Deck 12: Using HPE OneView
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/54
Play
Full screen (f)
Deck 12: Using HPE OneView
1
A network administrator deploys AirWave over a Mobility Master (MM)-Mobility Controller (MC) network to monitor, audit, and report activities. The main areas of concern are with high user density, not enough APs, or not enough channel bandwidth. Which two report options can the network administrator user to create a weekly report that shows networking equipment with more users and high-demand applications used by top talkers? (Select two.)
A) Most Utilized Folders by Maximum Concurrent Clients
B) Most Utilized by Usage
C) Top Applications Summary
D) Most Utilized by Maximum Concurrent Clients
E) Top 3 Applications For Top 10 Users
A) Most Utilized Folders by Maximum Concurrent Clients
B) Most Utilized by Usage
C) Top Applications Summary
D) Most Utilized by Maximum Concurrent Clients
E) Top 3 Applications For Top 10 Users
Most Utilized by Usage
Most Utilized by Maximum Concurrent Clients
Most Utilized by Maximum Concurrent Clients
2
A software development company has 700 employees who work from home. The company also has small offices located in different cities throughout the world. During working hours, they use RAPs to connect to a datacenter to upload software code as well as interact with databases. In the past two months, brief failures have occurred in the 7240XM Mobility Controller (MC) that runs ArubaOS 8.3 and terminates the RAPs. These RAPs disconnect, affecting the users connected to the RAPs. This also causes problems with code uploads and database synchronizations. Therefore, the company decides to add a second 7240XM controller for redundancy. How should the network administrator deploy both controllers in order to provide redundancy while preventing failover events from disconnecting users?
A) Connect both controllers with common VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
B) Connect both controllers with common VLANs, and create an HA fast failover group with public addresses in the internet VLAN.
C) Connect both controllers with different VLANs, and create an L2-connected cluster using private addresses in the internet VLAN.
D) Connect both controllers with common VLANs, and configure LMS/BLMS values equal to public addresses in the internet VLAN.
A) Connect both controllers with common VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
B) Connect both controllers with common VLANs, and create an HA fast failover group with public addresses in the internet VLAN.
C) Connect both controllers with different VLANs, and create an L2-connected cluster using private addresses in the internet VLAN.
D) Connect both controllers with common VLANs, and configure LMS/BLMS values equal to public addresses in the internet VLAN.
Connect both controllers with common VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
3
An organization wants to deploy a WLAN infrastructure that provides connectivity to these client categories: Employees Contractors Guest users Corporate IoT legacy devices that support no authentication or encryption Employees and contractors must authenticate with company credentials and get network access based on AD group membership. Guest users are required to authenticate with captive portal using predefined credentials. Only employees will run L2 encryption. Which implementation plan fulfills the requirements while maximizing the channel usage?
A) Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal.
B) Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal and L2 fail through.
C) Create a single VAP to run WPA2-AES and 802.1x authentication, MAC authentication L2 fail through, captive portal, and VIA support.
D) Create VAP1 to run WPA2-AES and 802.1x authentication, and VAP2 to run opensystem encryption with MAC authentication and captive portal.
A) Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal.
B) Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal and L2 fail through.
C) Create a single VAP to run WPA2-AES and 802.1x authentication, MAC authentication L2 fail through, captive portal, and VIA support.
D) Create VAP1 to run WPA2-AES and 802.1x authentication, and VAP2 to run opensystem encryption with MAC authentication and captive portal.
Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal.
4
Refer to the exhibit. 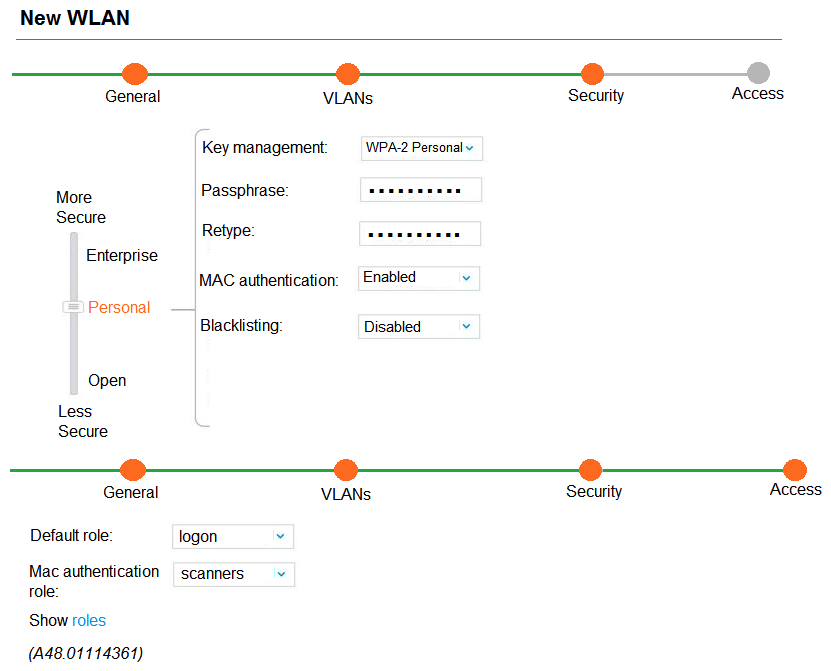 A company acquires ten barcode scanners to run inventory tasks. These Wifi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
A company acquires ten barcode scanners to run inventory tasks. These Wifi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
A) Add scanner MAC addresses in user derivation rules.
B) Add scanner MAC addresses in the internal database.
C) Set internal as the MAC authentication server group.
D) Enable L2 Authentication Fail Through.
 A company acquires ten barcode scanners to run inventory tasks. These Wifi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
A company acquires ten barcode scanners to run inventory tasks. These Wifi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?A) Add scanner MAC addresses in user derivation rules.
B) Add scanner MAC addresses in the internal database.
C) Set internal as the MAC authentication server group.
D) Enable L2 Authentication Fail Through.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
5
Company 1 and Company 2 are medium-sized companies that collaborate in a joint venture. Each company owns a building, and each has their own ArubaOS 8 Mobility Master (MM)-Mobility Controller (MC) deployment. The buildings are located in front of one another. For the initial stage of the project, the companies want to interconnect their networks with fiber, and broadcast each other's SSIDs. These are the requirements: Do not unify the company's network management responsibilities. Allow each company to take care of their own SSID setups when broadcasted in the other building. Terminate Company 1 user traffic on Company 1 MCs when they connect to Company 2 APs. Terminate Company 2 user traffic on Company 2 MCs when they connect to Company 1 APs. What is needed to meet the solution requirements?
A) Multizone APs
B) Inter MC S2S Ipsec tunnels
C) Multi MC Clusters
D) Inter MC GRE tunnels
A) Multizone APs
B) Inter MC S2S Ipsec tunnels
C) Multi MC Clusters
D) Inter MC GRE tunnels

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
6
Refer to the exhibit. 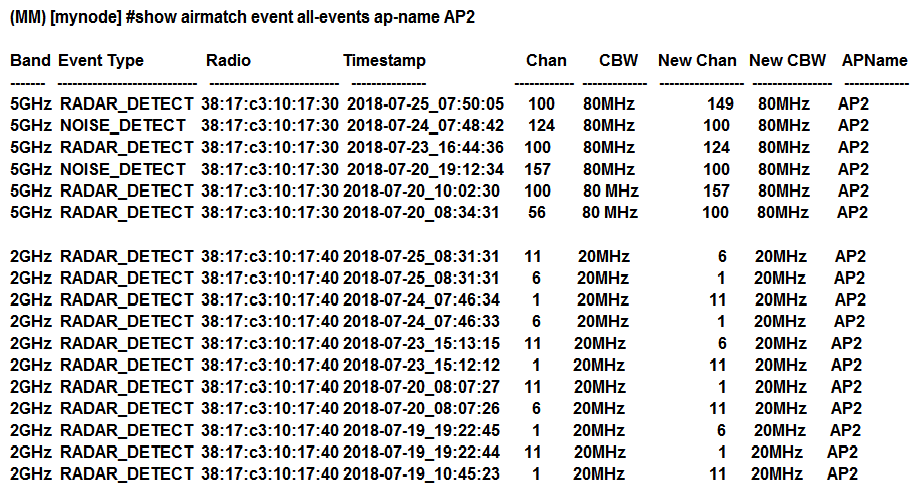 A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) network with APs in different locations. Users in one of the locations report that the WiFi network works fine for several hours, ang then they are suddenly disconnected. The symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?
A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) network with APs in different locations. Users in one of the locations report that the WiFi network works fine for several hours, ang then they are suddenly disconnected. The symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?
A) AirMatch is applying a scheduled optimization solution.
B) Users in the 2.4 GHz band are being affected by high interference.
C) Adpative Radio Management is reacting to RF events.
D) AirMatch is reacting to non-scheduled RF events.
 A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) network with APs in different locations. Users in one of the locations report that the WiFi network works fine for several hours, ang then they are suddenly disconnected. The symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?
A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) network with APs in different locations. Users in one of the locations report that the WiFi network works fine for several hours, ang then they are suddenly disconnected. The symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?A) AirMatch is applying a scheduled optimization solution.
B) Users in the 2.4 GHz band are being affected by high interference.
C) Adpative Radio Management is reacting to RF events.
D) AirMatch is reacting to non-scheduled RF events.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
7
A bank deploys an Aruba Mobility Master (MM)-Mobility Controller (MC) solution to provide wireless access for users that run different applications on their laptops, including SIP-based IP telephony. When users only run the IP telephony software, call quality is high. However, if users also run email, web, or mission critical applications, then voice quality drops. Which feature would help improve the quality of voice calls over the air when users run different applications?
A) DSCP for IPv4 traffic
B) WiFi Multi Media
C) Type of Service
D) High/Low Queue
A) DSCP for IPv4 traffic
B) WiFi Multi Media
C) Type of Service
D) High/Low Queue

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
8
Refer to the exhibit. 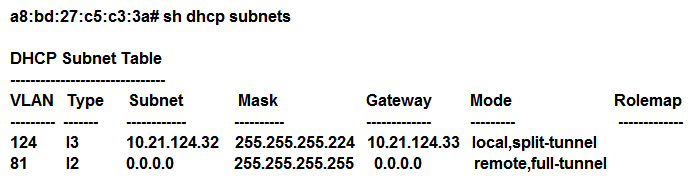 A network engineer deploys two different DHCP pools in an Instant AP (IAP) cluster for WLANs that will have connectivity to a remote site using Aruba IPSec. Based on the output shown in the exhibit, which IAP-VPN DHCP modes are being used?
A network engineer deploys two different DHCP pools in an Instant AP (IAP) cluster for WLANs that will have connectivity to a remote site using Aruba IPSec. Based on the output shown in the exhibit, which IAP-VPN DHCP modes are being used?
A) distributed L3 and centralized L3
B) distributed L3 and local L3
C) distributed L3 and centralized L2
D) local L3 and centralized L2
 A network engineer deploys two different DHCP pools in an Instant AP (IAP) cluster for WLANs that will have connectivity to a remote site using Aruba IPSec. Based on the output shown in the exhibit, which IAP-VPN DHCP modes are being used?
A network engineer deploys two different DHCP pools in an Instant AP (IAP) cluster for WLANs that will have connectivity to a remote site using Aruba IPSec. Based on the output shown in the exhibit, which IAP-VPN DHCP modes are being used?A) distributed L3 and centralized L3
B) distributed L3 and local L3
C) distributed L3 and centralized L2
D) local L3 and centralized L2

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
9
Refer to the exhibit. 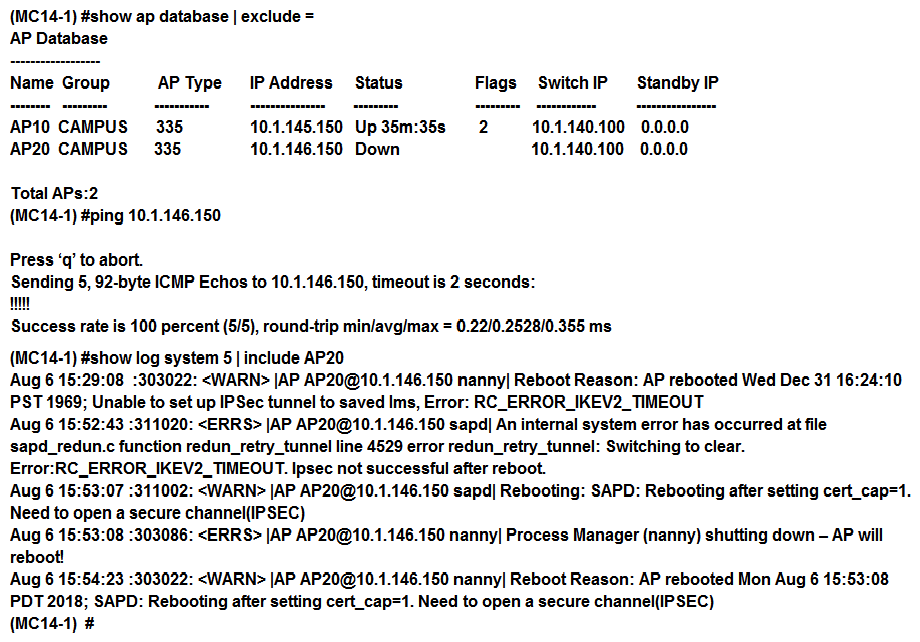 A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) solution in the headquarters. The network administrator prepares the wired side of the network with the proper VLAN, DHCP settings, and routing services to ensure that APs can reach the MCs. The network administrator connects two APs in different IP segments and waits for 20 minutes, but SSIDs are advertised in one of the APs only. The engineer logs into the MC console and sees the output shown in the exhibit. What is the reason that the AP20 is not broadcasting SSIDs?
A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) solution in the headquarters. The network administrator prepares the wired side of the network with the proper VLAN, DHCP settings, and routing services to ensure that APs can reach the MCs. The network administrator connects two APs in different IP segments and waits for 20 minutes, but SSIDs are advertised in one of the APs only. The engineer logs into the MC console and sees the output shown in the exhibit. What is the reason that the AP20 is not broadcasting SSIDs?
A) IPSec traffic is being blocked.
B) IKE traffic is being dropped.
C) PAPI traffic is being blocked.
D) GRE traffic is being blocked.
 A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) solution in the headquarters. The network administrator prepares the wired side of the network with the proper VLAN, DHCP settings, and routing services to ensure that APs can reach the MCs. The network administrator connects two APs in different IP segments and waits for 20 minutes, but SSIDs are advertised in one of the APs only. The engineer logs into the MC console and sees the output shown in the exhibit. What is the reason that the AP20 is not broadcasting SSIDs?
A network administrator deploys a Mobility Master (MM)-Mobility Controller (MC) solution in the headquarters. The network administrator prepares the wired side of the network with the proper VLAN, DHCP settings, and routing services to ensure that APs can reach the MCs. The network administrator connects two APs in different IP segments and waits for 20 minutes, but SSIDs are advertised in one of the APs only. The engineer logs into the MC console and sees the output shown in the exhibit. What is the reason that the AP20 is not broadcasting SSIDs?A) IPSec traffic is being blocked.
B) IKE traffic is being dropped.
C) PAPI traffic is being blocked.
D) GRE traffic is being blocked.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
10
Refer to the exhibit. 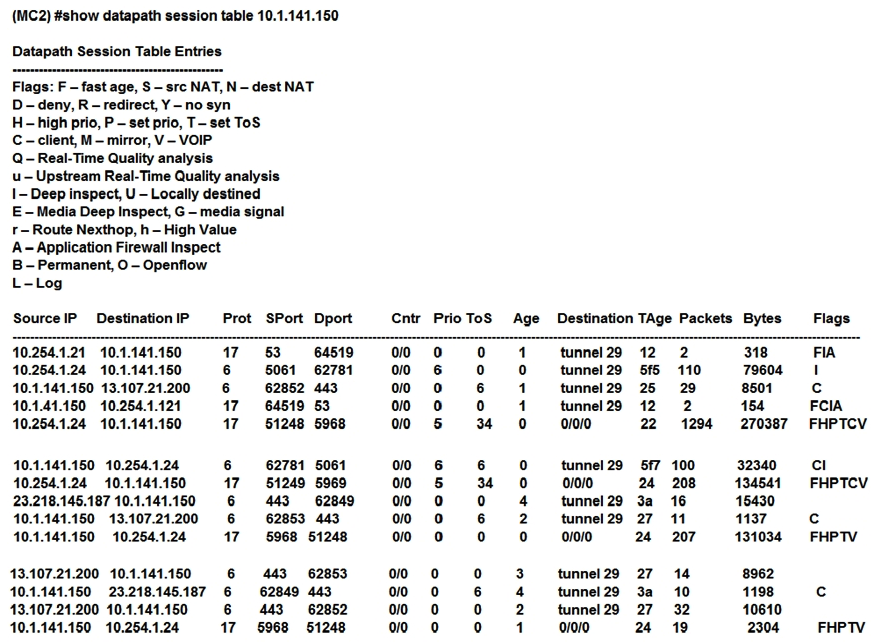 A network administrator deploys DSCP based prioritization in the entire wired network to improve voice quality for a SIP-based IP telephony system used by the company. However, users report that calls they make from the WLAN have poor audio quality, while desktop phones do not experience the same problem. The network administrator makes a test call and looks in the datapath session table. Based on the output shown in the exhibit, what is one area that the network administrator should focus on?
A network administrator deploys DSCP based prioritization in the entire wired network to improve voice quality for a SIP-based IP telephony system used by the company. However, users report that calls they make from the WLAN have poor audio quality, while desktop phones do not experience the same problem. The network administrator makes a test call and looks in the datapath session table. Based on the output shown in the exhibit, what is one area that the network administrator should focus on?
A) wireless network congestion
B) WMM support on the WLAN
C) UCC based DSCP correction
D) wired network congestion
 A network administrator deploys DSCP based prioritization in the entire wired network to improve voice quality for a SIP-based IP telephony system used by the company. However, users report that calls they make from the WLAN have poor audio quality, while desktop phones do not experience the same problem. The network administrator makes a test call and looks in the datapath session table. Based on the output shown in the exhibit, what is one area that the network administrator should focus on?
A network administrator deploys DSCP based prioritization in the entire wired network to improve voice quality for a SIP-based IP telephony system used by the company. However, users report that calls they make from the WLAN have poor audio quality, while desktop phones do not experience the same problem. The network administrator makes a test call and looks in the datapath session table. Based on the output shown in the exhibit, what is one area that the network administrator should focus on?A) wireless network congestion
B) WMM support on the WLAN
C) UCC based DSCP correction
D) wired network congestion

