Deck 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/41
Play
Full screen (f)
Deck 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)
1
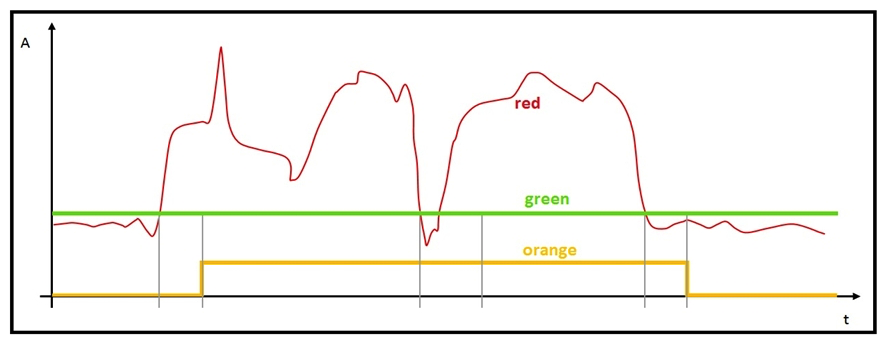 Refer to the exhibit. The graph has been provided by the monitoring team to the IoT Engineer. The red line represents the consumption of energy from an industrial machine. Which two pieces of information can be captured? (Choose two.)
Refer to the exhibit. The graph has been provided by the monitoring team to the IoT Engineer. The red line represents the consumption of energy from an industrial machine. Which two pieces of information can be captured? (Choose two.)A) The green graph visualizes the mean value of the data points.
B) The green graph visualizes if the electronic device is not in stand-by mode.
C) The orange graph visualizes a boolean: power on/off.
D) The orange graph contains more information than the red graph.
The green graph visualizes the mean value of the data points.
The orange graph visualizes a boolean: power on/off.
The orange graph visualizes a boolean: power on/off.
2
A network is being configured for an Ethernet-connected sensor. The sensor fails to send data to the configured destination. The IP address of the sensor can be pinged from a laptop on the same subnet. When a different subnet is used, the sensor cannot be reached, but other clients on the same subnet are still accessible. What are two reasons for the connectivity problem? (Choose two.)
A) wrong DNS server on the sensor
B) wrong subnet mask on your laptop
C) wrong default gateway on the sensor
D) wrong default gateway on your laptop
E) wrong subnet mask on the sensor
A) wrong DNS server on the sensor
B) wrong subnet mask on your laptop
C) wrong default gateway on the sensor
D) wrong default gateway on your laptop
E) wrong subnet mask on the sensor
wrong default gateway on the sensor
wrong subnet mask on the sensor
wrong subnet mask on the sensor
3
An IoT application has been built into the application CI/CD pipeline. The application needs credentials to access other applications, APIs, and cloud resources. When should the credentials be inserted into the application using the CI/CD process?
A) hard coded into your application code base
B) during application runtime
C) after application testing
D) during application build time
A) hard coded into your application code base
B) during application runtime
C) after application testing
D) during application build time
hard coded into your application code base
4
Which connector is southbound?
A) horizontal connector
B) cloud connector
C) device connector
D) universal connector
A) horizontal connector
B) cloud connector
C) device connector
D) universal connector

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
5
An IoT engineer is responsible for security at an organization. Humans and machines need to be allowed to access services like database or compute on AWS. The engineer decides to implement dynamic secrets. Which method helps to get this implementation accurate from a security point of view?
A) Create a central secret system for humans and machine to obtain very short-lived dynamic secrets to access any service.
B) Humans cannot be trusted, and each time they authenticate they should be issued with dynamic secrets. Machines can be trusted, and they can be issued with static credentials.
C) Maintain a different service associated to secret systems to issue access.
D) After a user is authenticated by any trusted system, the user can be trusted to use any service.
A) Create a central secret system for humans and machine to obtain very short-lived dynamic secrets to access any service.
B) Humans cannot be trusted, and each time they authenticate they should be issued with dynamic secrets. Machines can be trusted, and they can be issued with static credentials.
C) Maintain a different service associated to secret systems to issue access.
D) After a user is authenticated by any trusted system, the user can be trusted to use any service.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
6
The environment for an Industrial IoT project in a large open pit mine is being scoped. The location has a large amount of dust and the device will be exposed to less than 1 meter of water temporarily. When the edge device is being chosen, which Ingress protection rating must be used?
A) IP37
B) IP61
C) IP67
D) IP76
A) IP37
B) IP61
C) IP67
D) IP76

