Deck 7: Mist AI, Associate (JNCIA-MistAI)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/131
Play
Full screen (f)
Deck 7: Mist AI, Associate (JNCIA-MistAI)
1
Which three mechanisms are associated with the bridging process? (Choose three.)
A) blocking
B) flooding
C) aging
D) filtering
E) listening
A) blocking
B) flooding
C) aging
D) filtering
E) listening
flooding
aging
filtering
aging
filtering
2
What are two characteristics of OSPF ABRs? (Choose two.)
A) ABRs transmit routing information between the backbone and other areas.
B) ABRs cannot be part of the backbone and another area at the same time.
C) ABRs inject routing information from outside the OSPF domain.
D) ABRs link two OSPF areas.
A) ABRs transmit routing information between the backbone and other areas.
B) ABRs cannot be part of the backbone and another area at the same time.
C) ABRs inject routing information from outside the OSPF domain.
D) ABRs link two OSPF areas.
ABRs transmit routing information between the backbone and other areas.
ABRs link two OSPF areas.
ABRs link two OSPF areas.
3
Which two routes belong to the 172.16.0.0/22 aggregate route? (Choose two.)
A) 172.16.4.0/24
B) 172.16.0.0/24
C) 172.16.5.0/24
D) 172.16.3.0/24
A) 172.16.4.0/24
B) 172.16.0.0/24
C) 172.16.5.0/24
D) 172.16.3.0/24
172.16.0.0/24
172.16.3.0/24
172.16.3.0/24
4
Your network is configured with dynamic ARP inspection (DAI) using the default parameters for all the DHCP and ARP related configurations. You just added a new device connected to a trunk port and configured it to obtain an IP address using DHCP. Which two statements are correct in this scenario? (Choose two.)
A) The DHCP server assigns the IP addressing information to the new device.
B) DAI validates the ARP packets for the new device against the DHCP snooping database.
C) The ARP request and response packets for the new device will bypass DAI.
D) DHCP snooping adds the DHCP assigned IP address for the new device to its database.
A) The DHCP server assigns the IP addressing information to the new device.
B) DAI validates the ARP packets for the new device against the DHCP snooping database.
C) The ARP request and response packets for the new device will bypass DAI.
D) DHCP snooping adds the DHCP assigned IP address for the new device to its database.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
5
Which two port security features use the DHCP snooping database for additional port security? (Choose two.)
A) dynamic ARP inspection
B) MACsec
C) IP Source Guard
D) MAC learning
A) dynamic ARP inspection
B) MACsec
C) IP Source Guard
D) MAC learning

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
6
What are two reasons for configuring more than one VLAN on a switch? (Choose two.)
A) A group of clients requires that security be applied to traffic entering or exiting the group's devices.
B) A group of devices must forward traffic across a WAN.
C) A group of devices are connected to the same Layer 3 network.
D) A group of clients requires that the group's devices receive less broadcast traffic than they are currently receiving.
A) A group of clients requires that security be applied to traffic entering or exiting the group's devices.
B) A group of devices must forward traffic across a WAN.
C) A group of devices are connected to the same Layer 3 network.
D) A group of clients requires that the group's devices receive less broadcast traffic than they are currently receiving.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
7
Which static route next-hop value indicates that the packet will be silently dropped?
A) resolve
B) discard
C) reject
D) next-table
A) resolve
B) discard
C) reject
D) next-table

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
8
You want to advertise only a default route into a new area, which will be called area 7. In this scenario, which configuration statement would solve this problem?
A) user@host# set protocols ospf area 0.0.0.7 nssa default-lsa default-metric 10
B) user@host# set protocols ospf area 0.0.0.7 stub no-summaries
C) user@host# set protocols ospf area 0.0.0.7 stub default-metric 10
D) user@host# set protocols ospf area 0.0.0.7 stub
A) user@host# set protocols ospf area 0.0.0.7 nssa default-lsa default-metric 10
B) user@host# set protocols ospf area 0.0.0.7 stub no-summaries
C) user@host# set protocols ospf area 0.0.0.7 stub default-metric 10
D) user@host# set protocols ospf area 0.0.0.7 stub

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
9
Which statement is correct about trunk ports?
A) Trunk ports must have an IRB assigned to accept VLAN tagged traffic.
B) By default, trunk ports accept only VLAN tagged traffic.
C) By default, a trunk port can have only a single VLAN assigned.
D) Trunk ports must have an IRB assigned to accept untagged traffic.
A) Trunk ports must have an IRB assigned to accept VLAN tagged traffic.
B) By default, trunk ports accept only VLAN tagged traffic.
C) By default, a trunk port can have only a single VLAN assigned.
D) Trunk ports must have an IRB assigned to accept untagged traffic.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
10
Which statement is true about IP-IP tunnels?
A) Intermediate devices must have a route to the destination address of the traffic being tunneled.
B) Intermediate devices must have a route to both the tunnel source address and the tunnel destination address.
C) Intermediate devices must have a route to the tunnel destination address but do not require a route to the tunnel source address.
D) Intermediate devices must have a route to the tunnel source address but do not require a route to the tunnel destination address.
A) Intermediate devices must have a route to the destination address of the traffic being tunneled.
B) Intermediate devices must have a route to both the tunnel source address and the tunnel destination address.
C) Intermediate devices must have a route to the tunnel destination address but do not require a route to the tunnel source address.
D) Intermediate devices must have a route to the tunnel source address but do not require a route to the tunnel destination address.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
11
Which two sequences correctly describe the processing order of firewall filters on an EX Series switch? (Choose two.)
A) router filter > VLAN filter > port filter > transmit packet
B) port filter > VLAN filter > router filter > transmit packet
C) receive packet > port filter > VLAN filter > router filter
D) receive packet > router filter > VLAN filter > port filter
A) router filter > VLAN filter > port filter > transmit packet
B) port filter > VLAN filter > router filter > transmit packet
C) receive packet > port filter > VLAN filter > router filter
D) receive packet > router filter > VLAN filter > port filter

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
12
Which statement is correct about IS-IS link state PDUs?
A) They are used to maintain link-state database synchronization.
B) They are used to establish adjacencies.
C) They are used to build the link-state database.
D) They are used to determine whether the neighbors are Level 1 or Level 2.
A) They are used to maintain link-state database synchronization.
B) They are used to establish adjacencies.
C) They are used to build the link-state database.
D) They are used to determine whether the neighbors are Level 1 or Level 2.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
13
Which two OSPF header fields must match to form an adjacency over a broadcast connection? (Choose two.)
A) router priority
B) options
C) hello interval
D) neighbor
A) router priority
B) options
C) hello interval
D) neighbor

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
14
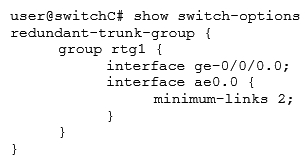
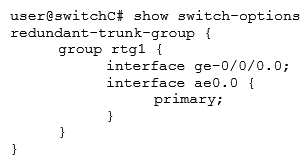
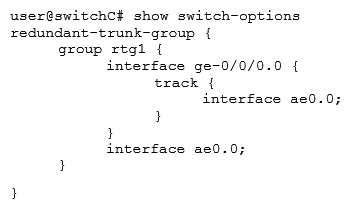
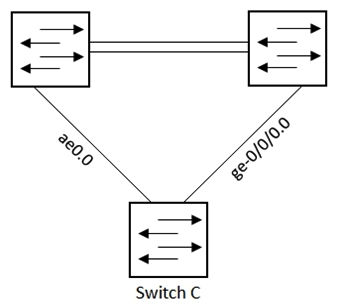 Referring to the exhibit, which configuration will force traffic to always use ae0.0 as long as it is active?
Referring to the exhibit, which configuration will force traffic to always use ae0.0 as long as it is active?A)
B)

C)
D)

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
15
Which Junos feature allows you to combine multiple interfaces into a single bundle?
A) VRRP
B) Virtual Chassis
C) LAG
D) NSB
A) VRRP
B) Virtual Chassis
C) LAG
D) NSB

