Deck 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/25
Play
Full screen (f)
Deck 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
1
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
A) An engineer should check the list of usernames currently logged in by running the command $ who | cut -d' ' -f1| sort | uniq An engineer should check the list of usernames currently logged in by running the command $ who | cut -d' ' -f1| sort | uniq
B) An engineer should check the server's processes by running commands ps -aux and sudo ps -a . An engineer should check the server's processes by running commands ps -aux and sudo ps -a .
C) An engineer should check the services on the machine by running the command service -status-all . An engineer should check the services on the machine by running the command service -status-all
D) An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log . An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log
A) An engineer should check the list of usernames currently logged in by running the command $ who | cut -d' ' -f1| sort | uniq An engineer should check the list of usernames currently logged in by running the command $ who | cut -d' ' -f1| sort | uniq
B) An engineer should check the server's processes by running commands ps -aux and sudo ps -a . An engineer should check the server's processes by running commands ps -aux and sudo ps -a .
C) An engineer should check the services on the machine by running the command service -status-all . An engineer should check the services on the machine by running the command service -status-all
D) An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log . An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log
An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log . An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log
2
What is the function of a disassembler?
A) aids performing static malware analysis
B) aids viewing and changing the running state
C) aids transforming symbolic language into machine code
D) aids defining breakpoints in program execution
A) aids performing static malware analysis
B) aids viewing and changing the running state
C) aids transforming symbolic language into machine code
D) aids defining breakpoints in program execution
aids performing static malware analysis
3
An "unknown error code" is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
A) /var/log/syslog.log
B) /var/log/vmksummary.log
C) var/log/shell.log
D) var/log/general/log
A) /var/log/syslog.log
B) /var/log/vmksummary.log
C) var/log/shell.log
D) var/log/general/log
/var/log/syslog.log
4
Which information is provided bout the object file by the "-h" option in the objdump line command objdump -b oasys -m vax -h fu.o ?
A) bfdname
B) debugging
C) help
D) headers
A) bfdname
B) debugging
C) help
D) headers

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
5
An attacker embedded a macro within a word processing file opened by a user in an organization's legal department. The attacker used this technique to gain access to confidential financial data. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
A) controlled folder access
B) removable device restrictions
C) signed macro requirements
D) firewall rules creation
E) network access control
A) controlled folder access
B) removable device restrictions
C) signed macro requirements
D) firewall rules creation
E) network access control

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
6
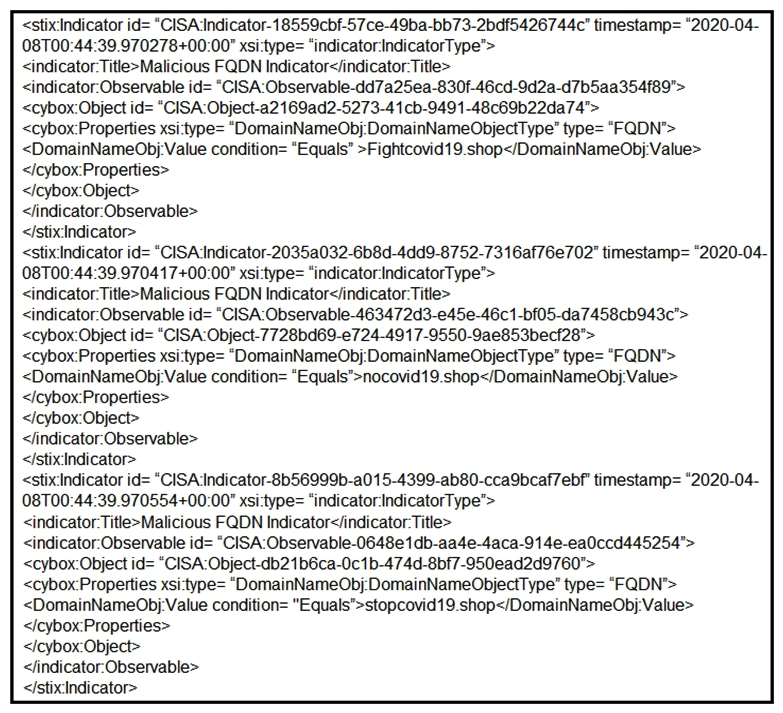 Refer to the exhibit. Which two actions should be taken based on the intelligence information? (Choose two.)
Refer to the exhibit. Which two actions should be taken based on the intelligence information? (Choose two.)A) Block network access to all .shop domains
B) Add a SIEM rule to alert on connections to identified domains.
C) Use the DNS server to block hole all .shop requests.
D) Block network access to identified domains.
E) Route traffic from identified domains to block hole.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
7
A security team received an alert of suspicious activity on a user's Internet browser. The user's anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis? (Choose two.)
A) Evaluate the process activity in Cisco Umbrella.
B) Analyze the TCP/IP Streams in Cisco Secure Malware Analytics (Threat Grid).
C) Evaluate the behavioral indicators in Cisco Secure Malware Analytics (Threat Grid).
D) Analyze the Magic File type in Cisco Umbrella.
E) Network Exit Localization in Cisco Secure Malware Analytics (Threat Grid).
A) Evaluate the process activity in Cisco Umbrella.
B) Analyze the TCP/IP Streams in Cisco Secure Malware Analytics (Threat Grid).
C) Evaluate the behavioral indicators in Cisco Secure Malware Analytics (Threat Grid).
D) Analyze the Magic File type in Cisco Umbrella.
E) Network Exit Localization in Cisco Secure Malware Analytics (Threat Grid).

