Deck 15: Implementing Cisco Service Provider VPN Services (SPVI)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/49
Play
Full screen (f)
Deck 15: Implementing Cisco Service Provider VPN Services (SPVI)
1
Which two are characteristics of using a non-MPLS peer-to-peer model over a traditional overlay model? (Choose two.)
A) The model is suited for nonredundant configurations.
B) The configuration on a newly added site PE is updated automatically.
C) Provider routers know the customer network topology.
D) The customer specifies the exact site-to-site traffic profile.
E) Routing information is exchanged between the customer router and one or a few PEs.
A) The model is suited for nonredundant configurations.
B) The configuration on a newly added site PE is updated automatically.
C) Provider routers know the customer network topology.
D) The customer specifies the exact site-to-site traffic profile.
E) Routing information is exchanged between the customer router and one or a few PEs.
Provider routers know the customer network topology.
Routing information is exchanged between the customer router and one or a few PEs.
Routing information is exchanged between the customer router and one or a few PEs.
2
Which utility can you use to validate an LSP in an MPLS environment?
A) uRPF
B) MPLS LSP ping
C) logging
D) RSVP
A) uRPF
B) MPLS LSP ping
C) logging
D) RSVP
MPLS LSP ping
3
You try to configure MPLS VPN VRF Selection based on a source IP address on an interface that has VRF configured, but you receive an error. Which action must you take to correct the problem?
A) Change the source IP address.
B) Add the IP address to the VRF table.
C) Remove the VRF from the interface.
D) Configure static routes for the VRF.
A) Change the source IP address.
B) Add the IP address to the VRF table.
C) Remove the VRF from the interface.
D) Configure static routes for the VRF.
Remove the VRF from the interface.
4
While configuring the VRF Selection feature, you get an error message after typing the below statement: Router(config)#no vrf selection source 172.16.0.0 255.255.0.0 vrf VRF1 Which action caused this message?
A) the entry of an inconsistent IP address and mask for VRF Selection
B) an attempt to configure a VRF instance on an interface that already has VRF Selection configured
C) an attempt to remove a VRF Selection entry that does not exist
D) an attempt to configure a VRF Selection table that does not exist
A) the entry of an inconsistent IP address and mask for VRF Selection
B) an attempt to configure a VRF instance on an interface that already has VRF Selection configured
C) an attempt to remove a VRF Selection entry that does not exist
D) an attempt to configure a VRF Selection table that does not exist

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
5
While troubleshooting EoMPLS configuration problems, which three parameters should an engineer match between the two ends of the pseudowire configurations? (Choose three.)
A) VLAN name
B) Xconnect group name
C) EFP subinterface number
D) pseudowire ID
E) MTU size
F) control word usage
A) VLAN name
B) Xconnect group name
C) EFP subinterface number
D) pseudowire ID
E) MTU size
F) control word usage

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
6
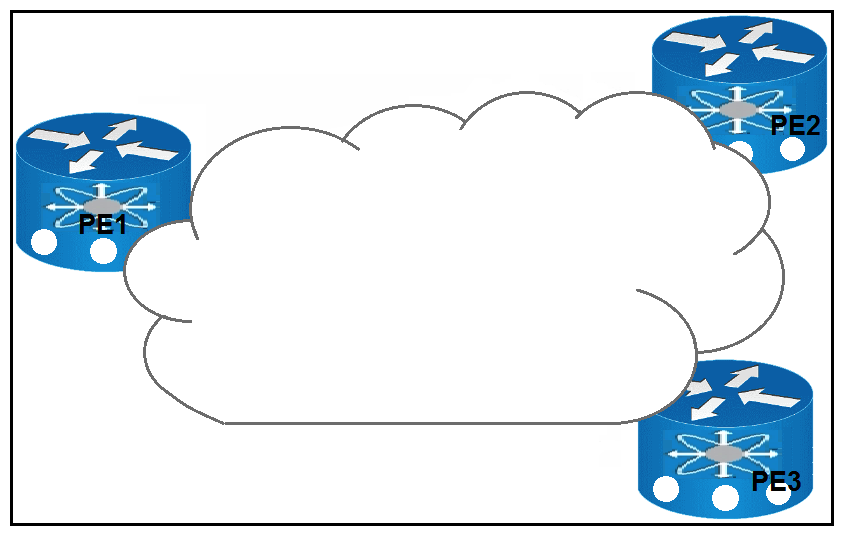 Refer to the exhibit. Which result occurs when PE1 learns a new MAC address and all three PEs are enabled with EVPN native?
Refer to the exhibit. Which result occurs when PE1 learns a new MAC address and all three PEs are enabled with EVPN native?A) A system notification is sent to the network administrator that triggers the manual configuration of the new MAC address on PE2 and PE3.
B) The new MAC address is sent by BGP to PE2 and PE3 as a Type 2 BGP route.
C) The MAC address is entered into the CAM table and is classified for use on the native VLAN
D) The MAC address is entered into the CAM table only if it is learned on the native VLAN.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
7
In a typical service provider environment, which two tools are used to help scale PE router connectivity requirements? (Choose two.)
A) route reflectors
B) VPNv4 address family
C) originator ID
D) cluster ID
E) confederations
A) route reflectors
B) VPNv4 address family
C) originator ID
D) cluster ID
E) confederations

