Deck 7: Nokia Quality of Service
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/24
Play
Full screen (f)
Deck 7: Nokia Quality of Service
1
Which of the following 5GS reference points is used for control plane signaling?
A) N3
B) N4
C) N6
D) N9
A) N3
B) N4
C) N6
D) N9
N3
2
Which of the following is NOT an EDCE5 core enhancement to support Option 3X?
A) Support for higher data rates for EPC interfaces.
B) MME selection of appropriate gateways capable of supporting NR.
C) PGW selection of appropriate PCRF that supports 5G policies.
D) Controlled UE access to NR based upon subscription information.
A) Support for higher data rates for EPC interfaces.
B) MME selection of appropriate gateways capable of supporting NR.
C) PGW selection of appropriate PCRF that supports 5G policies.
D) Controlled UE access to NR based upon subscription information.
Support for higher data rates for EPC interfaces.
3
Which of the following best describes the function of a PDU session flow classifier?
A) An SMF that dynamically inserts and removes uplink classifiers (UL CL) at the UPFs.
B) An SMF that dynamically inserts and removes UL CL at the UE.
C) A UPF that terminates the N6 interface towards the data network.
D) A UPF that filters uplink traffic according to UL CL rules provided by the SMF.
A) An SMF that dynamically inserts and removes uplink classifiers (UL CL) at the UPFs.
B) An SMF that dynamically inserts and removes UL CL at the UE.
C) A UPF that terminates the N6 interface towards the data network.
D) A UPF that filters uplink traffic according to UL CL rules provided by the SMF.
An SMF that dynamically inserts and removes uplink classifiers (UL CL) at the UPFs.
4
Which of the following statements about the downlink user plane data flow in Option 3X is FALSE?
A) Data packets of bearers that do not use dual connectivity are sent from EPC to UE through eNB.
B) When NR coverage is good, data packets of bearers that use dual connectivity are sent from EPC to UE using secondary cell group bearers.
C) When NR coverage degrades, the gNB decides when to use split bearers and send some of the packets received from the core through eNB.
D) When NR coverage is poor, data packets of bearers that use dual connectivity are sent to the UE through eNB.
A) Data packets of bearers that do not use dual connectivity are sent from EPC to UE through eNB.
B) When NR coverage is good, data packets of bearers that use dual connectivity are sent from EPC to UE using secondary cell group bearers.
C) When NR coverage degrades, the gNB decides when to use split bearers and send some of the packets received from the core through eNB.
D) When NR coverage is poor, data packets of bearers that use dual connectivity are sent to the UE through eNB.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
5
An AMF needs to know when an SMF deregisters with the NRF. Which of the following NRF APIs should the AMF use?
A) Nnrf_NFManagement_NFUpdate Request
B) Nnrf_NFDiscovery_NFDiscover Request
C) Nnrf_NFManagement_NFStatusSubscribe Request
D) Nnrf_NFManagement_NFDeregister Request
A) Nnrf_NFManagement_NFUpdate Request
B) Nnrf_NFDiscovery_NFDiscover Request
C) Nnrf_NFManagement_NFStatusSubscribe Request
D) Nnrf_NFManagement_NFDeregister Request

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
6
Which of the following statements about Option 3X dual connectivity is FALSE?
A) VoLTE traffic is handled by the LTE network.
B) Dual connectivity is used for high throughput services such as eMBB.
C) When NR radio quality becomes sub-optimal, gNB decides to split the bearer.
D) Both eNB and gNB are connected with S1-U interfaces to SGW.
A) VoLTE traffic is handled by the LTE network.
B) Dual connectivity is used for high throughput services such as eMBB.
C) When NR radio quality becomes sub-optimal, gNB decides to split the bearer.
D) Both eNB and gNB are connected with S1-U interfaces to SGW.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
7
Which 5GS network function allows UE connectivity to 5GC through non-3GPP access networks?
A) SEPP
B) N3IWF
C) NWDAF
D) NEF
A) SEPP
B) N3IWF
C) NWDAF
D) NEF

