Deck 22: Securing Networks with Cisco Firepower (300-710 SNCF)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/65
Play
Full screen (f)
Deck 22: Securing Networks with Cisco Firepower (300-710 SNCF)
1
When a local RBAC user account has the same name as a remote user account on an AAA server, what happens when a user with that name logs into a Cisco Nexus switch?
A) The user roles from the remote AAA user account are applied, not the configured local user roles.
B) All the roles are merged (logical OR).
C) The user roles from the local user account are applied, not the remote AAA user roles.
D) Only the roles that are defined on both accounts are merged (logical AND).
A) The user roles from the remote AAA user account are applied, not the configured local user roles.
B) All the roles are merged (logical OR).
C) The user roles from the local user account are applied, not the remote AAA user roles.
D) Only the roles that are defined on both accounts are merged (logical AND).
The user roles from the local user account are applied, not the remote AAA user roles.
2
You plan to implement the OSPF protocol whithin the data center network. Which two statements accurately describe OSPF on the Cisco NX-OS platform? (Choose two.)
A) The default reference bandwidth is 10 Gbps.
B) OSPF does not require additional licenses.
C) The OSPF area can be configured by using decimal notation only.
D) Redistributing routes into OSPF requires a route map.
E) The secondary IP address is advertised by default.
A) The default reference bandwidth is 10 Gbps.
B) OSPF does not require additional licenses.
C) The OSPF area can be configured by using decimal notation only.
D) Redistributing routes into OSPF requires a route map.
E) The secondary IP address is advertised by default.
The OSPF area can be configured by using decimal notation only.
Redistributing routes into OSPF requires a route map.
Redistributing routes into OSPF requires a route map.
3
You create a checkpoint on a Cisco Nexus 7700 Series switch. You plan to roll back the running configuration by using the checkpoint. You must ensure that changes are made only if the entire rollback can be applied successfully. Which rollback option should you use?
A) atomic
B) stop-at-first-failure
C) best-effort
D) verbose
A) atomic
B) stop-at-first-failure
C) best-effort
D) verbose
atomic
4
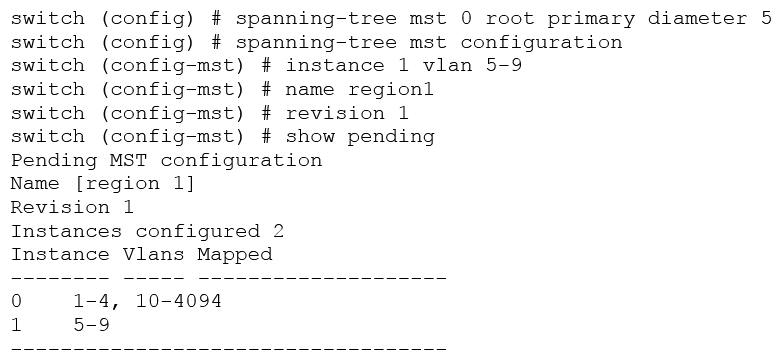 Refer to the exhibit. What does the diameter command specify?
Refer to the exhibit. What does the diameter command specify?A) the maximum number of hops between any two bridges on a network
B) the number of VLANs that were removed from the MSTI
C) the VLAN that becomes the root of the MSTI
D) the maximum number of hops between any two MST instances on a network

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
5
Which command should you ran to distribute NTP configuration changes by using Cisco Fabric Services?
A) ntp distribute
B) ntp server 1.2.3.4
C) ntp commit
D) ntp authenticate
A) ntp distribute
B) ntp server 1.2.3.4
C) ntp commit
D) ntp authenticate

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
6
When configuring PIM to support an OTV implementation, which PIM configuration is supported in Cisco NX-OS?
A) SwitchA(config-if)# ip pim ssm default
B) SwitchA(config-if)# ip pim sparse-mode
C) SwitchA(config-if)# ip pim dense-mode
D) SwitchA(config-if)# ip pim sparse-dense-mode
A) SwitchA(config-if)# ip pim ssm default
B) SwitchA(config-if)# ip pim sparse-mode
C) SwitchA(config-if)# ip pim dense-mode
D) SwitchA(config-if)# ip pim sparse-dense-mode

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
7
Switch(config)# login block-for 60 attempts 10 within 180 Switch(config)# login quiet-mode access-class acl Refer to the exhibit. Which statement is true about the impact to login requests on a Cisco NX-OS switch that uses this configuration?
A) Hosts in the ACL are denied after 10 failed login attempts occur within 180 seconds.
B) Hosts outside the ACL are allowed if more than 10 failed login attempts occur.
C) Hosts in the ACL are allowed after 10 failed login attempts occur within 180 seconds.
D) All hosts are denied if 10 failed login attempts from hosts in the ACL occur in 180 seconds.
A) Hosts in the ACL are denied after 10 failed login attempts occur within 180 seconds.
B) Hosts outside the ACL are allowed if more than 10 failed login attempts occur.
C) Hosts in the ACL are allowed after 10 failed login attempts occur within 180 seconds.
D) All hosts are denied if 10 failed login attempts from hosts in the ACL occur in 180 seconds.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
8
Which statement about SNMP support on Cisco Nexus switches is true?
A) SNMP requires the LAN_ENTERPRISE_SERVICES_PKG license.
B) SNMP is not VRF-aware.
C) Only users belonging to the network operator RBAC role can assign SNMP groups.
D) Cisco NX-OS supports one instance of the SNMP per VDC.
E) Cisco NX-OS only supports SNMP over IPv4.
A) SNMP requires the LAN_ENTERPRISE_SERVICES_PKG license.
B) SNMP is not VRF-aware.
C) Only users belonging to the network operator RBAC role can assign SNMP groups.
D) Cisco NX-OS supports one instance of the SNMP per VDC.
E) Cisco NX-OS only supports SNMP over IPv4.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
9
When you configure LISP, which two components must be configured at the site edge? (Choose two.)
A) AED
B) ELAN
C) ITR
D) EOBC
E) ETR
A) AED
B) ELAN
C) ITR
D) EOBC
E) ETR

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
10
You plan to configure authentication for OSPF. In which configuration mode should you configure OSPF authentication to use a specific key chain?
A) router ospf
B) global
C) vPC
D) interface
A) router ospf
B) global
C) vPC
D) interface

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
11
Which command allows a Cisco Nexus 7000 Series Switch to receive NTP configuration updates by using Cisco Fabric Services?
A) N7k (config)# feature ntp
B) N7k (config)# ntp distribute
C) N7k (config)# distribute
D) N7k (config)# ntp master
A) N7k (config)# feature ntp
B) N7k (config)# ntp distribute
C) N7k (config)# distribute
D) N7k (config)# ntp master

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
12
After enabling strong, reversible 128-bit Advanced Encryption Standard password type-6 encryption on a Cisco Nexus 7000, which command would convert existing plain or weakly encrypted passwords to type-6 encrypted passwords?
A) switch# encryption re-encrypt obfuscated switch# encryption re-encrypt obfuscated
B) switch# encryption decrypt type6 encryption decrypt type6
C) switch# key config-key ascii key config-key ascii
D) switch(config)# feature password encryption aes switch(config)# feature password encryption aes
A) switch# encryption re-encrypt obfuscated switch# encryption re-encrypt obfuscated
B) switch# encryption decrypt type6 encryption decrypt type6
C) switch# key config-key ascii key config-key ascii
D) switch(config)# feature password encryption aes switch(config)# feature password encryption aes

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
13
Which LISP component provides connectivity between LISP and non-LISP sites?
A) a map resolver
B) a proxy ETR
C) a proxy ITR
D) an ALT
A) a map resolver
B) a proxy ETR
C) a proxy ITR
D) an ALT

