Deck 22: HPE Sales Certified - Aruba Products and Solutions
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/36
Play
Full screen (f)
Deck 22: HPE Sales Certified - Aruba Products and Solutions
1
A customer is setting up Guest access with ClearPass. They are considering using 802.1X for both the Employee network and the Guest network. What are two issues the customer may encounter when deploying 802.1X with the Guest network? (Choose two.)
A) ClearPass will not be able to enforce individual Access Control policies.
B) difficult to maintain in an environment with a large number of transient guest users.
C) the lack of encryption during the authentication process.
D) Guests will not be able to be uniquely identified.
E) the high level of complexity for users to join the guest network.
A) ClearPass will not be able to enforce individual Access Control policies.
B) difficult to maintain in an environment with a large number of transient guest users.
C) the lack of encryption during the authentication process.
D) Guests will not be able to be uniquely identified.
E) the high level of complexity for users to join the guest network.
difficult to maintain in an environment with a large number of transient guest users.
the high level of complexity for users to join the guest network.
the high level of complexity for users to join the guest network.
2
Sponsorship has been enabled on the guest network. A guest user connects and completes the self-registration form indicating a valid sponsor. The guest then clicks submit . What is the current state of the guest account?
A) The guest account is created in an enabled state with the "Log In" button functional.
B) The guest account is created in disabled state, the "Log In" button will appear only after the sponsor approval process is completed.
C) The guest account is created in a disabled state with the "Log In" button grayed out.
D) The guest account is not yet created and remains in a disabled state. There is not "Log In" button yet displayed.
A) The guest account is created in an enabled state with the "Log In" button functional.
B) The guest account is created in disabled state, the "Log In" button will appear only after the sponsor approval process is completed.
C) The guest account is created in a disabled state with the "Log In" button grayed out.
D) The guest account is not yet created and remains in a disabled state. There is not "Log In" button yet displayed.
The guest account is created in disabled state, the "Log In" button will appear only after the sponsor approval process is completed.
3
What is true regarding Posturing and Profiling?
A) Profiling describes categorizing the user based on their department while Posturing validates the user as authenticated.
B) Profiling is the act of identifying the endpoint type while Posturing is assigning a status as to the health of the endpoint.
C) Posturing and Profiling are role assignments in ClearPass used internally to map to enforcement policies.
D) Both Posturing and Profiling describe the same thing; what is the health of the client endpoint?
A) Profiling describes categorizing the user based on their department while Posturing validates the user as authenticated.
B) Profiling is the act of identifying the endpoint type while Posturing is assigning a status as to the health of the endpoint.
C) Posturing and Profiling are role assignments in ClearPass used internally to map to enforcement policies.
D) Both Posturing and Profiling describe the same thing; what is the health of the client endpoint?
Both Posturing and Profiling describe the same thing; what is the health of the client endpoint?
4
What are "known" endpoints in ClearPass?
A) "Known" endpoints have be fingerprinted to determine their operating system and manufacturer.
B) These are endpoints whose beacons have been detected but have never completed authentication.
C) The label "Known" indicates rogue endpoints labeled as "friendly" or "ignore".
D) "Known" endpoints can be authenticated based on MAC address to bypass the captive portal login.
A) "Known" endpoints have be fingerprinted to determine their operating system and manufacturer.
B) These are endpoints whose beacons have been detected but have never completed authentication.
C) The label "Known" indicates rogue endpoints labeled as "friendly" or "ignore".
D) "Known" endpoints can be authenticated based on MAC address to bypass the captive portal login.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
5
Which statement is true about OnGuard? (Choose two.)
A) It is used to ensure that Antivirus/Antispyware programs are running
B) It supports both Windows and Mac OS X clients
C) It is used to identify and remove any malware/viruses
D) It only supports 802.1X authentication
A) It is used to ensure that Antivirus/Antispyware programs are running
B) It supports both Windows and Mac OS X clients
C) It is used to identify and remove any malware/viruses
D) It only supports 802.1X authentication

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
6
When ClearPass is communicating with external context servers, which connection protocol is typically used?
A) FTP over SSH
B) REST APIs over HTTPS
C) SOAP and XML
D) YAML
A) FTP over SSH
B) REST APIs over HTTPS
C) SOAP and XML
D) YAML

