Deck 5: HCNP-R&S Fast Track (Huawei Certified Network Professional - Routing & Switching Fast Track)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/733
Play
Full screen (f)
Deck 5: HCNP-R&S Fast Track (Huawei Certified Network Professional - Routing & Switching Fast Track)
1
Which of the following fiber interface types is usually used on the device side?
A) LC interface
B) RJ interface
C) FC interface
D) BNC interface
A) LC interface
B) RJ interface
C) FC interface
D) BNC interface
LC interface
2
When communicating with customers, Huawei engineers need to be groomed, well behaved, and appropriate in language use.
True
3
The project scope can be determined from three aspects. Which of the following is not included?
A) Functions and modules to be realized by the project
B) Geographic range of the network
C) Investment budget of the project
D) Responsibility division between the project and other matching systems
A) Functions and modules to be realized by the project
B) Geographic range of the network
C) Investment budget of the project
D) Responsibility division between the project and other matching systems
Investment budget of the project
4
Employees in an enterprise often need to connect to the enterprise's intranet for remote access when going on business. Which of the following technologies can meet this demand? (Choose two.)
A) MPLS VPN
B) IPSec VPN
C) SSL VPN
D) ISDN Dial-in
A) MPLS VPN
B) IPSec VPN
C) SSL VPN
D) ISDN Dial-in

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
5
Which of the following networks are involved during construction of a large enterprise network?
A) Backbone network
B) Transport network
C) Data center network
D) Wireless network
E) Storage network
F) None of the above
A) Backbone network
B) Transport network
C) Data center network
D) Wireless network
E) Storage network
F) None of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
6
Switches run the MSTP protocol by default. Which of the following statements regarding the default status is true?
A) All switches run in the same region by default.
B) The STP calculation speed is faster than that when multiple instances are configured.
C) Due to lack of configuration, all switches switch the running mode to RSTP.
D) Each switch runs in an independent region.
A) All switches run in the same region by default.
B) The STP calculation speed is faster than that when multiple instances are configured.
C) Due to lack of configuration, all switches switch the running mode to RSTP.
D) Each switch runs in an independent region.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
7
Currently, to which of the following modes does network design conform?
A) Modular
B) Automatic
C) Hierarchical
D) Modern
E) Standard
A) Modular
B) Automatic
C) Hierarchical
D) Modern
E) Standard

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
8
During MSTP troubleshooting, the display current-configuration command is executed to obtain the configuration file of the device. Which of the following statements is false?
A) Check the port configuration to verify that the MSTP-enabled port is configured (for example, using the bpdu enable command) to send protocol packets.
B) The port connected to a user device has MSTP disabled or is configured as the edge port.
C) The BPDU tunnel configuration has no impact on MSTP.
D) Check whether the interface is added to the correct VLAN.
A) Check the port configuration to verify that the MSTP-enabled port is configured (for example, using the bpdu enable command) to send protocol packets.
B) The port connected to a user device has MSTP disabled or is configured as the edge port.
C) The BPDU tunnel configuration has no impact on MSTP.
D) Check whether the interface is added to the correct VLAN.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
9
Data center switches greatly differ from campus switches. Which of the following features are specific to data center switches but are not supported by campus switches?
A) MSTP
B) TRILL
C) NFV
D) FCoE
E) VxLAN
A) MSTP
B) TRILL
C) NFV
D) FCoE
E) VxLAN

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
10
Current enterprise networks usually use OSPF as the routing protocol. What precautions are there when OSPF is used? (Choose four.)
A) Determine that the backbone area will not split.
B) Check whether secondary optimal routes exist on the network according to OSPF route selection rules.
C) Check whether all non-backbone areas are correctly and reliably connected to the backbone area.
D) Check the OSPF network topology and ensure that no loop exists when OSPF routes are being calculated.
E) Verify that OSPF costs can correctly demonstrate the actual bandwidth of links at more than 100 Mbit/s.
A) Determine that the backbone area will not split.
B) Check whether secondary optimal routes exist on the network according to OSPF route selection rules.
C) Check whether all non-backbone areas are correctly and reliably connected to the backbone area.
D) Check the OSPF network topology and ensure that no loop exists when OSPF routes are being calculated.
E) Verify that OSPF costs can correctly demonstrate the actual bandwidth of links at more than 100 Mbit/s.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
11
Ethernet is the most mainstream LAN. Which of the following factors should be considered in Ethernet type selection? (Choose two.)
A) Network rate
B) Network medium
C) Network scale
D) Network hierarchy
E) Encapsulation standard
A) Network rate
B) Network medium
C) Network scale
D) Network hierarchy
E) Encapsulation standard