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
14
When configuring HSPR on IPv6-enabled interfaces, which two commands are required? (Choose two.)
A) SwitchA(config-if)# hsrp version 2 SwitchA(config-if)# hsrp version 2
B) SwitchA(config-if)# hsrp ipv6 hsrp ipv6
C) SwitchA(config-if)# key 6 SwitchA(config-if)# key 6
D) SwitchA(config-if)# standby 6 preempt standby 6 preempt
E) SwitchA(config-if)# priority priority
A) SwitchA(config-if)# hsrp version 2 SwitchA(config-if)# hsrp version 2
B) SwitchA(config-if)# hsrp
C) SwitchA(config-if)# key 6 SwitchA(config-if)# key 6
D) SwitchA(config-if)# standby 6 preempt standby 6 preempt
E) SwitchA(config-if)# priority

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
15
Which command should you run to enforce SNMP message encryption for all SNMPv3 communications?
A) snmp-server globalEnforceAuth
B) snmp-server user Admin enforcePriv
C) snmp-server globalEnforcePriv
D) snmp-server user Admin enforceAuth
A) snmp-server globalEnforceAuth
B) snmp-server user Admin enforcePriv
C) snmp-server globalEnforcePriv
D) snmp-server user Admin enforceAuth

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
16
Which statement about the Layer 3 card on the Cisco Nexus 5500 Series Switch is true?
A) BGP support is not provided, but RIP, EIGRP, and OSPF support is provided.
B) Up to two 4-port cards are supported with up to 160 Gb/s of Layer 3 forwarding capability.
C) Up to 16 FEX connections are supported.
D) Port channels cannot be configured as Layer 3 interfaces.
A) BGP support is not provided, but RIP, EIGRP, and OSPF support is provided.
B) Up to two 4-port cards are supported with up to 160 Gb/s of Layer 3 forwarding capability.
C) Up to 16 FEX connections are supported.
D) Port channels cannot be configured as Layer 3 interfaces.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
17
What can be identified by running the show install all impact kickstart bootflash:n5000-uk9-kickstart.7.0.7.N.1.1.bin system bootflash:n5000-uk9.7.0.7.N1.1a.bin command?
A) whether the specified kickstart image is compatible with the start-up config
B) whether the specified system image supports the kickstart image
C) whether bootflash is supported for the specified Cisco NX-OS images
D) whether ISSU is supported for the specified Cisco NX-OS images
A) whether the specified kickstart image is compatible with the start-up config
B) whether the specified system image supports the kickstart image
C) whether bootflash is supported for the specified Cisco NX-OS images
D) whether ISSU is supported for the specified Cisco NX-OS images

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
18
Which GLBL load-balancing method ensures that a client is always mapped to the same virtual MAC address?
A) host-dependent
B) vmac-weighted
C) dedicated-vmac-mode
D) shortest-path and weighting
A) host-dependent
B) vmac-weighted
C) dedicated-vmac-mode
D) shortest-path and weighting

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
19
Which statement about RADIUS configuration distribution using Cisco Fabric Services on a Cisco Nexus 7000 Series Switch is true?
A) Cisco Fabric Services does not distribute the RADIUS server group configuration or server and global keys.
B) Enabling Cisco Fabric Services causes the existing RADIUS configuration on your Cisco NX- OS device to be immediately distributed.
C) When the RADIUS configuration is being simultaneously changed on more than one device in a Cisco Fabric Services region, the most recent changes will take precedence.
D) Only the Cisco NX-OS device with the lowest IP address in the Cisco Fabric Services region can lock the RADIUS configuration.
A) Cisco Fabric Services does not distribute the RADIUS server group configuration or server and global keys.
B) Enabling Cisco Fabric Services causes the existing RADIUS configuration on your Cisco NX- OS device to be immediately distributed.
C) When the RADIUS configuration is being simultaneously changed on more than one device in a Cisco Fabric Services region, the most recent changes will take precedence.
D) Only the Cisco NX-OS device with the lowest IP address in the Cisco Fabric Services region can lock the RADIUS configuration.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
20
Which two statements about Cisco Nexus 7000 line cards are true? (Choose two.)
A) M1, M2, and F1 cards are allowed in the same VDC.
B) M line cards are service-oriented and likely face the access layer and provide Layer 2 connectivity.
C) F line cards are performance-oriented and likely connect northbound to the core layer for Layer 3 connectivity.
D) M line cards support Layer 2, Layer 3, and Layer 4 with large forwarding tables and a rich feature set.
E) The F2 line card must reside in the admin VDC.
A) M1, M2, and F1 cards are allowed in the same VDC.
B) M line cards are service-oriented and likely face the access layer and provide Layer 2 connectivity.
C) F line cards are performance-oriented and likely connect northbound to the core layer for Layer 3 connectivity.
D) M line cards support Layer 2, Layer 3, and Layer 4 with large forwarding tables and a rich feature set.
E) The F2 line card must reside in the admin VDC.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
21
Refer to the exhibit. 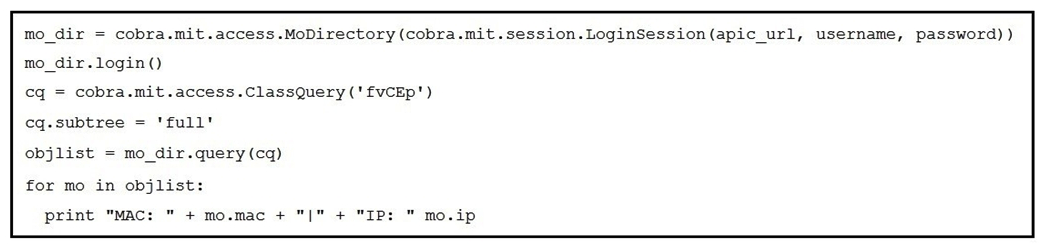 Which action does the execution of this ACI Cobra Python code perform?
Which action does the execution of this ACI Cobra Python code perform?
A) It prints all LLDP neighbor MAC and IP addresses.
B) It prints all Cisco Discovery Protocol neighbor MAC and IP addresses.
C) It prints all endpoint MAC and IP addresses.
D) It prints all APIC MAC and IP addresses.
 Which action does the execution of this ACI Cobra Python code perform?
Which action does the execution of this ACI Cobra Python code perform?A) It prints all LLDP neighbor MAC and IP addresses.
B) It prints all Cisco Discovery Protocol neighbor MAC and IP addresses.
C) It prints all endpoint MAC and IP addresses.
D) It prints all APIC MAC and IP addresses.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
22
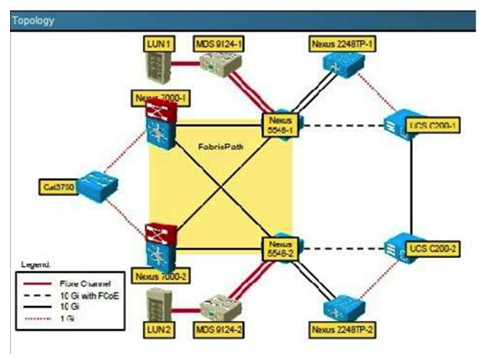
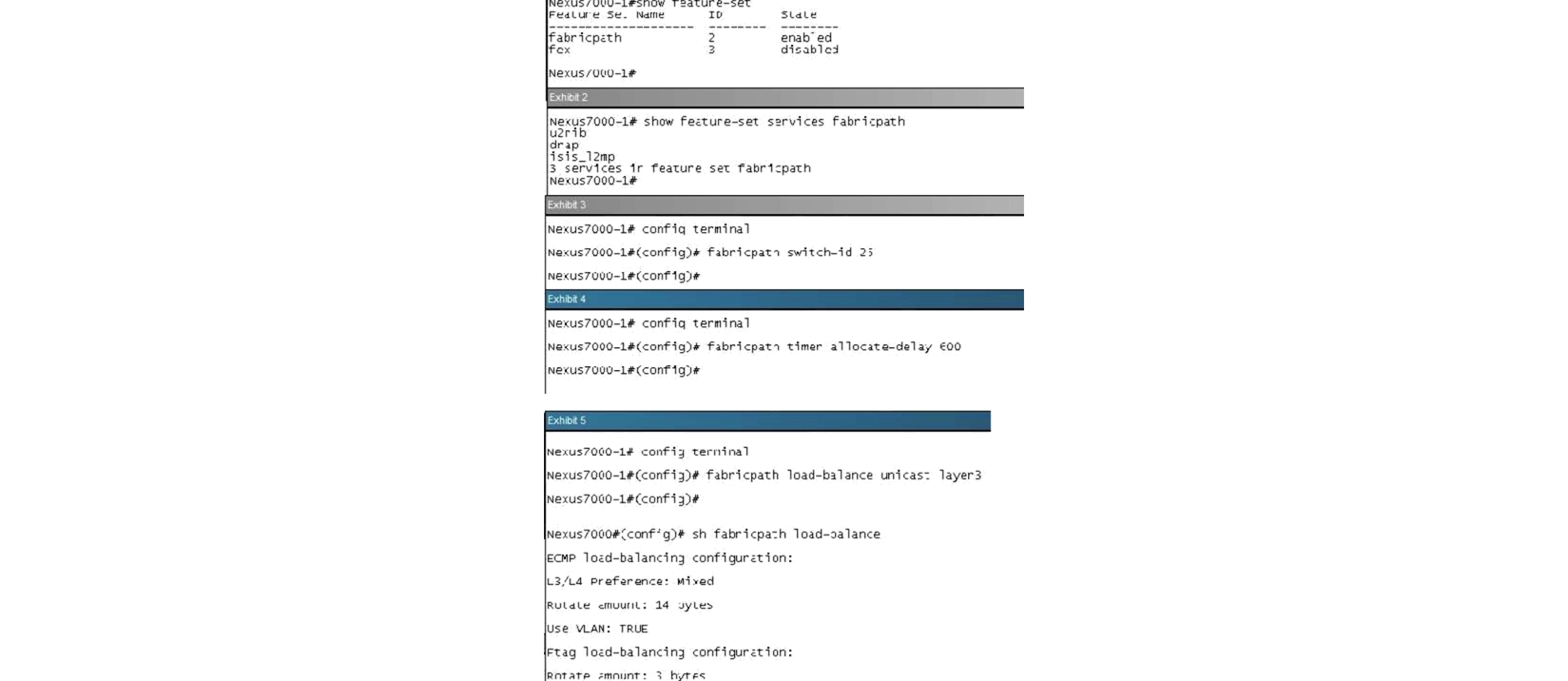 On a Cisco Nexus7000 switches what is true regarding Cisco FabricPath requirements?
On a Cisco Nexus7000 switches what is true regarding Cisco FabricPath requirements?A) Ensure that you have installed the Enhanced Layer 2 license and that you have installed an F Series module
B) Ensure that you have installed the Enhanced Layer 2 license and that you have installed an M Series module
C) Ensure that you have installed the Enhanced Layer 3 license and that you have installed an M Series module
D) Ensure that you have installed the Scalable Feature License license and that you have installed an F Series module

