traffic from S1 to S2. You must design a CoS deployment to address the traffic congestion issue. Referring to the exhibit, which two statements are true? (Choose two.) 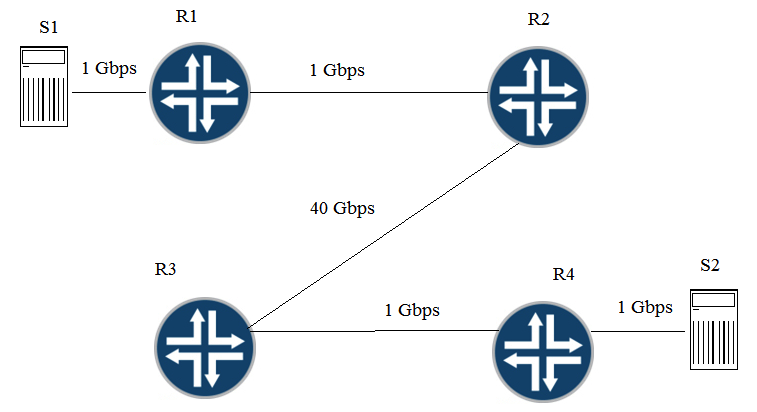
A) You should use BA classifiers on R1.
B) You should use multifield classifiers on R2, R3, and R4.
C) You should use multifield classifiers on R1.
D) You should use BA classifiers on R2, R3, and R4.

A) You should use BA classifiers on R1.
B) You should use multifield classifiers on R2, R3, and R4.
C) You should use multifield classifiers on R1.
D) You should use BA classifiers on R2, R3, and R4.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
45
A large multinational corporation wants to implement SDN for rapid deployment of application environments. You are asked to define SDN service chaining for a presentation to execute management. In this scenario, which statement would satisfy the requirement?
A) Integrated software is used to insert a software widget into the flow of network traffic.
B) Stacked hardware is used to insert a software widget into the flow of network traffic.
C) Software is used to virtually insert services into the flow of network traffic.
D) Hardware is used to virtually insert services into the flow of network traffic.
A) Integrated software is used to insert a software widget into the flow of network traffic.
B) Stacked hardware is used to insert a software widget into the flow of network traffic.
C) Software is used to virtually insert services into the flow of network traffic.
D) Hardware is used to virtually insert services into the flow of network traffic.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
46
Which two statements are correct about current data center designs? (Choose two.)
A) Network functions are being virtualized.
B) Public IP addresses are easy to obtain but not manage.
C) There is a proliferation of distributed applications.
D) There is a proliferation of monolithic applications.
A) Network functions are being virtualized.
B) Public IP addresses are easy to obtain but not manage.
C) There is a proliferation of distributed applications.
D) There is a proliferation of monolithic applications.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
47
Your data center uses an Ethernet fabric solution for the infrastructure switches. You must design a redundancy solution that addresses how the servers connect to the members of the Ethernet fabric. Which two statements are true in this scenario? (Choose two.)
A) It is necessary to use MC-LAG.
B) You should connect each server to one member with a two-interface LAG.
C) You should connect each server to two different members.
D) It is not necessary to use MC-LAG.
A) It is necessary to use MC-LAG.
B) You should connect each server to one member with a two-interface LAG.
C) You should connect each server to two different members.
D) It is not necessary to use MC-LAG.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
48
Which statement is true about highly available data center architectures?
A) All data center devices require the same level of uptime.
B) They require the use of a services block for non switching/routing devices.
C) They are never segmented into zones or PoDs.
D) During a failure, a data center should gracefully degrade.
A) All data center devices require the same level of uptime.
B) They require the use of a services block for non switching/routing devices.
C) They are never segmented into zones or PoDs.
D) During a failure, a data center should gracefully degrade.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
49
What are two requirements for a VXLAN tunnel endpoint (VTEP)? (Choose two.)
A) TCP session tracking
B) MAC address learning
C) IGMP filtering
D) IP address learning of interested VTEPs
A) TCP session tracking
B) MAC address learning
C) IGMP filtering
D) IP address learning of interested VTEPs