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following features is not applied to enterprise WANs?
A) Wide coverage
B) Difficult O&M
C) Multiple types
D) High costs of utilization
A) Wide coverage
B) Difficult O&M
C) Multiple types
D) High costs of utilization

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
13
Which of the following routers provides the cluster function?
A) AR G3
B) NE20S
C) NE40E
D) NE5000E
A) AR G3
B) NE20S
C) NE40E
D) NE5000E

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following causes may result in an IS-IS neighbor relationship fault?
A) The devices on two ends of a link have the same system ID.
B) The devices on two ends of a link have inconsistent IS-IS levels.
C) When an IS-IS Level-1 neighbor relationship is established, the devices on two ends of a link have inconsistent area addresses.
D) The IP addresses of interfaces on two ends of a link are on different network segments.
E) None of the above
A) The devices on two ends of a link have the same system ID.
B) The devices on two ends of a link have inconsistent IS-IS levels.
C) When an IS-IS Level-1 neighbor relationship is established, the devices on two ends of a link have inconsistent area addresses.
D) The IP addresses of interfaces on two ends of a link are on different network segments.
E) None of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
15
During EBGP peer relationship troubleshooting, it is found that two directly connected devices set up connections using loopback interfaces. Therefore, the display current-configuration configuration bgp command is executed to check the configuration of peer ebgp-max-hop hop-count. Which of the following statements is correct?
A) The hop count must be greater than 1.
B) The hop count must be greater than 2.
C) The hop count must be greater than 15.
D) The hop count must be greater than 255.
A) The hop count must be greater than 1.
B) The hop count must be greater than 2.
C) The hop count must be greater than 15.
D) The hop count must be greater than 255.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
16
To rectify a VRRP group two-master fault, run the display this command on VLANIF interfaces on both ends of the VRRP group. Which of the following operations is not performed?
A) Check whether the interface IP addresses are on the same network segment.
B) Check whether the VLANIF interfaces have the same VRRP group ID.
C) Check whether the virtual IP address is the same on the VLANIF interfaces in the VRRP group.
D) You do not need to check whether the interval for sending VRRP Advertisement packets is the same on the VLANIF interfaces.
A) Check whether the interface IP addresses are on the same network segment.
B) Check whether the VLANIF interfaces have the same VRRP group ID.
C) Check whether the virtual IP address is the same on the VLANIF interfaces in the VRRP group.
D) You do not need to check whether the interval for sending VRRP Advertisement packets is the same on the VLANIF interfaces.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
17
The display interface brief command can be executed to check the interface status. When sent and received traffic exceeds 70%, it can be determined that the traffic volume is high.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
18
When a Huawei router serves as an SSH client and attempts to log in to another Huawei router, the login fails. It is suspected that the SSH server configuration is incorrect. Which of the following causes is the most impossible for the server fault?
A) The SSH protocol is not bound in the VTY user interface view.
B) The user service type, authentication type, and user service type are not configured.
C) The SSH server and client have inconsistent versions.
D) The SSH first-time authentication function is disabled.
A) The SSH protocol is not bound in the VTY user interface view.
B) The user service type, authentication type, and user service type are not configured.
C) The SSH server and client have inconsistent versions.
D) The SSH first-time authentication function is disabled.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
19
Generally, which of the following enterprise services require user experience optimization?
A) Video surveillance
B) Videoconferencing
C) Voice call
D) Network management
A) Video surveillance
B) Videoconferencing
C) Voice call
D) Network management

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
20
During unpacking and inspection, the device appearance is intact and all modules work properly after the first power-on. After the device continuously runs for 24 hours, a fault occurs on a card. This situation does not conform to DOA conditions.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
21
Which statements are true? (Choose three.)
A) The routing ARP proxy allows the hosts on different physical networks of the same network segment to communicate with each other.
B) The intra-VLAN ARP proxy allows isolated users on a VLAN to communicate with each other.
C) The inter-VLAN ARP proxy allows hosts on different VLANs to communicate with each other through Layer 3.
D) The inter-VLAN ARP proxy function can't be enabled on the VLANIF interface of the super VLAN to implement communication between sub-VLANs.
A) The routing ARP proxy allows the hosts on different physical networks of the same network segment to communicate with each other.
B) The intra-VLAN ARP proxy allows isolated users on a VLAN to communicate with each other.
C) The inter-VLAN ARP proxy allows hosts on different VLANs to communicate with each other through Layer 3.
D) The inter-VLAN ARP proxy function can't be enabled on the VLANIF interface of the super VLAN to implement communication between sub-VLANs.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
22
Which of the following aspects should be considered for migration risk assessment?
A) Key risk positions
B) Risk impact scope
C) Risk impact time
D) Loss caused by risks
E) None of the above
A) Key risk positions
B) Risk impact scope
C) Risk impact time
D) Loss caused by risks
E) None of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
23
If the customer requires high mobility and easy management, the staff of different departments can be added to different VLANs. In addition, these VLANs are located on different IP subnets. Which VLAN allocation mode can meet these requirements?
A) VLAN allocation based on source IP addresses
B) VLAN allocation based on destination IP addresses
C) VLAN allocation based on source IP addresses and source MAC addresses
D) VLAN allocation based on destination MAC addresses and destination IP addresses
A) VLAN allocation based on source IP addresses
B) VLAN allocation based on destination IP addresses
C) VLAN allocation based on source IP addresses and source MAC addresses
D) VLAN allocation based on destination MAC addresses and destination IP addresses