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
23
Refer to the exhibit.  Which two statements are true about this API GET request to the ACI APIC? (Choose two.)
Which two statements are true about this API GET request to the ACI APIC? (Choose two.)
A) The API call creates a new 10G interface in the APIC.
B) The API call reads information from a managed object.
C) The API response is encoded in JSON.
D) The API call reads information from an object class.
E) The API response is encoded in XML.
 Which two statements are true about this API GET request to the ACI APIC? (Choose two.)
Which two statements are true about this API GET request to the ACI APIC? (Choose two.)A) The API call creates a new 10G interface in the APIC.
B) The API call reads information from a managed object.
C) The API response is encoded in JSON.
D) The API call reads information from an object class.
E) The API response is encoded in XML.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
24
What mode is required on a Cisco Nexus 7000 32-port 10-GB module port group to allow equal access to the 10-GB port controller?
A) dedicated
B) assigned
C) shared
D) community
A) dedicated
B) assigned
C) shared
D) community

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
25
Which function does the graceful restart feature allow a Cisco Nexus 7000 Series router to perform?
A) Perform a rapid route convergence.
B) Initialize a standby supervisor transparently when one is present.
C) Remain in the data forwarding path through a process restart.
D) Maintain a management connection throughout a router restart.
A) Perform a rapid route convergence.
B) Initialize a standby supervisor transparently when one is present.
C) Remain in the data forwarding path through a process restart.
D) Maintain a management connection throughout a router restart.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
26
Which statement about synchronous and asynchronous API calls is true?
A) Synchronous API calls wait to return until a response has been received.
B) Synchronous communication is harder to follow and troubleshoot.
C) Synchronous API calls must always use a proxy server.
D) Asynchronous communication uses more overhead for client authentication.
A) Synchronous API calls wait to return until a response has been received.
B) Synchronous communication is harder to follow and troubleshoot.
C) Synchronous API calls must always use a proxy server.
D) Asynchronous communication uses more overhead for client authentication.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
27
Which command enables NPIV on Cisco Nexus 5000 Series Switches and Cisco MDS switches?
A) switch(config)# npiv enable
B) switch(config)# npivon
C) switch(config)# feature npiv
D) switch(config)# npiv proxy
E) switch(config)# np proxy-enable
A) switch(config)# npiv enable
B) switch(config)# npivon
C) switch(config)# feature npiv
D) switch(config)# npiv proxy
E) switch(config)# np proxy-enable

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
28
Which protocol is the foundation for unified fabric as implemented in Cisco NX-OS?
A) Fibre Channel
B) Data Center Bridging
C) Fibre Channel over Ethernet
D) N proxy virtualization
E) N Port identifier virtualization
A) Fibre Channel
B) Data Center Bridging
C) Fibre Channel over Ethernet
D) N proxy virtualization
E) N Port identifier virtualization

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
29
Which two statements about gRPC are true? (Choose two.)
A) It is an IETF draft.
B) It is an IETF standard.
C) It runs over SSH.
D) It is an open source initiative.
E) It runs over HTTPS.
A) It is an IETF draft.
B) It is an IETF standard.
C) It runs over SSH.
D) It is an open source initiative.
E) It runs over HTTPS.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
30
What are two main guiding principles of REST? (Choose two.)
A) cacheable
B) trackable
C) stateless
D) single-layer system
E) stateful
A) cacheable
B) trackable
C) stateless
D) single-layer system
E) stateful

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
31
Which GLBP load-balancing algorithm ensures that a client is always mapped to the same VMAC address?
A) vmac-weighted
B) dedicated-vmac-mode
C) shortest-path and weighting
D) host-dependent
A) vmac-weighted
B) dedicated-vmac-mode
C) shortest-path and weighting
D) host-dependent