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
16
Which two characteristics are true for EBGP peerings? (Choose two.)
A) EBGP peers must be directly connected.
B) EBGP connects peer devices in the same autonomous system.
C) EBGP connects peer devices in two different autonomous systems.
D) EBGP peers can be connected over a multihop connection.
A) EBGP peers must be directly connected.
B) EBGP connects peer devices in the same autonomous system.
C) EBGP connects peer devices in two different autonomous systems.
D) EBGP peers can be connected over a multihop connection.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
17
Which two statements are correct regarding the root bridge election process when using STP? (Choose two.)
A) A lower system MAC address is preferred.
B) A higher bridge priority is preferred.
C) A lower bridge priority is preferred.
D) A higher system MAC address is preferred.
A) A lower system MAC address is preferred.
B) A higher bridge priority is preferred.
C) A lower bridge priority is preferred.
D) A higher system MAC address is preferred.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
18
What are two benefits of 802.3ad link aggregation? (Choose two.)
A) It increases bandwidth.
B) It ensures symmetrical paths.
C) It simplifies interface configuration.
D) It creates physical layer redundancy.
A) It increases bandwidth.
B) It ensures symmetrical paths.
C) It simplifies interface configuration.
D) It creates physical layer redundancy.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
19
What are two advantages of a point-to-point OSPF adjacency? (Choose two.)
A) Only a DR is elected.
B) No type 1 LSAs are generated.
C) No type 2 LSAs are generated.
D) There is quicker neighbor establishment.
A) Only a DR is elected.
B) No type 1 LSAs are generated.
C) No type 2 LSAs are generated.
D) There is quicker neighbor establishment.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
20
When configuring firewall filters, which function does the interface-specific parameter enable on an EX Series switch?
A) The interface-specific parameter is required to configure port-specific counters. The parameter is required to configure port-specific counters.
B) The interface-specific parameter is required to configure VLAN-specific counters. parameter is required to configure VLAN-specific counters.
C) The interface-specific parameter is required to configure VLAN-based filters. parameter is required to configure VLAN-based filters.
D) The interface-specific parameter is required to configure port-based firewall filters. parameter is required to configure port-based firewall filters.
A) The interface-specific parameter is required to configure port-specific counters. The parameter is required to configure port-specific counters.
B) The interface-specific parameter is required to configure VLAN-specific counters. parameter is required to configure VLAN-specific counters.
C) The interface-specific parameter is required to configure VLAN-based filters. parameter is required to configure VLAN-based filters.
D) The interface-specific parameter is required to configure port-based firewall filters. parameter is required to configure port-based firewall filters.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
21
Click the Exhibit button. 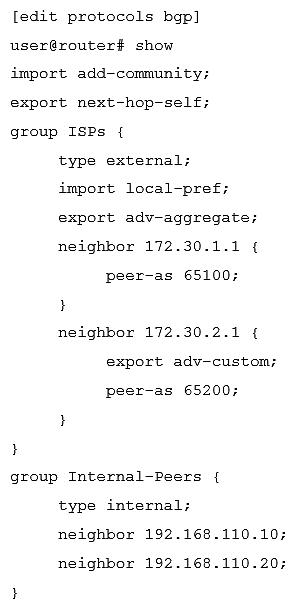 Which statement is true about the configuration shown in the exhibit?
Which statement is true about the configuration shown in the exhibit?
A) Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1 Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1
B) Only the add-community import policy will be evaluated when routes are learned from neighbor 172.30.1.1 add-community
C) No import policy will be evaluated when routes are learned from neighbor 172.30.2.1
D) Both the add-community and local-pref import policies will be evaluated when routes are learned from neighbor 172.30.2.1 Both the and import policies will be evaluated when routes are learned from neighbor 172.30.2.1
 Which statement is true about the configuration shown in the exhibit?
Which statement is true about the configuration shown in the exhibit?A) Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1 Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1
B) Only the add-community import policy will be evaluated when routes are learned from neighbor 172.30.1.1 add-community
C) No import policy will be evaluated when routes are learned from neighbor 172.30.2.1
D) Both the add-community and local-pref import policies will be evaluated when routes are learned from neighbor 172.30.2.1 Both the and import policies will be evaluated when routes are learned from neighbor 172.30.2.1

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
22
Which two statements about DHCP snooping are correct? (Choose two.)
A) DHCP snooping inspects all DHCP packets on untrusted ports.
B) By default, the Junos OS treats access ports as trusted and trunk ports as untrusted.
C) DHCP snooping uses ARP to add statically defined IP addresses to its database.
D) The DHCP database maps IP addresses, MAC addresses, and the associated VLAN.
A) DHCP snooping inspects all DHCP packets on untrusted ports.
B) By default, the Junos OS treats access ports as trusted and trunk ports as untrusted.
C) DHCP snooping uses ARP to add statically defined IP addresses to its database.
D) The DHCP database maps IP addresses, MAC addresses, and the associated VLAN.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
23
Click the Exhibit button. 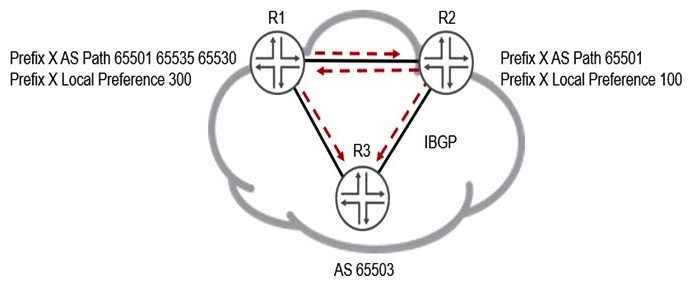 Both the R1 and R2 devices are advertising prefix X into AS 65530 with the BGP attributes shown in the exhibit. Which statement is correct in this scenario?
Both the R1 and R2 devices are advertising prefix X into AS 65530 with the BGP attributes shown in the exhibit. Which statement is correct in this scenario?
A) R2's version of prefix X will be active because of the local preference attribute.
B) R1's version of prefix X will be active because of the local preference attribute.
C) R1's version of prefix X will be active because of the AS path attribute.
D) R2's version of prefix X will be active because of the AS path attribute.
 Both the R1 and R2 devices are advertising prefix X into AS 65530 with the BGP attributes shown in the exhibit. Which statement is correct in this scenario?
Both the R1 and R2 devices are advertising prefix X into AS 65530 with the BGP attributes shown in the exhibit. Which statement is correct in this scenario?A) R2's version of prefix X will be active because of the local preference attribute.
B) R1's version of prefix X will be active because of the local preference attribute.
C) R1's version of prefix X will be active because of the AS path attribute.
D) R2's version of prefix X will be active because of the AS path attribute.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
24
What are two methods for reducing the size of an OSPF link-state database? (Choose two.)
A) Use unique router IDs where possible.
B) Use identical link metrics where possible.
C) Use point-to-point interface types where possible.
D) Use stub areas where possible.
A) Use unique router IDs where possible.
B) Use identical link metrics where possible.
C) Use point-to-point interface types where possible.
D) Use stub areas where possible.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
25
Click the Exhibit button. 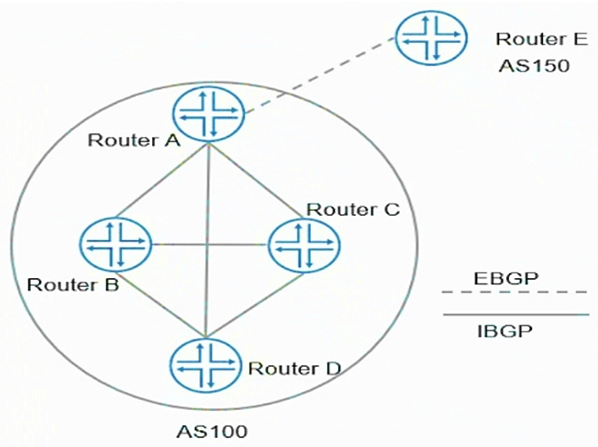 Referring to the exhibit, which two statements are correct? (Choose two.)
Referring to the exhibit, which two statements are correct? (Choose two.)
A) Router A does not send routes learned from Router E to Router B, Router C, and Router D
B) Router A sends routes learned from Router E to Router B, Router C, and Router D
C) Router A sends routes learned from Router D to Router B and Router C
D) Router A does not send routes learned from Router D to Router B and Router C
 Referring to the exhibit, which two statements are correct? (Choose two.)
Referring to the exhibit, which two statements are correct? (Choose two.)A) Router A does not send routes learned from Router E to Router B, Router C, and Router D
B) Router A sends routes learned from Router E to Router B, Router C, and Router D
C) Router A sends routes learned from Router D to Router B and Router C
D) Router A does not send routes learned from Router D to Router B and Router C

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
26
Which two statements are true about high availability on Junos devices? (Choose two.)
A) BFD is faster at detecting failures than default GRE or OSPF timers.
B) BFD is slower at detecting failures than default GRE or OSPF timers.
C) NSR is dependent on helper routers to assist the routing platform in restoring routing protocol information.
D) NSR is independent of helper routers to assist the routing platform in restoring routing protocol information.
A) BFD is faster at detecting failures than default GRE or OSPF timers.
B) BFD is slower at detecting failures than default GRE or OSPF timers.
C) NSR is dependent on helper routers to assist the routing platform in restoring routing protocol information.
D) NSR is independent of helper routers to assist the routing platform in restoring routing protocol information.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
27
You want to use filter-based forwarding (FBF) to forward traffic sourced from subnet 10.0.0.0/24 to a specific destination. Which two routing instance types would enable you to accomplish this task? (Choose two.)
A) virtual switch
B) virtual routing and forwarding
C) virtual router
D) forwarding
A) virtual switch
B) virtual routing and forwarding
C) virtual router
D) forwarding