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
8
A UE has a PDU session established using slice 1. The operator removes slice 1 from the UE subscription data stored in UDM. Which of the following actions is NOT performed as a result?
A) UDM notifies the serving AMF about the UE subscription data modification.
B) AMF initiates the UE configuration update procedure.
C) AMF requests the UE to release the established PDU session.
D) UE updates its slicing information with the data received from AMF.
A) UDM notifies the serving AMF about the UE subscription data modification.
B) AMF initiates the UE configuration update procedure.
C) AMF requests the UE to release the established PDU session.
D) UE updates its slicing information with the data received from AMF.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
9
A connected UE moves from 5GS to EPS using the inter-system handover procedure with N26 interface. Which of the following actions is NOT performed?
A) Source gNB sends an NGAP Handover Required message to source AMF with handover type set to "NRtoLTE".
B) Source AMF obtains session management contexts stored in UDM+HSS for each PDU session that supports interworking.
C) Source AMF sends a Forward Relocation Request message to the target MME and provides session management contexts.
D) Indirect downlink data forwarding paths are established from source gNB to target eNodeB.
A) Source gNB sends an NGAP Handover Required message to source AMF with handover type set to "NRtoLTE".
B) Source AMF obtains session management contexts stored in UDM+HSS for each PDU session that supports interworking.
C) Source AMF sends a Forward Relocation Request message to the target MME and provides session management contexts.
D) Indirect downlink data forwarding paths are established from source gNB to target eNodeB.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following elements is NOT used in the 5G non-standalone (NSA) deployment Option 3?
A) Evolved Packet Core
B) ng-eNB
C) gNB
D) Dual Radio UE
A) Evolved Packet Core
B) ng-eNB
C) gNB
D) Dual Radio UE

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
11
Which Nokia product is used for the AMF in 5GS?
A) Cloud Mobility Manager
B) Cloud Mobile Gateway
C) Network Resource Discovery
D) Smart Plan Suite
A) Cloud Mobility Manager
B) Cloud Mobile Gateway
C) Network Resource Discovery
D) Smart Plan Suite

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
12
The exhibit below displays a packet capture of the PFCP Session Modification Request message sent during a PDU Session Establishments procedure. What do the highlighted TEID and IP Address refer to? 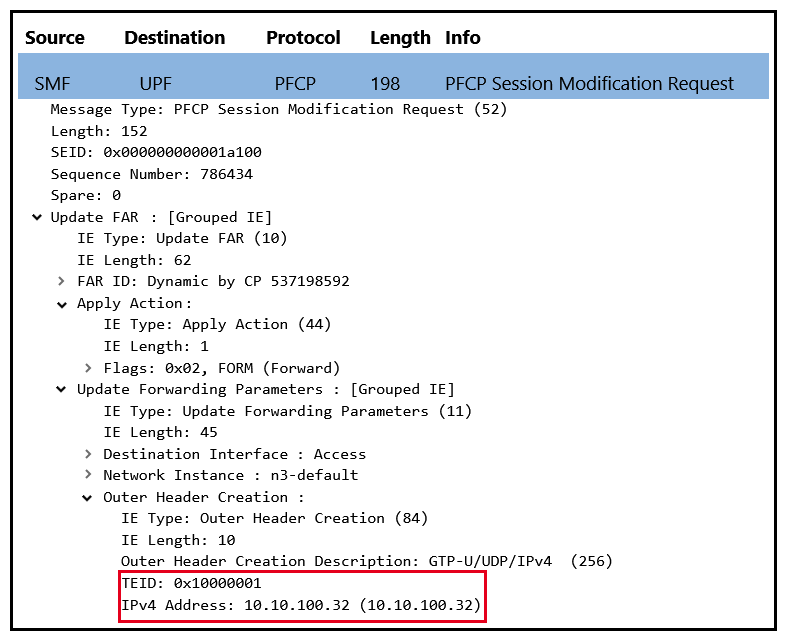
A) The N3 TEID allocated by gNB and the gNB IP address.
B) The N3 TEID allocated by UPF and the UPF IP address.
C) The N3 TEID allocated by SMF and the SMF IP address.
D) The N3 TEID allocated by SMF and the UPF IP address.

