Deck 10: Designing Cisco Enterprise Networks (ENSLD)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/109
Play
Full screen (f)
Deck 10: Designing Cisco Enterprise Networks (ENSLD)
1
An engineer must design a multicast network for a financial application. Most of the multicast sources also receive multicast traffic (many-to-many deployment model). To better scale routing tables, the design must not use source trees. Which multicast protocol satisfies these requirements?
A) PIM-SSM
B) PIM-SM
C) MSDP
D) BIDIR-PIM
A) PIM-SSM
B) PIM-SM
C) MSDP
D) BIDIR-PIM
PIM-SM
2
When IPsec VPNs are designed, what is a unique requirement if support for IP Multicast is required?
A) encapsulation of traffic with GRE or VTI
B) IPsec forwarding using transport mode
C) additional bandwidth for headend
D) IPsec forwarding using tunnel mode
A) encapsulation of traffic with GRE or VTI
B) IPsec forwarding using transport mode
C) additional bandwidth for headend
D) IPsec forwarding using tunnel mode
encapsulation of traffic with GRE or VTI
3
Which design consideration should be observed when EIGRP is configured on Data Center switches?
A) Perform manual summarization on all Layer 3 interfaces to minimize the size of the routing table.
B) Prevent unnecessary EIGRP neighborships from forming across switch virtual interfaces.
C) Lower EIGRP hello and hold timers to their minimum settings to ensure rapid route reconvergence.
D) Configure multiple EIGRP autonomous systems to segment Data Center services and applications.
A) Perform manual summarization on all Layer 3 interfaces to minimize the size of the routing table.
B) Prevent unnecessary EIGRP neighborships from forming across switch virtual interfaces.
C) Lower EIGRP hello and hold timers to their minimum settings to ensure rapid route reconvergence.
D) Configure multiple EIGRP autonomous systems to segment Data Center services and applications.
Perform manual summarization on all Layer 3 interfaces to minimize the size of the routing table.
4
Which nonproprietary mechanism can be used to automate rendezvous point distribution in a large PIM domain?
A) Embedded RP
B) BSR
C) Auto-RP
D) Static RP
A) Embedded RP
B) BSR
C) Auto-RP
D) Static RP

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
5
Which consideration must be taken into account when using the DHCP relay feature in a Cisco SD-Access Architecture?
A) DHCP-relay must be enabled on fabric edge nodes to provide the correct mapping of DHCP scope to the local anycast gateway.
B) A DHCP server must be enabled on the border nodes to allow subnets to span multiple fabric edges.
C) DHCP servers must support Cisco SD-Access extensions to correctly assign IPs to endpoints in an SD-Access fabric with anycast gateway.
D) DHCP Option-82 must be enabled to map the circuit IP option to the access fabric node where the DHCP discover originated.
A) DHCP-relay must be enabled on fabric edge nodes to provide the correct mapping of DHCP scope to the local anycast gateway.
B) A DHCP server must be enabled on the border nodes to allow subnets to span multiple fabric edges.
C) DHCP servers must support Cisco SD-Access extensions to correctly assign IPs to endpoints in an SD-Access fabric with anycast gateway.
D) DHCP Option-82 must be enabled to map the circuit IP option to the access fabric node where the DHCP discover originated.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
6
Which two BGP features will result in successful route exchanges between eBGP neighbors sharing the same AS number? (Choose two.)
A) advertise-best-external
B) bestpath as-path ignore
C) client-to-client reflection
D) as-override
E) allow-as-in
A) advertise-best-external
B) bestpath as-path ignore
C) client-to-client reflection
D) as-override
E) allow-as-in

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
7
Which design consideration must be made when dual vEdge routers are deployed at a branch site?
A) Use BGP AS-path prepending to influence egress traffic and use MED to influence ingress traffic from the branch.
B) HSRP priorities must match the OMP routing policy to prefer one vEdge over the other.
C) Traffic must be symmetrical as it egresses the vEdges and returns from remote sites for DPI to function properly.
D) Configure BFD between vEdge routers to detect sub-second link failures.
A) Use BGP AS-path prepending to influence egress traffic and use MED to influence ingress traffic from the branch.
B) HSRP priorities must match the OMP routing policy to prefer one vEdge over the other.
C) Traffic must be symmetrical as it egresses the vEdges and returns from remote sites for DPI to function properly.
D) Configure BFD between vEdge routers to detect sub-second link failures.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
8
What is a benefit of using VRRPv3 as compared to VRRPv2?
A) VRRPv3 supports IPv4 and IPv6
B) VRRPv3 supports authentication
C) VRRPv3 supports preemption
D) VRRPv3 supports stateful switchover
A) VRRPv3 supports IPv4 and IPv6
B) VRRPv3 supports authentication
C) VRRPv3 supports preemption
D) VRRPv3 supports stateful switchover

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
9
A customer is discussing QoS requirements with a network consultant. The customer has specified that end-to-end path verification is a requirement. Which QoS solution meets this requirement?
A) IntServ model with RSVP to support the traffic flows
B) DiffServ model with PHB to support the traffic flows
C) marking traffic at the access layer with DSCP to support the traffic flows
D) marking traffic at the access layer with CoS to support the traffic flows
A) IntServ model with RSVP to support the traffic flows
B) DiffServ model with PHB to support the traffic flows
C) marking traffic at the access layer with DSCP to support the traffic flows
D) marking traffic at the access layer with CoS to support the traffic flows

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
10
Which NETCONF operation creates filtering that is specific to the session notifications?
A)
B)
C)
D)
A)
B)
C)
D)

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
11
Which QoS feature responds to network congestion by dropping lower priority packets?
A) CBWFQ
B) tail drop
C) WRED
D) strict priority
A) CBWFQ
B) tail drop
C) WRED
D) strict priority

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
12
Which routes does the overlay management protocol advertise in an SD-WAN overlay?
A) underlay, MPLS, and overlay
B) primary, backup, and load-balanced
C) prefix, TLOC, and service
D) Internet, MPLS, and backup
A) underlay, MPLS, and overlay
B) primary, backup, and load-balanced
C) prefix, TLOC, and service
D) Internet, MPLS, and backup

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
13
When a network is designed using IS-IS protocol, which two circuit types are supported? (Choose two.)
A) nonbroadcast multiaccess
B) multiaccess
C) point-to-multipoint
D) nonbroadcast
E) point-to-point
A) nonbroadcast multiaccess
B) multiaccess
C) point-to-multipoint
D) nonbroadcast
E) point-to-point

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
14
What is one function of the vSmart controller in an SD-WAN deployment?
A) orchestrates vEdge and cEdge connectivity
B) responsible for the centralized control plane of the SD-WAN network
C) provides centralized network management and a GUI to monitor and operate the SD-WAN overlay
D) provides a data-plane at branch offices to pass traffic through the SD-WAN network
A) orchestrates vEdge and cEdge connectivity
B) responsible for the centralized control plane of the SD-WAN network
C) provides centralized network management and a GUI to monitor and operate the SD-WAN overlay
D) provides a data-plane at branch offices to pass traffic through the SD-WAN network

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
15
What is an advantage of designing an out-of-band network management solution?
A) In the event of a production network outage, network devices can still be managed.
B) There is no separation between the production network and the management network.
C) In the event of a production network outage, it can be used as a backup network path.
D) It is less expensive than an in-band management solution.
A) In the event of a production network outage, network devices can still be managed.
B) There is no separation between the production network and the management network.
C) In the event of a production network outage, it can be used as a backup network path.
D) It is less expensive than an in-band management solution.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
16
A network solution is being designed for a company that connects to multiple Internet service providers. Which Cisco proprietary BGP path attribute will influence outbound traffic flow?
A) Local Preference
B) MED
C) Weight
D) AS Path
E) Community
A) Local Preference
B) MED
C) Weight
D) AS Path
E) Community

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
17
An enterprise customer has these requirements: end-to-end QoS for the business-critical applications and VoIP services based on CoS marking. flexibility to offer services such as IPv6 and multicast without any reliance on the service provider. support for full-mesh connectivity at Layer 2. Which WAN connectivity option meets these requirements?
A) VPWS
B) MPLS VPN
C) DMVPN
D) VPLS
A) VPWS
B) MPLS VPN
C) DMVPN
D) VPLS

