Deck 9: Enterprise Routing and Switching, Specialist
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/39
Play
Full screen (f)
Deck 9: Enterprise Routing and Switching, Specialist
1
Which type of query is generated by the curl http://:8081/analytics/uves/vrouters command?
A) SSL
B) REST
C) SQL
D) XML
A) SSL
B) REST
C) SQL
D) XML
REST
2
You are asked to change the settings in the AppFormix UI so that compute1's status displays "Bad" only when CPU utilization is above 70%. In which workspace of the AppFormix UI would you perform this task?
A) SLA Settings
B) Notification Settings
C) Plugins
D) Services Settings
A) SLA Settings
B) Notification Settings
C) Plugins
D) Services Settings
SLA Settings
3
What are three benefits of implementing an NFV solution? (Choose three.)
A) increased network speed using bandwidth management
B) reduced hardware requirements
C) automated services
D) tenants charged only for what they use
E) isolated switching functions
A) increased network speed using bandwidth management
B) reduced hardware requirements
C) automated services
D) tenants charged only for what they use
E) isolated switching functions
increased network speed using bandwidth management
reduced hardware requirements
automated services
reduced hardware requirements
automated services
4
Which two statements about Kubernetes clusters are correct? (Choose two.)
A) The master coordinates the cluster.
B) The minions are responsible for running the applications.
C) The nodes are responsible for running the applications.
D) The pod controller coordinates the cluster.
A) The master coordinates the cluster.
B) The minions are responsible for running the applications.
C) The nodes are responsible for running the applications.
D) The pod controller coordinates the cluster.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
5
What are two networking components of OpenStack? (Choose two.)
A) Neutron
B) Nova
C) Ironic
D) Barbican
A) Neutron
B) Nova
C) Ironic
D) Barbican

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
6
Which two fabric management tasks would be completed using Contrail Command? (Choose two.)
A) Automatically deploy an P fabric underlay.
B) Modify routing protocol preferences.
C) Change user permissions on Junos devices.
D) Discover devices in the network.
A) Automatically deploy an P fabric underlay.
B) Modify routing protocol preferences.
C) Change user permissions on Junos devices.
D) Discover devices in the network.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
7
Which two statements regarding tags, within the Contrail Security framework, are correct? (Choose two.)
A) RBAC determines which user accounts can modify or remove attached tags.
B) Tags are communicated from the control node to vRouters through route updates.
C) Only the CSPadmin user account can modify or remove attached tags.
D) Tags are communicated from the config node to vRouters through route updates.
A) RBAC determines which user accounts can modify or remove attached tags.
B) Tags are communicated from the control node to vRouters through route updates.
C) Only the CSPadmin user account can modify or remove attached tags.
D) Tags are communicated from the config node to vRouters through route updates.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
8
Which SDN solution allows the control plane to remain on legacy hardware as a stop-gap measure until you are ready to replace the current hardware?
A) SDN using NVGRE
B) SDN as an overlay
C) SDN using an API
D) open SDN
A) SDN using NVGRE
B) SDN as an overlay
C) SDN using an API
D) open SDN

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
9
What are three ways to deploy an MX Series device as an SDN gateway? (Choose three.)
A) Configure it as an L4 gateway.
B) Configure it as an application gateway.
C) Configure it as an SDN-to-SDN gateway.
D) Configure it as an L3 gateway.
E) Configure it as an L2 gateway.
A) Configure it as an L4 gateway.
B) Configure it as an application gateway.
C) Configure it as an SDN-to-SDN gateway.
D) Configure it as an L3 gateway.
E) Configure it as an L2 gateway.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
10
What is a TAP interface in Contrail?
A) A software network interface that operates at OSI Layer 3.
B) A hardware network interface that operates at OSI Layer 3.
C) A software network interface that operates at OSI Layer 2.
D) A hardware network interface that operates at OSI Layer 2.
A) A software network interface that operates at OSI Layer 3.
B) A hardware network interface that operates at OSI Layer 3.
C) A software network interface that operates at OSI Layer 2.
D) A hardware network interface that operates at OSI Layer 2.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
11
Prior to installing Contrail, which list of settings must be verified on all participating servers?
A) DHCP is enabled, hostname resolution, and that SSH is enabled
B) time synchronization, hostname resolution, and that FTP is enabled
C) time synchronization, hostname resolution, and that SSH is enabled
D) DHCP is enabled, hostname resolution, and that FTP is enabled
A) DHCP is enabled, hostname resolution, and that SSH is enabled
B) time synchronization, hostname resolution, and that FTP is enabled
C) time synchronization, hostname resolution, and that SSH is enabled
D) DHCP is enabled, hostname resolution, and that FTP is enabled

