Deck 15: Aruba Certified Design Associate
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/34
Play
Full screen (f)
Deck 15: Aruba Certified Design Associate
1
Which checks are made with Onguard posture evaluation in ClearPass? (Choose three.)
A) Operating System version
B) Peer-to-peer application checks
C) EAP TLS certificate validity
D) Client role check
E) Registry keys
A) Operating System version
B) Peer-to-peer application checks
C) EAP TLS certificate validity
D) Client role check
E) Registry keys
Operating System version
Peer-to-peer application checks
Registry keys
Peer-to-peer application checks
Registry keys
2
Refer to the exhibit. 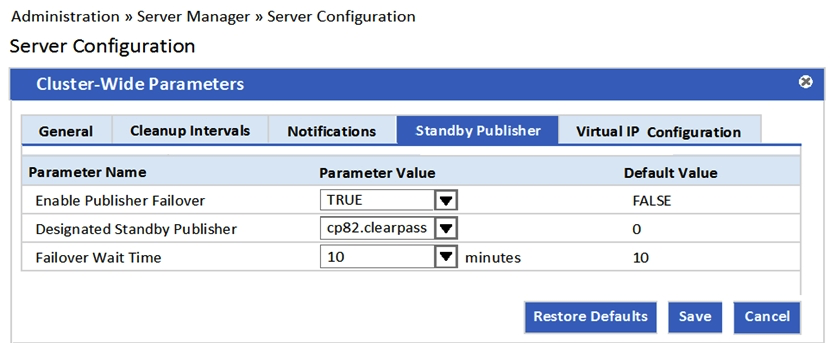 Which statement accurately describes the cp82 ClearPass node? (Choose two.)
Which statement accurately describes the cp82 ClearPass node? (Choose two.)
A) It stays as a Subscriber when the Publisher fails.
B) It becomes the Publisher when the primary Publisher fails.
C) It operates as a Publisher in a separate cluster when the Publisher is active.
D) It operates as a Publisher in the same cluster as the primary Publisher when the primary is active.
E) It operates as a Subscriber when the Publisher is active.
 Which statement accurately describes the cp82 ClearPass node? (Choose two.)
Which statement accurately describes the cp82 ClearPass node? (Choose two.)A) It stays as a Subscriber when the Publisher fails.
B) It becomes the Publisher when the primary Publisher fails.
C) It operates as a Publisher in a separate cluster when the Publisher is active.
D) It operates as a Publisher in the same cluster as the primary Publisher when the primary is active.
E) It operates as a Subscriber when the Publisher is active.
It stays as a Subscriber when the Publisher fails.
It operates as a Subscriber when the Publisher is active.
It operates as a Subscriber when the Publisher is active.
3
A customer wants to make enforcement decisions during 802.1x authentication based on a client's Onguard posture token. What enforcement profile should be used in the health check service?
A) Quarantine VLAN
B) RADIUS CoA
C) RADIUS Accept
D) RADIUS Reject
E) Full Access VLAN.
A) Quarantine VLAN
B) RADIUS CoA
C) RADIUS Accept
D) RADIUS Reject
E) Full Access VLAN.
RADIUS CoA
4
Refer to the exhibit. 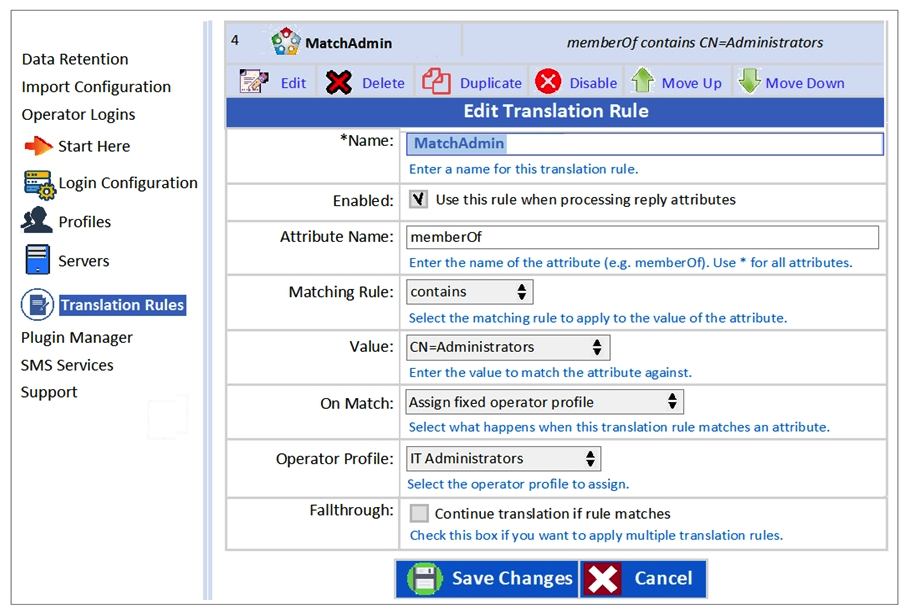 Based on the Translation Rule configuration shown, what will be the outcome?
Based on the Translation Rule configuration shown, what will be the outcome?
A) An AD user from AD group MatchAdmin will be assigned the operator profile of IT Administrators.
B) A user from AD group MatchAdmin will be assigned the operator profile of IT Administrators.
C) All active directory users will be assigned the operator profile of IT Administrators.
D) All ClearPass Policy Manager admin users who are members of the Administrators AD group will be assigned the TACACS profile of IT Administrators.
 Based on the Translation Rule configuration shown, what will be the outcome?
Based on the Translation Rule configuration shown, what will be the outcome?A) An AD user from AD group MatchAdmin will be assigned the operator profile of IT Administrators.
B) A user from AD group MatchAdmin will be assigned the operator profile of IT Administrators.
C) All active directory users will be assigned the operator profile of IT Administrators.