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
8
An engineer is investigating an MPLS LDP issue. Which command should an engineer use on a Cisco IOS XE device to display the contents of the LFIB?
A) show mpls forwarding-table
B) show mpls ldp neighbors
C) show mpls ldp labels
D) show mpls ldp bindings
A) show mpls forwarding-table
B) show mpls ldp neighbors
C) show mpls ldp labels
D) show mpls ldp bindings

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
9
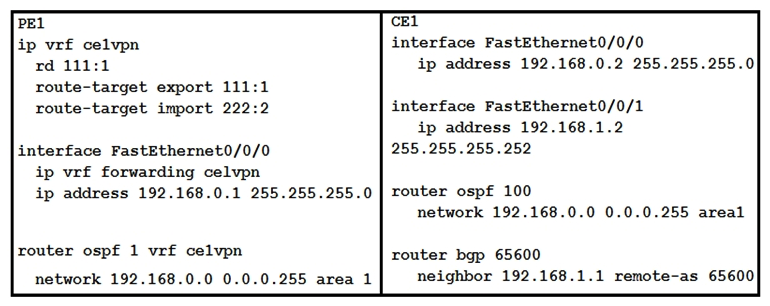 Refer to the exhibit. If the two devices are operating normally, which two conclusions can you draw from this configuration? (Choose two.)
Refer to the exhibit. If the two devices are operating normally, which two conclusions can you draw from this configuration? (Choose two.)A) CE1 must use OSPF to establish a neighbor relationship with PE1.
B) PE1 labels the routes it learns from CE1 with the route-target 222:2 and shares them with its VPNv4 peers.
C) PE1 labels the routes it learns from CE1 with the route-target 111:1 and shares them with its VPNv4 peers.
D) The PE-CE routes between the devices are being exchanged by OSPF
E) CE1 is supporting CSC.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
10
While troubleshooting an AToM L2VPN service, a network consultant notices that the AC Layer 2 encapsulations are different. Which action should the consultant take in order to make the MPLS L2VPN work?
A) tag-rewrite on the ingress and egress PE router
B) interworking IP configuration on the last PE router before label disposition
C) nonrouted interworking setup to properly translate only the Layer 2 information from the AC
D) interworking IP configuration on both the AC terminations on the PEs
A) tag-rewrite on the ingress and egress PE router
B) interworking IP configuration on the last PE router before label disposition
C) nonrouted interworking setup to properly translate only the Layer 2 information from the AC
D) interworking IP configuration on both the AC terminations on the PEs