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
11
Users run encrypted Skype for Business traffic with no WMM support over an Aruba Mobility Master (MM)-Mobility Controller (MC) based network. When voice, video, and application sharing traffic arrive at the wired side of the network, all the flows look alike due the lack of L2 or L3 markings. How can the network administrator identify these flows and mark QoS accordingly?
A) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable WMM in a VAP profile.
B) Confirm the MM is the Openflow controller of the MCs and Openflow is enabled in VAP and the firewall roles. Then integrate the MM with the Skype4Business SDN API, and enable the Skype4Business ALG in the UCC Profiles.
C) Confirm the MC is the OpenFlow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable the Skype4Business ALG in the UCC profiles.
D) Use a media firewall policy that match these three flows, and use permit and TOS actions with 56, 40, and 34 values for voice, video, and application sharing, respectively. Then enable the Skype4Business ALG in the UCC profiles.
A) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable WMM in a VAP profile.
B) Confirm the MM is the Openflow controller of the MCs and Openflow is enabled in VAP and the firewall roles. Then integrate the MM with the Skype4Business SDN API, and enable the Skype4Business ALG in the UCC Profiles.
C) Confirm the MC is the OpenFlow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable the Skype4Business ALG in the UCC profiles.
D) Use a media firewall policy that match these three flows, and use permit and TOS actions with 56, 40, and 34 values for voice, video, and application sharing, respectively. Then enable the Skype4Business ALG in the UCC profiles.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
12
Refer to the exhibits. Exhibit1 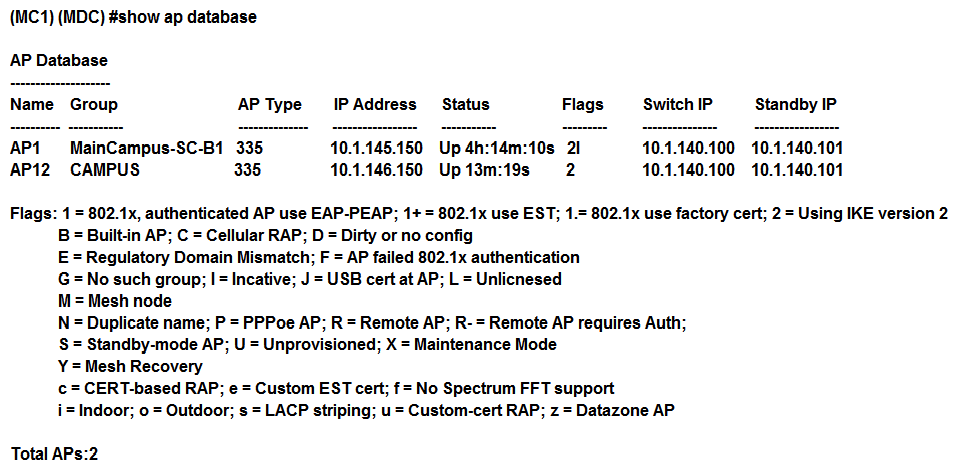 Exhibit 2
Exhibit 2 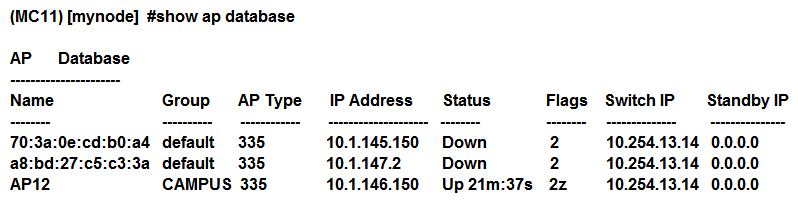 Based on outputs shown in the exhibits, what is the reason that AP12 is seen by two different controllers?
Based on outputs shown in the exhibits, what is the reason that AP12 is seen by two different controllers?
A) AP12 connects to a high availability group. MC1 is the active controller, and MC11 is the standby controller.
B) AP12 is a multizone AP. MC1 is part of the primary zone, and MC11 is part of the datazone.
C) AP12 connects to an MC cluster. MC1 is the A-AAC, and MC2 is S-AAC.
D) AP12 is in the middle of the boot process. MC1 is the master IP controller, and MC11 is the LMS IP controller.
 Exhibit 2
Exhibit 2  Based on outputs shown in the exhibits, what is the reason that AP12 is seen by two different controllers?
Based on outputs shown in the exhibits, what is the reason that AP12 is seen by two different controllers?A) AP12 connects to a high availability group. MC1 is the active controller, and MC11 is the standby controller.
B) AP12 is a multizone AP. MC1 is part of the primary zone, and MC11 is part of the datazone.
C) AP12 connects to an MC cluster. MC1 is the A-AAC, and MC2 is S-AAC.
D) AP12 is in the middle of the boot process. MC1 is the master IP controller, and MC11 is the LMS IP controller.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
13
Refer to the exhibit. 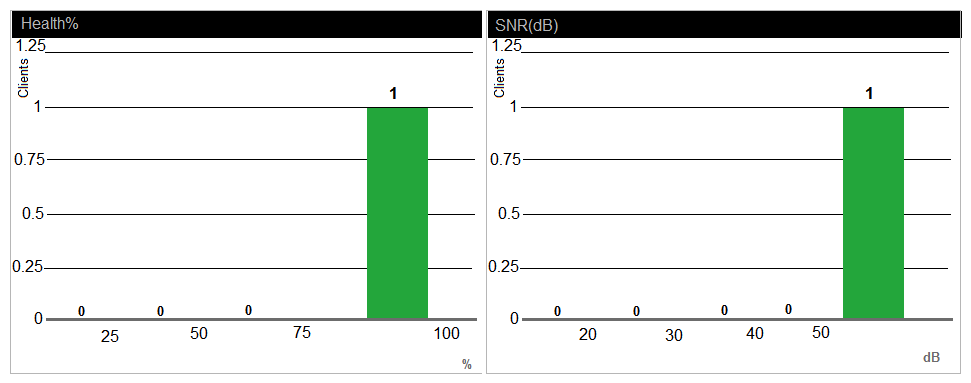
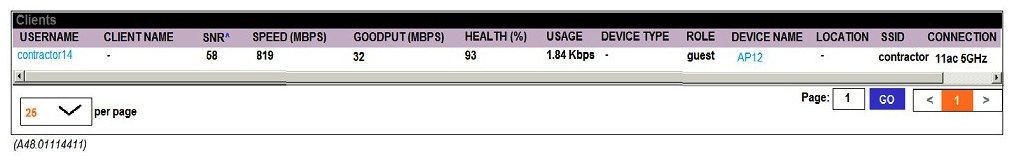 A network administrator receives a call from a contractor that was recently given wireless access to the network. The user reports that the response time is slow and suggests there might be a problem with the WLAN. The network administrator checks RF performance in AirWave to find the user and sees the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A network administrator receives a call from a contractor that was recently given wireless access to the network. The user reports that the response time is slow and suggests there might be a problem with the WLAN. The network administrator checks RF performance in AirWave to find the user and sees the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A) Client health and CNR are high, therefore, it is unlikely the client is experiencing an RF-related issue.
B) Goodput is low in relation to connection speed, which suggests a channel with high utilization, another channel should be used.
C) Client health and SNR are high but usage is low; therefore, there might be packet drops.
D) Client health is low, which suggests that there are packet drops and collisions in the RF environment.

 A network administrator receives a call from a contractor that was recently given wireless access to the network. The user reports that the response time is slow and suggests there might be a problem with the WLAN. The network administrator checks RF performance in AirWave to find the user and sees the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A network administrator receives a call from a contractor that was recently given wireless access to the network. The user reports that the response time is slow and suggests there might be a problem with the WLAN. The network administrator checks RF performance in AirWave to find the user and sees the output shown in the exhibit. What can the network administrator conclude after analyzing the data?A) Client health and CNR are high, therefore, it is unlikely the client is experiencing an RF-related issue.
B) Goodput is low in relation to connection speed, which suggests a channel with high utilization, another channel should be used.
C) Client health and SNR are high but usage is low; therefore, there might be packet drops.
D) Client health is low, which suggests that there are packet drops and collisions in the RF environment.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
14
Refer to the exhibit. 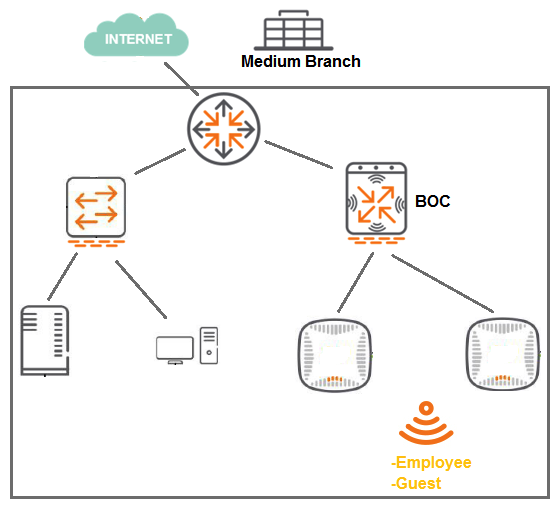 A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core router does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Select two.)
A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core router does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Select two.)
A) Configure all ports of the BOC as access ports on the controller VLAN, and change the gateway of clients to the core router IP.
B) Configure the uplink of the BOC as an access port on the controller VLAN, and enable NAT for the SSID VLANs.
C) Configure the uplink of the BOC as a trunk port, tagging the controller and the SSID VLANs, and enable NAT for the SSID VLANs.
D) Configure the uplink of the BOC as an access port on the controller VLAN, and add static router in the router for the SSID VLAN subnets.
E) Configure the uplink of the BOC as a trunk port that permits the controller and the SSID VLANs. The controller VLAN must be native.
 A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core router does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Select two.)
A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core router does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Select two.)A) Configure all ports of the BOC as access ports on the controller VLAN, and change the gateway of clients to the core router IP.
B) Configure the uplink of the BOC as an access port on the controller VLAN, and enable NAT for the SSID VLANs.
C) Configure the uplink of the BOC as a trunk port, tagging the controller and the SSID VLANs, and enable NAT for the SSID VLANs.
D) Configure the uplink of the BOC as an access port on the controller VLAN, and add static router in the router for the SSID VLAN subnets.
E) Configure the uplink of the BOC as a trunk port that permits the controller and the SSID VLANs. The controller VLAN must be native.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
15
Refer to the exhibit. 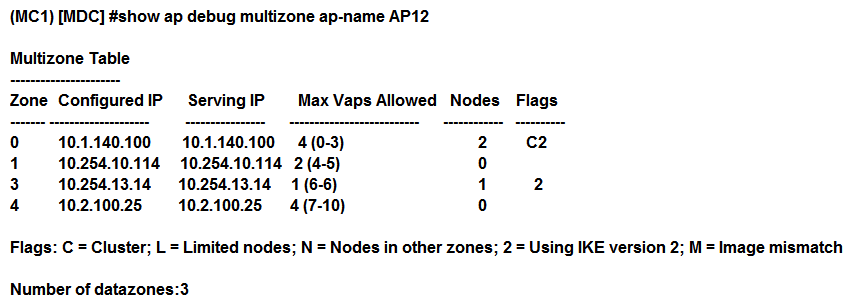 A network administrator deploys a multizone AP in the campus network in order to provide service for 11 SSIDs. After a few hours, the network administrator realizes that the AP is only broadcasting 5 out of the 11 SSIDs. The missing SSIDs belong to MC1 at IP address 10.254.10.114, and MC4 with IP address 10.2.100.25. Based on the exhibit, what should the network administrator do next to fix this problem?
A network administrator deploys a multizone AP in the campus network in order to provide service for 11 SSIDs. After a few hours, the network administrator realizes that the AP is only broadcasting 5 out of the 11 SSIDs. The missing SSIDs belong to MC1 at IP address 10.254.10.114, and MC4 with IP address 10.2.100.25. Based on the exhibit, what should the network administrator do next to fix this problem?
A) Confirm that AP12 is certified by the whitelist on MC1 and MC4, and confirm MC1 and MC4 are reachable by AP12.
B) Increase the number of nodes in zones 1 and 4, and confirm MC1 and MC4 are reachable by AP12.
C) Confirm that AP12 is certified by the whitelist on MC1 and MC4, and increase the number of nodes in zones 1 and 4.
D) Reduce the number of nodes in zones 0 and 4, and disband the cluster in zone 0.
 A network administrator deploys a multizone AP in the campus network in order to provide service for 11 SSIDs. After a few hours, the network administrator realizes that the AP is only broadcasting 5 out of the 11 SSIDs. The missing SSIDs belong to MC1 at IP address 10.254.10.114, and MC4 with IP address 10.2.100.25. Based on the exhibit, what should the network administrator do next to fix this problem?
A network administrator deploys a multizone AP in the campus network in order to provide service for 11 SSIDs. After a few hours, the network administrator realizes that the AP is only broadcasting 5 out of the 11 SSIDs. The missing SSIDs belong to MC1 at IP address 10.254.10.114, and MC4 with IP address 10.2.100.25. Based on the exhibit, what should the network administrator do next to fix this problem?A) Confirm that AP12 is certified by the whitelist on MC1 and MC4, and confirm MC1 and MC4 are reachable by AP12.
B) Increase the number of nodes in zones 1 and 4, and confirm MC1 and MC4 are reachable by AP12.
C) Confirm that AP12 is certified by the whitelist on MC1 and MC4, and increase the number of nodes in zones 1 and 4.
D) Reduce the number of nodes in zones 0 and 4, and disband the cluster in zone 0.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
16
A customer with a multi-controller network upgrades the ArubaOS from 6.4 to 8. The customer's clients must be able to move between different locations of the campus without disconnecting their applications, when roaming or if there are Mobility Controller (MC) failures. The customer also wants to have full control of the users, and be able to change their session properties from a RADIUS server. Which steps must the network consultant include in the implementation plan to meet these requirements?
A) 1. Create a controller cluster profile that contains the management and VRRP IP addresses of each member. 2. Apply the profile to all MCs in the cluster. 3. Confirm that the cluster is L2 connected.
B) 1. Configure a VRRP instance for all MCs 2. Create a controller cluster profile that contains the management IP and VIP addresses of each MC. 3. Apply the profile to all MCs in the cluster. 4. Confirm that the cluster is L2 connected.
C) 1. Configure a VRRP instance for each MC. 2. Create a controller cluster profile that contains the management IP of each member. 4. Confirm that the cluster is L3 connected.
D) 2. Apply the profile to the cluster leader.
A) 1. Create a controller cluster profile that contains the management and VRRP IP addresses of each member. 2. Apply the profile to all MCs in the cluster. 3. Confirm that the cluster is L2 connected.
B) 1. Configure a VRRP instance for all MCs 2. Create a controller cluster profile that contains the management IP and VIP addresses of each MC. 3. Apply the profile to all MCs in the cluster. 4. Confirm that the cluster is L2 connected.
C) 1. Configure a VRRP instance for each MC. 2. Create a controller cluster profile that contains the management IP of each member. 4. Confirm that the cluster is L3 connected.
D) 2. Apply the profile to the cluster leader.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
17
Refer to the exhibits. Exhibit 1 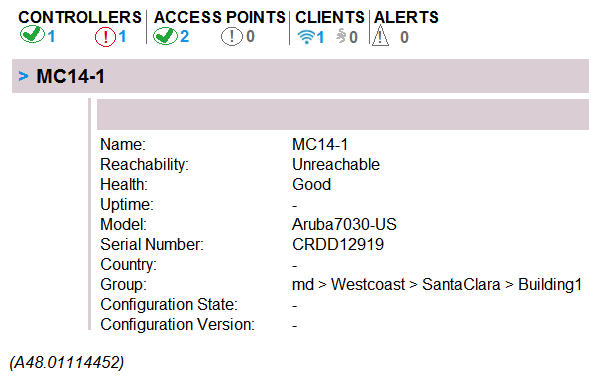 Exhibit 2
Exhibit 2 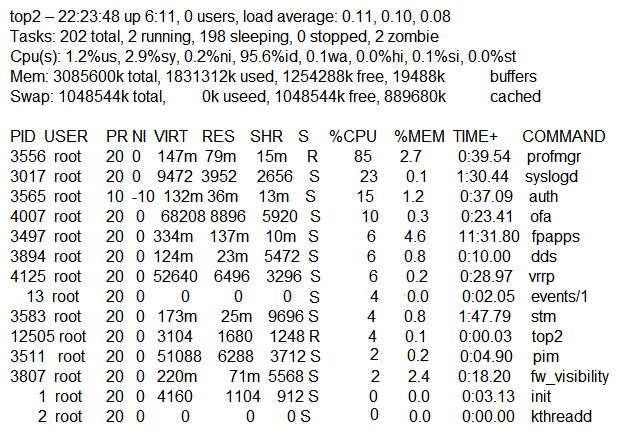 A network administrator adds a new Mobility Controller (MC) to the production Mobility Master (MM) and deploys APs that start broadcasting the employees SSID in the West wing of the building. Suddenly, the employed report client disconnects. When accessing the MM the network administrator notices that the MC is unreachable, then proceeds to access the MC's console and obtains the outputs shown in the exhibits. What should the network administrator do next to solve the current problem?
A network administrator adds a new Mobility Controller (MC) to the production Mobility Master (MM) and deploys APs that start broadcasting the employees SSID in the West wing of the building. Suddenly, the employed report client disconnects. When accessing the MM the network administrator notices that the MC is unreachable, then proceeds to access the MC's console and obtains the outputs shown in the exhibits. What should the network administrator do next to solve the current problem?
A) Decommission the MC from the MM, and add it again.
B) Open a TAC case, and send the output of tar crash.
C) Verify the license pools in the MM.
D) Kill two zombie processes, then reboot the MC.
 Exhibit 2
Exhibit 2  A network administrator adds a new Mobility Controller (MC) to the production Mobility Master (MM) and deploys APs that start broadcasting the employees SSID in the West wing of the building. Suddenly, the employed report client disconnects. When accessing the MM the network administrator notices that the MC is unreachable, then proceeds to access the MC's console and obtains the outputs shown in the exhibits. What should the network administrator do next to solve the current problem?
A network administrator adds a new Mobility Controller (MC) to the production Mobility Master (MM) and deploys APs that start broadcasting the employees SSID in the West wing of the building. Suddenly, the employed report client disconnects. When accessing the MM the network administrator notices that the MC is unreachable, then proceeds to access the MC's console and obtains the outputs shown in the exhibits. What should the network administrator do next to solve the current problem?A) Decommission the MC from the MM, and add it again.
B) Open a TAC case, and send the output of tar crash.
C) Verify the license pools in the MM.
D) Kill two zombie processes, then reboot the MC.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
18
An organization owns a fully functional multi-controller Aruba network with a Virtual Mobility Master (VMM) in VLAN 20. They have asked a network consultant to deploy a redundant MM on a different server. The solution must offer the lowest convergence time and require no human interaction in case of failure. The servers host other virtual machines and are connected to different switches that implement ACLs to protect them. The organization grants the network consultant access to the servers only, and appoints a network administrator to assist with the deployment. What must the network administrator do so the network consultant can successfully deploy the solution? (Select three.)
A) Reserve one IP address for the second MM and another IP address for its gateway
B) Configure an ACL entry that permits IP protocol 50, UDP port 500, and multicast IP 224.0.0.18.
C) Allocate VLAN 20 to the second server, and extend it throughout the switches.
D) Reserve one IP address for the second MM and another for the VIP.
E) Configure an ACL entry that permits UDP 500, UDP 4500, and multicast IP 224.0.0.1.
F) Allocate another VLAN to the second server, and permit routing between them.
A) Reserve one IP address for the second MM and another IP address for its gateway
B) Configure an ACL entry that permits IP protocol 50, UDP port 500, and multicast IP 224.0.0.18.
C) Allocate VLAN 20 to the second server, and extend it throughout the switches.
D) Reserve one IP address for the second MM and another for the VIP.
E) Configure an ACL entry that permits UDP 500, UDP 4500, and multicast IP 224.0.0.1.
F) Allocate another VLAN to the second server, and permit routing between them.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
19
Refer to exhibit. 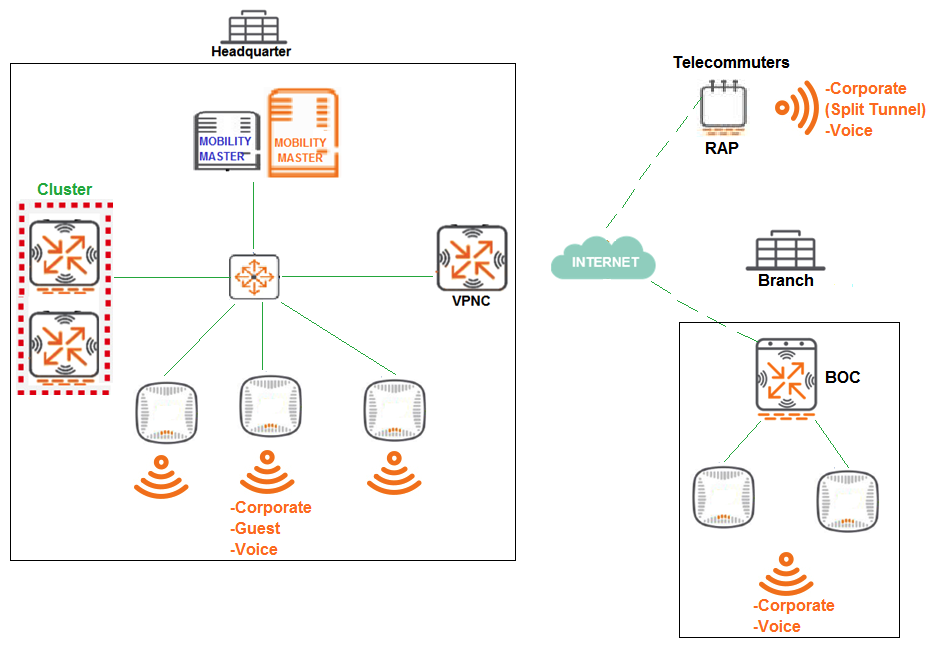 A company has a multiple Arua implementation with three different locations named Headquarter, Branch, and Telecommuters. The network design includes the following: Headquarter APs terminate at the Mobility Controller (MC) cluster and propagate Corporate, Guest, and Voice SSIDs Branch APs terminate at the Branch Office Controller (BOC) and propagate Corporate and Voice SSIDs BOC reaches the Mobility Master (MM) through a VPNC. Telecommuter RAPs terminate at VPNC and propagate Corporate and Voice SSIDs. The Corporate SSID on the RAPs is split-tunnel, all other SSIDs are tunnel. The network design requires minimal AP group and VAP configuration effor, while preventing unnecessary VAP propagation to lower hierarchy levels. Following Aruba node hierarchy desing recommendations, which group hierarchy design helps meet these requirements?
A company has a multiple Arua implementation with three different locations named Headquarter, Branch, and Telecommuters. The network design includes the following: Headquarter APs terminate at the Mobility Controller (MC) cluster and propagate Corporate, Guest, and Voice SSIDs Branch APs terminate at the Branch Office Controller (BOC) and propagate Corporate and Voice SSIDs BOC reaches the Mobility Master (MM) through a VPNC. Telecommuter RAPs terminate at VPNC and propagate Corporate and Voice SSIDs. The Corporate SSID on the RAPs is split-tunnel, all other SSIDs are tunnel. The network design requires minimal AP group and VAP configuration effor, while preventing unnecessary VAP propagation to lower hierarchy levels. Following Aruba node hierarchy desing recommendations, which group hierarchy design helps meet these requirements?
A) /md /md/Corp1/ /md/Corp1/Offices /md/Corp1/Offices/Headquarter /md/Corp1/Offices/Branch /md/Corp1/Telecommuters /mm /mm/mynode
B) /md/Headquarter /md/Branch /md/Telecommuters
C) /md/Locations /md/Locations/Headquarter /md/Locations/Branch /md/Locations/Telecommuters
D) /md/Location1/ /md/Location1/Branch /mdLocation1/Offices /md/Location1/Offices/Headquarter /md/Location1/Telecommuters
 A company has a multiple Arua implementation with three different locations named Headquarter, Branch, and Telecommuters. The network design includes the following: Headquarter APs terminate at the Mobility Controller (MC) cluster and propagate Corporate, Guest, and Voice SSIDs Branch APs terminate at the Branch Office Controller (BOC) and propagate Corporate and Voice SSIDs BOC reaches the Mobility Master (MM) through a VPNC. Telecommuter RAPs terminate at VPNC and propagate Corporate and Voice SSIDs. The Corporate SSID on the RAPs is split-tunnel, all other SSIDs are tunnel. The network design requires minimal AP group and VAP configuration effor, while preventing unnecessary VAP propagation to lower hierarchy levels. Following Aruba node hierarchy desing recommendations, which group hierarchy design helps meet these requirements?
A company has a multiple Arua implementation with three different locations named Headquarter, Branch, and Telecommuters. The network design includes the following: Headquarter APs terminate at the Mobility Controller (MC) cluster and propagate Corporate, Guest, and Voice SSIDs Branch APs terminate at the Branch Office Controller (BOC) and propagate Corporate and Voice SSIDs BOC reaches the Mobility Master (MM) through a VPNC. Telecommuter RAPs terminate at VPNC and propagate Corporate and Voice SSIDs. The Corporate SSID on the RAPs is split-tunnel, all other SSIDs are tunnel. The network design requires minimal AP group and VAP configuration effor, while preventing unnecessary VAP propagation to lower hierarchy levels. Following Aruba node hierarchy desing recommendations, which group hierarchy design helps meet these requirements?A) /md /md/Corp1/ /md/Corp1/Offices /md/Corp1/Offices/Headquarter /md/Corp1/Offices/Branch /md/Corp1/Telecommuters /mm /mm/mynode
B) /md/Headquarter /md/Branch /md/Telecommuters
C) /md/Locations /md/Locations/Headquarter /md/Locations/Branch /md/Locations/Telecommuters
D) /md/Location1/ /md/Location1/Branch /mdLocation1/Offices /md/Location1/Offices/Headquarter /md/Location1/Telecommuters