D) All ClearPass Policy Manager admin users who are members of the Administrators AD group will be assigned the TACACS profile of IT Administrators.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
5
Which authorization servers are supported by ClearPass? (Choose two.)
A) Active Directory
B) Cisco Controller
C) Aruba Controller
D) LDAP server
E) Aruba Mobility Access Switch
A) Active Directory
B) Cisco Controller
C) Aruba Controller
D) LDAP server
E) Aruba Mobility Access Switch

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
6
A University wants to deploy ClearPass with the Guest module. They have two types of users that need to use web login authentication. The first type of users are students whose accounts are in Active Directory server. The second type of user are friends of students who need to self-register to access the network. How should the service be setup in the Policy Manager for this Network?
A) Either the Guest User Repository or Active Directory server should be the single authentication source.
B) Guest User Repository as the authentication source, and Guest User Repository and Active Directory server as authentication sources.
C) Guest User Repository as the authentication source and the Active Directory server as authentication source.
D) Active Directory server as authentication source and the Guest User Repository as the authentication source.
E) Guest User Repository and Active Directory server both as authentication sources.
A) Either the Guest User Repository or Active Directory server should be the single authentication source.
B) Guest User Repository as the authentication source, and Guest User Repository and Active Directory server as authentication sources.
C) Guest User Repository as the authentication source and the Active Directory server as authentication source.
D) Active Directory server as authentication source and the Guest User Repository as the authentication source.
E) Guest User Repository and Active Directory server both as authentication sources.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
7
Refer to the exhibit. 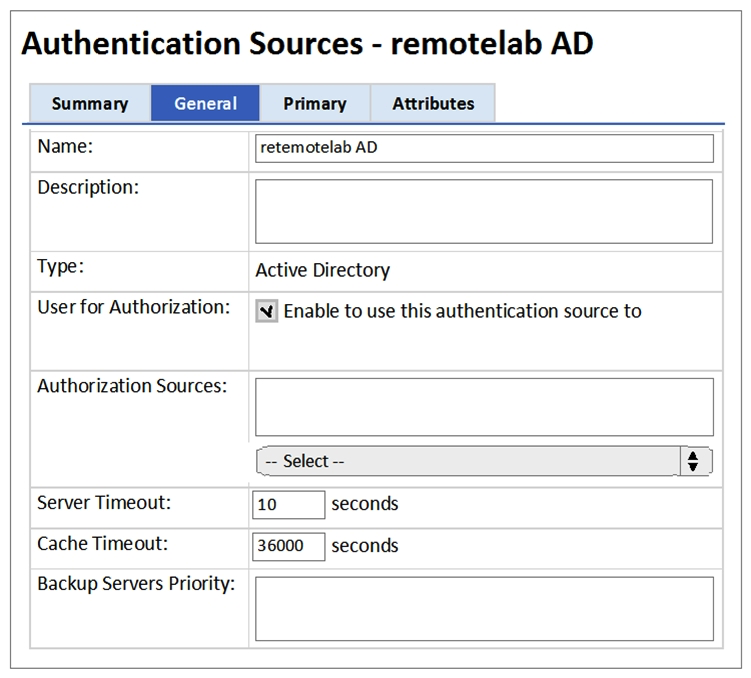 What does the Cache Timeout Value refer to?
What does the Cache Timeout Value refer to?
A) The amount of time the Policy Manager caches the user credentials stored in the Active Directory.
B) The amount of time the Policy Manager waits for a response from the Active Directory before checking the backup authentication source.
C) The amount of time the Policy Manager caches the user attributes fetched from Active Directory.
D) The amount of time the Policy Manager waits for response from the Active Directory before sending a timeout message to the Network Access Device.
E) The amount of time the Policy Manager caches the user\s client certificate.
 What does the Cache Timeout Value refer to?
What does the Cache Timeout Value refer to?A) The amount of time the Policy Manager caches the user credentials stored in the Active Directory.
B) The amount of time the Policy Manager waits for a response from the Active Directory before checking the backup authentication source.
C) The amount of time the Policy Manager caches the user attributes fetched from Active Directory.
D) The amount of time the Policy Manager waits for response from the Active Directory before sending a timeout message to the Network Access Device.
E) The amount of time the Policy Manager caches the user\s client certificate.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
8
Refer to the exhibit. 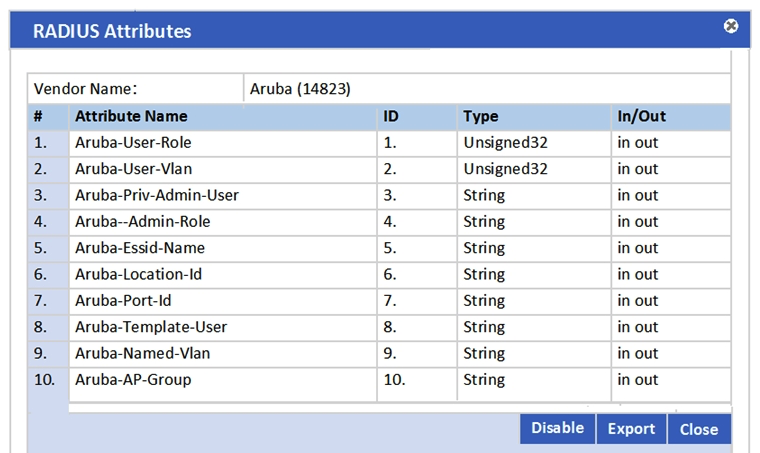 In the Aruba RADIUS dictionary shown, what is the purpose of the RADIUS attributes?
In the Aruba RADIUS dictionary shown, what is the purpose of the RADIUS attributes?
A) to send information via RADIUS packets to Aruba NADs
B) to gather and send Aruba NAD information to ClearPass
C) to send information via RADIUS packets to clients
D) to gather information about Aruba NADs for ClearPass
E) to send CoA packets from ClearPass to the Aruba NAD
 In the Aruba RADIUS dictionary shown, what is the purpose of the RADIUS attributes?