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
18
Which solution allows overlay VNs to communicate with each other in an SD-WAN Architecture?
A) External fusion routers can be used to map VNs to VRFs and selectively route traffic between VRFs.
B) GRE tunneling can be configured between fabric edges to connect one VN to another.
C) SGTs can be used to permit traffic from one VN to another.
D) Route leaking can be used on the fabric border nodes to inject routes from one VN to another.
A) External fusion routers can be used to map VNs to VRFs and selectively route traffic between VRFs.
B) GRE tunneling can be configured between fabric edges to connect one VN to another.
C) SGTs can be used to permit traffic from one VN to another.
D) Route leaking can be used on the fabric border nodes to inject routes from one VN to another.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
19
An engineer is looking for a standards-driven YANG model to manage a multivendor network environment. Which model must the engineer choose?
A) Native
B) OpenConfig
C) IETF
D) IEEE NETCONF
A) Native
B) OpenConfig
C) IETF
D) IEEE NETCONF

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
20
A company is running BGP on a single router, which has two connections to the same ISP. Which BGP feature ensures traffic is load balanced across the two links to the ISP?
A) Multihop
B) Multipath Load Sharing
C) Next-Hop Address Tracking
D) AS-Path Prepending
A) Multihop
B) Multipath Load Sharing
C) Next-Hop Address Tracking
D) AS-Path Prepending

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
21
A customer with an IPv4 only network topology wants to enable IPv6 connectivity while preserving the IPv4 topology services. The customer plans to migrate IPv4 services to the IPv6 topology, then decommission the IPv4 topology. Which topology supports these requirements?
A) dual stack
B) 6VPE
C) 6to4
D) NAT64
A) dual stack
B) 6VPE
C) 6to4
D) NAT64

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
22
Instructions The main screen consists of two parts; the Main scenario and the Topology tabs. The main scenario describes TSHOOT.com test bed. The Topology tabs allow you to display the appropriate and select the trouble ticket. To complete the item, you will first need to familiarize yourself with the TSHOOT.com test bed by clicking on the master scenario first and then the topologies tabs. Once you are familiar with the test bed and the topologies, you should start evaluating the trouble ticket. You will be presented with a Trouble Ticket scenario that will describe the fault condition. You will need to determine on which device the fault condition is located, to which technology the fault condition is related, and the solution to each trouble ticket. This will be done by answering three questions. Ticket Selection To begin, click on the Ticket on the Topology tabs. Please note. Some of the questions will require you to use the scroll bar to see all options. Fault Isolation Read the ticket scenario to understand the fault condition. Open the appropriate topology, based upon the ticket scenario. Open the console of the desired device by clicking on that device in the topology, based upon your troubleshooting methodology. Use the supported show, ping and trace commands to begin your fault isolation process. Move to other devices as need by clicking on those devices within the topology. Fault Identification The trouble ticket will include three questions that you will need to answer, 1. Which device contains the fault 2. Which technology the fault condition is related to 3. What is the solution to the issue To advance to the next question within the ticket click on " Next Question ". When you click " DONE ", the trouble ticket will turn RED and will no longer be accessible. You may also use the " Previous Question " button to review questions within that specific ticket. To complete a trouble ticket, answer all three questions and click " ". This will store your response to the questions. Do not click on " " unless you have answered all questions within the ticket. Item Completion Click the NEXT button on the bottom of the screen once a ticket is . This action moves you to the next item. Scenario The company has created the test bed network shown in the layer 2 and layer 3 topology exhibits. This network consists of four routers, two layer 3 switches and two layer 2 switches. In the IPv4 layer 3 topology, R1, R2, R3, and R4 are running OSPF with an OSPF process number 1. DSW1, DSW2 and R4 are running EIGRP with an AS of 10. Redistribution is enabled where necessary. R1 is running a BGP AS with a number of 65001. This AS has an eBGP connection to AS 65002 in the ISP's network. Because the company's address space is in the private range, R1 is also providing NAT translations between the inside (10.1.0.0/16 & 10.2.0.0/16) networks and the outside (209.65.200.0/24) network. ASW1 and ASW2 are layer 2 switches. NTP is enabled on all devices with 209.65.200.226 serving as the master clock source. The client workstations receive their IP address and default gateway via R4's DHCP server. The default gateway address of 10.2.1.254 is the IP address of HSRP group 10 which is running on DSW1 and DSW2. In the IPv6 layer 3 topology R1, R2, and R3 are running OSPFv3 with an OSPF process number 6. DSW1, DSW2 and R4 are running RIPng process name RIP_ZONE. The two IPv6 routing domains, OSPF 6 and RIPng are connected via GRE tunnel running over the underlying IPv4 OSPF domain. Redistribution is enabled where necessary. Recently the implementation group has been using the test bed to do a 'proof-of-concept' on several implementations. This involved changing the configuration on one or more of the devices. You will be presented with a series of trouble tickets related to issues introduced during these configurations. 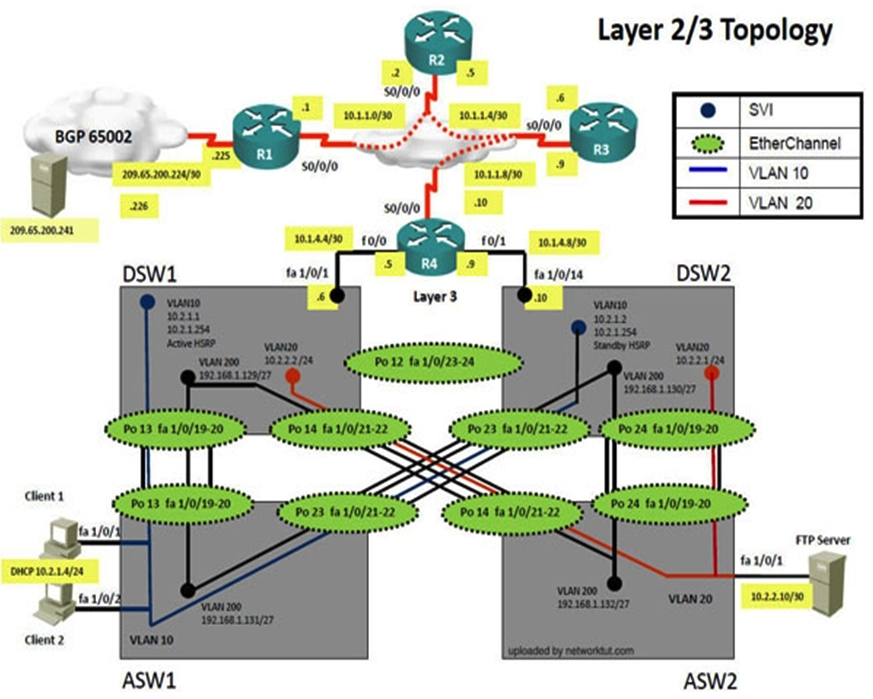 The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. On which device is the fault condition located?
The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. On which device is the fault condition located?
A) R1
B) R2
C) R3
D) R4
E) DSW1
F) DSW2
G) ASW1
H) ASW2
 The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. On which device is the fault condition located?
The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. On which device is the fault condition located?A) R1
B) R2
C) R3
D) R4
E) DSW1
F) DSW2
G) ASW1
H) ASW2

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
23
When designing interdomain multicast, which two protocols are deployed to achieve communication between multicast sources and receivers? (Choose two.)
A) IGMPv2
B) BIDIR-PIM
C) MP-BGP
D) MSDP
E) MLD
A) IGMPv2
B) BIDIR-PIM
C) MP-BGP
D) MSDP
E) MLD

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
24
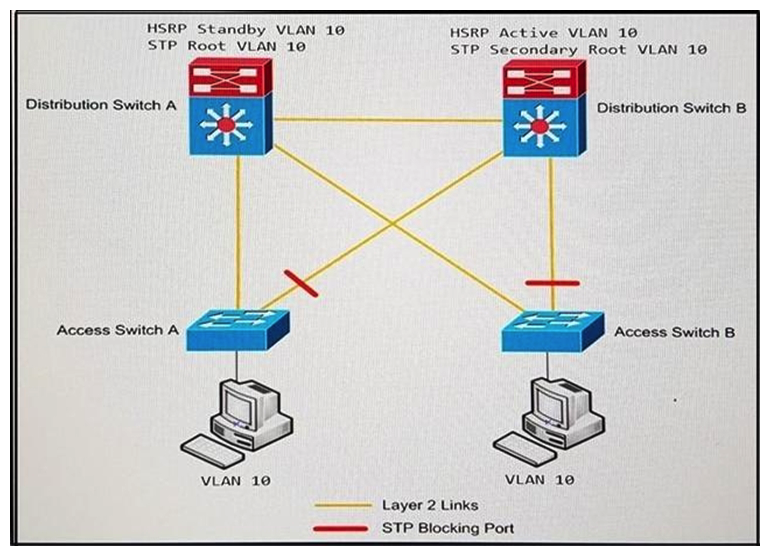 Refer to the exhibit. An engineer must optimize the traffic flow of the network. Which change provides a more efficient design between the access and the distribution layer?
Refer to the exhibit. An engineer must optimize the traffic flow of the network. Which change provides a more efficient design between the access and the distribution layer?A) Add a link between access switch A and access switch B
B) Reconfigure the distribution switch A to become the HSRP Active
C) Change the link between distribution switch A and distribution switch B to be a routed link
D) Create an EtherChannel link between distribution switch A and distribution switch B

