Deck 3: Security Design, Specialist (JNCDS-SEC)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/69
Play
Full screen (f)
Deck 3: Security Design, Specialist (JNCDS-SEC)
1
Your customer is getting ready to deploy a new WAN architecture. It must be simple to set up, address hub scaling concerns, and allow the automatic addition of new sites without requiring changes to the hub site. They want to deploy either AutoVPN or Auto Discovery VPN. In this scenario, why would you propose Auto Discovery VPN as a solution?
A) Your customer requires direct spoke-to-spoke communication
B) OSPF support is required
C) Only Auto Discovery VPN supports the automatic addition of valid spokes
D) Your customer needs to configure the hub site only once
A) Your customer requires direct spoke-to-spoke communication
B) OSPF support is required
C) Only Auto Discovery VPN supports the automatic addition of valid spokes
D) Your customer needs to configure the hub site only once
Your customer requires direct spoke-to-spoke communication
2
You are asked to virtualize numerous stateful firewalls in your customer's data center. The customer wants the solution to use the existing Kubernetes-orchestrated architecture. Which Juniper Networks product would satisfy this requirement?
A) vMX
B) vSRX
C) cSRX
D) CTP Series
A) vMX
B) vSRX
C) cSRX
D) CTP Series
cSRX
3
You are creating a security design proposal for an enterprise customer. As part of the design, you are implementing 802.1x authentication on your EX Series devices. In this scenario, which two statements are correct? (Choose two.)
A) The supplicant is the device that prevents the authenticator's access until it is authenticated
B) The supplicant is the device that is being authenticated
C) The authenticator is the device that is being authenticated
D) The authenticator is the device that prevents the supplicant's access until it is authenticated
A) The supplicant is the device that prevents the authenticator's access until it is authenticated
B) The supplicant is the device that is being authenticated
C) The authenticator is the device that is being authenticated
D) The authenticator is the device that prevents the supplicant's access until it is authenticated
The supplicant is the device that is being authenticated
The authenticator is the device that prevents the supplicant's access until it is authenticated
The authenticator is the device that prevents the supplicant's access until it is authenticated
4
A hosting company is migrating to cloud-based solutions. Their customers share a physical firewall cluster, subdivided into individual logical firewalls for each customer. Projection data shows that the cloud service will soon deplete all the resources within the physical firewall. As a consultant, you must propose a scalable solution that continues to protect all the cloud customers while still securing the existing physical network. In this scenario, which solution would you propose?
A) Deploy a vSRX cluster in front of each customer's servers while keeping the physical firewall cluster
B) Deploy a software-defined networking solution
C) Remove the physical firewall cluster and deploy vSRX clusters dedicated to each customer's servers
D) Replace the physical firewall cluster with a higher-performance firewall
A) Deploy a vSRX cluster in front of each customer's servers while keeping the physical firewall cluster
B) Deploy a software-defined networking solution
C) Remove the physical firewall cluster and deploy vSRX clusters dedicated to each customer's servers
D) Replace the physical firewall cluster with a higher-performance firewall

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
5
You are designing a network management solution that provides automation for Junos devices. Your customer wants to know which solutions would require additional software to be deployed to existing Junos devices. Which two solutions satisfy this scenario? (Choose two.)
A) SaltStack
B) Ansible
C) Puppet
D) Chef
A) SaltStack
B) Ansible
C) Puppet
D) Chef

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
6
You are deploying Security Director with the logging and reporting functionality for VMs that use SSDs. You expect to have approximately 20,000 events per second of logging in your network. In this scenario, what is the minimum number of logging and reporting devices that should be used?
A) 2
B) 4
C) 1
D) 3
A) 2
B) 4
C) 1
D) 3

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
7
You are creating a security design proposal for a customer who is connecting their headquarters to a remote branch site over an unsecured Internet connection. As part of your design, you must recommend a solution to connect these sites together and ensure that the communication is secured and encrypted. In this scenario, which solution do you recommend?
A) GRE
B) XMPP
C) IPsec
D) MPLS
A) GRE
B) XMPP
C) IPsec
D) MPLS