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following statements about STP is not true?
A) STP can manage redundant links.
B) STP can block redundant links to eliminate loops
C) STP can prevent temporary loss of connectivity
D) STP can make LAN switch operate normally in a network with loops
A) STP can manage redundant links.
B) STP can block redundant links to eliminate loops
C) STP can prevent temporary loss of connectivity
D) STP can make LAN switch operate normally in a network with loops

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following operations are performed during migration acceptance? (Choose three.)
A) Documentation transfer
B) Transfer-to-maintenance training
C) Acceptance meeting
D) Business expense accounting
A) Documentation transfer
B) Transfer-to-maintenance training
C) Acceptance meeting
D) Business expense accounting

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
26
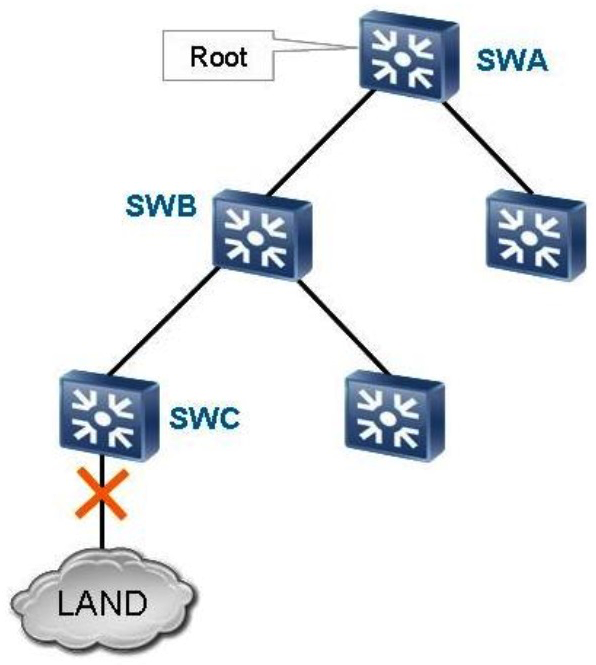 As shown in the figure, when the link between SWC and LAND is faulty, through which path are TCA BPDUs sent?
As shown in the figure, when the link between SWC and LAND is faulty, through which path are TCA BPDUs sent?A) From SWA to SWB
B) From SWB to SWC
C) From SWB to SWA
D) From SWC to SWB

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
27
The migration rollback time can be determined based on the actual migration situation, without the need to plan in advance.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
28
On the RSTP network with STP devices, which packets does an RSTP switch use to notify the STP switches of the topology change?
A) RSTP BPDUs with the TC flag
B) STP BPDUs with the TCN flag
C) RSTP BPDUs with the TCA flag
D) STP BPDUs with the TCA flag
A) RSTP BPDUs with the TC flag
B) STP BPDUs with the TCN flag
C) RSTP BPDUs with the TCA flag
D) STP BPDUs with the TCA flag

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following are migration difficulties? (Choose three.)
A) Minimizing on services
B) Achieving optimal risk prevention
C) Formulating a complete migration solution
D) Carrying out the migration smoothly
A) Minimizing on services
B) Achieving optimal risk prevention
C) Formulating a complete migration solution
D) Carrying out the migration smoothly

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
30
Which statements about QinQ are true? (Choose two.)
A) QinQ saves VLANs on the public network.
B) To avoid VLAN conflict, the customer must negotiate with the service provider before modifying the VLANs on its private network.
C) When the service provider upgrades the network, the configurations on the user network do not need to be modified.
D) All of the above
A) QinQ saves VLANs on the public network.
B) To avoid VLAN conflict, the customer must negotiate with the service provider before modifying the VLANs on its private network.
C) When the service provider upgrades the network, the configurations on the user network do not need to be modified.
D) All of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
31
Access control is used to limit the traffic rate or block specific traffic based on reachable network routes to meet service management and control needs.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the following aspects should be considered during preliminary analysis of a migration project? (Choose three.)
A) Necessity
B) Feasibility
C) Risks
D) Costs
A) Necessity
B) Feasibility
C) Risks
D) Costs