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
32
Which statement is true if password-strength checking is enabled?
A) Short, easy-to-decipher passwords will be rejected.
B) The strength of existing passwords will be checked.
C) Special characters, such as the dollar sign ($) or the percent sign (%), will not be allowed.
D) Passwords become case-sensitive.
A) Short, easy-to-decipher passwords will be rejected.
B) The strength of existing passwords will be checked.
C) Special characters, such as the dollar sign ($) or the percent sign (%), will not be allowed.
D) Passwords become case-sensitive.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
33
Which Ansible playbook fragment returns the fewest queried ACI endpoint groups?
A)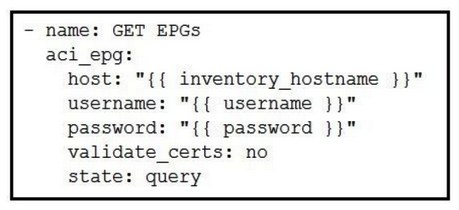
B)
C)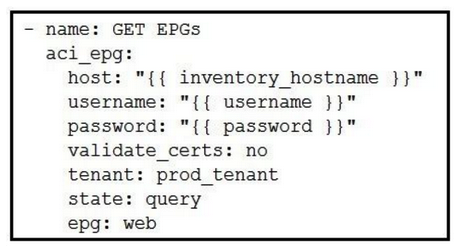
D)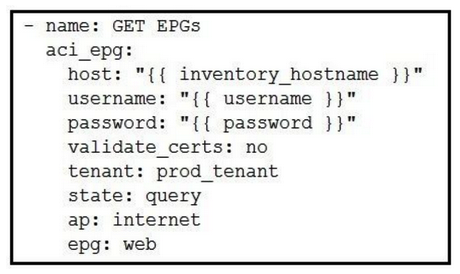
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
34
Which two items are types of application isolation options available when Kubernetes is deployed with the ACI CNI plug-in? (Choose two.)
A) VM Isolation
B) Cluster Isolation
C) Server Isolation
D) Process Isolation
E) Namespace Isolation
A) VM Isolation
B) Cluster Isolation
C) Server Isolation
D) Process Isolation
E) Namespace Isolation

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
35
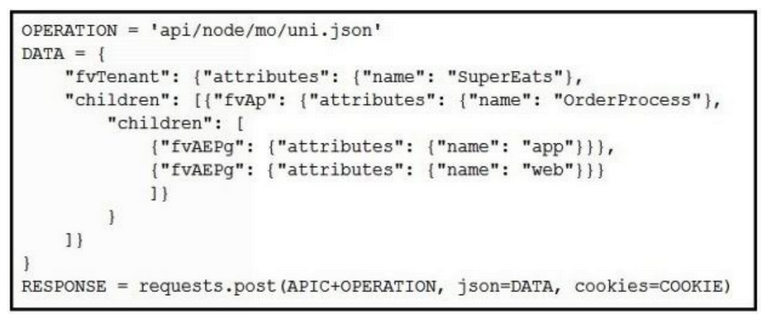
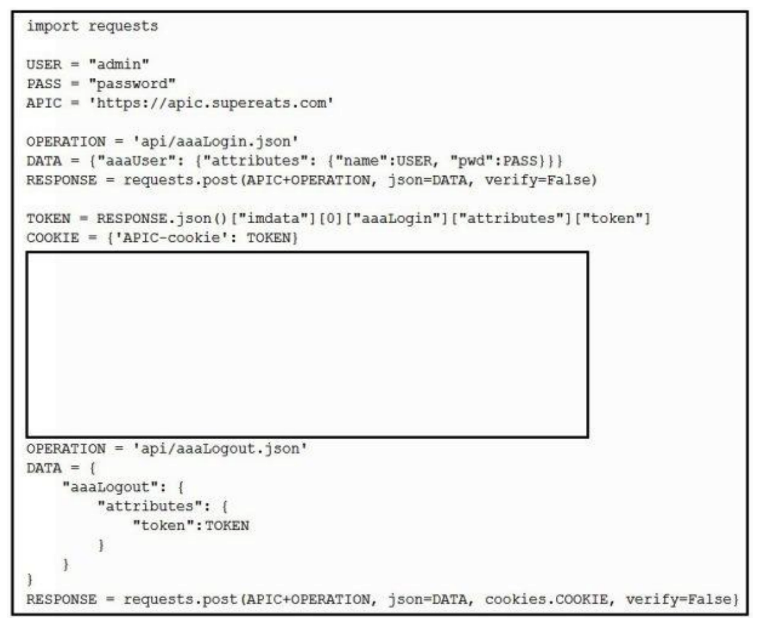 Which Python snippets create an application policy named OrderProcess that contains two application endpoint groups under Tenant SuperEats using direct calls to the ACI REST API? Assume that authentication and library imports are correct.
Which Python snippets create an application policy named OrderProcess that contains two application endpoint groups under Tenant SuperEats using direct calls to the ACI REST API? Assume that authentication and library imports are correct.A)
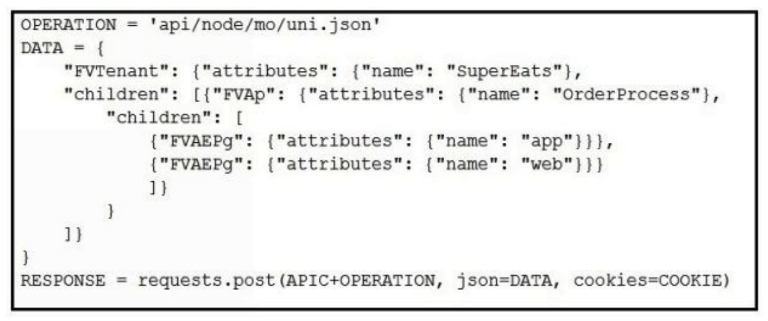
B)
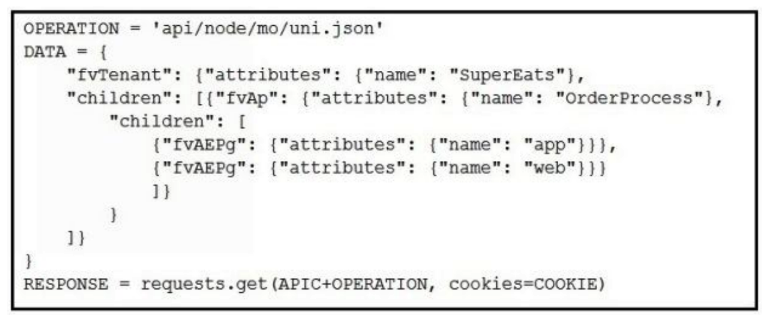
C)
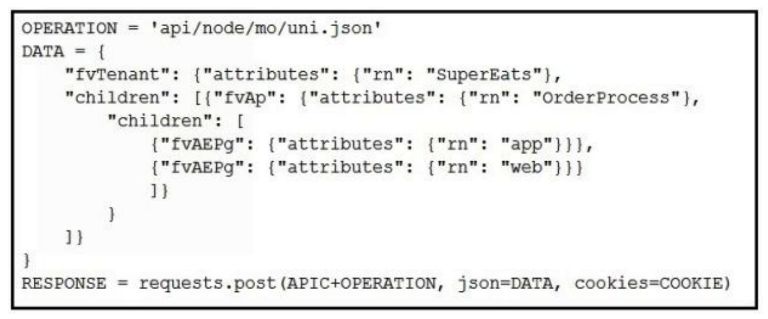
D)

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
36
What configuration is required when implementing FCoE?
A) disable LAN traffic on the interface
B) configure PortFast on the access port
C) permit all VLANs on the interface
D) permit all VSANs on the interface
A) disable LAN traffic on the interface
B) configure PortFast on the access port
C) permit all VLANs on the interface
D) permit all VSANs on the interface

