Deck 6: AWS Certified Developer Associate (DVA-C01)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/470
Play
Full screen (f)
Deck 6: AWS Certified Developer Associate (DVA-C01)
1
An application stores images in an S3 bucket. Amazon S3 event notifications are used to trigger a Lambda function that resizes the images. Processing each image takes less than a second. How will AWS Lambda handle the additional traffic?
A) Lambda will scale out to execute the requests concurrently.
B) Lambda will handle the requests sequentially in the order received.
C) Lambda will process multiple images in a single execution.
D) Lambda will add more compute to each execution to reduce processing time.
A) Lambda will scale out to execute the requests concurrently.
B) Lambda will handle the requests sequentially in the order received.
C) Lambda will process multiple images in a single execution.
D) Lambda will add more compute to each execution to reduce processing time.
Lambda will scale out to execute the requests concurrently.
2
A Developer is working on an application that tracks hundreds of millions of product reviews in an Amazon DynamoDB table. The records include the data elements shown in the table:  Which field, when used as the partition key, would result in the MOST consistent performance using DynamoDB?
Which field, when used as the partition key, would result in the MOST consistent performance using DynamoDB?
A) starRating
B) reviewID
C) comment
D) productID
 Which field, when used as the partition key, would result in the MOST consistent performance using DynamoDB?
Which field, when used as the partition key, would result in the MOST consistent performance using DynamoDB?A) starRating
B) reviewID
C) comment
D) productID
reviewID
3
Where should an Elastic Beanstalk configuration file named healthcheckur1.config be placed in the application source bundle?
A) In the root of the application
B) In the bin folder
C) In healthcheckur1.config.ebextension under root In healthcheckur1.config.ebextension under root
D) In the .ebextensions folder In the .ebextensions folder
A) In the root of the application
B) In the bin folder
C) In healthcheckur1.config.ebextension under root In healthcheckur1.config.ebextension under root
D) In the .ebextensions folder In the .ebextensions folder
In the .ebextensions folder In the .ebextensions folder
4
A Developer has written a serverless application using multiple AWS services. The business logic is written as a Lambda function which has dependencies on third-party libraries. The Lambda function endpoints will be exposed using Amazon API Gateway. The Lambda function will write the information to Amazon DynamoDB. The Developer is ready to deploy the application but must have the ability to rollback. How can this deployment be automated, based on these requirements?
A) Deploy using Amazon Lambda API operations to create the Lambda function by providing a deployment package.
B) Use an AWS CloudFormation template and use CloudFormation syntax to define the Lambda function resource in the template.
C) Use syntax conforming to the Serverless Application Model in the AWS CloudFormation template to define the Lambda function resource.
D) Create a bash script which uses AWS CLI to package and deploy the application.
A) Deploy using Amazon Lambda API operations to create the Lambda function by providing a deployment package.
B) Use an AWS CloudFormation template and use CloudFormation syntax to define the Lambda function resource in the template.
C) Use syntax conforming to the Serverless Application Model in the AWS CloudFormation template to define the Lambda function resource.
D) Create a bash script which uses AWS CLI to package and deploy the application.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
5
A company wants to implement a continuous integration for its workloads on AWS. The company wants to trigger unit test in its pipeline for commits-on its code repository, and wants to be notified of failure events in the pipeline. How can these requirements be met?
A) Store the source code in AWS CodeCommit. Create a CodePipeline to automate unit testing. Use Amazon SNS to trigger notifications of failure events.
B) Store the source code in GitHub. Create a CodePipeline to automate unit testing. Use Amazon SES to trigger notifications of failure events.
C) Store the source code on GitHub. Create a CodePipeline to automate unit testing. Use Amazon CloudWatch to trigger notifications of failure events.
D) Store the source code in AWS CodeCommit. Create a CodePipeline to automate unit testing. Use Amazon CloudWatch to trigger notification of failure events.
A) Store the source code in AWS CodeCommit. Create a CodePipeline to automate unit testing. Use Amazon SNS to trigger notifications of failure events.
B) Store the source code in GitHub. Create a CodePipeline to automate unit testing. Use Amazon SES to trigger notifications of failure events.
C) Store the source code on GitHub. Create a CodePipeline to automate unit testing. Use Amazon CloudWatch to trigger notifications of failure events.
D) Store the source code in AWS CodeCommit. Create a CodePipeline to automate unit testing. Use Amazon CloudWatch to trigger notification of failure events.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
6
A Developer is asked to implement a caching layer in front of Amazon RDS. Cached content is expensive to regenerate in case of service failure. Which implementation below would work while maintaining maximum uptime?
A) Implement Amazon ElastiCache Redis in Cluster Mode
B) Install Redis on an Amazon EC2 instance.
C) Implement Amazon ElastiCache Memcached.
D) Migrate the database to Amazon Redshift.
A) Implement Amazon ElastiCache Redis in Cluster Mode
B) Install Redis on an Amazon EC2 instance.
C) Implement Amazon ElastiCache Memcached.
D) Migrate the database to Amazon Redshift.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
7
A Developer is creating a web application that requires authentication, but also needs to support guest access to provide users limited access without having to authenticate. What service can provide support for the application to allow guest access?
A) IAM temporary credentials using AWS STS.
B) Amazon Directory Service
C) Amazon Cognito with unauthenticated access enabled
D) IAM with SAML integration
A) IAM temporary credentials using AWS STS.
B) Amazon Directory Service
C) Amazon Cognito with unauthenticated access enabled
D) IAM with SAML integration

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
8
A serverless application uses an API Gateway and AWS Lambda. Where should the Lambda function store its session information across function calls?
A) In an Amazon DynamoDB table
B) In an Amazon SQS queue
C) In the local filesystem
D) In an SQLite session table using -DSQLITE_ENABLE_SESSION In an SQLite session table using -DSQLITE_ENABLE_SESSION
A) In an Amazon DynamoDB table
B) In an Amazon SQS queue
C) In the local filesystem
D) In an SQLite session table using -DSQLITE_ENABLE_SESSION In an SQLite session table using -DSQLITE_ENABLE_SESSION

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
9
A large e-commerce site is being designed to deliver static objects from Amazon S3. The Amazon S3 bucket will server more than 300 GET requests per second. What should be done to optimize performance? (Choose two.)
A) Integrate Amazon CloudFront with Amazon S3.
B) Enable Amazon S3 cross-region replication.
C) Delete expired Amazon S3 server log files.
D) Configure Amazon S3 lifecycle rules.
E) Randomize Amazon S3 key name prefixes.
A) Integrate Amazon CloudFront with Amazon S3.
B) Enable Amazon S3 cross-region replication.
C) Delete expired Amazon S3 server log files.
D) Configure Amazon S3 lifecycle rules.
E) Randomize Amazon S3 key name prefixes.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
10
A company is building a stock trading application that requires sub-millisecond latency in processing trading requests. Amazon DynamoDB is used to store all the trading data that is used to process each request. After load testing the application, the development team found that due to data retrieval times, the latency requirement is not satisfied. Because of sudden high spikes in the number of requests, DynamoDB read capacity has to be significantly over-provisioned to avoid throttling. What steps should be taken to meet latency requirements and reduce the cost of running the application?
A) Add Global Secondary Indexes for trading data.
B) Store trading data in Amazon S3 and use Transfer Acceleration.
C) Add retries with exponential back-off for DynamoDB queries
D) Use DynamoDB Accelerator to cache trading data.
A) Add Global Secondary Indexes for trading data.
B) Store trading data in Amazon S3 and use Transfer Acceleration.
C) Add retries with exponential back-off for DynamoDB queries
D) Use DynamoDB Accelerator to cache trading data.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
11
A Developer has created an S3 bucket s3://mycoolapp and has enabled server across logging that points to the folder s3://mycoolapp/logs. The Developer moved 100 KB of Cascading Style Sheets (CSS) documents to the folder s3://mycoolapp/css , and then stopped work. When the developer came back a few days later, the bucket was 50 GB. What is the MOST likely cause of this situation?
A) The CSS files were not compressed and S3 versioning was enabled.
B) S3 replication was enabled on the bucket.
C) Logging into the same bucket caused exponential log growth.
D) An S3 lifecycle policy has moved the entire CSS file to S3 Infrequent Access.
A) The CSS files were not compressed and S3 versioning was enabled.
B) S3 replication was enabled on the bucket.
C) Logging into the same bucket caused exponential log growth.
D) An S3 lifecycle policy has moved the entire CSS file to S3 Infrequent Access.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
12
A current architecture uses many Lambda functions invoking one another as a large state machine. The coordination of this state machine is legacy custom code that breaks easily. Which AWS Service can help refactor and manage the state machine?
A) AWS Data Pipeline
B) AWS SNS with AWS SQS
C) Amazon Elastic MapReduce
D) AWS Step Functions
A) AWS Data Pipeline
B) AWS SNS with AWS SQS
C) Amazon Elastic MapReduce
D) AWS Step Functions