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
50
Which two statements are true about IP fabrics? (Choose two.)
A) IP-based applications do not require an overlay network to maintain connectivity.
B) Applications that require security needs an overlay to provide the security.
C) Applications that require Layer 2 adjacencies require an overlay network to maintain connectivity.
D) IP fabrics can natively support both Layer 2 and Layer 3 applications.
A) IP-based applications do not require an overlay network to maintain connectivity.
B) Applications that require security needs an overlay to provide the security.
C) Applications that require Layer 2 adjacencies require an overlay network to maintain connectivity.
D) IP fabrics can natively support both Layer 2 and Layer 3 applications.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
51
Click the Exhibit button. You are creating a resilient IP fabric for a data center based on a Clos architecture. Referring to the exhibit, which statement is true? 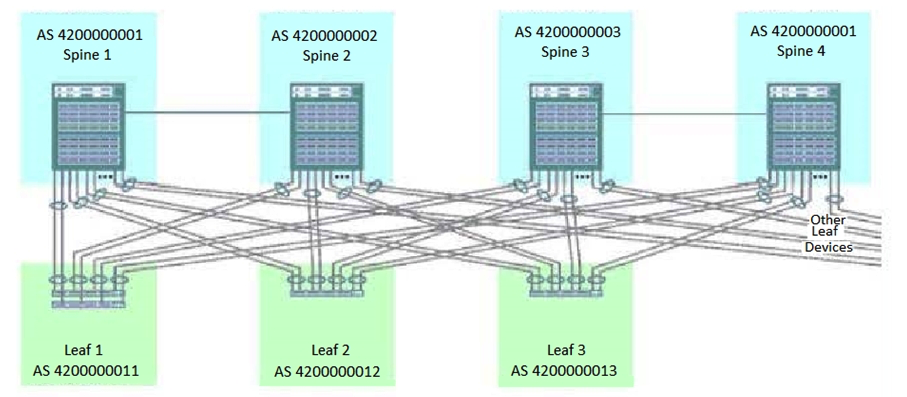
A) A physical link must be added between spine 2 and spine 3 and between spine 1 and spine 4.
B) Additional physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be added for resiliency.
C) No physical links need to be added or removed.
D) The physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be removed.

A) A physical link must be added between spine 2 and spine 3 and between spine 1 and spine 4.
B) Additional physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be added for resiliency.
C) No physical links need to be added or removed.
D) The physical links between spine 1 and spine 2 and between spine 3 and spine 4 must be removed.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
52
You are designing a Layer 2 fabric implementation for a small data center and have chosen to implement a Virtual Chassis Fabric. You must accommodate two racks of servers with 1 Gbps connectivity, 10 racks of servers with 10 Gbps connectivity, and maintain a single management interface. Which device would satisfy the requirements in this implementation?
A) QFX5110
B) QFX10002
C) EX4600
D) EX4300
A) QFX5110
B) QFX10002
C) EX4600
D) EX4300

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
53
You plan to deploy a set of SRX Series devices in an active/passive chassis cluster with an active/passive network infrastructure. Which two statements are true in this scenario? (Choose two.)
A) End-host traffic is serviced through both SRX nodes during non-failure conditions.
B) End-host traffic is serviced through one SRX node during non-failure conditions.
C) In non-failure conditions, the end-host traffic across the fabric link is present.
D) In non-failure conditions, the end-host traffic across the fabric link is eliminated.
A) End-host traffic is serviced through both SRX nodes during non-failure conditions.
B) End-host traffic is serviced through one SRX node during non-failure conditions.
C) In non-failure conditions, the end-host traffic across the fabric link is present.
D) In non-failure conditions, the end-host traffic across the fabric link is eliminated.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
54
You have included in your data center design an SRX1500 chassis cluster. The RFP requires a documented upgrade process for the cluster that minimizes downtime. What satisfies this requirement in this scenario?
A) an in-service software upgrade
B) a topology-independent in-service software upgrade
C) a manual device upgrade
D) a nonstop software upgrade
A) an in-service software upgrade
B) a topology-independent in-service software upgrade
C) a manual device upgrade
D) a nonstop software upgrade

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
55
Which two characteristics describe the deployment of high-density chassis switches in a data center? (Choose two.)
A) In EoR deployments, the switches are consolidated in one location.
B) The switches consume a great deal of power, cooling, and space.
C) In ToR deployments, the switches provide more port connections, but with lower speeds.
D) More switches are often needed to accommodate the number of server connections.
A) In EoR deployments, the switches are consolidated in one location.
B) The switches consume a great deal of power, cooling, and space.
C) In ToR deployments, the switches provide more port connections, but with lower speeds.
D) More switches are often needed to accommodate the number of server connections.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
56
Your data center uses a Virtual Chassis Fabric. The ToR switches have 48 ports and each rack supports 20 servers. Each server has two ports that are configured as a LAG. You need to implement link level redundancy but you cannot use two ports on the same device for this redundancy. Which type of connection should you use to complete this task?
A) MC-LAG
B) RTG
C) LAG
D) ESI
A) MC-LAG
B) RTG
C) LAG
D) ESI