A) The N3 TEID allocated by gNB and the gNB IP address.
B) The N3 TEID allocated by UPF and the UPF IP address.
C) The N3 TEID allocated by SMF and the SMF IP address.
D) The N3 TEID allocated by SMF and the UPF IP address.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
13
A UE is handed off from gNB1 to gNB2 using an N2-based handover procedure. The source I-UPF is to be relocated and an indirect data forwarding path is to be used. Which of the following statements is TRUE?
A) AMF decides that an in indirect data forwarding path is required and sends an indication to SMF.
B) gNB2 tunnel info is allocated for the indirect forwarding path and is included in the Handover Request Ack message sent to AMF.
C) Target I-UPF tunnel info is allocated for the indirect forwarding path and is provided to the UPF PSA.
D) UPF PSA tunnel info is allocated for the indirect forwarding path and is provided to the source I-UPF.
A) AMF decides that an in indirect data forwarding path is required and sends an indication to SMF.
B) gNB2 tunnel info is allocated for the indirect forwarding path and is included in the Handover Request Ack message sent to AMF.
C) Target I-UPF tunnel info is allocated for the indirect forwarding path and is provided to the UPF PSA.
D) UPF PSA tunnel info is allocated for the indirect forwarding path and is provided to the source I-UPF.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following statements about the 5G-globally unique temporary identity (5G-GUTI) is FALSE?
A) The 5G-GUTI provides a clear identification of the UE without revealing the UE permanent identity.
B) The 5G-GUTI contains an element identifying the AMF which allocated it.
C) The 5G network pages an idle UE using its 5G-GUTI.
D) During the initial registration procedure, the AMF allocates a 5G-GUTI and sends it to the UE.
A) The 5G-GUTI provides a clear identification of the UE without revealing the UE permanent identity.
B) The 5G-GUTI contains an element identifying the AMF which allocated it.
C) The 5G network pages an idle UE using its 5G-GUTI.
D) During the initial registration procedure, the AMF allocates a 5G-GUTI and sends it to the UE.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
15
When an idle UE moves from EPS to 5GS, which procedure is performed?
A) Registration
B) Tracking Area Update
C) Initial Attach
D) Service Request
A) Registration
B) Tracking Area Update
C) Initial Attach
D) Service Request