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
20
Refer to the exhibits. Exhibit1 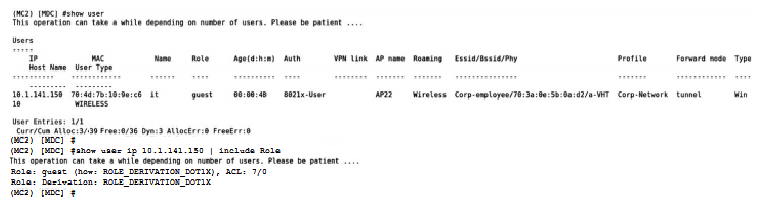 Exhibit2
Exhibit2 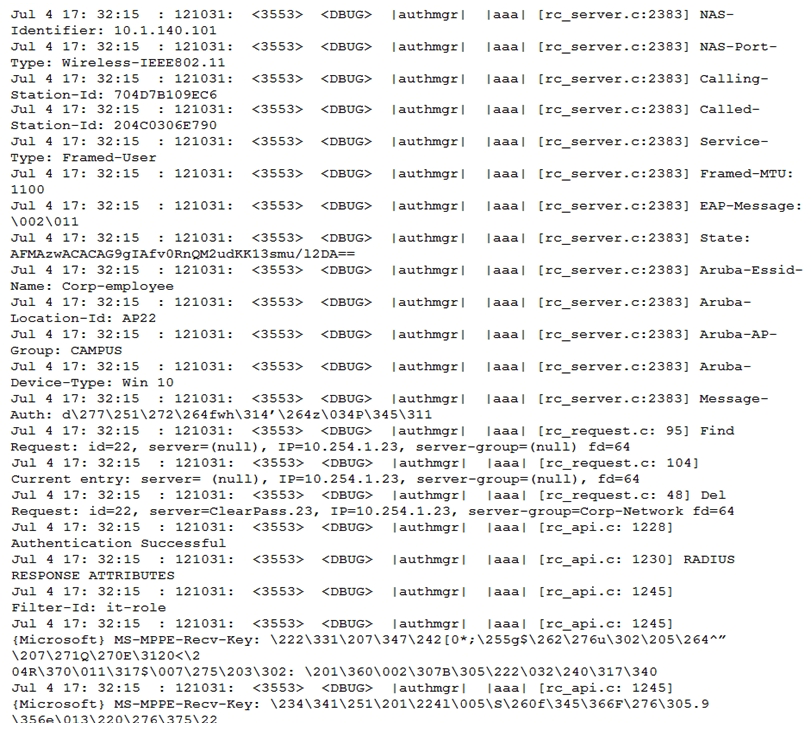 A network administrator integrates a current Mobility Master (MM)-Mobility Controller (MC) deployment with a RADIUS infrastructure. After using the RADIUS server to authenticate a wireless user, the network administrator realizes that the client machine is not falling into the it_department role, as shown in the exhibits. Which configuration is required to map the users into the proper role, based on standard attributes returned by the RADIUS server in the Access Accept message?
A network administrator integrates a current Mobility Master (MM)-Mobility Controller (MC) deployment with a RADIUS infrastructure. After using the RADIUS server to authenticate a wireless user, the network administrator realizes that the client machine is not falling into the it_department role, as shown in the exhibits. Which configuration is required to map the users into the proper role, based on standard attributes returned by the RADIUS server in the Access Accept message?
A) aaa server-group Corp-Network set role condition Filter-Id equals it-role set-value it_department
B) aaa server-group GROUP-RADIUS
C) aaa server-group Corp-employee
D) set role condition Filter-Id value-of
 Exhibit2
Exhibit2  A network administrator integrates a current Mobility Master (MM)-Mobility Controller (MC) deployment with a RADIUS infrastructure. After using the RADIUS server to authenticate a wireless user, the network administrator realizes that the client machine is not falling into the it_department role, as shown in the exhibits. Which configuration is required to map the users into the proper role, based on standard attributes returned by the RADIUS server in the Access Accept message?
A network administrator integrates a current Mobility Master (MM)-Mobility Controller (MC) deployment with a RADIUS infrastructure. After using the RADIUS server to authenticate a wireless user, the network administrator realizes that the client machine is not falling into the it_department role, as shown in the exhibits. Which configuration is required to map the users into the proper role, based on standard attributes returned by the RADIUS server in the Access Accept message?A) aaa server-group Corp-Network set role condition Filter-Id equals it-role set-value it_department
B) aaa server-group GROUP-RADIUS
C) aaa server-group Corp-employee
D) set role condition Filter-Id value-of