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
13
A Developer is testing a Docker-based application that uses the AWS SDK to interact with Amazon DynamoDB. In the local development environment, the application has used IAM access keys. The application is now ready for deployment onto an ECS cluster. How should the application authenticate with AWS services in production?
A) Configure an ECS task IAM role for the application to use
B) Refactor the application to call AWS STS AssumeRole based on an instance role
C) Configure AWS access key/secret access key environment variables with new credentials
D) Configure the credentials file with a new access key/secret access key
A) Configure an ECS task IAM role for the application to use
B) Refactor the application to call AWS STS AssumeRole based on an instance role
C) Configure AWS access key/secret access key environment variables with new credentials
D) Configure the credentials file with a new access key/secret access key

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
14
An application under development is required to store hundreds of video files. The data must be encrypted within the application prior to storage, with a unique key for each video file. How should the Developer code the application?
A) Use the KMS Encrypt API to encrypt the data. Store the encrypted data key and data. Use the KMS Encrypt API to encrypt the data. Store the encrypted data key and data.
B) Use a cryptography library to generate an encryption key for the application. Use the encryption key to encrypt the data. Store the encrypted data.
C) Use the KMS GenerateDataKey API to get a data key. Encrypt the data with the data key. Store the encrypted data key and data. GenerateDataKey API to get a data key. Encrypt the data with the data key. Store the encrypted data key and data.
D) Upload the data to an S3 bucket using server side-encryption with an AWS KMS key.
A) Use the KMS Encrypt API to encrypt the data. Store the encrypted data key and data. Use the KMS Encrypt API to encrypt the data. Store the encrypted data key and data.
B) Use a cryptography library to generate an encryption key for the application. Use the encryption key to encrypt the data. Store the encrypted data.
C) Use the KMS GenerateDataKey API to get a data key. Encrypt the data with the data key. Store the encrypted data key and data. GenerateDataKey API to get a data key. Encrypt the data with the data key. Store the encrypted data key and data.
D) Upload the data to an S3 bucket using server side-encryption with an AWS KMS key.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
15
An application is designed to use Amazon SQS to manage messages from many independent senders. Each sender's messages must be processed in the order they are received. Which SQS feature should be implemented by the Developer?
A) Configure each sender with a unique MessageGroupId Configure each sender with a unique MessageGroupId
B) Enable MessageDeduplicationIds on the SQS queue Enable MessageDeduplicationIds on the SQS queue
C) Configure each message with unique MessageGroupIds.
D) Enable ContentBasedDeduplication on the SQS queue ContentBasedDeduplication
A) Configure each sender with a unique MessageGroupId Configure each sender with a unique MessageGroupId
B) Enable MessageDeduplicationIds on the SQS queue Enable MessageDeduplicationIds on the SQS queue
C) Configure each message with unique MessageGroupIds.
D) Enable ContentBasedDeduplication on the SQS queue ContentBasedDeduplication

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
16
An application takes 40 seconds to process instructions received in an Amazon SQS message. Assuming the SQS queue is configured with the default VisibilityTimeout value, what is the BEST way, upon receiving a message, to ensure that no other instances can retrieve a message that has already been processed or is currently being processed?
A) Use the ChangeMessageVisibility API to increase the VisibilityTimeout, then use the DeleteMessage API to delete the message.
B) Use the DeleteMessage API call to delete the message from the queue, then call DeleteQueue API to remove the queue.
C) Use the ChangeMessageVisibility API to decrease the timeout value, then use the DeleteMessage API to delete the message.
D) Use the DeleteMessageVisibility API to cancel the VisibilityTimeout, then use the DeleteMessage API to delete the message.
A) Use the ChangeMessageVisibility API to increase the VisibilityTimeout, then use the DeleteMessage API to delete the message.
B) Use the DeleteMessage API call to delete the message from the queue, then call DeleteQueue API to remove the queue.
C) Use the ChangeMessageVisibility API to decrease the timeout value, then use the DeleteMessage API to delete the message.
D) Use the DeleteMessageVisibility API to cancel the VisibilityTimeout, then use the DeleteMessage API to delete the message.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
17
A Developer is creating an Auto Scaling group whose instances need to publish a custom metric to Amazon CloudWatch. Which method would be the MOST secure way to authenticate a CloudWatch PUT request?
A) Create an IAM user with PutMetricData permission and put the user credentials in a private repository; have applications pull the credentials as needed.
B) Create an IAM user with PutMetricData permission, and modify the Auto Scaling launch configuration to inject the user credentials into the instance user data.
C) Modify the CloudWatch metric policies to allow the PutMetricData permission to instances from the Auto Scaling group.
D) Create an IAM role with PutMetricData permission and modify the Auto Scaling launching configuration to launch instances using that role.
A) Create an IAM user with PutMetricData permission and put the user credentials in a private repository; have applications pull the credentials as needed.
B) Create an IAM user with PutMetricData permission, and modify the Auto Scaling launch configuration to inject the user credentials into the instance user data.
C) Modify the CloudWatch metric policies to allow the PutMetricData permission to instances from the Auto Scaling group.
D) Create an IAM role with PutMetricData permission and modify the Auto Scaling launching configuration to launch instances using that role.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
18
An application reads data from an Amazon DynamoDB table. Several times a day, for a period of 15 seconds, the application receives multiple ProvisionedThroughputExceeded errors. How should this exception be handled?
A) Create a new global secondary index for the table to help with the additional requests.
B) Retry the failed read requests with exponential backoff.
C) Immediately retry the failed read requests.
D) Use the DynamoDB "UpdateItem" API to increase the provisioned throughput capacity of the table.
A) Create a new global secondary index for the table to help with the additional requests.
B) Retry the failed read requests with exponential backoff.
C) Immediately retry the failed read requests.
D) Use the DynamoDB "UpdateItem" API to increase the provisioned throughput capacity of the table.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
19
A deployment package uses the AWS CLI to copy files into any S3 bucket in the account, using access keys stored in environment variables. The package is running on EC2 instances, and the instances have been modified to run with an assumed IAM role and a more restrictive policy that allows access to only one bucket. After the change, the Developer logs into the host and still has the ability to write into all of the S3 buckets in that account. What is the MOST likely cause of this situation?
A) An IAM inline policy is being used on the IAM role
B) An IAM managed policy is being used on the IAM role
C) The AWS CLI is corrupt and needs to be reinstalled
D) The AWS credential provider looks for instance profile credentials last
A) An IAM inline policy is being used on the IAM role
B) An IAM managed policy is being used on the IAM role
C) The AWS CLI is corrupt and needs to be reinstalled
D) The AWS credential provider looks for instance profile credentials last

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
20
When writing a Lambda function, what is the benefit of instantiating AWS clients outside the scope of the handler?
A) Legibility and stylistic convention
B) Taking advantage of connection re-use
C) Better error handling
D) Creating a new instance per invocation
A) Legibility and stylistic convention
B) Taking advantage of connection re-use
C) Better error handling
D) Creating a new instance per invocation

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
21
An application is real-time processing millions of events that are received through an API. What service could be used to allow multiple consumers to process the data concurrently and MOST cost-effectively?
A) Amazon SNS with fanout to an SQS queue for each application
B) Amazon SNS with fanout to an SQS FIFO (first-in, firtst-out) queue for each application
C) Amazon Kinesis Firehouse
D) Amazon Kinesis Streams
A) Amazon SNS with fanout to an SQS queue for each application
B) Amazon SNS with fanout to an SQS FIFO (first-in, firtst-out) queue for each application
C) Amazon Kinesis Firehouse
D) Amazon Kinesis Streams