In the Aruba RADIUS dictionary shown, what is the purpose of the RADIUS attributes?A) to send information via RADIUS packets to Aruba NADs
B) to gather and send Aruba NAD information to ClearPass
C) to send information via RADIUS packets to clients
D) to gather information about Aruba NADs for ClearPass
E) to send CoA packets from ClearPass to the Aruba NAD

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
9
Refer to the exhibit. 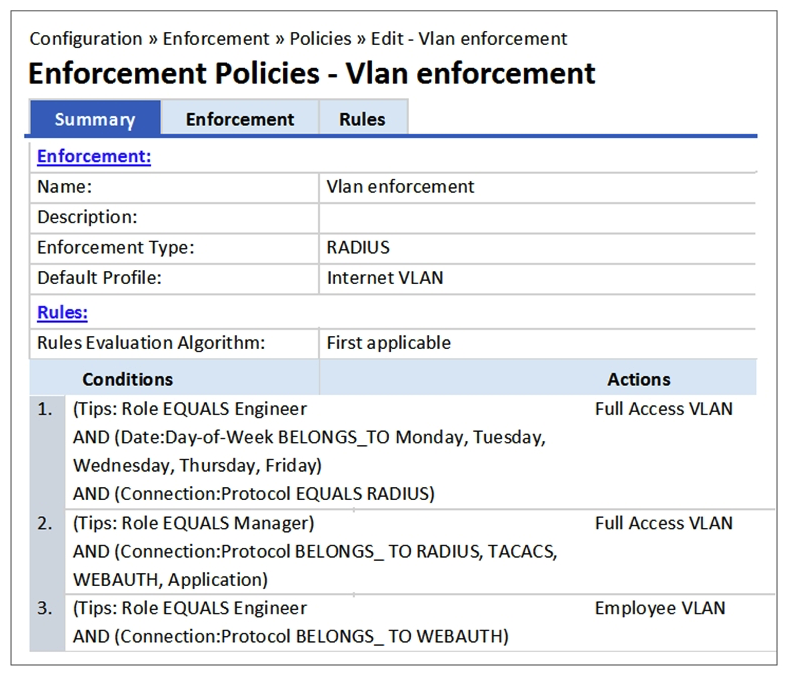 Based on the Policy configuration shown, which VLAN will be assigned when a user with a ClearPass role Engineer authenticates to the network successfully on Saturday using connection protocol WEBAUTH?
Based on the Policy configuration shown, which VLAN will be assigned when a user with a ClearPass role Engineer authenticates to the network successfully on Saturday using connection protocol WEBAUTH?
A) Full Access VLAN
B) Deny Access
C) Employee Vlan
D) Internet VLAN
 Based on the Policy configuration shown, which VLAN will be assigned when a user with a ClearPass role Engineer authenticates to the network successfully on Saturday using connection protocol WEBAUTH?
Based on the Policy configuration shown, which VLAN will be assigned when a user with a ClearPass role Engineer authenticates to the network successfully on Saturday using connection protocol WEBAUTH?A) Full Access VLAN
B) Deny Access
C) Employee Vlan
D) Internet VLAN

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
10
A bank would like to deploy ClearPass Guest with web login authentication so that their customers can self-register on the network to get network access when they have meetings with bank employees. However, they're concerned about security. What is true? (Choose three.)
A) If HTTPS is used for the web login page, after authentication is completed guest Internet traffic will all be encrypted as well.
B) During web login authentication, if HTTPS is used for the web login page, guest credentials will be encrypted.
C) After authentication, an IPSEC VPN on the guest's client be used to encrypt Internet traffic.
D) HTTPS should never be used for Web Login Page authentication.
E) If HTTPS is used for the web login page, after authentication is completed some guest Internet traffic may be unencrypted.
A) If HTTPS is used for the web login page, after authentication is completed guest Internet traffic will all be encrypted as well.
B) During web login authentication, if HTTPS is used for the web login page, guest credentials will be encrypted.
C) After authentication, an IPSEC VPN on the guest's client be used to encrypt Internet traffic.
D) HTTPS should never be used for Web Login Page authentication.
E) If HTTPS is used for the web login page, after authentication is completed some guest Internet traffic may be unencrypted.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
11
Which needs to be validated for a successful EAP-TLS authentication? (Choose two.)
A) WPA2-PSK
B) Username and Password
C) Client Certificate
D) Server Certificate
E) Pre-shared key
A) WPA2-PSK
B) Username and Password
C) Client Certificate
D) Server Certificate
E) Pre-shared key

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
12
What types of files are stored in the Local Shared Folders database in ClearPass? (Choose two.)
A) Backup Files
B) Posture dictionaries
C) Software image
D) Device fingerprint dictionaries
E) Log files
A) Backup Files
B) Posture dictionaries
C) Software image
D) Device fingerprint dictionaries
E) Log files

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
13
Refer to the exhibit. ![<strong>Refer to the exhibit. Based on the information, what is the purpose of using [Time Source] for authorization?</strong> A) to check how long it has been since the last login authentication B) to check whether the guest account expired C) to check whether the MAC address is in the MAC Caching repository D) to check whether the MAC address status is known in the endpoints table E) to check whether the MAC address status is unknown in the endpoints table](https://storage.examlex.com/C1454/11ec574e_f89e_9235_b2dd_cbf17c4c5f86_C1454_00.jpg) Based on the information, what is the purpose of using [Time Source] for authorization?
Based on the information, what is the purpose of using [Time Source] for authorization?
A) to check how long it has been since the last login authentication
B) to check whether the guest account expired
C) to check whether the MAC address is in the MAC Caching repository
D) to check whether the MAC address status is known in the endpoints table
E) to check whether the MAC address status is unknown in the endpoints table
![<strong>Refer to the exhibit. Based on the information, what is the purpose of using [Time Source] for authorization?</strong> A) to check how long it has been since the last login authentication B) to check whether the guest account expired C) to check whether the MAC address is in the MAC Caching repository D) to check whether the MAC address status is known in the endpoints table E) to check whether the MAC address status is unknown in the endpoints table](https://storage.examlex.com/C1454/11ec574e_f89e_9235_b2dd_cbf17c4c5f86_C1454_00.jpg) Based on the information, what is the purpose of using [Time Source] for authorization?