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
28
When electing a DIS in an IS-IS network, what is used to break a priority tie?
A) highest MAC address
B) highest router ID
C) lowest MAC address
D) lowest router ID
A) highest MAC address
B) highest router ID
C) lowest MAC address
D) lowest router ID

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
29
What are two characteristics of IS-IS CSNPs? (Choose two.)
A) IS-IS CSNPs contain header information for all link-state PDUs.
B) IS-IS CSNPs are used to request a copy of a missing link state PDU.
C) IS-IS CSNPs are used to maintain the link-state database synchronization.
D) IS-IS CSNPs contain header information for specific requested link-state PDUs.
A) IS-IS CSNPs contain header information for all link-state PDUs.
B) IS-IS CSNPs are used to request a copy of a missing link state PDU.
C) IS-IS CSNPs are used to maintain the link-state database synchronization.
D) IS-IS CSNPs contain header information for specific requested link-state PDUs.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
30
Click the Exhibit button. 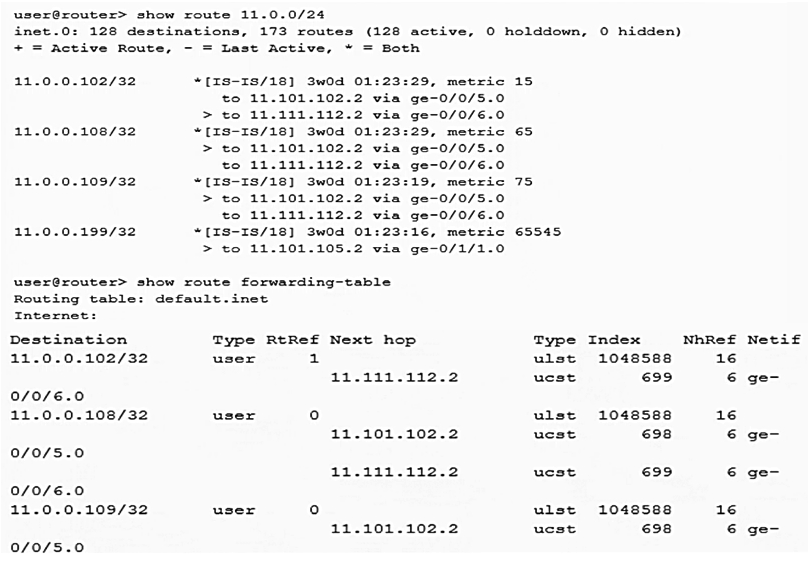 Referring to the output shown in the exhibit, which statement is correct?
Referring to the output shown in the exhibit, which statement is correct?
A) 11.0.0.108/32 is being per-flow load-balanced
B) 11.0.0.102/32 is being per-packet load-balanced
C) 11.0.0.102/32 is being per-flow load-balanced
D) 11.0.0.108/32 is being per-packet load-balanced
 Referring to the output shown in the exhibit, which statement is correct?
Referring to the output shown in the exhibit, which statement is correct?A) 11.0.0.108/32 is being per-flow load-balanced
B) 11.0.0.102/32 is being per-packet load-balanced
C) 11.0.0.102/32 is being per-flow load-balanced
D) 11.0.0.108/32 is being per-packet load-balanced

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
31
Click the Exhibit button. 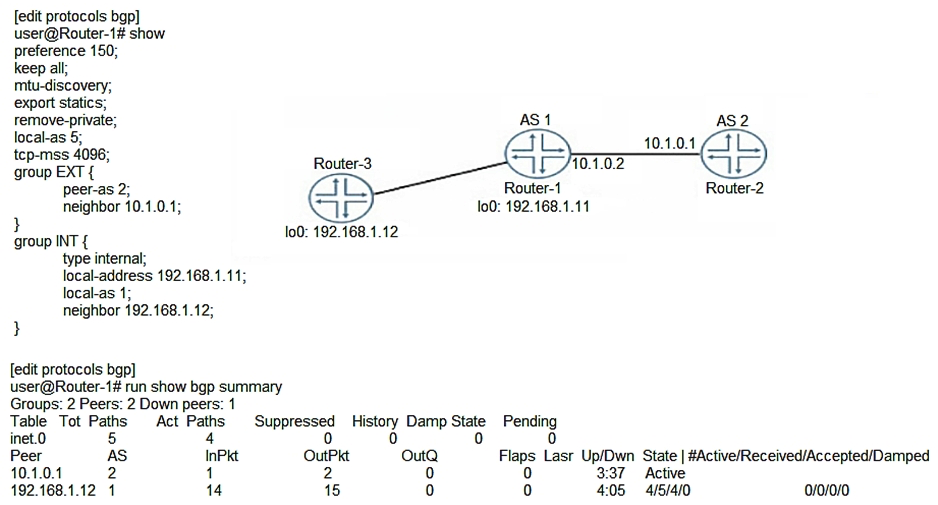 Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?
Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?
A) The TCP-MSS value is set too low
B) The EXT group is not configured as an external type BGP peering session The EXT group is not configured as an external type BGP peering session
C) The EBGP session is configured to use the wrong AS
D) The keep all statement is preventing the session from establishing keep all statement is preventing the session from establishing
 Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?
Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?A) The TCP-MSS value is set too low
B) The EXT group is not configured as an external type BGP peering session The EXT group is not configured as an external type BGP peering session
C) The EBGP session is configured to use the wrong AS
D) The keep all statement is preventing the session from establishing keep all statement is preventing the session from establishing

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
32
Click the Exhibit button. 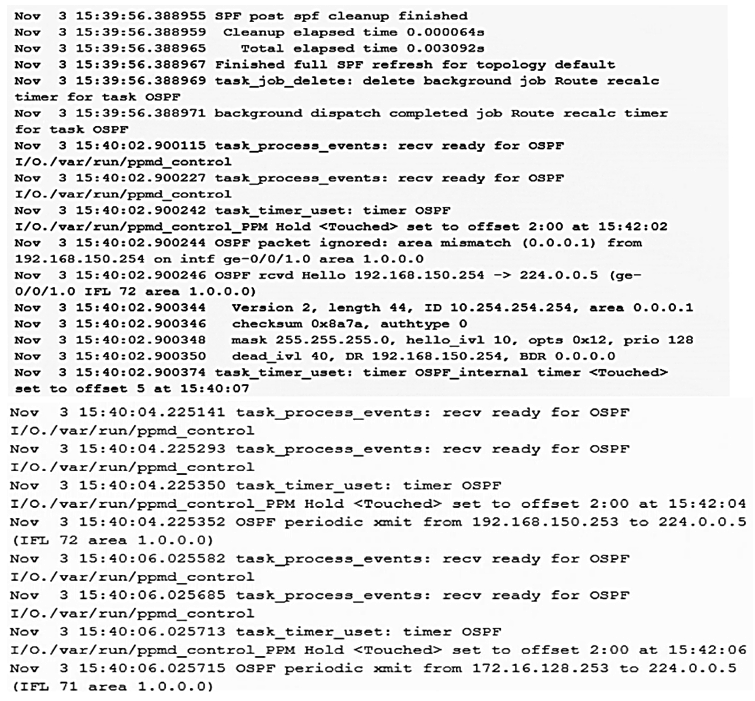 Based on the traceoptions output shown in the exhibit, what is the problem with the adjacency?
Based on the traceoptions output shown in the exhibit, what is the problem with the adjacency?
A) connectivity
B) authentication mismatch
C) MTU mismatch
D) area mismatch
 Based on the traceoptions output shown in the exhibit, what is the problem with the adjacency?
Based on the traceoptions output shown in the exhibit, what is the problem with the adjacency?A) connectivity
B) authentication mismatch
C) MTU mismatch
D) area mismatch

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
33
Click the Exhibit button. 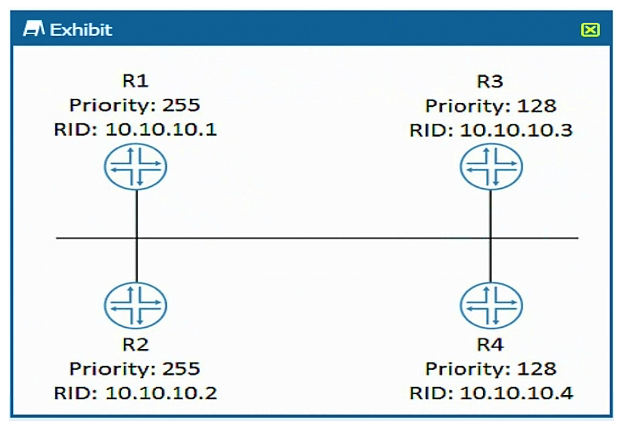 Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
A) R3
B) R4
C) R1
D) R2
 Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?A) R3
B) R4
C) R1
D) R2