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
7
What is the significance of using the [Allow ALL MAC AUTH] as an Authentication Method for Guests?
A) Client attempts will fail without an additional Authentication method applied.
B) All clients with unknown endpoints will be granted guest access regardless of authorization.
C) All clients with known endpoints will be granted guest access regardless of authorization.
D) This removes the reliance on the known or unknown status for MAC authentication.
A) Client attempts will fail without an additional Authentication method applied.
B) All clients with unknown endpoints will be granted guest access regardless of authorization.
C) All clients with known endpoints will be granted guest access regardless of authorization.
D) This removes the reliance on the known or unknown status for MAC authentication.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
8
An organization has configured guest self-registration with internal sponsorship. Which options can be configured to send guest users their credentials outside of the initial login web-page? (Choose two.)
A) Configure a Simple Mail Transport Protocol (SMTP) server in ClearPass Policy Manager administration.
B) Configure a Simple Mail Transport Protocol (SMTP) server in ClearPass Guest administration.
C) Configure a Short Message Service (SMS) Gateway in ClearPass Policy Manager administration.
D) Configure a Short Message Service (SMS) Gateway under ClearPass Guest configuration.
E) Configure the self-registration page for the guest to receive a Simple Mail Transport Protocol (SMTP) receipt.
A) Configure a Simple Mail Transport Protocol (SMTP) server in ClearPass Policy Manager administration.
B) Configure a Simple Mail Transport Protocol (SMTP) server in ClearPass Guest administration.
C) Configure a Short Message Service (SMS) Gateway in ClearPass Policy Manager administration.
D) Configure a Short Message Service (SMS) Gateway under ClearPass Guest configuration.
E) Configure the self-registration page for the guest to receive a Simple Mail Transport Protocol (SMTP) receipt.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
9
Refer to the exhibit. ![<strong>Refer to the exhibit. When creating a new ClearPass Service, the [Time Source] has been added as an authorization source. What time source is ClearPass referencing?</strong> A) the ClearPass server where Insight Master has been enabled the ClearPass server where Insight Master has been enabled B) the local clock of the ClearPass server doing the authentication C) the local time setting found on the authenticating client machine D) the NTP (Network Time Protocol) source indicated in the Cluster settings](https://storage.examlex.com/C1454/11ec574e_f8b5_00e6_b2dd_35ab97750e2b_C1454_00.jpg) When creating a new ClearPass Service, the [Time Source] has been added as an authorization source. What time source is ClearPass referencing?
When creating a new ClearPass Service, the [Time Source] has been added as an authorization source. What time source is ClearPass referencing?
A) the ClearPass server where Insight Master has been enabled the ClearPass server where Insight Master has been enabled
B) the local clock of the ClearPass server doing the authentication
C) the local time setting found on the authenticating client machine
D) the NTP (Network Time Protocol) source indicated in the Cluster settings
![<strong>Refer to the exhibit. When creating a new ClearPass Service, the [Time Source] has been added as an authorization source. What time source is ClearPass referencing?</strong> A) the ClearPass server where Insight Master has been enabled the ClearPass server where Insight Master has been enabled B) the local clock of the ClearPass server doing the authentication C) the local time setting found on the authenticating client machine D) the NTP (Network Time Protocol) source indicated in the Cluster settings](https://storage.examlex.com/C1454/11ec574e_f8b5_00e6_b2dd_35ab97750e2b_C1454_00.jpg) When creating a new ClearPass Service, the [Time Source] has been added as an authorization source. What time source is ClearPass referencing?
When creating a new ClearPass Service, the [Time Source] has been added as an authorization source. What time source is ClearPass referencing?A) the ClearPass server where Insight Master has been enabled the ClearPass server where Insight Master has been enabled
B) the local clock of the ClearPass server doing the authentication
C) the local time setting found on the authenticating client machine
D) the NTP (Network Time Protocol) source indicated in the Cluster settings