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
22
The Developer for a retail company must integrate a fraud detection solution into the order processing solution. The fraud detection solution takes between ten and thirty minutes to verify an order. At peak, the web site can receive one hundred orders per minute. What is the most scalable method to add the fraud detection solution to the order processing pipeline?
A) Add all new orders to an Amazon SQS queue. Configure a fleet of 10 EC2 instances spanning multiple AZs with the fraud detection solution installed on them to pull orders from this queue. Update the order with a pass or fails status.
B) Add all new orders to an SQS queue. Configure an Auto Scaling group that uses the queue depth metric as its unit of scale to launch a dynamically-sized fleet of EC2 instances spanning multiple AZs with the fraud detection solution installed on them to pull orders from this queue. Update the order with a pass or fails status.
C) Add all new orders to an Amazon Kinesis Stream. Subscribe a Lambda function to automatically read batches of records from the Kinesis Stream. The Lambda function includes the fraud detection software and will update the order with a pass or fail status.
D) Write all new orders to Amazon DynamoDB. Configure DynamoDB Streams to include all new orders. Subscribe a Lambda function to automatically read batches of records from the Kinesis Stream. The Lambda function includes the fraud detection software and will update the order with a pass or fail status.
A) Add all new orders to an Amazon SQS queue. Configure a fleet of 10 EC2 instances spanning multiple AZs with the fraud detection solution installed on them to pull orders from this queue. Update the order with a pass or fails status.
B) Add all new orders to an SQS queue. Configure an Auto Scaling group that uses the queue depth metric as its unit of scale to launch a dynamically-sized fleet of EC2 instances spanning multiple AZs with the fraud detection solution installed on them to pull orders from this queue. Update the order with a pass or fails status.
C) Add all new orders to an Amazon Kinesis Stream. Subscribe a Lambda function to automatically read batches of records from the Kinesis Stream. The Lambda function includes the fraud detection software and will update the order with a pass or fail status.
D) Write all new orders to Amazon DynamoDB. Configure DynamoDB Streams to include all new orders. Subscribe a Lambda function to automatically read batches of records from the Kinesis Stream. The Lambda function includes the fraud detection software and will update the order with a pass or fail status.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
23
An on-premises application is implemented using a Linux, Apache, MySQL and PHP (LAMP) stack. The Developer wants to run this application in AWS. Which of the following sets of AWS services can be used to run this stack?
A) Amazon API Gateway, Amazon S3
B) AWS Lambda, Amazon DynamoDB
C) Amazon EC2, Amazon Aurora
D) Amazon Cognito, Amazon RDS
E) Amazon ECS, Amazon EBS
A) Amazon API Gateway, Amazon S3
B) AWS Lambda, Amazon DynamoDB
C) Amazon EC2, Amazon Aurora
D) Amazon Cognito, Amazon RDS
E) Amazon ECS, Amazon EBS

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
24
An existing serverless application processes uploaded image files. The process currently uses a single Lambda function that takes an image file, performs the processing, and stores the file in Amazon S3. Users of the application now require thumbnail generation of the images. Users want to avoid any impact to the time it takes to perform the image uploads. How can thumbnail generation be added to the application, meeting user requirements while minimizing changes to existing code?
A) Change the existing Lambda function handling the uploads to create thumbnails at the time of upload. Have the function store both the image and thumbnail in Amazon S3.
B) Create a second Lambda function that handles thumbnail generation and storage. Change the existing Lambda function to invoke it asynchronously.
C) Create an S3 event notification with a Lambda function destination. Create a new Lambda function to generate and store thumbnails.
D) Create an S3 event notification to an SQS Queue. Create a scheduled Lambda function that processes the queue, and generates and stores thumbnails.
A) Change the existing Lambda function handling the uploads to create thumbnails at the time of upload. Have the function store both the image and thumbnail in Amazon S3.
B) Create a second Lambda function that handles thumbnail generation and storage. Change the existing Lambda function to invoke it asynchronously.
C) Create an S3 event notification with a Lambda function destination. Create a new Lambda function to generate and store thumbnails.
D) Create an S3 event notification to an SQS Queue. Create a scheduled Lambda function that processes the queue, and generates and stores thumbnails.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
25
A Developer must trigger an AWS Lambda function based on the item lifecycle activity in an Amazon DynamoDB table. How can the Developer create the solution?
A) Enable a DynamoDB stream that publishes an Amazon SNS message. Trigger the Lambda function synchronously from the SNS message.
B) Enable a DynamoDB stream that publishes an SNS message. Trigger the Lambda function asynchronously from the SNS message.
C) Enable a DynamoDB stream, and trigger the Lambda function synchronously from the stream.
D) Enable a DynamoDB stream, and trigger the Lambda function asynchronously from the stream.
A) Enable a DynamoDB stream that publishes an Amazon SNS message. Trigger the Lambda function synchronously from the SNS message.
B) Enable a DynamoDB stream that publishes an SNS message. Trigger the Lambda function asynchronously from the SNS message.
C) Enable a DynamoDB stream, and trigger the Lambda function synchronously from the stream.
D) Enable a DynamoDB stream, and trigger the Lambda function asynchronously from the stream.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
26
When a Developer tries to run an AWS CodeBuild project, it raises an error because the length of all environment variables exceeds the limit for the combined maximum of characters. What is the recommended solution?
A) Add the export LC_ALL="en_US.utf8" command to the pre_build section to ensure POSIX localization. Add the export LC_ALL="en_US.utf8" command to the pre_build section to ensure POSIX localization.
B) Use Amazon Cognito to store key-value pairs for large numbers of environment variables.
C) Update the settings for the build project to use an Amazon S3 bucket for large numbers of environment variables.
D) Use AWS Systems Manager Parameter Store to store large numbers of environment variables.
A) Add the export LC_ALL="en_US.utf8" command to the pre_build section to ensure POSIX localization. Add the export LC_ALL="en_US.utf8" command to the pre_build section to ensure POSIX localization.
B) Use Amazon Cognito to store key-value pairs for large numbers of environment variables.
C) Update the settings for the build project to use an Amazon S3 bucket for large numbers of environment variables.
D) Use AWS Systems Manager Parameter Store to store large numbers of environment variables.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
27
A website's page load times are gradually increasing as more users access the system at the same time. Analysis indicates that a user profile is being loaded from a database in all the web pages being visited by each user and this is increasing the database load and the page load latency. To address this issue the Developer decides to cache the user profile data. Which caching strategy will address this situation MOST efficiently?
A) Create a new Amazon EC2 Instance and run a NoSQL database on it. Cache the profile data within this database using the write-through caching strategy.
B) Create an Amazon ElastiCache cluster to cache the user profile data. Use a cache-aside caching strategy.
C) Use a dedicated Amazon RDS instance for caching profile data. Use a write-through caching strategy.
D) Create an ElastiCache cluster to cache the user profile data. Use a write-through caching strategy.
A) Create a new Amazon EC2 Instance and run a NoSQL database on it. Cache the profile data within this database using the write-through caching strategy.
B) Create an Amazon ElastiCache cluster to cache the user profile data. Use a cache-aside caching strategy.
C) Use a dedicated Amazon RDS instance for caching profile data. Use a write-through caching strategy.
D) Create an ElastiCache cluster to cache the user profile data. Use a write-through caching strategy.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
28
A set of APIs are exposed to customers using the Amazon API Gateway. These APIs have caching enabled on the API Gateway. Customers have asked for an option to invalidate this cache for each of the APIs. What action can be taken to allow API customers to invalidate the API Cache?
A) Ask customers to use AWS credentials to call the InvalidateCache API.
B) Ask customers to invoke an AWS API endpoint which invalidates the cache.
C) Ask customers to pass an HTTP header called Cache-Control:max-age=0.
D) Ask customers to add a query string parameter called "INVALIDATE_CACHE" when making an API call.
A) Ask customers to use AWS credentials to call the InvalidateCache API.
B) Ask customers to invoke an AWS API endpoint which invalidates the cache.
C) Ask customers to pass an HTTP header called Cache-Control:max-age=0.
D) Ask customers to add a query string parameter called "INVALIDATE_CACHE" when making an API call.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
29
A customer wants to deploy its source code on an AWS Elastic Beanstalk environment. The customer needs to perform deployment with minimal outage and should only use existing instances to retain application access log. What deployment policy would satisfy these requirements?
A) Rolling
B) All at once
C) Rolling with an additional batch
D) Immutable
A) Rolling
B) All at once
C) Rolling with an additional batch
D) Immutable