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
33
Which statements about MUX VLAN are true? (Choose two.)
A) MUX VLAN contains a principal VLAN and subordinate VLANs. The principal VLAN and subordinate VLANs cannot communicate.
B) MUX VLAN contains a principal VLAN and subordinate VLANs. The subordinate VLANs are classified into subordinate separate VLANs and subordinate group VLANs. The interfaces in the subordinate group VLAN can communicate with each other.
C) The principal VLAN and subordinate VLANs can communicate.
D) The interfaces of different subordinate separate VLANs can communicate with each other, but cannot communicate with the interfaces in the principal VLAN.
A) MUX VLAN contains a principal VLAN and subordinate VLANs. The principal VLAN and subordinate VLANs cannot communicate.
B) MUX VLAN contains a principal VLAN and subordinate VLANs. The subordinate VLANs are classified into subordinate separate VLANs and subordinate group VLANs. The interfaces in the subordinate group VLAN can communicate with each other.
C) The principal VLAN and subordinate VLANs can communicate.
D) The interfaces of different subordinate separate VLANs can communicate with each other, but cannot communicate with the interfaces in the principal VLAN.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
34
During the migration test, which of the following indicates that the test is completed?
A) The network is running properly.
B) Tested network services are running properly.
C) Tested upper-layer application services are running properly on the network.
D) Command outputs are correct.
E) None of the above
A) The network is running properly.
B) Tested network services are running properly.
C) Tested upper-layer application services are running properly on the network.
D) Command outputs are correct.
E) None of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
35
Which statements about VLAN aggregation are true? (Choose three.)
A) "multiple" VLANs (broadcast domains) are on the same physical network; therefore, different VLANs belong to the same subnet.
B) VLAN aggregation can save IP addresses.
C) Only the super VLAN requires an IP address, but sub-VLANs do not need.
D) The VLAN that is used to separate broadcast domains is called super VLAN.
A) "multiple" VLANs (broadcast domains) are on the same physical network; therefore, different VLANs belong to the same subnet.
B) VLAN aggregation can save IP addresses.
C) Only the super VLAN requires an IP address, but sub-VLANs do not need.
D) The VLAN that is used to separate broadcast domains is called super VLAN.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
36
Two switches are directly connected to each other and they are working in full duplex mode. By default, RSTP will consider the link between the switches as point-to-point link.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
37
The STP protocol cannot prevent MAC address table flapping caused by loops on the Layer 2 network.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
38
Which statement about port isolation configuration is false?
A) Port isolation can be used for Layer 2 isolation.
B) In port isolation mode, ports are isolated at Layer 2 but can communicate at Layer 3 by default.
C) Before the port isolation function takes effect on an interface, the port isolation function must be enabled first.
D) The port-isolate enable command can run in the system view.
A) Port isolation can be used for Layer 2 isolation.
B) In port isolation mode, ports are isolated at Layer 2 but can communicate at Layer 3 by default.
C) Before the port isolation function takes effect on an interface, the port isolation function must be enabled first.
D) The port-isolate enable command can run in the system view.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following work is not prepared before the migration?
A) Hardware test
B) Software test
C) Expenses
D) Tools
A) Hardware test
B) Software test
C) Expenses
D) Tools