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
21
Refer to the exhibit. 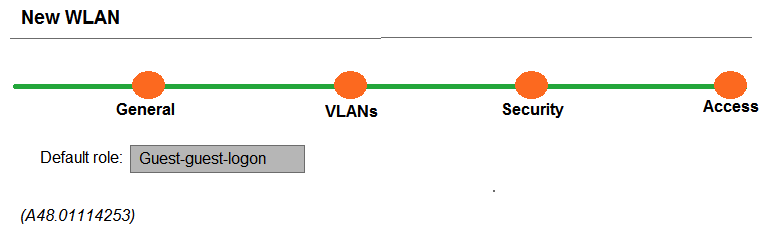 A network administrator completes the task to cretae a WLAN, as shown in the exhibit. The network administrator selects the options to use guest as primary usage and Internal captive portal with authentication in the security step. Next, the network administrator creates a policy that denies access to the internal network. Which additional step must the network administrator complete in order to prevent authenticated users from reaching internal corporate resources while allowing Internet access?
A network administrator completes the task to cretae a WLAN, as shown in the exhibit. The network administrator selects the options to use guest as primary usage and Internal captive portal with authentication in the security step. Next, the network administrator creates a policy that denies access to the internal network. Which additional step must the network administrator complete in order to prevent authenticated users from reaching internal corporate resources while allowing Internet access?
A) Apply the policy on the guest-guest-logon role.
B) Apply the policy on the authenticated role.
C) Apply the policy on the guest role.
D) Create a policy that permits dhcp, dns, and http access.
 A network administrator completes the task to cretae a WLAN, as shown in the exhibit. The network administrator selects the options to use guest as primary usage and Internal captive portal with authentication in the security step. Next, the network administrator creates a policy that denies access to the internal network. Which additional step must the network administrator complete in order to prevent authenticated users from reaching internal corporate resources while allowing Internet access?
A network administrator completes the task to cretae a WLAN, as shown in the exhibit. The network administrator selects the options to use guest as primary usage and Internal captive portal with authentication in the security step. Next, the network administrator creates a policy that denies access to the internal network. Which additional step must the network administrator complete in order to prevent authenticated users from reaching internal corporate resources while allowing Internet access?A) Apply the policy on the guest-guest-logon role.
B) Apply the policy on the authenticated role.
C) Apply the policy on the guest role.
D) Create a policy that permits dhcp, dns, and http access.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
22
A foreign exchange broker in a shared office space uses an Aruba Mobility Master (MM)-Mobility Controller (MC) architecture along with ClearPass and AirWave. The corporate network is FXBroker121, but users report that they cannot access the FXBroker111 SSID. The team suspects that a rogue AP is in place and a malicious user tried to disguise the WLAN name. How can the organization's network administrator identify and locate the potential rogue AP?
A) Create an AirWave RAPIDS rule with a Suspected Rogue classification and the SSID Matches FXBroker111 condition, then access any RAPID List entry that matches the rule and click on Location.
B) Use ClearPass Event viewer and search for entries with the FXBroker111 Aruba-Essid-Name VSA attribute, then obtain the value of the Aruba-AP-Group attribute.
C) Use ClearPass Event viewer and search for entries with the FXBroker111 Aruba-Essid-Name VSA attribute, then obtain the value of the Aruba-Location-id attribute.
D) Create and AirWave RAPIDS rule with a Suspected Rogue classification and the SSID Does Not Match FXBroker121 condition, then access any RAPIDS List entry that matches the rule and click on Location.
A) Create an AirWave RAPIDS rule with a Suspected Rogue classification and the SSID Matches FXBroker111 condition, then access any RAPID List entry that matches the rule and click on Location.
B) Use ClearPass Event viewer and search for entries with the FXBroker111 Aruba-Essid-Name VSA attribute, then obtain the value of the Aruba-AP-Group attribute.
C) Use ClearPass Event viewer and search for entries with the FXBroker111 Aruba-Essid-Name VSA attribute, then obtain the value of the Aruba-Location-id attribute.
D) Create and AirWave RAPIDS rule with a Suspected Rogue classification and the SSID Does Not Match FXBroker121 condition, then access any RAPIDS List entry that matches the rule and click on Location.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
23
Refer to the exhibit. 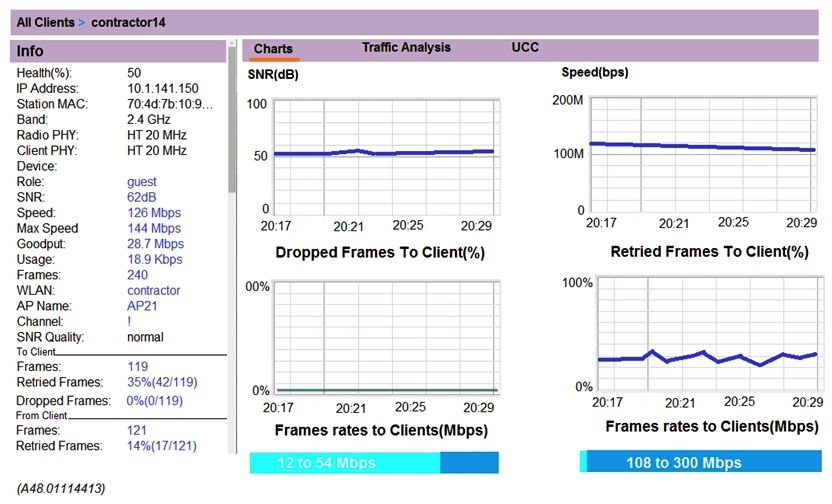 A user reports show response time to a network administrator and suggests that there might be a problem with the WLAN. The user's laptop supports 802.11n in the 2.4 GHz band only. The network administrator finds the user on the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A user reports show response time to a network administrator and suggests that there might be a problem with the WLAN. The user's laptop supports 802.11n in the 2.4 GHz band only. The network administrator finds the user on the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A) Client health is low, and retried frames are high. It is possible there is high channel utilization.
B) Client health is low, but SNR is high. It is possible data in the dashboard is not accurate and needs to be updated.
C) The speed is good. Client health seems to be related to a problem with the client NIC.
D) The network is low because of low SNR. TX power must be increased in both the client and the AP.
 A user reports show response time to a network administrator and suggests that there might be a problem with the WLAN. The user's laptop supports 802.11n in the 2.4 GHz band only. The network administrator finds the user on the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A user reports show response time to a network administrator and suggests that there might be a problem with the WLAN. The user's laptop supports 802.11n in the 2.4 GHz band only. The network administrator finds the user on the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?A) Client health is low, and retried frames are high. It is possible there is high channel utilization.
B) Client health is low, but SNR is high. It is possible data in the dashboard is not accurate and needs to be updated.
C) The speed is good. Client health seems to be related to a problem with the client NIC.
D) The network is low because of low SNR. TX power must be increased in both the client and the AP.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
24
An airline wants to invest in an Aruba Mobility (MM)-Mobility Controller (MC) solution for the three hubs it has throughout the country. A single MM is located in the datacenter at one of the hubs. The MCs in the other two hubs reach the MM through a site-to-site IPSec VPN. The operations team does not want to lose monitoring and configuration control of the MCs if something happens to the datacenter where the MM resides. Which solution ensures that there is management access to the MCs in case of an MM failure due to a datacenter outage?
A) Deploy another MM in a different location, and enable L2 redundancy.
B) Install AirWave Management Platform, and enable Read and Write Management access on devices.
C) Deploy another MM in a different location, and enable L3 redundancy.
D) Deploy a local MM on each hub, and synchronize the configuration between all MMs.
A) Deploy another MM in a different location, and enable L2 redundancy.
B) Install AirWave Management Platform, and enable Read and Write Management access on devices.
C) Deploy another MM in a different location, and enable L3 redundancy.
D) Deploy a local MM on each hub, and synchronize the configuration between all MMs.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
25
A point venture between two companies results in a fully functional WLAN Aruba solution. The network administrator uses the following script to integrate the WLAN solution with two radius servers, radius1 and radius2. 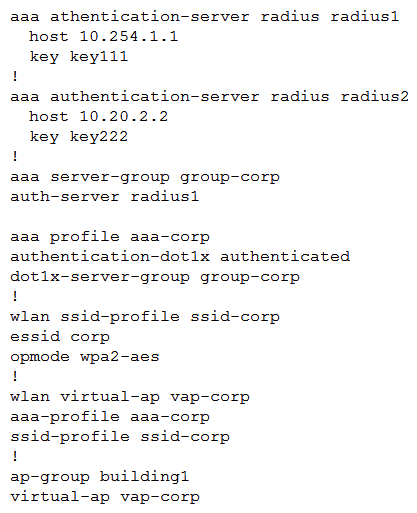 While all users authenticate with username@doaminname.com type of credentials, radius1 has user accounts without the domain name portion. Which additional configuration is required to authenticate corp1.com users with radius1 and corp2 users with radius2?
While all users authenticate with username@doaminname.com type of credentials, radius1 has user accounts without the domain name portion. Which additional configuration is required to authenticate corp1.com users with radius1 and corp2 users with radius2?
A) aaa authentication-server radius radius1 trim-fqdn ! aaa server-group-corp auth-server radius1 match-authstring corp1.com auth-server radius1 match-authstring corp2.com
B) auth-server radius1 match-fqdn corp1.com auth-server radius1 trim-fqdn auth-server radius2 match-fqdn corp2.com
C) aaa authentication-server tadius radius1 auth-server radius1 match-string corp1.com trim-fqdn auth-server radius1 match-string corp2.com
D) auth-server radius1 match-domain corp1.com auth-server radius1 match-domain corp2.com
 While all users authenticate with username@doaminname.com type of credentials, radius1 has user accounts without the domain name portion. Which additional configuration is required to authenticate corp1.com users with radius1 and corp2 users with radius2?
While all users authenticate with username@doaminname.com type of credentials, radius1 has user accounts without the domain name portion. Which additional configuration is required to authenticate corp1.com users with radius1 and corp2 users with radius2?A) aaa authentication-server radius radius1 trim-fqdn ! aaa server-group-corp auth-server radius1 match-authstring corp1.com auth-server radius1 match-authstring corp2.com
B) auth-server radius1 match-fqdn corp1.com auth-server radius1 trim-fqdn auth-server radius2 match-fqdn corp2.com
C) aaa authentication-server tadius radius1 auth-server radius1 match-string corp1.com trim-fqdn auth-server radius1 match-string corp2.com
D) auth-server radius1 match-domain corp1.com auth-server radius1 match-domain corp2.com

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
26
Refer to the exhibit. 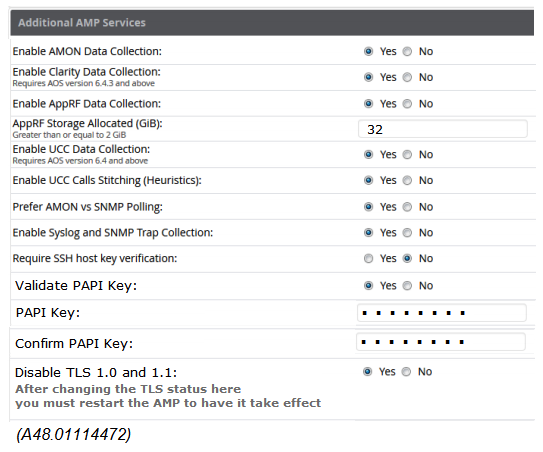 A network administrator configures a Mobility Master (MM)-Mobility Controller (MC) solution and integrates it with AirWave. The network administrator configures the SNMP and terminal credentials in the MM and MC, and then monitors the mobility devices from AirWave, including Clarity for user association and basic network services verification. However, AirWave does not display any UCC data that is available in the MM dashboard. Based on the information shown in the exhibit, which configuration step should the network administrator do next in the MM to complete the integration with AirWave?
A network administrator configures a Mobility Master (MM)-Mobility Controller (MC) solution and integrates it with AirWave. The network administrator configures the SNMP and terminal credentials in the MM and MC, and then monitors the mobility devices from AirWave, including Clarity for user association and basic network services verification. However, AirWave does not display any UCC data that is available in the MM dashboard. Based on the information shown in the exhibit, which configuration step should the network administrator do next in the MM to complete the integration with AirWave?
A) Define AirWave as a management server in the MM.
B) Enable the inline network services statistics in the AMP profile.
C) Enable UCC monitoring in the AMP profile.
D) Verify the papi-security key in the AMP profile.
 A network administrator configures a Mobility Master (MM)-Mobility Controller (MC) solution and integrates it with AirWave. The network administrator configures the SNMP and terminal credentials in the MM and MC, and then monitors the mobility devices from AirWave, including Clarity for user association and basic network services verification. However, AirWave does not display any UCC data that is available in the MM dashboard. Based on the information shown in the exhibit, which configuration step should the network administrator do next in the MM to complete the integration with AirWave?
A network administrator configures a Mobility Master (MM)-Mobility Controller (MC) solution and integrates it with AirWave. The network administrator configures the SNMP and terminal credentials in the MM and MC, and then monitors the mobility devices from AirWave, including Clarity for user association and basic network services verification. However, AirWave does not display any UCC data that is available in the MM dashboard. Based on the information shown in the exhibit, which configuration step should the network administrator do next in the MM to complete the integration with AirWave?A) Define AirWave as a management server in the MM.
B) Enable the inline network services statistics in the AMP profile.
C) Enable UCC monitoring in the AMP profile.
D) Verify the papi-security key in the AMP profile.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
27
A network administrator deploys APs with radios in Air Monitor mode and detects several APs and SSIDs that belong to stores next door. The Mobility Master (MM) classifies the APs and SSIDs as potential rogues. The network administrator wants to prevent the Air Monitor from applying countermeasures against these APs. How can the network administrator accomplish this?
A) Select the BSSID and click reclassify, then select neighbor.
B) Run the Define WIP Policy task, and define the BSSIDs of the neighboring APs as interfering.
C) Select the BSSID and click reclassify, then select interfering.
D) Run the Define WIP Policy task, and define the BSSIDs of the neighboring APs as Authorized.
A) Select the BSSID and click reclassify, then select neighbor.
B) Run the Define WIP Policy task, and define the BSSIDs of the neighboring APs as interfering.
C) Select the BSSID and click reclassify, then select interfering.
D) Run the Define WIP Policy task, and define the BSSIDs of the neighboring APs as Authorized.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
28
Refer to the exhibit. 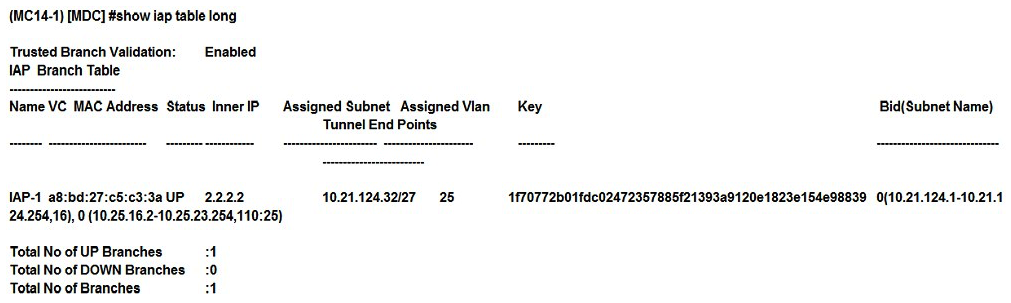 A network administrator configures an Instant AP (IAP) to establish an Aruba IPSec tunnel across the Internet, and configures two DHCP pools for wireless users. Based on the output shown in the exhibit, which device behaves as a DHCP server for the users?
A network administrator configures an Instant AP (IAP) to establish an Aruba IPSec tunnel across the Internet, and configures two DHCP pools for wireless users. Based on the output shown in the exhibit, which device behaves as a DHCP server for the users?
A) Mobility Master
B) Mobility Controller
C) External server
D) DSL modem
E) Virtual Controller
 A network administrator configures an Instant AP (IAP) to establish an Aruba IPSec tunnel across the Internet, and configures two DHCP pools for wireless users. Based on the output shown in the exhibit, which device behaves as a DHCP server for the users?
A network administrator configures an Instant AP (IAP) to establish an Aruba IPSec tunnel across the Internet, and configures two DHCP pools for wireless users. Based on the output shown in the exhibit, which device behaves as a DHCP server for the users?A) Mobility Master
B) Mobility Controller
C) External server
D) DSL modem
E) Virtual Controller

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
29
A financial institution contacts an Aruba partner to deploy an advanced and secure Mobility Master (MM)-Mobility Controller (MC) WLAN solution in its main campus and 14 small offices/home offices (SOHOs). Key requirements are that users at all locations, including telecommuters with VIA, should be assigned roles with policies that filter undesired traffic. Also, advanced WIPs should be enforced at the campus only. These are additional requirements for this deployment: RAPs should ship directly to their final destinations without any pre-setup and should come up with the right configuration as soon as they get Internet access. Activate should be configured with devices MACs, serial numbers, and provisioning rules that redirect them to the standalone VMC at the DMZ Users should be able to reach DNS, FTP, Web and telephone servers in the campus as well as send and receive IP telephone calls to and from the voice 10.1.50.0/24 segment. Local Internet access should be granted. Refer to the exhibit. 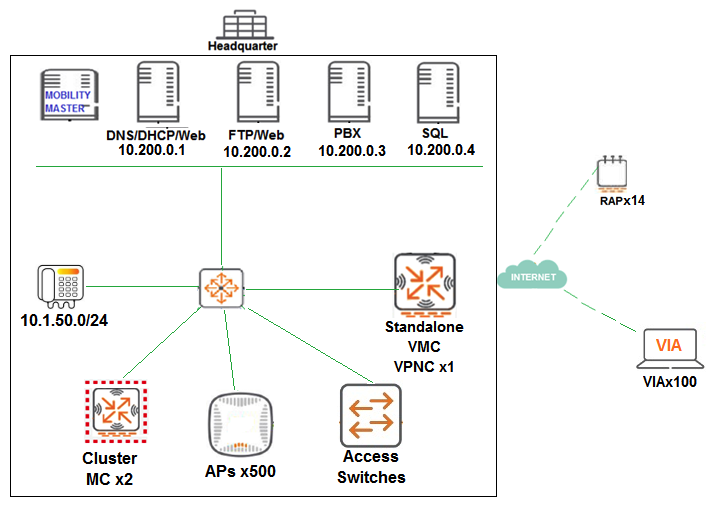 Refer to the scenario and the exhibit.
Refer to the scenario and the exhibit. 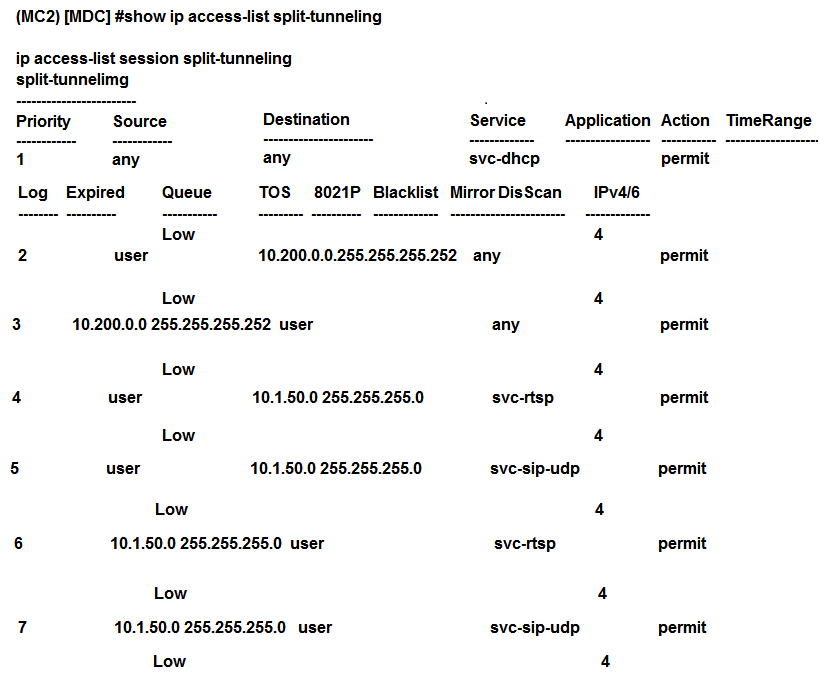 Which command must the network administrator add in the split-tunneling policy to meet the requirements for the RAP employee SSID?
Which command must the network administrator add in the split-tunneling policy to meet the requirements for the RAP employee SSID?
A) user any svc-http permit
B) user any any src-nat pool dynamic-srcnat
C) any user any src-nat pool dynamic-srcnat
D) user any any dst-nat
 Refer to the scenario and the exhibit.
Refer to the scenario and the exhibit.  Which command must the network administrator add in the split-tunneling policy to meet the requirements for the RAP employee SSID?
Which command must the network administrator add in the split-tunneling policy to meet the requirements for the RAP employee SSID?A) user any svc-http permit
B) user any any src-nat pool dynamic-srcnat
C) any user any src-nat pool dynamic-srcnat
D) user any any dst-nat