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
11
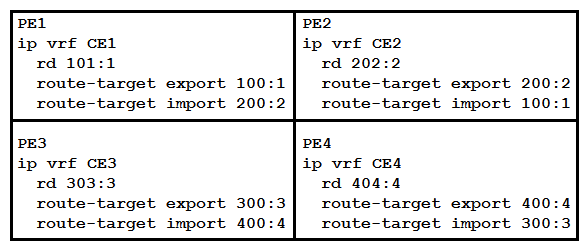 Refer to the exhibit. A network engineer has been called to configure the four PE devices in order to enable full communication among the four CE devices connected to them. While starting to configure, he experienced a connectivity issue. Which two tasks should the engineer perform in order to begin the process correctly? (Choose two.)
Refer to the exhibit. A network engineer has been called to configure the four PE devices in order to enable full communication among the four CE devices connected to them. While starting to configure, he experienced a connectivity issue. Which two tasks should the engineer perform in order to begin the process correctly? (Choose two.)A) Configure PE3 to export route-targets 100:1 and 200:2.
B) Configure PE3 to import route-targets 100:1 and 200:2.
C) Configure PE4 to import route-targets 101:1 and 202:2.
D) Configure PE2 to export route-targets 300:3 and 400:4.
E) Configure PE1 to import route-targets 300:3 and 400:4.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
12
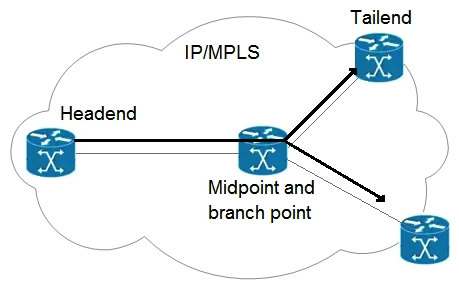 Refer to the exhibit. An engineer is implementing an MPLS P2MP TE solution. Which type of router can serve as the midpoint router and the tailend router in this P2MP TE network implementation?
Refer to the exhibit. An engineer is implementing an MPLS P2MP TE solution. Which type of router can serve as the midpoint router and the tailend router in this P2MP TE network implementation?A) headend
B) source
C) transit
D) bud

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
13
Which two BGP attributes prevent loops in a route reflector environment? (Choose two.)
A) cluster ID
B) local preference
C) origin
D) originator ID
E) AS_PATH
A) cluster ID
B) local preference
C) origin
D) originator ID
E) AS_PATH

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
14
The CTO of a company requires the support of a network consultant to deliver an MPLS solution without resigning to a certain degree of redundancy and scalability. Which solution effectively scales to hundreds or thousands of sites?
A) L2VPN with the broadcast traffic processed at the ingress PE.
B) L3VPN with direct LSP connectivity between all PEs.
C) L2VPN by encapsulating multiple frame formats with interworking.
D) L3VPN using a hierarchical topology of N-PEs and U-PEs.
A) L2VPN with the broadcast traffic processed at the ingress PE.
B) L3VPN with direct LSP connectivity between all PEs.
C) L2VPN by encapsulating multiple frame formats with interworking.
D) L3VPN using a hierarchical topology of N-PEs and U-PEs.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
15
A network architect is troubleshooting the L2TPv3 tunneling security due to the untrusted nature of the underlaying network. Which two L2TPv3 features does the architect deploy to address the ongoing issues? (Choose two.)
A) TCP MD5 authentication
B) control message hashing
C) CHAP authentication
D) control message rate limiting
E) asymmetric mutual authentication with PSK
A) TCP MD5 authentication
B) control message hashing
C) CHAP authentication
D) control message rate limiting
E) asymmetric mutual authentication with PSK

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
16
Which two frames can be configured on an Ethernet flow point? (Choose two.)
A) of a specific VLAN
B) with different type of service values
C) with identical type of service value
D) with different class of service values
E) with no tags
A) of a specific VLAN
B) with different type of service values
C) with identical type of service value
D) with different class of service values
E) with no tags

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
17
An engineer needs to improve MPLS network management by implementing a set of tools to support the NOC engineers in troubleshooting network failures. Which feature should the engineer implement to check the connectivity of the MPLS LSP between the ingress and egress PE routers?
A) MPLS OAM
B) MPLS-TP
C) LDP autodiscovery
D) extended ping
A) MPLS OAM
B) MPLS-TP
C) LDP autodiscovery
D) extended ping

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
18
Which two statements describe primary differences between MPLS Layer 2 and Layer 3 VPNs? (Choose two.)
A) Layer 2 VPNs use IPsec tunneling, but Layer 3 VPNs use L2TPv3 tunneling.
B) Layer 2 VPNs use AToM, but Layer 3 VPNs use MPLS/BGP.
C) Layer 2 VPNs use BGP, but Layer 3 VPNs use VPLS.
D) Layer 2 VPNs use L2TPv3 tunneling, but Layer 3 VPNs use GRE tunneling.
E) Layer 2 VPNs use IPsec tunneling, but Layer 3 VPNs use pseudowires to provide tunneling.
A) Layer 2 VPNs use IPsec tunneling, but Layer 3 VPNs use L2TPv3 tunneling.
B) Layer 2 VPNs use AToM, but Layer 3 VPNs use MPLS/BGP.
C) Layer 2 VPNs use BGP, but Layer 3 VPNs use VPLS.
D) Layer 2 VPNs use L2TPv3 tunneling, but Layer 3 VPNs use GRE tunneling.
E) Layer 2 VPNs use IPsec tunneling, but Layer 3 VPNs use pseudowires to provide tunneling.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
19
You are troubleshooting ARP connectivity issues for an Ethernet interface on an IOS XR network that runs IS-IS. You verify that the IGP protocol is running, but an ARP entry has not yet been created. Which action should you take?
A) debug ping packets
B) debug ARP
C) ping the connected neighbor
D) verify the RIB table routes
A) debug ping packets
B) debug ARP
C) ping the connected neighbor
D) verify the RIB table routes