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
12
To retrieve attributes of a new virtual machine, with which Contrail component does the OpenStack Nova agent communicate to create a virtual network?
A) Neutron
B) Glance
C) Analytics
D) Control
A) Neutron
B) Glance
C) Analytics
D) Control

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
13
What is AppFormix used for in Contrail?
A) to deploy an underlay fabric
B) to create VNFs
C) to analyze network performance
D) to secure application traffic
A) to deploy an underlay fabric
B) to create VNFs
C) to analyze network performance
D) to secure application traffic

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
14
You have deployed a Contrail cluster that must support bare-metal servers. Which protocol is used to communicate between the bare-metal server's virtual tunnel endpoints and the Contrail cluster to establish sessions with the VM servers?
A) SRTP
B) EVPN/VXLAN
C) BGP
D) XMPP
A) SRTP
B) EVPN/VXLAN
C) BGP
D) XMPP

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
15
Which command displays routes in vRouter VRF?
A) rt
B) show route
C) show route table vrf-name
D) route print
A) rt
B) show route
C) show route table vrf-name
D) route print

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
16
Which two deployment methods does AppFormix support? (Choose two.)
A) Hyper-V
B) VMware
C) OpenStack
D) Xen
A) Hyper-V
B) VMware
C) OpenStack
D) Xen

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
17
Which two statements are true about Generic Device Operations? (Choose two.)
A) Generic Device Operations execute multiple commands on multiple devices.
B) Generic Device Operations are executed using the REST API.
C) Generic Device Operations are executed using Ansible.
D) Generic Device Operations execute a single command on multiple devices.
A) Generic Device Operations execute multiple commands on multiple devices.
B) Generic Device Operations are executed using the REST API.
C) Generic Device Operations are executed using Ansible.
D) Generic Device Operations execute a single command on multiple devices.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
18
Which two statements about SDN and NFV are true? (Choose two.)
A) NFV separates network control and forwarding functions and provides a centralized view of the network.
B) SDN decouples network services from hardware appliances so they can run in software.
C) SDN separates network control and forwarding functions and provides a centralized view of the network.
D) NFV decouples network services from hardware appliances so they can run in software.
A) NFV separates network control and forwarding functions and provides a centralized view of the network.
B) SDN decouples network services from hardware appliances so they can run in software.
C) SDN separates network control and forwarding functions and provides a centralized view of the network.
D) NFV decouples network services from hardware appliances so they can run in software.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
19
Which BMS feature ensures that IP address management is consistent between the virtual and physical instances?
A) inventory management
B) image management
C) IPAM management
D) network security management
A) inventory management
B) image management
C) IPAM management
D) network security management

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
20
You decide to create only host routes for each of your virtual networks in a project. Each virtual network is sent its correct host prefix. When troubleshooting inter-VN connectivity, using the ping command, the response times out between two virtual networks even though your policies allow for it. What is the problem in this scenario?
A) The VMs do not have interfaces.
B) Using host routes prevents the default route from being sent.
C) Your VMs have incorrect DNS settings.
D) The IPAM settings are incorrect.
A) The VMs do not have interfaces.
B) Using host routes prevents the default route from being sent.
C) Your VMs have incorrect DNS settings.
D) The IPAM settings are incorrect.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
21
Which Kubernetes resource defines the traffic allowed to reach the pod?
A) SecurityGroup
B) NetworkPolicy
C) Ingress
D) IPAM
A) SecurityGroup
B) NetworkPolicy
C) Ingress
D) IPAM