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
30
Refer to the exhibit. 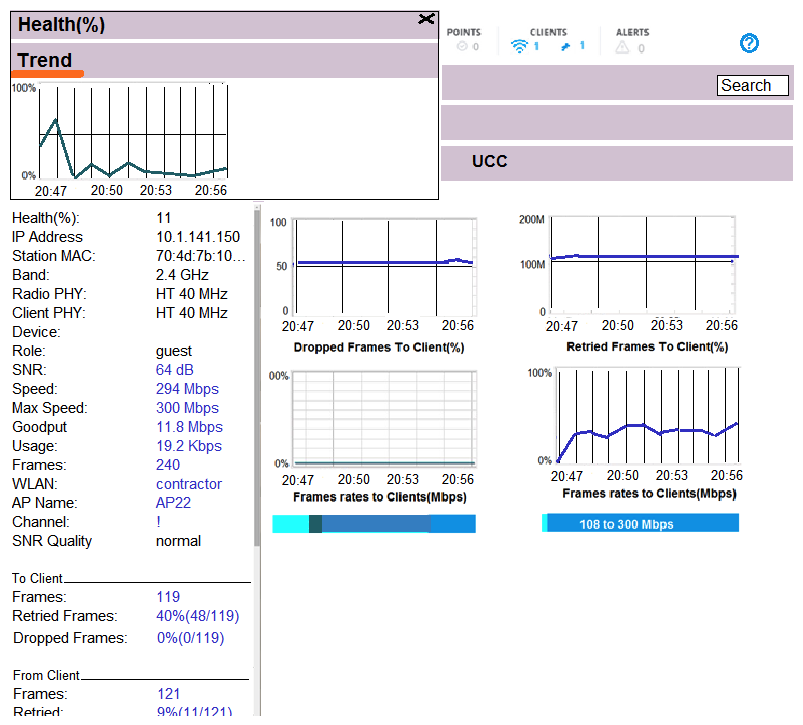 A user's laptop only operates in the 2.4 GHz band and supports 802.11n. This user reports that the network is slow at the cafeteria that is serviced by three APs, and suggests that there might be a problem with the WLAN. The network administrator finds the user in the MM, and obrains the output shown in the exhibit. What should the network administrator do to optimize the client connection?
A user's laptop only operates in the 2.4 GHz band and supports 802.11n. This user reports that the network is slow at the cafeteria that is serviced by three APs, and suggests that there might be a problem with the WLAN. The network administrator finds the user in the MM, and obrains the output shown in the exhibit. What should the network administrator do to optimize the client connection?
A) Disable lower transmit rates in the SSID profile.
B) Change the channel being used in the radio profile.
C) Reduce Min/Max channel bandwidth in the radio profile.
D) Reduce Min/Max EIRP in the ARM profile.
 A user's laptop only operates in the 2.4 GHz band and supports 802.11n. This user reports that the network is slow at the cafeteria that is serviced by three APs, and suggests that there might be a problem with the WLAN. The network administrator finds the user in the MM, and obrains the output shown in the exhibit. What should the network administrator do to optimize the client connection?
A user's laptop only operates in the 2.4 GHz band and supports 802.11n. This user reports that the network is slow at the cafeteria that is serviced by three APs, and suggests that there might be a problem with the WLAN. The network administrator finds the user in the MM, and obrains the output shown in the exhibit. What should the network administrator do to optimize the client connection?A) Disable lower transmit rates in the SSID profile.
B) Change the channel being used in the radio profile.
C) Reduce Min/Max channel bandwidth in the radio profile.
D) Reduce Min/Max EIRP in the ARM profile.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
31
Refer to the exhibits. Exhibit 1 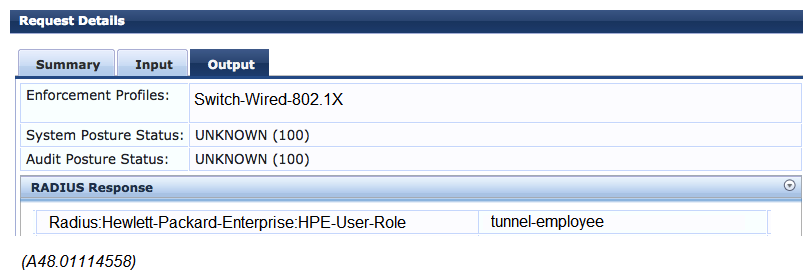 Exhibit 2
Exhibit 2 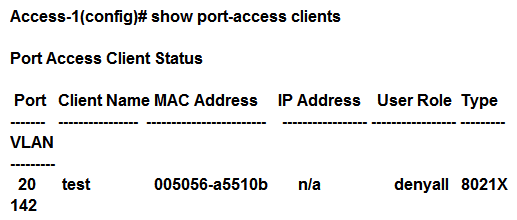 A network administrator deploys role-based tunneled node in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the HPE-User-Role attribute as expected. However, the switch always applies the denyall role. Why does the switch fail to allocate the tunnel-employee role?
A network administrator deploys role-based tunneled node in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the HPE-User-Role attribute as expected. However, the switch always applies the denyall role. Why does the switch fail to allocate the tunnel-employee role?
A) Denyall is a secondary role contained within tunnel-employee.
B) The switch is not configured with primary tunneled-node user role.
C) The switch is not configured with secondary tunneled-node user role.
D) RADIUS Access Accept messages time out in the switch.
 Exhibit 2
Exhibit 2  A network administrator deploys role-based tunneled node in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the HPE-User-Role attribute as expected. However, the switch always applies the denyall role. Why does the switch fail to allocate the tunnel-employee role?
A network administrator deploys role-based tunneled node in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the HPE-User-Role attribute as expected. However, the switch always applies the denyall role. Why does the switch fail to allocate the tunnel-employee role?A) Denyall is a secondary role contained within tunnel-employee.
B) The switch is not configured with primary tunneled-node user role.
C) The switch is not configured with secondary tunneled-node user role.
D) RADIUS Access Accept messages time out in the switch.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
32
Refer to the exhibits. Exhibit 1  Exhibit 2
Exhibit 2 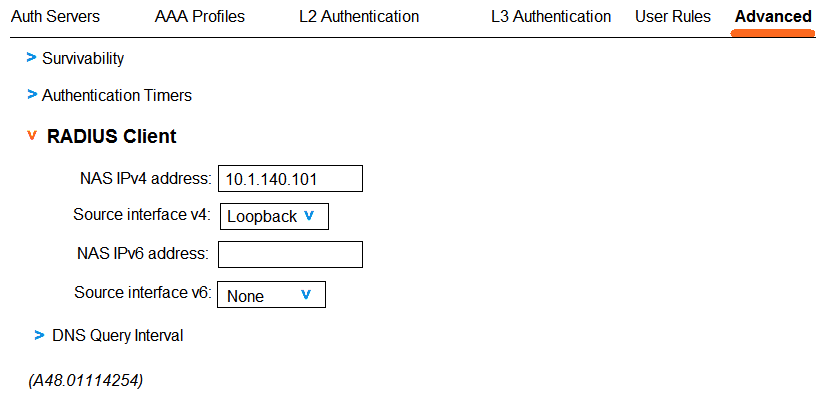 Exhibit 3
Exhibit 3 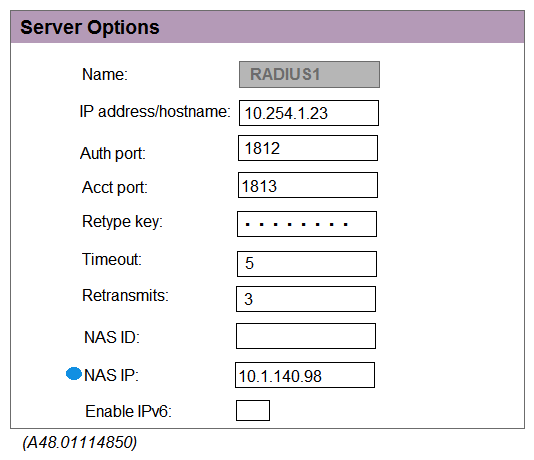 A network administrator must ensure that a ClearPass server can receive the RADIUS authentication request from a single Mobility Controller (MC) managed by a Mobility Master (MM). Based on the exhibits, what is the value of NAS-IP contained in the RADIUS access requests?
A network administrator must ensure that a ClearPass server can receive the RADIUS authentication request from a single Mobility Controller (MC) managed by a Mobility Master (MM). Based on the exhibits, what is the value of NAS-IP contained in the RADIUS access requests?
A) 10.1.140.98
B) 10.1.140.99
C) 10.1.140.100
D) 10.1.140.101
 Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  A network administrator must ensure that a ClearPass server can receive the RADIUS authentication request from a single Mobility Controller (MC) managed by a Mobility Master (MM). Based on the exhibits, what is the value of NAS-IP contained in the RADIUS access requests?
A network administrator must ensure that a ClearPass server can receive the RADIUS authentication request from a single Mobility Controller (MC) managed by a Mobility Master (MM). Based on the exhibits, what is the value of NAS-IP contained in the RADIUS access requests?A) 10.1.140.98
B) 10.1.140.99
C) 10.1.140.100
D) 10.1.140.101

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
33
A network administrator implements a SIP-based IP telephone solution. The objective is to ensure that APs use 100% of their airtime for network access whenever a voice call is taking place, to minimize communication delays. The network administrator also wants to ensure that a log entry is generated when voice calls occur. Which setup accomplishes these tasks?
A) ip access-list session voice user any svc-rtsp permit log queue high user any svc-sip-udp permit log queue high
B) user any-svc-rtsp permit disable-scanning log user any svc-sip-udp permit disable-scanning log
C) user any svc-rtsp permit log dot1p-priority 7 user any svc-sip-udp permit log dot1p-priority 7
D) user any svc-rtsp permit log tos 56 user any svc-sip-udp permit log tos 56
A) ip access-list session voice user any svc-rtsp permit log queue high user any svc-sip-udp permit log queue high
B) user any-svc-rtsp permit disable-scanning log user any svc-sip-udp permit disable-scanning log
C) user any svc-rtsp permit log dot1p-priority 7 user any svc-sip-udp permit log dot1p-priority 7
D) user any svc-rtsp permit log tos 56 user any svc-sip-udp permit log tos 56

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
34
A financial institution contacts an Aruba partner to deploy an advanced and secure Mobility Master (MM)-Mobility Controller (MC) WLAN solution in its main campus and 14 small offices/home offices (SOHOs). Key requirements are that users at all locations, including telecommuters with VIA, should be assigned roles with policies that filter undesired traffic. Also, advanced WIPs should be enforced at the campus only. These are additional requirements for this deployment: RAPs should ship directly to their final destinations without any pre-setup and should come up with the right configuration as soon as they get Internet access. Activate should be configured with devices MACs, serial numbers, and provisioning rules that redirect them to the standalone VMC at the DMZ Users should be able to reach DNS, FTP, Web and telephone servers in the campus as well as send and receive IP telephone calls to and from the voice 10.1.50.0/24 segment. Local Internet access should be granted. Refer to the exhibit. 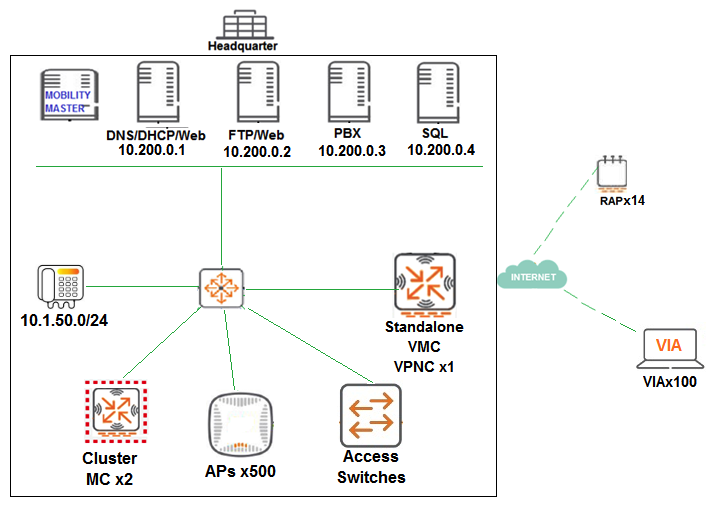 Refer to the scenario and the exhibit.
Refer to the scenario and the exhibit. 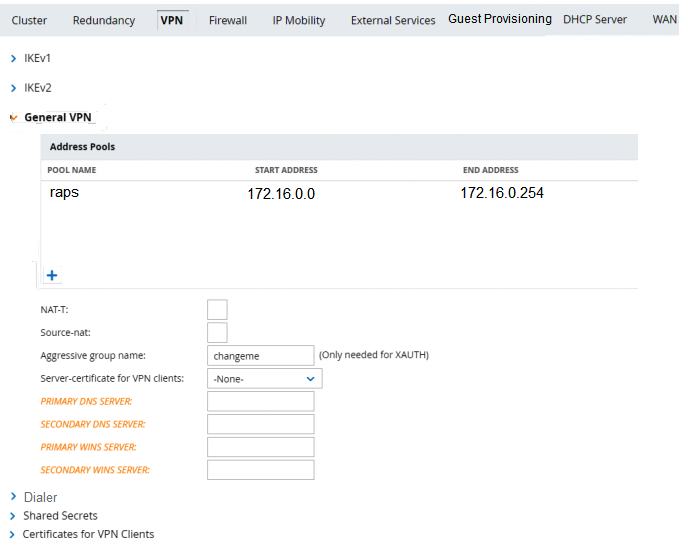 The standalone VMC will act as a VPN Concentrator of the RAPs. The network administrator configures the Standalone VMC with a pool of addresses and the SOHOs AP Group from the MM. Which additional steps must the network administrator perform to allow the RAPs to terminate their IPSec tunnels and associate to the Standalone VMC?
The standalone VMC will act as a VPN Concentrator of the RAPs. The network administrator configures the Standalone VMC with a pool of addresses and the SOHOs AP Group from the MM. Which additional steps must the network administrator perform to allow the RAPs to terminate their IPSec tunnels and associate to the Standalone VMC?
A) Add RAP MAC addresses into the RAP whitelist, and associate them with the SOHOs AP-Group.
B) Add RAP MAC addresses into the CPSec whitelist, and associate them with the SOHOs AP-Group.
C) Configure the same IP Pool at the MM group level, then create user accounts for the RAPs in the internal database.
D) Create user accounts with the sys-ap-role, and define shared secrets to associate to RAP IP addresses at the MM group level.
 Refer to the scenario and the exhibit.
Refer to the scenario and the exhibit.  The standalone VMC will act as a VPN Concentrator of the RAPs. The network administrator configures the Standalone VMC with a pool of addresses and the SOHOs AP Group from the MM. Which additional steps must the network administrator perform to allow the RAPs to terminate their IPSec tunnels and associate to the Standalone VMC?
The standalone VMC will act as a VPN Concentrator of the RAPs. The network administrator configures the Standalone VMC with a pool of addresses and the SOHOs AP Group from the MM. Which additional steps must the network administrator perform to allow the RAPs to terminate their IPSec tunnels and associate to the Standalone VMC?A) Add RAP MAC addresses into the RAP whitelist, and associate them with the SOHOs AP-Group.
B) Add RAP MAC addresses into the CPSec whitelist, and associate them with the SOHOs AP-Group.
C) Configure the same IP Pool at the MM group level, then create user accounts for the RAPs in the internal database.
D) Create user accounts with the sys-ap-role, and define shared secrets to associate to RAP IP addresses at the MM group level.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
35
Refer to the exhibit. 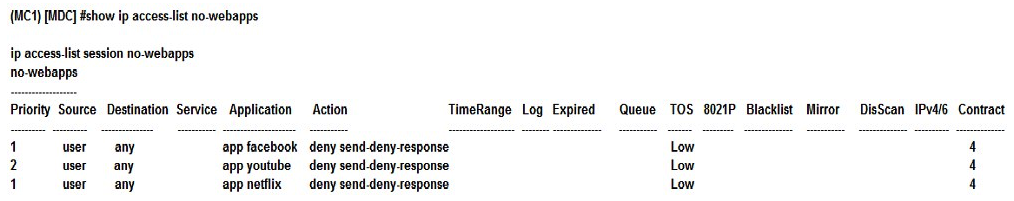 A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, the network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit. Which additional steps must be done to make sure this configuration takes effecr over the contractor users?
A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, the network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit. Which additional steps must be done to make sure this configuration takes effecr over the contractor users?
A) Apply the policy in the contractors user role. Enable deep packet inspection.
B) Reload the MCs.
C) Enable the firewall visibility. Enable web-content classification
D) Enable firewall visibility Reload the MMs.
 A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, the network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit. Which additional steps must be done to make sure this configuration takes effecr over the contractor users?
A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, the network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit. Which additional steps must be done to make sure this configuration takes effecr over the contractor users?A) Apply the policy in the contractors user role. Enable deep packet inspection.
B) Reload the MCs.
C) Enable the firewall visibility. Enable web-content classification
D) Enable firewall visibility Reload the MMs.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
36
Refer to the exhibit. 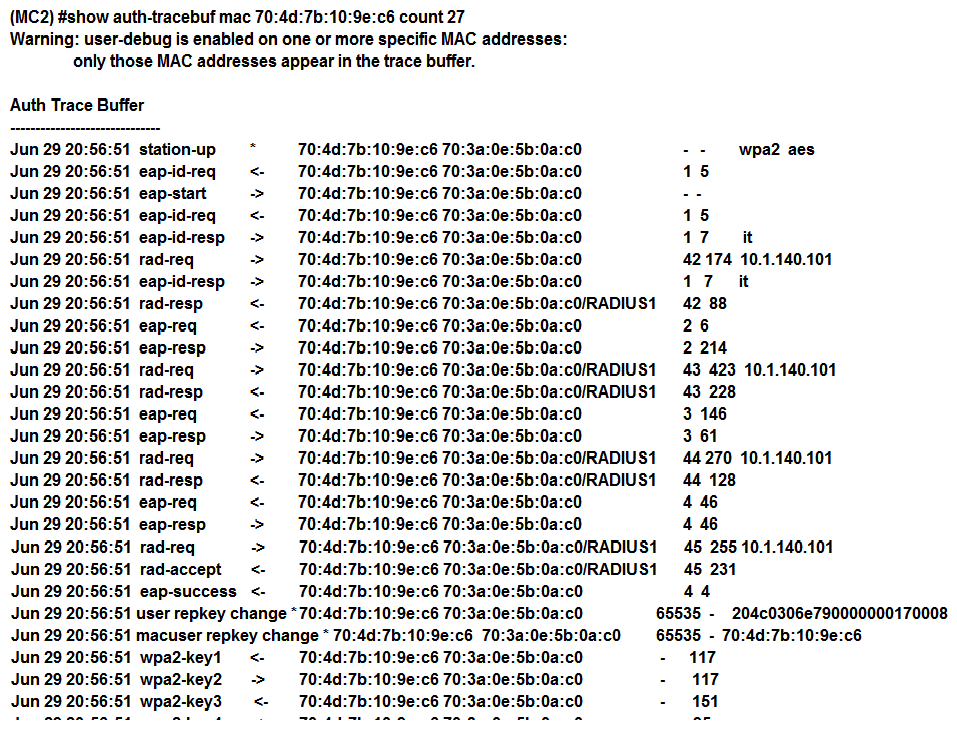 A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by the wireless station?
A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by the wireless station?
A) 802.1X user authentication
B) EAP authentication
C) 802.1X machine authentication
D) MAC authentication
 A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by the wireless station?
A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by the wireless station?A) 802.1X user authentication
B) EAP authentication
C) 802.1X machine authentication
D) MAC authentication

