Deck 12: Information Technology Auditing
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/25
Play
Full screen (f)
Deck 12: Information Technology Auditing
1
The Espy Company recently had an outside consulting firm perform an audit of its infor- mation systems department. One of the consultants identified some business risks and their probability of occurrence. Estimates of the potential losses and estimated control costs are given in Figure 12-11 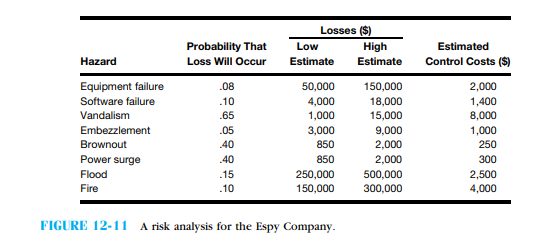 .
.
a. Using the Figure 12-11 information, develop a risk assessment for the Espy Company.
b. If you were the manager responsible for the Espy Company's information processing system, which controls would you implement and why?
 .
.a. Using the Figure 12-11 information, develop a risk assessment for the Espy Company.
b. If you were the manager responsible for the Espy Company's information processing system, which controls would you implement and why?
a.
Risk assessment mainly focus on finding weakness and make control procedures to control weakness. It is generally done by external audit to find the flaws in the system operation.
The risk assessment gives estimates of the maximum and minimum losses. It will also give the control cost. Based on the estimates company will take decision to implement control measures.
The risk assessment for the company done is given below. The benefit cost ratio is calculated. Benefit to cost ratio is the ratio of the benefit the organization would gain by incurring particular amount as control measure cost. The calculation is done as shown below.
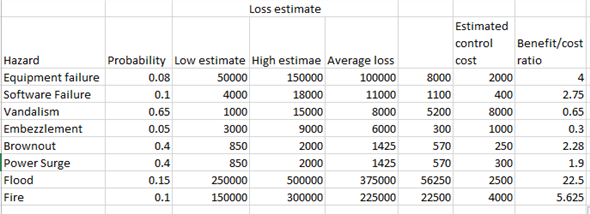 b.
b.
Based on the benefit cost ratio calculation as a part of risk assessment the following actions to be taken:
As a first and foremost action Flood control should be implemented as it has the highest benefit to cost ratio. It is then followed by fire control.
Risk assessment mainly focus on finding weakness and make control procedures to control weakness. It is generally done by external audit to find the flaws in the system operation.
The risk assessment gives estimates of the maximum and minimum losses. It will also give the control cost. Based on the estimates company will take decision to implement control measures.
The risk assessment for the company done is given below. The benefit cost ratio is calculated. Benefit to cost ratio is the ratio of the benefit the organization would gain by incurring particular amount as control measure cost. The calculation is done as shown below.
 b.
b.Based on the benefit cost ratio calculation as a part of risk assessment the following actions to be taken:
As a first and foremost action Flood control should be implemented as it has the highest benefit to cost ratio. It is then followed by fire control.
2
In auditing program change control, the IT auditor will:
a. Make sure that only computer programmers have tested the changes they made to programs
b. Ensure an organization is following the process described in their documentation for program change control
c. Not need to inspect program authorization forms for signatures
d. Make sure that only computer programmers move their own changes into a production environment
a. Make sure that only computer programmers have tested the changes they made to programs
b. Ensure an organization is following the process described in their documentation for program change control
c. Not need to inspect program authorization forms for signatures
d. Make sure that only computer programmers move their own changes into a production environment
An IT auditor must ensure that the programming software used by the organization is not manipulated at the time of audit. Hence an auditor must vouch all the programs provided by the client. The same can be achieved through test of program change controls
The following steps encompass the test of program change controls:
1. Any newly developed program or program modification is properly documented through special forms.
2. The forms should include the personnel responsible for the work and the signature of the approving authority.
3. There should be separate forms for showing the completion of work and proper authorisation for the use of programs for data processing.
4. It also requires the programmers to use test environment rather than live environment for developing and implementing changes.
An auditor through program change control ensures that organization has sound authorisation procedure and the same is observed by its employees.
Thus, in auditing program change control, the IT auditor will ensure an organization is following the process described in their documentation for program change control.
The following steps encompass the test of program change controls:
1. Any newly developed program or program modification is properly documented through special forms.
2. The forms should include the personnel responsible for the work and the signature of the approving authority.
3. There should be separate forms for showing the completion of work and proper authorisation for the use of programs for data processing.
4. It also requires the programmers to use test environment rather than live environment for developing and implementing changes.
An auditor through program change control ensures that organization has sound authorisation procedure and the same is observed by its employees.
Thus, in auditing program change control, the IT auditor will ensure an organization is following the process described in their documentation for program change control.
3
Distinguish between the roles of an internal and an external auditor. Cite at least two examples of auditing procedures that might reasonably be expected of an internal auditor but not an external auditor. Which type of auditor would you rather be? Why?
An Internal Auditor is an auditor who is employed by the company from within its own employees.
An External Auditor is an auditor who is working for an outside CPA firm.
The primary differences in the roles of an Internal and external auditor are as follows:
1. Scope of Audit: The scope of an internal audit is relatively broader than external audit.
An Internal Audit can evaluate almost all the aspects of the company. His primary role is to increase the efficiency of the company's operations. An External Audit on the other hand provides an opinion on the financial statements of the company as to true and fair view.