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
22
Your development team asks you to provision twenty exact copies of a three-tier application containing three VMs. Each copy of the application must be on their own isolated network. The development team also wants to deploy more copies in the future from a self-service portal. What will accomplish this task?
A) Create a Heat orchestration template for the application and then launch twenty stacks using the Horizon dashboard or OpenStack CLI.
B) Use the Contrail fabric manager to define and launch all twenty stacks using an intent-driven automation feature.
C) Create all twenty networks and launch each instance using the Horizon instance creation wizard.
D) Create a Heat orchestration template for the application and then launch twenty stacks using the AppFormix user interface.
A) Create a Heat orchestration template for the application and then launch twenty stacks using the Horizon dashboard or OpenStack CLI.
B) Use the Contrail fabric manager to define and launch all twenty stacks using an intent-driven automation feature.
C) Create all twenty networks and launch each instance using the Horizon instance creation wizard.
D) Create a Heat orchestration template for the application and then launch twenty stacks using the AppFormix user interface.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
23
Which three elements should be used in a greenfield fabric deployment? (Choose three.)
A) multi-area OSPF
B) BGP
C) ZTP
D) existing IP fabric
E) LLDP
A) multi-area OSPF
B) BGP
C) ZTP
D) existing IP fabric
E) LLDP

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
24
What are two Contrail Command BMS life cycle management functions? (Choose two.)
A) PXE interface management
B) BIOS updates
C) image management
D) IPAM
A) PXE interface management
B) BIOS updates
C) image management
D) IPAM

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
25
Which two interfaces are active in the Contrail analyzer-vm-console-two-if.qcow2 traffic analyzer image? (Choose two.)
A) left
B) right
C) monitor
D) management
A) left
B) right
C) monitor
D) management

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
26
Which role does OpenStack serve in SDN?
A) vRouter
B) controller
C) gateway
D) orchestrator
A) vRouter
B) controller
C) gateway
D) orchestrator

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
27
Two virtual machines that belong to the same virtual network are not able to communicate with each other. Which statement is true in this scenario?
A) A floating IP address is assigned to the virtual machine.
B) Images used to spawn the two virtual machines have different flavors.
C) A security group is blocking the communication.
D) The two virtual machines are in different availability zones.
A) A floating IP address is assigned to the virtual machine.
B) Images used to spawn the two virtual machines have different flavors.
C) A security group is blocking the communication.
D) The two virtual machines are in different availability zones.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
28
Which protocol does Contrail use to exchange information between the Contrail Controller and the Contrail vRouter?
A) NETCONF
B) XMPP
C) BGP
D) SSH
A) NETCONF
B) XMPP
C) BGP
D) SSH

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
29
What are three examples of hypervisors? (Choose three.)
A) VMware ESXi
B) Juniper vSRX
C) KVM
D) OpenStack Nova
E) Microsoft Hyper-V
A) VMware ESXi
B) Juniper vSRX
C) KVM
D) OpenStack Nova
E) Microsoft Hyper-V

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
30
You are configuring a Contrail Security firewall policy rule and need to specify an exact port. Which two statements describe how to accomplish this task? (Choose two.)
A) You should create a tag and specify it in the firewall policy rule.
B) You should create an address group and specify it in the firewall policy rule.
C) You should create a service group and specify it in the firewall policy rule.
D) You should specify the service in the firewall policy rule.
A) You should create a tag and specify it in the firewall policy rule.
B) You should create an address group and specify it in the firewall policy rule.
C) You should create a service group and specify it in the firewall policy rule.
D) You should specify the service in the firewall policy rule.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
31
What are two advantages of SDN? (Choose two.)
A) centralized management
B) decentralized management
C) programmability
D) static networking
A) centralized management
B) decentralized management
C) programmability
D) static networking