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
37
A network administrator wants to receive a major alarm every time a controller or an Aruba switch goes down for either a local or an upstream device failure. Which alarm definition must the network administrator create to accomplish this?
A)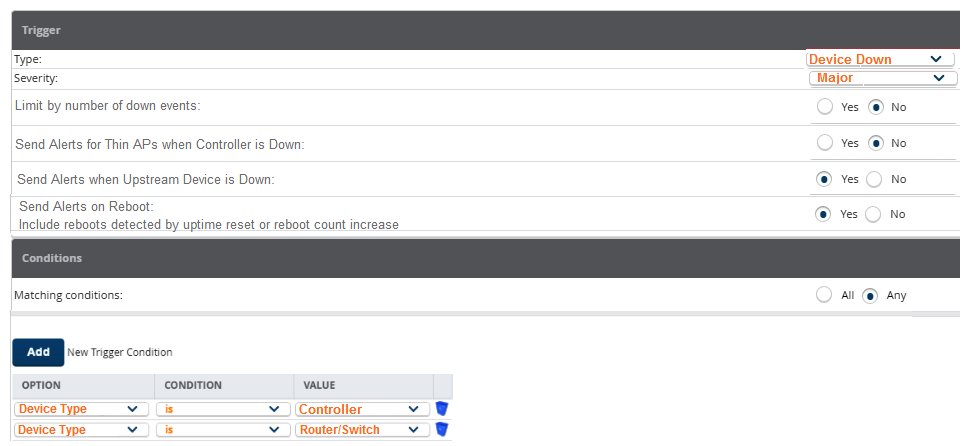
B)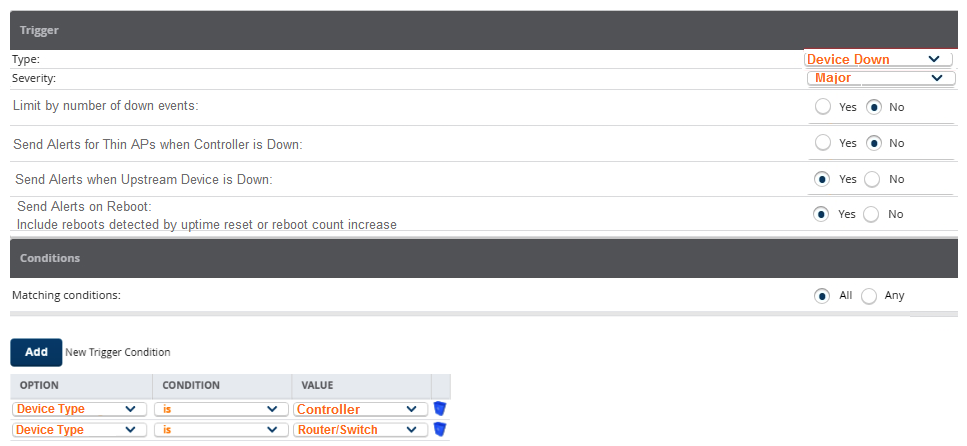
C)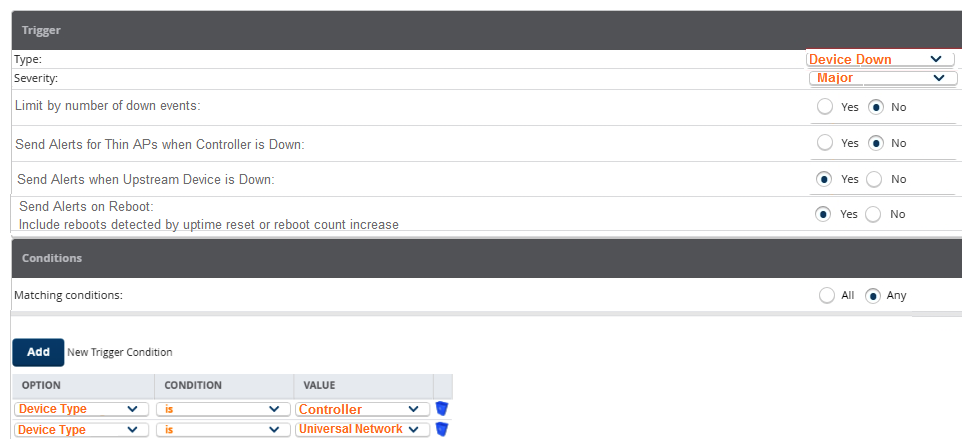
A)

B)

C)


Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
38
Refer to the exhibit. 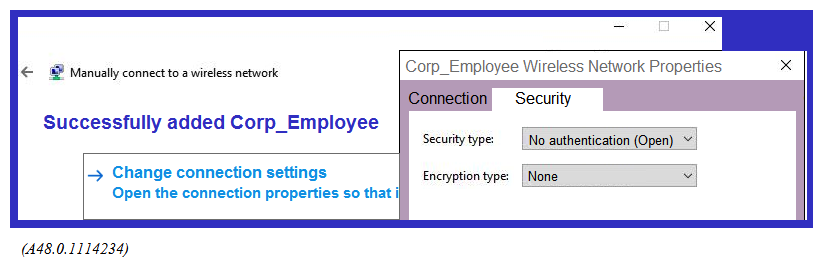 A network administrator wants to configure an 802.1x supplicamt for a wireless network that includes the following: AES encryption EAP-MSCHAP v2-based user and machine authentication Validation of server certificate in Microsoft Windows 10 The network administrator creates a WLAN profile and selects the change connection settings option. Then the network administrator changes the security type to Microsoft: Protected EAP (PEAP), and enables user and machine authentication under Additonal Settings. What must the network administrator do next to accomplish the task?
A network administrator wants to configure an 802.1x supplicamt for a wireless network that includes the following: AES encryption EAP-MSCHAP v2-based user and machine authentication Validation of server certificate in Microsoft Windows 10 The network administrator creates a WLAN profile and selects the change connection settings option. Then the network administrator changes the security type to Microsoft: Protected EAP (PEAP), and enables user and machine authentication under Additonal Settings. What must the network administrator do next to accomplish the task?
A) Enable user authentication under Settings.
B) Change the security type to Microsoft. Smart Card or other certificate.
C) Enable server certificate validation under Settings.
D) Enable computer autentication under Settings.
 A network administrator wants to configure an 802.1x supplicamt for a wireless network that includes the following: AES encryption EAP-MSCHAP v2-based user and machine authentication Validation of server certificate in Microsoft Windows 10 The network administrator creates a WLAN profile and selects the change connection settings option. Then the network administrator changes the security type to Microsoft: Protected EAP (PEAP), and enables user and machine authentication under Additonal Settings. What must the network administrator do next to accomplish the task?
A network administrator wants to configure an 802.1x supplicamt for a wireless network that includes the following: AES encryption EAP-MSCHAP v2-based user and machine authentication Validation of server certificate in Microsoft Windows 10 The network administrator creates a WLAN profile and selects the change connection settings option. Then the network administrator changes the security type to Microsoft: Protected EAP (PEAP), and enables user and machine authentication under Additonal Settings. What must the network administrator do next to accomplish the task?A) Enable user authentication under Settings.
B) Change the security type to Microsoft. Smart Card or other certificate.
C) Enable server certificate validation under Settings.
D) Enable computer autentication under Settings.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
39
Refer to the exhibits. Exhibit 1 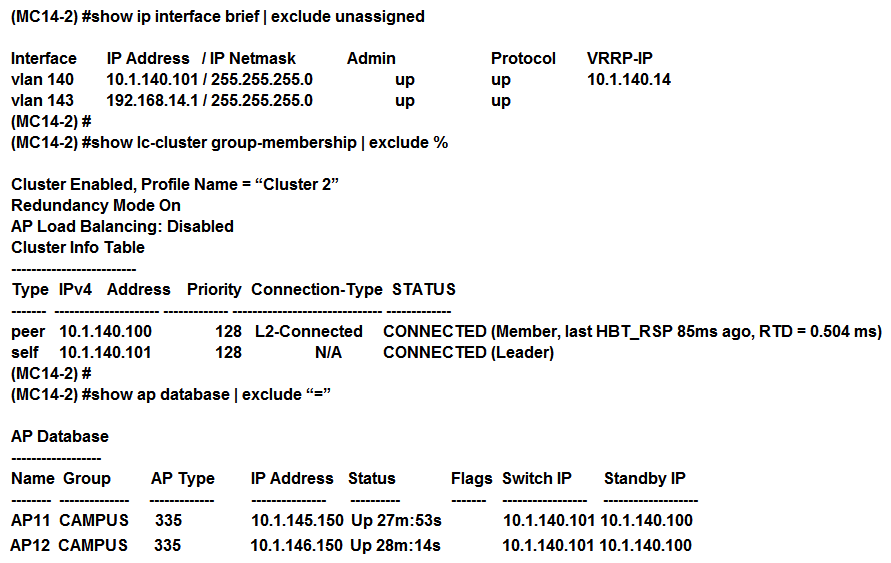 Exhibit 2
Exhibit 2 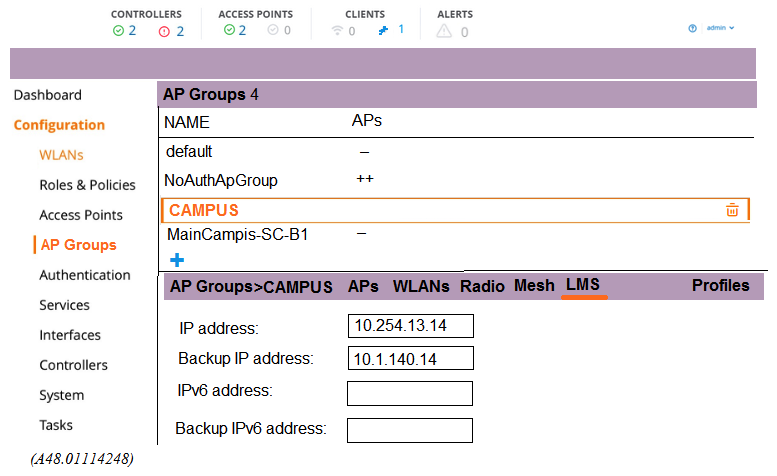 A network administrator deploys a test environment with two Mobility Masters (MMs), two two-member Mobility Controller (MC) clusters, and two CAPs, with the intention of testing several ArubaOS features, Cluster members run VRRP for AP boot redundancy. Based on the information shown in the exhibits, what is the current status of the APs?
A network administrator deploys a test environment with two Mobility Masters (MMs), two two-member Mobility Controller (MC) clusters, and two CAPs, with the intention of testing several ArubaOS features, Cluster members run VRRP for AP boot redundancy. Based on the information shown in the exhibits, what is the current status of the APs?
A) APs are currently communicating with LMS IP, and 10.1.140.100 is S-AAC.
B) APs are currently communicating with BLMS IP, and 10.1.140.101 is A-AAC.
C) APs are currently communicating with BLMS IP, and 10.1.140.101 is S-AAC.
D) APs are currently communicating with BLMS IP, and 10.1.140.100 is A-AAC.
 Exhibit 2
Exhibit 2  A network administrator deploys a test environment with two Mobility Masters (MMs), two two-member Mobility Controller (MC) clusters, and two CAPs, with the intention of testing several ArubaOS features, Cluster members run VRRP for AP boot redundancy. Based on the information shown in the exhibits, what is the current status of the APs?
A network administrator deploys a test environment with two Mobility Masters (MMs), two two-member Mobility Controller (MC) clusters, and two CAPs, with the intention of testing several ArubaOS features, Cluster members run VRRP for AP boot redundancy. Based on the information shown in the exhibits, what is the current status of the APs?A) APs are currently communicating with LMS IP, and 10.1.140.100 is S-AAC.
B) APs are currently communicating with BLMS IP, and 10.1.140.101 is A-AAC.
C) APs are currently communicating with BLMS IP, and 10.1.140.101 is S-AAC.
D) APs are currently communicating with BLMS IP, and 10.1.140.100 is A-AAC.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
40
A network administrator deplos a guest solution over WiFi and creates a corp_guest role for this purpose. The network administrator must configure the solution with a custom policy that permits visitors to get an IP address, perform DNS resolutions, and get internet access while blocking any attempt to reach internal resources at the 10.0.0.0/8 network. The solution should prevent visitors from acting as rogue DHCP servers, then blacklist and log the attempt if this ever happens. Which setup meets these requirements?
A) netdestination corporate_network network 10.0.0.0 255.0.0.0 ip access-list session corp_guests user any udp 68 deny log blacklist any any svc-dhcp permit user alias coroporate_network deny user any any permit user-role Corp_guest access-list session corp_guests
B) any any udp 68 deny log blacklist
C) user any udp 67 deny log blacklist
D) any any udp 67 deny log blacklist
A) netdestination corporate_network network 10.0.0.0 255.0.0.0 ip access-list session corp_guests user any udp 68 deny log blacklist any any svc-dhcp permit user alias coroporate_network deny user any any permit user-role Corp_guest access-list session corp_guests
B) any any udp 68 deny log blacklist
C) user any udp 67 deny log blacklist
D) any any udp 67 deny log blacklist

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
41
Refer to the exhibit. 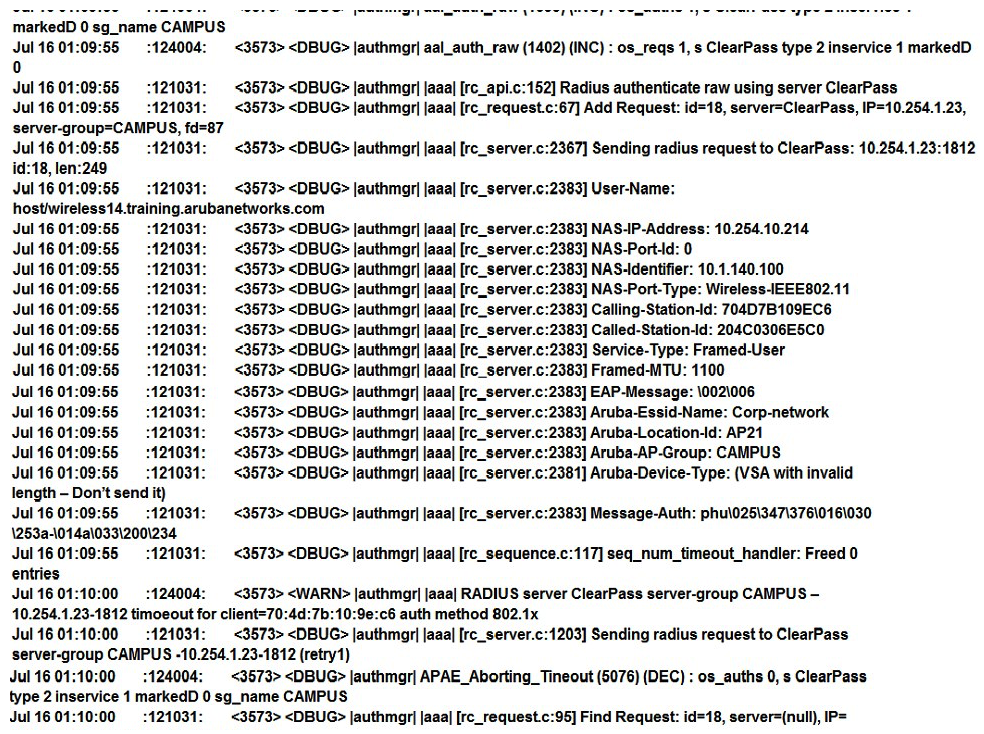 A network administrator deploys a new WLAN named Corp-Network. The security suite is WPA2 with 802.1X. A new ClearPass server is used as the authentication server. Connection attempts to this WLAN are rejected, and no trace of the attempt is seen in the ClearPass Policy Manager Access Tracker. However, the network administrator is able to see the logs shown in the exhibit. What must the network administrator do to solve the problem?
A network administrator deploys a new WLAN named Corp-Network. The security suite is WPA2 with 802.1X. A new ClearPass server is used as the authentication server. Connection attempts to this WLAN are rejected, and no trace of the attempt is seen in the ClearPass Policy Manager Access Tracker. However, the network administrator is able to see the logs shown in the exhibit. What must the network administrator do to solve the problem?
A) Add the correct network device IP address in ClearPass.
B) Change the ClearPass server IP address in the MC.
C) Fix the RADIUS shared secret in the MC.
D) Disable machine authentication in the MC and client PC.
 A network administrator deploys a new WLAN named Corp-Network. The security suite is WPA2 with 802.1X. A new ClearPass server is used as the authentication server. Connection attempts to this WLAN are rejected, and no trace of the attempt is seen in the ClearPass Policy Manager Access Tracker. However, the network administrator is able to see the logs shown in the exhibit. What must the network administrator do to solve the problem?
A network administrator deploys a new WLAN named Corp-Network. The security suite is WPA2 with 802.1X. A new ClearPass server is used as the authentication server. Connection attempts to this WLAN are rejected, and no trace of the attempt is seen in the ClearPass Policy Manager Access Tracker. However, the network administrator is able to see the logs shown in the exhibit. What must the network administrator do to solve the problem?A) Add the correct network device IP address in ClearPass.
B) Change the ClearPass server IP address in the MC.
C) Fix the RADIUS shared secret in the MC.
D) Disable machine authentication in the MC and client PC.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
42
A company has headquarters based in the US and rents internation office space in Mexico City so that 10 employees can work remotely. The company must implement a remote access technology so branch office employees can access all servers at the headquareters. The office has both wired and wireless internet connectivity, with no restrictions on what device connects to the network. However, ports UDP 4500, 5060, and 5061 are blocked by the primeter firewall. Which remote access technology is required to allow employees to access the servers at the headquarters?
A) BOC with CAPs
B) IAP VPN
C) RAP
D) VIA
A) BOC with CAPs
B) IAP VPN
C) RAP
D) VIA