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
25
Which feature is required for graceful restart to recover from a processor failure?
A) Cisco Express Forwarding
B) Virtual Switch System
C) Stateful Switchover
D) Bidirectional Forwarding Detection
A) Cisco Express Forwarding
B) Virtual Switch System
C) Stateful Switchover
D) Bidirectional Forwarding Detection

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
26
A router running ISIS is showing high CPU and bandwidth utilization. An engineer discovers that the router is configured as L1/L2 and has L1 and L2 neighbors. Which step optimizes the design to address the issue?
A) Make this router a DIS for each of the interfaces
B) Disable the default behavior of advertising the default route on the L1/L2 router
C) Configure the router to be either L1 or L2
D) Configure each interface as either L1 or L2 circuit type
A) Make this router a DIS for each of the interfaces
B) Disable the default behavior of advertising the default route on the L1/L2 router
C) Configure the router to be either L1 or L2
D) Configure each interface as either L1 or L2 circuit type

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
27
An engineer is designing an enterprise campus network. The LAN infrastructure consists of switches from multiple vendors, and Spanning Tree must be used as a Layer 2 loop prevention mechanism. All configured VLANs must be grouped in two STP instances. Which standards-based Spanning Tree technology supports this design solution?
A) MSTP
B) RSTP
C) Rapid PVST
D) STP
A) MSTP
B) RSTP
C) Rapid PVST
D) STP

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
28
An engineer is working with NETCONF and Cisco NX-OS based devices. The engineer needs a YANG model that supports a specific feature relevant only to Cisco NX-OS. Which model must the engineer choose?
A) Native
B) IEEE
C) OpenConfig
D) IETF
A) Native
B) IEEE
C) OpenConfig
D) IETF

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
29
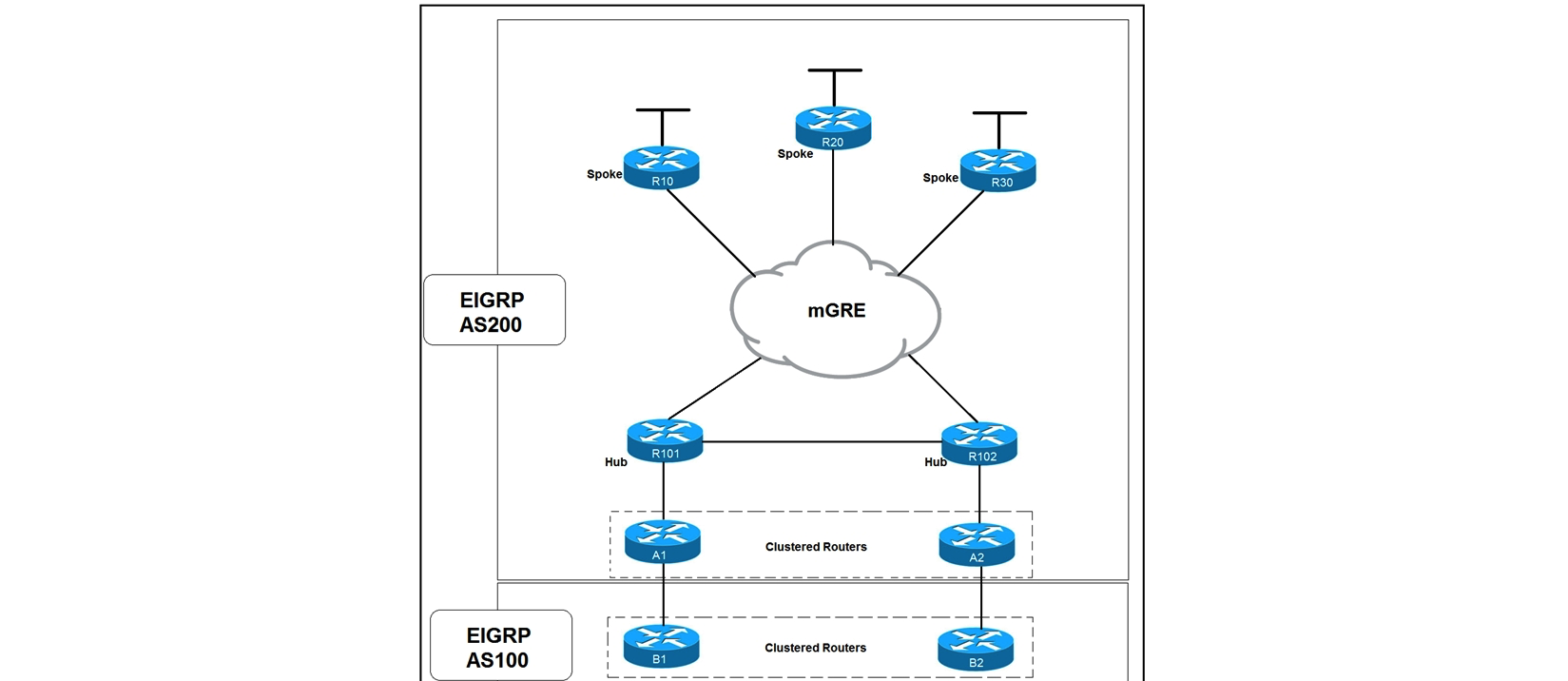 Refer to the exhibit. Which solution decreases the EIGRP convergence time?
Refer to the exhibit. Which solution decreases the EIGRP convergence time?A) Enable subsecond timers
B) Increase the hold time value
C) Increase the dead timer value
D) Enable stub routing on the spokes

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
30
When a first hop redundancy solution is designed, which protocol ensures that load balancing occurs over multiple routers using a single virtual IP address and multiple virtual MAC addresses?
A) GLBP
B) IRDP
C) VRRP
D) HSRP
A) GLBP
B) IRDP
C) VRRP
D) HSRP

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
31
Which control-plane technology allows the same subnet to exist across multiple network locations?
A) LISP
B) VXLAN
C) FabricPath
D) ISE mobility services
A) LISP
B) VXLAN
C) FabricPath
D) ISE mobility services