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
8
You are responding to an RFP for securing a large enterprise. The RFP requires an onsite security solution which can use logs from third-party sources to prevent threats. The solution should also have the capability to detect and stop zero-day attacks. Which Juniper Networks solution satisfies this requirement?
A) IDP
B) Sky ATP
C) JSA
D) JATP
A) IDP
B) Sky ATP
C) JSA
D) JATP

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
9
Which solution centralizes the management of security devices in your data center?
A) Juniper Networks Secure Analytics
B) J-Web
C) Junos Space Security Director
D) Junos CLI
A) Juniper Networks Secure Analytics
B) J-Web
C) Junos Space Security Director
D) Junos CLI

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
10
You are concerned about malicious attachments being transferred to your e-mail server at work through encrypted channels. You want to block these malicious files using your SRX Series device. Which two features should you use in this scenario? (Choose two.)
A) Sky ATP SMTP scanning
B) Sky ATP HTTP scanning
C) SSL forward proxy
D) SSL reverse proxy
A) Sky ATP SMTP scanning
B) Sky ATP HTTP scanning
C) SSL forward proxy
D) SSL reverse proxy

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
11
You are concerned about users attacking the publicly accessible servers in your data center through encrypted channels. You want to block these attacks using your SRX Series devices. In this scenario, which two features should you use? (Choose two.)
A) Sky ATP
B) IPS
C) SSL forward proxy
D) SSL reverse proxy
A) Sky ATP
B) IPS
C) SSL forward proxy
D) SSL reverse proxy

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
12
You have multiple SRX chassis clusters on a single broadcast domain. Why must you assign different cluster IDs in this scenario?
A) to avoid MAC address conflicts
B) to avoid control link conflicts
C) to avoid node numbering conflicts
D) to avoid redundancy group conflicts
A) to avoid MAC address conflicts
B) to avoid control link conflicts
C) to avoid node numbering conflicts
D) to avoid redundancy group conflicts

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
13
You are designing a solution to protect a service provider network against volumetric denial-of-service attacks. Your main concern is to protect the network devices. Which two solutions accomplish this task? (Choose two.)
A) next-generation firewall
B) screens
C) intrusion prevention system
D) BGP FlowSpec
A) next-generation firewall
B) screens
C) intrusion prevention system
D) BGP FlowSpec

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
14
You are designing a new campus Internet access service that implements dynamic NAT for customer IP addressing. The customer requires services that allow peer-to-peer networking and online gaming. In this scenario, what will accomplish this task?
A) EVPN over IPsec
B) one-to-one NAT
C) stacked VLAN tagging
D) endpoint independent mapping
A) EVPN over IPsec
B) one-to-one NAT
C) stacked VLAN tagging
D) endpoint independent mapping

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
15
What are two benefits of the vSRX in a virtualized private or public cloud multitenant environment? (Choose two.)
A) full logical systems capabilities
B) stateful firewall protection at the tenant edge
C) 100GbE interface support
D) OSPFv3 capabilities
A) full logical systems capabilities
B) stateful firewall protection at the tenant edge
C) 100GbE interface support
D) OSPFv3 capabilities

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
16
Click the Exhibit button. 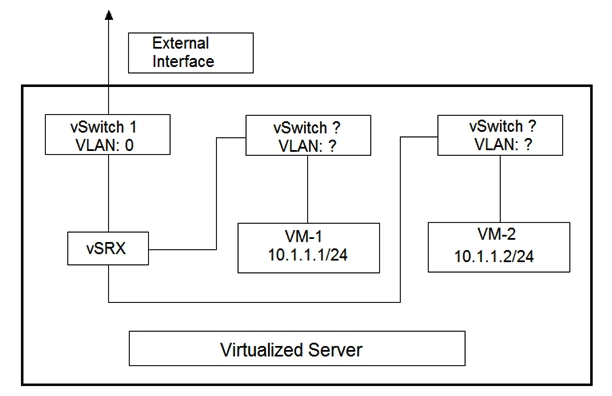 You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device. Which two actions must you perform to accomplish this task? (Choose two.)
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device. Which two actions must you perform to accomplish this task? (Choose two.)
A) Place both VMs in the same vSwitch
B) Place both VMs in the same VLAN
C) Place both VMs in different vSwitches
D) Place both VMs in different VLANs
 You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device. Which two actions must you perform to accomplish this task? (Choose two.)
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device. Which two actions must you perform to accomplish this task? (Choose two.)A) Place both VMs in the same vSwitch
B) Place both VMs in the same VLAN
C) Place both VMs in different vSwitches
D) Place both VMs in different VLANs