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
20
An ISP provides a major client MPLS VPN for managed services. The MPLS engineering team needs to use the advanced VPN feature of selective VRF import so that only specific prefixes are present in the required VPNs. Which aspect of this feature must the team consider?
A) A route must pass the import route map first and then the route target import filter.
B) The routers that are imported in the VRF can be BGP and IGP routes, so other match conditions in the route map, besides communities, can be used.
C) The import-map command is applied under the PE interface that connects to the CE router. The import-map command is applied under the PE interface that connects to the CE router.
D) A route is imported into the VRF only when at least one RT that is attached to the route matches one RT that is configured in the VRF and the route is permitted by the import route map.
A) A route must pass the import route map first and then the route target import filter.
B) The routers that are imported in the VRF can be BGP and IGP routes, so other match conditions in the route map, besides communities, can be used.
C) The import-map command is applied under the PE interface that connects to the CE router. The import-map command is applied under the PE interface that connects to the CE router.
D) A route is imported into the VRF only when at least one RT that is attached to the route matches one RT that is configured in the VRF and the route is permitted by the import route map.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
21
In an Ethernet Virtual Circuit environment, which restriction do bridge domains have when STP is running?
A) The STP mode must be RSTP or PVST+
B) Bridge domains must be mapped to a different VLAN.
C) The STP mode must be MSTP
D) Bridge domains must belong to different MST instances.
A) The STP mode must be RSTP or PVST+
B) Bridge domains must be mapped to a different VLAN.
C) The STP mode must be MSTP
D) Bridge domains must belong to different MST instances.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
22
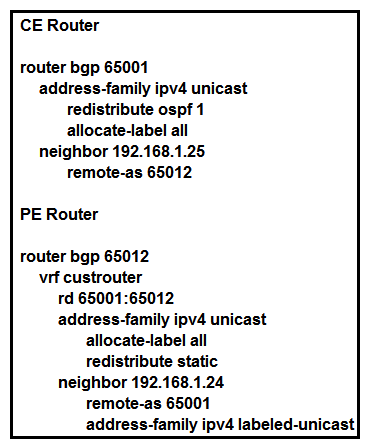 Refer to the exhibit. The CE router has established a BGP peering with the PE router, and the CE will use the core infrastructure of the PE as a backbone carrier to support CSC. Which additional task can you perform to complete the configuration?
Refer to the exhibit. The CE router has established a BGP peering with the PE router, and the CE will use the core infrastructure of the PE as a backbone carrier to support CSC. Which additional task can you perform to complete the configuration?A) Configure static routing on the CE router.
B) Configure the address-family ipv4 labeled-unicast command under the neighbor configuration of the CE router for the PE. Configure the address-family ipv4 labeled-unicast command under the neighbor configuration of the CE router for the PE.
C) Change the rd value to 65001:65001 under the VRF section of the PE router. Change the rd value to 65001:65001 under the VRF section of the PE router.
D) Configure OSPF on the PE router.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
23
An engineer is troubleshooting AToM on an IOS XE router and receives an error when creating the xconnect. Which command does he need to complete to create the xconnect in AToM?
A) encapsulation mpls
B) encapsulation 12tpv3
C) protocol 12tpv3
D) protocol none
A) encapsulation mpls
B) encapsulation 12tpv3
C) protocol 12tpv3
D) protocol none