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
32
Which two steps can be taken to improve convergence in an OSPF network? (Choose two.)
A) Use Bidirectional Forwarding Detection
B) Merge all the areas into one backbone area
C) Tune OSPF parameters
D) Make all non-backbone areas stub areas
E) Span the same IP network across multiple areas.
A) Use Bidirectional Forwarding Detection
B) Merge all the areas into one backbone area
C) Tune OSPF parameters
D) Make all non-backbone areas stub areas
E) Span the same IP network across multiple areas.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
33
The implementations group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing scheme, DHCP services, NTP services, layer 2 connectivity, FHRP services, and device security, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolated the cause of this fault and answer the following questions. What is the solution to the fault condition?
A) Enable OSPF authentication on the s0/0/0 interface using the ip ospf authentication message-digest command
B) Enable OSPF routing on the s0/0/0 interface using the network 10.1.1.0 0.0.0.255 area 12 command.
C) Enable OSPF routing on the s0/0/0 interface using the network 209.65.200.0 0.0.0.255 area 12 command.
D) Redistribute the BGP route into OSPF using the redistribute BGP 65001 subnet command.
A) Enable OSPF authentication on the s0/0/0 interface using the ip ospf authentication message-digest command
B) Enable OSPF routing on the s0/0/0 interface using the network 10.1.1.0 0.0.0.255 area 12 command.
C) Enable OSPF routing on the s0/0/0 interface using the network 209.65.200.0 0.0.0.255 area 12 command.
D) Redistribute the BGP route into OSPF using the redistribute BGP 65001 subnet command.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
34
Instructions The main screen consists of two parts; the Main scenario and the Topology tabs. The main scenario describes TSHOOT.com test bed. The Topology tabs allow you to display the appropriate and select the trouble ticket. To complete the item, you will first need to familiarize yourself with the TSHOOT.com test bed by clicking on the master scenario first and then the topologies tabs. Once you are familiar with the test bed and the topologies, you should start evaluating the trouble ticket. You will be presented with a Trouble Ticket scenario that will describe the fault condition. You will need to determine on which device the fault condition is located, to which technology the fault condition is related, and the solution to each trouble ticket. This will be done by answering three questions. Ticket Selection To begin, click on the Ticket on the Topology tabs. Please note. Some of the questions will require you to use the scroll bar to see all options. Fault Isolation Read the ticket scenario to understand the fault condition. Open the appropriate topology, based upon the ticket scenario. Open the console of the desired device by clicking on that device in the topology, based upon your troubleshooting methodology. Use the supported show, ping and trace commands to begin your fault isolation process. Move to other devices as need by clicking on those devices within the topology. Fault Identification The trouble ticket will include three questions that you will need to answer, 1. Which device contains the fault 2. Which technology the fault condition is related to 3. What is the solution to the issue To advance to the next question within the ticket click on " Next Question ". When you click " DONE ", the trouble ticket will turn RED and will no longer be accessible. You may also use the " Previous Question " button to review questions within that specific ticket. To complete a trouble ticket, answer all three questions and click " ". This will store your response to the questions. Do not click on " " unless you have answered all questions within the ticket. Item Completion Click the NEXT button on the bottom of the screen once a ticket is . This action moves you to the next item. Scenario The company has created the test bed network shown in the layer 2 and layer 3 topology exhibits. This network consists of four routers, two layer 3 switches and two layer 2 switches. In the IPv4 layer 3 topology, R1, R2, R3, and R4 are running OSPF with an OSPF process number 1. DSW1, DSW2 and R4 are running EIGRP with an AS of 10. Redistribution is enabled where necessary. R1 is running a BGP AS with a number of 65001. This AS has an eBGP connection to AS 65002 in the ISP's network. Because the company's address space is in the private range, R1 is also providing NAT translations between the inside (10.1.0.0/16 & 10.2.0.0/16) networks and the outside (209.65.200.0/24) network. ASW1 and ASW2 are layer 2 switches. NTP is enabled on all devices with 209.65.200.226 serving as the master clock source. The client workstations receive their IP address and default gateway via R4's DHCP server. The default gateway address of 10.2.1.254 is the IP address of HSRP group 10 which is running on DSW1 and DSW2. In the IPv6 layer 3 topology R1, R2, and R3 are running OSPFv3 with an OSPF process number 6. DSW1, DSW2 and R4 are running RIPng process name RIP_ZONE. The two IPv6 routing domains, OSPF 6 and RIPng are connected via GRE tunnel running over the underlying IPv4 OSPF domain. Redistribution is enabled where necessary. Recently the implementation group has been using the test bed to do a 'proof-of-concept' on several implementations. This involved changing the configuration on one or more of the devices. You will be presented with a series of trouble tickets related to issues introduced during these configurations. 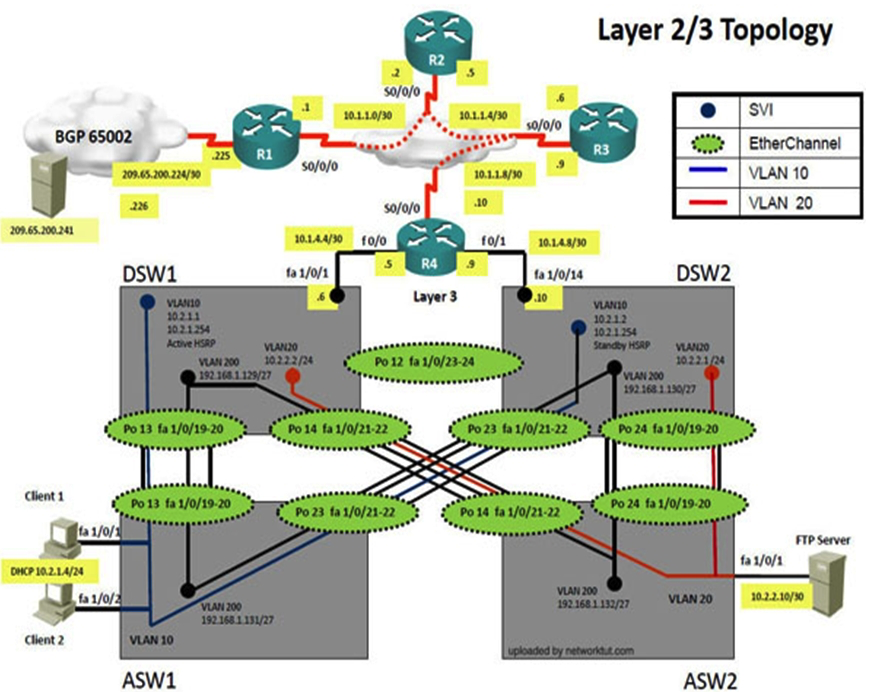 The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. The fault condition is related to which technology?
The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. The fault condition is related to which technology?
A) NTP
B) Switch-to-Switch Connectivity
C) Loop Prevention
D) Access Vlans
E) Port Security
F) VLAN ACL / Port ACL
G) Switch Virtual Interface
 The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. The fault condition is related to which technology?
The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing schemes, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. The fault condition is related to which technology?A) NTP
B) Switch-to-Switch Connectivity
C) Loop Prevention
D) Access Vlans
E) Port Security
F) VLAN ACL / Port ACL
G) Switch Virtual Interface

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
35
Instructions The main screen consists of two parts the Main scenario and the Topology tabs. The main scenario describes TSHOOT.com test bed. The Topology tabs allow you to display the appropriate and select the trouble ticket. To complete the item, you will first need to familiarize yourself with the TSHOOT.com test bed by clicking on the master scenario first and then the topologies tabs. Once you are familiar with the test bed and the topologies, you should start evaluating the trouble ticket. You will be presented with a Trouble Ticket scenario that will describe the fault condition. You will need to determine on which device the fault condition is located, to which technology the fault condition is related, and the solution to each trouble ticket. This will be done by respnsing three questions. Ticket Selection To begin, click on the Ticket on the Topology tabs. Please note. Some of the questions will require you to use the scroll bar to see all options. Fault Isolation Read the ticket scenario to understand the fault condition. Open the appropriate topology, based upon the ticket scenario. Open the console of the desired device by clicking on that device in the topology, based upon your troubleshooting methodology. Use the supported show, ping and trace commands to begin your fault isolation process. Move to other devices as need by clicking on those devices within the topology. Fault Identification The trouble ticket will include three questions that you will need to answer, 1. Which device contains the fault 2. Which technology the fault condition is related to 3. What is the solution to the issue To advance to the next question within the ticket click on " Next Question ". When you click " DONE ", the trouble ticket will turn RED and will no longer be accessible. You may also use the " Previous Question " button to review questions within that specific ticket. To complete a trouble ticket, answer all three questions and click " ". This will store your response to the questions. Do not click on " " unless you have responsed all questions within the ticket. Item Completion Click the NEXT button on the bottom of the screen once a ticket is . This action moves you to the next item. Scenario The company has created the test bed network shown in the layer 2 and layer 3 topology exhibits. This network consists of four routers, two layer 3 switches and two layer 2 switches. In the IPv4 layer 3 topology, R1, R2, R3, and R4 are running OSPF with an OSPF process number 1. DSW1, DSW2 and R4 are running EIGRP with an AS of 10. Redistribution is enabled where necessary. R1 is running a BGP AS with a number of 65001. This AS has an eBGP connection to AS 65002 in the ISP's network. Because the company's address space is in the private range, R1 is also providing NAT translations between the inside (10.1.0.0/16 & 10.2.0.0/16) networks and the outside (209.65.200.0/24) network. ASW1 and ASW2 are layer 2 switches. NTP is enabled on all devices with 209.65.200.226 serving as the master clock source. The client workstations receive their IP address and default gateway via R4's DHCP server. The default gateway address of 10.2.1.254 is the IP address of HSRP group 10 which is running on DSW1 and DSW2. In the IPv6 layer 3 topology R1, R2, and R3 are running OSPFv3 with an OSPF process number 6. DSW1, DSW2 and R4 are running RIPng process name RIP_ZONE. The two IPv6 routing domains, OSPF 6 and RIPng are connected via GRE tunnel running over the underlying IPv4 OSPF domain. Redistribution is enabled where necessary. Recently the implementation group has been using the test bed to do a 'proof-of-concept' on several implementations. This involved changing the configuration on one or more of the devices. You will be presented with a series of trouble tickets related to issues introduced during these configurations. 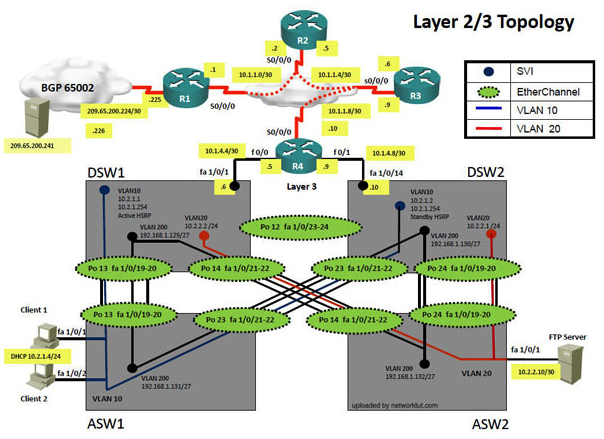 The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing scheme, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. What is the solution to the fault condition?
The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing scheme, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. What is the solution to the fault condition?
A) In configuration mode, using the interface range port-channel 23, port-channel 24 , then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,20,200 commands. In configuration mode, using the interface range port-channel 23, port-channel 24 , then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,20,200 commands.
B) In configuration mode, using the interface range port-channel 13, port-channel 23, then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,200 commands. interface range port-channel 13, port-channel 23, then configure switchport trunk allowed vlan none switchport trunk allowed vlan 10,200
C) In configuration mode, using the interface range port-channel 23, port-channel 24, then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,20, commands. interface range port-channel 23, port-channel 24, then configure switchport trunk allowed vlan 10,20,
D) In configuration mode, using the interface range port-channel 13, port-channel 23, then configure switchport trunk allowed vlan 10,200 followed by interface Fastethernet 1/0/1, then no shutdown commands. interface range port-channel 13, port-channel 23, interface Fastethernet 1/0/1, then no shutdown
 The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing scheme, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. What is the solution to the fault condition?
The implementation group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing scheme, DHCP services, NTP services, and FHRP services, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolate the cause of this fault and answer the following questions. What is the solution to the fault condition?A) In configuration mode, using the interface range port-channel 23, port-channel 24 , then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,20,200 commands. In configuration mode, using the interface range port-channel 23, port-channel 24 , then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,20,200 commands.
B) In configuration mode, using the interface range port-channel 13, port-channel 23, then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,200 commands. interface range port-channel 13, port-channel 23, then configure switchport trunk allowed vlan none switchport trunk allowed vlan 10,200
C) In configuration mode, using the interface range port-channel 23, port-channel 24, then configure switchport trunk allowed vlan none followed by switchport trunk allowed vlan 10,20, commands. interface range port-channel 23, port-channel 24, then configure switchport trunk allowed vlan 10,20,
D) In configuration mode, using the interface range port-channel 13, port-channel 23, then configure switchport trunk allowed vlan 10,200 followed by interface Fastethernet 1/0/1, then no shutdown commands. interface range port-channel 13, port-channel 23, interface Fastethernet 1/0/1, then no shutdown

