Deck 43: CCDE Design Written
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/145
Play
Full screen (f)
Deck 43: CCDE Design Written
1
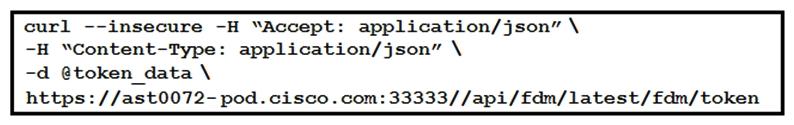 Refer to the exhibit. The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file "@token_data" that cURL is handling?
Refer to the exhibit. The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file "@token_data" that cURL is handling?A) This file is a container to log possible error responses in the request.
B) This file is given as input to store the access token received from FDM.
C) This file is used to send authentication-related headers.
D) This file contains raw data that is needed for token authentication.
This file is given as input to store the access token received from FDM.
2
Which two methods are API security best practices? (Choose two.)
A) Use tokens after the identity of a client has been established.
B) Use the same operating system throughout the infrastructure.
C) Use encryption and signatures to secure data.
D) Use basic auth credentials over all internal API interactions.
E) Use cloud hosting services to manage security configuration.
A) Use tokens after the identity of a client has been established.
B) Use the same operating system throughout the infrastructure.
C) Use encryption and signatures to secure data.
D) Use basic auth credentials over all internal API interactions.
E) Use cloud hosting services to manage security configuration.
Use tokens after the identity of a client has been established.
Use encryption and signatures to secure data.
Use encryption and signatures to secure data.
3
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have been received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances. Which two actions can improve the design of the application to identify the faults? (Choose two.)
A) Automatically pull out the container that fails the most over a time period.
B) Implement a tagging methodology that follows the application execution from service to service.
C) Add logging on exception and provide immediate notification.
D) Do a write to the datastore every time there is an application failure.
E) Implement an SNMP logging system with alerts in case a network link is slow.
A) Automatically pull out the container that fails the most over a time period.
B) Implement a tagging methodology that follows the application execution from service to service.
C) Add logging on exception and provide immediate notification.
D) Do a write to the datastore every time there is an application failure.
E) Implement an SNMP logging system with alerts in case a network link is slow.
Implement a tagging methodology that follows the application execution from service to service.
Add logging on exception and provide immediate notification.
Add logging on exception and provide immediate notification.
4
Which RFC5988 (Web Linking) relation type is used in the Link header to control pagination in APIs?
A) rel="index"
B) rel="page"
C) rel="next"
D) rel="section"
A) rel="index"
B) rel="page"
C) rel="next"
D) rel="section"

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
5
Where should distributed load balancing occur in a horizontally scalable architecture?
A) firewall-side/policy load balancing
B) network-side/central load balancing
C) service-side/remote load balancing
D) client-side/local load balancing
A) firewall-side/policy load balancing
B) network-side/central load balancing
C) service-side/remote load balancing
D) client-side/local load balancing

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
6
A developer has completed the implementation of a REST API, but when it is executed, it returns a 401 error message. What must be done on the API to resolve the issue?
A) Access permission to the resource must be granted, before the request.
B) Configure new valid credentials.
C) The requested API endpoint does not exist, and the request URL must be changed.
D) Additional permission must be granted before the request can submitted.
A) Access permission to the resource must be granted, before the request.
B) Configure new valid credentials.
C) The requested API endpoint does not exist, and the request URL must be changed.
D) Additional permission must be granted before the request can submitted.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
7
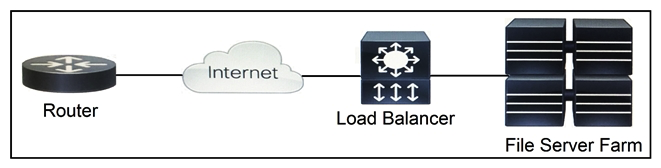 Refer to the exhibit. Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
Refer to the exhibit. Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)A) Terminate the TLS over the UDP connection from the router and originate an HTTPS connection to the selected server.
B) Terminate the TLS over the UDP connection from the router and originate an HTTP connection to the selected server.
C) Terminate the TLS over the TCP connection from the router and originate an HTTP connection to the selected server.
D) Terminate the TLS over the TCP connection from the router and originate an HTTPS connection to the selected server.
E) Terminate the TLS over the SCTP connection from the router and originate an HTTPS connection to the selected server.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
8
A network operations team is using the cloud to automate some of their managed customer and branch locations. They require that all of their tooling be ephemeral by design and that the entire automation environment can be recreated without manual commands. Automation code and configuration state will be stored in git for change control and versioning. The engineering high-level plan is to use VMs in a cloud-provider environment then configure open source tooling onto these VMs to poll, test, and configure the remote devices, as well as deploy the tooling itself. Which configuration management and/or automation tooling is needed for this solution?
A) Ansible
B) Ansible and Terraform
C) NSO
D) Terraform
E) Ansible and NSO
A) Ansible
B) Ansible and Terraform
C) NSO
D) Terraform
E) Ansible and NSO

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
9
An Etag header is included in the HTTP response for an API resource. What are two benefits of using the value of the Etag for future interactions involving the same API resource? (Choose two.)
A) caching and optimization of response payloads
B) creating conditional requests
C) categorizing and comparing this API resource with others
D) checking the integrity of the resource
E) requesting the list of operations authorized for this resource
A) caching and optimization of response payloads
B) creating conditional requests
C) categorizing and comparing this API resource with others
D) checking the integrity of the resource
E) requesting the list of operations authorized for this resource

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
10
User report that they can no longer able to process transactions with the online ordering application, and the logging dashboard is displaying these messages. Fri Jan 10 19:37:31.123 EST 2020 [FRONTEND] INFO: Incoming request to add item to cart from user 45834534858 Fri Jan 10 19:37:31 247 EST 2020 [BACKEND] INFO: Attempting to add item to cart Fri Jan 10 19:37:31 250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused What is causing the problem seen in these log messages?
A) The database server container has crashed.
B) The backend process is overwhelmed with too many transactions.
C) The backend is not authorized to commit to the database.
D) The user is not authorized to add the item to their cart.
A) The database server container has crashed.
B) The backend process is overwhelmed with too many transactions.
C) The backend is not authorized to commit to the database.
D) The user is not authorized to add the item to their cart.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
11
Which two statements about a stateless application are true? (Choose two.)
A) Different requests can be processed by different servers.
B) Requests are based only on information relayed with each request.
C) Information about earlier requests must be kept and must be accessible.
D) The same server must be used to process all requests that are linked to the same state.
E) No state information can be shared across servers.
A) Different requests can be processed by different servers.
B) Requests are based only on information relayed with each request.
C) Information about earlier requests must be kept and must be accessible.
D) The same server must be used to process all requests that are linked to the same state.
E) No state information can be shared across servers.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
12
How should a web application be designed to work on a platform where up to 1000 requests per second can be served?
A) Use algorithms like random early detection to deny excessive requests.
B) Set a per-user limit (for example, 5 requests/minute/ user) and deny the requests from the users who have reached the limit.
C) Only 1000 user connections are allowed; further connections are denied so that all connected users can be served.
D) All requests are saved and processed one by one so that all users can be served eventually.
A) Use algorithms like random early detection to deny excessive requests.
B) Set a per-user limit (for example, 5 requests/minute/ user) and deny the requests from the users who have reached the limit.
C) Only 1000 user connections are allowed; further connections are denied so that all connected users can be served.
D) All requests are saved and processed one by one so that all users can be served eventually.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
13
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
A) Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
B) Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
C) Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
D) Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
A) Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
B) Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
C) Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
D) Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
14
 Refer to the exhibit. An Intersight API is being used to query RackUnit resources that have a tag keyword set to "Site". What is the expected output of this command?
Refer to the exhibit. An Intersight API is being used to query RackUnit resources that have a tag keyword set to "Site". What is the expected output of this command?A) list of all resources that have a tag with the keyword "Site"
B) error message because the Value field was not specified
C) error message because the tag filter should be lowercase
D) list of all sites that contain RackUnit tagged compute resources

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
15
Which two data encoding techniques are supported by gRPC? (Choose two.)
A) XML
B) JSON
C) ASCII
D) ProtoBuf
E) YAML
A) XML
B) JSON
C) ASCII
D) ProtoBuf
E) YAML

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
16
Which statement about microservices architecture is true?
A) Applications are written in a single unit.
B) It is a complex application composed of multiple independent parts.
C) It is often a challenge to scale individual parts.
D) A single faulty service can bring the whole application down.
A) Applications are written in a single unit.
B) It is a complex application composed of multiple independent parts.
C) It is often a challenge to scale individual parts.
D) A single faulty service can bring the whole application down.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
17
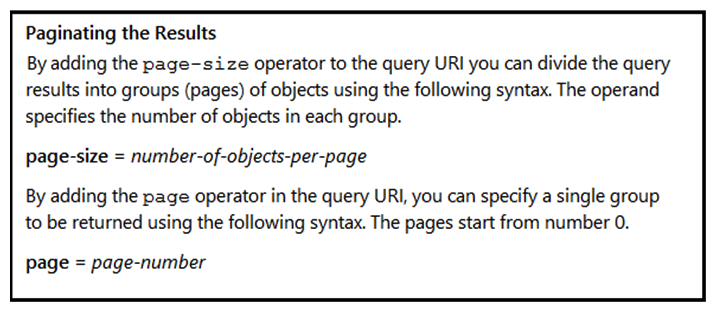 Refer to the exhibit. Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 31 through 45?
Refer to the exhibit. Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 31 through 45?A) GET https://apic-ip-address/api/class/faultInfo.json?\order-by=faultinst.severity|desc&page=1&page-size=15
B) GET https://apic-ip-address/api/class/faultInfo.json?\order-by=faultinst.severity|desc&page=2&page-size=15
C) GET https://apic-ip-address/api/class/faultInfo.json?\order-by=faultinst.severity|desc&page-size=30
D) GET https://apic-ip-address/api/class/faultInfo.json?\order-by=faultinst.severity|desc&page=2&page-size=30