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
8
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?
A)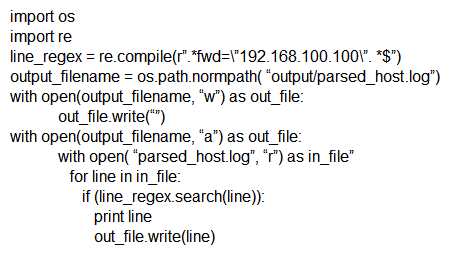
B)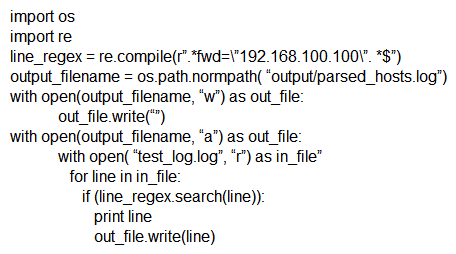
C)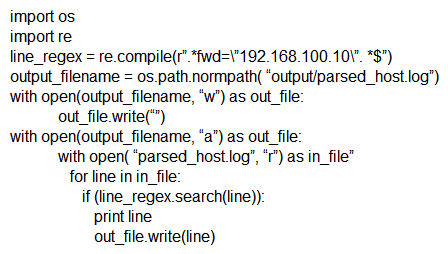
D)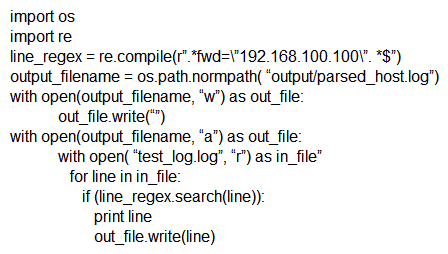
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
9
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
A) Introduce a priority rating for incident response workloads.
B) Provide phishing awareness training for the fill security team.
C) Conduct a risk audit of the incident response workflow.
D) Create an executive team delegation plan.
E) Automate security alert timeframes with escalation triggers.
A) Introduce a priority rating for incident response workloads.
B) Provide phishing awareness training for the fill security team.
C) Conduct a risk audit of the incident response workflow.
D) Create an executive team delegation plan.
E) Automate security alert timeframes with escalation triggers.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
10
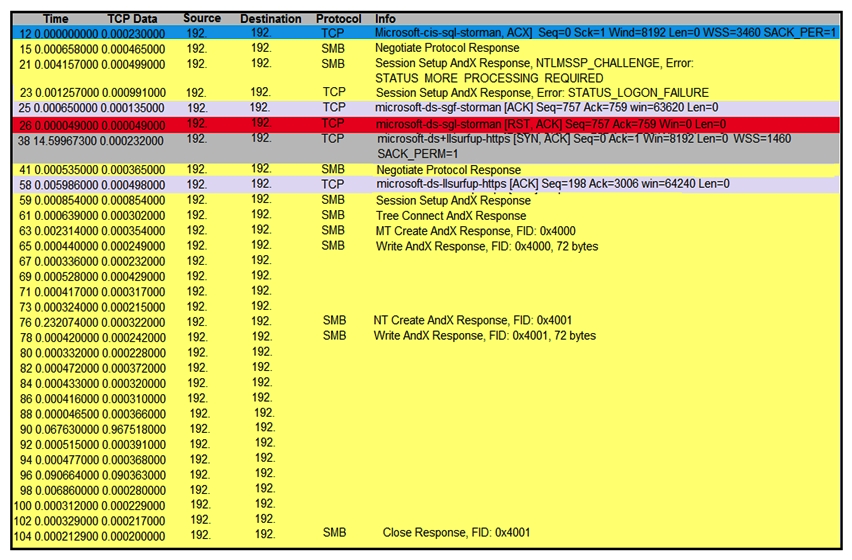 Refer to the exhibit. An engineer is analyzing a TCP stream in a Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
Refer to the exhibit. An engineer is analyzing a TCP stream in a Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?A) It is redirecting to a malicious phishing website,
B) It is exploiting redirect vulnerability
C) It is requesting authentication on the user site.
D) It is sharing access to files and printers.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
11
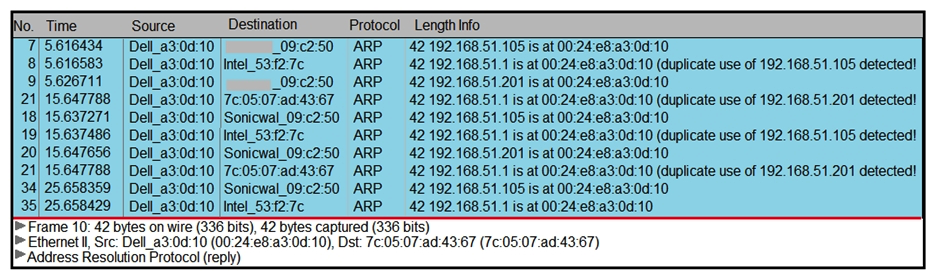 Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?A) DNS spoofing; encrypt communication protocols
B) SYN flooding, block malicious packets
C) ARP spoofing; configure port security
D) MAC flooding; assign static entries