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
32
Click the Exhibit button. 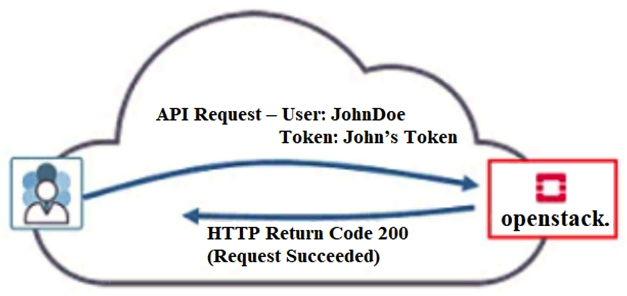 Referring to the exhibit, what must have occurred prior to JohnDoe sending the request?
Referring to the exhibit, what must have occurred prior to JohnDoe sending the request?
A) JohnDoe must have obtained a valid token from Horizon.
B) JohnDoe must have successfully authenticated using OpenStack's Web user interface.
C) JohnDoe must have obtained a valid token from Keystone.
D) JonnDoe must have obtained a valid token from the Contrail control node.
 Referring to the exhibit, what must have occurred prior to JohnDoe sending the request?
Referring to the exhibit, what must have occurred prior to JohnDoe sending the request?A) JohnDoe must have obtained a valid token from Horizon.
B) JohnDoe must have successfully authenticated using OpenStack's Web user interface.
C) JohnDoe must have obtained a valid token from Keystone.
D) JonnDoe must have obtained a valid token from the Contrail control node.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
33
Which two OpenStack components are optional services? (Choose two.)
A) Nova
B) Heat
C) Glance
D) Magnum
A) Nova
B) Heat
C) Glance
D) Magnum

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
34
You have an existing spine and leaf topology that you want to add into Contrail Command for fabric management. Which two configuration tasks are required to accomplish this task? (Choose two.)
A) Enable OVSDB in the Contrail Command UI.
B) Enable the REST API on the network devices.
C) Enable VXLAN routing in the Contrail Command UI.
D) Enable netconf SSH on the network devices.
A) Enable OVSDB in the Contrail Command UI.
B) Enable the REST API on the network devices.
C) Enable VXLAN routing in the Contrail Command UI.
D) Enable netconf SSH on the network devices.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
35
Which two nodes are part of the Contrail controller role? (Choose two.)
A) config
B) control
C) analytics
D) load balancer
A) config
B) control
C) analytics
D) load balancer

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
36
Which endpoint type in Contrail Security provides multidimensional segmentation such as application, tier, deployment or site parameters?
A) domain
B) virtual network
C) tag
D) address group
A) domain
B) virtual network
C) tag
D) address group

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
37
Which role does Contrail serve in SDN?
A) orchestrator
B) controller
C) gateway
D) fabric
A) orchestrator
B) controller
C) gateway
D) fabric

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
38
What is the proper order for creating a virtual network?
A) Configure the IPAM, virtual network, DNS, and then the virtual machine.
B) Configure the DNS, IPAM, virtual network, and then the virtual machine.
C) Configure the virtual network, DNS, IPAM, and then the virtual machine.
D) Configure the IPAM, DNS, virtual network, and then the virtual machine.
A) Configure the IPAM, virtual network, DNS, and then the virtual machine.
B) Configure the DNS, IPAM, virtual network, and then the virtual machine.
C) Configure the virtual network, DNS, IPAM, and then the virtual machine.
D) Configure the IPAM, DNS, virtual network, and then the virtual machine.

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck
39
You have a centrally routed and bridged topology. In this scenario, routing between subnets would be performed on which two types of devices? (Choose two.)
A) leaf
B) spine
C) DC gateway
D) bridge
A) leaf
B) spine
C) DC gateway
D) bridge

Unlock Deck
Unlock for access to all 39 flashcards in this deck.
Unlock Deck
k this deck