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
17
You are designing a new network for your organization with the characteristics shown below. All traffic must pass inspection by a security device. A center-positioned segmentation gateway must provide deep inspection of each packet using 10 Gbps interfaces. Policy enforcement must be centrally managed. Which security model should you choose for your network design?
A) Intrazone Permit
B) trust but verify
C) user-role firewall policies
D) Zero Trust
A) Intrazone Permit
B) trust but verify
C) user-role firewall policies
D) Zero Trust

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
18
You are creating a data center security design. Virtual security functions must be performed on east-west traffic. Security functions must be commissioned and decommissioned frequently, and the least resource-intensive architecture must be used. In this scenario, what will accomplish this task?
A) all-in-one NFV security devices with device templates
B) service chaining with container-based security functions
C) a security appliance segmented into logical systems
D) filter-based forwarding to direct traffic to the required security devices
A) all-in-one NFV security devices with device templates
B) service chaining with container-based security functions
C) a security appliance segmented into logical systems
D) filter-based forwarding to direct traffic to the required security devices

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
19
What are two reasons for using cSRX over vSRX? (Choose two.)
A) cSRX loads faster
B) cSRX uses less memory
C) cSRX supports the BGP protocol
D) cSRX supports IPsec
A) cSRX loads faster
B) cSRX uses less memory
C) cSRX supports the BGP protocol
D) cSRX supports IPsec

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
20
Your customer needs help designing a single solution to protect their combination of various Junos network devices from unauthorized management access. Which Junos OS feature will provide this protection?
A) Use a firewall filter applied to the fxp0 interface
B) Use a security policy with the destination of the junos-host zone
C) Use the management zone host-inbound-traffic feature
D) Use a firewall filter applied to the lo0 interface
A) Use a firewall filter applied to the fxp0 interface
B) Use a security policy with the destination of the junos-host zone
C) Use the management zone host-inbound-traffic feature
D) Use a firewall filter applied to the lo0 interface

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
21
You have a campus location with multiple WAN links. You want to specify the primary link used for your VoIP traffic. In this scenario, which type of WAN load balancing would you use?
A) BGP
B) OSPF
C) FBF
D) ECMP
A) BGP
B) OSPF
C) FBF
D) ECMP

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
22
You are working with a customer to create a design proposal using SRX Series devices. As part of the design, you must consider the requirements shown below: You must ensure that every packet entering your device is independently inspected against a set of rules. You must provide a way to protect the device from undesired access attempts. You must ensure that you can apply a different set of rules for traffic leaving the device than are in use for traffic entering the device. In this scenario, what do you recommend using to accomplish these requirements?
A) firewall filters
B) intrusion prevention system
C) unified threat management
D) screens
A) firewall filters
B) intrusion prevention system
C) unified threat management
D) screens

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
23
Your company has 500 branch sites and the CIO is concerned about minimizing the potential impact of a VPN router being stolen from an enterprise branch site. You want the ability to quickly disable a stolen VPN router while minimizing administrative overhead. Which solution accomplishes this task?
A) Implement a certificate-based VPN using a public key infrastructure (PKI)
B) Modify your IKE proposals to use Diffie-Hellman group 14 or higher
C) Use firewall filters to block traffic from the stolen VPN router
D) Rotate VPN pre-shared keys every month
A) Implement a certificate-based VPN using a public key infrastructure (PKI)
B) Modify your IKE proposals to use Diffie-Hellman group 14 or higher
C) Use firewall filters to block traffic from the stolen VPN router
D) Rotate VPN pre-shared keys every month