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
7
Which statement explains the correct position of a PLC within the CPwE architecture?
A) PLCs are always part of Level 0 - process control.
B) PLCs are part of Level 4 - site business planning.
C) PLCs are part of Level 1 - basic control.
D) PLCs are placed at Level 2 - area supervisory control.
A) PLCs are always part of Level 0 - process control.
B) PLCs are part of Level 4 - site business planning.
C) PLCs are part of Level 1 - basic control.
D) PLCs are placed at Level 2 - area supervisory control.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
8
Which two states are applications expected to be seen in when they are managed on Cisco IOx? (Choose two.)
A) DEACTIVATED
B) ACTIVATED
C) ALLOWED
D) STOPPED
E) VALIDATED
A) DEACTIVATED
B) ACTIVATED
C) ALLOWED
D) STOPPED
E) VALIDATED

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
9
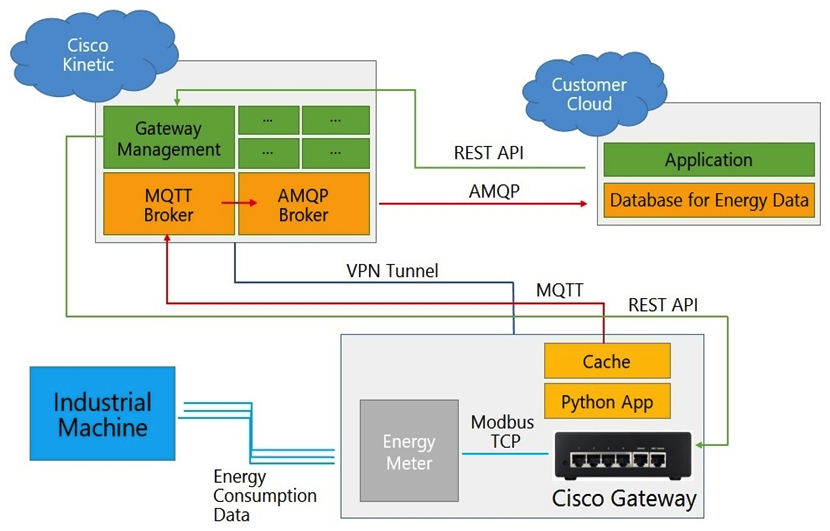 Refer to the exhibit. Which two statements about data flow are true? (Choose two.)
Refer to the exhibit. Which two statements about data flow are true? (Choose two.)A) Another AMQP broker should be implemented on the customer cloud.
B) Instead of AMQP, MQTT should be used for compatibility issues in a cloud-to-cloud connection.
C) A VPN tunnel is not necessary because the MQTT payload is encrypted by default.
D) The gateway must stay constantly connected to the Kinetic cloud to avoid blank data sets, even when using caching functions.
E) The Python application could use the paho-mqtt library.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
10
When trying to subscribe to an MQTT broker on the internet, the MQTT client is on a private subnet and must be NATed to reach the public broker. What is the expected outcome when this configuration is in place?
A) The client periodically reconnects to the default gateway.
B) The client connects only once using the PENDING message to the broker.
C) The client periodically reconnects to the broker over the NAT connection.
D) The client connects only once using the CONNECT massage to the broker.
A) The client periodically reconnects to the default gateway.
B) The client connects only once using the PENDING message to the broker.
C) The client periodically reconnects to the broker over the NAT connection.
D) The client connects only once using the CONNECT massage to the broker.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
11
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API. Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
A) Respond to request failures in detail to allow users for easier troubleshooting.
B) Implement HTTP whitelisting to only methods that are allowed.
C) Implement and review audit logs for security-related events.
D) Reject HTTP methods that are invalid with an error code 404.
E) Implement physical firewalling and access control to the resources.
A) Respond to request failures in detail to allow users for easier troubleshooting.
B) Implement HTTP whitelisting to only methods that are allowed.
C) Implement and review audit logs for security-related events.
D) Reject HTTP methods that are invalid with an error code 404.
E) Implement physical firewalling and access control to the resources.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
12
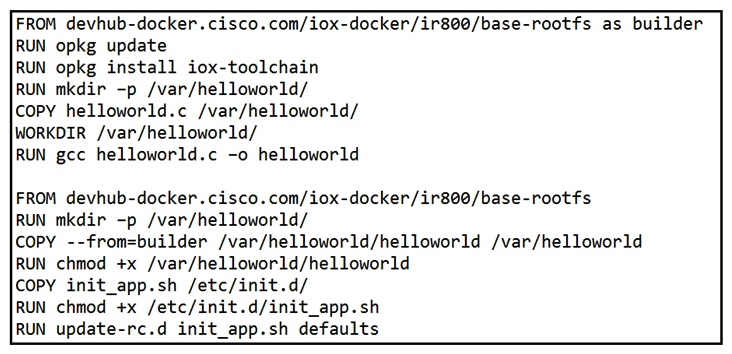 Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and before? (Choose two.)
Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and before? (Choose two.)A) It builds an image that can be executed on all Cisco platforms.
B) It builds a Docker image that cannot be used directly on Cisco IOx.
C) It compiles a "hello world" program in C.
D) It creates two separate images.
E) It builds an IOx package that can be deployed directly.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
13
A company is collecting data from several thousand machines globally. Which software component in the overall architecture is the next destination of the dataflow after the data has been gathered and normalized on the edge data software?
A) relational database: MySQL
B) historian database: influxDB
C) message broker: Apache Kafka
D) dashboard: Node.js web app
A) relational database: MySQL
B) historian database: influxDB
C) message broker: Apache Kafka
D) dashboard: Node.js web app