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
18
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScnpt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline. Which step should be omitted from the pipeline?
A) Deploy the code to one or more environments, such as staging and/or production.
B) Build one of more containers that package up code and all its dependencies.
C) Compile code.
D) Run automated tests to validate the code.
A) Deploy the code to one or more environments, such as staging and/or production.
B) Build one of more containers that package up code and all its dependencies.
C) Compile code.
D) Run automated tests to validate the code.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
19
A client is written that uses a REST API to interact with a server. Using HTTPS as the transport, an HTTP request is sent and received an HTTP response. The response contains the HTTP response status code: 503 Service Unavailable. Which action is the appropriate response?
A) Add an Authorization header that supplies appropriate credentials and sends the updated request.
B) Resend the request using HTTP as the transport instead of HTTPS.
C) Add an Accept header that indicates the content types that the client understands and send the updated request.
D) Look for a Retry-After header in the response and resend the request after the amount of time indicated.
A) Add an Authorization header that supplies appropriate credentials and sends the updated request.
B) Resend the request using HTTP as the transport instead of HTTPS.
C) Add an Accept header that indicates the content types that the client understands and send the updated request.
D) Look for a Retry-After header in the response and resend the request after the amount of time indicated.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
20
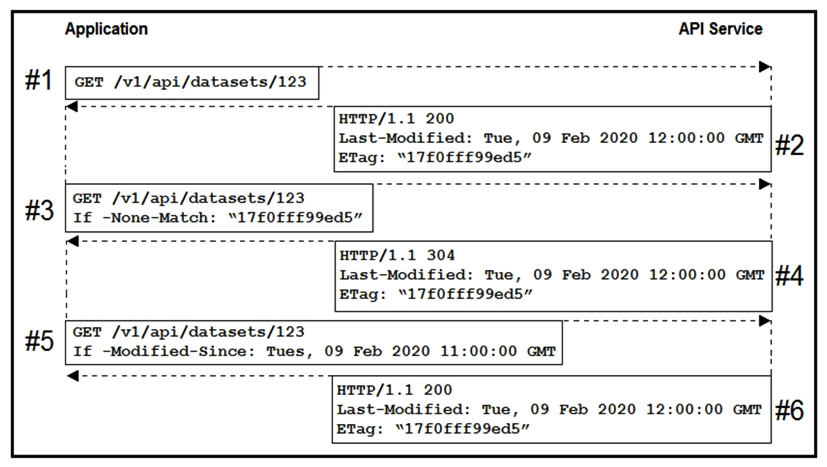 Refer to the exhibit. An application uses an API to periodically sync a large data set. Based on the HTTP message sequence provided, which statements are true about the caching behavior seen in the scenario? (Choose two.)
Refer to the exhibit. An application uses an API to periodically sync a large data set. Based on the HTTP message sequence provided, which statements are true about the caching behavior seen in the scenario? (Choose two.)A) The full dataset was transmitted to the client twice.
B) The dataset changed sometime between message #4 and #5.
C) A partial dataset was transmitted to the client in message #4.
D) The dataset did not change during the scenario.
E) Messages #3 and #5 are equivalent.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
21
Which two actions must be taken when an observable microservice application is developed? (Choose two.)
A) Know the state of a single instance of a single service.
B) Place "try/except" statement in code.
C) Place log statements in the code.
D) Use distributed tracing techniques.
E) Deploy microservice to multiple datacenters.
A) Know the state of a single instance of a single service.
B) Place "try/except" statement in code.
C) Place log statements in the code.
D) Use distributed tracing techniques.
E) Deploy microservice to multiple datacenters.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
22
Click on the GET Resource button above to view resources that will help with this question. 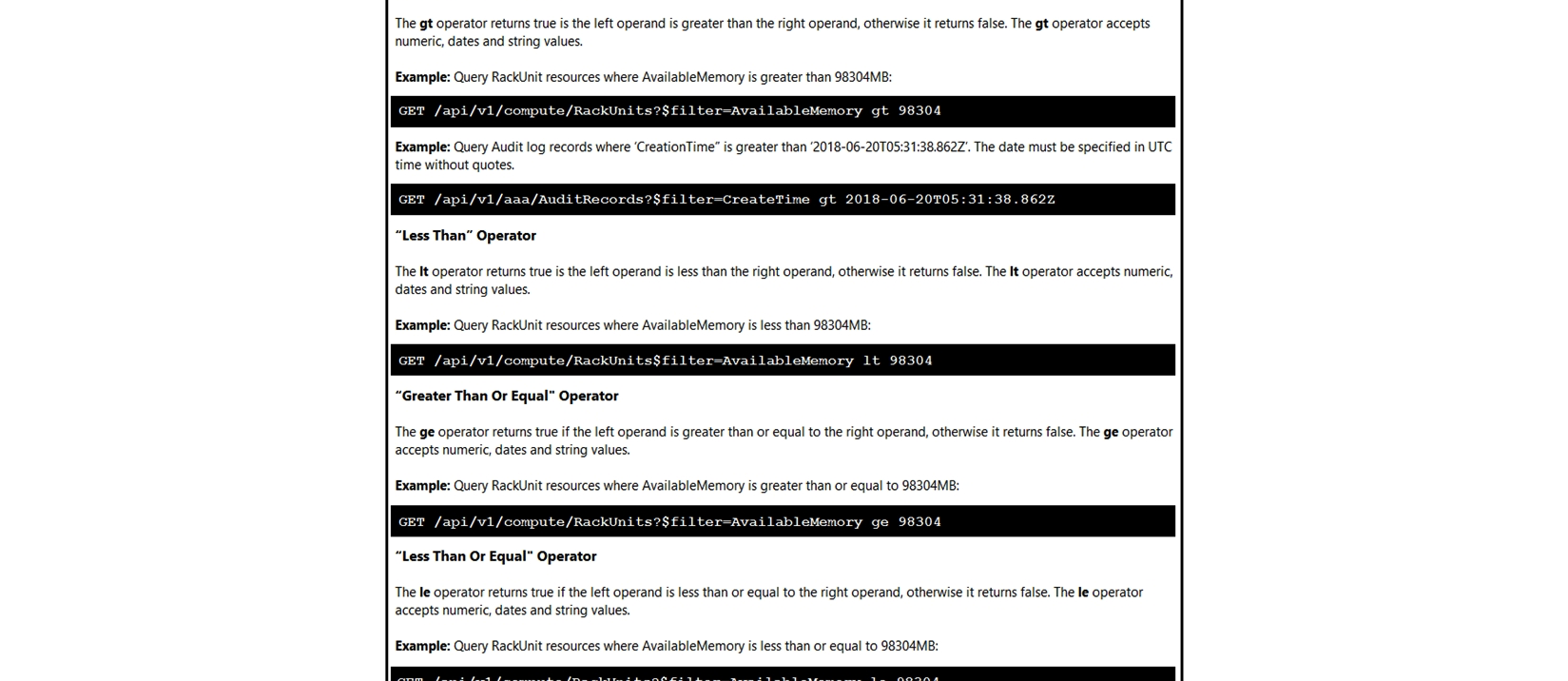
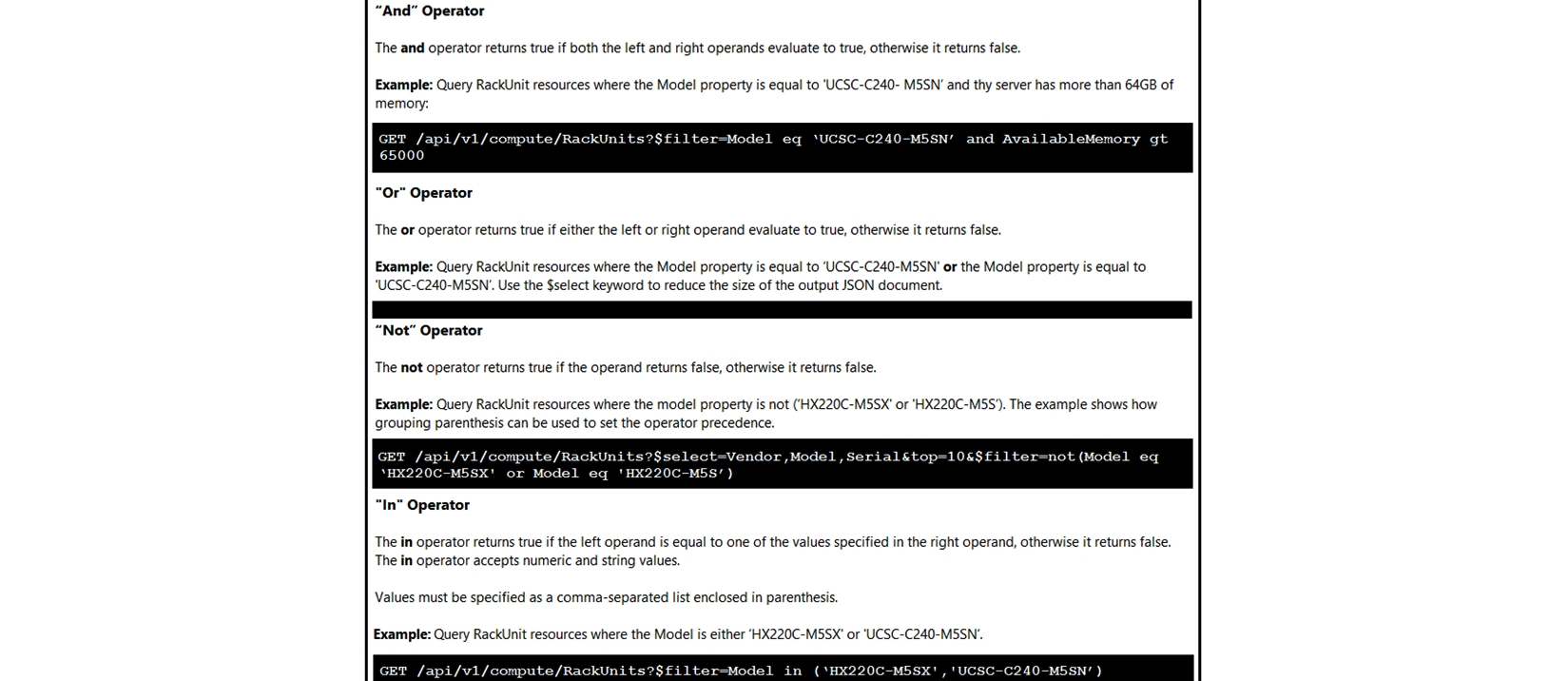
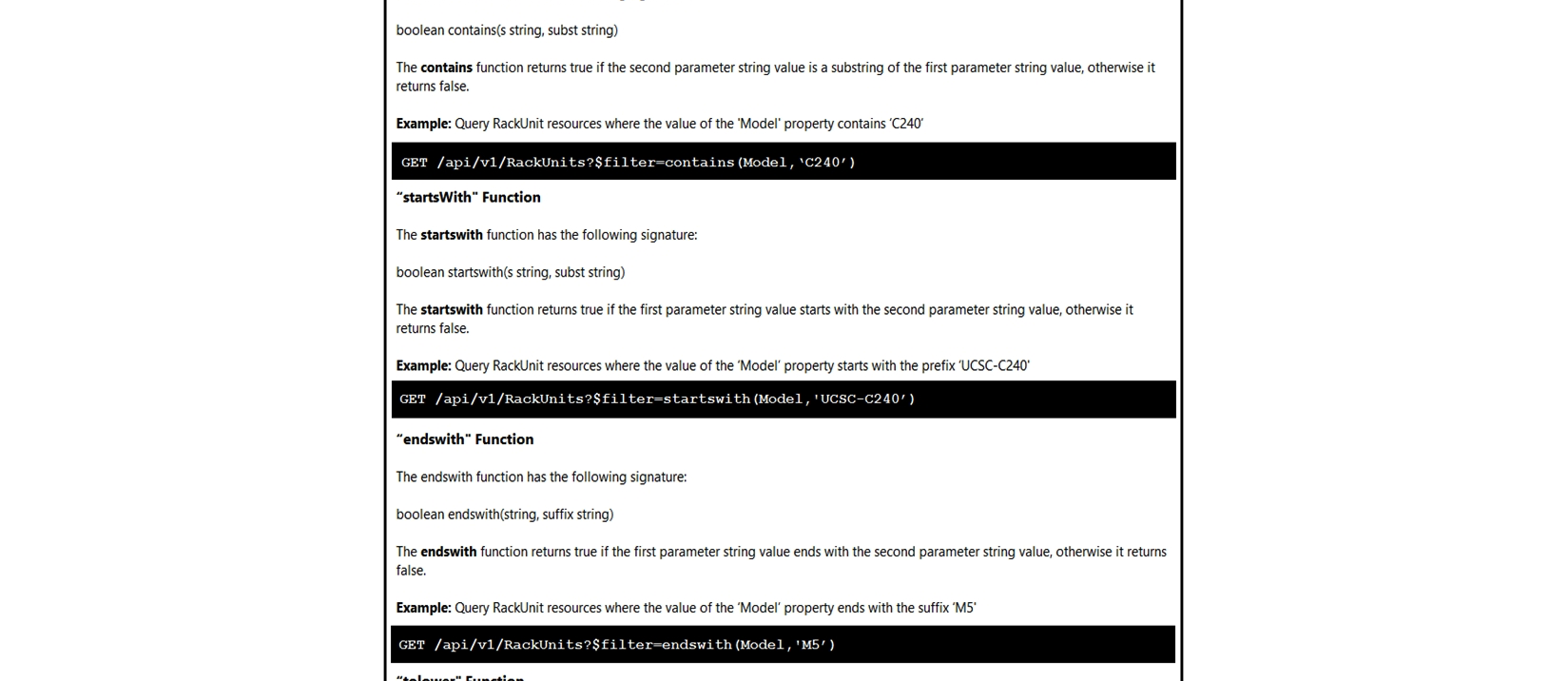 An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
A) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=not(Model eq 'UCSC') and AvailableMemory le 5000
B) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=Model eq 'UCSB' and AvailableMemory lt 5000
C) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=contains(Model, UCSB') and AvailableMemory lt 5000
D) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=contains(Model, UCSB') and AvailableMemory le 5000