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
24
In a data center, what are two characteristics of access tier VLAN termination on the aggregation tier? (Choose two.)
A) Multiple VLANs can be part of one security zone
B) A security zone is limited to a single VLAN
C) Inter-VLAN traffic within a zone can bypass firewall services
D) Inter-VLAN traffic is secured through firewall services
A) Multiple VLANs can be part of one security zone
B) A security zone is limited to a single VLAN
C) Inter-VLAN traffic within a zone can bypass firewall services
D) Inter-VLAN traffic is secured through firewall services

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
25
You are asked to include anti-malware features into an existing network design. Traffic from the infected machines must be moved to a quarantined VLAN. Which product will provide this segregation?
A) screens
B) Sky ATP
C) unified threat management
D) Software Defined Secure Network
A) screens
B) Sky ATP
C) unified threat management
D) Software Defined Secure Network

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
26
You are using SRX Series devices to secure your network and you require sandboxing for malicious file detonation. However, per company policy, you cannot send potentially malicious files outside your network for sandboxing. Which feature should you use in this situation?
A) Sky ATP
B) UTM antivirus
C) IPS
D) JATP
A) Sky ATP
B) UTM antivirus
C) IPS
D) JATP

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
27
Which two steps should be included in your security design process? (Choose two.)
A) Identify external attackers
B) Define safety requirements for the customer's organization
C) Identify the firewall enforcement points
D) Define overall security policies
A) Identify external attackers
B) Define safety requirements for the customer's organization
C) Identify the firewall enforcement points
D) Define overall security policies

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
28
You are deploying a data center Clos architecture and require secure data transfers within the switching fabric. In this scenario, what will accomplish this task?
A) MACsec encryption
B) LAG Layer 2 hashing
C) IRB VLAN routing between hosts
D) stacked VLAN tagging on the core switches
A) MACsec encryption
B) LAG Layer 2 hashing
C) IRB VLAN routing between hosts
D) stacked VLAN tagging on the core switches

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
29
You are asked to design a secure enterprise WAN where all payload data is encrypted and branch sites communicate directly without routing all traffic through a central hub. Which two technologies would accomplish this task? (Choose two.)
A) group VPN
B) AutoVPN
C) MPLS Layer 3 VPN
D) Auto Discovery VPN
A) group VPN
B) AutoVPN
C) MPLS Layer 3 VPN
D) Auto Discovery VPN

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
30
You want to deploy a VPN that will connect branch locations to the main office. You will eventually add additional branch locations to the topology, and you must avoid additional configuration on the hub when those sites are added. In this scenario, which VPN solution would you recommend?
A) Site-to-Site VPN
B) Hub-and-Spoke VPN
C) AutoVPN
D) Group VPN
A) Site-to-Site VPN
B) Hub-and-Spoke VPN
C) AutoVPN
D) Group VPN

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
31
You are asked to provide a design proposal for a campus network. As part of the design, the customer requires that all end user devices must be authenticated before being granted access to their Layer 2 network. Which feature meets this requirement?
A) IPsec
B) 802.1X
C) NAT
D) ALGs
A) IPsec
B) 802.1X
C) NAT
D) ALGs

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
32
You have a site that has two Internet connections but no switch on the outside of the firewall. You want to use ISP-A over ISP-B during normal operations. Which type of chassis cluster design would you propose to satisfy this requirement?
A) Propose active/active cluster deployment with separate redundancy groups
B) Propose active/passive cluster deployment with separate redundancy groups
C) Propose active/active cluster deployment without separate redundancy groups
D) Propose active/passive cluster deployment without separate redundancy groups
A) Propose active/active cluster deployment with separate redundancy groups
B) Propose active/passive cluster deployment with separate redundancy groups
C) Propose active/active cluster deployment without separate redundancy groups
D) Propose active/passive cluster deployment without separate redundancy groups

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
33
What is the maximum number of SRX Series devices in a chassis cluster?
A) 2
B) 3
C) 4
D) 5
A) 2
B) 3
C) 4
D) 5

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
34
You must design a small branch office firewall solution that provides application usage statistics. In this scenario, which feature would accomplish this task?
A) AppFW
B) AppTrack
C) UTM
D) AppQoS
A) AppFW
B) AppTrack
C) UTM
D) AppQoS