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
14
Which two data sources are used with a visualization tool such as Grafana? (Choose two.)
A) Microsoft Power BI
B) Kibana
C) InfluxDB
D) Elasticsearch
E) Tableau
A) Microsoft Power BI
B) Kibana
C) InfluxDB
D) Elasticsearch
E) Tableau

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
15
Which two statements define the mechanism for console access of the Guest Operating System from the Cisco IR829 router? (Choose two.)
A) The Guest OS can be accessed by default on Telnet port 2070 from the Cisco IR829 console.
B) The Guest OS console is available directly by the AUX port 3362 from the Cisco IR829 router.
C) The Guest OS can be accessed directly using the console port on the Cisco IR829 router.
D) The Guest OS can be accessed by initiating SSH from the Cisco IR829 console.
E) The Guest OS console is available only when a static IP is configured on the host.
A) The Guest OS can be accessed by default on Telnet port 2070 from the Cisco IR829 console.
B) The Guest OS console is available directly by the AUX port 3362 from the Cisco IR829 router.
C) The Guest OS can be accessed directly using the console port on the Cisco IR829 router.
D) The Guest OS can be accessed by initiating SSH from the Cisco IR829 console.
E) The Guest OS console is available only when a static IP is configured on the host.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
16
When an RS232 device is connected to a Cisco IR829 router, the data collected is not being parsed correctly by the edge application. Which two steps should be taken to troubleshoot the issue? (Choose two.)
A) SSH access on the Cisco IR829 router must be enabled for IOx Guest OS.
B) Communication mode must be set to half duplex over serial connection.
C) Serial cable length should not exceed 1.5 meters.
D) Ensure that communication parameters like baud rate and parity are set correctly.
E) Set the cable connections based on the PIN layout from the sensor vendor.
A) SSH access on the Cisco IR829 router must be enabled for IOx Guest OS.
B) Communication mode must be set to half duplex over serial connection.
C) Serial cable length should not exceed 1.5 meters.
D) Ensure that communication parameters like baud rate and parity are set correctly.
E) Set the cable connections based on the PIN layout from the sensor vendor.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
17
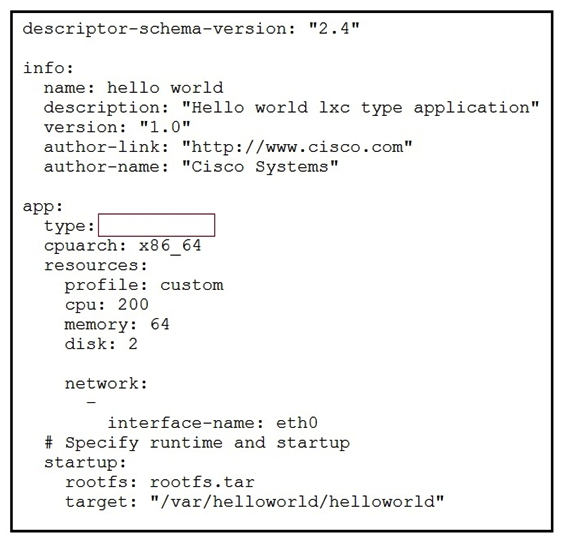 Refer to the exhibit. While troubleshooting an error on an application descriptor for a Docker app in Cisco IOx (package.yaml), the app type appears to be missing. Which app type must be added to the snippet to resolve the issue?
Refer to the exhibit. While troubleshooting an error on an application descriptor for a Docker app in Cisco IOx (package.yaml), the app type appears to be missing. Which app type must be added to the snippet to resolve the issue?A) paas
B) docker-vm
C) docker
D) docker-app