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
34
Which statement is true when using LAGs with an EX4300?
A) Speeds on member links can differ.
B) Member links must be contiguous.
C) Half duplex is supported on the LAG.
D) You can have up to 16 member links per LAG.
A) Speeds on member links can differ.
B) Member links must be contiguous.
C) Half duplex is supported on the LAG.
D) You can have up to 16 member links per LAG.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
35
Click the Exhibit button. 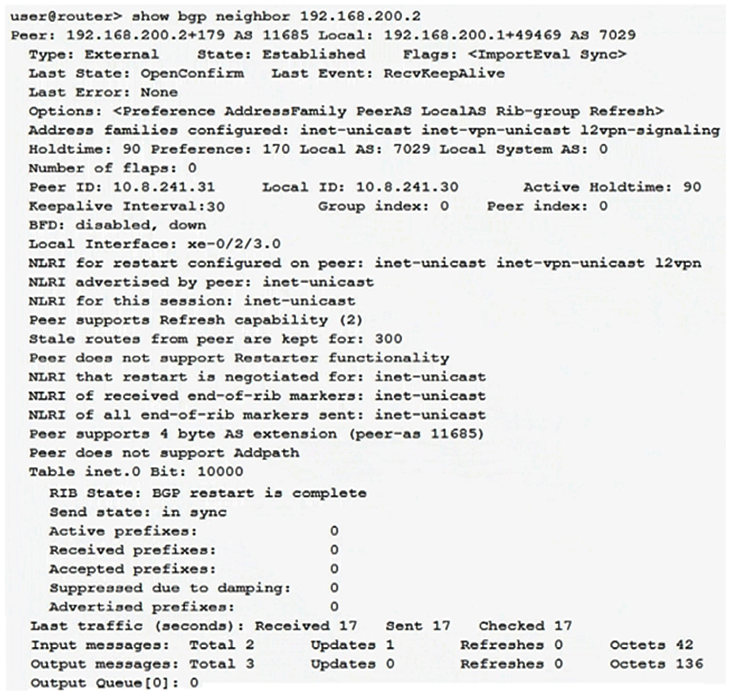 Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?
Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?
A) inet-unicast inet-vpn-unicast 12vpn-signaling
B) inet-unicast
C) inet-vpn-unicast
D) inet-unicast inet-vpn-unicast 12vpn
 Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?
Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?A) inet-unicast inet-vpn-unicast 12vpn-signaling
B) inet-unicast
C) inet-vpn-unicast
D) inet-unicast inet-vpn-unicast 12vpn

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
36
Click the Exhibit button. 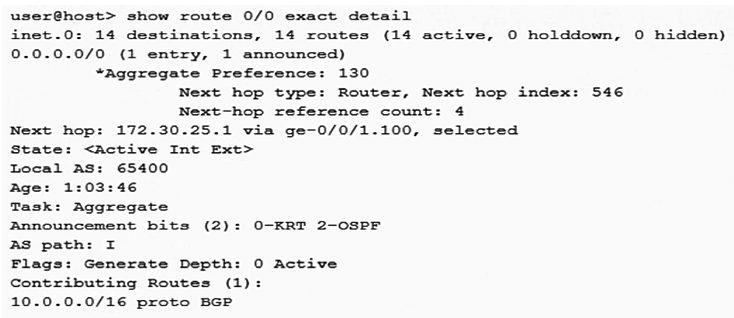 Referring to the output shown in the exhibit, which two statements are true? (Choose two.)
Referring to the output shown in the exhibit, which two statements are true? (Choose two.)
A) The route is active
B) The route is not active
C) The route is a generate route
D) The route is an aggregate route
 Referring to the output shown in the exhibit, which two statements are true? (Choose two.)
Referring to the output shown in the exhibit, which two statements are true? (Choose two.)A) The route is active
B) The route is not active
C) The route is a generate route
D) The route is an aggregate route

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
37
What are two interarea OSPF LSA types? (Choose two.)
A) Type 1 router LSAs
B) Type 3 summary LSAs
C) Type 4 ASBR summary LSAs
D) Type 2 network LSAs
A) Type 1 router LSAs
B) Type 3 summary LSAs
C) Type 4 ASBR summary LSAs
D) Type 2 network LSAs

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
38
Which OSPF packet type is sent when an OSPF router detects its database is stale?
A) database description
B) link-state acknowledgment
C) link-state request
D) hello
A) database description
B) link-state acknowledgment
C) link-state request
D) hello

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
39
Click the Exhibit button. 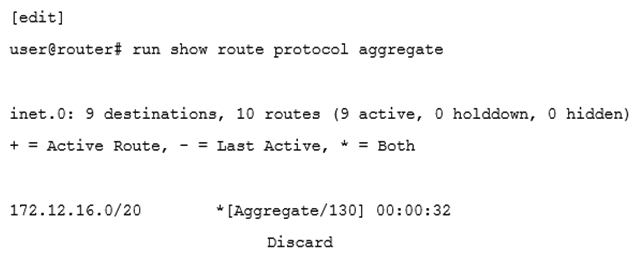 Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
A) 172.12.31.0/24
B) 172.12.33.0/24
C) 172.12.30.0/24
D) 172.12.32.0/24
 Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)A) 172.12.31.0/24
B) 172.12.33.0/24
C) 172.12.30.0/24
D) 172.12.32.0/24

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
40
What are the three possible port states when using RSTP? (Choose three.)
A) forwarding
B) learning
C) discarding
D) listening
E) tagging
A) forwarding
B) learning
C) discarding
D) listening
E) tagging

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
41
Which two statements describe NSR? (Choose two.)
A) NSR requires GRES to function properly.
B) NSR provides routing loop protection.
C) NSR rapidly detects link failures.
D) NSR provides high availability with multiple Routing Engines.
A) NSR requires GRES to function properly.
B) NSR provides routing loop protection.
C) NSR rapidly detects link failures.
D) NSR provides high availability with multiple Routing Engines.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
42
Click the Exhibit button. 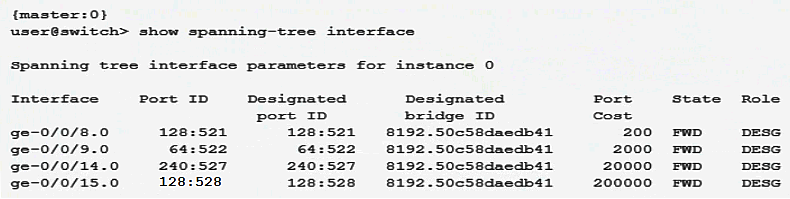 Based on the output shown in the exhibit, which statement is correct?
Based on the output shown in the exhibit, which statement is correct?
A) The ge-0/0/9 interface is using the default interface priority value.
B) This switch has a bridge priority of 8k.
C) This switch is currently blocking all traffic.
D) The ge-0/0/15 interface is using the default port cost.
 Based on the output shown in the exhibit, which statement is correct?
Based on the output shown in the exhibit, which statement is correct?A) The ge-0/0/9 interface is using the default interface priority value.
B) This switch has a bridge priority of 8k.
C) This switch is currently blocking all traffic.
D) The ge-0/0/15 interface is using the default port cost.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
43
Click the Exhibit button. 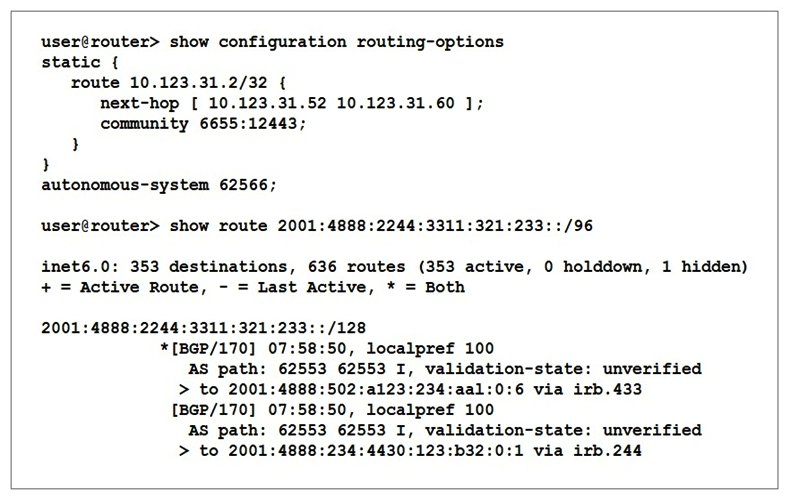 Referring to the exhibit, which two statements are correct? (Choose two.)
Referring to the exhibit, which two statements are correct? (Choose two.)
A) The AS path shows two hops to other IBGP routers within autonomous system 62553.
B) The active path to 2001:4888:2244:3311:321:233::/128 will exit using interface irb.433.
C) Route 2001:4888:2244:3311:321:233::/128 will be advertised to an EBGP peer in AS 62553.
D) Route 2001:4888:2244:3311:321:233::/128 has been prepended.
 Referring to the exhibit, which two statements are correct? (Choose two.)
Referring to the exhibit, which two statements are correct? (Choose two.)A) The AS path shows two hops to other IBGP routers within autonomous system 62553.
B) The active path to 2001:4888:2244:3311:321:233::/128 will exit using interface irb.433.
C) Route 2001:4888:2244:3311:321:233::/128 will be advertised to an EBGP peer in AS 62553.
D) Route 2001:4888:2244:3311:321:233::/128 has been prepended.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
44
Which mechanism is used to share routes between routing tables?
A) RIB groups
B) routing instances
C) forwarding instances
D) filter-based forwarding
A) RIB groups
B) routing instances
C) forwarding instances
D) filter-based forwarding