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
35
You are designing a data center security solution for a customer. The customer asks that you provide a DDoS solution. Several IPsec tunnels will be terminated at the data center gateway. Which type of security is your customer asking you to implement?
A) segmentation
B) intra-data center policy enforcement
C) perimeter protection
D) compliance
A) segmentation
B) intra-data center policy enforcement
C) perimeter protection
D) compliance

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
36
You are designing an enterprise WAN network that must connect multiple sites. You must provide a design proposal for the security elements needed to encrypt traffic between the remote sites. Which feature will secure the traffic?
A) BFD
B) OSPF
C) GRE
D) IPsec
A) BFD
B) OSPF
C) GRE
D) IPsec

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
37
You are asked to design a security solution for your client's new two-tier data center. The client has a need for some flows to bypass firewall inspection entirely. Where should the firewall be deployed in this data center?
A) inline, between the core switches and the access switches
B) inline, between the core switches and the edge routers
C) one-arm configuration, connected to the core switches
D) one-arm configuration, connected to each access switch
A) inline, between the core switches and the access switches
B) inline, between the core switches and the edge routers
C) one-arm configuration, connected to the core switches
D) one-arm configuration, connected to each access switch

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
38
You are deploying Security Director with the logging and reporting functionality for VMs that use SSDs. You expect to have approximately 20,000 events per second of logging in your network. In this scenario, what is the minimum number of log receiver devices that you should use?
A) 4
B) 3
C) 2
D) 1
A) 4
B) 3
C) 2
D) 1

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
39
You want to deploy JATP in your network that uses SRX Series devices. In this scenario, which feature must you enable on the SRX Series devices?
A) SSL forward proxy
B) AppSecure
C) UTM antivirus
D) IPS
A) SSL forward proxy
B) AppSecure
C) UTM antivirus
D) IPS

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
40
You are designing a data center security architecture. The design requires automated scaling of security services according to real-time traffic flows. Which two design components will accomplish this task? (Choose two.)
A) telemetry with an SDN controller
B) JFlow traffic monitoring with event scripts
C) VNF security devices deployed on x86 servers
D) VRF segmentation on high-capacity physical security appliances
A) telemetry with an SDN controller
B) JFlow traffic monitoring with event scripts
C) VNF security devices deployed on x86 servers
D) VRF segmentation on high-capacity physical security appliances

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
41
You will be managing 1000 SRX Series devices. Each SRX Series device requires basic source NAT to access the Internet. Which product should you use to manage these NAT rules on the SRX Series devices?
A) Security Director
B) CSO
C) Contrail
D) JSA
A) Security Director
B) CSO
C) Contrail
D) JSA

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
42
What are two benefits of the vSRX in a virtualized private or public cloud multitenant environment? (Choose two.)
A) full logical systems capabilities
B) stateful firewall protection at the tenant edge
C) 100GbE interface support
D) OSPFv3 capabilities
A) full logical systems capabilities
B) stateful firewall protection at the tenant edge
C) 100GbE interface support
D) OSPFv3 capabilities

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
43
What are two reasons for using cSRX over vSRX? (Choose two.)
A) cSRX loads faster
B) cSRX uses less memory
C) cSRX supports the BGP protocol
D) cSRX supports IPsec
A) cSRX loads faster
B) cSRX uses less memory
C) cSRX supports the BGP protocol
D) cSRX supports IPsec