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
36
Which two statements describe source trees in a multicast environment? (Choose two.)
A) Source trees guarantee the minimum amount of network latency for forwarding multicast traffic
B) Source trees create an optimal path between the source and the receivers
C) Source trees use a single common root placed at some chosen point in the network
D) Source trees can introduce latency in packet delivery
E) Source trees can create suboptimal paths between the source and the receivers
A) Source trees guarantee the minimum amount of network latency for forwarding multicast traffic
B) Source trees create an optimal path between the source and the receivers
C) Source trees use a single common root placed at some chosen point in the network
D) Source trees can introduce latency in packet delivery
E) Source trees can create suboptimal paths between the source and the receivers

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
37
The implementations group has been using the test bed to do a 'proof-of-concept' that requires both Client 1 and Client 2 to access the WEB Server at 209.65.200.241. After several changes to the network addressing, routing scheme, DHCP services, NTP services, layer 2 connectivity, FHRP services, and device security, a trouble ticket has been opened indicating that Client 1 cannot ping the 209.65.200.241 address. Use the supported commands to isolated the cause of this fault and answer the following questions. The fault condition is related to which technology?
A) BGP
B) NTP
C) IP NAT
D) IPv4 OSPF Routing
E) IPv4 OSPF Redistribution
F) IPv6 OSPF Routing
G) IPv4 layer 3 security
A) BGP
B) NTP
C) IP NAT
D) IPv4 OSPF Routing
E) IPv4 OSPF Redistribution
F) IPv6 OSPF Routing
G) IPv4 layer 3 security

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
38
Which two routing protocols allow for unequal cost load balancing? (Choose two.)
A) EIGRP
B) IS-IS
C) BGP
D) OSPF
E) RIPng
A) EIGRP
B) IS-IS
C) BGP
D) OSPF
E) RIPng

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
39
What are two valid scaling techniques when an EIGRP network is designed that consists of more than 1000 routers? (Choose two.)
A) Use structured hierarchical topology with route summarization
B) Used sub-second timers
C) Use the distribute-list command to filter routes Use the distribute-list command to filter routes
D) Modify delay parameters on the links
E) Implement multiple EIGRP autonomous systems
A) Use structured hierarchical topology with route summarization
B) Used sub-second timers
C) Use the distribute-list command to filter routes Use the distribute-list command to filter routes
D) Modify delay parameters on the links
E) Implement multiple EIGRP autonomous systems

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
40
When vEdge router redundancy is designed, which FHRP is supported?
A) HSRP
B) OMP
C) GLBP
D) VRRP
A) HSRP
B) OMP
C) GLBP
D) VRRP

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
41
You have executed the following commands on switchA: 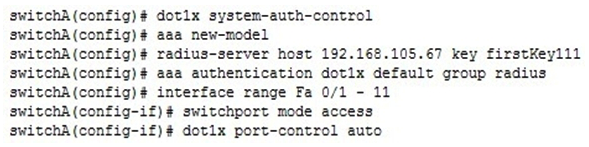 What is the result of executing the given commands? (Choose two.)
What is the result of executing the given commands? (Choose two.)
A) Only the listed RADIUS server is used for authentication
B) 802.1X authentication is enabled on the Fa0/1 interface only
C) The key for the RADIUS server is firstKey111
D) AAA is not enabled on the switch
 What is the result of executing the given commands? (Choose two.)
What is the result of executing the given commands? (Choose two.)A) Only the listed RADIUS server is used for authentication
B) 802.1X authentication is enabled on the Fa0/1 interface only
C) The key for the RADIUS server is firstKey111
D) AAA is not enabled on the switch

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
42
Which technology provides a multichassis IP connection between VSS-enabled switches and downstream devices?
A) LACP
B) MEC
C) ICCP
D) LAG
E) BFD
F) PAgP
A) LACP
B) MEC
C) ICCP
D) LAG
E) BFD
F) PAgP

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
43
Refer to the exhibit. MTU has been configured as shown, and no MTU command has been configured on the tunnel interfaces. It has been found that fragmentation is occurring when tunneled packets are placed onto the IPv6 underlay network. Which configuration change will resolve this problem? 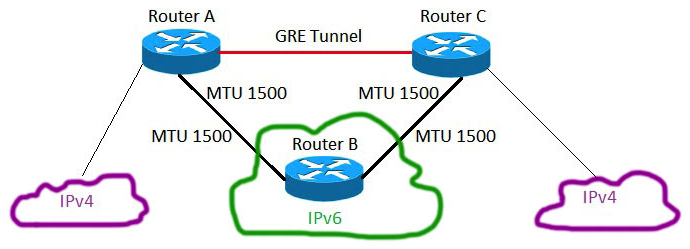
A) Set the MTU to 1476 on the tunnel interfaces
B) Increase the MTU on the IPv6 network
C) Set the MTU to 1500 on the tunnel interfaces
D) Increase the MTU on the IPv4 networks

A) Set the MTU to 1476 on the tunnel interfaces
B) Increase the MTU on the IPv6 network
C) Set the MTU to 1500 on the tunnel interfaces
D) Increase the MTU on the IPv4 networks