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
45
Click the Exhibit button. 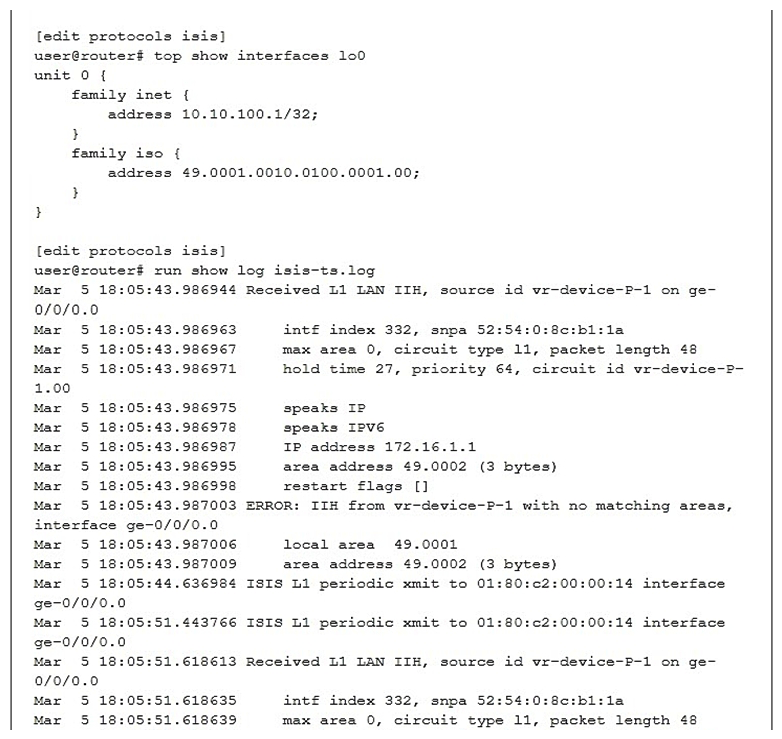 Referring to the exhibit, the local router should have an IS-IS adjacency with a neighboring router, but the adjacency never establishes correctly. What should you do to solve the problem?
Referring to the exhibit, the local router should have an IS-IS adjacency with a neighboring router, but the adjacency never establishes correctly. What should you do to solve the problem?
A) Disable level 2 for the interfaces.
B) Disable level 1 for the interfaces.
C) Disable wide metrics.
D) Change the local IS-IS area ID to 49.0002.
 Referring to the exhibit, the local router should have an IS-IS adjacency with a neighboring router, but the adjacency never establishes correctly. What should you do to solve the problem?
Referring to the exhibit, the local router should have an IS-IS adjacency with a neighboring router, but the adjacency never establishes correctly. What should you do to solve the problem?A) Disable level 2 for the interfaces.
B) Disable level 1 for the interfaces.
C) Disable wide metrics.
D) Change the local IS-IS area ID to 49.0002.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
46
Which statement about configuring persistent MAC learning is correct?
A) Persistent MAC learning requires 802.1X authentication.
B) Persistent MAC learning can be configured on access mode interfaces.
C) Persistent MAC learning flushes dynamically learned MAC addresses on reboots.
D) Persistent MAC learning cannot be configured on redundant trunk groups.
A) Persistent MAC learning requires 802.1X authentication.
B) Persistent MAC learning can be configured on access mode interfaces.
C) Persistent MAC learning flushes dynamically learned MAC addresses on reboots.
D) Persistent MAC learning cannot be configured on redundant trunk groups.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
47
Which two statements are correct regarding the root bridge election process when using STP? (Choose two.)
A) A lower system MAC address is preferred.
B) A higher bridge priority is preferred.
C) A lower bridge priority is preferred.
D) A higher system MAC address is preferred.
A) A lower system MAC address is preferred.
B) A higher bridge priority is preferred.
C) A lower bridge priority is preferred.
D) A higher system MAC address is preferred.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
48
Which two port security features use the DHCP snooping database for additional port security? (Choose two.)
A) dynamic ARP inspection
B) MACsec
C) IP Source Guard
D) MAC learning
A) dynamic ARP inspection
B) MACsec
C) IP Source Guard
D) MAC learning

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
49
Click the Exhibit button. 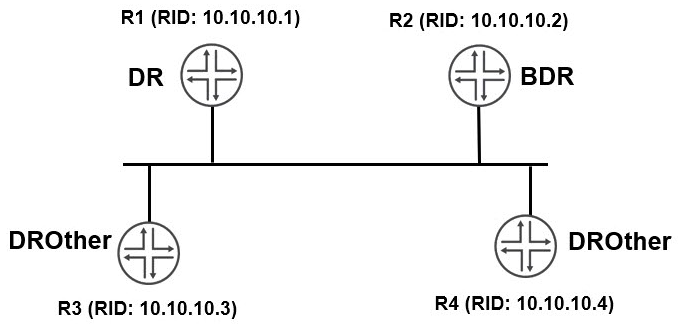 You have configured OSPF routing as shown in the exhibit. You notice that all interfaces have formed full adjacencies, with the exception of the interfaces connecting R3 and R4 with a status of 2Way . What is the reason for this status?
You have configured OSPF routing as shown in the exhibit. You notice that all interfaces have formed full adjacencies, with the exception of the interfaces connecting R3 and R4 with a status of 2Way . What is the reason for this status?
A) The two routers must both be configured as DR routers.
B) DROther routers will not form a full adjacency with each other.
C) The two routers must be configured in different areas.
D) The interface-type is not configured as p2p . The interface-type is not configured as p2p
 You have configured OSPF routing as shown in the exhibit. You notice that all interfaces have formed full adjacencies, with the exception of the interfaces connecting R3 and R4 with a status of 2Way . What is the reason for this status?
You have configured OSPF routing as shown in the exhibit. You notice that all interfaces have formed full adjacencies, with the exception of the interfaces connecting R3 and R4 with a status of 2Way . What is the reason for this status?A) The two routers must both be configured as DR routers.
B) DROther routers will not form a full adjacency with each other.
C) The two routers must be configured in different areas.
D) The interface-type is not configured as p2p . The interface-type is not configured as p2p