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
44
Click the Exhibit button. 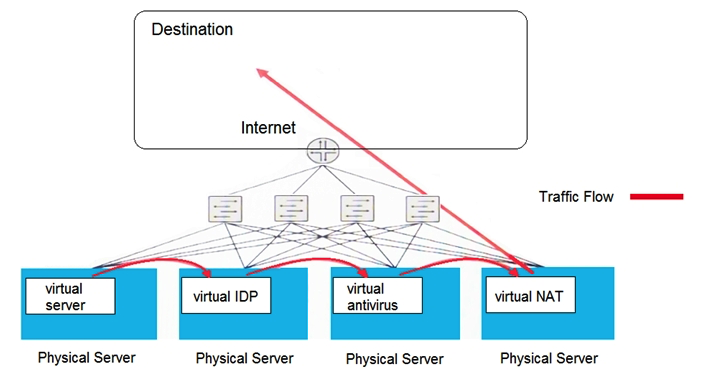 Which type of security solution is shown in this exhibit?
Which type of security solution is shown in this exhibit?
A) service chain model
B) centralized model
C) inline security model
D) de-centralized model
 Which type of security solution is shown in this exhibit?
Which type of security solution is shown in this exhibit?A) service chain model
B) centralized model
C) inline security model
D) de-centralized model

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
45
You are designing an enterprise WAN network that must connect multiple sites. You must provide a design proposal for the security elements needed to encrypt traffic between the remote sites. Which feature will secure the traffic?
A) BFD
B) OSPF
C) GRE
D) IPsec
A) BFD
B) OSPF
C) GRE
D) IPsec

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
46
You are designing a data center interconnect between two sites across a service provider Layer 2 leased line. The sites require Layer 2 connectivity between hosts, and the connection must be secure. In this scenario, what will accomplish this task?
A) IRB VLAN routing
B) MACsec encryption
C) EVPN over IPsec
D) IPsec encryption
A) IRB VLAN routing
B) MACsec encryption
C) EVPN over IPsec
D) IPsec encryption

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
47
Which solution provides a certificate based on user identity for network access?
A) network access control
B) user firewall
C) IP filtering
D) MAC filtering
A) network access control
B) user firewall
C) IP filtering
D) MAC filtering

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
48
You must design a small branch office firewall solution that provides application usage statistics. In this scenario, which feature would accomplish this task?
A) AppFW
B) AppTrack
C) UTM
D) AppQoS
A) AppFW
B) AppTrack
C) UTM
D) AppQoS

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
49
A hosting company is migrating to cloud-based solutions. Their customers share a physical firewall cluster, subdivided into individual logical firewalls for each customer. Projection data shows that the cloud service will soon deplete all the resources within the physical firewall. As a consultant, you must propose a scalable solution that continues to protect all the cloud customers while still securing the existing physical network. In this scenario, which solution would you propose?
A) Deploy a vSRX cluster in front of each customer's servers while keeping the physical firewall cluster
B) Deploy a software-defined networking solution
C) Remove the physical firewall cluster and deploy vSRX clusters dedicated to each customer's servers
D) Replace the physical firewall cluster with a higher-performance firewall
A) Deploy a vSRX cluster in front of each customer's servers while keeping the physical firewall cluster
B) Deploy a software-defined networking solution
C) Remove the physical firewall cluster and deploy vSRX clusters dedicated to each customer's servers
D) Replace the physical firewall cluster with a higher-performance firewall

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
50
Which two protocols are supported natively by the Junos automation stack? (Choose two.)
A) NETCONF
B) PyEZ
C) Jenkins
D) CIP
A) NETCONF
B) PyEZ
C) Jenkins
D) CIP

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
51
You are creating a security design proposal for an enterprise customer. As part of the design, you are implementing 802.1x authentication on your EX Series devices. In this scenario, which two statements are correct? (Choose two.)
A) The supplicant is the device that prevents the authenticator's access until it is authenticated
B) The supplicant is the device that is being authenticated
C) The authenticator is the device that is being authenticated
D) The authenticator is the device that prevents the supplicant's access until it is authenticated
A) The supplicant is the device that prevents the authenticator's access until it is authenticated
B) The supplicant is the device that is being authenticated
C) The authenticator is the device that is being authenticated
D) The authenticator is the device that prevents the supplicant's access until it is authenticated

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
52
You are working on a network design that will use EX Series devices as Layer 2 access switches in a campus environment. You must include Junos Space in your design. You want to take advantage of security features supported on the devices. Which two security features would satisfy this requirement? (Choose two.)
A) SDSN
B) Stateful Firewall
C) Access Control
D) ALG
A) SDSN
B) Stateful Firewall
C) Access Control
D) ALG