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
10
Refer to the exhibit. 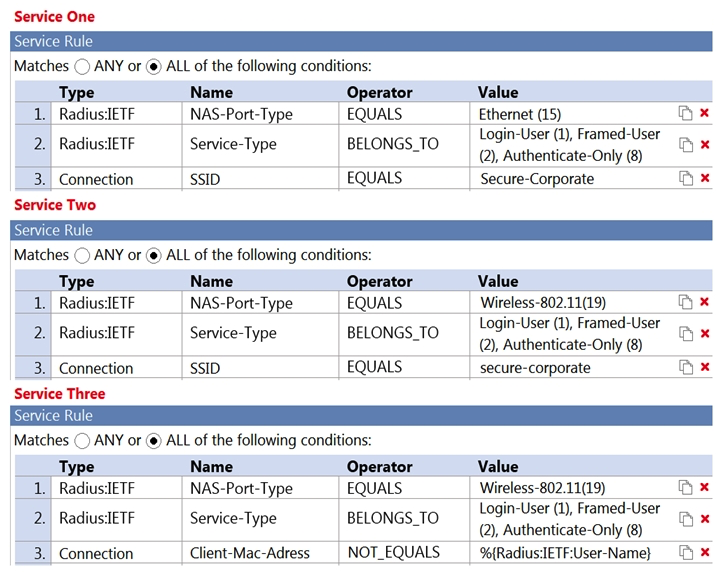 A user connects to an Aruba Access Point wireless SSID named "Secure-Corporate" and performs an 802.1X authentication with ClearPass as the authentication server. Based on this service configuration, which service will be triggered?
A user connects to an Aruba Access Point wireless SSID named "Secure-Corporate" and performs an 802.1X authentication with ClearPass as the authentication server. Based on this service configuration, which service will be triggered?
A) No service will be triggered
B) Service Three
C) Service Two
D) Service One
 A user connects to an Aruba Access Point wireless SSID named "Secure-Corporate" and performs an 802.1X authentication with ClearPass as the authentication server. Based on this service configuration, which service will be triggered?
A user connects to an Aruba Access Point wireless SSID named "Secure-Corporate" and performs an 802.1X authentication with ClearPass as the authentication server. Based on this service configuration, which service will be triggered?A) No service will be triggered
B) Service Three
C) Service Two
D) Service One

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
11
Refer to the exhibit. 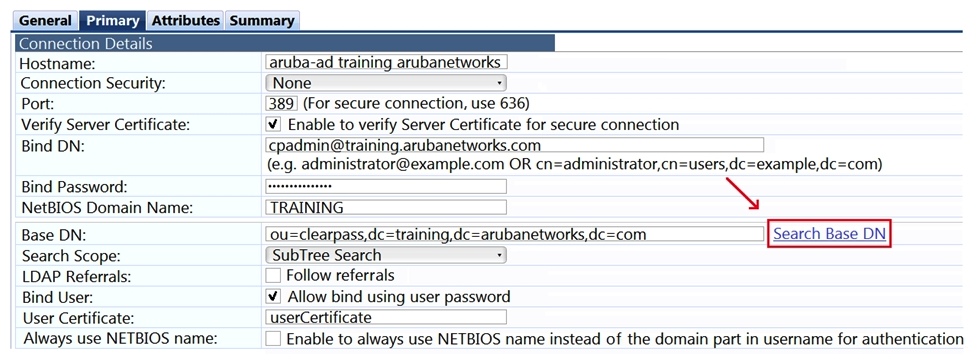 What does Search Base Dn do when joining an Active Directory domain? (Choose two.)
What does Search Base Dn do when joining an Active Directory domain? (Choose two.)
A) validates the connection details entered in the Connection Details
B) searches for the Base DN (Distinguished Name) based on what was typed in the field
C) sets the starting point in the directory tree for the Base DN (Distinguished Name) search
D) updates the Base DN (Distinguished Name) in Active Directory if no match is found
E) runs an Active Directory query that returns all results along with any matching the entered Base DN (Distinguished Name)
 What does Search Base Dn do when joining an Active Directory domain? (Choose two.)
What does Search Base Dn do when joining an Active Directory domain? (Choose two.)A) validates the connection details entered in the Connection Details
B) searches for the Base DN (Distinguished Name) based on what was typed in the field
C) sets the starting point in the directory tree for the Base DN (Distinguished Name) search
D) updates the Base DN (Distinguished Name) in Active Directory if no match is found
E) runs an Active Directory query that returns all results along with any matching the entered Base DN (Distinguished Name)