 An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?A) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=not(Model eq 'UCSC') and AvailableMemory le 5000
B) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=Model eq 'UCSB' and AvailableMemory lt 5000
C) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=contains(Model, UCSB') and AvailableMemory lt 5000
D) GET/api/v1/compute/RackUnits?$select=Vendor,Model,Serial&$filter=contains(Model, UCSB') and AvailableMemory le 5000

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
23
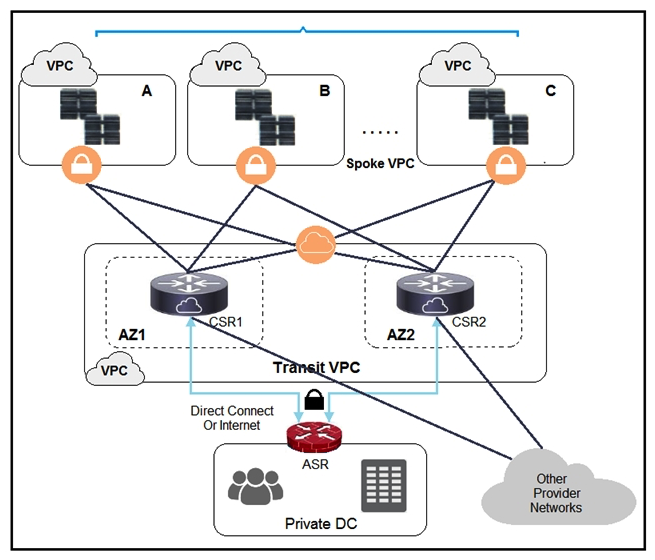 Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)A) Dynamic routing combined with multi-AZ- deployment creates a robust network infrastructure.
B) VPC virtual gateways provide highly available connections to virtual networks.
C) Dedicated VPC simplifies load balancing by combining internal and external web services.
D) VPC virtual gateways provide more secure connections to virtual networks.
E) Dedicated VPC simplifies routing by not combining this service with other shared services.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
24
On a Cisco Catalyst 9300 Series Switch, the guest shell is being used to create a service within a container. Which change is needed to allow the service to have external access?
A) Apply ip nat overload on VirtualPortGroup0. Apply ip nat overload on VirtualPortGroup0.
B) Apply ip nat inside on Interface VirtualPortGroup0. ip nat inside on Interface VirtualPortGroup0.
C) Apply ip nat outside on Interface VirtualPortGroup0. ip nat outside
D) Apply ip nat inside on Interface GigabitEthernet1. on Interface GigabitEthernet1.
A) Apply ip nat overload on VirtualPortGroup0. Apply ip nat overload on VirtualPortGroup0.
B) Apply ip nat inside on Interface VirtualPortGroup0. ip nat inside on Interface VirtualPortGroup0.
C) Apply ip nat outside on Interface VirtualPortGroup0. ip nat outside
D) Apply ip nat inside on Interface GigabitEthernet1. on Interface GigabitEthernet1.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
25
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
A) It checks for potential tainted data where input is not checked.
B) It enforces proper coding standards and style.
C) It performs a quick analysis of whether tests will pass or fail when run.
D) It checks for race conditions in threaded applications.
E) It estimates the performance of the code when run.
A) It checks for potential tainted data where input is not checked.
B) It enforces proper coding standards and style.
C) It performs a quick analysis of whether tests will pass or fail when run.
D) It checks for race conditions in threaded applications.
E) It estimates the performance of the code when run.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
26
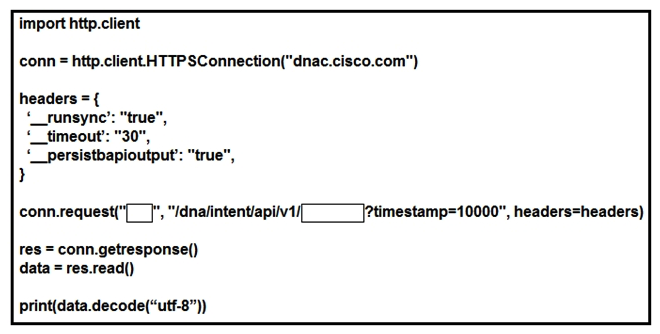 Refer to the exhibit. Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?
Refer to the exhibit. Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?A) PUT; network-health;
B) GET; client-health;
C) GET; network-device;
D) POST; network-device;