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
53
You are creating a data center security design. Virtual security functions must be performed on east-west traffic. Security functions must be commissioned and decommissioned frequently, and the least resource-intensive architecture must be used. In this scenario, what will accomplish this task?
A) all-in-one NFV security devices with device templates
B) service chaining with container-based security functions
C) a security appliance segmented into logical systems
D) filter-based forwarding to direct traffic to the required security devices
A) all-in-one NFV security devices with device templates
B) service chaining with container-based security functions
C) a security appliance segmented into logical systems
D) filter-based forwarding to direct traffic to the required security devices

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
54
You are responding to an RFP for securing a large enterprise. The RFP requires an onsite security solution which can use logs from third-party sources to prevent threats. The solution should also have the capability to detect and stop zero-day attacks. Which Juniper Networks solution satisfies this requirement?
A) IDP
B) Sky ATP
C) JSA
D) JATP
A) IDP
B) Sky ATP
C) JSA
D) JATP

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
55
You have a campus location with multiple WAN links. You want to specify the primary link used for your VoIP traffic. In this scenario, which type of WAN load balancing would you use?
A) BGP
B) OSPF
C) FBF
D) ECMP
A) BGP
B) OSPF
C) FBF
D) ECMP

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
56
You are designing a new network for your organization with the characteristics shown below. All traffic must pass inspection by a security device. A center-positioned segmentation gateway must provide deep inspection of each packet using 10 Gbps interfaces. Policy enforcement must be centrally managed. Which security model should you choose for your network design?
A) Intrazone Permit
B) trust but verify
C) user-role firewall policies
D) Zero Trust
A) Intrazone Permit
B) trust but verify
C) user-role firewall policies
D) Zero Trust

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
57
You are designing a DDoS solution for an ISP using BGP FlowSpec. You want to ensure that BGP FlowSpec does not overwhelm the ISP's edge routers. Which two requirements should be included in your design? (Choose two.)
A) Specify a maximum number BGP FlowSpec prefixes per neighbor
B) Implement a route policy to limit advertised routes to /24 subnets
C) Implement a route policy to limit advertised routes to any public IP space
D) Specify a maximum number of BGP FlowSpec prefixes per device
A) Specify a maximum number BGP FlowSpec prefixes per neighbor
B) Implement a route policy to limit advertised routes to /24 subnets
C) Implement a route policy to limit advertised routes to any public IP space
D) Specify a maximum number of BGP FlowSpec prefixes per device

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
58
Your company has outgrown its existing secure enterprise WAN that is configured to use OSPF, AutoVPN, and IKE version 1. You are asked if it is possible to make a design change to improve the WAN performance without purchasing new hardware. Which two design changes satisfy these requirements? (Choose two.)
A) Modify the IPsec proposal from AES-128 to AES-256
B) Change the IGP from OSPF to IS-IS
C) Migrate to IKE version 2
D) Implement Auto Discovery VPN
A) Modify the IPsec proposal from AES-128 to AES-256
B) Change the IGP from OSPF to IS-IS
C) Migrate to IKE version 2
D) Implement Auto Discovery VPN

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
59
What is the maximum number of SRX Series devices in a chassis cluster?
A) 2
B) 3
C) 4
D) 5
A) 2
B) 3
C) 4
D) 5

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
60
You are designing a new campus Internet access service that implements dynamic NAT for customer IP addressing. The customer requires services that allow peer-to-peer networking and online gaming. In this scenario, what will accomplish this task?
A) EVPN over IPsec
B) one-to-one NAT
C) stacked VLAN tagging
D) endpoint independent mapping
A) EVPN over IPsec
B) one-to-one NAT
C) stacked VLAN tagging
D) endpoint independent mapping

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
61
You have a site that has two Internet connections but no switch on the outside of the firewall. You want to use ISP-A over ISP-B during normal operations. Which type of chassis cluster design would you propose to satisfy this requirement?
A) Propose active/active cluster deployment with separate redundancy groups
B) Propose active/passive cluster deployment with separate redundancy groups
C) Propose active/active cluster deployment without separate redundancy groups
D) Propose active/passive cluster deployment without separate redundancy groups
A) Propose active/active cluster deployment with separate redundancy groups
B) Propose active/passive cluster deployment with separate redundancy groups
C) Propose active/active cluster deployment without separate redundancy groups
D) Propose active/passive cluster deployment without separate redundancy groups