Based on the information, what is the purpose of using [Time Source] for authorization?A) to check how long it has been since the last login authentication
B) to check whether the guest account expired
C) to check whether the MAC address is in the MAC Caching repository
D) to check whether the MAC address status is known in the endpoints table
E) to check whether the MAC address status is unknown in the endpoints table

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
14
Refer to the exhibit. 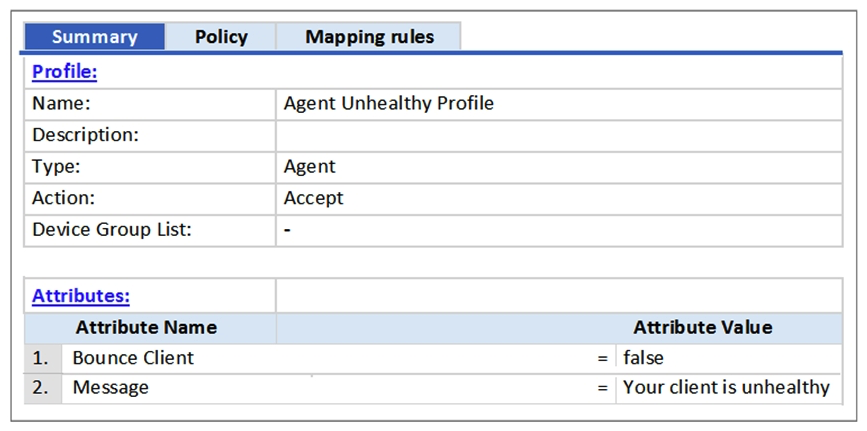 Based on the Enforcement Profile configuration shown, which statement accurately describes what is sent?
Based on the Enforcement Profile configuration shown, which statement accurately describes what is sent?
A) A limited access VLAN value is sent to the Network Access Device.
B) A message is sent to the Onguard Agent on the client device.
C) An unhealthy role value is sent to the Network Access Device.
D) A RADIUS CoA message is sent to bounce the client.
E) A RADIUS access-accept message is sent to the Controller.
 Based on the Enforcement Profile configuration shown, which statement accurately describes what is sent?
Based on the Enforcement Profile configuration shown, which statement accurately describes what is sent?A) A limited access VLAN value is sent to the Network Access Device.
B) A message is sent to the Onguard Agent on the client device.
C) An unhealthy role value is sent to the Network Access Device.
D) A RADIUS CoA message is sent to bounce the client.
E) A RADIUS access-accept message is sent to the Controller.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
15
Refer to the exhibit. 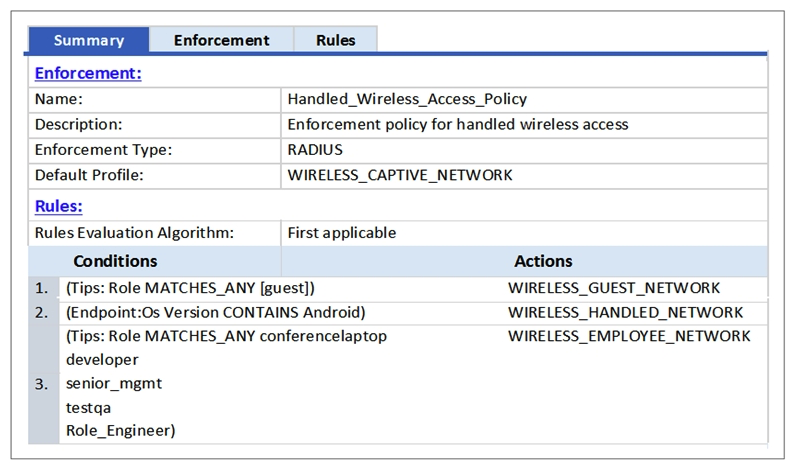 A user who is tagged with the ClearPass roles of Role_Engineer and developer, but not testqa, connects to the network with a corporate Windows laptop. Which Enforcement Profile is applied?
A user who is tagged with the ClearPass roles of Role_Engineer and developer, but not testqa, connects to the network with a corporate Windows laptop. Which Enforcement Profile is applied?
A) WIRELESS_GUEST_NETWORK
B) WIRELESS_CAPTIVE_NETWORK
C) WIRELESS_HANDHELD_NETWORK
D) WIRELESS_EMPLOYEE_NETWORK
 A user who is tagged with the ClearPass roles of Role_Engineer and developer, but not testqa, connects to the network with a corporate Windows laptop. Which Enforcement Profile is applied?
A user who is tagged with the ClearPass roles of Role_Engineer and developer, but not testqa, connects to the network with a corporate Windows laptop. Which Enforcement Profile is applied?A) WIRELESS_GUEST_NETWORK
B) WIRELESS_CAPTIVE_NETWORK
C) WIRELESS_HANDHELD_NETWORK
D) WIRELESS_EMPLOYEE_NETWORK

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
16
What is RADIUS CoA (RFC 3576) used for?
A) To force the client to re-authenticate upon roaming to a new Controller.
B) To authenticate users or devices before granting them access to a network.
C) To validate a host address against a whitelist or a blacklist.
D) To transmit messages to the NAD/NAS to modify a user's session status.
E) To apply firewall policies based on authentication credentials.
A) To force the client to re-authenticate upon roaming to a new Controller.
B) To authenticate users or devices before granting them access to a network.
C) To validate a host address against a whitelist or a blacklist.
D) To transmit messages to the NAD/NAS to modify a user's session status.