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
24
Which two statements about MPLS L3 VPN RDs are true? (Choose two.)
A) They enable EIGRP to use address families to separate traffic between IPv4 and VPNv4.
B) They are represented as 32-bit values
C) They are represented as 64-bit values.
D) They enable OSPF to import and export routes into the global routing table of a router.
E) They allow BGP to uniquely identify duplicate routes.
A) They enable EIGRP to use address families to separate traffic between IPv4 and VPNv4.
B) They are represented as 32-bit values
C) They are represented as 64-bit values.
D) They enable OSPF to import and export routes into the global routing table of a router.
E) They allow BGP to uniquely identify duplicate routes.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
25
What is the primary function of a VRF on a router?
A) It enables the router to support multiple separate routing tables, which allows the device to handle overlapping IP addresses.
B) It enables a router to run BGP and a distance vector routing protocol at the same time, which allows it to serve as a VPN endpoint between remote sites.
C) It enables a router to configure VLANs locally, which provides segregation between networks.
D) It enables the router to provide faster switching through the network by using labels to identify the input and output interfaces for neighbor routers.
A) It enables the router to support multiple separate routing tables, which allows the device to handle overlapping IP addresses.
B) It enables a router to run BGP and a distance vector routing protocol at the same time, which allows it to serve as a VPN endpoint between remote sites.
C) It enables a router to configure VLANs locally, which provides segregation between networks.
D) It enables the router to provide faster switching through the network by using labels to identify the input and output interfaces for neighbor routers.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
26
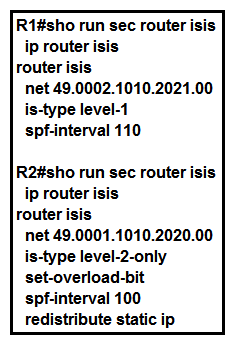 Refer to the exhibit. A technician is troubleshooting a connectivity issue and notices that there is no IS-IS adjacency between R1 and R2. What can the technician change to bring the IS-IS adjacency up?
Refer to the exhibit. A technician is troubleshooting a connectivity issue and notices that there is no IS-IS adjacency between R1 and R2. What can the technician change to bring the IS-IS adjacency up?A) Change R2's net address to be in the same area as R1.
B) Change R1's is-type to level-2-only
C) Change R1's net address to be in the same area as R2.
D) Change R2's configuration to no longer set the overload bit.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
27
In Layer 3 MPLS VPN implementations, if some of the VPNv4 routes on one PE router do not appear on another PE router, what could be the problem?
A) RD mismatch between the PE routers
B) RT export and import configuration errors
C) VRF name mismatch between the PE routers
D) RD export and import configuration errors
A) RD mismatch between the PE routers
B) RT export and import configuration errors
C) VRF name mismatch between the PE routers
D) RD export and import configuration errors

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
28
An engineer is investigating an EVPN traffic flow issue. Which type of traffic should the engineer allow in an EVPN Tree Service in order to fix this issue?
A) known unicast from a leaf to another leaf
B) unknown unicast from a leaf to another leaf
C) multicast from a leaf to another leaf
D) known unicast from a root to another root
A) known unicast from a leaf to another leaf
B) unknown unicast from a leaf to another leaf
C) multicast from a leaf to another leaf
D) known unicast from a root to another root

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
29
Which mechanism reduces the network flooding caused by host ARP learning behavior?
A) ARP suppression
B) storm control
C) root guard
D) BPDU guard
A) ARP suppression
B) storm control
C) root guard
D) BPDU guard

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
30
What must match in the EVPN and L2VPN configuration mode when configuring EVPN native in a router?
A) interface
B) address family
C) bridge domain
D) EVI
A) interface
B) address family
C) bridge domain
D) EVI