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
62
You are deploying Security Director with the logging and reporting functionality for VMs that use SSDs. You expect to have approximately 20,000 events per second of logging in your network. In this scenario, what is the minimum number of log receiver devices that you should use?
A) 4
B) 3
C) 2
D) 1
A) 4
B) 3
C) 2
D) 1

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
63
You are asked to deploy a security solution in your data center that ensures all traffic flows through the SRX Series devices. Which firewall deployment method meets this requirement?
A) one-arm
B) two-arm
C) transparent
D) inline
A) one-arm
B) two-arm
C) transparent
D) inline

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
64
Your company has 500 branch sites and the CIO is concerned about minimizing the potential impact of a VPN router being stolen from an enterprise branch site. You want the ability to quickly disable a stolen VPN router while minimizing administrative overhead. Which solution accomplishes this task?
A) Implement a certificate-based VPN using a public key infrastructure (PKI)
B) Modify your IKE proposals to use Diffie-Hellman group 14 or higher
C) Use firewall filters to block traffic from the stolen VPN router
D) Rotate VPN pre-shared keys every month
A) Implement a certificate-based VPN using a public key infrastructure (PKI)
B) Modify your IKE proposals to use Diffie-Hellman group 14 or higher
C) Use firewall filters to block traffic from the stolen VPN router
D) Rotate VPN pre-shared keys every month

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
65
You are designing a data center security architecture. The design requires automated scaling of security services according to real-time traffic flows. Which two design components will accomplish this task? (Choose two.)
A) telemetry with an SDN controller
B) JFlow traffic monitoring with event scripts
C) VNF security devices deployed on x86 servers
D) VRF segmentation on high-capacity physical security appliances
A) telemetry with an SDN controller
B) JFlow traffic monitoring with event scripts
C) VNF security devices deployed on x86 servers
D) VRF segmentation on high-capacity physical security appliances

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
66
You want to deploy a VPN that will connect branch locations to the main office. You will eventually add additional branch locations to the topology, and you must avoid additional configuration on the hub when those sites are added. In this scenario, which VPN solution would you recommend?
A) Site-to-Site VPN
B) Hub-and-Spoke VPN
C) AutoVPN
D) Group VPN
A) Site-to-Site VPN
B) Hub-and-Spoke VPN
C) AutoVPN
D) Group VPN

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
67
You are working with a customer to create a design proposal using SRX Series devices. As part of the design, you must consider the requirements shown below: You must ensure that every packet entering your device is independently inspected against a set of rules. You must provide a way to protect the device from undesired access attempts. You must ensure that you can apply a different set of rules for traffic leaving the device than are in use for traffic entering the device. In this scenario, what do you recommend using to accomplish these requirements?
A) firewall filters
B) intrusion prevention system
C) unified threat management
D) screens
A) firewall filters
B) intrusion prevention system
C) unified threat management
D) screens

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
68
Which statement is correct about service chaining?
A) Service chaining uses IPsec to connect together two or more VMs
B) Service chaining evaluates traffic by using multiple security features on the same instance
C) Service chaining redirects traffic back through the same device for additional processing
D) Service chaining combines multiple VNF instances together in the data flow
A) Service chaining uses IPsec to connect together two or more VMs
B) Service chaining evaluates traffic by using multiple security features on the same instance
C) Service chaining redirects traffic back through the same device for additional processing
D) Service chaining combines multiple VNF instances together in the data flow

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck
69
You are asked to provide a design proposal for a campus network. As part of the design, the customer requires that all end user devices must be authenticated before being granted access to their Layer 2 network. Which feature meets this requirement?
A) IPsec
B) 802.1X
C) NAT
D) ALGs
A) IPsec
B) 802.1X
C) NAT
D) ALGs

Unlock Deck
Unlock for access to all 69 flashcards in this deck.
Unlock Deck
k this deck