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
44
Refer to the exhibit. 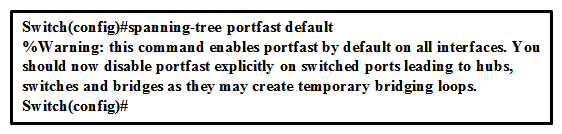 When troubleshooting a network problem, a network analyzer is connected to Port f0/1 of a LAN switch. Which command can prevent BPDU transmission on this port?
When troubleshooting a network problem, a network analyzer is connected to Port f0/1 of a LAN switch. Which command can prevent BPDU transmission on this port?
A) spanning-tree portfast bpduguard enable
B) spanning-tree bpduguard default
C) spanning-tree portfast bpdufilter default
D) no spanning-tree link-type shared
 When troubleshooting a network problem, a network analyzer is connected to Port f0/1 of a LAN switch. Which command can prevent BPDU transmission on this port?
When troubleshooting a network problem, a network analyzer is connected to Port f0/1 of a LAN switch. Which command can prevent BPDU transmission on this port?A) spanning-tree portfast bpduguard enable
B) spanning-tree bpduguard default
C) spanning-tree portfast bpdufilter default
D) no spanning-tree link-type shared

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
45
Refer to the exhibit.  Which statement about the INTERNET ACL is true?
Which statement about the INTERNET ACL is true?
A) The denied entries will be logged because of the explicit deny ipv6 any any log line.
B) A packet with a source address of 2001:DB8:AD59:ACC0:2020:882:DB8:1125 will be denied.
C) HTTPS traffic from the 2001:DB8:AD59:BA21::/64 subnet will automatically be permitted along with HTTP traffic.
D) A packet with a source address of 2001:DB80:AD59:BA21:101:CAB:64:38 destined to port 80 will be permitted.
 Which statement about the INTERNET ACL is true?
Which statement about the INTERNET ACL is true?A) The denied entries will be logged because of the explicit deny ipv6 any any log line.
B) A packet with a source address of 2001:DB8:AD59:ACC0:2020:882:DB8:1125 will be denied.
C) HTTPS traffic from the 2001:DB8:AD59:BA21::/64 subnet will automatically be permitted along with HTTP traffic.
D) A packet with a source address of 2001:DB80:AD59:BA21:101:CAB:64:38 destined to port 80 will be permitted.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
46
Which authentication service is needed to configure 802.1x?
A) RADIUS with EAP Extension
B) TACACS+
C) RADIUS with CoA
D) RADIUS using VSA
A) RADIUS with EAP Extension
B) TACACS+
C) RADIUS with CoA
D) RADIUS using VSA

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
47
Which method will filter routes between EIGRP neighbors within the same autonomous system?
A) distribute-list
B) policy-based routing
C) leak-map
D) route tagging
A) distribute-list
B) policy-based routing
C) leak-map
D) route tagging

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
48
A company is using OSPF between its HQ location and a branch office. HQ is assigned to area 0, and the branch office is assigned to area 1. The company purchases a second branch office, but due to circuit delays to HQ, it decides to connect the new branch office to the existing branch office as a temporary measure. The new branch office is assigned to area 2. Which OSPF configuration enables all three locations to exchange routes?
A) The existing branch office must be configured as a stub area
B) A virtual link must be configured between the new branch office and HQ
C) A sham link must be configured between the new branch office and HQ
D) The new branch office must be configured as a stub area
A) The existing branch office must be configured as a stub area
B) A virtual link must be configured between the new branch office and HQ
C) A sham link must be configured between the new branch office and HQ
D) The new branch office must be configured as a stub area

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
49
Refer to the exhibit. PC-2 failed to establish a Telnet connection to the Terminal Server. Which solution allows PC-2 to establish the Telnet connection? 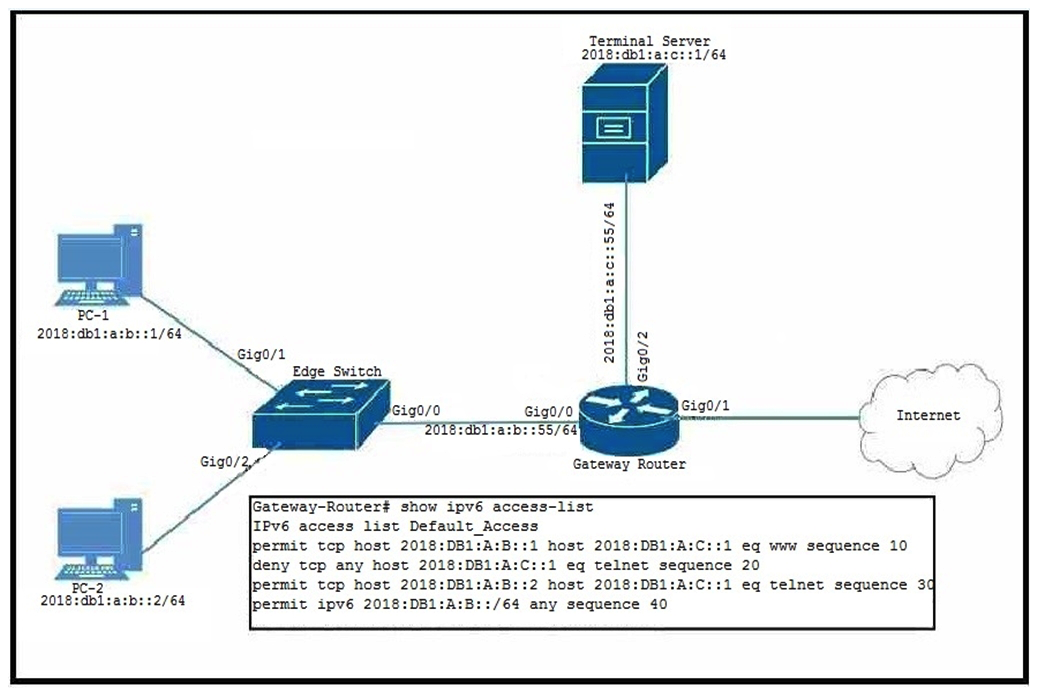
A) Gateway-Router(config)# ipv6 access-list Default_Access Gateway-Router(config-ipv6-acl)# no sequence 20 Gateway-Router(config-ipv6-acl)# sequence 5 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet Gateway-Router(config)# ipv6 access-list Default_Access Gateway-Router(config-ipv6-acl)# no sequence 20 sequence 5 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet
B) Gateway-Router(config-ipv6-acl)# permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet
C) Gateway-Router(config-ipv6-acl)# sequence 15 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet sequence 15 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet
D) Gateway-Router(config-ipv6-acl)# sequence 25 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet sequence 25 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet

A) Gateway-Router(config)# ipv6 access-list Default_Access Gateway-Router(config-ipv6-acl)# no sequence 20 Gateway-Router(config-ipv6-acl)# sequence 5 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet Gateway-Router(config)# ipv6 access-list Default_Access Gateway-Router(config-ipv6-acl)# no sequence 20 sequence 5 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet
B) Gateway-Router(config-ipv6-acl)# permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet
C) Gateway-Router(config-ipv6-acl)# sequence 15 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet sequence 15 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet
D) Gateway-Router(config-ipv6-acl)# sequence 25 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet sequence 25 permit tcp host 2018:DB1:A:B::2 host 2018:DB1:A:C::1 eq telnet

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
50
Which switch feature prevents traffic on a LAN from being overwhelmed by continuous multicast or broadcast traffic?
A) storm control
B) port security
C) VTP pruning
D) VLAN trunking
A) storm control
B) port security
C) VTP pruning
D) VLAN trunking

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
51
Which two tasks must you perform to configure DHCP snooping on a device? (Choose two.)
A) Enable DHCP packet validation on the device
B) Enable DHCP option 82
C) Enable DHCP snooping on the VLAN
D) Enable DHCP snooping globally
E) Enable VRF support for the DHCP relay agent
A) Enable DHCP packet validation on the device
B) Enable DHCP option 82
C) Enable DHCP snooping on the VLAN
D) Enable DHCP snooping globally
E) Enable VRF support for the DHCP relay agent