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
27
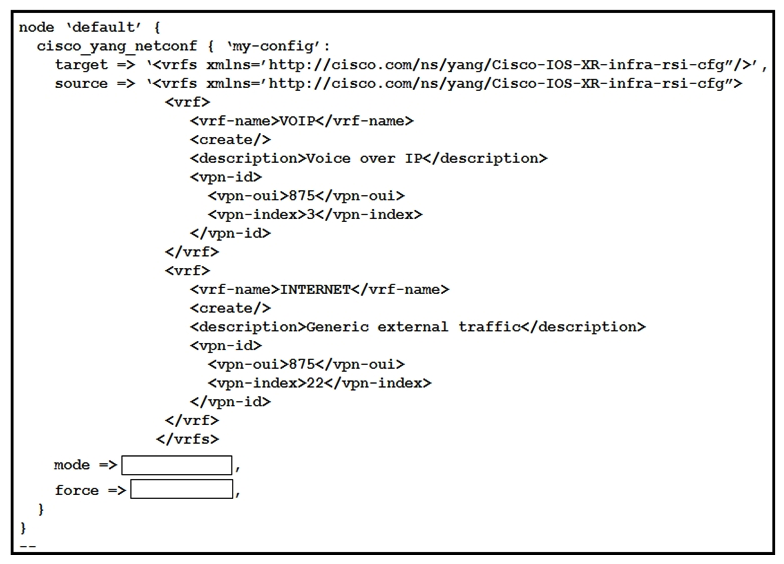 Refer to the exhibit. This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type. Which two words are required to complete the script? (Choose two.)
Refer to the exhibit. This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type. Which two words are required to complete the script? (Choose two.)A) ensure
B) commit
C) false
D) replace
E) none

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
28
Which two principles are included in the codebase tenet of the 12-factor app methodology? (Choose two.)
A) An application is always tracked in a version control system.
B) There are multiple codebases per application.
C) The codebase is the same across all deploys.
D) There can be a many-to-one correlation between codebase and application.
E) It is only possible to have one application deployment per codebase.
A) An application is always tracked in a version control system.
B) There are multiple codebases per application.
C) The codebase is the same across all deploys.
D) There can be a many-to-one correlation between codebase and application.
E) It is only possible to have one application deployment per codebase.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
29
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
A) URI to which the authorization server will send the user-agent back when access is granted or denied
B) list of the API resources that the application is requesting to access
C) secret that was generated by the authorization server when the application registered as an OAuth integration
D) list of scopes that correspond to the API resources to which the application is requesting to access
E) name of the application under which the application registered as an OAuth integration
A) URI to which the authorization server will send the user-agent back when access is granted or denied
B) list of the API resources that the application is requesting to access
C) secret that was generated by the authorization server when the application registered as an OAuth integration
D) list of scopes that correspond to the API resources to which the application is requesting to access
E) name of the application under which the application registered as an OAuth integration

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
30
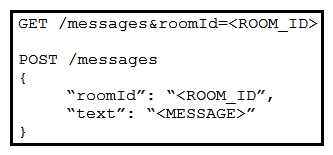
 Refer to the exhibit. Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
Refer to the exhibit. Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?A)
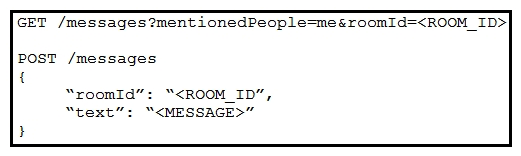
B)
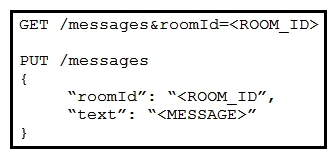
C)
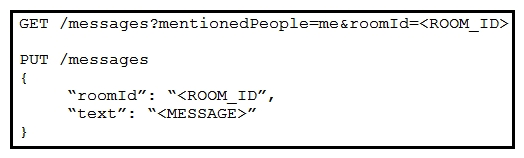
D)

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
31
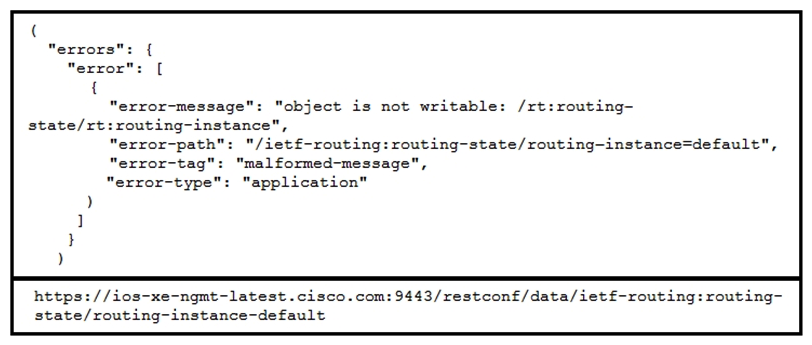 Refer to the exhibits above and click on the IETF Routing tab in the top left corner to help with this question. A developer is trying to update the routing instance by adding a new route to the routes list using the URL in the exhibit. What action must be taken to fix the error being received?
Refer to the exhibits above and click on the IETF Routing tab in the top left corner to help with this question. A developer is trying to update the routing instance by adding a new route to the routes list using the URL in the exhibit. What action must be taken to fix the error being received?A) Fix the body being sent to update the routes list
B) Change the HTTP Method being used to make the change
C) Change the url to "/ietf-routing:routing/routing-instance=default"
D) Update the authorization credentials
E) Change the URL to "/ietf-routing:routing-instance/default"

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
32
Which two techniques protect against injection attacks? (Choose two.)
A) input validation
B) trim whitespace
C) limit text areas to 255 characters
D) string escaping of user free text and data entry
E) only use dropdown, checkbox, and radio button fields
A) input validation
B) trim whitespace
C) limit text areas to 255 characters
D) string escaping of user free text and data entry
E) only use dropdown, checkbox, and radio button fields

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
33
 Refer to the exhibit. This snippet of a script has recently started exiting abnormally with an exception stating " Unexpected HTTP Response code: 429 ". Which solution handles rate limiting by the remote API?
Refer to the exhibit. This snippet of a script has recently started exiting abnormally with an exception stating " Unexpected HTTP Response code: 429 ". Which solution handles rate limiting by the remote API?A)
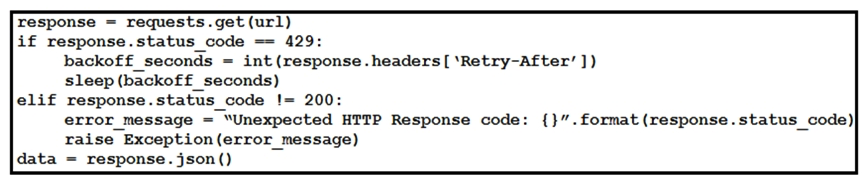
B)

C)
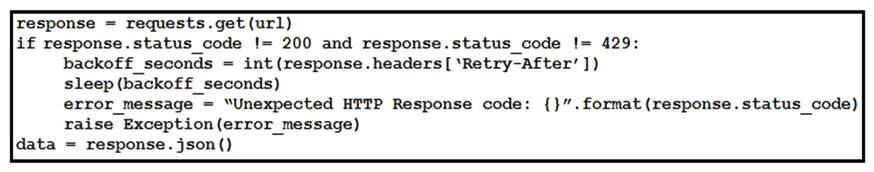
D)
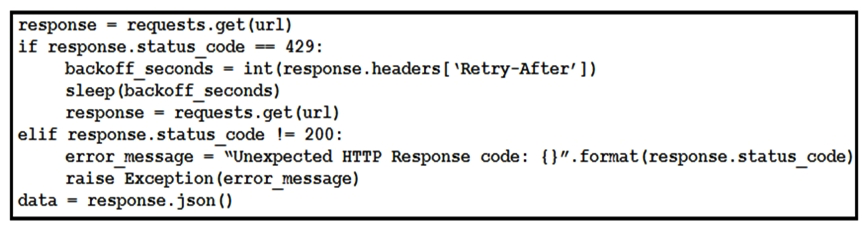

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
34
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch. Which two interface configuration options should be used? (Choose two.)
A) trunk interface
B) bridged virtual interface
C) SPAN port
D) management interface
E) subinterface
A) trunk interface
B) bridged virtual interface
C) SPAN port
D) management interface
E) subinterface

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
35
The Meraki API url https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been stored in the environment variable meraki_url , and the API key has been stored in meraki_api_key . Which snippet presents the correct API call to configure, secure, and enable an SSID using the Meraki API?
A)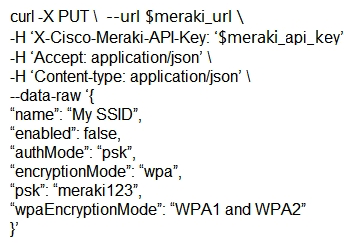
B)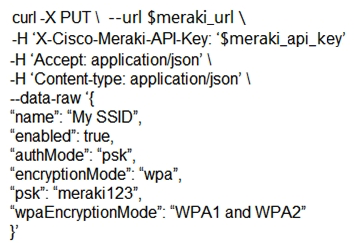
C)
D)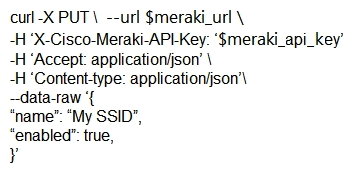
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
36
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
A) initial-template
B) updating-template
C) abstract-template
D) attached-template
E) base-template
A) initial-template
B) updating-template
C) abstract-template
D) attached-template
E) base-template

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
37
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority. Which approach must be taken to secure API keys and passwords?
A) Embed them directly in the code.
B) Store them in a hidden file.
C) Store them inside the source tree of the application.
D) Change them periodically.
A) Embed them directly in the code.
B) Store them in a hidden file.
C) Store them inside the source tree of the application.
D) Change them periodically.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
38
What is submitted when an SSL certificate is requested?
A) PEM
B) CRT
C) DER
D) CSR
A) PEM
B) CRT
C) DER
D) CSR