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
30
A Developer is developing an application that manages financial transactions. To improve security, multi-factor authentication (MFA) will be required as part of the login protocol. What services can the Developer use to meet these requirements?
A) Amazon DynamoDB to store MFA session data, and Amazon SNS to send MFA codes
B) Amazon Cognito with MFA
C) AWS Directory Service
D) AWS IAM with MFA enabled
A) Amazon DynamoDB to store MFA session data, and Amazon SNS to send MFA codes
B) Amazon Cognito with MFA
C) AWS Directory Service
D) AWS IAM with MFA enabled

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
31
An application running on EC2 instances is storing data in an S3 bucket. Security policy mandates that all data must be encrypted in transit. How can the Developer ensure that all traffic to the S3 bucket is encrypted?
A) Install certificates on the EC2 instances.
B) Create a bucket policy that allows traffic where SecureTransport is true.
C) Create an HTTPS redirect on the EC2 instances.
D) Create a bucket policy that denies traffic where SecureTransport is false.
A) Install certificates on the EC2 instances.
B) Create a bucket policy that allows traffic where SecureTransport is true.
C) Create an HTTPS redirect on the EC2 instances.
D) Create a bucket policy that denies traffic where SecureTransport is false.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
32
An application overwrites an object in Amazon S3, and then immediately reads the same object. Why would the application sometimes retrieve the old version of the object?
A) S3 overwrite PUTS are eventually consistent, so the application may read the old object.
B) The application needs to add extra metadata to label the latest version when uploading to Amazon S3.
C) All S3 PUTS are eventually consistent, so the application may read the old object.
D) The application needs to explicitly specify latest version when retrieving the object.
A) S3 overwrite PUTS are eventually consistent, so the application may read the old object.
B) The application needs to add extra metadata to label the latest version when uploading to Amazon S3.
C) All S3 PUTS are eventually consistent, so the application may read the old object.
D) The application needs to explicitly specify latest version when retrieving the object.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
33
A company is using AWS CodeBuild to compile a website from source code stored in AWS CodeCommit. A recent change to the source code has resulted in the CodeBuild project being unable to successfully compile the website. How should the Developer identify the cause of the failures?
A) Modify the buildspec.yml file to include steps to send the output of build commands to Amazon CloudWatch.
B) Use a custom Docker image that includes the AWS X-Ray agent in the AWS CodeBuild project configuration.
C) Check the build logs of the failed phase in the last build attempt in the AWS CodeBuild project build history.
D) Manually re-run the build process on a local machine so that the output can be visualized.
A) Modify the buildspec.yml file to include steps to send the output of build commands to Amazon CloudWatch.
B) Use a custom Docker image that includes the AWS X-Ray agent in the AWS CodeBuild project configuration.
C) Check the build logs of the failed phase in the last build attempt in the AWS CodeBuild project build history.
D) Manually re-run the build process on a local machine so that the output can be visualized.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
34
A Developer needs to use AWS X-Ray to monitor an application that is deployed on EC2 instances. What steps have to be executed to perform the monitoring?
A) Deploy the X-Ray SDK with the application and use X-Ray annotation.
B) Install the X-Ray daemon and instrument the application code.
C) Install the X-Ray daemon and configure it to forward data to Amazon CloudWatch Events.
D) Deploy the X-Ray SDK with the application and instrument the application code.
A) Deploy the X-Ray SDK with the application and use X-Ray annotation.
B) Install the X-Ray daemon and instrument the application code.
C) Install the X-Ray daemon and configure it to forward data to Amazon CloudWatch Events.
D) Deploy the X-Ray SDK with the application and instrument the application code.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
35
The Lambda function below is being called through an API using Amazon API Gateway. The average execution time for the Lambda function is about 1 second. The pseudocode for the Lambda function is as shown in the exhibit.  What two actions can be taken to improve the performance of this Lambda function without increasing the cost of the solution? (Choose two.)
What two actions can be taken to improve the performance of this Lambda function without increasing the cost of the solution? (Choose two.)
A) Package only the modules the Lambda function requires
B) Use Amazon DynamoDB instead of Amazon RDS
C) Move the initialization of the variable Amazon RDS connection outside of the handler function
D) Implement custom database connection pooling with the Lambda function
E) Implement local caching of Amazon RDS data so Lambda can re-use the cache
 What two actions can be taken to improve the performance of this Lambda function without increasing the cost of the solution? (Choose two.)
What two actions can be taken to improve the performance of this Lambda function without increasing the cost of the solution? (Choose two.)A) Package only the modules the Lambda function requires
B) Use Amazon DynamoDB instead of Amazon RDS
C) Move the initialization of the variable Amazon RDS connection outside of the handler function
D) Implement custom database connection pooling with the Lambda function
E) Implement local caching of Amazon RDS data so Lambda can re-use the cache

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
36
An application will ingest data at a very high throughput from many sources and must store the data in an Amazon S3 bucket. Which service would BEST accomplish this task?
A) Amazon Kinesis Firehose
B) Amazon S3 Acceleration Transfer
C) Amazon SQS
D) Amazon SNS
A) Amazon Kinesis Firehose
B) Amazon S3 Acceleration Transfer
C) Amazon SQS
D) Amazon SNS

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
37
A development team is using AWS Elastic Beanstalk to deploy a two-tier application that consists of a load-balanced web tier and an Amazon RDS database tier in production. The team would like to separate the RDS instance from the Elastic Beanstalk. How can this be accomplished?
A) Use the Elastic Beanstalk CLI to disassociate the database.
B) Use the AWS CLI to disassociate the database.
C) Change the deployment policy to disassociate the database.
D) Recreate a new Elastic Beanstalk environment without Amazon RDS.
A) Use the Elastic Beanstalk CLI to disassociate the database.
B) Use the AWS CLI to disassociate the database.
C) Change the deployment policy to disassociate the database.
D) Recreate a new Elastic Beanstalk environment without Amazon RDS.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
38
A gaming company is developing a mobile game application for iOS® and Android® platforms. This mobile game securely stores user data locally on the device. The company wants to allow users to use multiple device for the game, which requires user data synchronization across devices. Which service should be used to synchronize user data across devices without the need to create a backend application?
A) AWS Lambda
B) Amazon S3
C) Amazon DynamoDB
D) Amazon Cognito
A) AWS Lambda
B) Amazon S3
C) Amazon DynamoDB
D) Amazon Cognito

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
39
A static website is hosted in an Amazon S3 bucket. Several HTML pages on the site use JavaScript to download images from another Amazon S3 bucket. These images are not displayed when users browse the site. What is the possible cause for the issue?
A) The referenced Amazon S3 bucket is in another region.
B) The images must be stored in the same Amazon S3 bucket.
C) Port 80 must be opened on the security group in which the Amazon S3 bucket is located.
D) Cross Origin Resource Sharing must be enabled on the Amazon S3 bucket.
A) The referenced Amazon S3 bucket is in another region.
B) The images must be stored in the same Amazon S3 bucket.
C) Port 80 must be opened on the security group in which the Amazon S3 bucket is located.
D) Cross Origin Resource Sharing must be enabled on the Amazon S3 bucket.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
40
A company needs to encrypt data at rest, but it wants to leverage an AWS managed service using its own master key. Which of the following AWS service can be used to meet these requirements?
A) SSE with Amazon S3
B) SSE with AWS KMS
C) Client-side encryption
D) AWS IAM roles and policies
A) SSE with Amazon S3
B) SSE with AWS KMS
C) Client-side encryption
D) AWS IAM roles and policies

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
41
A company caches session information for a web application in an Amazon DynamoDB table. The company wants an automated way to delete old items from the table. What is the simplest way to do this?
A) Write a script that deletes old records; schedule the scripts as a cron job on an Amazon EC2 instance.
B) Add an attribute with the expiration time; enable the Time To Live feature based on that attribute.
C) Each day, create a new table to hold session data; delete the previous day's table.
D) Add an attribute with the expiration time; name the attribute ItemExpiration . Add an attribute with the expiration time; name the attribute ItemExpiration .
A) Write a script that deletes old records; schedule the scripts as a cron job on an Amazon EC2 instance.
B) Add an attribute with the expiration time; enable the Time To Live feature based on that attribute.
C) Each day, create a new table to hold session data; delete the previous day's table.
D) Add an attribute with the expiration time; name the attribute ItemExpiration . Add an attribute with the expiration time; name the attribute ItemExpiration .