E) To apply firewall policies based on authentication credentials.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
17
In single SSID Onboarding, which method can be used in the Enforcement Policy to distinguish between a provisioned device and a device that has not gone through the Onboard workflow?
A) Onguard Agent used
B) Authentication Method used
C) Network Access Device used
D) Active Directory Attributes
E) Endpoint OS Category
A) Onguard Agent used
B) Authentication Method used
C) Network Access Device used
D) Active Directory Attributes
E) Endpoint OS Category

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
18
Refer to the exhibit. ![<strong>Refer to the exhibit. Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?</strong> A) RestrictedACL B) HR VLAN C) Remote Employee ACL D) [Deny Access Profile] E) EMPLOYEE_VLAN](https://storage.examlex.com/C1454/11ec574e_f89d_329f_b2dd_79482d1aa892_C1454_00.jpg) Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
A) RestrictedACL
B) HR VLAN
C) Remote Employee ACL
D) [Deny Access Profile]
E) EMPLOYEE_VLAN
![<strong>Refer to the exhibit. Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?</strong> A) RestrictedACL B) HR VLAN C) Remote Employee ACL D) [Deny Access Profile] E) EMPLOYEE_VLAN](https://storage.examlex.com/C1454/11ec574e_f89d_329f_b2dd_79482d1aa892_C1454_00.jpg) Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?A) RestrictedACL
B) HR VLAN
C) Remote Employee ACL
D) [Deny Access Profile]
E) EMPLOYEE_VLAN

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
19
Refer to the exhibit. 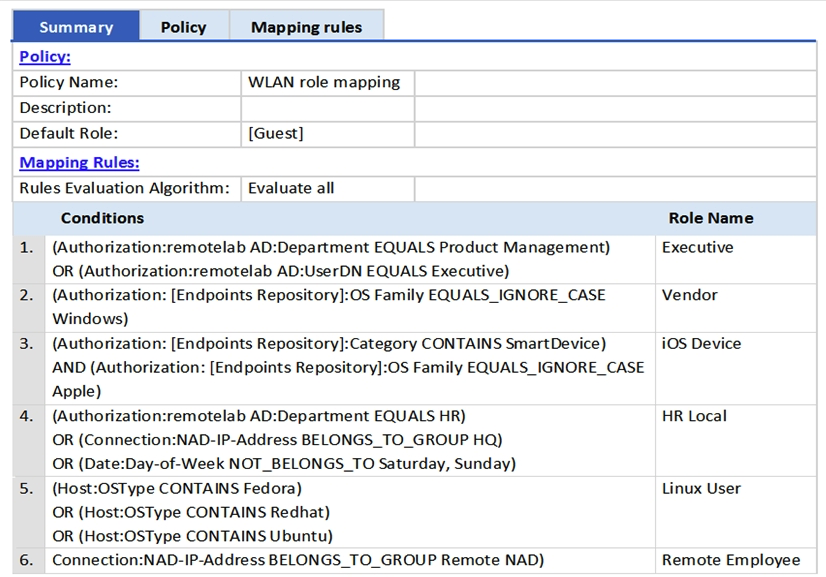 An AD user's department attribute is configured as "HR". The user connects on Monday using an Android phone to an Aruba Controller that belongs to the Device Group Remote NAD. Which roles are assigned to the user in ClearPass? (Choose two.)
An AD user's department attribute is configured as "HR". The user connects on Monday using an Android phone to an Aruba Controller that belongs to the Device Group Remote NAD. Which roles are assigned to the user in ClearPass? (Choose two.)
A) Remote Employee
B) Executive
C) Vendor
D) iOS Device
E) HR Local
 An AD user's department attribute is configured as "HR". The user connects on Monday using an Android phone to an Aruba Controller that belongs to the Device Group Remote NAD. Which roles are assigned to the user in ClearPass? (Choose two.)
An AD user's department attribute is configured as "HR". The user connects on Monday using an Android phone to an Aruba Controller that belongs to the Device Group Remote NAD. Which roles are assigned to the user in ClearPass? (Choose two.)A) Remote Employee
B) Executive
C) Vendor
D) iOS Device
E) HR Local

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
20
Refer to the exhibit. 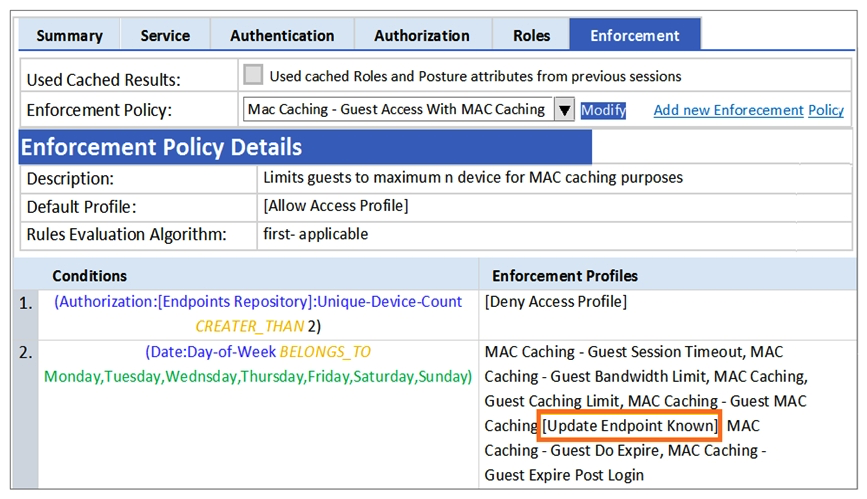 A guest to the Guest SSID and authenticates successfully using the guest php web login page. Based on the MAC Caching service information shown, which statement about the guest's MAC address is accurate?
A guest to the Guest SSID and authenticates successfully using the guest php web login page. Based on the MAC Caching service information shown, which statement about the guest's MAC address is accurate?
A) It will be visible in the Guest User Repository with Unknown Status.
B) It will be deleted from the Endpoints tables.
C) It will be visible in the Guest User Repository with Known Status.
D) It will be visible in the Endpoints table with Unknown Status.
E) It will be visible in the Endpoints table with Known Status.
 A guest to the Guest SSID and authenticates successfully using the guest php web login page. Based on the MAC Caching service information shown, which statement about the guest's MAC address is accurate?
A guest to the Guest SSID and authenticates successfully using the guest php web login page. Based on the MAC Caching service information shown, which statement about the guest's MAC address is accurate?A) It will be visible in the Guest User Repository with Unknown Status.
B) It will be deleted from the Endpoints tables.
C) It will be visible in the Guest User Repository with Known Status.
D) It will be visible in the Endpoints table with Unknown Status.
E) It will be visible in the Endpoints table with Known Status.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
21
Refer to the exhibit. 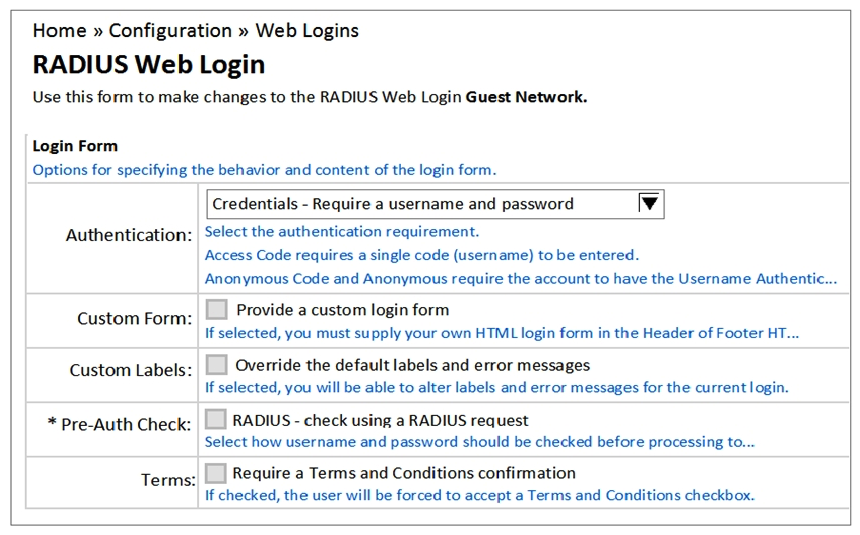 A Web Login Page is configured in ClearPass Guest as shown. What is the purpose of the Pre-Auth Check?
A Web Login Page is configured in ClearPass Guest as shown. What is the purpose of the Pre-Auth Check?
A) To -re-authenticate users when they're roaming from one NAD to another.
B) To authenticate users before they launch the Web Login Page.
C) To replace the need for the NAD to send an authentication request to ClearPass.
D) To authenticate users after the NAD sends an authentication request to ClearPass.
E) To authenticate users before the client sends the credentials to the NAD.
 A Web Login Page is configured in ClearPass Guest as shown. What is the purpose of the Pre-Auth Check?
A Web Login Page is configured in ClearPass Guest as shown. What is the purpose of the Pre-Auth Check?A) To -re-authenticate users when they're roaming from one NAD to another.
B) To authenticate users before they launch the Web Login Page.
C) To replace the need for the NAD to send an authentication request to ClearPass.
D) To authenticate users after the NAD sends an authentication request to ClearPass.
E) To authenticate users before the client sends the credentials to the NAD.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
22
An SNMP probe is sent from ClearPass to a network access device but ClearPass is unable to get profiling information. What could be a valid cause? (Choose three.)
A) Mismatching SNMP community string in the ClearPass and NAD configuration.
B) Only SNMP read has been configured but SNMP write is needed for profiling information.
C) SNMP is not enabled on the NAD.
D) An external firewall is blocking SNMP traffic.
E) SNMP probing is not supported between ClearPass and NADs.
A) Mismatching SNMP community string in the ClearPass and NAD configuration.
B) Only SNMP read has been configured but SNMP write is needed for profiling information.
C) SNMP is not enabled on the NAD.
D) An external firewall is blocking SNMP traffic.
E) SNMP probing is not supported between ClearPass and NADs.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
23
Refer to the exhibit. ![<strong>Refer to the exhibit. An AD user's department attribute value is configured as Product Management. The user connects on Monday to a NAD that belongs to the Device Group HQ. Which role is assigned to the user in ClearPass?</strong> A) Linux User B) Executive C) [Employee] D) [Guest] E) HR Local](https://storage.examlex.com/C1454/11ec574e_f89f_7c98_b2dd_699b8922921f_C1454_00.jpg) An AD user's department attribute value is configured as "Product Management". The user connects on Monday to a NAD that belongs to the Device Group HQ. Which role is assigned to the user in ClearPass?
An AD user's department attribute value is configured as "Product Management". The user connects on Monday to a NAD that belongs to the Device Group HQ. Which role is assigned to the user in ClearPass?
A) Linux User
B) Executive
C) [Employee]
D) [Guest]
E) HR Local
![<strong>Refer to the exhibit. An AD user's department attribute value is configured as Product Management. The user connects on Monday to a NAD that belongs to the Device Group HQ. Which role is assigned to the user in ClearPass?</strong> A) Linux User B) Executive C) [Employee] D) [Guest] E) HR Local](https://storage.examlex.com/C1454/11ec574e_f89f_7c98_b2dd_699b8922921f_C1454_00.jpg) An AD user's department attribute value is configured as "Product Management". The user connects on Monday to a NAD that belongs to the Device Group HQ. Which role is assigned to the user in ClearPass?
An AD user's department attribute value is configured as "Product Management". The user connects on Monday to a NAD that belongs to the Device Group HQ. Which role is assigned to the user in ClearPass?A) Linux User
B) Executive
C) [Employee]
D) [Guest]
E) HR Local

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
24
Refer to the exhibit. ![<strong>Refer to the exhibit. An AD user's department attribute value is configured as QA. The user authenticates from a laptop running MAC OS X. Which role is assigned to the user in ClearPass?</strong> A) HR Local B) Remote Employee C) [Guest] D) iOS Device E) Executive](https://storage.examlex.com/C1454/11ec574e_f89e_e056_b2dd_15ae864d4f52_C1454_00.jpg) An AD user's department attribute value is configured as "QA". The user authenticates from a laptop running MAC OS X. Which role is assigned to the user in ClearPass?
An AD user's department attribute value is configured as "QA". The user authenticates from a laptop running MAC OS X. Which role is assigned to the user in ClearPass?
A) HR Local
B) Remote Employee
C) [Guest]
D) iOS Device
E) Executive
![<strong>Refer to the exhibit. An AD user's department attribute value is configured as QA. The user authenticates from a laptop running MAC OS X. Which role is assigned to the user in ClearPass?</strong> A) HR Local B) Remote Employee C) [Guest] D) iOS Device E) Executive](https://storage.examlex.com/C1454/11ec574e_f89e_e056_b2dd_15ae864d4f52_C1454_00.jpg) An AD user's department attribute value is configured as "QA". The user authenticates from a laptop running MAC OS X. Which role is assigned to the user in ClearPass?
An AD user's department attribute value is configured as "QA". The user authenticates from a laptop running MAC OS X. Which role is assigned to the user in ClearPass?A) HR Local
B) Remote Employee
C) [Guest]
D) iOS Device
E) Executive

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
25
Refer to the exhibit. 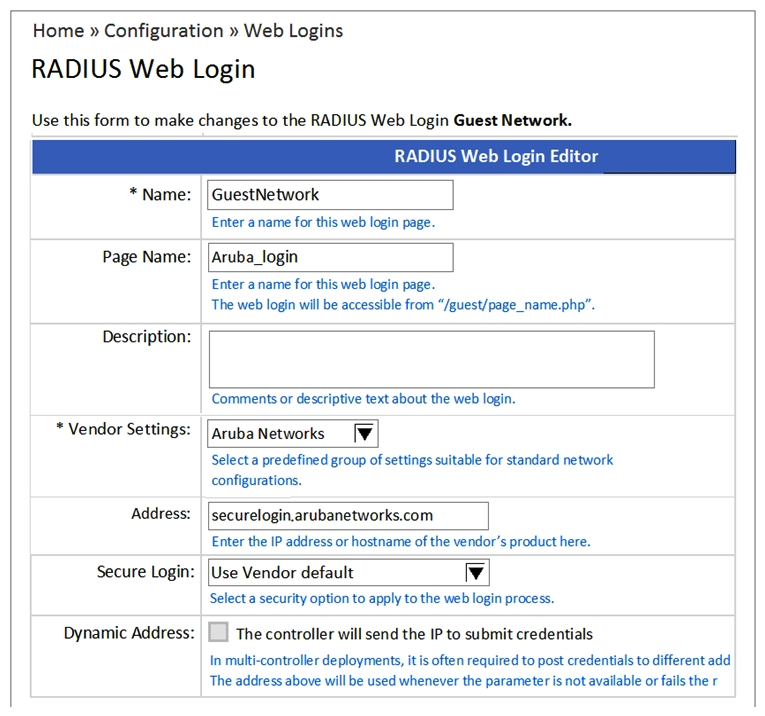 When configuring a Web Login Page in ClearPass Guest, the information shown is displayed. What is the Address field value 'securelogin.arubanetworks.com' used for?
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed. What is the Address field value 'securelogin.arubanetworks.com' used for?
A) For the client to POST the user credentials to the NAD.
B) For ClearPass to send a RADIUS request to the NAD.
C) For ClearPass to send a TACACS+ request to the NAD.
D) For appending to the Web Login URL, after the page name.
E) For appending to the Web Login URL, before the page name.
 When configuring a Web Login Page in ClearPass Guest, the information shown is displayed. What is the Address field value 'securelogin.arubanetworks.com' used for?
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed. What is the Address field value 'securelogin.arubanetworks.com' used for?A) For the client to POST the user credentials to the NAD.
B) For ClearPass to send a RADIUS request to the NAD.
C) For ClearPass to send a TACACS+ request to the NAD.
D) For appending to the Web Login URL, after the page name.
E) For appending to the Web Login URL, before the page name.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
26
Which statement is true? (Choose two.)
A) Mobile device Management is the result of Onboarding.
B) Third party Mobile Device Management solutions can be integrated with ClearPass.
C) Mobile Device Management is the authentication that happens before Onboarding.
D) Mobile Device Management is an application container that is used to provision work applications.
E) Mobile Device Management is used to control device functions post-Onboarding.
A) Mobile device Management is the result of Onboarding.
B) Third party Mobile Device Management solutions can be integrated with ClearPass.
C) Mobile Device Management is the authentication that happens before Onboarding.
D) Mobile Device Management is an application container that is used to provision work applications.
E) Mobile Device Management is used to control device functions post-Onboarding.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
27
What is the purpose of the Audit Viewer in the Monitoring section of ClearPass Policy Manager?
A) To display the entire configuration of the ClearPass Policy Manager.
B) To audit the network for PCI compliance.
C) To display system events like high CPU usage.
D) To audit client authentications.
E) To display changes made to the ClearPass configuration.
A) To display the entire configuration of the ClearPass Policy Manager.
B) To audit the network for PCI compliance.
C) To display system events like high CPU usage.
D) To audit client authentications.
E) To display changes made to the ClearPass configuration.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
28
What must be configured to enable RADIUS authentication with ClearPass on a network access device (NAD)? (Choose two.)
A) The ClearPass server must have the network device added as a valid NAD.
B) The ClearPass server certificate must be installed on the NAD.
C) A matching shared secret must be configured on both the ClearPass server and NAD.
D) An NTP server needs to be set on the NAD.
E) A bind username and bind password must be provided.
A) The ClearPass server must have the network device added as a valid NAD.