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
43
A company currently offers guest access with an open SSID and no authentication. A network administrator needs to integrate a web login page for visitors. To accomplish this integration, the network administrator fully deploys a guest solution with self-registration in ClearPass, and defines the Mobility Controller (MC) as a RADIUS client. Then, the network administrator defines ClearPass as a RADIUS server and adds it into a server group in the MC. Which two actions must the network administrator do next on the MC side to complete the deployment? (Select two.)
A) Associate the captive portal profile to the initial role
B) Define the web login URL and server group in a captive portal profile
C) Associate the captive portal profile to the VAP profile
D) Associate the captive portal to an AAA profile.
E) Define the web login URL in a captive portal profile and the server group in an AAA profile.
A) Associate the captive portal profile to the initial role
B) Define the web login URL and server group in a captive portal profile
C) Associate the captive portal profile to the VAP profile
D) Associate the captive portal to an AAA profile.
E) Define the web login URL in a captive portal profile and the server group in an AAA profile.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
44
A financial institution contacts an Aruba partner to deploy an advanced and secure Mobility Master (MM)-Mobility Controller (MC) WLAN solution in its main campus and 14 small offices/home offices (SOHOs). Key requirements are that users at all locations, including telecommuters with VIA, should be assigned roles with policies that filter undesired traffic. Also, advanced WIPs should be enforced at the campus only. These are additional requirements for this deployment: RAPs should ship directly to their final destinations without any pre-setup and should come up with the right configuration as soon as they get Internet access. Activate should be configured with devices MACs, serial numbers, and provisioning rules that redirect them to the standalone VMC at the DMZ Users should be able to reach DNS, FTP, Web and telephone servers in the campus as well as send and receive IP telephone calls to and from the voice 10.1.50.0/24 segment. Local Internet access should be granted. Refer to the exhibit. 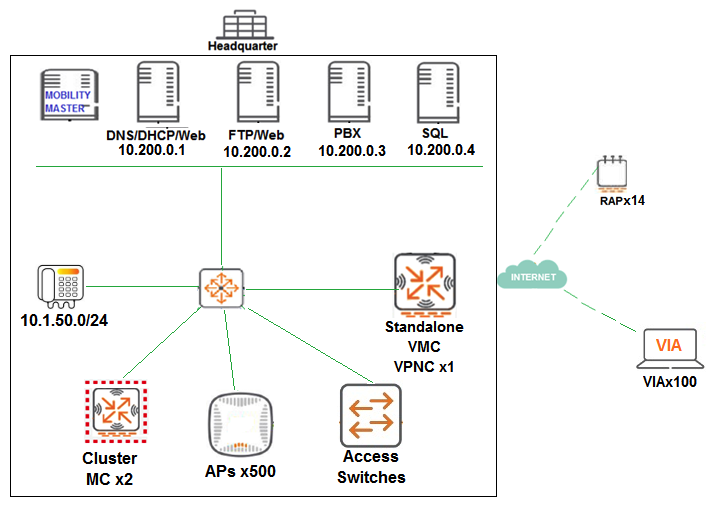 Refer to the scenario and the exhibit. What is the minimal license capacity in use to support this proposal?
Refer to the scenario and the exhibit. What is the minimal license capacity in use to support this proposal?
A)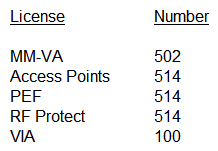
B)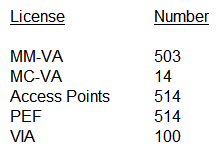
C)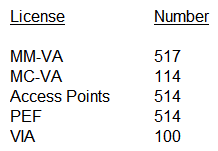
D)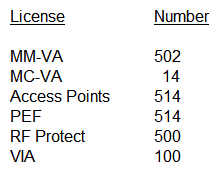
 Refer to the scenario and the exhibit. What is the minimal license capacity in use to support this proposal?
Refer to the scenario and the exhibit. What is the minimal license capacity in use to support this proposal?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
45
A network administrator assists with the migration of a WLAN from a third-party vendor to Aruba in different locations throughout the country. In order to manage the solution from a central point, the network administrator decides to deploy redundant Mobility Masters (MMs) in a datacenter that are reachable through the Internet. Since not all locations own public IP addresses, the security team is not able to configure strict firewall policies at the datacenter without disrupting some MM to Mobility Controller (MC) communications. They are also concerned about exposing the MMs to unauthorized inbound connection attempts. What should the network administrator do to ensure the solution is functional and secure?
A) Deploy an MC at the datacenter as a VPN concentrator.
B) Block all ports to the MMs except UDP 500 and 4500.
C) Install a PEFV license, and configure firewall policies that protect the MM.
D) Block all inbound connections, and instruct the MM to initiate the connection to the MCs.
A) Deploy an MC at the datacenter as a VPN concentrator.
B) Block all ports to the MMs except UDP 500 and 4500.
C) Install a PEFV license, and configure firewall policies that protect the MM.
D) Block all inbound connections, and instruct the MM to initiate the connection to the MCs.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
46
Refer to the exhibits. Exhibit 1 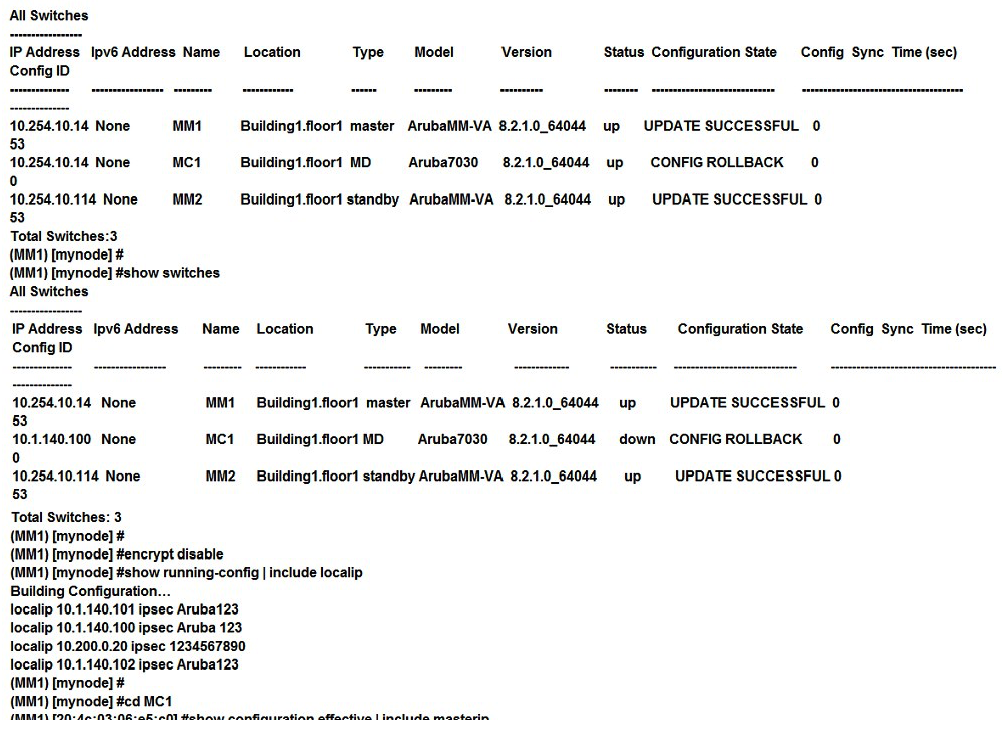 Exhibit 2
Exhibit 2 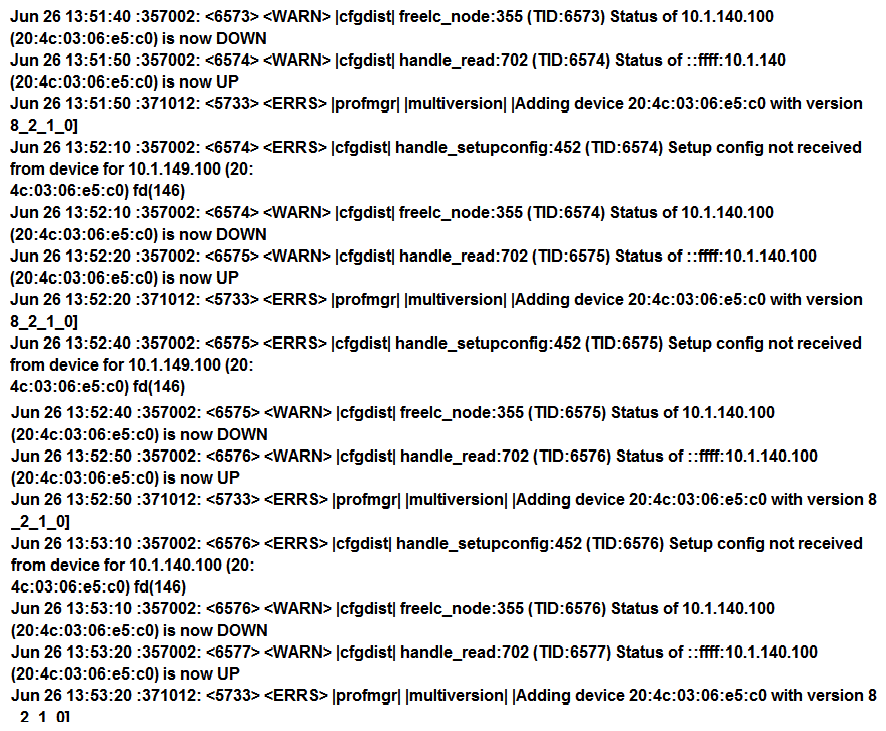 Exhibit 3
Exhibit 3 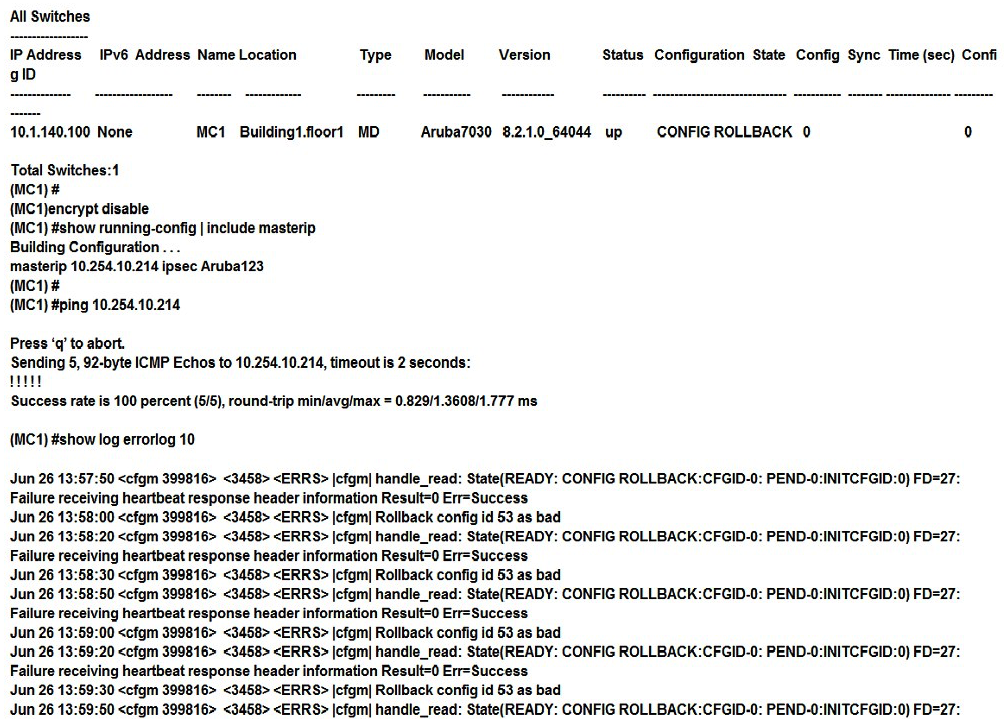 A network administrator deploys a Mobility Master (MM) pair with the VRRP VIP equal to 10.254.10.214, and attempts to associate MC1 to it. At first, the integration appears to be successful. However after a few minutes the network administrator issues the show switches command and sees that the MC1 is down, even though the device is up and running. Every time the network administrator reboots the Mobility Controller (MC), the MC shows as being up and then it shows as being down. The network administrator gathers the information shown in the exhibits. What should the network administrator do to resolve this problem?
A network administrator deploys a Mobility Master (MM) pair with the VRRP VIP equal to 10.254.10.214, and attempts to associate MC1 to it. At first, the integration appears to be successful. However after a few minutes the network administrator issues the show switches command and sees that the MC1 is down, even though the device is up and running. Every time the network administrator reboots the Mobility Controller (MC), the MC shows as being up and then it shows as being down. The network administrator gathers the information shown in the exhibits. What should the network administrator do to resolve this problem?
A) Change the localip ipsec key to Aruba123 in the mynode device level from the MM, save, and reboot.
B) Enable disaster recovery mode in MC1 and change the masterip ipsec key to Aruba 123, save, and reboot.
C) Change the masterip ipsec key to Aruba123 in the device level from the MM, save, then reboot MC1.
D) Wipe out the configuration in MC1 and reboot, then run the full-setup configuration dialog all over again.
 Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  A network administrator deploys a Mobility Master (MM) pair with the VRRP VIP equal to 10.254.10.214, and attempts to associate MC1 to it. At first, the integration appears to be successful. However after a few minutes the network administrator issues the show switches command and sees that the MC1 is down, even though the device is up and running. Every time the network administrator reboots the Mobility Controller (MC), the MC shows as being up and then it shows as being down. The network administrator gathers the information shown in the exhibits. What should the network administrator do to resolve this problem?
A network administrator deploys a Mobility Master (MM) pair with the VRRP VIP equal to 10.254.10.214, and attempts to associate MC1 to it. At first, the integration appears to be successful. However after a few minutes the network administrator issues the show switches command and sees that the MC1 is down, even though the device is up and running. Every time the network administrator reboots the Mobility Controller (MC), the MC shows as being up and then it shows as being down. The network administrator gathers the information shown in the exhibits. What should the network administrator do to resolve this problem?A) Change the localip ipsec key to Aruba123 in the mynode device level from the MM, save, and reboot.
B) Enable disaster recovery mode in MC1 and change the masterip ipsec key to Aruba 123, save, and reboot.
C) Change the masterip ipsec key to Aruba123 in the device level from the MM, save, then reboot MC1.
D) Wipe out the configuration in MC1 and reboot, then run the full-setup configuration dialog all over again.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
47
Refer to the exhibit.  A network engineer configures some VAPs in customer groups and creates a pool of licenses with enough units for seven APs. The network engineer deploys the first two APs, looks at the ap database, and notices the APs are inactive and experience licensing-related issues. Based on the show command outputs shown in the exhibit, what must the engineer do to solve the problem?
A network engineer configures some VAPs in customer groups and creates a pool of licenses with enough units for seven APs. The network engineer deploys the first two APs, looks at the ap database, and notices the APs are inactive and experience licensing-related issues. Based on the show command outputs shown in the exhibit, what must the engineer do to solve the problem?
A) Allocate two more MM-VA licenses to the pool.
B) Allocate two more MC-VA-US licenses to the pool.
C) Allocate seven more MM-VA licenses to the pool.
D) Allocate seven more MC-VA-US licenses to the pool.
 A network engineer configures some VAPs in customer groups and creates a pool of licenses with enough units for seven APs. The network engineer deploys the first two APs, looks at the ap database, and notices the APs are inactive and experience licensing-related issues. Based on the show command outputs shown in the exhibit, what must the engineer do to solve the problem?
A network engineer configures some VAPs in customer groups and creates a pool of licenses with enough units for seven APs. The network engineer deploys the first two APs, looks at the ap database, and notices the APs are inactive and experience licensing-related issues. Based on the show command outputs shown in the exhibit, what must the engineer do to solve the problem?A) Allocate two more MM-VA licenses to the pool.
B) Allocate two more MC-VA-US licenses to the pool.
C) Allocate seven more MM-VA licenses to the pool.
D) Allocate seven more MC-VA-US licenses to the pool.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
48
Refer to the exhibit. 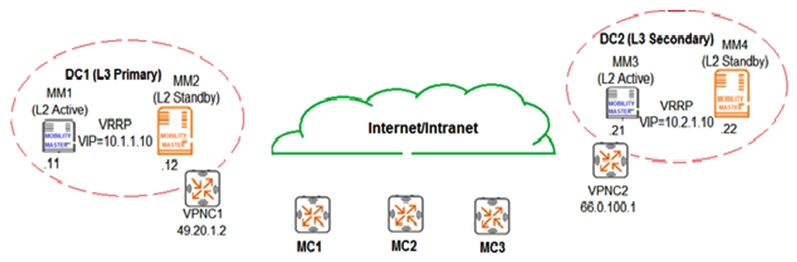 An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active, and L3 Primary. Which MM IP will MCs communicate with if MM1 fails?
An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active, and L3 Primary. Which MM IP will MCs communicate with if MM1 fails?
A) 10.1.1.10
B) 10.1.1.12
C) 10.2.1.10
D) 10.2.1.21
 An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active, and L3 Primary. Which MM IP will MCs communicate with if MM1 fails?
An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active, and L3 Primary. Which MM IP will MCs communicate with if MM1 fails?A) 10.1.1.10
B) 10.1.1.12
C) 10.2.1.10
D) 10.2.1.21