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
37
Refer to the exhibit. 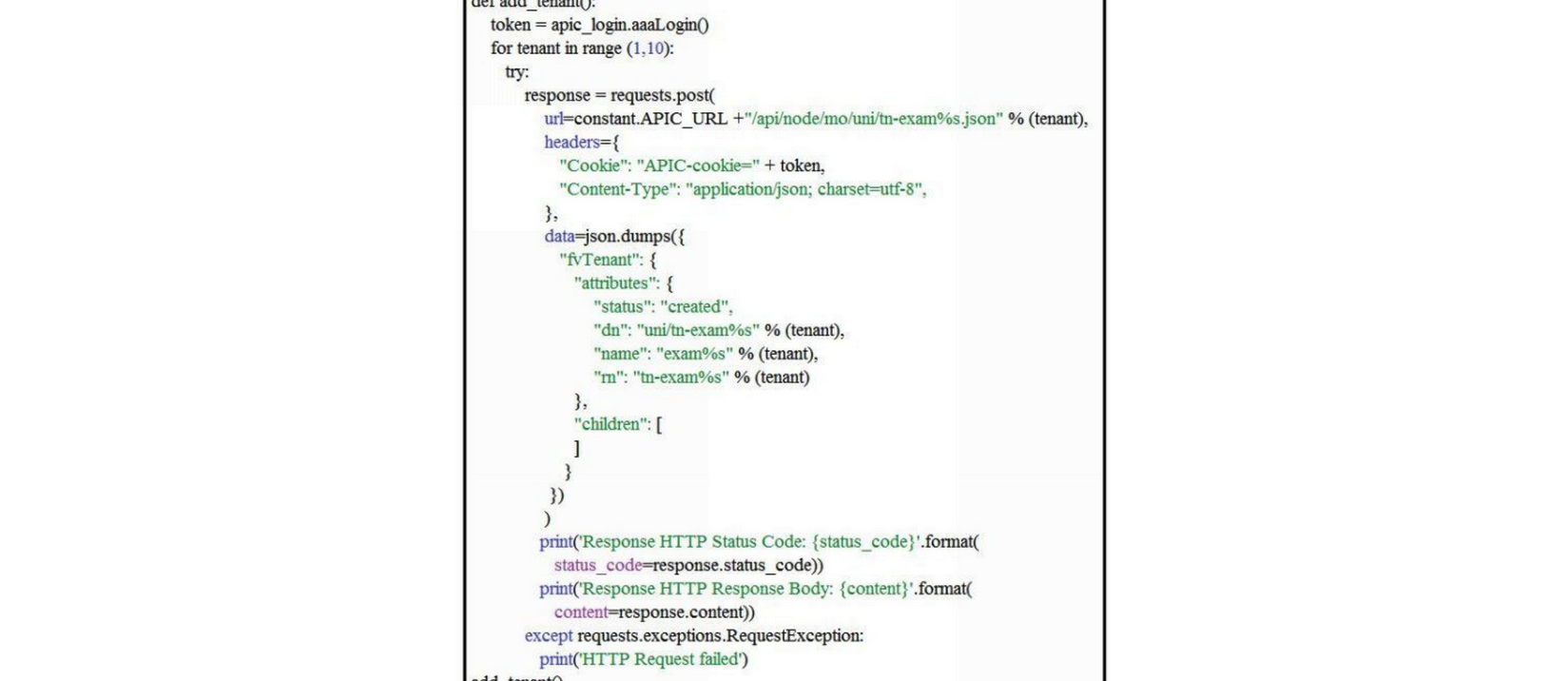 Assuming a new ACI instance, what is the result when this script is run?
Assuming a new ACI instance, what is the result when this script is run?
A) Ten objects are created and subsequently deleted.
B) Nine objects are created.
C) An exception is thrown.
D) Ten objects are created.
 Assuming a new ACI instance, what is the result when this script is run?
Assuming a new ACI instance, what is the result when this script is run?A) Ten objects are created and subsequently deleted.
B) Nine objects are created.
C) An exception is thrown.
D) Ten objects are created.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
38
Which three VDC resources can be constrained with a resource template? (Choose three.)
A) CLs
B) NAT entries
C) IPv4 routes
D) IPv6 routes
E) SPAN sessions
F) RBAC users
A) CLs
B) NAT entries
C) IPv4 routes
D) IPv6 routes
E) SPAN sessions
F) RBAC users

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
39
Which two benefits of using network configuration tools such as Ansible and Puppet to automate data center platforms are valid? (Choose two.)
A) consistency of systems configuration
B) automation of repetitive tasks
C) ability to create device and interface groups
D) ability to add VLANs and routes per device
E) removal of network protocols such as Spanning Tree
A) consistency of systems configuration
B) automation of repetitive tasks
C) ability to create device and interface groups
D) ability to add VLANs and routes per device
E) removal of network protocols such as Spanning Tree

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
40
How is an ACI class name composed?
A) :Method
B) ClassName:Method
C) Package:ClassName
D) MitName:Method
A) :Method
B) ClassName:Method
C) Package:ClassName
D) MitName:Method

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
41
What is a key characteristic of an ACI policy model?
A) Logical and concrete domains are separated.
B) All configuration is carried out against concrete entities.
C) It allows communications with newly connected devices.
D) Network administrators configure logical and physical system resources directly.
A) Logical and concrete domains are separated.
B) All configuration is carried out against concrete entities.
C) It allows communications with newly connected devices.
D) Network administrators configure logical and physical system resources directly.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
42
Refer to the exhibit. 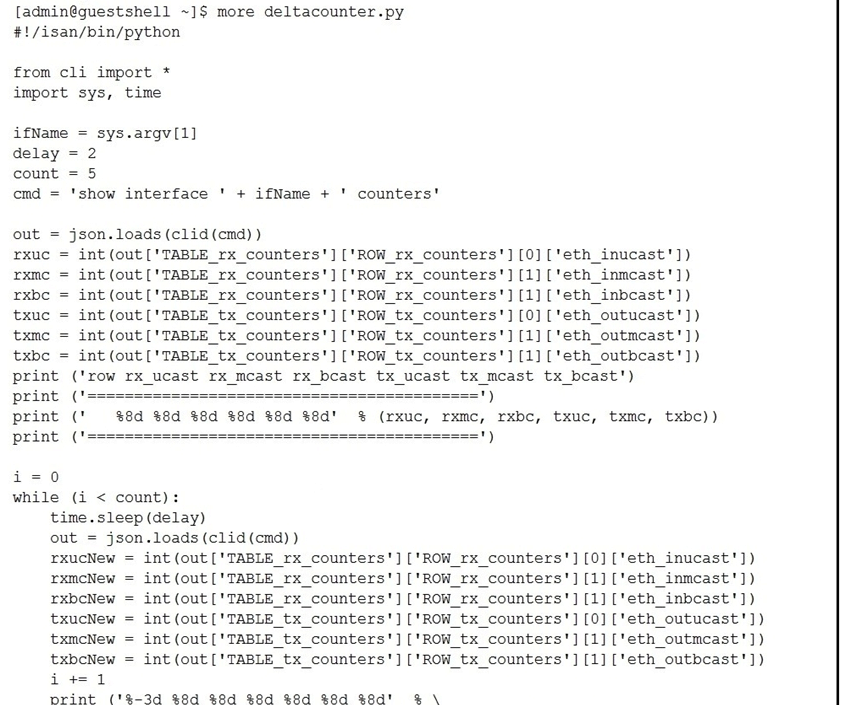 The script is called deltacounters.py and it is currently inside a Guest Shell container running inside a Cisco NX-OS switch. Which Cisco NX-OS command results in a successful execution of this script?
The script is called deltacounters.py and it is currently inside a Guest Shell container running inside a Cisco NX-OS switch. Which Cisco NX-OS command results in a successful execution of this script?
A) python /home/admin/bootflash:deltacounters.py ethemet1/1
B) show python bootflash:deltacounters.py ethernet1/1
C) guestshell run python /home/admin/deltacounter.py ethernet1/1
D) guestshell execute python /home/admin/deltacounter.py ethernet1/1
 The script is called deltacounters.py and it is currently inside a Guest Shell container running inside a Cisco NX-OS switch. Which Cisco NX-OS command results in a successful execution of this script?
The script is called deltacounters.py and it is currently inside a Guest Shell container running inside a Cisco NX-OS switch. Which Cisco NX-OS command results in a successful execution of this script?A) python /home/admin/bootflash:deltacounters.py ethemet1/1
B) show python bootflash:deltacounters.py ethernet1/1
C) guestshell run python /home/admin/deltacounter.py ethernet1/1
D) guestshell execute python /home/admin/deltacounter.py ethernet1/1