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following statements regarding the 5G security components is FALSE?
A) The authentication credential repository and processing function (ARPF) selects the authentication method to use for the UE.
B) The authentication server function (AUSF) handles authentication requests for both 3GPP and non-3GPP access.
C) The security anchor function (SEAF) makes the final decision on UE authentication.
D) The security identifier de-concealing function (SIDF) decrypts the UE's SUCI to obtain its corresponding SUPI.
A) The authentication credential repository and processing function (ARPF) selects the authentication method to use for the UE.
B) The authentication server function (AUSF) handles authentication requests for both 3GPP and non-3GPP access.
C) The security anchor function (SEAF) makes the final decision on UE authentication.
D) The security identifier de-concealing function (SIDF) decrypts the UE's SUCI to obtain its corresponding SUPI.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
17
Which of the following statements about 5G QoS Flows is FALSE?
A) A QoS Flow is the finest granularity of QoS differentiation within a PDU session.
B) A PDU session has one or more QoS Flows.
C) All QoS Flows of a PDU session are served by a single N3 GTP-U tunnel.
D) Each QoS Flow is served by a dedicated data radio bearer.
A) A QoS Flow is the finest granularity of QoS differentiation within a PDU session.
B) A PDU session has one or more QoS Flows.
C) All QoS Flows of a PDU session are served by a single N3 GTP-U tunnel.
D) Each QoS Flow is served by a dedicated data radio bearer.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
18
Which of the following does NOT apply to an idle UE in MICO mode?
A) The UE performs registration updates.
B) The UE connects to the network to send uplink data.
C) Power and signaling efficiency is optimized for the UE.
D) The UE listens and responds to paging.
A) The UE performs registration updates.
B) The UE connects to the network to send uplink data.
C) Power and signaling efficiency is optimized for the UE.
D) The UE listens and responds to paging.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
19
Which of the following actions is NOT performed during an Xn-based Inter NG-RAN Handover with I-UPF Insertion procedure?
A) AMF determines that a new I-UPF needs to be added for a PDU session.
B) SMF provides N3 tunnel info of I-UPF to target gNB via AMF.
C) SMF provides N9 tunnel info of UPF PSA to I-UPF.
D) SMF provides N9 tunnel info of I-UPF to UPF PSA.
A) AMF determines that a new I-UPF needs to be added for a PDU session.
B) SMF provides N3 tunnel info of I-UPF to target gNB via AMF.
C) SMF provides N9 tunnel info of UPF PSA to I-UPF.
D) SMF provides N9 tunnel info of I-UPF to UPF PSA.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
20
NF A wants to explicitly subscribe for event notifications at NF B. Which of the following actions regarding this mechanism is FALSE?
A) NF A acts as a service consumer and NF B acts as a service producer.
B) NF A includes a subscription identifier in the request message sent to NF B.
C) NF A includes a callback URI in the request message sent to NF B.
D) NF A includes event filtering criteria in the request message sent to NF B.
A) NF A acts as a service consumer and NF B acts as a service producer.
B) NF A includes a subscription identifier in the request message sent to NF B.
C) NF A includes a callback URI in the request message sent to NF B.
D) NF A includes event filtering criteria in the request message sent to NF B.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
21
Which of the following is NOT an advantage of the 5GS service-based architecture?
A) Application programming interfaces (APIs) are used to invoke services.
B) Service-based interfaces are point-to-point.
C) The service-based architecture enables flexible addition of new network functions and services.
D) Service producers are not aware of service consumers.
A) Application programming interfaces (APIs) are used to invoke services.
B) Service-based interfaces are point-to-point.
C) The service-based architecture enables flexible addition of new network functions and services.
D) Service producers are not aware of service consumers.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
22
Which of the following statements about 5GS PDU sessions is FALSE?
A) A PDU session allows for the exchange of PDUs between UE and a data network.
B) A PDU session contains one single dedicated radio bearer and one or more N3 GTP-U tunnels.
C) A PDU session has one default QoS flow and can have multiple non-default QoS flows.
D) A PDU session has one or more UPFs acting as PDU session anchors.
A) A PDU session allows for the exchange of PDUs between UE and a data network.
B) A PDU session contains one single dedicated radio bearer and one or more N3 GTP-U tunnels.
C) A PDU session has one default QoS flow and can have multiple non-default QoS flows.
D) A PDU session has one or more UPFs acting as PDU session anchors.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following statements about the protection of service-based interfaces (SBIs) is FALSE?
A) The transport layer security (TLS) performs certification-based authentication, providing connection security between network functions within a PLMN.
B) The OAuth 2.0 framework is used to secure the communication between network functions within a PLMN at the network layer.
C) The network domain security/Internet protocol (NDS/IP) provides confidentiality and data integrity between network functions within a PLMN.
D) The security edge protection proxy (SEPP) handles the security of inter-domain SBIs and protects the interaction between network functions in different PLMNs.
A) The transport layer security (TLS) performs certification-based authentication, providing connection security between network functions within a PLMN.
B) The OAuth 2.0 framework is used to secure the communication between network functions within a PLMN at the network layer.
C) The network domain security/Internet protocol (NDS/IP) provides confidentiality and data integrity between network functions within a PLMN.
D) The security edge protection proxy (SEPP) handles the security of inter-domain SBIs and protects the interaction between network functions in different PLMNs.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following is an HTTP method used by an NF service consumer to create a new resource at an NF service producer when the resource URI is selected by the consumer?
A) POST
B) PUT
C) PATCH
D) UPDATE
A) POST
B) PUT
C) PATCH
D) UPDATE

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck