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
12
Refer to the exhibit. 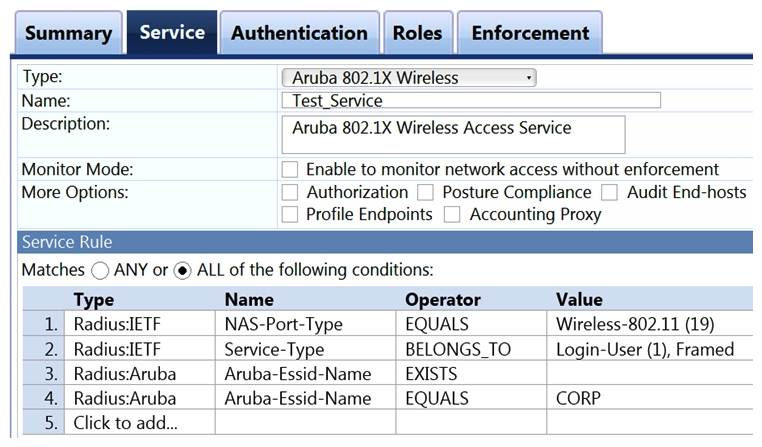 Which user authentication request will match the service rules of the Policy Service shown?
Which user authentication request will match the service rules of the Policy Service shown?
A) a wireless user connection would fail because of miss-configured service rules
B) a wireless user connected to any SSID named "CORP"
C) a wireless user connecting to any SSID on an Aruba Controller
D) a wireless user connecting to an Aruba IAP on the SSID "CORP"
 Which user authentication request will match the service rules of the Policy Service shown?
Which user authentication request will match the service rules of the Policy Service shown?A) a wireless user connection would fail because of miss-configured service rules
B) a wireless user connected to any SSID named "CORP"
C) a wireless user connecting to any SSID on an Aruba Controller
D) a wireless user connecting to an Aruba IAP on the SSID "CORP"

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
13
When should a role mapping policy be used in an 802.1x service with Active Directory as the authentication source?
A) When you want to match Active Directory attributes directly to an enforcement policy.
B) When you want to match Active Directory attributes to an Aruba firewall role on an Aruba Network Access Device.
C) When you want to translate and combine Active Directory attributes into ClearPass roles.
D) When you want to enable attributes as roles directly without combining multiple attributes.
A) When you want to match Active Directory attributes directly to an enforcement policy.
B) When you want to match Active Directory attributes to an Aruba firewall role on an Aruba Network Access Device.
C) When you want to translate and combine Active Directory attributes into ClearPass roles.
D) When you want to enable attributes as roles directly without combining multiple attributes.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
14
A customer with 677 employees would like to authenticate employees using a captive portal guest web login page. Employees should use their AD credentials to login on this page. Which statement is true?
A) The customer needs to add second guest service in the policy manager for the guest network.
B) The customer needs to add the AD server as an authentication source in a guest service.
C) Employees must be taken to a separate web login page on the guest network.
D) The customer needs to add the AD servers RADIUS certificate to the guest network.
A) The customer needs to add second guest service in the policy manager for the guest network.
B) The customer needs to add the AD server as an authentication source in a guest service.
C) Employees must be taken to a separate web login page on the guest network.
D) The customer needs to add the AD servers RADIUS certificate to the guest network.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
15
Which option supports DHCP profiling for devices in a network?
A) configuring ClearPass as a DHCP relay for the client
B) DHCP profiling is enabled on ClearPass by default; configuration of the network access devices is not necessary
C) enabling the DHCP server to profile endpoints and forward meta-data to ClearPass
D) enabling DHCP relay on our network access devices so DHCP requests are forwarded to ClearPass
A) configuring ClearPass as a DHCP relay for the client
B) DHCP profiling is enabled on ClearPass by default; configuration of the network access devices is not necessary
C) enabling the DHCP server to profile endpoints and forward meta-data to ClearPass
D) enabling DHCP relay on our network access devices so DHCP requests are forwarded to ClearPass