2. Type of Checking: An Internal Auditor generally checks all the transactions. An External Auditor relies on the internal audit reports in determining the nature, extent and timing of the audit procedures. He may or may not check all the transactions.
3. Guidance: An Internal Auditor provides valuable insight to the management for improving the effectiveness of its operations.
An external auditor may or may not provide guidance to the management. His main function is to provide an opinion on the financial statements so that they can be relied upon.
4. Report submission: An internal auditor submits his report to the management of the company. An external auditor submits his report to the shareholders of the company.
5. Responsibilities: An internal auditor's primary responsibility is to prevent the occurrence of errors and frauds in the company. An external auditor's prime responsibility is to make sure that the financial statements are accurate and can be relied upon by the stakeholders of the company. He does come across errors and frauds while conducting audit but it is not his primary responsibility.
Overall, even though the differences exists between internal and external auditors, they can work together to increase the reliability of the financial statements and efficiency of the company's operations. Generally, an external auditor places a lot of reliance on the reports of internal auditor in determining the nature, extent and timing of audit procedures.
The two examples of internal audit procedures which the external auditor does not perform are as follows:
1. An internal auditor makes sure that the employees of the organization adhere to the standard policies and procedures laid down by the organization.
2. An internal auditor prepares internal control questionnaire and flow charts to establish the adequacy of the internal control system. The external auditor does not prepare them but relies on them in conducting audit.
Both the internal and external auditor requires reviewing and evaluating the financial statements of the organization. However, the scope of an internal auditor is broader than the external auditor.
Also, the internal auditor is an employee of the company and hence he may not get the opportunity and the independence to express his views freely and frankly. He submits his reports to the management and he has to work as per their instructions at times.
Whereas the external auditor is working for an independent accounting firm and hence he can express his opinion with full freedom and independence.
Hence, I would like to be an external auditor so that I can work independently and professionally.
An External Auditor is an auditor who is working for an outside CPA firm.
The primary differences in the roles of an Internal and external auditor are as follows:
1. Scope of Audit: The scope of an internal audit is relatively broader than external audit.
An Internal Audit can evaluate almost all the aspects of the company. His primary role is to increase the efficiency of the company's operations. An External Audit on the other hand provides an opinion on the financial statements of the company as to true and fair view.
2. Type of Checking: An Internal Auditor generally checks all the transactions. An External Auditor relies on the internal audit reports in determining the nature, extent and timing of the audit procedures. He may or may not check all the transactions.
3. Guidance: An Internal Auditor provides valuable insight to the management for improving the effectiveness of its operations.
An external auditor may or may not provide guidance to the management. His main function is to provide an opinion on the financial statements so that they can be relied upon.
4. Report submission: An internal auditor submits his report to the management of the company. An external auditor submits his report to the shareholders of the company.
5. Responsibilities: An internal auditor's primary responsibility is to prevent the occurrence of errors and frauds in the company. An external auditor's prime responsibility is to make sure that the financial statements are accurate and can be relied upon by the stakeholders of the company. He does come across errors and frauds while conducting audit but it is not his primary responsibility.
Overall, even though the differences exists between internal and external auditors, they can work together to increase the reliability of the financial statements and efficiency of the company's operations. Generally, an external auditor places a lot of reliance on the reports of internal auditor in determining the nature, extent and timing of audit procedures.
The two examples of internal audit procedures which the external auditor does not perform are as follows:
1. An internal auditor makes sure that the employees of the organization adhere to the standard policies and procedures laid down by the organization.
2. An internal auditor prepares internal control questionnaire and flow charts to establish the adequacy of the internal control system. The external auditor does not prepare them but relies on them in conducting audit.
Both the internal and external auditor requires reviewing and evaluating the financial statements of the organization. However, the scope of an internal auditor is broader than the external auditor.
Also, the internal auditor is an employee of the company and hence he may not get the opportunity and the independence to express his views freely and frankly. He submits his reports to the management and he has to work as per their instructions at times.
Whereas the external auditor is working for an independent accounting firm and hence he can express his opinion with full freedom and independence.
Hence, I would like to be an external auditor so that I can work independently and professionally.
4
Visit http://www.isaca.org, the Web site for the Information Systems Audit and Control Association. Investigate the Certified Information Systems Auditor (CISA) credential. Describe the purpose of the credential and the types of auditing CISAs perform.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
5
An IT Auditor:
a. Must be an external auditor
b. Must be an internal auditor
c. Canbeeitheraninternalorexternalauditor
d. Must be a Certified Public Accountant
a. Must be an external auditor
b. Must be an internal auditor
c. Canbeeitheraninternalorexternalauditor
d. Must be a Certified Public Accountant