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
43
What are two capabilities of the DCNM REST API? (Choose two.)
A) uses the dcnm-token header for requests authentication after initial basic authentication
B) uses basic authentication without encoding for username and password
C) supports HTTP until release 11.0(1)
D) uses bearer key authorization
E) is separated into Classic LAN, LAN Fabric, Media Controller, and SAN Management categories
A) uses the dcnm-token header for requests authentication after initial basic authentication
B) uses basic authentication without encoding for username and password
C) supports HTTP until release 11.0(1)
D) uses bearer key authorization
E) is separated into Classic LAN, LAN Fabric, Media Controller, and SAN Management categories

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
44
Refer to the exhibit. 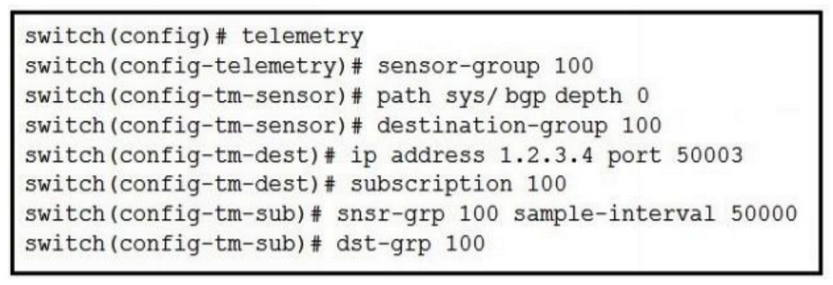 How often is the subscription stream for sys/bgp going to be sent?
How often is the subscription stream for sys/bgp going to be sent?
A) 5 sec
B) 5 msec
C) 5000 sec
D) 5 min
 How often is the subscription stream for sys/bgp going to be sent?
How often is the subscription stream for sys/bgp going to be sent?A) 5 sec
B) 5 msec
C) 5000 sec
D) 5 min

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
45
Using the NX-API CLI JSON-RPC interface, which two Python data structure and requests call create an SVI? (Choose two.)
A)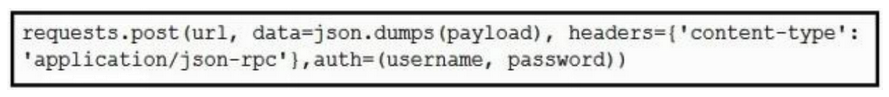
B)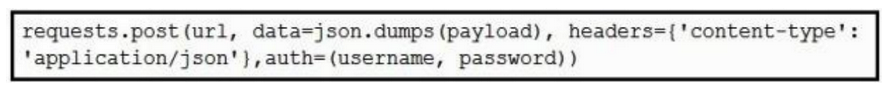
C)
D)
E)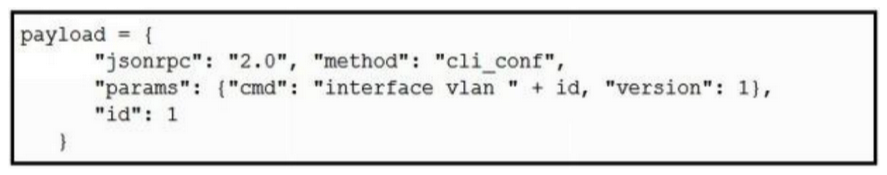
A)

B)

C)

D)

E)


Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
46
Which authentication method is used when the REST API of the Cisco UCS Director is accessed?
A) Bearer ((Bearer Token)) Bearer ((Bearer Token))
B) HTTP Basic Auth
C) RestAuth: ((User's Auth Token)) RestAuth: ((User's Auth Token))
D) X-Cloupia-Request-Key: ((User's Auth Token)) X-Cloupia-Request-Key:
A) Bearer ((Bearer Token)) Bearer ((Bearer Token))
B) HTTP Basic Auth
C) RestAuth: ((User's Auth Token)) RestAuth: ((User's Auth Token))
D) X-Cloupia-Request-Key: ((User's Auth Token)) X-Cloupia-Request-Key:

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
47
Refer to the exhibit.  Which change allows the code to configure VLAN 10 in the Cisco UCS?
Which change allows the code to configure VLAN 10 in the Cisco UCS?
A) Lines 8 and 9 should have a line continuation \ at the end.
B) Line 13 should include "handle.commit()" . Line 13 should include "handle.commit()" .
C) Line 4 should include transport 443 option.
D) Line 3 should add an import for query_dn . Line 3 should add an import for query_dn
 Which change allows the code to configure VLAN 10 in the Cisco UCS?
Which change allows the code to configure VLAN 10 in the Cisco UCS?A) Lines 8 and 9 should have a line continuation \ at the end.
B) Line 13 should include "handle.commit()" . Line 13 should include "handle.commit()" .
C) Line 4 should include transport 443 option.
D) Line 3 should add an import for query_dn . Line 3 should add an import for query_dn

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
48
Which two capabilities apply to the DCNM API? (Choose two.)
A) DCNM provides an XML-based SOAP API.
B) DCNM requires a license to use the API.
C) Some features of DCNM must be configured through the GUI.
D) All API operations can be performed using the DCNM GUI.
E) DCNM provides a REST-based API.
A) DCNM provides an XML-based SOAP API.
B) DCNM requires a license to use the API.
C) Some features of DCNM must be configured through the GUI.
D) All API operations can be performed using the DCNM GUI.
E) DCNM provides a REST-based API.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
49
Which Ansible playbook creates a new VLAN 10 named Web?
A)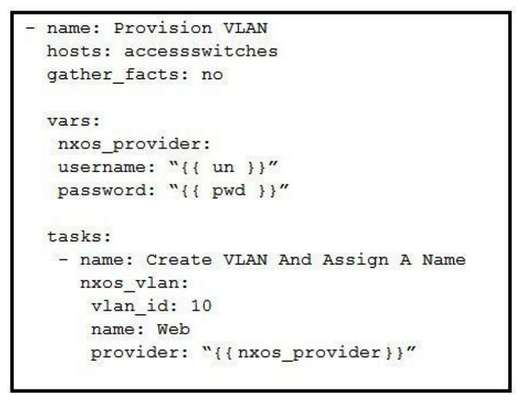
B)
C)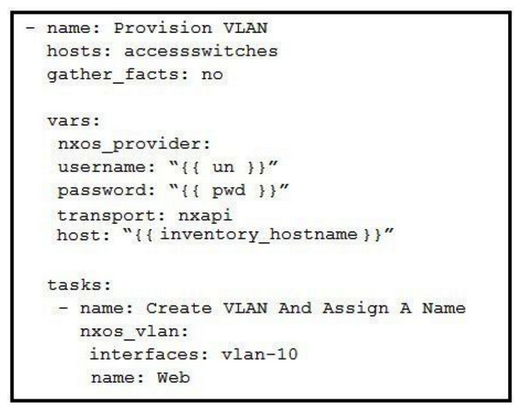
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
50
Refer to the exhibit. 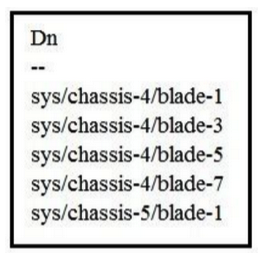 Which two Cisco UCS PowerTool commands provide this output? (Choose two.)
Which two Cisco UCS PowerTool commands provide this output? (Choose two.)
A) Get-UcsServer | Select-Object Dn
B) Get-UcsRack Systems | Select-Object Dn
C) Get-UcsBlade | Select-Object Dn
D) Get-UcsRackUnit | Select-Object Dn
E) Get-UcsSystems | Select-Object Dn
 Which two Cisco UCS PowerTool commands provide this output? (Choose two.)
Which two Cisco UCS PowerTool commands provide this output? (Choose two.)A) Get-UcsServer | Select-Object Dn
B) Get-UcsRack Systems | Select-Object Dn
C) Get-UcsBlade | Select-Object Dn
D) Get-UcsRackUnit | Select-Object Dn
E) Get-UcsSystems | Select-Object Dn