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
18
When constructing a Python script for data extraction using GMM APIs on a Cisco Kinetic Cloud platform, how should the API authentication be implemented?
A) Generate the API keys once and edit the permissions as needed.
B) Generate and use the API keys for the required access level from the Kinetic Cloud application.
C) Use a complex username and password with 128-bit encryption.
D) Use a complex username with an auto-generated password from the Kinetic Cloud application.
A) Generate the API keys once and edit the permissions as needed.
B) Generate and use the API keys for the required access level from the Kinetic Cloud application.
C) Use a complex username and password with 128-bit encryption.
D) Use a complex username with an auto-generated password from the Kinetic Cloud application.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
19
Which two actions must be completed before starting the process of sending IoT data to the cloud via edge routers? (Choose two.)
A) Measure the voltage, power rating, and quiescent current for the sensors that send data to the cloud.
B) Gather the hardware (MAC) addresses of local and cloud routers to ensure low latency communication.
C) Collect information about the CPU architecture in the cloud and edge to ensure that they match.
D) Gather the interval, the volume, and the latency that the data must be provisioned with.
E) Collect information about growth, required elasticity, and high availability of the provisioning process.
A) Measure the voltage, power rating, and quiescent current for the sensors that send data to the cloud.
B) Gather the hardware (MAC) addresses of local and cloud routers to ensure low latency communication.
C) Collect information about the CPU architecture in the cloud and edge to ensure that they match.
D) Gather the interval, the volume, and the latency that the data must be provisioned with.
E) Collect information about growth, required elasticity, and high availability of the provisioning process.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
20
A customer is deploying sensors with Cisco IR829 routers in moving trucks to continuously monitor the health of engines using a cloud application. Which data extraction and processing strategy is best suited in this environment?
A) No need to store data locally, upload in real time to the cloud for processing.
B) Generate local alerts and create reports at the edge, and upload to the cloud at the end of the day.
C) Use the store and forward mechanism to upload the information at the earliest to cloud.
D) Ensure that data is stored for a longer duration locally and upload to the cloud every week.
A) No need to store data locally, upload in real time to the cloud for processing.
B) Generate local alerts and create reports at the edge, and upload to the cloud at the end of the day.
C) Use the store and forward mechanism to upload the information at the earliest to cloud.
D) Ensure that data is stored for a longer duration locally and upload to the cloud every week.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
21
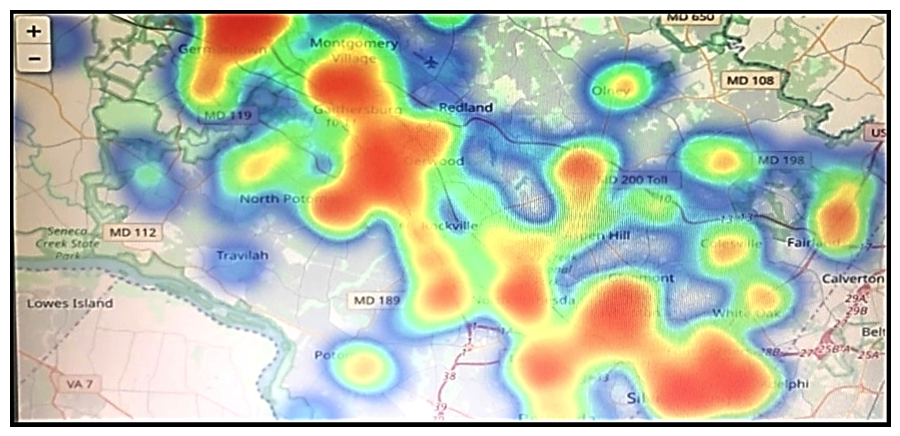 Refer to the exhibit. Which two statements are true? (Choose two.)
Refer to the exhibit. Which two statements are true? (Choose two.)A) That is a heatmap projected on top of a geographic map.
B) That is a treemap projected on top of a geographic map.
C) The color red usually stands for lower values and the color blue usually stands for higher values.
D) Another suitable visualization technique for this image would be line graphs.
E) The color blue usually stands for lower values and the color red usually stands for higher values.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
22
Which element ensures that PKI is used to establish the identity of IoT devices?
A) unique device identifier
B) encryption key
C) air gap
D) hashed routes
A) unique device identifier
B) encryption key
C) air gap
D) hashed routes