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
6
Continuous auditing:
a. Has been talked about for years but will never catch on
b. Will likely become more popular as organizations adopt XBRL in their financial reporting
c. Does not include techniques such as embedded audit modules
d. Will never allow IT auditors to provide sometypesofassuranceonareal-timebasis
a. Has been talked about for years but will never catch on
b. Will likely become more popular as organizations adopt XBRL in their financial reporting
c. Does not include techniques such as embedded audit modules
d. Will never allow IT auditors to provide sometypesofassuranceonareal-timebasis

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
7
How does information technology auditing differ from financial auditing? Make a list of the skills you think are important for financial auditors and for IT auditors. Do you think all auditors should have all the skills on both lists? Why or why not?

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
8
Information systems auditors sometimes use tools or information they can download from the Internet. These tools or information may include software, audit guides, or computer security advisories. Locate some examples from the Internet of audit tools, audit guides, or computer security advisories that you would find useful in conducting an audit of a client's computer system.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
9
Which of the following is not true with respect to forensic accountants?
a. They specialize in fraud investigation
b. They are always external auditors
c. They may work for the FBI
d. Forensic accounting is an example of an assurance service
a. They specialize in fraud investigation
b. They are always external auditors
c. They may work for the FBI
d. Forensic accounting is an example of an assurance service

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
10
With respect to changes in IT auditing today, which of the following is not true?
a. IT governance, which ties IT to organizational strategy, is increasingly important
b. Section 404 of the Sarbanes-Oxley Act of 2002 created an increase in demand for both IT auditors and internal auditors
c. IT auditors are concerned only with supporting financial auditors and should not investigate fraud cases
d. Third-party assurance seals may provide some comfort to e-business customers regarding the security of online transactions
a. IT governance, which ties IT to organizational strategy, is increasingly important
b. Section 404 of the Sarbanes-Oxley Act of 2002 created an increase in demand for both IT auditors and internal auditors
c. IT auditors are concerned only with supporting financial auditors and should not investigate fraud cases
d. Third-party assurance seals may provide some comfort to e-business customers regarding the security of online transactions

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
11
Describe the differences between general-use software and generalized audit software. How might you use spreadsheet software, database software, and word processing software in conducting an audit of fixed assets?

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
12
Continuous auditing has the potential to reduce labor costs associated with auditing. It also can provide audit assurance closer to the occurrence of a transaction, which improves the reliability of frequent or real-time financial reports. Using an Internet search engine, find an example of an organization's usage of continuous auditing.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
13
In determining the scope of an IT audit, the auditor should pay most attention to:
a. Threats and risks
b. The cost of the audit
c. What the IT manager asks to be evaluated
d. Listings of standard control procedures
a. Threats and risks
b. The cost of the audit
c. What the IT manager asks to be evaluated
d. Listings of standard control procedures

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
14
Of the following, the primary objective of compliance testing is to determine whether:9
a. Procedures are regularly updated
b. Financial statement line items are properly stated
c. Controls are functioning as planned
d. Collusion is taking place
a. Procedures are regularly updated
b. Financial statement line items are properly stated
c. Controls are functioning as planned
d. Collusion is taking place