B) The ClearPass server certificate must be installed on the NAD.
C) A matching shared secret must be configured on both the ClearPass server and NAD.
D) An NTP server needs to be set on the NAD.
E) A bind username and bind password must be provided.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
29
What are Operator Profiles used for?
A) To map AD attributes to admin privilege levels in ClearPass Guest.
B) To enforce role based access control for ClearPass Guest Admin users.
C) To enforce role based access control for Aruba Controllers.
D) To assign ClearPass roles to guest users.
E) To enforce role based access control for ClearPass Policy Manager users.
A) To map AD attributes to admin privilege levels in ClearPass Guest.
B) To enforce role based access control for ClearPass Guest Admin users.
C) To enforce role based access control for Aruba Controllers.
D) To assign ClearPass roles to guest users.
E) To enforce role based access control for ClearPass Policy Manager users.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
30
Which statement is true about the configuration of a generic LDAP server as an External Authentication server in ClearPass? (Choose three.)
A) Generic LDAP Browser can be used to search the Base DN.
B) An administrator can customize the selection of attributes fetched from an LDAP server.
C) The bind DN can be in the administrator@domain format.
D) A maximum of one generic LDAP server can be configured in ClearPass.
E) A LDAP Browser can be used to search the Base DN.
A) Generic LDAP Browser can be used to search the Base DN.
B) An administrator can customize the selection of attributes fetched from an LDAP server.
C) The bind DN can be in the administrator@domain format.
D) A maximum of one generic LDAP server can be configured in ClearPass.
E) A LDAP Browser can be used to search the Base DN.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
31
What does the Posture Token QUARANTINE imply?
A) The client is compliant. However, there is an update available to remediate the client to HEALTHY state.
B) The posture of the client is unknown.
C) The client is infected and is a threat to other systems in the network.
D) The client is out of compliance, but has HEALTHY state.
E) The client is out of compliance.
A) The client is compliant. However, there is an update available to remediate the client to HEALTHY state.
B) The posture of the client is unknown.
C) The client is infected and is a threat to other systems in the network.
D) The client is out of compliance, but has HEALTHY state.
E) The client is out of compliance.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
32
What can ClearPass use to assign roles to the client during policy service processing? (Choose two.)
A) Through a role mapping policy.
B) From the attributes configures in a Network Access Device.
C) From the server derivation rule in the Aruba Controller server group for the client.
D) From the attributes configured in Active Directory.
E) Roles can be derived from the Aruba Network Access Device.
A) Through a role mapping policy.
B) From the attributes configures in a Network Access Device.
C) From the server derivation rule in the Aruba Controller server group for the client.
D) From the attributes configured in Active Directory.
E) Roles can be derived from the Aruba Network Access Device.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
33
A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server outage. 802.1x authentications will not be interrupted. The administrator has enabled a single Virtual IP address on two ClearPass servers. Which statement is true? (Choose two.)
A) Both the primary and secondary nodes will respond to authentication requests sent to the Virtual IP address when the primary node is active.
B) The primary node will respond to authentication requests sent to the Virtual IP address when the primary node is active.
C) The NAD should be configured with the primary node IP address for RADIUS authentications on the 802.1x network.
D) A new Virtual IP address should be created for each NAD.
E) The NAD should be configured with the virtual IP address for RADIUS authentications on the 802.1x network.
A) Both the primary and secondary nodes will respond to authentication requests sent to the Virtual IP address when the primary node is active.
B) The primary node will respond to authentication requests sent to the Virtual IP address when the primary node is active.
C) The NAD should be configured with the primary node IP address for RADIUS authentications on the 802.1x network.
D) A new Virtual IP address should be created for each NAD.
E) The NAD should be configured with the virtual IP address for RADIUS authentications on the 802.1x network.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck
34
Refer to the exhibit. 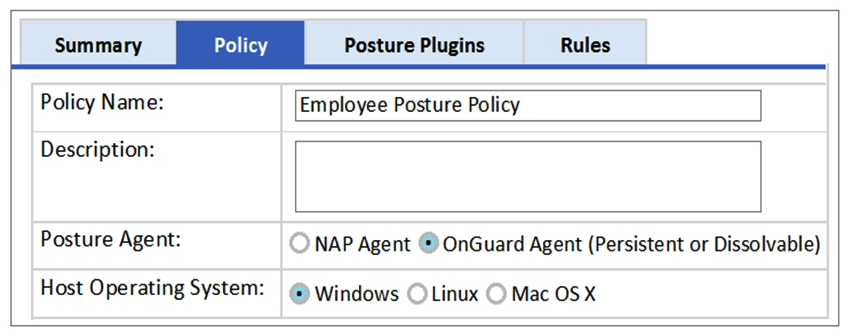 Based on the Posture Policy configuration shown, above, which statement is true?
Based on the Posture Policy configuration shown, above, which statement is true?
A) This Posture Policy can only be applied to an 802.1x wired service not 802.1x wireless.
B) This Posture Policy checks the health status of devices running Windows, Linux and Mac OS X.
C) This Posture Policy can use either the persistent or dissolvable Onguard agent to obtain the statement of health.
D) This Posture Policy checks for presence of a firewall application in Windows devices.
E) This Posture Policy checks with a Windows NPS server for posture tokens.
 Based on the Posture Policy configuration shown, above, which statement is true?
Based on the Posture Policy configuration shown, above, which statement is true?A) This Posture Policy can only be applied to an 802.1x wired service not 802.1x wireless.
B) This Posture Policy checks the health status of devices running Windows, Linux and Mac OS X.
C) This Posture Policy can use either the persistent or dissolvable Onguard agent to obtain the statement of health.
D) This Posture Policy checks for presence of a firewall application in Windows devices.
E) This Posture Policy checks with a Windows NPS server for posture tokens.

Unlock Deck
Unlock for access to all 34 flashcards in this deck.
Unlock Deck
k this deck