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
31
 Refer to the exhibit. Which statement about this command is true?
Refer to the exhibit. Which statement about this command is true?A) It must be configured on each PE router to enable the PE routers to receive multicast traffic for this particular MVRF.
B) It is used to set the designated router on a link using PIM-SM.
C) It must be configured on the PE and CE router to enable MP-BGP to send labels for CSC.
D) It is used to set the router that will server as the root bridge for STP.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
32
Which statement describes the no bgp default route-target filter command?
A) Prefixes that are received with route targets and distinguisher are accepted.
B) Prefixes that are received with route targets and distinguisher are not accepted.
C) Prefixes that are received with route targets that are not imported at the PE are not accepted.
D) Prefixes that are received with route targets that are not imported at the PE are accepted.
A) Prefixes that are received with route targets and distinguisher are accepted.
B) Prefixes that are received with route targets and distinguisher are not accepted.
C) Prefixes that are received with route targets that are not imported at the PE are not accepted.
D) Prefixes that are received with route targets that are not imported at the PE are accepted.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
33
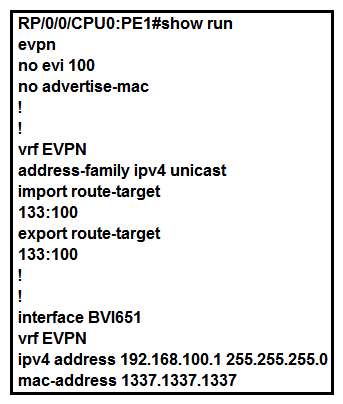 Refer to the exhibit. A network operator is implementing EVPN IRB on PE1. Which two command placements enable the advertisement of Type 2 routes and what information do Type 2 routes contain? (Choose two.)
Refer to the exhibit. A network operator is implementing EVPN IRB on PE1. Which two command placements enable the advertisement of Type 2 routes and what information do Type 2 routes contain? (Choose two.)A) The operator adds in "host-routing" under the VRF EVPN.
B) Type 2 routes contain MAC/IP information.
C) Type 2 routes contain Ethernet Auto-Discovery information.
D) The operator adds in "host-routing" under the BVI651 interface.
E) Type 2 routes contain inclusive source-specific multicast route information.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
34
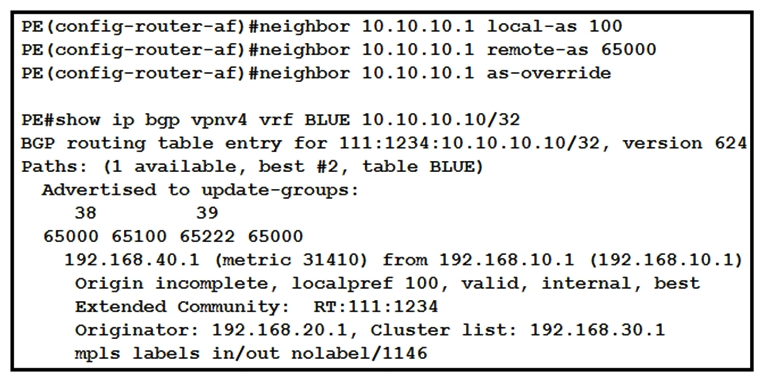 Refer to the exhibit. While provisioning a new BGP session between the PE and CE router, you issue the as-override command. Which statement describes modification of the prefix before being sent to the CE router (10.10.10.1)?
Refer to the exhibit. While provisioning a new BGP session between the PE and CE router, you issue the as-override command. Which statement describes modification of the prefix before being sent to the CE router (10.10.10.1)?A) The fourth AS changes, but no other autonomous systems change.
B) The first and fourth autonomous systems change.
C) The second and third autonomous systems change.
D) The first AS changes, but no other autonomous systems change.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
35
The network engineering group of a large ISP needs to harden the management plane of its Cisco 9000 Series ASRs. While addressing IPv6 ICMP issues, they realized they have to limit the rate at which IPv6 ICMP error messages are sent out on the network. Which command do they need to apply?
A) icmp ipv6 rate-limit unreachable 1000
B) ipv6 rate-limit 1000
C) icmp ipv4 rate-limit unreachable 1000
D) ipv6 icmp error-interval 50 20
A) icmp ipv6 rate-limit unreachable 1000
B) ipv6 rate-limit 1000
C) icmp ipv4 rate-limit unreachable 1000
D) ipv6 icmp error-interval 50 20

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
36
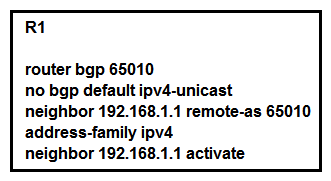 Refer to the exhibit. Which statement describes the result of this BGP configuration?
Refer to the exhibit. Which statement describes the result of this BGP configuration?A) R1 operates using IPv4 and VPNv4 address families.
B) R1 operates on IPv6 only because the bgp default ipv4-unicast command is missing. R1 operates on IPv6 only because the bgp default ipv4-unicast command is missing.
C) R1 establishes a VPNv4 eBGP relationship with neighbor 192.168.1.1.
D) R1 establishes an iBGP relationship with peer 192.168.1.1.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
37
Which tool identifies the point of failure in a P2MP LSP from the ingress LSR?
A) Jitter TLV
B) SPAN
C) P2MP traceroute
D) P2MP ping
A) Jitter TLV
B) SPAN
C) P2MP traceroute
D) P2MP ping