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
15
IT auditors need people skills as well as technical skills. One such skill is the ability to interview effectively. Discuss some techniques or tools that might help an interviewer get the best information from an interviewee, including sensitive information.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
16
Basic Requirements (Systems Reliability Assurance) Kara and Scott Baker own a small retail company, Basic Requirements, with one store located in a small college town and a Web site through which customers can make purchases. The store sells traditional but up-to-date clothing for young women such as tee shirts, jeans, chinos, and skirts. The store has been open for 10 years, and the owners added the online shopping capability just last year. Online business has been slow, but Kara and Scott believe that as student customers graduate from the university they will use the online site to continue to have access to their favorite store from their college days. The store's Web site has many features. It classifies clothing by type, and customers can view items in various colors. To purchase an item, the user clicks on the icon depicting the desired product and adds it to an individual online shopping basket. The customer can view the basket and make a purchase at any time while browsing the site. When checking out at the site, a new customer must first register, providing billing and shipping information, as well as credit card data. Returning customers log in with the identification code and password they created when they registered. They also use that method to check on an order status. If a customer forgets their login information, they can simply click on a link to have it e-mailed to them. Once a user registers, Basic Requirements' system will automatically add their e-mail address to a file that they use to regularly send out e-mails about sales and other promotions. Kara and Scott are concerned about internal controls in their business. They especially worry because they know that their Web access creates some special risks. They have asked one of their customers who is an accounting student at the university to evaluate the reliability of their information system, with respect to security, availability, and privacy.
Requirements
1. Identify two security, availability, and privacy risks that Basic Requirements faces.
2. For each risk identified above, describe two internal controls Basic Requirements should use to protect against these risks.
3. The accounting student who is evaluating the reliability of Basic Requirements' infor mation system is interested in becoming an IT auditor. Describe some of the specific actions an IT auditor would take to verify that Kara and Scott have adequate controls in place concerning privacy.
Requirements
1. Identify two security, availability, and privacy risks that Basic Requirements faces.
2. For each risk identified above, describe two internal controls Basic Requirements should use to protect against these risks.
3. The accounting student who is evaluating the reliability of Basic Requirements' infor mation system is interested in becoming an IT auditor. Describe some of the specific actions an IT auditor would take to verify that Kara and Scott have adequate controls in place concerning privacy.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
17
Auditing around the computer:
a. Is the approach to auditing that is recommended in most cases to reduce IT audit costs
b. Focuses on computerized control procedures
c. Assumes that accurate output is sufficient evidence that processing operations are appropriate
d. Follows the audit trail through internal computer operations
a. Is the approach to auditing that is recommended in most cases to reduce IT audit costs
b. Focuses on computerized control procedures
c. Assumes that accurate output is sufficient evidence that processing operations are appropriate
d. Follows the audit trail through internal computer operations

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
18
Tiffany Martin, CPA (Information Technology Audit Skills) Tiffany Martin is an audit manager in a medium-size public accounting firm. Tiffany graduated from college 7 years ago with a degree in accounting. She obtained her CPA certification soon after she joined the firm where she currently works. Tiffany is a financial auditor; she has had little training in auditing computerized information systems. The current engagement Tiffany is working on includes a complex information process ing system with multiple applications. The financial accounting transactions are processed on a server. The IT department employs 25 personnel, including programmers, systems analysts, a database administrator, computer operators, technical support, and a director. Tiffany has not spoken with anyone in the department because she is fearful that her lack of technical knowledge relative to IT will cause some concern with the client. Because Tiffany does not understand the complexities of the computer processing environment, she is unable to determine what risks might result from the computerized system's operations. She is particularly worried about unauthorized changes to programs and data that would affect the reliability of the financial statements. Tiffany has spoken to Dick Stanton, the partner who has responsibility for this audit client, about her concerns. Dick has suggested that Tiffany conduct more substantive testing than she would undertake in a less complex processing environment. This additional testing will hopefully ensure that there are no errors or fraud associated with the computer processing of the financial statements.
Requirements
1. Do you think that Dick Stanton's suggested approach is the most efficient way to control risks associated with complex computer environments?
2. How should Tiffany respond to Dick's suggestion?
3. What can a public accounting firm, such as the one in which Tiffany works, do to ensure that audits of computerized accounting information systems are conducted efficiently and effectively?
4. Should Tiffany be allowed to conduct this audit given her limited skill level? How might she acquire the necessary skills?
Requirements
1. Do you think that Dick Stanton's suggested approach is the most efficient way to control risks associated with complex computer environments?
2. How should Tiffany respond to Dick's suggestion?
3. What can a public accounting firm, such as the one in which Tiffany works, do to ensure that audits of computerized accounting information systems are conducted efficiently and effectively?
4. Should Tiffany be allowed to conduct this audit given her limited skill level? How might she acquire the necessary skills?