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
42
A Development team is working on a case management solution that allows medical claims to be processed and reviewed. Users log in to provide information related to their medical and financial situations. As part of the application, sensitive documents such as medical records, medical imaging, bank statements, and receipts are uploaded to Amazon S3. All documents must be securely transmitted and stored. All access to the documents must be recorded for auditing. What is the MOST secure approach?
A) Use S3 default encryption using Advanced Encryption Standard-256 (AES-256) on the destination bucket.
B) Use Amazon Cognito for authorization and authentication to ensure the security of the application and documents.
C) Use AWS Lambda to encrypt and decrypt objects as they are placed into the S3 bucket.
D) Use client-side encryption/decryption with Amazon S3 and AWS KMS.
A) Use S3 default encryption using Advanced Encryption Standard-256 (AES-256) on the destination bucket.
B) Use Amazon Cognito for authorization and authentication to ensure the security of the application and documents.
C) Use AWS Lambda to encrypt and decrypt objects as they are placed into the S3 bucket.
D) Use client-side encryption/decryption with Amazon S3 and AWS KMS.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
43
A company has an internet-facing application that uses Web Identity Federation to obtain a temporary credential from AWS Security Token Service (AWS STS). The app then uses the token to access AWS services. Review the following response: 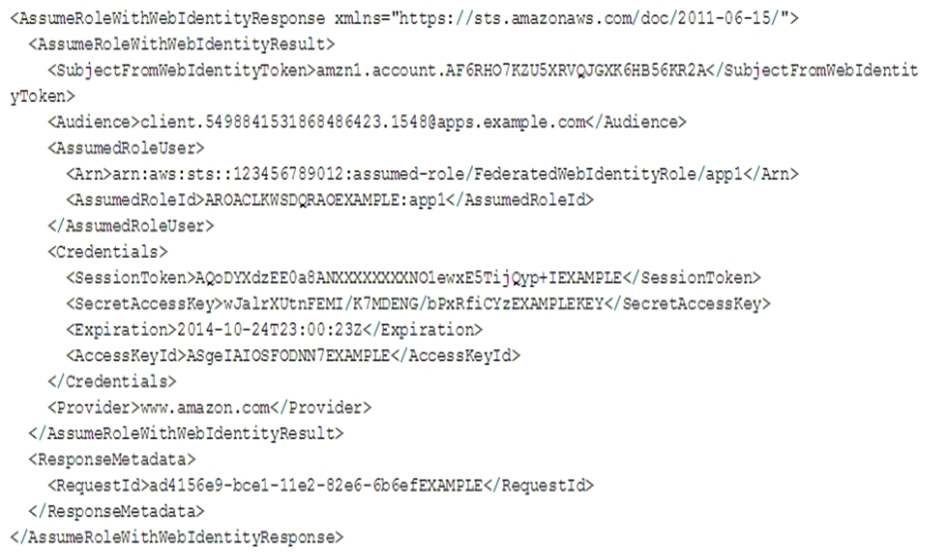 Based on the response displayed, what permissions are associated with the call from the application?
Based on the response displayed, what permissions are associated with the call from the application?
A) Permissions associated with the role AROACLKWSDQRAOEXAMPLE:app1 Permissions associated with the role AROACLKWSDQRAOEXAMPLE:app1
B) Permissions associated with the default role used when the AWS service was built
C) Permission associated with the IAM principal that owns the AccessKeyID ASgeIAIOSFODNN7EXAMPLE Permission associated with the IAM principal that owns the AccessKeyID ASgeIAIOSFODNN7EXAMPLE
D) Permissions associated with the account that owns the AWS service
 Based on the response displayed, what permissions are associated with the call from the application?
Based on the response displayed, what permissions are associated with the call from the application?A) Permissions associated with the role AROACLKWSDQRAOEXAMPLE:app1 Permissions associated with the role AROACLKWSDQRAOEXAMPLE:app1
B) Permissions associated with the default role used when the AWS service was built
C) Permission associated with the IAM principal that owns the AccessKeyID ASgeIAIOSFODNN7EXAMPLE Permission associated with the IAM principal that owns the AccessKeyID ASgeIAIOSFODNN7EXAMPLE
D) Permissions associated with the account that owns the AWS service

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
44
Queries to an Amazon DynamoDB table are consuming a large amount of read capacity. The table has a significant number of large attributes. The application does not need all of the attribute data. How can DynamoDB costs be minimized while maximizing application performance?
A) Batch all the writes, and perform the write operations when no or few reads are being performed.
B) Create a global secondary index with a minimum set of projected attributes.
C) Implement exponential backoffs in the application.
D) Load balance the reads to the table using an Application Load Balancer.
A) Batch all the writes, and perform the write operations when no or few reads are being performed.
B) Create a global secondary index with a minimum set of projected attributes.
C) Implement exponential backoffs in the application.
D) Load balance the reads to the table using an Application Load Balancer.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
45
A company has an AWS CloudFormation template that is stored as a single file. The template is able to launch and create a full infrastructure stack. Which best practice would increase the maintainability of the template?
A) Use nested stacks for common template patterns.
B) Embed credentials to prevent typos.
C) Remove mappings to decrease the number of variables.
D) Use AWS::Include to reference publicly-hosted template files. Use AWS::Include to reference publicly-hosted template files.
A) Use nested stacks for common template patterns.
B) Embed credentials to prevent typos.
C) Remove mappings to decrease the number of variables.
D) Use AWS::Include to reference publicly-hosted template files. Use AWS::Include to reference publicly-hosted template files.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
46
An organization is storing large files in Amazon S3, and is writing a web application to display meta-data about the files to end-users. Based on the metadata a user selects an object to download. The organization needs a mechanism to index the files and provide single-digit millisecond latency retrieval for the metadata. What AWS service should be used to accomplish this?
A) Amazon DynamoDB
B) Amazon EC2
C) AWS Lambda
D) Amazon RDS
A) Amazon DynamoDB
B) Amazon EC2
C) AWS Lambda
D) Amazon RDS

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
47
Where can PortMapping be defined when launching containers in Amazon ECS?
A) Security groups
B) Amazon Elastic Container Registry (Amazon ECR)
C) Container agent
D) Task definition
A) Security groups
B) Amazon Elastic Container Registry (Amazon ECR)
C) Container agent
D) Task definition

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
48
The upload of a 15 GB object to Amazon S3 fails. The error message reads: "Your proposed upload exceeds the maximum allowed object size." What technique will allow the Developer to upload this object?
A) Upload the object using the multi-part upload API.
B) Upload the object over an AWS Direct Connect connection.
C) Contact AWS Support to increase the object size limit.
D) Upload the object to another AWS region.
A) Upload the object using the multi-part upload API.
B) Upload the object over an AWS Direct Connect connection.
C) Contact AWS Support to increase the object size limit.
D) Upload the object to another AWS region.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
49
A company needs a fully-managed source control service that will work in AWS. The service must ensure that revision control synchronizes multiple distributed repositories by exchanging sets of changes peer-to-peer. All users need to work productively even when not connected to a network. Which source control service should be used?
A) Subversion
B) AWS CodeBuild
C) AWS CodeCommit
D) AWS CodeStar
A) Subversion
B) AWS CodeBuild
C) AWS CodeCommit
D) AWS CodeStar