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
50
Which two statements are true about an EX2300 device? (Choose two.)
A) By default, trunk ports can carry untagged traffic.
B) By default, all switch ports are trunk ports.
C) By default, all switch ports are access ports.
D) By default, all switch ports are associated with the default VLAN.
A) By default, trunk ports can carry untagged traffic.
B) By default, all switch ports are trunk ports.
C) By default, all switch ports are access ports.
D) By default, all switch ports are associated with the default VLAN.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
51
Click the Exhibit button. 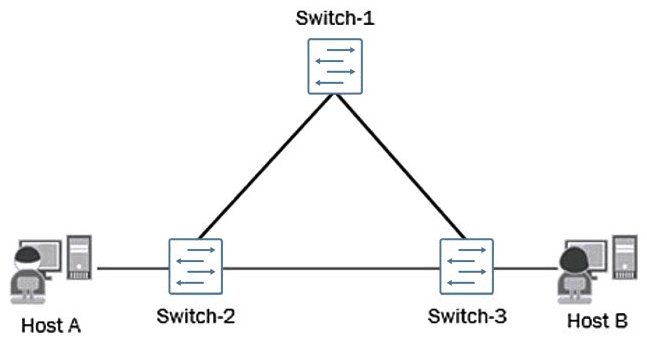 A number of reports from end users indicate that internal and external communications are intermittent and not reliable. You verified the status of the switch ports and have determined that they are up and operational. You also noticed a very high level of link bandwidth utilization on those same ports. The current topology of the affected environment is shown in the exhibit. What would be the cause of the reported issues?
A number of reports from end users indicate that internal and external communications are intermittent and not reliable. You verified the status of the switch ports and have determined that they are up and operational. You also noticed a very high level of link bandwidth utilization on those same ports. The current topology of the affected environment is shown in the exhibit. What would be the cause of the reported issues?
A) A misconfigured interior gateway protocol (IGP).
B) A lack of a loop-prevention mechanism or protocol.
C) A lack of port-based ACLs filtering the traffic flows.
D) A malformed route-based ACL improperly filtering traffic flows.
 A number of reports from end users indicate that internal and external communications are intermittent and not reliable. You verified the status of the switch ports and have determined that they are up and operational. You also noticed a very high level of link bandwidth utilization on those same ports. The current topology of the affected environment is shown in the exhibit. What would be the cause of the reported issues?
A number of reports from end users indicate that internal and external communications are intermittent and not reliable. You verified the status of the switch ports and have determined that they are up and operational. You also noticed a very high level of link bandwidth utilization on those same ports. The current topology of the affected environment is shown in the exhibit. What would be the cause of the reported issues?A) A misconfigured interior gateway protocol (IGP).
B) A lack of a loop-prevention mechanism or protocol.
C) A lack of port-based ACLs filtering the traffic flows.
D) A malformed route-based ACL improperly filtering traffic flows.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
52
Which statement is true about IP-IP tunnels?
A) Intermediate devices must have a route to the destination address of the traffic being tunneled.
B) Intermediate devices must have a route to both the tunnel source address and the tunnel destination address.
C) Intermediate devices must have a route to the tunnel destination address but do not require a route to the tunnel source address.
D) Intermediate devices must have a route to the tunnel source address but do not require a route to the tunnel destination address.
A) Intermediate devices must have a route to the destination address of the traffic being tunneled.
B) Intermediate devices must have a route to both the tunnel source address and the tunnel destination address.
C) Intermediate devices must have a route to the tunnel destination address but do not require a route to the tunnel source address.
D) Intermediate devices must have a route to the tunnel source address but do not require a route to the tunnel destination address.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
53
Which statement is correct about trunk ports?
A) Trunk ports must have an IRB assigned to accept VLAN tagged traffic.
B) By default, trunk ports accept only VLAN tagged traffic.
C) By default, a trunk port can have only a single VLAN assigned.
D) trunk ports must have an IRB assigned to accept untagged traffic.
A) Trunk ports must have an IRB assigned to accept VLAN tagged traffic.
B) By default, trunk ports accept only VLAN tagged traffic.
C) By default, a trunk port can have only a single VLAN assigned.
D) trunk ports must have an IRB assigned to accept untagged traffic.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
54
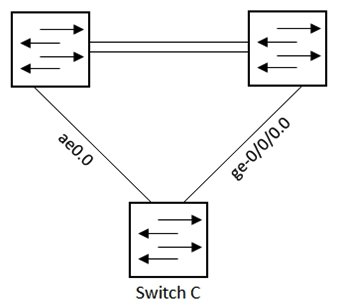 Referring to the exhibit, which configuration will force traffic to always use ae0.0 as long as it is active?
Referring to the exhibit, which configuration will force traffic to always use ae0.0 as long as it is active?A)
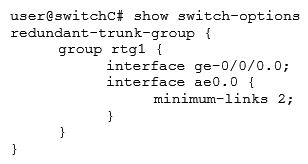
B)

C)
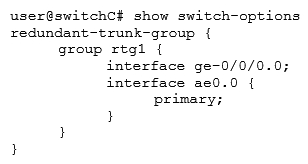
D)
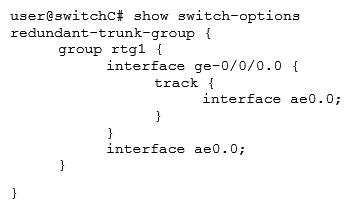

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
55
Which two characteristics are true for EBGP peerings? (Choose two.)
A) EBGP peers must be directly connected.
B) EBGP connects peer devices in the same autonomous system.
C) EBGP connects peer devices in two different autonomous systems.
D) EBGP peers can be connected over a multihop connection.
A) EBGP peers must be directly connected.
B) EBGP connects peer devices in the same autonomous system.
C) EBGP connects peer devices in two different autonomous systems.
D) EBGP peers can be connected over a multihop connection.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
56
Your network is configured with dynamic ARP inspection (DAI) using the default parameters for all the DHCP and ARP related configurations. You just added a new device connected to a trunk port and configured it to obtain an IP address using DHCP. Which two statements are correct in this scenario? (Choose two.)
A) The DHCP server assigns the IP addressing information to the new device.
B) DAI validates the ARP packets for the new device against the DHCP snooping database.
C) The ARP request and response packets for the new device will bypass DAI.
D) DHCP snooping adds the DHCP assigned IP address for the new device to its database.
A) The DHCP server assigns the IP addressing information to the new device.
B) DAI validates the ARP packets for the new device against the DHCP snooping database.
C) The ARP request and response packets for the new device will bypass DAI.
D) DHCP snooping adds the DHCP assigned IP address for the new device to its database.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
57
You have a conference room with an open network port that is used by employees to connect to the network. You are concerned about rogue switches being connected to this port. Which two features should you enable on your switch to limit access to this port? (Choose two.)
A) DHCP snooping
B) dynamic ARP inspection
C) MAC limiting
D) 802.1X
A) DHCP snooping
B) dynamic ARP inspection
C) MAC limiting
D) 802.1X

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
58
How many bytes of overhead does an IP-IP tunnel add to a packet?
A) 20 bytes
B) 24 bytes
C) 28 bytes
D) 14 bytes
A) 20 bytes
B) 24 bytes
C) 28 bytes
D) 14 bytes

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
59
Click the Exhibit button. 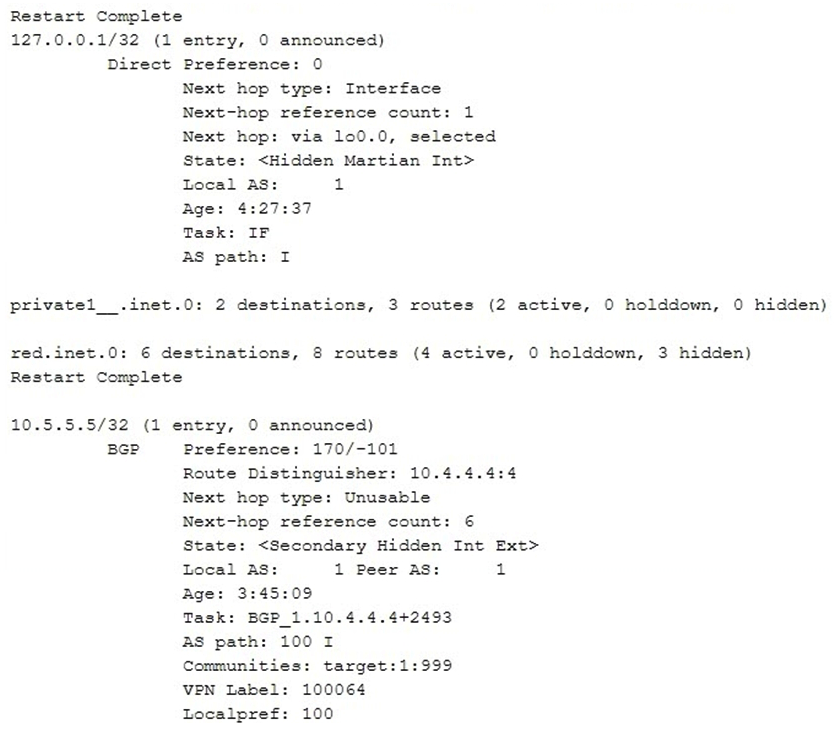 Referring to the exhibit, why is the route for 10.5.5.5 hidden?
Referring to the exhibit, why is the route for 10.5.5.5 hidden?
A) It is a martian route.
B) It has an invalid community.
C) It is an L3VPN route.
D) The next hop cannot be resolved.
 Referring to the exhibit, why is the route for 10.5.5.5 hidden?
Referring to the exhibit, why is the route for 10.5.5.5 hidden?A) It is a martian route.
B) It has an invalid community.
C) It is an L3VPN route.
D) The next hop cannot be resolved.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
60
Which statement is correct about IS-IS link state PDUs?
A) They are used to maintain link-state database synchronization.
B) They are used to establish adjacencies.
C) They are used to build the link-state database.
D) They are used to determine whether the neighbors are Level 1 or Level 2.
A) They are used to maintain link-state database synchronization.
B) They are used to establish adjacencies.
C) They are used to build the link-state database.
D) They are used to determine whether the neighbors are Level 1 or Level 2.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
61
Click the Exhibit button. 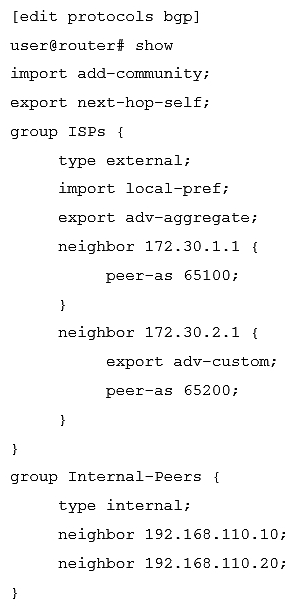 Which statement is true about the configuration shown in the exhibit?
Which statement is true about the configuration shown in the exhibit?
A) Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1 Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1
B) Only the add-community import policy will be evaluated when routes are learned from neighbor 172.30.1.1 add-community
C) No import policy will be evaluated when routes are learned from neighbor 172.30.2.1
D) Both the add-community and local-pref import policies will be evaluated when routes are learned from neighbor 172.30.2.1 Both the and import policies will be evaluated when routes are learned from neighbor 172.30.2.1
 Which statement is true about the configuration shown in the exhibit?
Which statement is true about the configuration shown in the exhibit?A) Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1 Only the local-pref import policy will be evaluated when routes are learned from neighbor 172.30.1.1
B) Only the add-community import policy will be evaluated when routes are learned from neighbor 172.30.1.1 add-community
C) No import policy will be evaluated when routes are learned from neighbor 172.30.2.1
D) Both the add-community and local-pref import policies will be evaluated when routes are learned from neighbor 172.30.2.1 Both the and import policies will be evaluated when routes are learned from neighbor 172.30.2.1