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
23
Which method is used to gather data from a sensor?
A) Configure the edge application to push data to the cloud.
B) Set up a rendezvous point where the sensor and edge application meet.
C) Set up a dedicate process for each sensor that grabs data.
D) Pull data from the sensor.
A) Configure the edge application to push data to the cloud.
B) Set up a rendezvous point where the sensor and edge application meet.
C) Set up a dedicate process for each sensor that grabs data.
D) Pull data from the sensor.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
24
Which action should be taken when a southbound device is not connecting?
A) Verify the gateway link status.
B) Review the edge application logs.
C) Verify the sensor status.
D) Redeploy the edge application.
A) Verify the gateway link status.
B) Review the edge application logs.
C) Verify the sensor status.
D) Redeploy the edge application.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
25
Mosquitto was installed correctly on the Cisco IR829 router as a Cisco IOx application. When the sensor is connected to the broker on the Cisco IR829 router with the default port, the connection is refused (Error Code 5). Which action should be done to resolve the issue?
A) Insert in the IOS config: ip nat inside source static tcp 1883 interface GigabitEthernet0 1883 Insert in the IOS config: ip nat inside source static tcp 1883 interface GigabitEthernet0 1883
B) Insert in the package_config.ini file under section ports: tcp: ["8883"] Insert in the package_config.ini file under section ports: tcp: ["8883"]
C) Use the correct username and password.
D) Insert in the package.yaml file under section ports: tcp: ["1883"] Insert in the package.yaml file under section ports: tcp: ["1883"]
A) Insert in the IOS config: ip nat inside source static tcp
B) Insert in the package_config.ini file under section ports: tcp: ["8883"] Insert in the package_config.ini file under section ports: tcp: ["8883"]
C) Use the correct username and password.
D) Insert in the package.yaml file under section ports: tcp: ["1883"] Insert in the package.yaml file under section ports: tcp: ["1883"]

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
26
After an application is deployed, potential issues arise around connectivity. As part of the troubleshooting process, the IP address must be determined to ensure end-to-end communication. Which method provides the required details using the Cisco IOx CLI?
A) ioxclient application status
B) ioxclient application metrics
C) ioxclient application getconfig
D) ioxclient application info
A) ioxclient application status
B) ioxclient application metrics
C) ioxclient application getconfig
D) ioxclient application info