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
50
A company needs a new REST API that can return information about the contents of an Amazon S3 bucket, such as a count of the objects stored in it. The company has decided that the new API should be written as a microservice using AWS Lambda and Amazon API Gateway. How should the Developer ensure that the microservice has the necessary access to the Amazon S3 bucket, while adhering to security best practices?
A) Create an IAM user that has permissions to access the Amazon S3 bucket, and store the IAM user credentials in the Lambda function source code.
B) Create an IAM role that has permissions to access the Amazon S3 bucket and assign it to the Lambda function as its execution role.
C) Create an Amazon S3 bucket policy that specifies the Lambda service as its principal and assign it to the Amazon S3 bucket.
D) Create an IAM role, attach the AmazonS3FullAccess managed policy to it, and assign the role to the Lambda function as its execution role.
A) Create an IAM user that has permissions to access the Amazon S3 bucket, and store the IAM user credentials in the Lambda function source code.
B) Create an IAM role that has permissions to access the Amazon S3 bucket and assign it to the Lambda function as its execution role.
C) Create an Amazon S3 bucket policy that specifies the Lambda service as its principal and assign it to the Amazon S3 bucket.
D) Create an IAM role, attach the AmazonS3FullAccess managed policy to it, and assign the role to the Lambda function as its execution role.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
51
A Developer is writing an imaging micro service on AWS Lambda. The service is dependent on several libraries that are not available in the Lambda runtime environment. Which strategy should the Developer follow to create the Lambda deployment package?
A) Create a ZIP file with the source code and all dependent libraries.
B) Create a ZIP file with the source code and a script that installs the dependent libraries at runtime.
C) Create a ZIP file with the source code. Stage the dependent libraries on an Amazon S3 bucket indicated by the Lambda environment variable LD_LIBRARY_PATH Create a ZIP file with the source code. Stage the dependent libraries on an Amazon S3 bucket indicated by the Lambda environment variable LD_LIBRARY_PATH
D) Create a ZIP file with the source code and a buildspec.yaml file that installs the dependent libraries on AWS Lambda.
A) Create a ZIP file with the source code and all dependent libraries.
B) Create a ZIP file with the source code and a script that installs the dependent libraries at runtime.
C) Create a ZIP file with the source code. Stage the dependent libraries on an Amazon S3 bucket indicated by the Lambda environment variable LD_LIBRARY_PATH Create a ZIP file with the source code. Stage the dependent libraries on an Amazon S3 bucket indicated by the Lambda environment variable LD_LIBRARY_PATH
D) Create a ZIP file with the source code and a buildspec.yaml file that installs the dependent libraries on AWS Lambda.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
52
What does an Amazon SQS delay queue accomplish?
A) Messages are hidden for a configurable amount of time when they are first added to the queue.
B) Messages are hidden for a configurable amount of time after they are consumed from the queue.
C) The consumer can poll the queue for a configurable amount of time before retrieving a message.
D) Message cannot be deleted for a configurable amount of time after they are consumed from the queue.
A) Messages are hidden for a configurable amount of time when they are first added to the queue.
B) Messages are hidden for a configurable amount of time after they are consumed from the queue.
C) The consumer can poll the queue for a configurable amount of time before retrieving a message.
D) Message cannot be deleted for a configurable amount of time after they are consumed from the queue.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
53
A Developer has developed a web application and wants to deploy it quickly on a Tomcat server on AWS. The Developer wants to avoid having to manage the underlying infrastructure. What is the easiest way to deploy the application, based on these requirements?
A) AWS CloudFormation
B) AWS Elastic Beanstalk
C) Amazon S3
D) AWS CodePipeline
A) AWS CloudFormation
B) AWS Elastic Beanstalk
C) Amazon S3
D) AWS CodePipeline

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
54
An application running on Amazon EC2 instances must access objects within an Amazon S3 bucket that are encrypted using server-side encryption using AWS KMS encryption keys (SSE-KMS). The application must have access to the customer master key (CMK) to decrypt the objects. Which combination of steps will grant the application access? (Choose two.)
A) Write an S3 bucket policy that grants the bucket access to the key.
B) Grant access to the key in the IAM EC2 role attached to the application's EC2 instances.
C) Write a key policy that enables IAM policies to grant access to the key.
D) Grant access to the key in the S3 bucket's ACL
E) Create a Systems Manager parameter that exposes the KMS key to the EC2 instances.
A) Write an S3 bucket policy that grants the bucket access to the key.
B) Grant access to the key in the IAM EC2 role attached to the application's EC2 instances.
C) Write a key policy that enables IAM policies to grant access to the key.
D) Grant access to the key in the S3 bucket's ACL
E) Create a Systems Manager parameter that exposes the KMS key to the EC2 instances.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
55
An application is expected to process many files. Each file takes four minutes to process each AWS Lambda invocation. The Lambda function does not return any important data. What is the fastest way to process all the files?
A) First split the files to make them smaller, then process with synchronous RequestResponse Lambda invocations. First split the files to make them smaller, then process with synchronous RequestResponse Lambda invocations.
B) Make synchronous RequestResponse Lambda invocations and process the files one by one. Make synchronous Lambda invocations and process the files one by one.
C) Make asynchronous Event Lambda invocations and process the files in parallel. Make asynchronous Event Lambda invocations and process the files in parallel.
D) First join all the files, then process it all at once with an asynchronous Event Lambda invocation. First join all the files, then process it all at once with an asynchronous Lambda invocation.
A) First split the files to make them smaller, then process with synchronous RequestResponse Lambda invocations. First split the files to make them smaller, then process with synchronous RequestResponse Lambda invocations.
B) Make synchronous RequestResponse Lambda invocations and process the files one by one. Make synchronous Lambda invocations and process the files one by one.
C) Make asynchronous Event Lambda invocations and process the files in parallel. Make asynchronous Event Lambda invocations and process the files in parallel.
D) First join all the files, then process it all at once with an asynchronous Event Lambda invocation. First join all the files, then process it all at once with an asynchronous Lambda invocation.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
56
A stock market monitoring application uses Amazon Kinesis for data ingestion. During simulated tests of peak data rates, the Kinesis stream cannot keep up with the incoming data. What step will allow Kinesis to accommodate the traffic during peak hours?
A) Install the Kinesis Producer Library (KPL) for ingesting data into the stream.
B) Reduce the data retention period to allow for more data ingestion using DecreaseStreamRetentionPeriod . Reduce the data retention period to allow for more data ingestion using DecreaseStreamRetentionPeriod .
C) Increase the shard count of the stream using UpdateShardCount . Increase the shard count of the stream using UpdateShardCount
D) Ingest multiple records into the stream in a single call using PutRecords . Ingest multiple records into the stream in a single call using PutRecords
A) Install the Kinesis Producer Library (KPL) for ingesting data into the stream.
B) Reduce the data retention period to allow for more data ingestion using DecreaseStreamRetentionPeriod . Reduce the data retention period to allow for more data ingestion using DecreaseStreamRetentionPeriod .
C) Increase the shard count of the stream using UpdateShardCount . Increase the shard count of the stream using UpdateShardCount
D) Ingest multiple records into the stream in a single call using PutRecords . Ingest multiple records into the stream in a single call using PutRecords

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
57
A Developer wants to encrypt new objects that are being uploaded to an Amazon S3 bucket by an application. There must be an audit trail of who has used the key during this process. There should be no change to the performance of the application. Which type of encryption meets these requirements?
A) Server-side encryption using S3-managed keys
B) Server-side encryption with AWS KMS-managed keys
C) Client-side encryption with a client-side symmetric master key
D) Client-side encryption with AWS KMS-managed keys
A) Server-side encryption using S3-managed keys
B) Server-side encryption with AWS KMS-managed keys
C) Client-side encryption with a client-side symmetric master key
D) Client-side encryption with AWS KMS-managed keys

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
58
A Developer is writing a serverless application that requires that an AWS Lambda function be invoked every 10 minutes. What is an automated and serverless way to trigger the function?
A) Deploy an Amazon EC2 instance based on Linux, and edit its /etc/crontab file by adding a command to periodically invoke the Lambda function.
B) Configure an environment variable named PERIOD for the Lambda function. Set the value to 600.
C) Create an Amazon CloudWatch Events rule that triggers on a regular schedule to invoke the Lambda function.
D) Create an Amazon SNS topic that has a subscription to the Lambda function with a 600-second timer.
A) Deploy an Amazon EC2 instance based on Linux, and edit its /etc/crontab file by adding a command to periodically invoke the Lambda function.
B) Configure an environment variable named PERIOD for the Lambda function. Set the value to 600.
C) Create an Amazon CloudWatch Events rule that triggers on a regular schedule to invoke the Lambda function.
D) Create an Amazon SNS topic that has a subscription to the Lambda function with a 600-second timer.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
59
A Developer is creating a Lambda function that will generate and export a file. The function requires 100 MB of temporary storage for temporary files while executing. These files will not be needed after the function is complete. How can the Developer MOST efficiently handle the temporary files?
A) Store the files in EBS and delete the files at the end of the Lambda function.
B) Copy the files to EFS and delete the files at the end of the Lambda function.
C) Store the files in the /tmp directory and delete the files at the end of the Lambda function.
D) Copy the files to an S3 bucket with a lifecycle policy to delete the files.
A) Store the files in EBS and delete the files at the end of the Lambda function.
B) Copy the files to EFS and delete the files at the end of the Lambda function.
C) Store the files in the /tmp directory and delete the files at the end of the Lambda function.
D) Copy the files to an S3 bucket with a lifecycle policy to delete the files.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
60
An application uses Amazon Kinesis Data Streams to ingest and process large streams of data records in real time. Amazon EC2 instances consume and process the data from the shards of the Kinesis data stream by using Amazon Kinesis Client Library (KCL). The application handles the failure scenarios and does not require standby workers. The application reports that a specific shard is receiving more data than expected. To adapt to the changes in the rate of data flow, the "hot" shard is resharded. Assuming that the initial number of shards in the Kinesis data stream is 4, and after resharding the number of shards increased to 6, what is the maximum number of EC2 instances that can be deployed to process data from all the shards?
A) 12
B) 6
C) 4
D) 1
A) 12
B) 6
C) 4
D) 1