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
19
Describe how an auditor might use through-the-computer techniques such as test data, an integrated test facility, parallel simulation, or validation of computer programs to accomplish audit objectives relative to accounts payable.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
20
Consolidated Company (Audit Program for Access Controls) Jason Saving is an IT auditor for a large, public accounting firm. His manager has assigned him to the Consolidated Company audit. The IT auditors must complete several evaluating and testing procedures in order to help determine the scope of the financial audit. The IT auditors also need to evaluate IT controls to provide the financial auditors with information in order to form an opinion on internal controls as part of Sarbanes-Oxley compliance. Consolidated Company manufactures automotive parts and supplies them to the largest auto makers. The company has approximately 1,500 employees and has manufacturing operations and offices in three locations. Consolidated uses a midsized ERP software program for manufacturers that they acquired and implemented 2 years ago. You need to develop an audit program to examine logical access to the ERP system. According to the Security Administrator at Consolidated, each employee is assigned a unique User ID and password when they join the company. The company is very concerned about security, so there is no remote access to the ERP system. The ERP system requires that users change their passwords every 6 months. System and group settings assigned to each User ID determine what parts of the ERP systems are available to each user.
Requirements
1. Explain how a deficiency in controls over User IDs and passwords might affect the financial statements.
2. Why is it necessary to examine User IDs and passwords?
3. Describe at least four control procedures that Consolidated should have in place to ensure that only authorized users access the system and that user access is limited according to their responsibilities.
Requirements
1. Explain how a deficiency in controls over User IDs and passwords might affect the financial statements.
2. Why is it necessary to examine User IDs and passwords?
3. Describe at least four control procedures that Consolidated should have in place to ensure that only authorized users access the system and that user access is limited according to their responsibilities.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
21
COBIT is:
a. A control framework developed by the Institute of Internal Auditors
b. A control framework developed specifically for organizations involved in e-business
c. An internal control model that covers both automated and manual systems
d. An internal control framework and model that encompasses an organization's IT gover- nance and information technologies
a. A control framework developed by the Institute of Internal Auditors
b. A control framework developed specifically for organizations involved in e-business
c. An internal control model that covers both automated and manual systems
d. An internal control framework and model that encompasses an organization's IT gover- nance and information technologies

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
22
Jose Rodriguez was the only internal auditor of a medium-size communications firm. The company used a computer for most of its accounting applications, and recently, several new software packages had been implemented to handle the increased volume of the company's business. To evaluate the packages' control capabilities, Jose performed a cost-benefit analysis and found that many of the control procedures were potentially useful but not clearly cost- effective. The problem, therefore, was what to say in his report to management. After pondering this question for some time, he decided to recommend almost all the controls based on the idea that a company was ''better to be safe than sorry.'' Comment on the wisdom of this idea.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following is not true with respect to generalized audit software (GAS)?
a. They require auditors to rewrite processing programs frequently while reviewing computer files
b. They are specifically tailored to auditor tasks
c. They may be used for specific application areas, such as accounts receivable and inventory
d. They allow auditors to manipulate files to extract and compare data
a. They require auditors to rewrite processing programs frequently while reviewing computer files
b. They are specifically tailored to auditor tasks
c. They may be used for specific application areas, such as accounts receivable and inventory
d. They allow auditors to manipulate files to extract and compare data

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
24
This chapter described several third-party assurance seals, including CPA WebTrust, BBB- Online, and TRUSTe. Explain the differences among them. Identify at least one other third-party assurance seal available for companies that allows them to demonstrate to their customers that they may be trusted in business transactions.

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following is not an audit technique for auditing computerized AIS?
a. Parallel simulation
b. Use of specialized control software
c. Continuous auditing
d. All of the above are techniques used to audit computerized AIS
a. Parallel simulation
b. Use of specialized control software
c. Continuous auditing
d. All of the above are techniques used to audit computerized AIS

Unlock Deck
Unlock for access to all 25 flashcards in this deck.
Unlock Deck
k this deck