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
52
A company has the following network infrastructure. (Refer to the exhibit.) 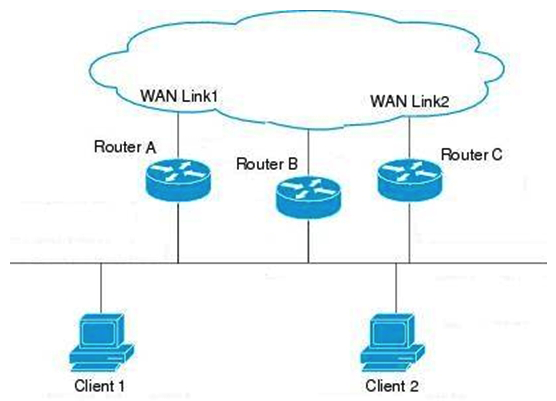 Router A is a GLBP active virtual gateway with priority level set to 250. Routers B and C are configured with the default GLPB configurations. The configuration of the active virtual gateway needs to be changed such that if the AVG fails, Router C should be elected to be used as an active virtual gateway. As the network administrator, you have been asked to make corresponding changes to the configuration. Which command would you use for this purpose on Router C, and where would the command be configured?
Router A is a GLBP active virtual gateway with priority level set to 250. Routers B and C are configured with the default GLPB configurations. The configuration of the active virtual gateway needs to be changed such that if the AVG fails, Router C should be elected to be used as an active virtual gateway. As the network administrator, you have been asked to make corresponding changes to the configuration. Which command would you use for this purpose on Router C, and where would the command be configured?
A) glbp 10 preempt (on Router B)
B) glbp 10 preempt (on Router C)
C) glbp 10 priority 200 (on Router B)
D) glbp 10 priority 200 (on Router C)
 Router A is a GLBP active virtual gateway with priority level set to 250. Routers B and C are configured with the default GLPB configurations. The configuration of the active virtual gateway needs to be changed such that if the AVG fails, Router C should be elected to be used as an active virtual gateway. As the network administrator, you have been asked to make corresponding changes to the configuration. Which command would you use for this purpose on Router C, and where would the command be configured?
Router A is a GLBP active virtual gateway with priority level set to 250. Routers B and C are configured with the default GLPB configurations. The configuration of the active virtual gateway needs to be changed such that if the AVG fails, Router C should be elected to be used as an active virtual gateway. As the network administrator, you have been asked to make corresponding changes to the configuration. Which command would you use for this purpose on Router C, and where would the command be configured?A) glbp 10 preempt (on Router B)
B) glbp 10 preempt (on Router C)
C) glbp 10 priority 200 (on Router B)
D) glbp 10 priority 200 (on Router C)

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
53
Which three feature sets are used in Stackwise technology? (Choose three.)
A) LAN Base
B) IP Base
C) WAN Services
D) IP Services
E) ARP Base
F) LAN Agent
A) LAN Base
B) IP Base
C) WAN Services
D) IP Services
E) ARP Base
F) LAN Agent

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
54
In what mode does an LWAPP-enabled access point operate?
A) lightweight mode
B) autonomous mode
C) WGB
D) ad hoc mode
A) lightweight mode
B) autonomous mode
C) WGB
D) ad hoc mode

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
55
Which statements about RSPAN are true? (Choose two.)
A) It supports MAC address learning.
B) RSPAN VLANS can carry RSPAN traffic only.
C) only one RSPAN VLAN can be configured per device.
D) RSPAN VLANs are exempt from VTP pruning.
E) MAC address learning is not supported
F) RSPAN uses are GRE tunnel to transmit captured traffic.
A) It supports MAC address learning.
B) RSPAN VLANS can carry RSPAN traffic only.
C) only one RSPAN VLAN can be configured per device.
D) RSPAN VLANs are exempt from VTP pruning.
E) MAC address learning is not supported
F) RSPAN uses are GRE tunnel to transmit captured traffic.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
56
Which of the following features does GLBP provide, but not HSRP and VRRP? (Choose all that apply.)
A) Support for single active router
B) Support for automatic load balancing
C) Support for multiple gateways
D) Support for interface tracking
A) Support for single active router
B) Support for automatic load balancing
C) Support for multiple gateways
D) Support for interface tracking

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
57
Which command is needed to enable DHCP snooping if a switchport is connected to a DHCP server?
A) ip dhcp snooping trust
B) ip dhcp snooping
C) ip dhcp trust
D) ip dhcp snooping information
A) ip dhcp snooping trust
B) ip dhcp snooping
C) ip dhcp trust
D) ip dhcp snooping information

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
58
When provisioning bandwidth for an IP telephony network, which elements are unique to an IP telephony call? (Choose two.)
A) voice stream
B) IGMP packets
C) call-control signaling
D) routing protocol packets
E) speed of the segment to the telephone
A) voice stream
B) IGMP packets
C) call-control signaling
D) routing protocol packets
E) speed of the segment to the telephone

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
59
Refer to the exhibit. An IPv6 network was just deployed in the environment and the help desk has reported that R3 is not able to SSH to R2's Loopback interface. Which sequence number of the filter is preventing access? 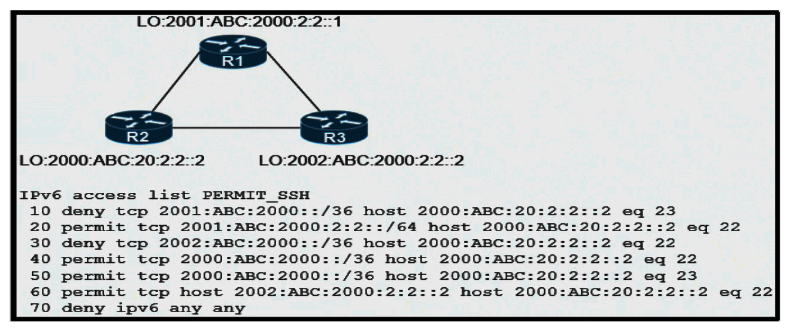
A) 10
B) 20
C) 30
D) 70

A) 10
B) 20
C) 30
D) 70

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
60
Which statement describes what happens if all VSL connections between the virtual switch members are lost?
A) Both virtual switch members cease to forward traffic.
B) The VSS transitions to the dual active recovery mode, and both virtual switch members continue to forward traffic independently.
C) The virtual switch members reload.
D) The VSS transitions to the dual active recovery mode, and only the new active virtual switch continues to forward traffic.
A) Both virtual switch members cease to forward traffic.
B) The VSS transitions to the dual active recovery mode, and both virtual switch members continue to forward traffic independently.
C) The virtual switch members reload.
D) The VSS transitions to the dual active recovery mode, and only the new active virtual switch continues to forward traffic.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
61
Which OSPF area blocks LSA Type 3, 4 and 5, but allows a default summary route?
A) normal
B) stub
C) NSSA
D) totally stubby
A) normal
B) stub
C) NSSA
D) totally stubby

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
62
How is end-to-end microsegmentation enforced in a Cisco SD-Access architecture?
A) VLANs are used to segment traffic at Layer 2.
B) 5-tuples and ACLs are used to permit or deny traffic.
C) SGTs and SGTACLs are used to control access to various resources.
D) VRFs are used to segment traffic at Layer 3.
A) VLANs are used to segment traffic at Layer 2.
B) 5-tuples and ACLs are used to permit or deny traffic.
C) SGTs and SGTACLs are used to control access to various resources.
D) VRFs are used to segment traffic at Layer 3.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
63
An engineer must propose a QoS architecture model that allows an application to inform the network of its traffic profile and to request a particular type of service to support its bandwidth and delay requirements. The application requires consistent and dedicated bandwidth end to end. Which QoS architecture model meets these requirements?
A) DiffServ
B) LLQ
C) WRED
D) IntServ
A) DiffServ
B) LLQ
C) WRED
D) IntServ

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
64
Which function are fabric intermediate nodes responsible for in an SD-Access Architecture?
A) mapping EIDs to RLOCs
B) encapsulating user traffic in a VXLAN header including the SGT
C) registering new endpoints in the HTDB
D) transporting IP packets between edge nodes and border nodes
A) mapping EIDs to RLOCs
B) encapsulating user traffic in a VXLAN header including the SGT
C) registering new endpoints in the HTDB
D) transporting IP packets between edge nodes and border nodes

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
65
An engineer is designing a QoS policy that queues excess packets for later transmission. Which mechanism must be included in the design?
A) shaping
B) WRED
C) policing
D) RED
A) shaping
B) WRED
C) policing
D) RED

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
66
Which two techniques improve the application experience in a Cisco SD-WAN design? (Choose two.)
A) utilizing forward error correction
B) implementing a stateful application firewall
C) implementing AMP
D) utilizing quality of service
E) implementing Cisco Umbrella
A) utilizing forward error correction
B) implementing a stateful application firewall
C) implementing AMP
D) utilizing quality of service
E) implementing Cisco Umbrella