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
61
A Development team currently supports an application that uses an in-memory store to save accumulated game results. Individual results are stored in a database. As part of migrating to AWS, the team needs to use automatic scaling. The team knows this will yield inconsistent results. Where should the team store these accumulated game results to BEST allow for consistent results without impacting performance?
A) Amazon S3
B) Amazon RDS
C) Amazon ElastiCache
D) Amazon Kinesis
A) Amazon S3
B) Amazon RDS
C) Amazon ElastiCache
D) Amazon Kinesis

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
62
A Developer has created a Lambda function and is finding that the function is taking longer to complete than expected. After some debugging, the Developer has discovered that increasing compute capacity would improve performance. How can the Developer increase the Lambda compute resources?
A) Run on a larger instance size with more compute capacity.
B) Increase the maximum execution time.
C) Specify a larger compute capacity when calling the Lambda function.
D) Increase the allocated memory for the Lambda function.
A) Run on a larger instance size with more compute capacity.
B) Increase the maximum execution time.
C) Specify a larger compute capacity when calling the Lambda function.
D) Increase the allocated memory for the Lambda function.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
63
A company has an application that logs all information to Amazon S3. Whenever there is a new log file, an AWS Lambda function is invoked to process the log files. The code works, gathering all of the necessary information. However, when checking the Lambda function logs, duplicate entries with the same request ID are found. What is causing the duplicate entries?
A) The S3 bucket name was specified incorrectly.
B) The Lambda function failed, and the Lambda service retried the invocation with a delay.
C) There was an S3 outage, which caused duplicate entries of the same log file.
D) The application stopped intermittently and then resumed.
A) The S3 bucket name was specified incorrectly.
B) The Lambda function failed, and the Lambda service retried the invocation with a delay.
C) There was an S3 outage, which caused duplicate entries of the same log file.
D) The application stopped intermittently and then resumed.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
64
A company is using Amazon RDS MySQL instances for its application database tier and Apache Tomcat servers for its web tier. Most of the database queries from web applications are repeated read requests. Use of which AWS service would increase in performance by adding in-memory store for repeated read queries?
A) Amazon RDS Multi-AZ
B) Amazon SQS
C) Amazon ElastiCache
D) Amazon RDS read replica
A) Amazon RDS Multi-AZ
B) Amazon SQS
C) Amazon ElastiCache
D) Amazon RDS read replica

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
65
A company is providing services to many downstream consumers. Each consumer may connect to one or more services. This has resulted in a complex architecture that is difficult to manage and does not scale well. The company needs a single interface to manage these services to consumers. Which AWS service should be used to refactor this architecture?
A) AWS Lambda
B) AWS X-Ray
C) Amazon SQS
D) Amazon API Gateway
A) AWS Lambda
B) AWS X-Ray
C) Amazon SQS
D) Amazon API Gateway

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
66
A company uses Amazon DynamoDB for managing and tracking orders. The DynamoDB table is partitioned based on the order date. The company receives a huge increase in orders during a sales event, causing DynamoDB writes to throttle, and the consumed throughput is far below the provisioned throughput. According to AWS best practices, how can this issue be resolved with MINIMAL costs?
A) Create a new DynamoDB table for every order date.
B) Increase the read and write capacity units of the DynamoDB table.
C) Add a random number suffix to the partition key values.
D) Add a global secondary index to the DynamoDB table.
A) Create a new DynamoDB table for every order date.
B) Increase the read and write capacity units of the DynamoDB table.
C) Add a random number suffix to the partition key values.
D) Add a global secondary index to the DynamoDB table.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
67
A Developer is building a mobile application and needs any update to user profile data to be pushed to all devices accessing the specific identity. The Developer does not want to manage a back end to maintain the user profile data. What is the MOST efficient way for the Developer to achieve these requirements using Amazon Cognito?
A) Use Cognito federated identities.
B) Use a Cognito user pool.
C) Use Cognito Sync.
D) Use Cognito events.
A) Use Cognito federated identities.
B) Use a Cognito user pool.
C) Use Cognito Sync.
D) Use Cognito events.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
68
A company maintains a REST service using Amazon API Gateway and the API Gateway native API key validation. The company recently launched a new registration page, which allows users to sign up for the service. The registration page creates a new API key using CreateApiKey and sends the new key to the user. When the user attempts to call the API using this key, the user receives a 403 Forbidden error. Existing users are unaffected and can still call the API. What code updates will grant these new users access to the API?
A) The createDeployment method must be called so the API can be redeployed to include the newly created API key. The createDeployment method must be called so the API can be redeployed to include the newly created API key.
B) The updateAuthorizer method must be called to update the API's authorizer to include the newly created API key. updateAuthorizer method must be called to update the API's authorizer to include the newly created API key.
C) The importApiKeys method must be called to import all newly created API keys into the current stage of the API. importApiKeys method must be called to import all newly created API keys into the current stage of the API.
D) The createUsagePlanKey method must be called to associate the newly created API key with the correct usage plan. createUsagePlanKey method must be called to associate the newly created API key with the correct usage plan.
A) The createDeployment method must be called so the API can be redeployed to include the newly created API key. The createDeployment method must be called so the API can be redeployed to include the newly created API key.
B) The updateAuthorizer method must be called to update the API's authorizer to include the newly created API key. updateAuthorizer method must be called to update the API's authorizer to include the newly created API key.
C) The importApiKeys method must be called to import all newly created API keys into the current stage of the API. importApiKeys method must be called to import all newly created API keys into the current stage of the API.
D) The createUsagePlanKey method must be called to associate the newly created API key with the correct usage plan. createUsagePlanKey method must be called to associate the newly created API key with the correct usage plan.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
69
A Developer is making changes to a custom application that is currently using AWS Elastic Beanstalk. After the Developer completes the changes, what solutions will update the Elastic Beanstalk environment with the new application version? (Choose two.)
A) Package the application code into a .zip file, and upload, then deploy the packaged application from the AWS Management Console
B) Package the application code into a .tar file, create a new application version from the AWS Management Console, then update the environment by using AWS CLI
C) Package the application code into a .tar file, and upload and deploy the packaged application from the AWS Management Console
D) Package the application code into a .zip file, create a new application version from the packaged application by using AWS CLI, then update the environment by using AWS CLI
E) Package the application code into a .zip file, create a new application version from the AWS Management Console, then rebuild the environment by using AWS CLI
A) Package the application code into a .zip file, and upload, then deploy the packaged application from the AWS Management Console
B) Package the application code into a .tar file, create a new application version from the AWS Management Console, then update the environment by using AWS CLI
C) Package the application code into a .tar file, and upload and deploy the packaged application from the AWS Management Console
D) Package the application code into a .zip file, create a new application version from the packaged application by using AWS CLI, then update the environment by using AWS CLI
E) Package the application code into a .zip file, create a new application version from the AWS Management Console, then rebuild the environment by using AWS CLI