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
16
Refer to the exhibit. 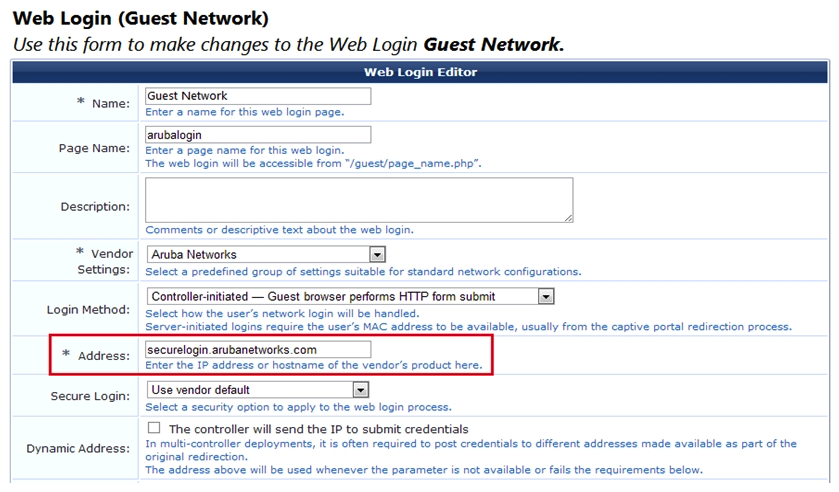 Where will the guests browser be redirected during a captive portal login attempt?
Where will the guests browser be redirected during a captive portal login attempt?
A) The redirect will time out and fail to resolve.
B) The captive portal page hosted on Aruba Central in the cloud.
C) The captive portal page hosted on the Aruba controller.
D) The captive portal page hosted on ClearPass.
 Where will the guests browser be redirected during a captive portal login attempt?
Where will the guests browser be redirected during a captive portal login attempt?A) The redirect will time out and fail to resolve.
B) The captive portal page hosted on Aruba Central in the cloud.
C) The captive portal page hosted on the Aruba controller.
D) The captive portal page hosted on ClearPass.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
17
What happens when a client successfully authenticates but does not match any Enforcement Policy rules?
A) A RADIUS reject is returned for the client.
B) A RADIUS Accept is returned with no Enforcement Profile applied.
C) A RADIUS Accept is returned, and the default Enforcement Profile is applied.
D) A RADIUS Accept is returned, and the default rule is applied to the device.
A) A RADIUS reject is returned for the client.
B) A RADIUS Accept is returned with no Enforcement Profile applied.
C) A RADIUS Accept is returned, and the default Enforcement Profile is applied.
D) A RADIUS Accept is returned, and the default rule is applied to the device.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
18
What is RADIUS Change of Authorization (CoA)?
A) It is a mechanism that enables ClearPass to assigned a User-Based Tunnel (UBT) between a switch and controller for Dynamic Segmentation.
B) It allows clients to issue a privilege escalation request to ClearPass using RADIUS to switch to TACACS+.
C) It allows ClearPass to transmit messages to the Network Attached Device/Network Attached Server (NAD/NAS) to modify a user's session status.
D) It forces the client to re-authenticate upon roaming to an access point controlled by a foreign mobility controller.
A) It is a mechanism that enables ClearPass to assigned a User-Based Tunnel (UBT) between a switch and controller for Dynamic Segmentation.
B) It allows clients to issue a privilege escalation request to ClearPass using RADIUS to switch to TACACS+.
C) It allows ClearPass to transmit messages to the Network Attached Device/Network Attached Server (NAD/NAS) to modify a user's session status.
D) It forces the client to re-authenticate upon roaming to an access point controlled by a foreign mobility controller.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
19
What is an effect of the Cache Timeout setting on the authentication source settings for Active Directory?
A) ClearPass will validate the user credentials, then, for the duration of the cache, ClearPass will just fetch account attributes.
B) The Cache Timeout is designed to reduce the amount of traffic between ClearPass and the A/D server by caching the attributes.
C) ClearPass will validate the user credentials on the first attempt, then will always fetch the account attributes.
D) The Cache Timeout is designed to reduce the amount of traffic between ClearPass and the A/D server by caching the credentials.
A) ClearPass will validate the user credentials, then, for the duration of the cache, ClearPass will just fetch account attributes.
B) The Cache Timeout is designed to reduce the amount of traffic between ClearPass and the A/D server by caching the attributes.
C) ClearPass will validate the user credentials on the first attempt, then will always fetch the account attributes.
D) The Cache Timeout is designed to reduce the amount of traffic between ClearPass and the A/D server by caching the credentials.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
20
Which must be taken into account if a customer wants to use the DHCP collector with 802.1X authentication?
A) When a client sends an authentication request to ClearPass, the profiler will also gather DHCP information.
B) Because DHCP fingerprinted is a Layer-3 function, it cannot be used with an 802.1X authentication service.
C) The client needs to connect to an open network first to be profiled, then shifted to the secure 802.1x network.
D) The client needs to be granted limited access before the enforcement policy can take into account the device type.
A) When a client sends an authentication request to ClearPass, the profiler will also gather DHCP information.
B) Because DHCP fingerprinted is a Layer-3 function, it cannot be used with an 802.1X authentication service.
C) The client needs to connect to an open network first to be profiled, then shifted to the secure 802.1x network.
D) The client needs to be granted limited access before the enforcement policy can take into account the device type.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
21
An organization with 347 employees wants to have the guest create their own accounts for access to the public WLAN, and when guests reconnect, they do not want the guest to have to log in again. Which ClearPass features can be used to meet these requirements?
A) Guest access with MAC caching
B) Guest self-registration with sponsor approval
C) Enforcement based on endpoint profiling
D) ClearPass Onboard Portal
A) Guest access with MAC caching
B) Guest self-registration with sponsor approval
C) Enforcement based on endpoint profiling
D) ClearPass Onboard Portal