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
39
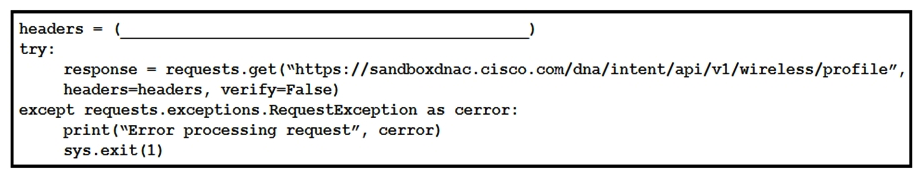 Refer to the exhibit. Which code snippet is required in the headers to successfully authorize wireless information from Cisco DNA Center?
Refer to the exhibit. Which code snippet is required in the headers to successfully authorize wireless information from Cisco DNA Center?A) headers = {'X-auth-token':'fa8426a0-8eaf-4d22-8e13-7c1b16a9370c'}
B) headers = {'Authorization':'Basic YWRtaW46R3JhcGV2aW5IMQ=='}
C) headers = {'Authorization':'Bearer ASDNFALKJER23412RKDALSNKF'}
D) headers = {'Content-type':'application/json'}

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
40
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
A) external USB storage
B) internal SSD
C) CD-ROM
D) SD-card
E) bootflash
A) external USB storage
B) internal SSD
C) CD-ROM
D) SD-card
E) bootflash

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
41
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online. Which configuration management and/or automation tooling is needed for this solution?
A) Ansible
B) Ansible and Terraform
C) NSO
D) Terraform
E) Ansible and NSO
A) Ansible
B) Ansible and Terraform
C) NSO
D) Terraform
E) Ansible and NSO

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
42
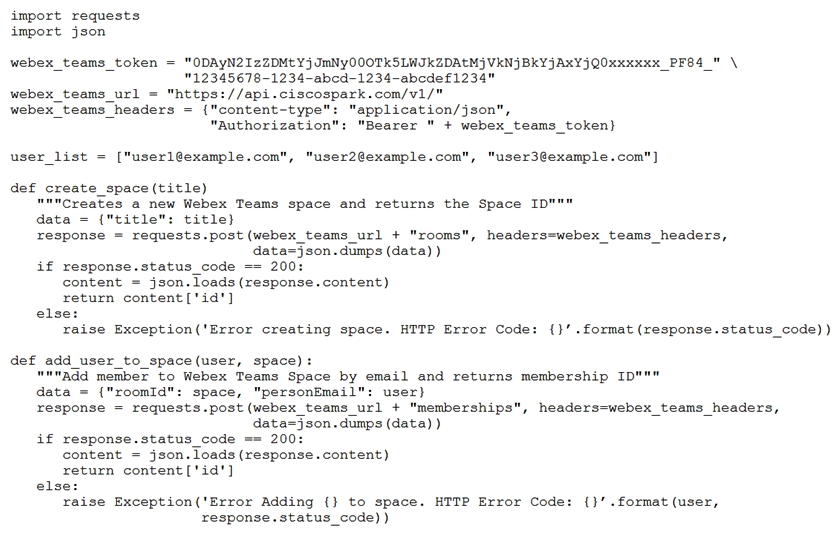 Refer to the exhibit. Which snippet creates a Webex Teams space and adds the users in the variable user_list to that space?
Refer to the exhibit. Which snippet creates a Webex Teams space and adds the users in the variable user_list to that space?A)
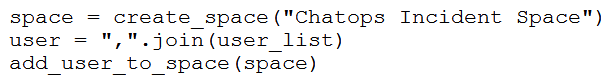
B)
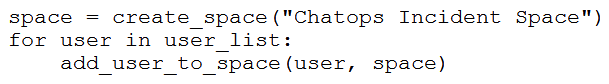
C)
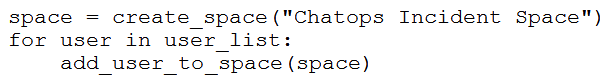
D)
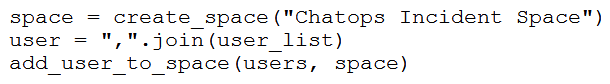

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
43
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
A) Puppet for orchestration
B) Terraform for orchestration
C) Terraform for configuration
D) Ansible for orchestration
E) Ansible for configuration
A) Puppet for orchestration
B) Terraform for orchestration
C) Terraform for configuration
D) Ansible for orchestration
E) Ansible for configuration

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
44
Which two strategies are used to protect personally identifiable information? (Choose two.)
A) Encrypt data in transit.
B) Encrypt hash values of data.
C) Encrypt data at rest.
D) Only hash usernames and passwords for efficient lookup.
E) Only encrypt usernames and passwords for efficient lookup.
A) Encrypt data in transit.
B) Encrypt hash values of data.
C) Encrypt data at rest.
D) Only hash usernames and passwords for efficient lookup.
E) Only encrypt usernames and passwords for efficient lookup.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
45
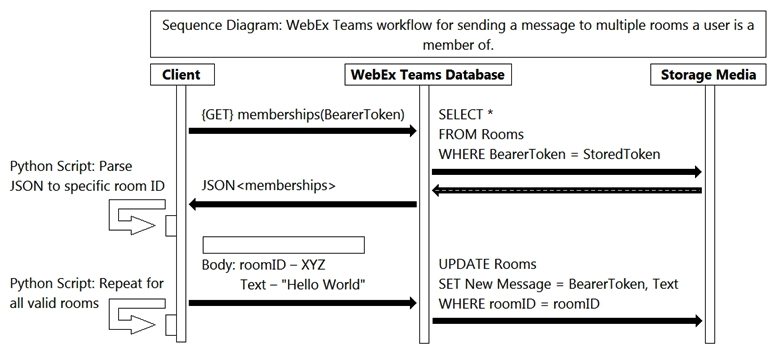 Refer to the exhibit. Which action will complete the workflow that represents how an API call sends multiple messages?
Refer to the exhibit. Which action will complete the workflow that represents how an API call sends multiple messages?A) {PUT} messages(roomID)
B) {PUT} messages(BearerToken)
C) {POST} messages(roomID)
D) {POST} messages(BearerToken)

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
46
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
A) 202
B) 401
C) 429
D) 503
A) 202
B) 401
C) 429
D) 503

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
47
An application has initiated an OAuth authorization code grant flow to get access to an API resource on behalf of an end user. Which two parameters are specified in the HTTP request coming back to the application as the end user grants access? (Choose two.)
A) access token and a refresh token with respective expiration times to access the API resource
B) access token and expiration time to access the API resource
C) redirect URI a panel that shows the list of permissions to grant
D) code that can be exchanged for an access token
E) state can be used for correlation and security checks
A) access token and a refresh token with respective expiration times to access the API resource
B) access token and expiration time to access the API resource
C) redirect URI a panel that shows the list of permissions to grant
D) code that can be exchanged for an access token
E) state can be used for correlation and security checks

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
48
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct. Which action accomplishes this task?
A) Encrypt the username, hash the password, and store these values.
B) Hash the username, hash the password, and store these values.
C) Encrypt the username, encrypt the password, and store these values.
D) Hash the username, encrypt the password, and store these values.
A) Encrypt the username, hash the password, and store these values.
B) Hash the username, hash the password, and store these values.
C) Encrypt the username, encrypt the password, and store these values.
D) Hash the username, encrypt the password, and store these values.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
49
 Refer to the exhibit. The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?
Refer to the exhibit. The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?A) VRFs not defined in the host_vars file are removed from the device.
B) VRFs not defined in the host_vars file are added to the device, and any other VRFs on the device remain.
C) VRFs defined in the host_vars file are removed from the device.
D) VRFs are added to the device from the host_vars file, and any other VRFs on the device are removed.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
50
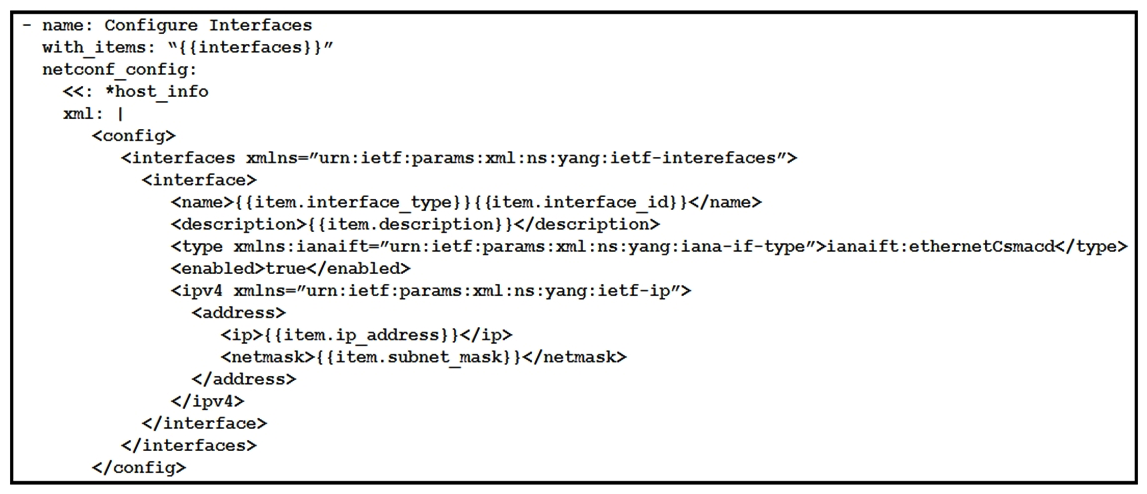 Refer to the exhibit. As part of the Ansible playbook workflow, several new interfaces are being configured using the netconf_config module. The task references the interface variables that are unique per device. In which directory is the YAML file with these variables found?
Refer to the exhibit. As part of the Ansible playbook workflow, several new interfaces are being configured using the netconf_config module. The task references the interface variables that are unique per device. In which directory is the YAML file with these variables found?A) host_vars directory
B) home directory
C) group_vars directory
D) current working directory

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
51
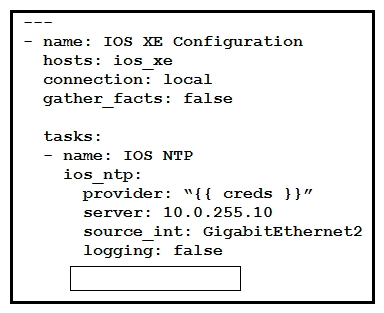 Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?A) state: present
B) state: True
C) config: present
D) config: True