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
49
Refer to the exhibits. Exhibit 1 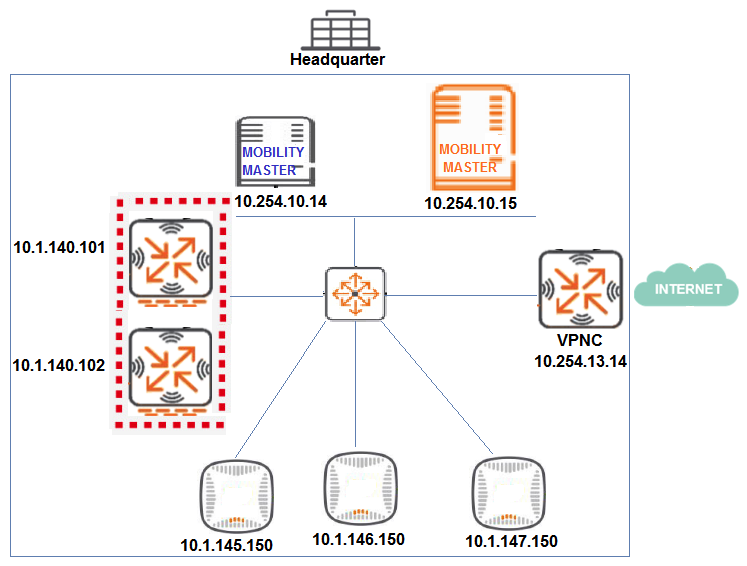 Exhibit 2
Exhibit 2 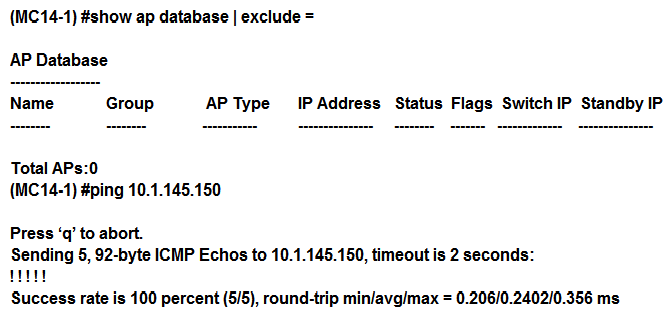 Exhibit 3
Exhibit 3  A network engineer deploys a Master Controller (MC) cluster at Headquarter to offer high levels of redundancy, and prepares the wired side of the network. This preparation includes the VLAN, DHCP Settings, and unicast routing services that APs require to reach the cluster. The network engineer waits for 20 minutes after connecting the APs and sees that no SSIDs are advertised. The network engineer logs into one of the MCs and one of the AP's consoles to obtain the outputs shown in the exhibits. What can the network engineer do to fix the APs discovery process, to ensure the best scalability even if one MC fails?
A network engineer deploys a Master Controller (MC) cluster at Headquarter to offer high levels of redundancy, and prepares the wired side of the network. This preparation includes the VLAN, DHCP Settings, and unicast routing services that APs require to reach the cluster. The network engineer waits for 20 minutes after connecting the APs and sees that no SSIDs are advertised. The network engineer logs into one of the MCs and one of the AP's consoles to obtain the outputs shown in the exhibits. What can the network engineer do to fix the APs discovery process, to ensure the best scalability even if one MC fails?
A) Reprovision the APs with a different Master IP.
B) Modify the IP address in one of the MCs.
C) Modify option 43 in the DHCP pool.
D) Create a VRRP instance in the MCs.
 Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  A network engineer deploys a Master Controller (MC) cluster at Headquarter to offer high levels of redundancy, and prepares the wired side of the network. This preparation includes the VLAN, DHCP Settings, and unicast routing services that APs require to reach the cluster. The network engineer waits for 20 minutes after connecting the APs and sees that no SSIDs are advertised. The network engineer logs into one of the MCs and one of the AP's consoles to obtain the outputs shown in the exhibits. What can the network engineer do to fix the APs discovery process, to ensure the best scalability even if one MC fails?
A network engineer deploys a Master Controller (MC) cluster at Headquarter to offer high levels of redundancy, and prepares the wired side of the network. This preparation includes the VLAN, DHCP Settings, and unicast routing services that APs require to reach the cluster. The network engineer waits for 20 minutes after connecting the APs and sees that no SSIDs are advertised. The network engineer logs into one of the MCs and one of the AP's consoles to obtain the outputs shown in the exhibits. What can the network engineer do to fix the APs discovery process, to ensure the best scalability even if one MC fails?A) Reprovision the APs with a different Master IP.
B) Modify the IP address in one of the MCs.
C) Modify option 43 in the DHCP pool.
D) Create a VRRP instance in the MCs.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
50
Refer to the exhibit. 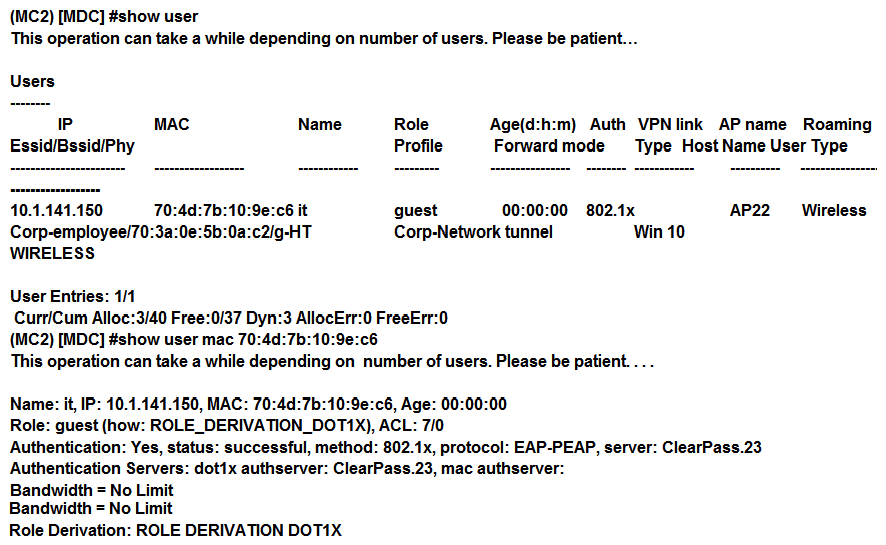 A network administrator evaluates a deployment to validate that users are assigned to the proper roles. Based on the output shown in the exhibit, what can the network administrator conclude?
A network administrator evaluates a deployment to validate that users are assigned to the proper roles. Based on the output shown in the exhibit, what can the network administrator conclude?
A) The MC assigned the machine authentication default user role.
B) The MC assigned the role based on user-derivation rules.
C) The MC assigned the role based on server-derivation rules.
D) The MC assigned the default role of the authentication method.
 A network administrator evaluates a deployment to validate that users are assigned to the proper roles. Based on the output shown in the exhibit, what can the network administrator conclude?
A network administrator evaluates a deployment to validate that users are assigned to the proper roles. Based on the output shown in the exhibit, what can the network administrator conclude?A) The MC assigned the machine authentication default user role.
B) The MC assigned the role based on user-derivation rules.
C) The MC assigned the role based on server-derivation rules.
D) The MC assigned the default role of the authentication method.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
51
Refer to the exhibit. 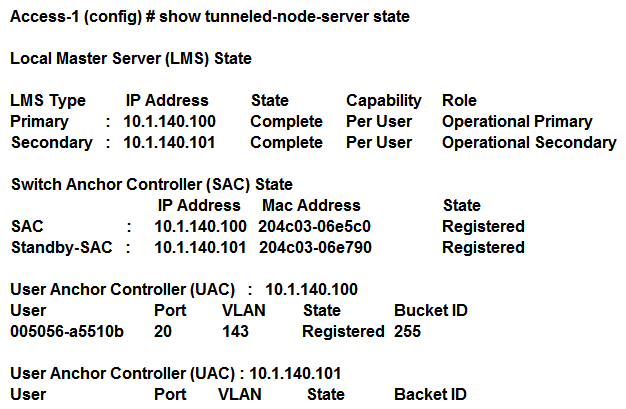 Based on the output shown in the exhibitm with which Aruba devices has Access-1 established tunnels?
Based on the output shown in the exhibitm with which Aruba devices has Access-1 established tunnels?
A) a pair of MCs within a cluster
B) a single standalone MC
C) a pair of MCs with APFF enabled
D) a pair of switches
 Based on the output shown in the exhibitm with which Aruba devices has Access-1 established tunnels?
Based on the output shown in the exhibitm with which Aruba devices has Access-1 established tunnels?A) a pair of MCs within a cluster
B) a single standalone MC
C) a pair of MCs with APFF enabled
D) a pair of switches

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
52
Refer to the exhibit. 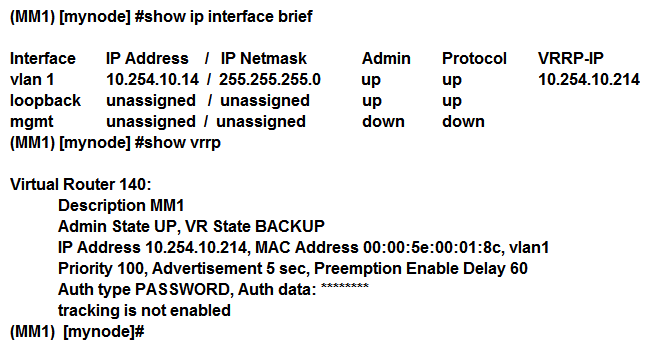 After a recent power outage where MM1 is located, the network administrator could not perform configuration tasks on Mobility Controllers (MC) for several hours. The network administrator decides to acquire another Mobility Master (MM) and deploy L2 MM redundancy. The new MM is assigned the 10.254.10.15 IP address and VRRP is configured in both units. The network administrator verifies that VRRP is running, and prepares to complete the setup with the following scripts.
After a recent power outage where MM1 is located, the network administrator could not perform configuration tasks on Mobility Controllers (MC) for several hours. The network administrator decides to acquire another Mobility Master (MM) and deploy L2 MM redundancy. The new MM is assigned the 10.254.10.15 IP address and VRRP is configured in both units. The network administrator verifies that VRRP is running, and prepares to complete the setup with the following scripts. 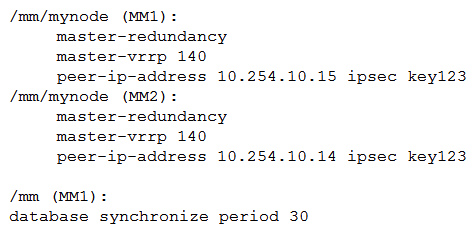 Which configuration tasks must the network administrator do before applying the script in order to successfully deploy L2 MM redundancy and prevent any other control plane outage?
Which configuration tasks must the network administrator do before applying the script in order to successfully deploy L2 MM redundancy and prevent any other control plane outage?
A) Confirm that the VRRP and master redundancy keys are the same.
B) Change the VIP address of ther VRRP process 140 to 10.254.10.15.
C) Reduce the VRRP priority to 90 and restart the process in MM2.
D) Enable the MM database synchronization in MM2.
 After a recent power outage where MM1 is located, the network administrator could not perform configuration tasks on Mobility Controllers (MC) for several hours. The network administrator decides to acquire another Mobility Master (MM) and deploy L2 MM redundancy. The new MM is assigned the 10.254.10.15 IP address and VRRP is configured in both units. The network administrator verifies that VRRP is running, and prepares to complete the setup with the following scripts.
After a recent power outage where MM1 is located, the network administrator could not perform configuration tasks on Mobility Controllers (MC) for several hours. The network administrator decides to acquire another Mobility Master (MM) and deploy L2 MM redundancy. The new MM is assigned the 10.254.10.15 IP address and VRRP is configured in both units. The network administrator verifies that VRRP is running, and prepares to complete the setup with the following scripts.  Which configuration tasks must the network administrator do before applying the script in order to successfully deploy L2 MM redundancy and prevent any other control plane outage?
Which configuration tasks must the network administrator do before applying the script in order to successfully deploy L2 MM redundancy and prevent any other control plane outage?A) Confirm that the VRRP and master redundancy keys are the same.
B) Change the VIP address of ther VRRP process 140 to 10.254.10.15.
C) Reduce the VRRP priority to 90 and restart the process in MM2.
D) Enable the MM database synchronization in MM2.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
53
Refer to the exhibit.  A network administrator deploys a new Mobility Master (MM)-Mobility Controller (MC) network. To test the solution, the network administrator accessess some of the AP consoles and statistically provisions them. However, these APs do not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?
A network administrator deploys a new Mobility Master (MM)-Mobility Controller (MC) network. To test the solution, the network administrator accessess some of the AP consoles and statistically provisions them. However, these APs do not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?
A) Reprovision one of the APs with a different name, and add new entries with the proper group in the whitelist.
B) Reprovision the AP with a different group, and modify the name of one AP in the whitelist.
C) Create another AP group in the MC's configuration and reprovision one AP with a different group.
D) Reprovision one of the APs with a different name, and modify the name of one AP in the whitelist.
 A network administrator deploys a new Mobility Master (MM)-Mobility Controller (MC) network. To test the solution, the network administrator accessess some of the AP consoles and statistically provisions them. However, these APs do not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?
A network administrator deploys a new Mobility Master (MM)-Mobility Controller (MC) network. To test the solution, the network administrator accessess some of the AP consoles and statistically provisions them. However, these APs do not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?A) Reprovision one of the APs with a different name, and add new entries with the proper group in the whitelist.
B) Reprovision the AP with a different group, and modify the name of one AP in the whitelist.
C) Create another AP group in the MC's configuration and reprovision one AP with a different group.
D) Reprovision one of the APs with a different name, and modify the name of one AP in the whitelist.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck
54
Refer to the exhibit. 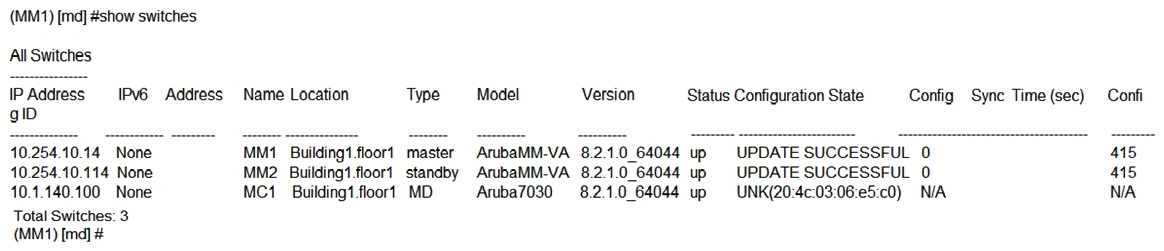 A network administrator adds a Mobility Controller (MC) in the /mm level and notices that the device does not show up in the managed networks hierarchy. The network administrator accesses the CLI, executes the show switches command, and obtains the output shown in the exhibit. What is the reason that the MC does not appear as a managed device in the hierarchy?
A network administrator adds a Mobility Controller (MC) in the /mm level and notices that the device does not show up in the managed networks hierarchy. The network administrator accesses the CLI, executes the show switches command, and obtains the output shown in the exhibit. What is the reason that the MC does not appear as a managed device in the hierarchy?
A) The network administrator added the device using the wrong Pre=shared Key (PSK).
B) The digital certificate of the MC is not trusted by the MM.
C) The IP address of the MC does not match the one that was defined in the MM.
D) The network administrator has not moved the device into a group yet.
 A network administrator adds a Mobility Controller (MC) in the /mm level and notices that the device does not show up in the managed networks hierarchy. The network administrator accesses the CLI, executes the show switches command, and obtains the output shown in the exhibit. What is the reason that the MC does not appear as a managed device in the hierarchy?
A network administrator adds a Mobility Controller (MC) in the /mm level and notices that the device does not show up in the managed networks hierarchy. The network administrator accesses the CLI, executes the show switches command, and obtains the output shown in the exhibit. What is the reason that the MC does not appear as a managed device in the hierarchy?A) The network administrator added the device using the wrong Pre=shared Key (PSK).
B) The digital certificate of the MC is not trusted by the MM.
C) The IP address of the MC does not match the one that was defined in the MM.
D) The network administrator has not moved the device into a group yet.

Unlock Deck
Unlock for access to all 54 flashcards in this deck.
Unlock Deck
k this deck