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
38
While implementing Layer 3 MPLS VPN, which feature should an engineer use at the PEs to transform the customer IPv4 prefixes into a unique 96-bit prefix?
A) RT
B) VC ID
C) RD
D) PW ID
A) RT
B) VC ID
C) RD
D) PW ID

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
39
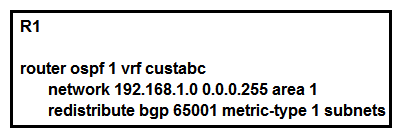 Refer to the exhibit. Which statement describes the result of this configuration?
Refer to the exhibit. Which statement describes the result of this configuration?A) R1 redistributes BGP routes into the OSPF process of VRF custabc as E1 routes.
B) R1 redistributes BGP routes into the OSPF process of VRF custabc as E2 routes.
C) R1 mutually redistributes routes between BGP 65001 and the OSPF process of VRF custabc.
D) R1 redistributes BGP routes into the OSPF process of VRF custabc as OIA routes.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
40
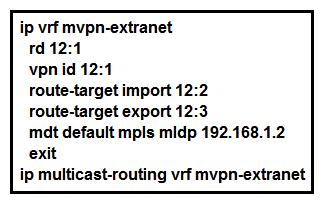 Refer to the exhibit. What is the effect of this configuration?
Refer to the exhibit. What is the effect of this configuration?A) The mroute table is cleared.
B) Router 1 accepts multicast routes with a tag of 12:1
C) A Cisco MPLS TE tunnel is generated with 192.168.1.2 as the source IP address of router 1.
D) An LSP virtual interface tunnel is created.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
41
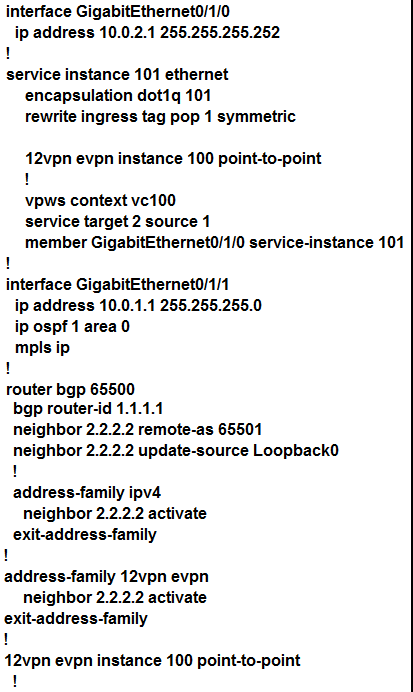 Refer to the exhibit. An engineer is trying to configure an EVPN VWPS. What is the issue with this configuration?
Refer to the exhibit. An engineer is trying to configure an EVPN VWPS. What is the issue with this configuration?A) The member in the VPWS context should be the PE-facing interface.
B) The 12vpn evpn command should be instance 101. The 12vpn evpn command should be instance 101.
C) Interface GigabitEthernet0/1/0 should not have any IP address.
D) The service instance and the EVPN instance are different.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
42
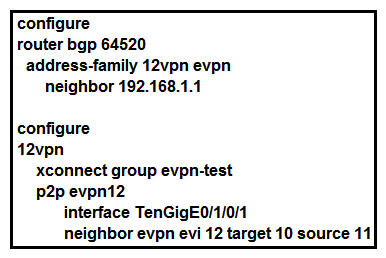 Refer to the exhibit. Which effect of this configuration is true?
Refer to the exhibit. Which effect of this configuration is true?A) It configures VPWS multihomed.
B) It configures VPWS single homed.
C) It configures an IPv4 peering with 192.168.1.1
D) It configures MPLS traffic engineering.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
43
With Layer 3 MPLS VPN implementations on Cisco IOS XR PE routers, an interface is assigned to a VRF using the vrf command in which configuration mode?
A) RP/0/RP0/CPU0:PE(config-bgp)#
B) RP/0/RP0/CPU0:PE(config-if)#
C) RP/0/RP0/CPU0:PE(config-bgp-af)#
D) RP/0/RP0/CPU0:PE(config-vrf)#
A) RP/0/RP0/CPU0:PE(config-bgp)#
B) RP/0/RP0/CPU0:PE(config-if)#
C) RP/0/RP0/CPU0:PE(config-bgp-af)#
D) RP/0/RP0/CPU0:PE(config-vrf)#