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
57
You are designing a DCI strategy. You must provide a solution that meets the requirements shown below: -sub 50 ms failover to alternate path -supports L2 and L3 VPNs -supports traffic engineered paths Which technology would satisfy the requirements?
A) MPLS
B) GRE
C) BGP
D) IPsec
A) MPLS
B) GRE
C) BGP
D) IPsec

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
58
You need a security management solution for your data center that will support centralized network visibility and control, J-Flow collection from existing perimeter devices, and SIEM. In this scenario, which two products should you choose for your data center design? (Choose two.)
A) vSRX
B) Security Director
C) JSA
D) Sky ATP
A) vSRX
B) Security Director
C) JSA
D) Sky ATP

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
59
What are two components of a class-of-service (CoS) switching configuration? (Choose two.)
A) forwarding tables
B) bandwidth
C) port speed
D) forwarding class
A) forwarding tables
B) bandwidth
C) port speed
D) forwarding class

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
60
Your company is deploying a private cloud based on OpenStack and has selected Contrail Networking as its SDN controller. Which two statements are true in this scenario? (Choose two.)
A) Underlay tunnels are established between virtualized and bare-metal servers.
B) MPLS over UDP tunnels are supported.
C) Overlay tunnels are established between virtualized and bare-metal servers.
D) MPLS over GRE tunnels are supported.
A) Underlay tunnels are established between virtualized and bare-metal servers.
B) MPLS over UDP tunnels are supported.
C) Overlay tunnels are established between virtualized and bare-metal servers.
D) MPLS over GRE tunnels are supported.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
61
Which two security components are inherent in a Contrail vRouter? (Choose two.)
A) basic tenant separation directional control for Layer 3 and Layer 4 traffic
B) Layer 7 traffic filters
C) security groups
D) encapsulation around each VM residing on the compute node
A) basic tenant separation directional control for Layer 3 and Layer 4 traffic
B) Layer 7 traffic filters
C) security groups
D) encapsulation around each VM residing on the compute node

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
62
Which protocol is used on the VPCs of a Virtual Chassis Fabric?
A) IEEE 802.1BR
B) MPLS
C) VCCP
D) IS-IS
A) IEEE 802.1BR
B) MPLS
C) VCCP
D) IS-IS

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
63
What is a characteristic of VRRP?
A) VRRP routers must communicate over a direct connection.
B) VRRP participating routers all act as active gateways.
C) VRRP provides high availability for a host's default gateway.
D) VRRP routes must communicate over a common switch.
A) VRRP routers must communicate over a direct connection.
B) VRRP participating routers all act as active gateways.
C) VRRP provides high availability for a host's default gateway.
D) VRRP routes must communicate over a common switch.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
64
You want to use the Intrusion Prevention System features of a vSRX virtual firewall to protect systems from attacks embedded in traffic. In this scenario, which three technologies would be used? (Choose three.)
A) protocol decodes
B) zero-day protection
C) traffic normalization
D) application firewall
E) application tracking
A) protocol decodes
B) zero-day protection
C) traffic normalization
D) application firewall
E) application tracking

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
65
Which two statements describe the Contrail vRouter? (Choose two.)
A) It is forwarding plane that runs software on a virtualized server.
B) It extends the network form physical routers and switches into an overlay network hosted in virtual server.
C) It is responsible for providing the management, control, and analytics functions of the virtualized network.
D) It provides the logically centralized control plane and management plane of the system.
A) It is forwarding plane that runs software on a virtualized server.
B) It extends the network form physical routers and switches into an overlay network hosted in virtual server.
C) It is responsible for providing the management, control, and analytics functions of the virtualized network.
D) It provides the logically centralized control plane and management plane of the system.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
66
Which devices are recommended by Juniper Networks as edge routers in a data center?
A) EX Series
B) QFX Series
C) MX Series
D) CTP Series
A) EX Series
B) QFX Series
C) MX Series
D) CTP Series

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
67
What would you use to balance traffic loads between servers in a Clos Layer 3 data center fabric?
A) MC-LAG
B) multicast protocols
C) ECMP routing
D) BGP export policies
A) MC-LAG
B) multicast protocols
C) ECMP routing
D) BGP export policies