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
52
A web application is susceptible to cross-site scripting. Which two methods allow this issue to be mitigated? (Choose two.)
A) Use only drop downs.
B) Limit user input to acceptable characters.
C) Encrypt user input on the client side.
D) Use AES encryption to secure the script.
E) Remove all HTML/XML tags from user input.
A) Use only drop downs.
B) Limit user input to acceptable characters.
C) Encrypt user input on the client side.
D) Use AES encryption to secure the script.
E) Remove all HTML/XML tags from user input.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
53
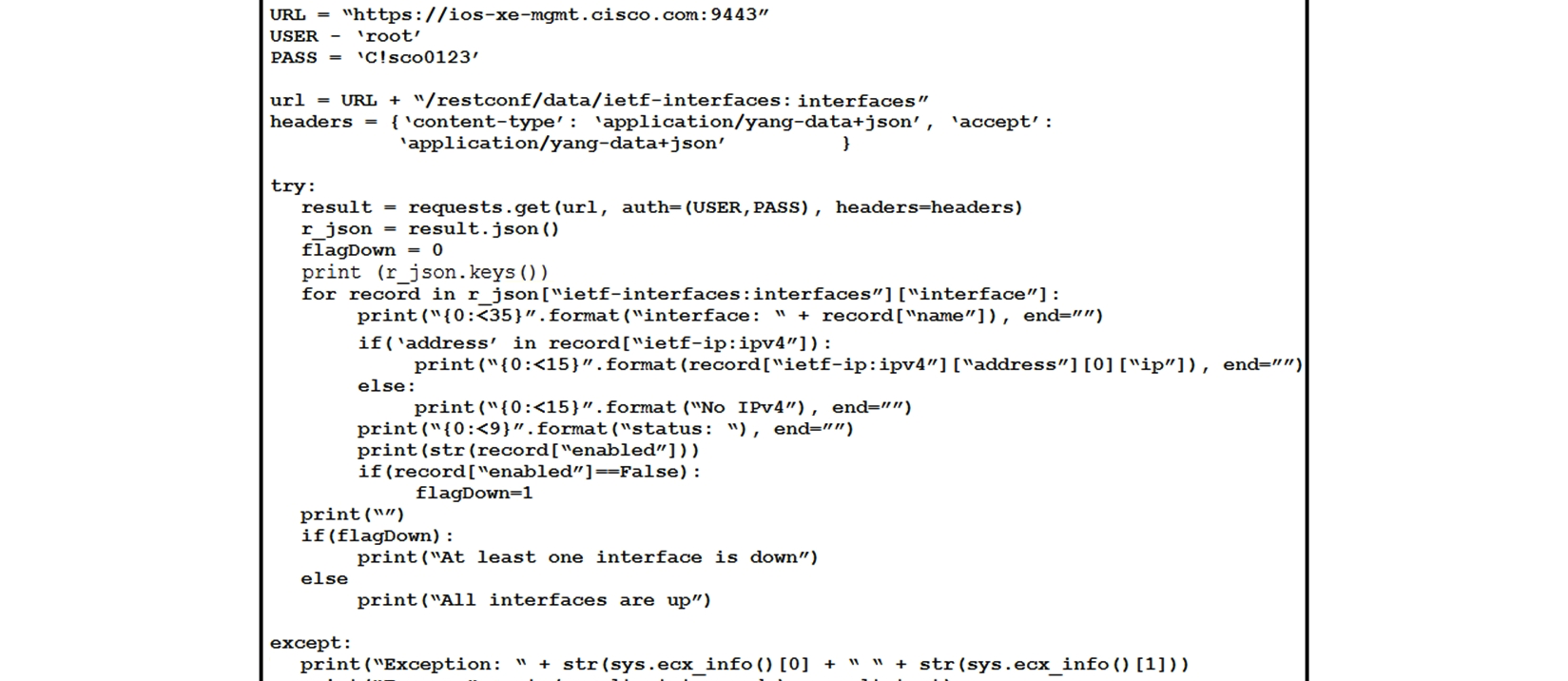 Refer to the exhibit. What is the output of this IOS-XE configuration program?
Refer to the exhibit. What is the output of this IOS-XE configuration program?A) interface operational status in IPv6 addresses
B) interface administrative status in IPv4 addresses
C) interface operational status in IPv4 addresses
D) interface administrative status in IPv6 addresses

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
54
Which tool is used to deploy an IOx application to a group of IOx devices at one time?
A) ioxclient
B) IOx local manager
C) Fog Network Director
D) Kubernetes
A) ioxclient
B) IOx local manager
C) Fog Network Director
D) Kubernetes

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
55
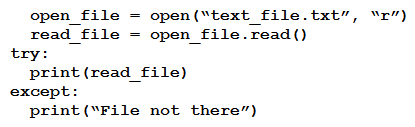
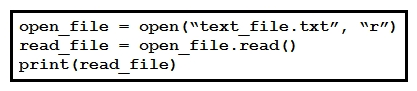 Refer to the exhibit. A developer created the code, but it fails to execute. Which code snippet helps to identify the issue?
Refer to the exhibit. A developer created the code, but it fails to execute. Which code snippet helps to identify the issue?A)
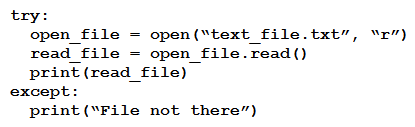
B)
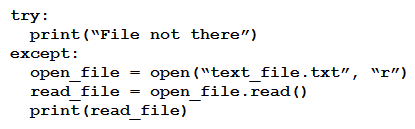
C)
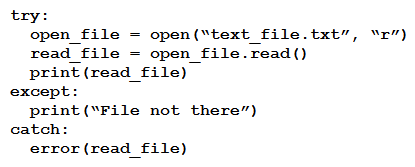
D)

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
56
Application sometimes store configuration as constants in the code, which is a violation of strict separation of configuration from code. Where should application configuration be stored?
A) environment variables
B) YAML files
C) Python libraries
D) Dockerfiles
E) INI files
A) environment variables
B) YAML files
C) Python libraries
D) Dockerfiles
E) INI files

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
57
Which database type should be used to store data received from model-driven telemetry?
A) BigQuery database
B) Time series database
C) NoSQL database
D) PostgreSQL database
A) BigQuery database
B) Time series database
C) NoSQL database
D) PostgreSQL database

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
58
A heterogeneous network of vendors and device types needs automating for better efficiency and to enable future automated testing. The network consists of switches, routers, firewalls and load balancers from different vendors, however they all support the NETCONF/RESTCONF configuration standards and the YAML models with every feature the business requires. The business is looking for a buy versus build solution because they cannot dedicate engineering resources, and they need configuration diff and rollback functionality from day 1. Which configuration management for automation tooling is needed for this solution?
A) Ansible
B) Ansible and Terraform
C) NSO
D) Terraform
E) Ansible and NSO
A) Ansible
B) Ansible and Terraform
C) NSO
D) Terraform
E) Ansible and NSO

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
59
The response from a server includes the header ETag: W/"7eb8b94419e371767916ef13e0d6e63d" . Which statement is true?
A) The ETag has a Strong validator directive.
B) The ETag has a Weak validator directive, which is an optional directive.
C) The ETag has a Weak validator directive, which is a mandatory directive.
D) The ETag has a Strong validator directive, which it is incorrectly formatted.
A) The ETag has a Strong validator directive.
B) The ETag has a Weak validator directive, which is an optional directive.
C) The ETag has a Weak validator directive, which is a mandatory directive.
D) The ETag has a Strong validator directive, which it is incorrectly formatted.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
60
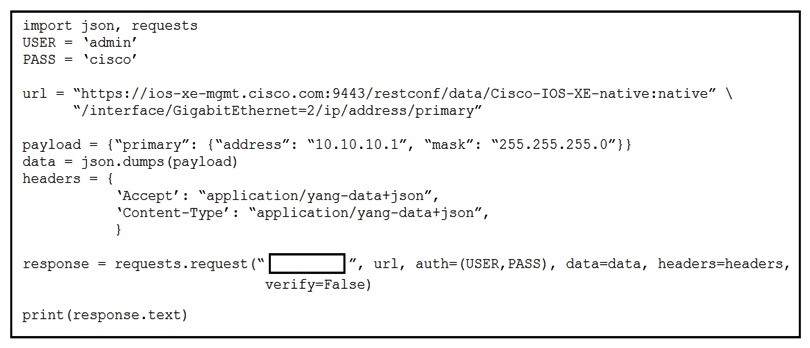 Refer to the exhibit. Which RESTCONF verb changes the GigabitEthernet2 interface from 192.168.100.1/24 to 10.10.10.1/24?
Refer to the exhibit. Which RESTCONF verb changes the GigabitEthernet2 interface from 192.168.100.1/24 to 10.10.10.1/24?A) POST
B) PATCH
C) GET
D) HEAD

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
61
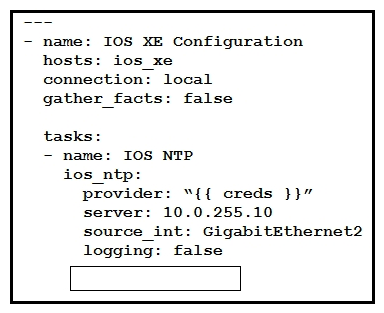 Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates the NTP server peer?
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates the NTP server peer?A) state: absent
B) state: False
C) config: absent
D) config: False