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
12
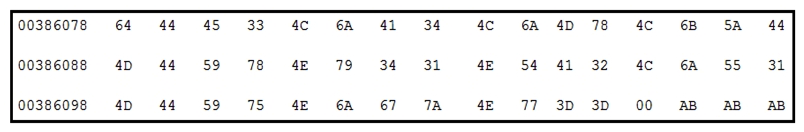 Refer to the exhibit. Which encoding technique is represented by this HEX string?
Refer to the exhibit. Which encoding technique is represented by this HEX string?A) Unicode
B) Binary
C) Base64
D) Charcode

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
13
Which tool conducts memory analysis?
A) MemDump
B) Sysinternals Autoruns
C) Volatility
D) Memoryze
A) MemDump
B) Sysinternals Autoruns
C) Volatility
D) Memoryze

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
14
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
A) process injection
B) privilege escalation
C) GPO modification
D) token manipulation
A) process injection
B) privilege escalation
C) GPO modification
D) token manipulation

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
15
A security team receives reports of multiple files causing suspicious activity on users' workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
A) Inspect registry entries
B) Inspect processes.
C) Inspect file hash.
D) Inspect file type.
E) Inspect PE header.
A) Inspect registry entries
B) Inspect processes.
C) Inspect file hash.
D) Inspect file type.
E) Inspect PE header.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
16
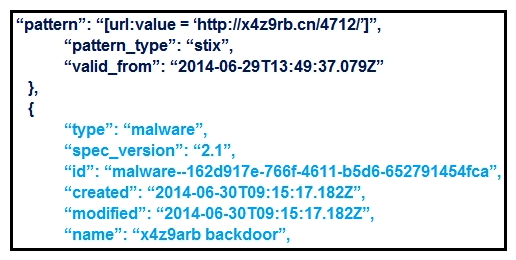 Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?
Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?A) malware; 'http://x4z9arb.cn/4712/'
B) malware; x4z9arb backdoor
C) x4z9arb backdoor; http://x4z9arb.cn/4712/
D) malware; malware--162d917e-766f-4611-b5d6-652791454fca
E) stix; 'http://x4z9arb.cn/4712/'

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
17
Which magic byte indicates that an analyzed file is a pdf file?
A) cGRmZmlsZQ
B) 706466666
C) 255044462d
D) 0a0ah4cg
A) cGRmZmlsZQ
B) 706466666
C) 255044462d
D) 0a0ah4cg