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
22
Refer to the exhibit. 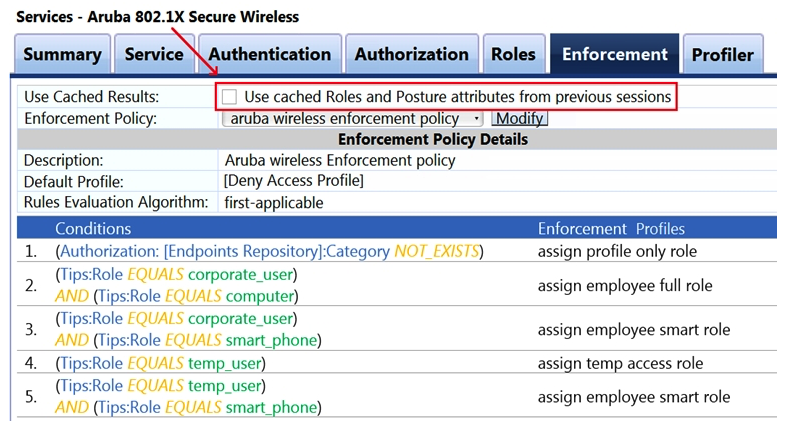 What is true regarding leaving the indicated option "Use cached Roles and Posture attributes from previous sessions" unchecked?
What is true regarding leaving the indicated option "Use cached Roles and Posture attributes from previous sessions" unchecked?
A) A posture change applied to an endpoint is going to be lost each time the client re-authenticates.
B) The service will make the enforcement decision based upon the updated Posture regardless of caching.
C) Posturing will no longer be evaluated in determining the enforcement policy for current or future sessions.
D) Cached posture results are no longer stored by ClearPass but instead are saved to the endpoint of the client.
 What is true regarding leaving the indicated option "Use cached Roles and Posture attributes from previous sessions" unchecked?
What is true regarding leaving the indicated option "Use cached Roles and Posture attributes from previous sessions" unchecked?A) A posture change applied to an endpoint is going to be lost each time the client re-authenticates.
B) The service will make the enforcement decision based upon the updated Posture regardless of caching.
C) Posturing will no longer be evaluated in determining the enforcement policy for current or future sessions.
D) Cached posture results are no longer stored by ClearPass but instead are saved to the endpoint of the client.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
23
An organization wants to have guests connect their own personal devices to the wireless network without requiring a receptionist setting up a guest account. Which ClearPass feature can be used to meet the organization's requirements?
A) Policy Manager Enforcement
B) MAC authentication with profiling
C) ClearPass Onboard
D) Guest with self-registration
A) Policy Manager Enforcement
B) MAC authentication with profiling
C) ClearPass Onboard
D) Guest with self-registration

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
24
Refer to the Endpoint in the screenshot. 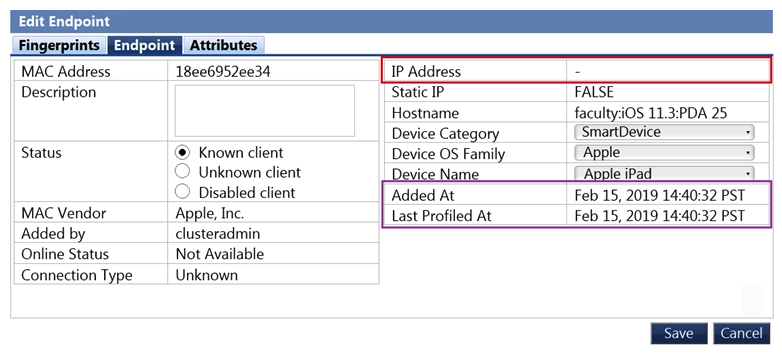 What are possible ways that it was profiled? (Choose two.)
What are possible ways that it was profiled? (Choose two.)
A) Exchange Plugging agent
B) NAD ARP listening handler
C) 3rd part MDM
D) DNS fingerprinting
E) Cisco Device Sensor
 What are possible ways that it was profiled? (Choose two.)
What are possible ways that it was profiled? (Choose two.)A) Exchange Plugging agent
B) NAD ARP listening handler
C) 3rd part MDM
D) DNS fingerprinting
E) Cisco Device Sensor