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
44
Which optional information can be included with an IPv6 ping to support the troubleshooting process?
A) IPv4 IP address
B) source MAC address
C) destination MAC address
D) IPv6 hostname
A) IPv4 IP address
B) source MAC address
C) destination MAC address
D) IPv6 hostname

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
45
You are writing the requirements for an MPLS L3VPN environment that uses MP-BGP between PE routers. In this environment, route targets and route distinguishers need to be advertised between the PE routers. Which three operations meet these requirements? (Choose three.)
A) mandatory creation of PE-to-PE BGP sessions between the outgoing interface IP addresses
B) advertisement of standard communities, enabled on the PE-to-PE BGP neighbors
C) creation of PE-to-PE BGP sessions between loopback IP addresses
D) full mesh of IBGP sessions
E) full mesh of EBGP sessions and partial mesh of IBGP sessions
F) advertisement of extended communities, enabled on the PE-to-PE BGP neighbors
A) mandatory creation of PE-to-PE BGP sessions between the outgoing interface IP addresses
B) advertisement of standard communities, enabled on the PE-to-PE BGP neighbors
C) creation of PE-to-PE BGP sessions between loopback IP addresses
D) full mesh of IBGP sessions
E) full mesh of EBGP sessions and partial mesh of IBGP sessions
F) advertisement of extended communities, enabled on the PE-to-PE BGP neighbors

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
46
Which BGP feature causes to replace the AS number of originating router with the AS number of the sending router?
A) route reflectors
B) route dampening
C) confederations
D) AS override
A) route reflectors
B) route dampening
C) confederations
D) AS override

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
47
What do EVPN single-active and all-active have in common?
A) They are default gateway redundancy options.
B) They are multihoming mechanisms used for CE devices.
C) They are used to provide single connection from a CE device to a service provider.
D) They are both roles that a designated router can take when MPLS is used with EVPN.
A) They are default gateway redundancy options.
B) They are multihoming mechanisms used for CE devices.
C) They are used to provide single connection from a CE device to a service provider.
D) They are both roles that a designated router can take when MPLS is used with EVPN.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
48
Which is the primary function of a MPLS L3 VPN route target?
A) It imports and exports identified routes into selected VRFs.
B) It uniquely identifies NLRIs that have the same numeric value.
C) It imports the external routes it identifies into VRFs that support Internet traffic
D) It supports QoS by classifying traffic by file type when it applies MPLS EXP bits to each packet.
A) It imports and exports identified routes into selected VRFs.
B) It uniquely identifies NLRIs that have the same numeric value.
C) It imports the external routes it identifies into VRFs that support Internet traffic
D) It supports QoS by classifying traffic by file type when it applies MPLS EXP bits to each packet.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
49
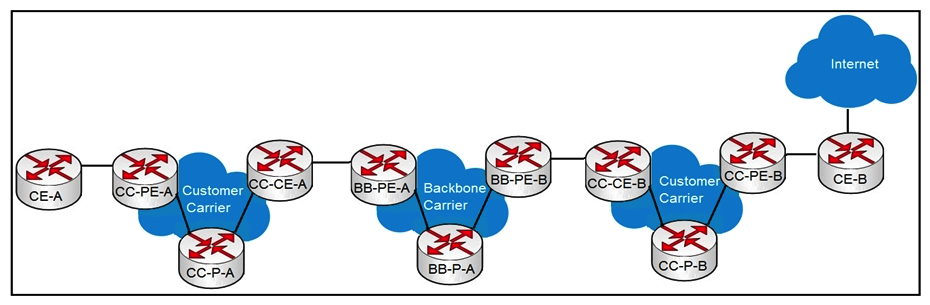 Refer to the exhibit. A customer carrier running MPLS VPN wants to utilize a backbone carrier to forward traffic and exchange VPNv4 prefixes between the two customer carrier networks depicted. Which two sets of routers must establish MP-iBGP sessions? (Choose two.)
Refer to the exhibit. A customer carrier running MPLS VPN wants to utilize a backbone carrier to forward traffic and exchange VPNv4 prefixes between the two customer carrier networks depicted. Which two sets of routers must establish MP-iBGP sessions? (Choose two.)A) BB-PE-A and CC-PE-B
B) CC-PE-A and CC-PE-B
C) BB-PE-A and BB-PE-B
D) CC-PE-A and BB-PE-A
E) BB-PE-A and BB-P-A
F) CC-PE-A and CC-P-A

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck