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
70
A Developer is designing a new application that uses Amazon S3. To satisfy compliance requirements, the Developer must encrypt the data at rest. How can the Developer accomplish this?
A) Use s3:x-amz-acl as a condition in the S3 bucket policy. Use s3:x-amz-acl as a condition in the S3 bucket policy.
B) Use Amazon RDS with default encryption.
C) Use aws:SecureTransport as a condition in the S3 bucket policy. aws:SecureTransport
D) Turn on S3 default encryption for the S3 bucket.
A) Use s3:x-amz-acl as a condition in the S3 bucket policy. Use s3:x-amz-acl as a condition in the S3 bucket policy.
B) Use Amazon RDS with default encryption.
C) Use aws:SecureTransport as a condition in the S3 bucket policy. aws:SecureTransport
D) Turn on S3 default encryption for the S3 bucket.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
71
A Developer has a stateful web server on-premises that is being migrated to AWS. The Developer must have greater elasticity in the new design. How should the Developer re-factor the application to make it more elastic? (Choose two.)
A) Use pessimistic concurrency on Amazon DynamoDB
B) Use Amazon CloudFront with an Auto Scaling group
C) Use Amazon CloudFront with an AWS Web Application Firewall
D) Store session state data in an Amazon DynamoDB table
E) Use an ELB with an Auto Scaling group
A) Use pessimistic concurrency on Amazon DynamoDB
B) Use Amazon CloudFront with an Auto Scaling group
C) Use Amazon CloudFront with an AWS Web Application Firewall
D) Store session state data in an Amazon DynamoDB table
E) Use an ELB with an Auto Scaling group

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
72
A Developer is creating an AWS Lambda function to process a stream of data from an Amazon Kinesis Data Stream. When the Lambda function parses the data and encounters a missing field, it exits the function with an error. The function is generating duplicate records from the Kinesis stream. When the Developer looks at the stream output without the Lambda function, there are no duplicate records. What is the reason for the duplicates?
A) The Lambda function did not advance the Kinesis stream pointer to the next record after the error.
B) The Lambda event source used asynchronous invocation, resulting in duplicate records.
C) The Lambda function did not handle the error, and the Lambda service attempted to reprocess the data.
D) The Lambda function is not keeping up with the amount of data coming from the stream.
A) The Lambda function did not advance the Kinesis stream pointer to the next record after the error.
B) The Lambda event source used asynchronous invocation, resulting in duplicate records.
C) The Lambda function did not handle the error, and the Lambda service attempted to reprocess the data.
D) The Lambda function is not keeping up with the amount of data coming from the stream.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
73
An application that runs on an Amazon EC2 instance needs to access and make API calls to multiple AWS services. What is the MOST secure way to provide access to the AWS services with MINIMAL management overhead?
A) Use AWS KMS to store and retrieve credentials.
B) Use EC2 instance profiles.
C) Use AWS root user to make requests to the application.
D) Store and retrieve credentials from AWS CodeCommit.
A) Use AWS KMS to store and retrieve credentials.
B) Use EC2 instance profiles.
C) Use AWS root user to make requests to the application.
D) Store and retrieve credentials from AWS CodeCommit.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
74
A Developer has published an update to an application that is served to a global user base using Amazon CloudFront. After deploying the application, users are not able to see the updated changes. How can the Developer resolve this issue?
A) Remove the origin from the CloudFront configuration and add it again.
B) Disable forwarding of query strings and request headers from the CloudFront distribution configuration.
C) Invalidate all the application objects from the edge caches.
D) Disable the CloudFront distribution and enable it again to update all the edge locations.
A) Remove the origin from the CloudFront configuration and add it again.
B) Disable forwarding of query strings and request headers from the CloudFront distribution configuration.
C) Invalidate all the application objects from the edge caches.
D) Disable the CloudFront distribution and enable it again to update all the edge locations.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
75
A company is migrating a single-server, on-premises web application to AWS. The company intends to use multiple servers behind an Elastic Load Balancer (ELB) to balance the load, and will also store session data in memory on the web server. The company does not want to lose that session data if a server fails or goes offline, and it wants to minimize user's downtime. Where should the company move session data to MOST effectively reduce downtime and make users' session data more fault tolerant?
A) An Amazon ElastiCache for Redis cluster
B) A second Amazon EBS volume
C) The web server's primary disk
D) An Amazon EC2 instance dedicated to session data
A) An Amazon ElastiCache for Redis cluster
B) A second Amazon EBS volume
C) The web server's primary disk
D) An Amazon EC2 instance dedicated to session data

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
76
A Developer must analyze performance issues with production-distributed applications written as AWS Lambda functions. These distributed Lambda applications invoke other components that make up the applications. How should the Developer identify and troubleshoot the root cause of the performance issues in production?
A) Add logging statements to the Lambda functions, then use Amazon CloudWatch to view the logs.
B) Use AWS CloudTrail and then examine the logs.
C) Use AWS X-Ray, then examine the segments and errors.
D) Run Amazon Inspector agents and then analyze performance.
A) Add logging statements to the Lambda functions, then use Amazon CloudWatch to view the logs.
B) Use AWS CloudTrail and then examine the logs.
C) Use AWS X-Ray, then examine the segments and errors.
D) Run Amazon Inspector agents and then analyze performance.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
77
A company has a multi-tiered web application on AWS. During a recent spike in traffic, one of the primary relational databases on Amazon RDS could not serve all the traffic. Some read queries for repeatedly accessed items failed, so users received error messages. What can be done to minimize the impact on database read queries MOST efficiently during future traffic spikes?
A) Use Amazon S3 to cache database query results.
B) Use Amazon RDS as a custom origin for Amazon CloudFront.
C) Use local storage and memory on Amazon EC2 instances to cache data.
D) Use Amazon ElastiCache in front of the primary database to cache data.
A) Use Amazon S3 to cache database query results.
B) Use Amazon RDS as a custom origin for Amazon CloudFront.
C) Use local storage and memory on Amazon EC2 instances to cache data.
D) Use Amazon ElastiCache in front of the primary database to cache data.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
78
A Developer wants access to make the log data of an application running on an EC2 instance available to systems administrators. Which of the following enables monitoring of this metric in Amazon CloudWatch?
A) Retrieve the log data from CloudWatch using the GetMetricData API call. Retrieve the log data from CloudWatch using the GetMetricData API call.
B) Retrieve the log data from AWS CloudTrail using the LookupEvents API call. Retrieve the log data from AWS CloudTrail using the LookupEvents API call.
C) Launch a new EC2 instance, configure Amazon CloudWatch Events, and then install the application.
D) Install the Amazon CloudWatch Logs agent on the EC2 instance that the application is running on.
A) Retrieve the log data from CloudWatch using the GetMetricData API call. Retrieve the log data from CloudWatch using the GetMetricData API call.
B) Retrieve the log data from AWS CloudTrail using the LookupEvents API call. Retrieve the log data from AWS CloudTrail using the LookupEvents API call.
C) Launch a new EC2 instance, configure Amazon CloudWatch Events, and then install the application.
D) Install the Amazon CloudWatch Logs agent on the EC2 instance that the application is running on.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
79
A company is running an application built on AWS Lambda functions. One Lambda function has performance issues when it has to download a 50MB file from the Internet in every execution. This function is called multiple times a second. What solution would give the BEST performance increase?
A) Cache the file in the /tmp directory
B) Increase the Lambda maximum execution time
C) Put an Elastic Load Balancer in front of the Lambda function
D) Cache the file in Amazon S3
A) Cache the file in the /tmp directory
B) Increase the Lambda maximum execution time
C) Put an Elastic Load Balancer in front of the Lambda function
D) Cache the file in Amazon S3

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck
80
A Developer created configuration specifications for an AWS Elastic Beanstalk application in a file named healthcheckurl.yaml in the .ebextensions/directory of their application source bundle. The file contains the following:  After the application launches, the health check is not being run on the correct path, even though it is valid. What can be done to correct this configuration file?
After the application launches, the health check is not being run on the correct path, even though it is valid. What can be done to correct this configuration file?
A) Convert the file to JSON format.
B) Rename the file to a .config extension.
C) Change the configuration section from options_settings to resources . Change the configuration section from options_settings to resources .
D) Change the namespace of the option settings to a custom namespace.
 After the application launches, the health check is not being run on the correct path, even though it is valid. What can be done to correct this configuration file?
After the application launches, the health check is not being run on the correct path, even though it is valid. What can be done to correct this configuration file?A) Convert the file to JSON format.
B) Rename the file to a .config extension.
C) Change the configuration section from options_settings to resources . Change the configuration section from options_settings to resources .
D) Change the namespace of the option settings to a custom namespace.

Unlock Deck
Unlock for access to all 470 flashcards in this deck.
Unlock Deck
k this deck