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
25
What is the benefit of installing a wild card certificate for captive portal authentication?
A) Wild card certificates provide greater security than normal certificates.
B) Allows different certificates for each controller for increased security.
C) Guests no longer are required to validate certificates during captive portal.
D) Allows the single wild card certificate to be installed on all controllers in the environment.
A) Wild card certificates provide greater security than normal certificates.
B) Allows different certificates for each controller for increased security.
C) Guests no longer are required to validate certificates during captive portal.
D) Allows the single wild card certificate to be installed on all controllers in the environment.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
26
When joining ClearPass to an Active Directory (AD) domain, what information is required? (Choose two.)
A) Fully Qualified Domain Name (FQDN) of the AD Domain Controller.
B) ClearPass Policy Manager (CPPM) enterprise credentials.
C) Domain Administrator credentials with at least read access.
D) Cache Timeout value set to at least 10 hours.
E) Domain User credentials with read-write access.
A) Fully Qualified Domain Name (FQDN) of the AD Domain Controller.
B) ClearPass Policy Manager (CPPM) enterprise credentials.
C) Domain Administrator credentials with at least read access.
D) Cache Timeout value set to at least 10 hours.
E) Domain User credentials with read-write access.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
27
What are two ways to add guest accounts to ClearPass? (Choose two.)
A) Importing accounts from Active Directory once ClearPass is added with Admin credentials.
B) Assigning the default role "Lobby Ambassador to a receptionist to then add the accounts.
C) Using the "Import Accounts" under ClearPass Guest.
D) Using the "Create Account" or "Create Multiple" options under ClearPass Guest.
E) Using the "Sync Accounts" under ClearPass Guest.
A) Importing accounts from Active Directory once ClearPass is added with Admin credentials.
B) Assigning the default role "Lobby Ambassador to a receptionist to then add the accounts.
C) Using the "Import Accounts" under ClearPass Guest.
D) Using the "Create Account" or "Create Multiple" options under ClearPass Guest.
E) Using the "Sync Accounts" under ClearPass Guest.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
28
Refer to the exhibit. 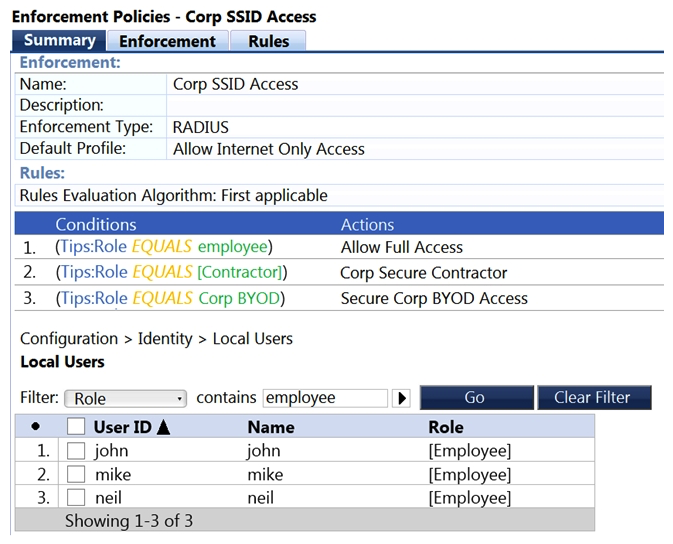 What will be the enforcement for the user "neil"?
What will be the enforcement for the user "neil"?
A) Allow Full Access
B) Secure Corp BYOD Access
C) Allow Internet Only Access
D) Corp Secure Contractor
 What will be the enforcement for the user "neil"?
What will be the enforcement for the user "neil"?A) Allow Full Access
B) Secure Corp BYOD Access
C) Allow Internet Only Access
D) Corp Secure Contractor