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
68
How many inches does one RU equal?
A) 1.000
B) 1.251
C) 1.527
D) 1.752
A) 1.000
B) 1.251
C) 1.527
D) 1.752

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
69
Click the Exhibit button. Traffic congestion has been noticed when S1 is sending traffic to S2. You must design a CoS deployment to address the traffic congestion issue. Referring to the exhibit, which statement is true? 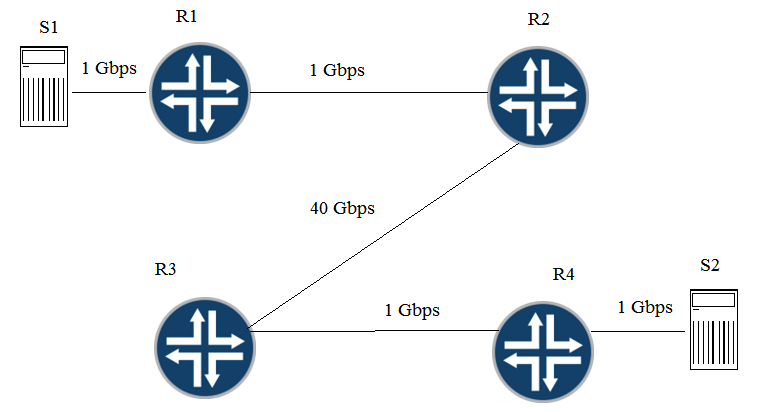
A) You should deploy CoS on R1 and R4.
B) You should deploy CoS on R1, R3 and R4.
C) You should deploy CoS on S1, R1, R2, R3, R4, and S2.
D) You should deploy CoS on R1, R2, R3, and R4.

A) You should deploy CoS on R1 and R4.
B) You should deploy CoS on R1, R3 and R4.
C) You should deploy CoS on S1, R1, R2, R3, R4, and S2.
D) You should deploy CoS on R1, R2, R3, and R4.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
70
You are asked to create a new data center based on an IP fabric architecture. The data center must support many segmented applications that require Layer 2 adjacencies. You decide to use EVPN-VXLAN as an overlay technology to accomplish the task. To meet the requirements, each application will be placed in its own VLAN. In this scenario, what is required for communication between VLANs to occur?
A) IBGP and Q-in-Q
B) IBGP and MP-BGP
C) IBGP and MPLS
D) IBGP and GVRP
A) IBGP and Q-in-Q
B) IBGP and MP-BGP
C) IBGP and MPLS
D) IBGP and GVRP

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
71
You are re-designing a traditional multitiered data center into a modern spine-and-leaf data center architecture. In this scenario, which two tiers are collapsed? (Choose two.)
A) distribution
B) WAN
C) access
D) core
A) distribution
B) WAN
C) access
D) core

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
72
You are designing a Junos-based Ethernet Fabric for a data center that has a combination of 60 EX Series and QFX Series devices. In this scenario, which solution would you choose?
A) Junos Fusion Provider Edge
B) Virtual Chassis
C) Junos Fusion Data Center
D) Virtual Chassis Fabric
A) Junos Fusion Provider Edge
B) Virtual Chassis
C) Junos Fusion Data Center
D) Virtual Chassis Fabric

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
73
You are implementing a Virtual Chassis Fabric using QFX5110 devices. Which two statements are true in this scenario according to Juniper Networks recommendations? (Choose two.)
A) Spine devices must assume the RE role.
B) Leaf devices must have a direct link to all other leaf devices.
C) Spine devices must assume the line card role.
D) Leaf devices must have a direct link to all spine devices.
A) Spine devices must assume the RE role.
B) Leaf devices must have a direct link to all other leaf devices.
C) Spine devices must assume the line card role.
D) Leaf devices must have a direct link to all spine devices.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck
74
Which statement is correct about a Junos Fusion Data Center fabric deployment?
A) Each aggregation device is managed separately.
B) Each satellite device is managed separately.
C) At satellite devices are managed and configured by an aggregation device.
D) All satellite and aggregation devices must be running the same version of Junos OS.
A) Each aggregation device is managed separately.
B) Each satellite device is managed separately.
C) At satellite devices are managed and configured by an aggregation device.
D) All satellite and aggregation devices must be running the same version of Junos OS.

Unlock Deck
Unlock for access to all 74 flashcards in this deck.
Unlock Deck
k this deck


