Deck 7: Ethernet Lan
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/24
Play
Full screen (f)
Deck 7: Ethernet Lan
1
EQUIP Co's Ethernet LAN (in the textbook) was divided into a production network and a _________:
A) security protection network
B) building maintenance network
C) video surveillance network
D) facility management network
E) virtual LANs
A) security protection network
B) building maintenance network
C) video surveillance network
D) facility management network
E) virtual LANs
C
2
In implementing VLANs, the switch port can be a(n):
A) access port or dynamic port
B) access port or trunk port
C) trunk port or dynamic port
D) static port or trunk port
E) access port or static port
A) access port or dynamic port
B) access port or trunk port
C) trunk port or dynamic port
D) static port or trunk port
E) access port or static port
B
3
When a campus network has many network nodes, the network designer may consider a hierarchical topology with:
A) access, trunk, and core layers
B) access, distribution, and root layers
C) access, distribution, and core layers
D) trunk, distribution, and root layers
E) access, distribution, and trunk layers
A) access, trunk, and core layers
B) access, distribution, and root layers
C) access, distribution, and core layers
D) trunk, distribution, and root layers
E) access, distribution, and trunk layers
C
4
When a switch is in the out-of-the-box condition, all entries of its switch table belong to the:
A) data VLAN
B) management VLAN
C) voice VLAN
D) default VLAN
E) null VLAN
A) data VLAN
B) management VLAN
C) voice VLAN
D) default VLAN
E) null VLAN

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
5
Which protocol is used to detect and remove redundant links within a switched Ethernet?
A) Link aggregation protocol
B) Spanning tree protocol
C) CSMA/CD protocol
D) VLAN trunking protocol
E) Link layer control (LLC) protocol
A) Link aggregation protocol
B) Spanning tree protocol
C) CSMA/CD protocol
D) VLAN trunking protocol
E) Link layer control (LLC) protocol

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
6
The default VLAN, data VLAN, and _______ are three main types of the VLAN:
A) voice VLAN
B) security VLAN
C) surveillance VLAN
D) storage VLAN
E) broadcasting VLAN
A) voice VLAN
B) security VLAN
C) surveillance VLAN
D) storage VLAN
E) broadcasting VLAN

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
7
Which concept is IRRELEVANT to the Spanning Tree Protocol?
A) Link redundancy
B) Bridge Protocol Data Unit (BPDU)
C) Blocking state of a port
D) Forwarding state of a port
E) Link aggregation
A) Link redundancy
B) Bridge Protocol Data Unit (BPDU)
C) Blocking state of a port
D) Forwarding state of a port
E) Link aggregation

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
8
The Ethernet frame has several fields in its header and trailer. Choose an INCORRECT description.
A) Preamble: synchronizes the clock speed between communicating nodes
B) Start Frame Delimiter: indicates the starting point of a frame
C) Source/Destination Address: 48 bit MAC addresses
D) PAD: used if the data field is too small to meet the minimum size requirement
E) Frame Check Sequence: indicates the end of a frame
A) Preamble: synchronizes the clock speed between communicating nodes
B) Start Frame Delimiter: indicates the starting point of a frame
C) Source/Destination Address: 48 bit MAC addresses
D) PAD: used if the data field is too small to meet the minimum size requirement
E) Frame Check Sequence: indicates the end of a frame

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
9
What is a popular device used to interconnect different VLANs?
A) switch
B) bridge
C) router
D) repeater
E) access point
A) switch
B) bridge
C) router
D) repeater
E) access point

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
10
Choose a CORRECT statement on the Ethernet technology.
A) Switches do not regenerate arrived signals in their shapes and strengths.
B) The LLC sub-layer header describes the type of packet contained in the frame's data field.
C) Ethernet switches utilize CSMA/CD to control network access.
D) It is generally OK for office workers to install hubs or switches in their office because this does not affect overall network performance.
E) Most switches rely on the half-duplex mode of data transmissions.
A) Switches do not regenerate arrived signals in their shapes and strengths.
B) The LLC sub-layer header describes the type of packet contained in the frame's data field.
C) Ethernet switches utilize CSMA/CD to control network access.
D) It is generally OK for office workers to install hubs or switches in their office because this does not affect overall network performance.
E) Most switches rely on the half-duplex mode of data transmissions.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
11
Sub-interfaces of a router are used for ________.
A) link aggregation
B) inter-VLAN routing
C) VLAN tagging
D) removal of path redundancy
E) layer 3 switching
A) link aggregation
B) inter-VLAN routing
C) VLAN tagging
D) removal of path redundancy
E) layer 3 switching

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
12
In switched Ethernet, VLAN trunking becomes possible with the ______ mechanism.
A) VLAN priority
B) Inter-VLAN routing
C) Spanning Tree Protocol
D) VLAN tagging
E) link redundancy
A) VLAN priority
B) Inter-VLAN routing
C) Spanning Tree Protocol
D) VLAN tagging
E) link redundancy