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
29
An organization wants guests to be able to create their own guest accounts for access to the public WLAN. Guests do not want to have to repeatedly log in multiple times through the day. Which ClearPass feature can meet these requirements?
A) ClearPass Onboard Portal.
B) Guest access with Media Access Control (MAC) caching.
C) Enforcement based on endpoint profiling.
D) Guest self-registration with sponsor approval.
A) ClearPass Onboard Portal.
B) Guest access with Media Access Control (MAC) caching.
C) Enforcement based on endpoint profiling.
D) Guest self-registration with sponsor approval.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
30
Which Authorization Source supports device profile enforcement?
A) Local User Repository
B) OnGuard Repository
C) Endpoints Repository
D) Guest User Repository
A) Local User Repository
B) OnGuard Repository
C) Endpoints Repository
D) Guest User Repository

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
31
Refer to the exhibit. 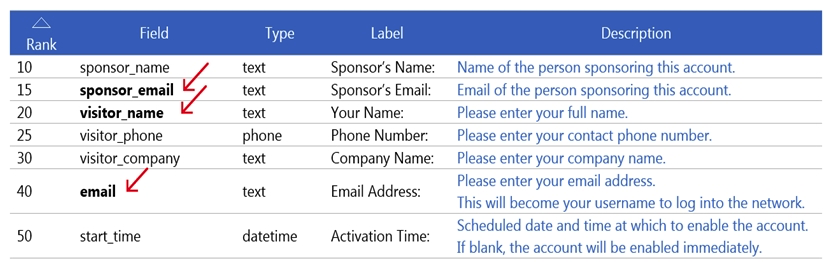 What does a bold field indicate?
What does a bold field indicate?
A) The field is a non-system field
B) The field is currently enabled
C) The field has been customized
D) The field is required
 What does a bold field indicate?
What does a bold field indicate?A) The field is a non-system field
B) The field is currently enabled
C) The field has been customized
D) The field is required

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
32
Which items can be obtained from device profiling? (Choose three.)
A) Device Category
B) Device Family
C) Device Health
D) Device Type
E) Device Location
A) Device Category
B) Device Family
C) Device Health
D) Device Type
E) Device Location

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
33
When using Guest Authentication with MAC Caching service template, which statements are true? (Choose two.)
A) The guest authentication is provided better security than without using MAC caching.
B) The endpoint status of the client will be treated as "known" the first time the client associates to the network.
C) Which wireless SSID and wireless controller must be indicated when configuring the template.
D) The client will be required to re-enter their credentials even if still within the MAC-Auth Expiry term.
A) The guest authentication is provided better security than without using MAC caching.
B) The endpoint status of the client will be treated as "known" the first time the client associates to the network.
C) Which wireless SSID and wireless controller must be indicated when configuring the template.
D) The client will be required to re-enter their credentials even if still within the MAC-Auth Expiry term.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
34
What needs to be configured for ClearPass use an enforcement rule base on client Data Cap?
A) Enable Logging of Accounting Start-Stop packets. Enable Logging of Accounting Start-Stop packets.
B) Interim Accounting on the Network Access Device (NAD).
C) Make sure the Endpoint Profiling is configured.
D) Enable Active Sessions in ClearPass Guest
A) Enable Logging of Accounting Start-Stop packets. Enable Logging of Accounting Start-Stop packets.
B) Interim Accounting on the Network Access Device (NAD).
C) Make sure the Endpoint Profiling is configured.
D) Enable Active Sessions in ClearPass Guest

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
35
Which authentication method requires a client certificate?
A) EAP-TLS
B) Guest self-registration
C) PEAP
D) MAC Authentication
A) EAP-TLS
B) Guest self-registration
C) PEAP
D) MAC Authentication

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck
36
Your boss suggests configuring a guest self-registration page in ClearPass for an upcoming conference event. What are the benefits of using guest self-registration? (Choose two.)
A) This will allow conference employees to pre-load additional device information as guests arrive and register.
B) This strategy effectively stops employees from putting their own corporate devices on the guest network.
C) This will enable additional information to be gathered about guests during the conference.
D) This allows guest users to create and manage their own login account.
E) This will allow employee personal devices to be Onboarded to the corporate network.
A) This will allow conference employees to pre-load additional device information as guests arrive and register.
B) This strategy effectively stops employees from putting their own corporate devices on the guest network.
C) This will enable additional information to be gathered about guests during the conference.
D) This allows guest users to create and manage their own login account.
E) This will allow employee personal devices to be Onboarded to the corporate network.

Unlock Deck
Unlock for access to all 36 flashcards in this deck.
Unlock Deck
k this deck