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
27
Which command is used to package a Docker-style Cisco IOx app using ioxclient?
A) ioxclient docker create helloworld:1.0.
B) ioxclient docker-app helloworld:1.0.
C) ioxclient docker package helloworld:1.0.
D) ioxclient docker helloworld:1.0.
A) ioxclient docker create helloworld:1.0.
B) ioxclient docker-app helloworld:1.0.
C) ioxclient docker package helloworld:1.0.
D) ioxclient docker helloworld:1.0.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
28
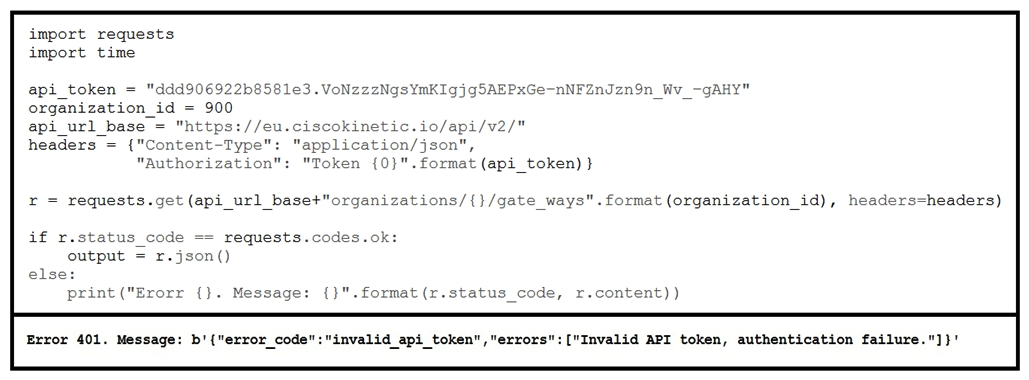 Refer to the exhibit. The code and the error message that are received when the code is run is presented. What causes issues authenticating with Cisco GMM API using the web-generated API key?
Refer to the exhibit. The code and the error message that are received when the code is run is presented. What causes issues authenticating with Cisco GMM API using the web-generated API key?A) firewall that blocks authentication ports
B) incorrect username and password
C) incorrect GMM Cluster selection
D) incorrect key size and data encryption

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
29
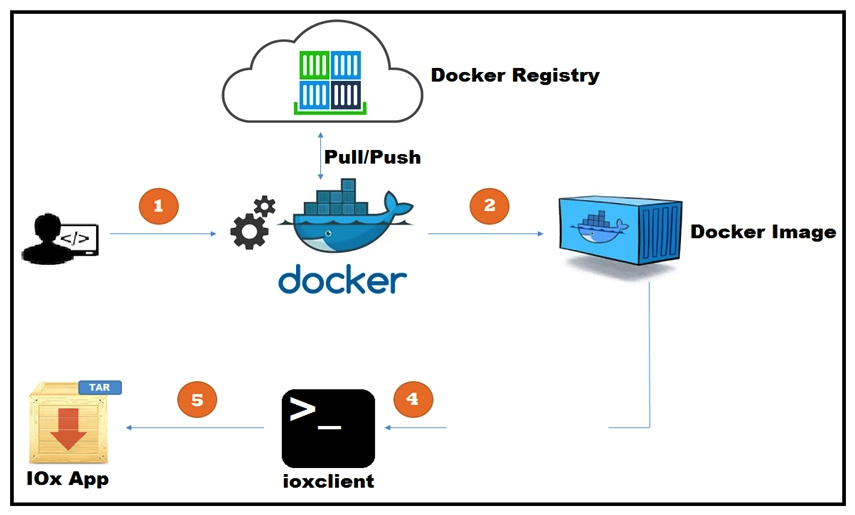 Refer to the exhibit. A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?
Refer to the exhibit. A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?A) Pull/push the image to the Docker registry.
B) Build the package.yaml files.
C) Build the package.cert file to sign the app.
D) Log in to device manager and load the application.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
30
Which computer security concept is violated when a web server is written that uses the "root" account for all interactions with a Linux system?
A) principle of least privilege
B) PermitRootLogin
C) certificate-based authentication
D) RBAC
A) principle of least privilege
B) PermitRootLogin
C) certificate-based authentication
D) RBAC