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
40
Which statement is true?
A) The principal VLAN must be configured before subordinate VLANs.
B) The MUX VLAN function takes effect without being enabled on an interface.
C) In MUX VLAN, a VLAN can function as both principal VLAN and subordinate VLAN.
D) The MUX VLAN can contain only one subordinate separate VLAN.
A) The principal VLAN must be configured before subordinate VLANs.
B) The MUX VLAN function takes effect without being enabled on an interface.
C) In MUX VLAN, a VLAN can function as both principal VLAN and subordinate VLAN.
D) The MUX VLAN can contain only one subordinate separate VLAN.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
41
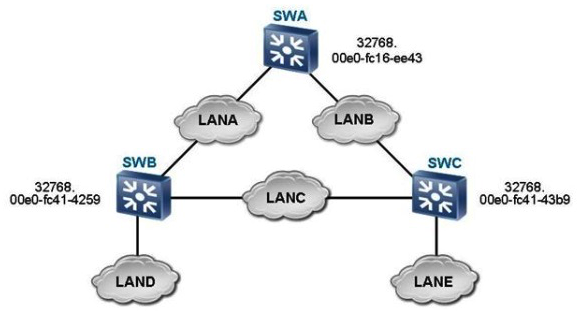 On the STP network as shown in the figure, which device may be the blocked port belong to?
On the STP network as shown in the figure, which device may be the blocked port belong to?A) SWA
B) SWB
C) SWC
D) None of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
42
Which statement about ARP proxy is false?
A) The ARP proxy, namely, the gateway, sends ARP request for the host. The MAC address in the ARP request packet is the MAC address of the host.
B) The ARP proxy, namely, the gateway, sends ARP request for the host. The MAC address in the ARP request packet is the MAC address of its own interface.
C) ARP proxy is also called promiscuous ARP or ARP hack.
D) The ARP proxy allows the hosts on the networks with the same network ID to communicate with each other.
A) The ARP proxy, namely, the gateway, sends ARP request for the host. The MAC address in the ARP request packet is the MAC address of the host.
B) The ARP proxy, namely, the gateway, sends ARP request for the host. The MAC address in the ARP request packet is the MAC address of its own interface.
C) ARP proxy is also called promiscuous ARP or ARP hack.
D) The ARP proxy allows the hosts on the networks with the same network ID to communicate with each other.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
43
Which statements are true? (Choose three.)
A) The sub-VLANs are configured in the super VLAN view.
B) VLANs 1 to 4094 can be configured as a super VLAN.
C) The aggregate-vlan command is used to configure the super VLAN.
D) A VLAN to be configured as a super VLAN cannot contain any interface.
A) The sub-VLANs are configured in the super VLAN view.
B) VLANs 1 to 4094 can be configured as a super VLAN.
C) The aggregate-vlan command is used to configure the super VLAN.
D) A VLAN to be configured as a super VLAN cannot contain any interface.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
44
Which statements are true? (Choose three.)
A) Port isolation is a mechanism that controls the access between switch interfaces.
B) Port isolation is an isolation mechanism at the physical layer.
C) Port isolation prevents the computers connected to different ports from accessing each other.
D) Port isolation can be configured based on VLANs.
A) Port isolation is a mechanism that controls the access between switch interfaces.
B) Port isolation is an isolation mechanism at the physical layer.
C) Port isolation prevents the computers connected to different ports from accessing each other.
D) Port isolation can be configured based on VLANs.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
45
Which statement about the following configuration is true? port link-type hybrid port hybrid pvidvlan 2 port hybrid untagged vlan 2 port hybrid tagged vlan 3
A) The default VLAN of the interface is VLAN 2.
B) The port hybrid tagged vlan 3 command configures the VLAN for a hybrid interface. Frames in the VLAN then pass through the hybrid interface in untagged mode.
C) The port hybrid untagged vlan 2 command configures the VLAN for a hybrid interface. Frames in the VLAN then pass through the hybrid interface in tagged mode.
D) All of the above.
A) The default VLAN of the interface is VLAN 2.
B) The port hybrid tagged vlan 3 command configures the VLAN for a hybrid interface. Frames in the VLAN then pass through the hybrid interface in untagged mode.
C) The port hybrid untagged vlan 2 command configures the VLAN for a hybrid interface. Frames in the VLAN then pass through the hybrid interface in tagged mode.
D) All of the above.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following statements about the link failure detection in STP protocol is not true?
A) When network topology is stable, the Designated Port sends BPDU packet at every Hello Time interval.
B) When network topology is stable, BPDU packets will be transmitted periodically.
C) When the port does not receive new BPDU within a certain interval, the old configuration BPDU will time out and the link failure can be detected.
D) The port sends Configuration BPDU at every Hello Time interval. When the link fails, Configuration BPDU cannot be sent out. As a result, this port can detect the link failure.
A) When network topology is stable, the Designated Port sends BPDU packet at every Hello Time interval.
B) When network topology is stable, BPDU packets will be transmitted periodically.
C) When the port does not receive new BPDU within a certain interval, the old configuration BPDU will time out and the link failure can be detected.
D) The port sends Configuration BPDU at every Hello Time interval. When the link fails, Configuration BPDU cannot be sent out. As a result, this port can detect the link failure.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
47
When the GVRP registration mode is FIXED, which statement is true?
A) VLANs can be manually created and registered on the interface, and can also be dynamically registered and deregistered on the interface.
B) VLANs cannot be manually created and registered on the interface, but can be dynamically registered and deregistered on the interface.
C) VLANs can be manually created and registered on the interface, but cannot be dynamically registered or deregistered on the interface.
D) VLANs cannot be manually created and registered on the interface, and cannot be dynamically registered or deregistered on the interface.
A) VLANs can be manually created and registered on the interface, and can also be dynamically registered and deregistered on the interface.
B) VLANs cannot be manually created and registered on the interface, but can be dynamically registered and deregistered on the interface.
C) VLANs can be manually created and registered on the interface, but cannot be dynamically registered or deregistered on the interface.
D) VLANs cannot be manually created and registered on the interface, and cannot be dynamically registered or deregistered on the interface.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
48
The following is the command output on a root switch of an MSTP region. How many switches are located in the MSTP region?
A) Less than 10
B) Less than 20
C) Less than 30
D) Less than 40
A) Less than 10
B) Less than 20
C) Less than 30
D) Less than 40