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
62
You configured a GRE tunnel that traverses a path using default MTU settings. You want to ensure that packets are not dropped of fragmented. In this scenario, what is the maximum packet size that would traverse the GRE tunnel?
A) 1500
B) 1400
C) 1524
D) 1476
A) 1500
B) 1400
C) 1524
D) 1476

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
63
You are enabling dynamic ARP inspection on an EX4300 switch. Which service is enabled by default in this scenario?
A) DHCP snooping
B) persistent MAC learning
C) MAC limiting
D) IP Source Guard
A) DHCP snooping
B) persistent MAC learning
C) MAC limiting
D) IP Source Guard

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
64
Click the Exhibit button. 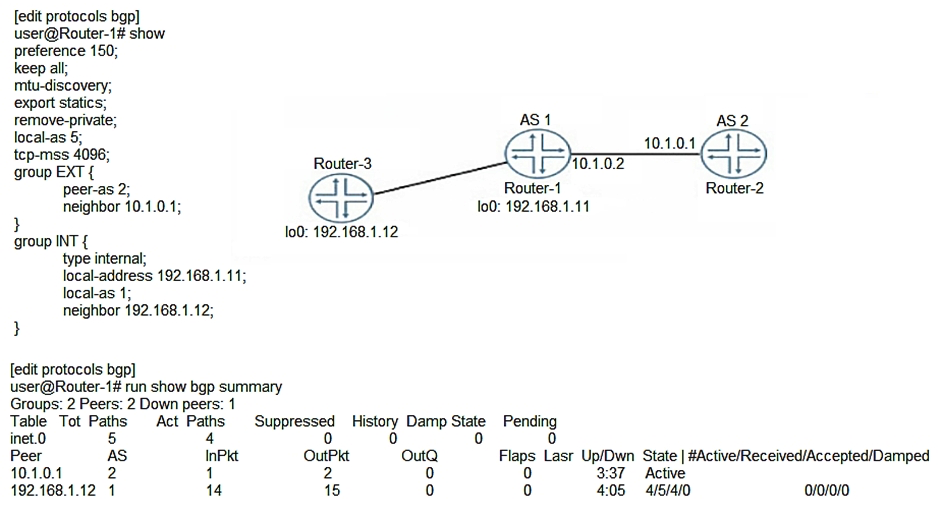 Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?
Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?
A) The TCP-MSS value is set too low
B) The EXT group is not configured as an external type BGP peering session The EXT group is not configured as an external type BGP peering session
C) The EBGP session is configured to use the wrong AS
D) The keep all statement is preventing the session from establishing keep all statement is preventing the session from establishing
 Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?
Referring to the exhibit, Router-1 is attempting to form an EBGP session with Router-2. However, BGP routes are never exchanged between Router-1 and Router-2. What is causing the problem?A) The TCP-MSS value is set too low
B) The EXT group is not configured as an external type BGP peering session The EXT group is not configured as an external type BGP peering session
C) The EBGP session is configured to use the wrong AS
D) The keep all statement is preventing the session from establishing keep all statement is preventing the session from establishing

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
65
Which two requirements must be satisfied before graceful restart will work? (Choose two.)
A) a stable network topology
B) a neighbor configured with BFD
C) a neighbor configured with graceful restart
D) a neighbor with an uptime greater than an hour
A) a stable network topology
B) a neighbor configured with BFD
C) a neighbor configured with graceful restart
D) a neighbor with an uptime greater than an hour

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
66
Click the Exhibit button. 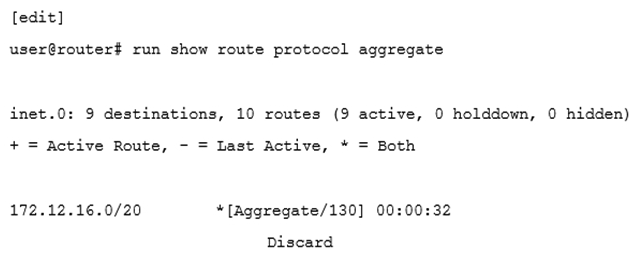 Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
A) 172.12.31.0/24
B) 172.12.33.0/24
C) 172.12.30.0/24
D) 172.12.32.0/24
 Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)
Given the route shown in the exhibit, which two prefixes contribute to the aggregate route? (Choose two.)A) 172.12.31.0/24
B) 172.12.33.0/24
C) 172.12.30.0/24
D) 172.12.32.0/24

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
67
Your network connections to the Internet through two different ISPs using EBGP. You must ensure that ISP1 is the primary path used for all traffic entering your network while using ISP2 as a backup path. In this scenario, which statement is correct?
A) You should use a lower MED value on routes sent to ISP1.
B) You should assign a higher local preference on routes that you are sending to ISP1.
C) You should change the next hop for all routers sent to ISP2.
D) You should prepend your local AS number three times on routes that you are sending to ISP2.
A) You should use a lower MED value on routes sent to ISP1.
B) You should assign a higher local preference on routes that you are sending to ISP1.
C) You should change the next hop for all routers sent to ISP2.
D) You should prepend your local AS number three times on routes that you are sending to ISP2.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
68
Which static route next-hop value indicates that the packet will be silently dropped?
A) resolve
B) discard
C) reject
D) next-table
A) resolve
B) discard
C) reject
D) next-table

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
69
Click the Exhibit button. 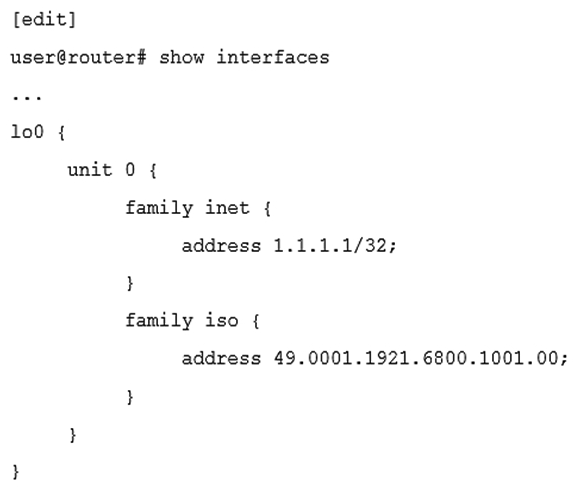 Which statement is correct about the ISO NET address shown in the exhibit?
Which statement is correct about the ISO NET address shown in the exhibit?
A) The system identifier is 6800.1001.00
B) The area identifier is 0001
C) The authority and format identifier (AFI) is 00
D) This is not a valid NET address
 Which statement is correct about the ISO NET address shown in the exhibit?
Which statement is correct about the ISO NET address shown in the exhibit?A) The system identifier is 6800.1001.00
B) The area identifier is 0001
C) The authority and format identifier (AFI) is 00
D) This is not a valid NET address

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
70
You want to advertise only a default route into a new area, which will be called area 7. In this scenario, which configuration statement would solve this problem?
A) user@host# set protocols ospf area 0.0.0.7 nssa default-lsa default-metric 10
B) user@host# set protocols ospf area 0.0.0.7 stub no-summaries
C) user@host# set protocols ospf area 0.0.0.7 stub default-metric 10
D) user@host# set protocols ospf area 0.0.0.7 stub
A) user@host# set protocols ospf area 0.0.0.7 nssa default-lsa default-metric 10
B) user@host# set protocols ospf area 0.0.0.7 stub no-summaries
C) user@host# set protocols ospf area 0.0.0.7 stub default-metric 10
D) user@host# set protocols ospf area 0.0.0.7 stub