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
67
A network engineer must segregate three interconnected campus networks using IS-IS routing. A two-layer hierarchy must be used to support large routing domains and to avoid more specific routes from each campus network being advertised to other campus network routers automatically. Which two actions does the engineer take to accomplish this segregation? (Choose two.)
A) Designate two IS-IS routers as BDR routers at the edge of each campus, and configure one BDR for all Level 1 routers and one BDR for all Level 2 routers.
B) Designate two IS-IS routers from each campus to act as Level 1/Level 2 backbone routers at the edge of each campus network.
C) Assign the same IS-IS NET value for each campus, and configure internal campus routers with Level 1/Level 2 routing.
D) Utilize different MTU values for each campus network segment. Level 2 backbone routers must utilize a larger MTU size of 9216.
E) Assign a unique IS-IS NET value for each campus, and configure internal campus routers with Level 1 routing.
A) Designate two IS-IS routers as BDR routers at the edge of each campus, and configure one BDR for all Level 1 routers and one BDR for all Level 2 routers.
B) Designate two IS-IS routers from each campus to act as Level 1/Level 2 backbone routers at the edge of each campus network.
C) Assign the same IS-IS NET value for each campus, and configure internal campus routers with Level 1/Level 2 routing.
D) Utilize different MTU values for each campus network segment. Level 2 backbone routers must utilize a larger MTU size of 9216.
E) Assign a unique IS-IS NET value for each campus, and configure internal campus routers with Level 1 routing.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
68
Which design element should an engineer consider when multicast is included in a Cisco SD-Access architecture?
A) PIM SSM must run in the underlay.
B) Multicast clients reside in the underlay, and the multicast source is outside the fabric or in the overlay.
C) Rendezvous points must be used in a PIM SSM deployment.
D) Multicast traffic is transported in the overlay and the EID space for wired and wireless clients.
A) PIM SSM must run in the underlay.
B) Multicast clients reside in the underlay, and the multicast source is outside the fabric or in the overlay.
C) Rendezvous points must be used in a PIM SSM deployment.
D) Multicast traffic is transported in the overlay and the EID space for wired and wireless clients.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
69
Which control-plane protocol is used to map an endpoint to a location in a Cisco SD-Access network?
A) FabricPath
B) IS-IS
C) LISP
D) MP-BGP
A) FabricPath
B) IS-IS
C) LISP
D) MP-BGP

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
70
A large chain of stores currently uses MPLS-based T1 lines to connect their stores to their data center. An architect must design a new solution to improve availability and reduce costs while keeping these considerations in mind: The company uses multicast to deliver training to the stores. The company uses dynamic routing protocols and has implemented QoS. To simplify deployments, tunnels should be created dynamically on the hub when additional stores open. Which solution should be included in this design?
A) VPLS
B) GET VPN
C) DMVPN
D) IPsec
A) VPLS
B) GET VPN
C) DMVPN
D) IPsec

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
71
A company with multiple service providers wants to speed up BGP convergence time in the event a failure occurs with their primary link. Which approach achieves this goal and does not impact router CPU utilization?
A) Utilize BFD and tune the multiplier to 50
B) Lower the BGP hello interval
C) Decrease the BGP keepalive timer
D) Utilize BFD and keep the default BGP timers
A) Utilize BFD and tune the multiplier to 50
B) Lower the BGP hello interval
C) Decrease the BGP keepalive timer
D) Utilize BFD and keep the default BGP timers

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
72
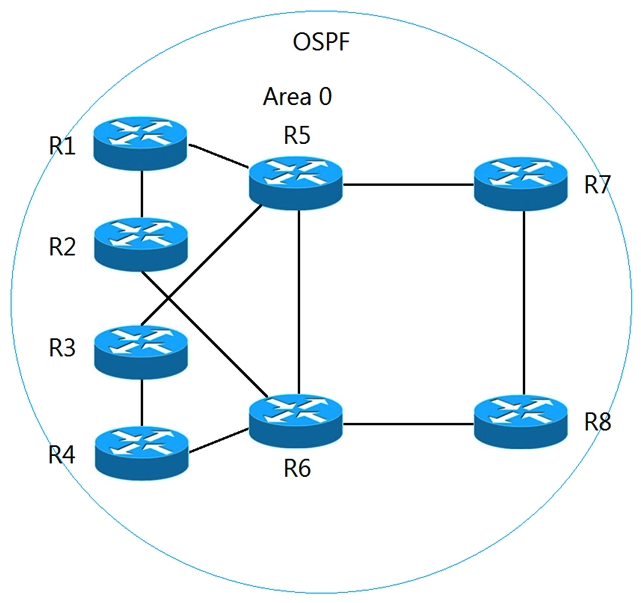 Refer to the exhibit. All routers currently reside in OSPF area 0. The network manager recently used R1 and R2 as aggregation routers for remote branch locations and R3 and R4 for aggregation routers for remote office locations. The network has since been suffering from outages, which are causing frequent SPF runs. To enhance stability and introduce areas to the OSPF network with the minimal number of ABRs possible, which two solutions should the network manager recommend? (Choose two.)
Refer to the exhibit. All routers currently reside in OSPF area 0. The network manager recently used R1 and R2 as aggregation routers for remote branch locations and R3 and R4 for aggregation routers for remote office locations. The network has since been suffering from outages, which are causing frequent SPF runs. To enhance stability and introduce areas to the OSPF network with the minimal number of ABRs possible, which two solutions should the network manager recommend? (Choose two.)A) a new OSPF area for R1 and R2 connections, with R1 and R2 as ABRs
B) a new OSPF area for R3 and R4 connections, with R5 and R6 as ABRs
C) a new OSPF area for R3 and R4 connections, with R3 and R4 as ABRs
D) a new OSPF area for R1, R2, R3, and R4 connections, with R1, R2, R3, and R4 as ABRs
E) a new OSPF area for R1 and R2 connections, with R5 and R6 as ABRs

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
73
Which PIM mode uses a shared tree only?
A) bidirectional
B) sparse
C) dense
D) source-specific
A) bidirectional
B) sparse
C) dense
D) source-specific

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
74
An organization is designing a detailed QoS plan that limits bandwidth to specific rates. Which two parameters are supported by the traffic policing feature? (Choose two.)
A) violating
B) marking
C) shaping
D) bursting
E) conforming
A) violating
B) marking
C) shaping
D) bursting
E) conforming

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
75
What are two benefits of designing an SD-WAN network fabric with direct Internet access implemented at every site? (Choose two.)
A) It decreases latency to applications hosted by public cloud service provider.
B) It decreases latency on Internet circuits.
C) It increases the speed of delivery of site deployments through zero-touch provisioning.
D) It increases the total available bandwidth on Internet circuits.
E) It alleviates network traffic on MPLS circuits.
A) It decreases latency to applications hosted by public cloud service provider.
B) It decreases latency on Internet circuits.
C) It increases the speed of delivery of site deployments through zero-touch provisioning.
D) It increases the total available bandwidth on Internet circuits.
E) It alleviates network traffic on MPLS circuits.

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
76
Company A recently acquired another company. Users of the newly acquired company must be able to access a server that exists on Company A's network, both companies use overlapping IP address ranges. Which action conserves IP address space and provides access to the server?
A) Use a single IP address to create overload NAT
B) Use a single IP address to create a static NAT entry
C) Build one-to-one NAT translation for every user that needs access
D) Re-IP overlapping address space in the acquired company
A) Use a single IP address to create overload NAT
B) Use a single IP address to create a static NAT entry
C) Build one-to-one NAT translation for every user that needs access
D) Re-IP overlapping address space in the acquired company

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
77
An engineer is working for a large cable TV provider that requires multiple sources streaming video on different channels using multicast with no rendezvous point. Which multicast protocol meets these requirements?
A) PIM-SM
B) PIM-SSM
C) any-source multicast
D) BIDIR-PIM
A) PIM-SM
B) PIM-SSM
C) any-source multicast
D) BIDIR-PIM

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
78
Which two functions are provided by the Cisco SD-WAN orchestration plane? (Choose two.)
A) centralized provisioning
B) primary authentication point
C) NAT traversal facilitation
D) Zero Touch Provisioning
E) troubleshooting and monitoring
A) centralized provisioning
B) primary authentication point
C) NAT traversal facilitation
D) Zero Touch Provisioning
E) troubleshooting and monitoring

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
79
Which two best practices must be followed when designing an out-of-band management network? (Choose two.)
A) Enforce access control
B) Facilitate network integration
C) Back up data using the management network
D) Ensure that the management network is a backup to the data network
E) Ensure network isolation
A) Enforce access control
B) Facilitate network integration
C) Back up data using the management network
D) Ensure that the management network is a backup to the data network
E) Ensure network isolation

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck
80
An infrastructure team is concerned about the shared memory utilization of a device, and for this reason, they need to monitor the device state. Which solution limits impact on the device and provides the required data?
A) IPFIX
B) static telemetry
C) on-change subscription
D) periodic subscription
A) IPFIX
B) static telemetry
C) on-change subscription
D) periodic subscription

Unlock Deck
Unlock for access to all 109 flashcards in this deck.
Unlock Deck
k this deck