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
49
Which statement about VLAN mapping is false?
A) VLAN mapping is also called VLAN translation.
B) VLAN mapping can implement translation between C-VLAN IDs and S-VLAN IDs.
C) VLAN mapping can be configured.
D) VLAN mapping means that a VLAN tag is added to packets.
A) VLAN mapping is also called VLAN translation.
B) VLAN mapping can implement translation between C-VLAN IDs and S-VLAN IDs.
C) VLAN mapping can be configured.
D) VLAN mapping means that a VLAN tag is added to packets.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
50
After detecting a user with a new MAC address, the switch initiates an EAP authentication request. If the client does not respond and the MAC address bypass authentication is not configured, which statement is false?
A) If the client does not respond after the number of authentication requests reaches a specified value, the switch considers that the client software is not installed.
B) All permissions of the user are prohibited.
C) The user is allowed to access only the isolated zone.
D) Detection is initiated again after a period of time.
A) If the client does not respond after the number of authentication requests reaches a specified value, the switch considers that the client software is not installed.
B) All permissions of the user are prohibited.
C) The user is allowed to access only the isolated zone.
D) Detection is initiated again after a period of time.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
51
In STP configuration, which statement about BPDUs is true?
A) BPDUs cannot be sent from the designated port.
B) BPDUs can be sent only from the designated port.
C) BPDUs can be sent from any port.
D) None of the above.
A) BPDUs cannot be sent from the designated port.
B) BPDUs can be sent only from the designated port.
C) BPDUs can be sent from any port.
D) None of the above.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
52
According to the MSTP protocol, each MST instance calculates an independent spanning tree by using the RSTP algorithm.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
53
The STP protocol can prevent broadcast storms caused by loops on the Layer 2 network.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
54
When the GVRP registration mode is FORBIDDEN, no VLAN can be created or registered on the interface. In addition, which VLANs are deregistered on the interface?
A) All VLANs except VLAN 1
B) All VLANs except VLAN 4095
C) All VLANs
D) All VLANs except the VLAN specified by the user
A) All VLANs except VLAN 1
B) All VLANs except VLAN 4095
C) All VLANs
D) All VLANs except the VLAN specified by the user

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
55
Which statement about the hybrid interface is true?
A) A hybrid interface can only be connected to network device.
B) A hybrid interface can only be connected to host.
C) A hybrid interface can be connected to host or network device.
D) A hybrid interface cannot be configured with VLAN ID.
A) A hybrid interface can only be connected to network device.
B) A hybrid interface can only be connected to host.
C) A hybrid interface can be connected to host or network device.
D) A hybrid interface cannot be configured with VLAN ID.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
56
Which statements about the PVID on the access interface are true?
A) When receiving a packet without the VLAN tag, the interface adds the VLAN tag to the packet and sets the VID in the tag to the default VLAN ID.
B) When receiving a packet with a VLAN tag, the interface compares the VLAN ID in the tag with the default VLAN ID. If they are the same, the interface forwards the packets; otherwise, the interface discards the packets.
C) When the interface sends a packet with a VLAN tag that contains the default VLAN ID, the system removes the VLAN tag of the packet, and then forwards the packet.
D) None of the above.
A) When receiving a packet without the VLAN tag, the interface adds the VLAN tag to the packet and sets the VID in the tag to the default VLAN ID.
B) When receiving a packet with a VLAN tag, the interface compares the VLAN ID in the tag with the default VLAN ID. If they are the same, the interface forwards the packets; otherwise, the interface discards the packets.
C) When the interface sends a packet with a VLAN tag that contains the default VLAN ID, the system removes the VLAN tag of the packet, and then forwards the packet.
D) None of the above.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
57
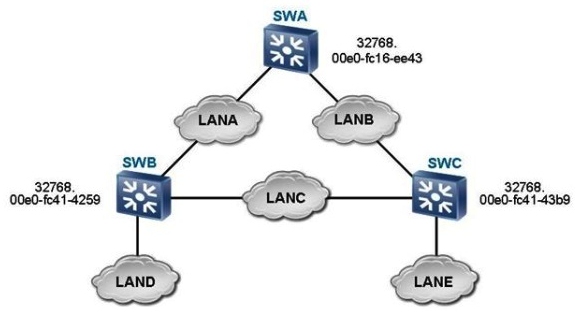 As shown in the figure, which switch is the root switch according to the configuration?
As shown in the figure, which switch is the root switch according to the configuration?A) SWA
B) SWB
C) SWC
D) None of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
58
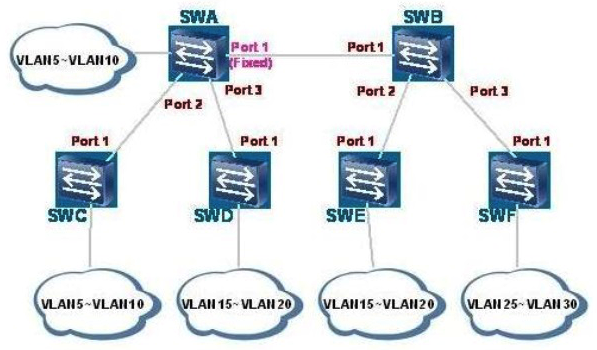 As shown in the figure, port 1 of switch A is configured with the Fixed mode, and other ports are configured with the Normal mode. The trunk interfaces allow all VLANs. Which VLANs are registered on port 1 of switch C? (Choose three.)
As shown in the figure, port 1 of switch A is configured with the Fixed mode, and other ports are configured with the Normal mode. The trunk interfaces allow all VLANs. Which VLANs are registered on port 1 of switch C? (Choose three.)A) VLAN 1
B) VLAN 5 to VLAN 10
C) VLAN 15 to VLAN 20
D) VLAN 25 to VLAN 30