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
18
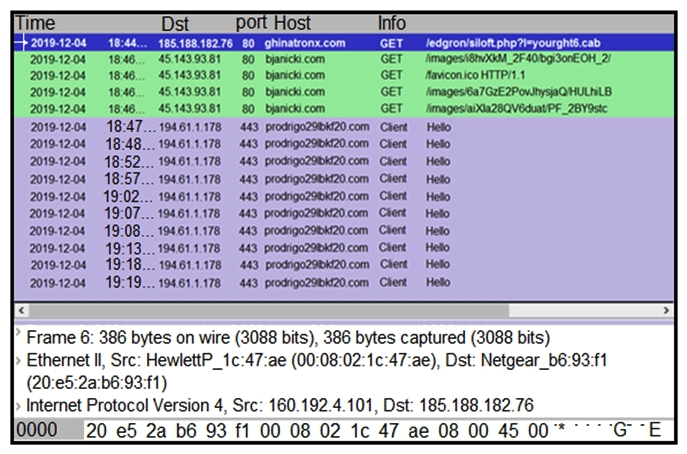 Refer to the exhibit. A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
Refer to the exhibit. A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?A) http.request.un matches
B) tls.handshake.type ==1
C) tcp.port eq 25
D) tcp.window_size ==0

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
19
 Refer to the exhibit. Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
Refer to the exhibit. Which two determinations should be made about the attack from the Apache access logs? (Choose two.)A) The attacker used r57 exploit to elevate their privilege.
B) The attacker uploaded the word press file manager trojan.
C) The attacker performed a brute force attack against word press and used sql injection against the backend database.
D) The attacker used the word press file manager plugin to upoad r57.php.
E) The attacker logged on normally to word press admin page.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
20
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
A) Get-Content-Folder \\Server\FTPFolder\Logfiles\ftpfiles.log | Show-From "ERROR", "SUCCESS"
B) Get-Content -ifmatch \\Server\FTPFolder\Logfiles\ftpfiles.log | Copy-Marked "ERROR", "SUCCESS"
C) Get-Content -Directory \\Server\FTPFolder\Logfiles\ftpfiles.log | Export-Result "ERROR", "SUCCESS"
D) Get-Content -Path \\Server\FTPFolder\Logfiles\ftpfiles.log | Select-String "ERROR", "SUCCESS"
A) Get-Content-Folder \\Server\FTPFolder\Logfiles\ftpfiles.log | Show-From "ERROR", "SUCCESS"
B) Get-Content -ifmatch \\Server\FTPFolder\Logfiles\ftpfiles.log | Copy-Marked "ERROR", "SUCCESS"
C) Get-Content -Directory \\Server\FTPFolder\Logfiles\ftpfiles.log | Export-Result "ERROR", "SUCCESS"
D) Get-Content -Path \\Server\FTPFolder\Logfiles\ftpfiles.log | Select-String "ERROR", "SUCCESS"

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
21
A scanner detected a malware-infected file on an endpoint that is attempting to beacon to an external site. An analyst has reviewed the IPS and SIEM logs but is unable to identify the file's behavior. Which logs should be reviewed next to evaluate this file further?
A) email security appliance
B) DNS server
C) Antivirus solution
D) network device
A) email security appliance
B) DNS server
C) Antivirus solution
D) network device

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
22
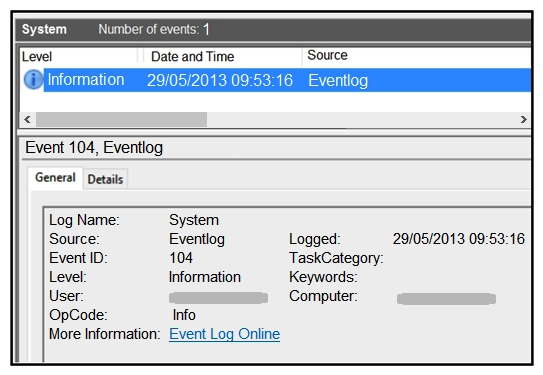 Refer to the exhibit. An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
Refer to the exhibit. An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?A) data obfuscation
B) reconnaissance attack
C) brute-force attack
D) log tampering