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
62
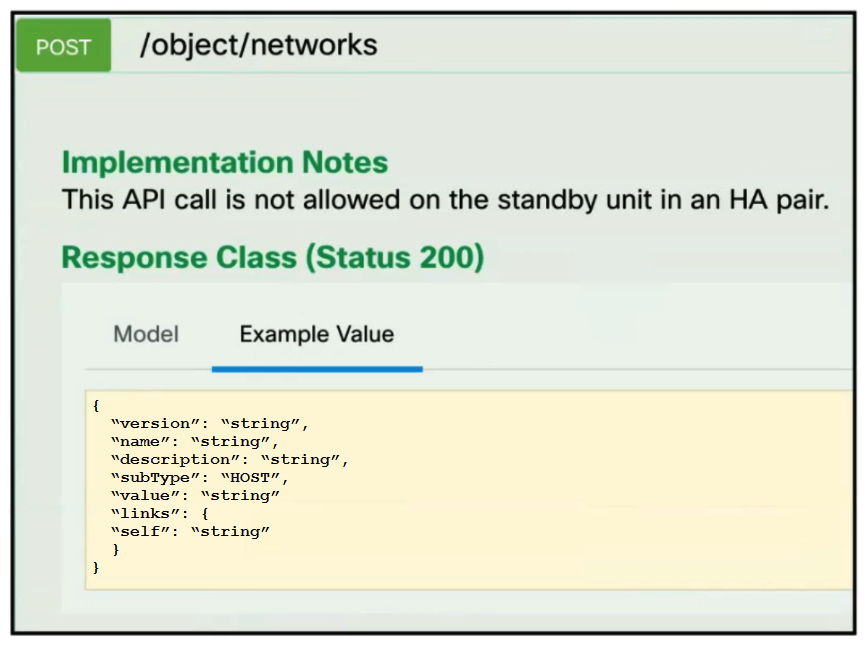 Refer to the exhibit. A developer must create a new network object named testnetwork by using the Cisco Firepower Device Management API. The script must also handle any exceptions that occur during the request and print out any resulting errors. Which script must be used?
Refer to the exhibit. A developer must create a new network object named testnetwork by using the Cisco Firepower Device Management API. The script must also handle any exceptions that occur during the request and print out any resulting errors. Which script must be used?A)
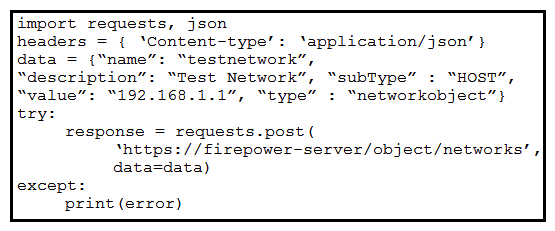
B)
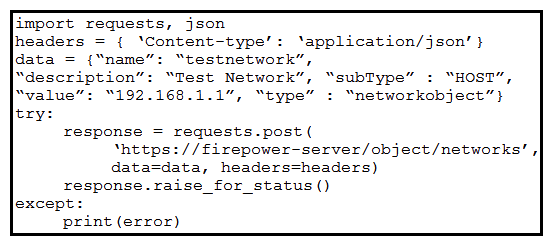
C)
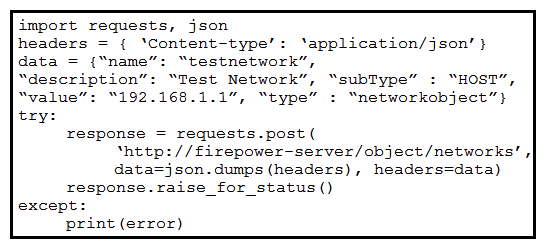
D)
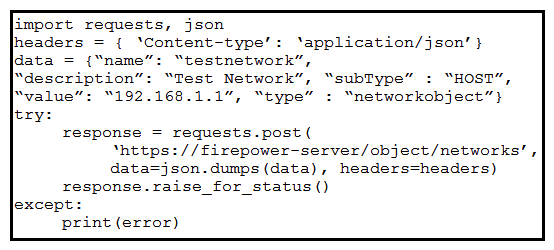

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
63
Why is end-to-end encryption deployed when exposing sensitive data through APIs?
A) Data transfers are untraceable from source to destination.
B) Data cannot be read or modified other than by the true source and destination.
C) Server-side encryption enables the destination to control data protection.
D) Traffic is encrypted and decrypted at every hop in the network path.
A) Data transfers are untraceable from source to destination.
B) Data cannot be read or modified other than by the true source and destination.
C) Server-side encryption enables the destination to control data protection.
D) Traffic is encrypted and decrypted at every hop in the network path.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
64
Which Puppet manifest needs to be used to configure an interface GigabitEthernet 0/1 on a Cisco IOS switch?
A)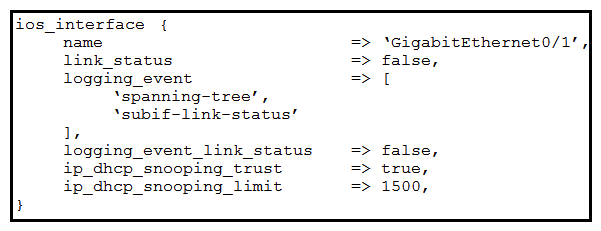
B)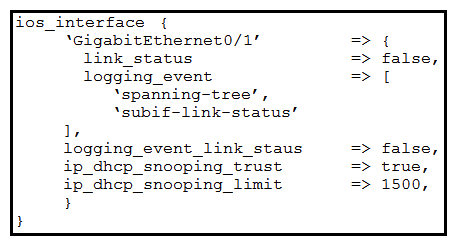
C)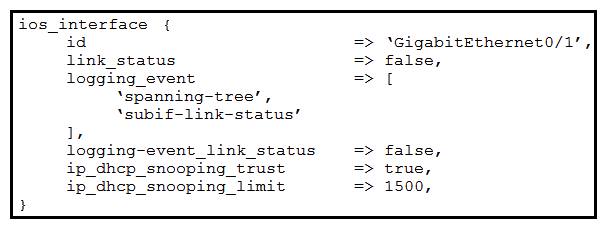
D)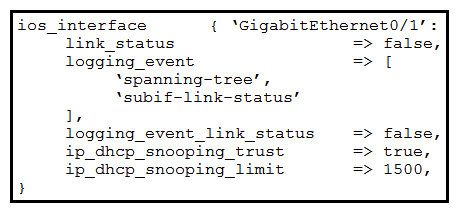
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
65
What is a benefit of continuous testing?
A) increases the number of bugs found in production
B) enables parallel testing
C) removes the requirement for test environments
D) decreases the frequency of code check-ins
A) increases the number of bugs found in production
B) enables parallel testing
C) removes the requirement for test environments
D) decreases the frequency of code check-ins

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
66
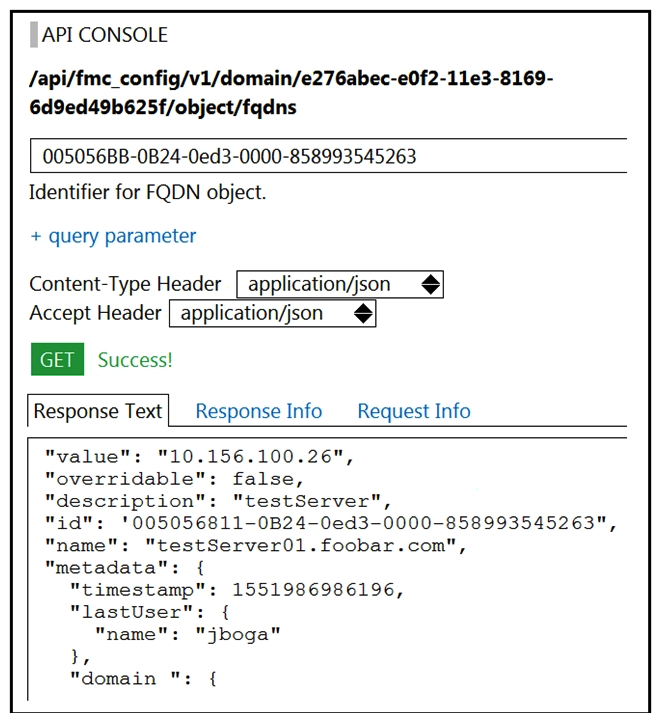 Refer to the exhibit. Which API call does an engineer use to delete the FQDN object?
Refer to the exhibit. Which API call does an engineer use to delete the FQDN object?A) DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f
B) DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f/object/fqdns/005056BB-0B24-0ed3-0000-858993545263
C) DELETE /api/fmc_config/v1/domain?id=e276abec-e0f2-11e3-8169-6d9ed49b625f
D) DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f/object/fqdns?id=005056BB-0B24-0ed3-0000-858993545263

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
67
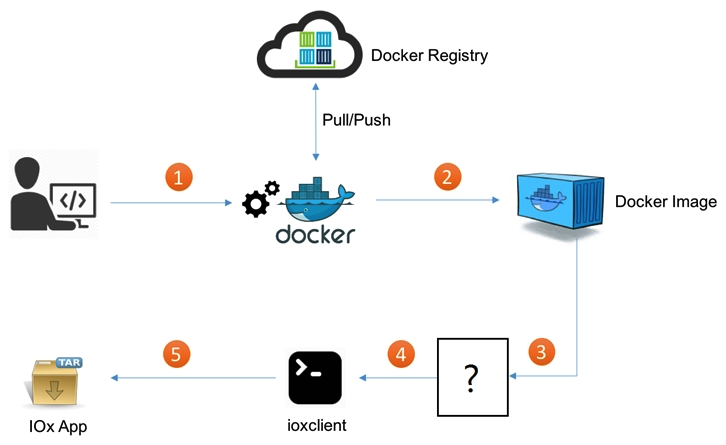 Refer to the exhibit. What is the missing step in deploying a Docker container to IOx?
Refer to the exhibit. What is the missing step in deploying a Docker container to IOx?A) Build the package.yaml file.
B) Pull/push the image to the Docker registry.
C) Build the package.cert file to sign the app.
D) Log in to Device Manager.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
68
Which two types of organization are subject to GDPR? (Choose two.)
A) only organizations that operate outside the EU
B) any organization that offers goods or services to customers in the EU
C) only organizations that have offices in countries that are part of the EU
D) any organization that operates within the EU
E) only organizations that physically reside in the EU
A) only organizations that operate outside the EU
B) any organization that offers goods or services to customers in the EU
C) only organizations that have offices in countries that are part of the EU
D) any organization that operates within the EU
E) only organizations that physically reside in the EU