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
59
QinQ provides a simplified Layer 2 VPN tunnel.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
60
Which statements about the VLAN on S series switches are true? (Choose two.)
A) The VLAN IDs on the switch range from 1 to 4090.
B) The switch has a default VLAN.
C) The priority value in the VLAN tag can be changed on the switch.
D) A VLAN tag contains one byte.
A) The VLAN IDs on the switch range from 1 to 4090.
B) The switch has a default VLAN.
C) The priority value in the VLAN tag can be changed on the switch.
D) A VLAN tag contains one byte.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
61
On a switch running GVRP, each interface is considered as a participant. The participants can exchange information.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
62
Which statement is false?
A) The switch supports 1:1 VLAN mapping.
B) The switch does not support N:1 VLAN mapping on an interface.
C) The switch can perform VLAN mapping for double-tagged packets.
D) The switch can map the outer VLAN ID of packets to another VLAN ID.
A) The switch supports 1:1 VLAN mapping.
B) The switch does not support N:1 VLAN mapping on an interface.
C) The switch can perform VLAN mapping for double-tagged packets.
D) The switch can map the outer VLAN ID of packets to another VLAN ID.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
63
Which statements about VLAN mapping are true? (Choose two.)
A) When sending a frame from the local VLAN, the switch replaces the VLAN tag in the frame with another VLAN tag.
B) When receiving a frame from another VLAN, the switch replaces the VLAN tag of the frame with the local VLAN tag.
C) When an interface receives a frame from another VLAN, it does not replace the VLAN tag of the frame. The interface replaces the VLAN tag of the frame with another VLAN tag only when it sends a frame.
D) The interface replaces the VLAN tag of only the frame received from another VLAN, but does not change the VLAN tag of the frame it sends out.
A) When sending a frame from the local VLAN, the switch replaces the VLAN tag in the frame with another VLAN tag.
B) When receiving a frame from another VLAN, the switch replaces the VLAN tag of the frame with the local VLAN tag.
C) When an interface receives a frame from another VLAN, it does not replace the VLAN tag of the frame. The interface replaces the VLAN tag of the frame with another VLAN tag only when it sends a frame.
D) The interface replaces the VLAN tag of only the frame received from another VLAN, but does not change the VLAN tag of the frame it sends out.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
64
Which problems on a single spanning tree network can be solved by MSTP? (Choose three.)
A) Traffic forwarding paths in some VLANs are faulty.
B) Traffic cannot be load balanced.
C) The second best path problem may occur.
D) The network reliability cannot be improved.
A) Traffic forwarding paths in some VLANs are faulty.
B) Traffic cannot be load balanced.
C) The second best path problem may occur.
D) The network reliability cannot be improved.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
65
Which statements about the access interface are true? (Choose three.)
A) Only the VLAN whose ID is the same as the PVID of the access interface are allowed on the access interface.
B) When receiving an untagged frame, the access interface adds its own PVID to the frame.
C) The access interface sends only untagged frames to the peer device.
D) None of the above.
A) Only the VLAN whose ID is the same as the PVID of the access interface are allowed on the access interface.
B) When receiving an untagged frame, the access interface adds its own PVID to the frame.
C) The access interface sends only untagged frames to the peer device.
D) None of the above.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
66
On an RSTP network, when an edge port is in protected state, what operation is performed after the edge port receives BPDUs?
A) The edge port forwards BPDUs.
B) The edge port discards BPDUs.
C) The edge port is shut down.
D) The edge port obtains required information from BPDUs.
A) The edge port forwards BPDUs.
B) The edge port discards BPDUs.
C) The edge port is shut down.
D) The edge port obtains required information from BPDUs.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
67
The port isolation function can isolate the ports on the same switch.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
68
Which statements about the relationship between GVRP and GARP are true? (Choose two.)
A) GVRP, GARP, and GMRP are the standards of the same type.
B) GVRP and GARP are defined by IEEE 802.1p.
C) GVRP is based on GARP, and is an application of GARP.
D) GVRP is a new definition of GARP.
A) GVRP, GARP, and GMRP are the standards of the same type.
B) GVRP and GARP are defined by IEEE 802.1p.
C) GVRP is based on GARP, and is an application of GARP.
D) GVRP is a new definition of GARP.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
69
Which is the port state defined in RSTP?
A) Discarding
B) Learning
C) Forwarding
D) All of the above
A) Discarding
B) Learning
C) Forwarding
D) All of the above