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
71
You are adding a new EX4300 member switch to your existing EX4300 Virtual Chassis. However, the new member is not running the same Junos version as the other members. By default, what is the expected behavior in this scenario?
A) the Virtual Chassis will transition into a split brain situation between the existing master Routing Engine and the switch running the different version.
B) The new switch will automatically pull the correct version from the master Routing Engine and perform the necessary upgrade.
C) The new switch will be assigned a member ID and then placed in an inactive state.
D) The new switch is not recognized by the Virtual Chassis.
A) the Virtual Chassis will transition into a split brain situation between the existing master Routing Engine and the switch running the different version.
B) The new switch will automatically pull the correct version from the master Routing Engine and perform the necessary upgrade.
C) The new switch will be assigned a member ID and then placed in an inactive state.
D) The new switch is not recognized by the Virtual Chassis.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
72
Click the Exhibit button. 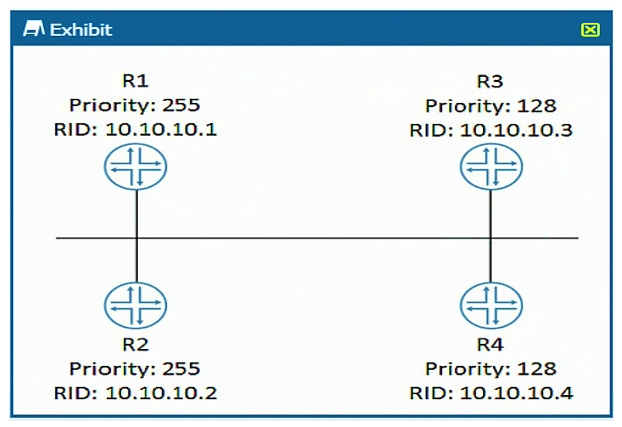 Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
A) R3
B) R4
C) R1
D) R2
 Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?
Referring to the exhibit, which router becomes the OSPF DR when all routers are powered on at the same time?A) R3
B) R4
C) R1
D) R2

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
73
What are two characteristics of IS-IS CSNPs? (Choose two.)
A) IS-IS CSNPs contain header information for all link-state PDUs.
B) IS-IS CSNPs are used to request a copy of a missing link state PDU.
C) IS-IS CSNPs are used to maintain the link-state database synchronization.
D) IS-IS CSNPs contain header information for specific requested link-state PDUs.
A) IS-IS CSNPs contain header information for all link-state PDUs.
B) IS-IS CSNPs are used to request a copy of a missing link state PDU.
C) IS-IS CSNPs are used to maintain the link-state database synchronization.
D) IS-IS CSNPs contain header information for specific requested link-state PDUs.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
74
Click the Exhibit button. 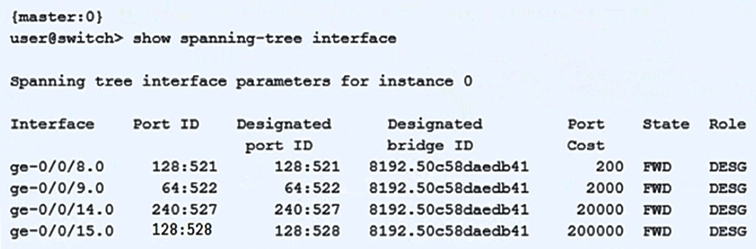 Based on the output shown in the exhibit, which statement is correct?
Based on the output shown in the exhibit, which statement is correct?
A) This switch has been elected as the root bridge
B) This switch has a bridge priority of 32k
C) The ge-0/0/15 interface is using the default port cost
D) The ge-0/0/9 interface is using the default priority value
 Based on the output shown in the exhibit, which statement is correct?
Based on the output shown in the exhibit, which statement is correct?A) This switch has been elected as the root bridge
B) This switch has a bridge priority of 32k
C) The ge-0/0/15 interface is using the default port cost
D) The ge-0/0/9 interface is using the default priority value

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
75
Which two statements describe BGP attributes? (Choose two.)
A) BGP attributes help determine the best path to a destination.
B) The origin attribute indicates the autonomous systems through which the route has traversed.
C) BGP attributes are always optional.
D) The AS path attribute indicates the autonomous systems through which the route has traversed.
A) BGP attributes help determine the best path to a destination.
B) The origin attribute indicates the autonomous systems through which the route has traversed.
C) BGP attributes are always optional.
D) The AS path attribute indicates the autonomous systems through which the route has traversed.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
76
You have configured the router with an IS-IS interface metric of 2048. However, the IS-IS interface metric of 63 is being applied for the interface of this router. What must you do to enable the larger metric value?
A) Enable wide metrics.
B) Disable narrow metrics.
C) Restart the IS-IS protocol.
D) Enable level 1 IS-IS routing.
A) Enable wide metrics.
B) Disable narrow metrics.
C) Restart the IS-IS protocol.
D) Enable level 1 IS-IS routing.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
77
When configuring firewall filters, which function does the interface-specific parameter enable on an EX Series switch?
A) The interface-specific parameter is required to configure port-specific counters. The parameter is required to configure port-specific counters.
B) The interface-specific parameter is required to configure VLAN-specific counters. parameter is required to configure VLAN-specific counters.
C) The interface-specific parameter is required to configure VLAN-based filters. parameter is required to configure VLAN-based filters.
D) The interface-specific parameter is required to configure port-based firewall filters. parameter is required to configure port-based firewall filters.
A) The interface-specific parameter is required to configure port-specific counters. The parameter is required to configure port-specific counters.
B) The interface-specific parameter is required to configure VLAN-specific counters. parameter is required to configure VLAN-specific counters.
C) The interface-specific parameter is required to configure VLAN-based filters. parameter is required to configure VLAN-based filters.
D) The interface-specific parameter is required to configure port-based firewall filters. parameter is required to configure port-based firewall filters.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
78
Which device is used to separate collision domains?
A) switch
B) router
C) hub
D) firewall
A) switch
B) router
C) hub
D) firewall

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
79
You added a new ESXi host connected to port ge-0/0/1. One of the VMs configured with VLAN 10 is not reachable from any other device on the switch. To troubleshoot, you decide to verify if the VM's MAC address is learned properly under VLAN 10. Which command would you use in this scenario?
A) show ethernet-switching table vlan-id 10
B) show interfaces ge-0/0/1 detail
C) show vlans 10
D) monitor interface ge-0/0/1
A) show ethernet-switching table vlan-id 10
B) show interfaces ge-0/0/1 detail
C) show vlans 10
D) monitor interface ge-0/0/1

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
80
Click the Exhibit button. 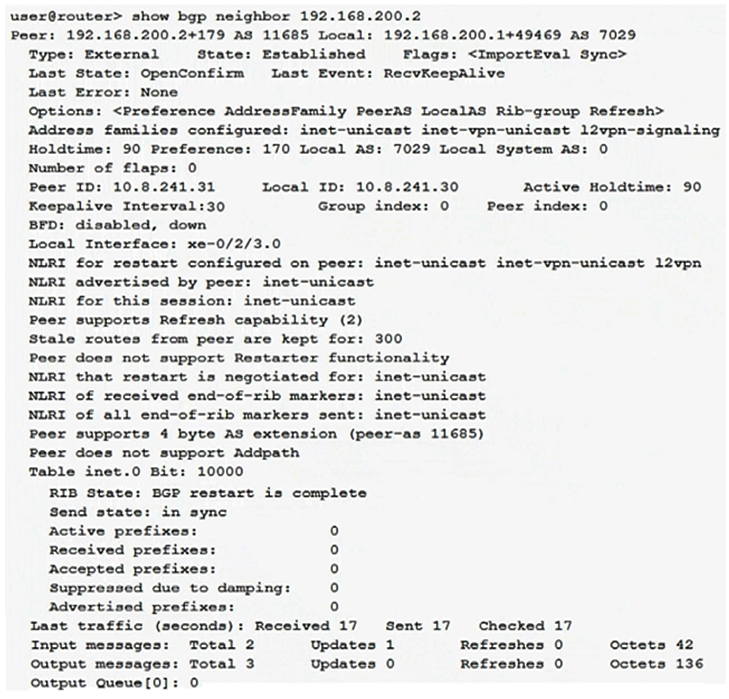 Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?
Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?
A) inet-unicast inet-vpn-unicast 12vpn-signaling
B) inet-unicast
C) inet-vpn-unicast
D) inet-unicast inet-vpn-unicast 12vpn
 Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?
Your router is configured to peer with your ISP's router using BGP. You can only control your BGP configuration. Which address families are negotiated between the two BGP peers shown in the exhibit?A) inet-unicast inet-vpn-unicast 12vpn-signaling
B) inet-unicast
C) inet-vpn-unicast
D) inet-unicast inet-vpn-unicast 12vpn

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck