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
23
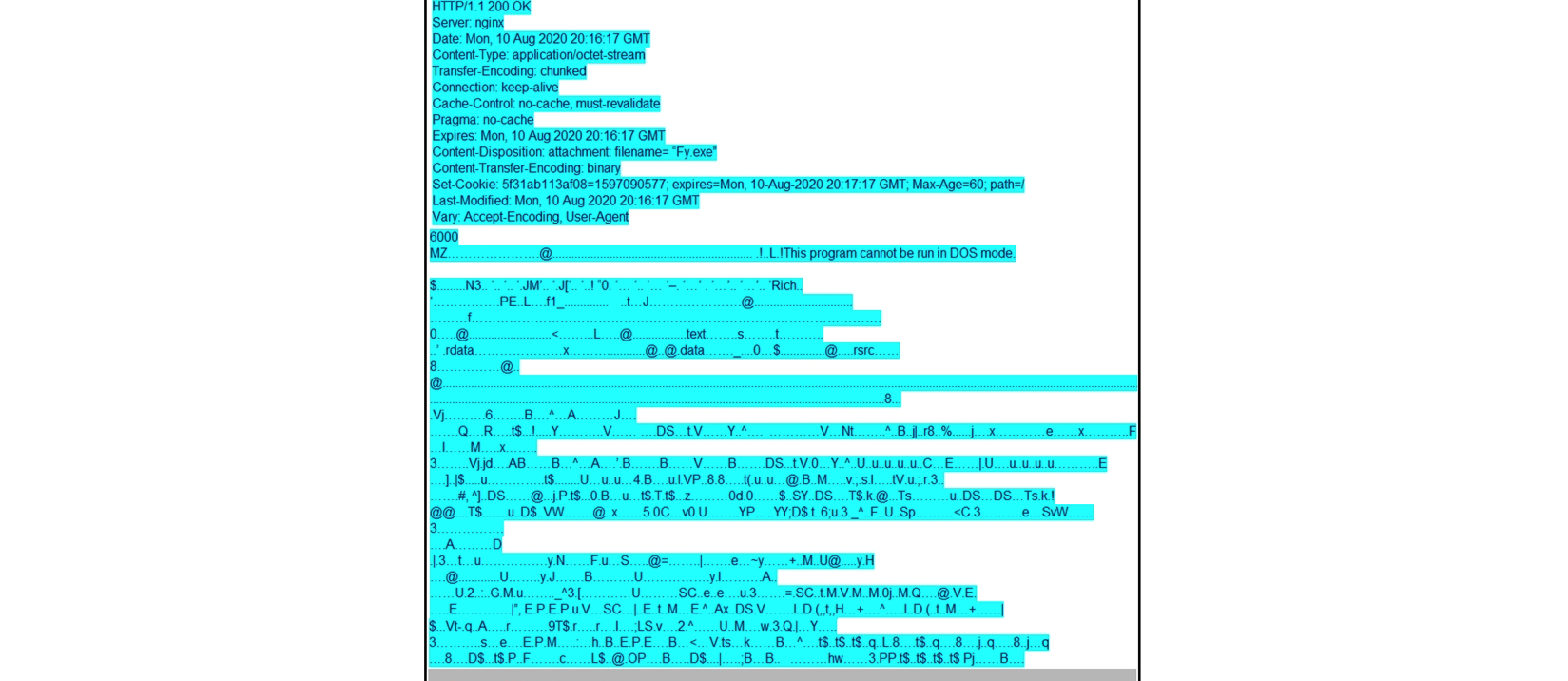 Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)A) Domain name:iraniansk.com
B) Server: nginx
C) Hash value: 5f31ab113af08=1597090577
D) filename= "Fy.exe"
E) Content-Type: application/octet-stream

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
24
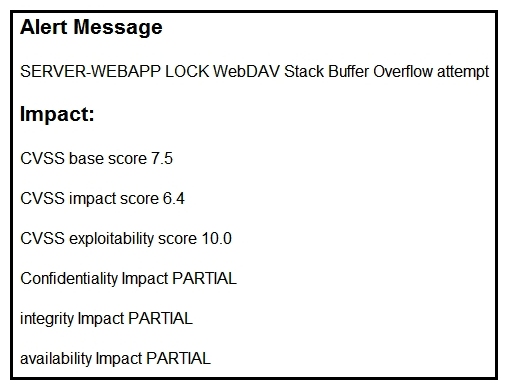 Refer to the exhibit. After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business critical, web-based application and violated its availability. Which two migration techniques should the engineer recommend? (Choose two.)
Refer to the exhibit. After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business critical, web-based application and violated its availability. Which two migration techniques should the engineer recommend? (Choose two.)A) encapsulation
B) NOP sled technique
C) address space randomization
D) heap-based security
E) data execution prevention

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
25
 Refer to the exhibit. What should be determined from this Apache log?
Refer to the exhibit. What should be determined from this Apache log?A) A module named mod_ssl is needed to make SSL connections.
B) The private key does not match with the SSL certificate.
C) The certificate file has been maliciously modified
D) The SSL traffic setup is improper

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck