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
51
What is a feature of model-driven telemetry?
A) randomizes the data out of the network
B) continuously streams data out of the network
C) randomizes the data coming to the network
D) continuously pulls data out of the network
A) randomizes the data out of the network
B) continuously streams data out of the network
C) randomizes the data coming to the network
D) continuously pulls data out of the network

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
52
What is the network bootstrap program used by Cisco NX-OS iPXE?
A) NETBOOT
B) NX-OS iPXE
C) iPXE-POAP
D) Mini-OS
A) NETBOOT
B) NX-OS iPXE
C) iPXE-POAP
D) Mini-OS

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
53
When should the API Inspector be used?
A) to send an API request to the APIC
B) to learn or identify the sequence of API calls for a specific operation in the APIC GUI
C) to verify the XML structure of an object based on a specific operation in the APIC GUI
D) to launch an Ansible playbook
A) to send an API request to the APIC
B) to learn or identify the sequence of API calls for a specific operation in the APIC GUI
C) to verify the XML structure of an object based on a specific operation in the APIC GUI
D) to launch an Ansible playbook

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
54
When the Cisco bigmuddy-network-telemetry-collector from GitHub is used, which command displays only the message headers?
A) --print
B) --all
C) --brief
D) --print-all
A) --print
B) --all
C) --brief
D) --print-all

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
55
Refer to the exhibit. 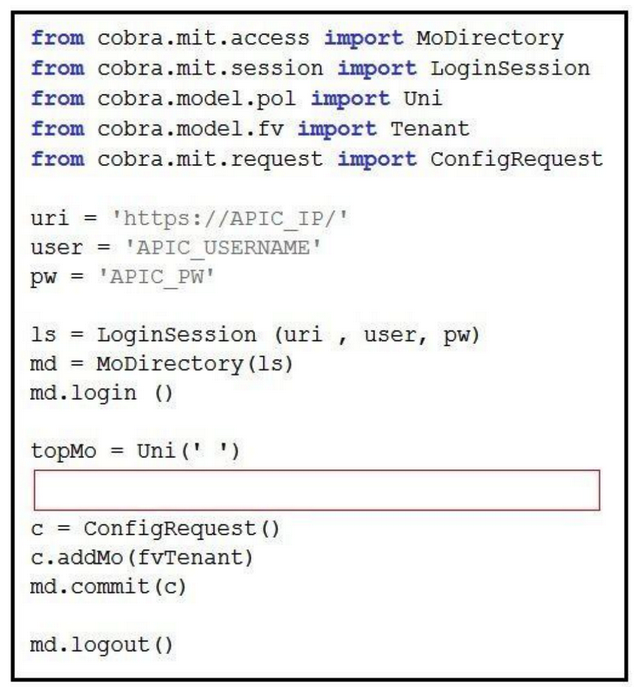 The code should create a new tenant named Cisco via the Cobra SDK, which shows up after the execution of this script in the APIC dashboard. Which code must he inserted into the red box to create this tenant?
The code should create a new tenant named Cisco via the Cobra SDK, which shows up after the execution of this script in the APIC dashboard. Which code must he inserted into the red box to create this tenant?
A) fvTenant = NewTenant(name='Cisco')
B) tenant = Tenant(topMo. name='Cisco')
C) fvTenant = Tenant(topMo, name='Cisco')
D) fvTenant = Tenant('Cisco')
 The code should create a new tenant named Cisco via the Cobra SDK, which shows up after the execution of this script in the APIC dashboard. Which code must he inserted into the red box to create this tenant?
The code should create a new tenant named Cisco via the Cobra SDK, which shows up after the execution of this script in the APIC dashboard. Which code must he inserted into the red box to create this tenant?A) fvTenant = NewTenant(name='Cisco')
B) tenant = Tenant(topMo. name='Cisco')
C) fvTenant = Tenant(topMo, name='Cisco')
D) fvTenant = Tenant('Cisco')

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
56
Which Kubernetes container network interface provides intent-based networking from the same pane of glass that VMs and bare-metal servers are managed?
A) ACI CNI plug-in
B) Contiv CNI plug-in
C) Ingress CNI plug-in
D) Calico CNI plug-in
A) ACI CNI plug-in
B) Contiv CNI plug-in
C) Ingress CNI plug-in
D) Calico CNI plug-in

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
57
Which two bootstrap technologies are supported by Cisco NX-OS platforms? (Choose two.)
A) iPXE
B) PNP
C) POAP
D) BOOTP
E) DHCP
A) iPXE
B) PNP
C) POAP
D) BOOTP
E) DHCP

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
58
Refer to the exhibit. 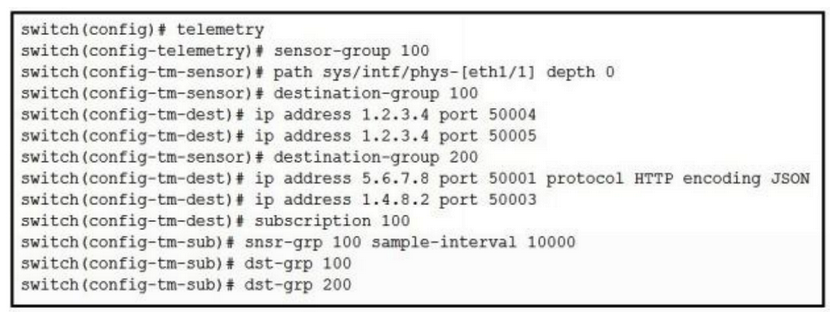 Where and how often does the subscription stream data for Ethernet port 1/1?
Where and how often does the subscription stream data for Ethernet port 1/1?
A) to four different destinations every 10000 microseconds
B) to four different destinations every 100 milliseconds
C) to four different destinations every 10 seconds
D) to four different destinations every 10000 seconds
 Where and how often does the subscription stream data for Ethernet port 1/1?
Where and how often does the subscription stream data for Ethernet port 1/1?A) to four different destinations every 10000 microseconds
B) to four different destinations every 100 milliseconds
C) to four different destinations every 10 seconds
D) to four different destinations every 10000 seconds

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
59
What are two differences between SNMP and model-driven telemetry? (Choose two.)
A) SNMP uses a continuous stream model.
B) SNMP uses a push model.
C) SNMP uses a pull model.
D) Model-driven telemetry uses a pull model.
E) Model-driven telemetry uses a push model.
A) SNMP uses a continuous stream model.
B) SNMP uses a push model.
C) SNMP uses a pull model.
D) Model-driven telemetry uses a pull model.
E) Model-driven telemetry uses a push model.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
60
Refer to the exhibit.  Which configuration change command must be run on the Cisco NX-OS device to make this command work?
Which configuration change command must be run on the Cisco NX-OS device to make this command work?
A) enable bash-shell
B) bash-shell enable
C) service bash-shell
D) feature bash-shell
 Which configuration change command must be run on the Cisco NX-OS device to make this command work?
Which configuration change command must be run on the Cisco NX-OS device to make this command work?A) enable bash-shell
B) bash-shell enable
C) service bash-shell
D) feature bash-shell