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
31
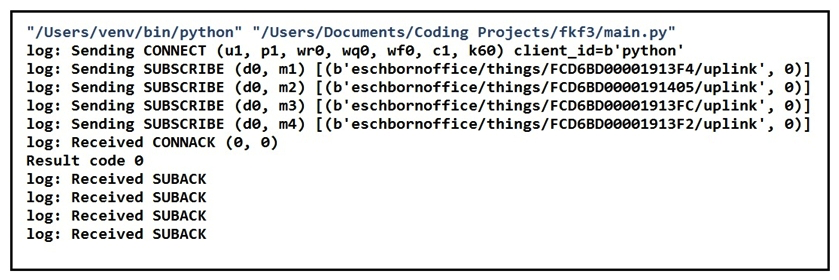 Refer to the exhibit. Which two statements about MQTT messaging are true? (Choose two.)
Refer to the exhibit. Which two statements about MQTT messaging are true? (Choose two.)A) Result code 5 means the connection is accepted; result code 0 means the connection is "refused, not authorized".
B) Redundant ClientIDs are supported by MQTT brokers.
C) MQTT does not support a "keep alive" functionality because it runs on top of TCP.
D) Result code 0 means the connection is accepted; result code 5 means the connection is "refused, not authorized".
E) Brokers can send the Last Will and Testament messages on behalf of the client.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
32
As part of an IoT project, an organization is developing an edge application that will run on a gateway to securely transmit sensor information it receives into an IoT cloud. Based on the Agile software development lifecycle, the development team is planning to implement a CI/CD pipeline. Which two methods should be suggested to make the software development lifecycle more secure during the implementation and testing? (Choose two.)
A) Perform automated code reviews prior to deployment.
B) Implement auto-provisioning security inspection for the code.
C) Perform on-going penetration testing on the system.
D) Perform a GAP analysis on current security activities and policies.
E) Train members of the team in a secure software development lifecycle methodology such as OWASP.
A) Perform automated code reviews prior to deployment.
B) Implement auto-provisioning security inspection for the code.
C) Perform on-going penetration testing on the system.
D) Perform a GAP analysis on current security activities and policies.
E) Train members of the team in a secure software development lifecycle methodology such as OWASP.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
33
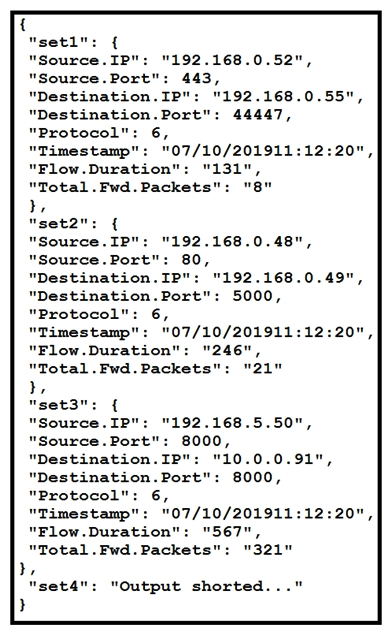 Refer to the exhibit. The code snippet provides information about the packet captures within a network. How can the most used source IP addresses within a specific time be visualized?
Refer to the exhibit. The code snippet provides information about the packet captures within a network. How can the most used source IP addresses within a specific time be visualized?A) line graph
B) bar histogram
C) scatter plot
D) heatmap

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
34
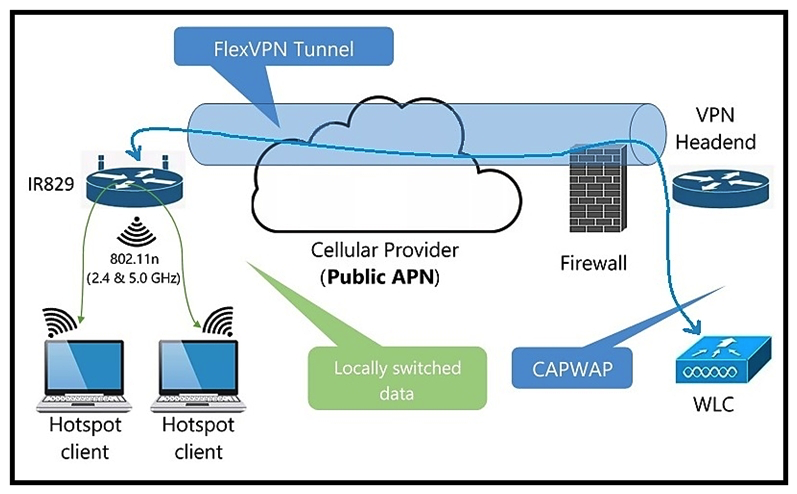 Refer to the exhibit. Which protocol is used to make a FlexVPN connection from a Cisco IR829 router to a headend router?
Refer to the exhibit. Which protocol is used to make a FlexVPN connection from a Cisco IR829 router to a headend router?A) SSL
B) IKEv2
C) NAT
D) IS-IS

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
35
Which lightweight protocol is used to send data from the edge compute resources to the cloud?
A) MQTT
B) XMPP
C) AMQP
D) MT Connect
A) MQTT
B) XMPP
C) AMQP
D) MT Connect

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
36
What are two functionalities of edge data services? (Choose two.)
A) creating a machine learning data model
B) supporting many interfaces and APIs
C) applying advanced data analytics
D) filtering, normalizing and aggregating data
E) saving data for a prolonged time period
A) creating a machine learning data model
B) supporting many interfaces and APIs
C) applying advanced data analytics
D) filtering, normalizing and aggregating data
E) saving data for a prolonged time period