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
69
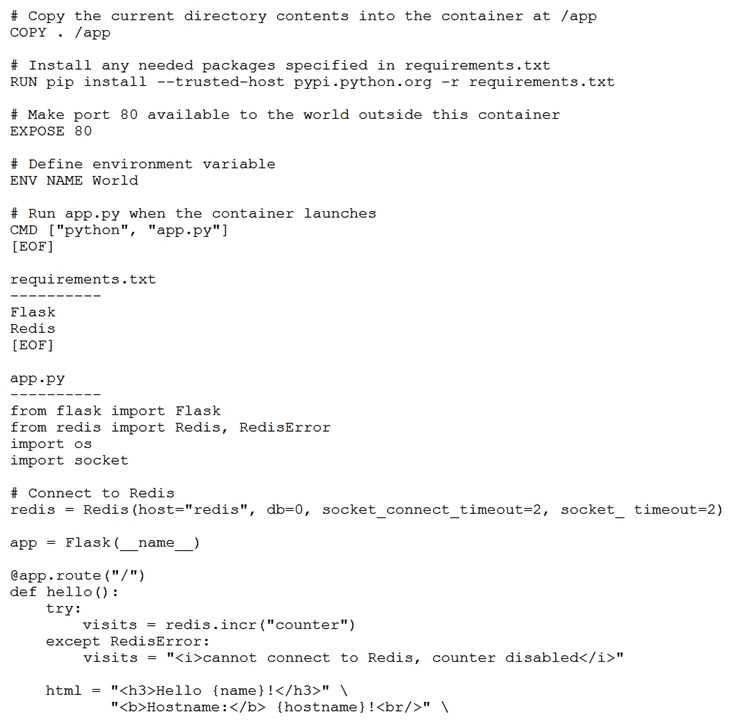 Refer to the exhibit. The command docker build --tag=friendlyhello . is run to build a docker image from the given Dockerfile, reguirements.txt, and app.py. Then the command docker run -p 4000:80 friendlyhello is executed to run the application. Which URL is entered in the web browser to see the content served by the application?
Refer to the exhibit. The command docker build --tag=friendlyhello . is run to build a docker image from the given Dockerfile, reguirements.txt, and app.py. Then the command docker run -p 4000:80 friendlyhello is executed to run the application. Which URL is entered in the web browser to see the content served by the application?A) http://127.0.0.1:80
B) http://4000:80
C) http://localhost:4000
D) http://localhost:80

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
70
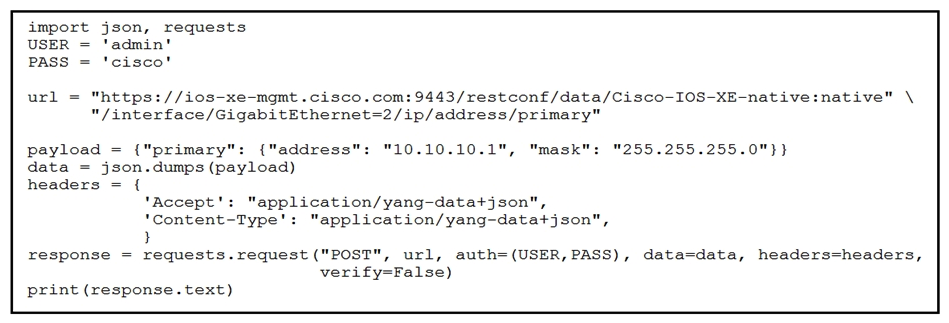 Refer to the exhibit. An engineer needs to change the IP address via RESTCONF on interface GigabitEthemet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?
Refer to the exhibit. An engineer needs to change the IP address via RESTCONF on interface GigabitEthemet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?A) Change POST to PATCH Change POST to PATCH
B) Issue a DELETE before POST Issue a DELETE before
C) Issue a DELETE before PATCH
D) Change POST to GET GET

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
71
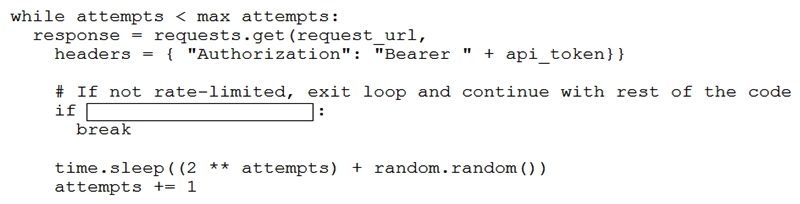 Refer to the exhibit. Which code snippet completes this code to handle API rate-limit?
Refer to the exhibit. Which code snippet completes this code to handle API rate-limit?A) response.status_code == 429
B) response.status_code != 408
C) response.status != 408
D) response.status_code != 429

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
72
What are two steps in the OAuth2 protocol flow? (Choose two.)
A) The user is authenticated by the authorization server and granted an access token.
B) The user's original credentials are validated by the resource server and authorization is granted.
C) The user indirectly requests authorization through the authorization server.
D) The user requests an access token by authentication and authorization grant presentation.
E) The user requests the protected resource from the resource server using the original credentials.
A) The user is authenticated by the authorization server and granted an access token.
B) The user's original credentials are validated by the resource server and authorization is granted.
C) The user indirectly requests authorization through the authorization server.
D) The user requests an access token by authentication and authorization grant presentation.
E) The user requests the protected resource from the resource server using the original credentials.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
73
While working with the Webex Teams API, on an application that uses end-to-end encryption, a webhook has been received. What must be considered to read the message?
A) Webhook information cannot be used to read the message because of end-to-end encryption. The API key is needed to decrypt the message.
B) Webhook returns the full unencrypted message. Only the body is needed to query the API.
C) Webhook returns a hashed version of the message that must be unhashed with the API key.
D) Webhook returns message identification. To query, the API is needed for that message to get the decrypted information.
A) Webhook information cannot be used to read the message because of end-to-end encryption. The API key is needed to decrypt the message.
B) Webhook returns the full unencrypted message. Only the body is needed to query the API.
C) Webhook returns a hashed version of the message that must be unhashed with the API key.
D) Webhook returns message identification. To query, the API is needed for that message to get the decrypted information.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
74
A team of developers created their own CA and started signing certificates for all of their IoT devices. Which action will make the browser accept these certificates?
A) Install a TLS instead of SSL certificate on the IoT devices.
B) Set the private keys 1024-bit RSA.
C) Preload the developer CA on the trusted CA list of the browser.
D) Enable HTTPS or port 443 on the browser.
A) Install a TLS instead of SSL certificate on the IoT devices.
B) Set the private keys 1024-bit RSA.
C) Preload the developer CA on the trusted CA list of the browser.
D) Enable HTTPS or port 443 on the browser.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
75
What is a characteristic of a monolithic architecture?
A) It is an application with multiple independent parts.
B) New capabilities are deployed by restarting a component of the application.
C) A service failure can bring down the whole application.
D) The components are platform-agnostic.
A) It is an application with multiple independent parts.
B) New capabilities are deployed by restarting a component of the application.
C) A service failure can bring down the whole application.
D) The components are platform-agnostic.

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
76
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
A) Jenkins for orchestration
B) Terraform for orchestration
C) Bamboo for configuration
D) Kubernetes for orchestration
E) Ansible for configuration
A) Jenkins for orchestration
B) Terraform for orchestration
C) Bamboo for configuration
D) Kubernetes for orchestration
E) Ansible for configuration

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
77
A developer plans to create a new bugfix branch to fix a bug that was found on the release branch. Which command completes the task?
A) git checkout -t RELEASE BUGFIX
B) git checkout -b RELEASE BUGFIX
C) git checkout -t BUGFIX RELEASE
D) git checkout -b BUGFIX RELEASE
A) git checkout -t RELEASE BUGFIX
B) git checkout -b RELEASE BUGFIX
C) git checkout -t BUGFIX RELEASE
D) git checkout -b BUGFIX RELEASE

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
78
What are two advantages of using model-driven telemetry, such as gRPC, instead of traditional telemetry gathering methods? (Choose two.)
A) all data is ad-hoc
B) decentralized storage of telemetry
C) efficient use of bandwidth
D) no overhead
E) continuous information with incremental updates
A) all data is ad-hoc
B) decentralized storage of telemetry
C) efficient use of bandwidth
D) no overhead
E) continuous information with incremental updates

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
79
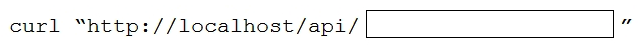 Refer to the exhibit. An application's REST API GET call is tested to the inventory database. Which missing code must be included to limit the number of values that are returned from the query to 20?
Refer to the exhibit. An application's REST API GET call is tested to the inventory database. Which missing code must be included to limit the number of values that are returned from the query to 20?A) inventory=20
B) inventory?limit=20
C) limit=?20
D) inventory=limit?20

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck
80
In the three-legged OAuth2 authorization workflow, which entity grants access to a protected resource?
A) resource owner
B) client
C) resource server
D) authorization server
A) resource owner
B) client
C) resource server
D) authorization server

Unlock Deck
Unlock for access to all 145 flashcards in this deck.
Unlock Deck
k this deck