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
61
Which two statements describe the authentication method used with Cisco Intersight REST API Requests? (Choose two.)
A) The REST API request contains a base64-encoded signature of the message content and headers.
B) The REST API request message body is encoded as a SHA384 hash and then signed with the API Key ID.
C) The Cisco Intersight Web service verifies the signature of incoming request with the RSA public key for the API Key ID.
D) The incoming REST API request is challenged by the Cisco Intersight Web service with a request for the RSA private key.
E) The message body is encoded as a SHA256 hash if the message body is not empty and then signed with the API Key ID.
A) The REST API request contains a base64-encoded signature of the message content and headers.
B) The REST API request message body is encoded as a SHA384 hash and then signed with the API Key ID.
C) The Cisco Intersight Web service verifies the signature of incoming request with the RSA public key for the API Key ID.
D) The incoming REST API request is challenged by the Cisco Intersight Web service with a request for the RSA private key.
E) The message body is encoded as a SHA256 hash if the message body is not empty and then signed with the API Key ID.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
62
Refer to the exhibit. 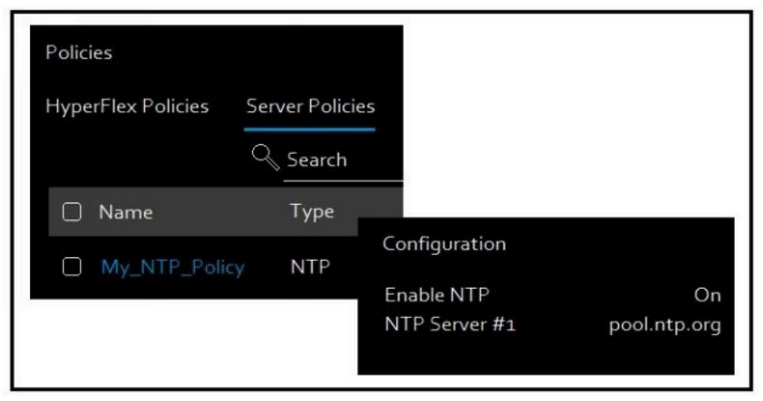 Cisco Intersight has an NTP server policy called My_NTP_Policy configured that contains a single NTP server pool entry "pool.ntp.org". Which Cisco Intersight API call adds an additional NTP server (10.20.0.1) to the My_NTP_Policy server policy?
Cisco Intersight has an NTP server policy called My_NTP_Policy configured that contains a single NTP server pool entry "pool.ntp.org". Which Cisco Intersight API call adds an additional NTP server (10.20.0.1) to the My_NTP_Policy server policy?
A)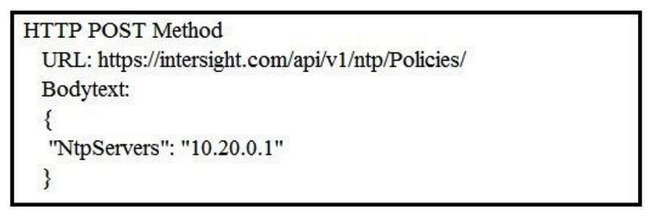
B)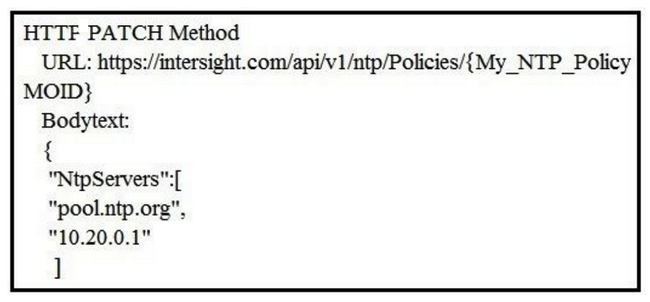
C)
D)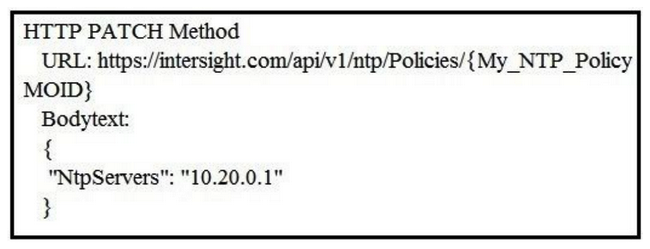
 Cisco Intersight has an NTP server policy called My_NTP_Policy configured that contains a single NTP server pool entry "pool.ntp.org". Which Cisco Intersight API call adds an additional NTP server (10.20.0.1) to the My_NTP_Policy server policy?
Cisco Intersight has an NTP server policy called My_NTP_Policy configured that contains a single NTP server pool entry "pool.ntp.org". Which Cisco Intersight API call adds an additional NTP server (10.20.0.1) to the My_NTP_Policy server policy?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
63
Refer to the exhibit. 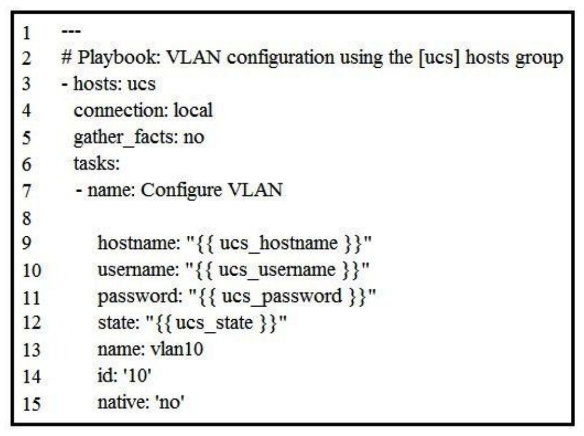 Which Ansible module is needed in line 8 to create a new VLAN 10 on the hosts defined in the "ucs" group?
Which Ansible module is needed in line 8 to create a new VLAN 10 on the hosts defined in the "ucs" group?
A) vlan
B) ucs_vlans
C) vlans
D) nxos_vlans
 Which Ansible module is needed in line 8 to create a new VLAN 10 on the hosts defined in the "ucs" group?
Which Ansible module is needed in line 8 to create a new VLAN 10 on the hosts defined in the "ucs" group?A) vlan
B) ucs_vlans
C) vlans
D) nxos_vlans

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
64
Which two statements apply to authentication when using the Cisco Intersight API? (Choose two.)
A) Each API Key can be assigned specific roles but not privileges.
B) Secret Key is only available at API Key creation time.
C) An API Key is composed of a Key ID and Secret Key.
D) The user credentials for the cisco.com accounts are shared with the Cisco Intersight Web Service.
E) An API Key is composed of a keyId and sessionCookie.
A) Each API Key can be assigned specific roles but not privileges.
B) Secret Key is only available at API Key creation time.
C) An API Key is composed of a Key ID and Secret Key.
D) The user credentials for the cisco.com accounts are shared with the Cisco Intersight Web Service.
E) An API Key is composed of a keyId and sessionCookie.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
65
Which two components are required from the Cisco Intersight REST API Authentication? (Choose two.)
A) SHA256 hash of the message body and message headers.
B) SHA256 hash of the message body, including empty message bodies.
C) RSA private key with a key size of 2048.
D) RSA private key with a key size of 1024.
E) SHA384 hash of the message body, excluding empty message bodies.
A) SHA256 hash of the message body and message headers.
B) SHA256 hash of the message body, including empty message bodies.
C) RSA private key with a key size of 2048.
D) RSA private key with a key size of 1024.
E) SHA384 hash of the message body, excluding empty message bodies.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck