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
37
An IoT engineer is working on a connected machines project. Which two protocols must be used during the data provisioning process when data is sent from the shop floor IoT system to the customer's public cloud? (Choose two.)
A) COAP
B) Modbus TCP
C) MQTT
D) AMQP
E) OPC-DA
A) COAP
B) Modbus TCP
C) MQTT
D) AMQP
E) OPC-DA

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
38
Which two security approaches help build a strong authentication scheme? (Choose two.)
A) connection based on location
B) session IDs accepted only from cookies
C) maximum allowed connections
D) user logout
E) session logout because of inactivity
A) connection based on location
B) session IDs accepted only from cookies
C) maximum allowed connections
D) user logout
E) session logout because of inactivity

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
39
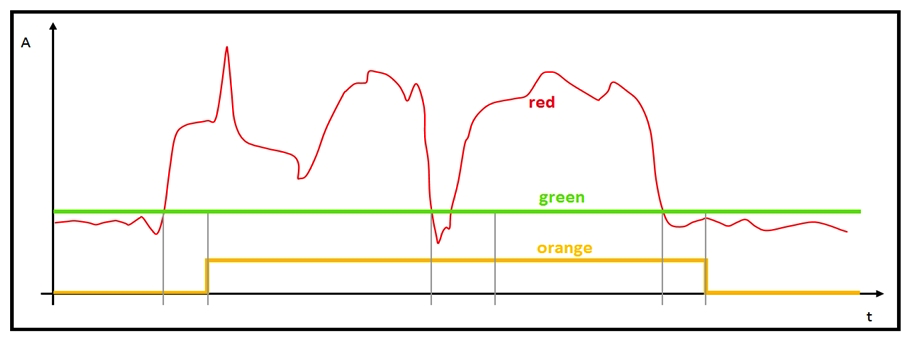 Refer to the exhibit. The red line represents the energy consumption of an industrial machine. Which two statements about the graphs are true? (Choose two.)
Refer to the exhibit. The red line represents the energy consumption of an industrial machine. Which two statements about the graphs are true? (Choose two.)A) The orange graph is expected to drop to zero for a brief period around the midpoint on the x axis. The orange graph is expected to drop to zero for a brief period around the midpoint on the x axis.
B) The red graph contains the raw data points.
C) The green graph is the mean value of the data points.
D) The green graph does not give us any valuable information.
E) The orange graph has three values on the y -axis. The orange graph has three values on the y -axis.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
40
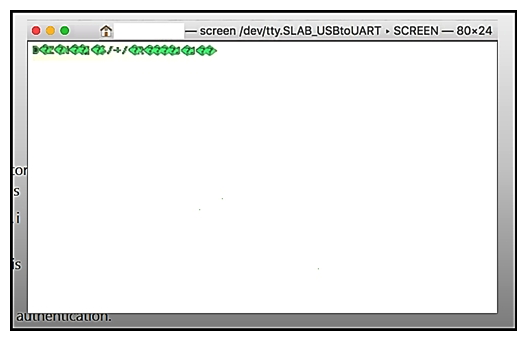 Refer to the exhibit. When a laptop is connected to a device via a serial connection, which action makes the output readable?
Refer to the exhibit. When a laptop is connected to a device via a serial connection, which action makes the output readable?A) Change the baudrate in the connection settings.
B) Reboot the device in case a firmware error is the issue.
C) Change the power level of the device.
D) Change the unicode settings to UTF-8.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck
41
Which method defines the integration of Cisco Industrial Network Director with the Cisco identity Service Engine?
A) Cisco IND integrates with ISE via Cisco Strealthwatch services.
B) Cisco IND integrates with ISE using RADIUS services.
C) Cisco IND is registered with pxGrid on ISE as a publisher.
D) Cisco IND pulls the profiling information from ISE.
A) Cisco IND integrates with ISE via Cisco Strealthwatch services.
B) Cisco IND integrates with ISE using RADIUS services.
C) Cisco IND is registered with pxGrid on ISE as a publisher.
D) Cisco IND pulls the profiling information from ISE.

Unlock Deck
Unlock for access to all 41 flashcards in this deck.
Unlock Deck
k this deck