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
70
The dot1x authentication-method command is used to set the 802.1x authentication mode. Which is the most secure authentication mode?
A) PAP
B) EAP
C) CHAP
D) EAP-TTLS
A) PAP
B) EAP
C) CHAP
D) EAP-TTLS

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
71
GARP involves various messages. Besides JoinIn message and Leave message, which are also the GARP messages? (Choose three.)
A) Notice
B) Empty
C) JoinEmpty
D) LeaveAll
A) Notice
B) Empty
C) JoinEmpty
D) LeaveAll

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
72
Which are contained in a GARP participant? (Choose two.)
A) GARP Application
B) GARP Information Propagation (GIP)
C) GARP Information Declaration (GID)
D) Interface LLC
A) GARP Application
B) GARP Information Propagation (GIP)
C) GARP Information Declaration (GID)
D) Interface LLC

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
73
Which statement about VLAN is false?
A) VLAN tag contains a 3-bit priority field. The priority value ranges from 0 to 7. It is used for differentiated service forwarding.
B) The priority in the VLAN tag can be mapped to the internal priority of the switch, for differentiated service forwarding.
C) The priority in the VLAN tag can be changed on the switch.
D) The priority in the VLAN tag cannot be changed.
A) VLAN tag contains a 3-bit priority field. The priority value ranges from 0 to 7. It is used for differentiated service forwarding.
B) The priority in the VLAN tag can be mapped to the internal priority of the switch, for differentiated service forwarding.
C) The priority in the VLAN tag can be changed on the switch.
D) The priority in the VLAN tag cannot be changed.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
74
On an STP network, before the interface status transits from non-forwarding to forwarding, how many Forward Delay intervals does the interface wait for?
A) 2
B) 3
C) 4
D) 5
A) 2
B) 3
C) 4
D) 5

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
75
Which are the two parts in the port identifier of the uplink interface on a non-root switch?
A) 1-bit port priority and 1-bit port number
B) 1-bit port priority and 2-bit port number
C) 2-bit port priority and 1-bit port number
D) 2-bit port priority and 2-bit port number
A) 1-bit port priority and 1-bit port number
B) 1-bit port priority and 2-bit port number
C) 2-bit port priority and 1-bit port number
D) 2-bit port priority and 2-bit port number

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
76
Which statements about the MUX VLAN configuration are true? (Choose two.) 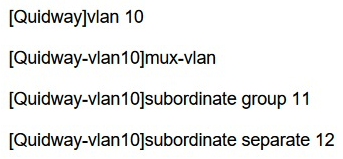
A) VLAN 10 is the principal VLAN
B) VLAN 11 is the principal VLAN
C) VLAN 12 is the subordinate separate VLAN

A) VLAN 10 is the principal VLAN
B) VLAN 11 is the principal VLAN
C) VLAN 12 is the subordinate separate VLAN

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
77
When configuring VLAN mapping, you must set the priority of outer VLAN ID.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
78
RSTP has all functions that STP has and it is backward compatible with STP.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
79
The Layer 2 packet header in EAPoL packets is | DMAC | SMAC | TYPE | EAPOL | FCS |. Which statements are true? (Choose three.)
A) The destination address of packets is a specified MAC address.
B) The destination address of packets is a unicast MAC address.
C) EAPoL packets cannot be forwarded by switches.
D) The source MAC address of packets is the MAC address of the interface that sends packets.
A) The destination address of packets is a specified MAC address.
B) The destination address of packets is a unicast MAC address.
C) EAPoL packets cannot be forwarded by switches.
D) The source MAC address of packets is the MAC address of the interface that sends packets.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck
80
STP distributes configuration message by sending BPDU packet to each other.

Unlock Deck
Unlock for access to all 733 flashcards in this deck.
Unlock Deck
k this deck