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
13
The Ethernet frame has several fields in its header and trailer. Choose an INCORRECT description of each field.
A) Preamble: synchronizes the clock speed between communicating nodes
B) Start Frame Delimiter: indicates the starting point of a frame
C) TPID: indicate presence of link aggregation
D) PAD: used if the data field is too small to meet the minimum size requirement
E) Frame Check Sequence: contains an error detection code
A) Preamble: synchronizes the clock speed between communicating nodes
B) Start Frame Delimiter: indicates the starting point of a frame
C) TPID: indicate presence of link aggregation
D) PAD: used if the data field is too small to meet the minimum size requirement
E) Frame Check Sequence: contains an error detection code

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
14
Layer 2 Ethernet switches _______
A) Have frequent collisions.
B) Can have an active loop between two stations.
C) Broadcast messages to all participants.
D) Connect workstations in a dual-ring structure.
E) Use MAC addresses for frame delivery.
A) Have frequent collisions.
B) Can have an active loop between two stations.
C) Broadcast messages to all participants.
D) Connect workstations in a dual-ring structure.
E) Use MAC addresses for frame delivery.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
15
Why end users (not IT staff) should NOT be allowed to install network nodes themselves?
A) Unintended link redundancy and loops can be introduced.
B) That practice puts financial burden on a business organization.
C) That affects the integrity of structured cabling.
D) The additional traffic generated slows network performance.
E) That makes the horizontal cabling less reliable.
A) Unintended link redundancy and loops can be introduced.
B) That practice puts financial burden on a business organization.
C) That affects the integrity of structured cabling.
D) The additional traffic generated slows network performance.
E) That makes the horizontal cabling less reliable.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
16
If a station broadcasts a frame, what will be the destination MAC address?
A) FF-FF-FF-FF-FF-FF
B) FF-FF-FF-00-00-00
C) 00-00-00-FF-FF-FF
D) 00-00-00-00-00-00
E) AA-AA-AA-AA-AA-AA
A) FF-FF-FF-FF-FF-FF
B) FF-FF-FF-00-00-00
C) 00-00-00-FF-FF-FF
D) 00-00-00-00-00-00
E) AA-AA-AA-AA-AA-AA

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
17
Refer to the figure below. 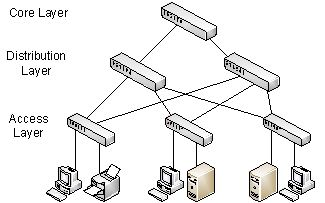 The switching table of the core layer switch should has to have _____ entries to prevent unwanted broadcasting of an incoming frame.
The switching table of the core layer switch should has to have _____ entries to prevent unwanted broadcasting of an incoming frame.
A) 2
B) 3
C) 4
D) 6
E) 7
 The switching table of the core layer switch should has to have _____ entries to prevent unwanted broadcasting of an incoming frame.
The switching table of the core layer switch should has to have _____ entries to prevent unwanted broadcasting of an incoming frame.A) 2
B) 3
C) 4
D) 6
E) 7

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
18
Refer to the figure below. 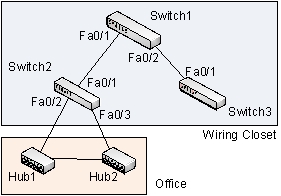 It highlights a potential problem of Ethernet. What can it be?
It highlights a potential problem of Ethernet. What can it be?
A) Need for link aggregation between switches
B) Redundancy in active paths
C) Absence of a router for inter-VLAN routing
D) Convergence failure of Spanning Tree Protocol (STP)
E) Need for creating virtual LANs
 It highlights a potential problem of Ethernet. What can it be?
It highlights a potential problem of Ethernet. What can it be?A) Need for link aggregation between switches
B) Redundancy in active paths
C) Absence of a router for inter-VLAN routing
D) Convergence failure of Spanning Tree Protocol (STP)
E) Need for creating virtual LANs

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
19
Refer to the figure below. 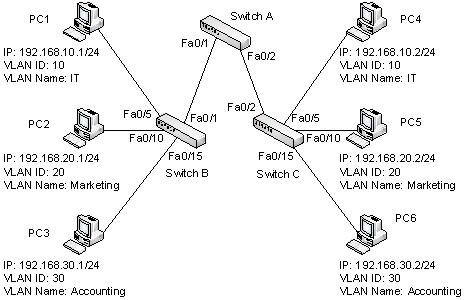 At least how many ports of Switch B should be configured as access ports for the network to be operational?
At least how many ports of Switch B should be configured as access ports for the network to be operational?
A) 1
B) 2
C) 3
D) 4
E) 0
 At least how many ports of Switch B should be configured as access ports for the network to be operational?
At least how many ports of Switch B should be configured as access ports for the network to be operational?A) 1
B) 2
C) 3
D) 4
E) 0

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
20
Refer to the Figure below. 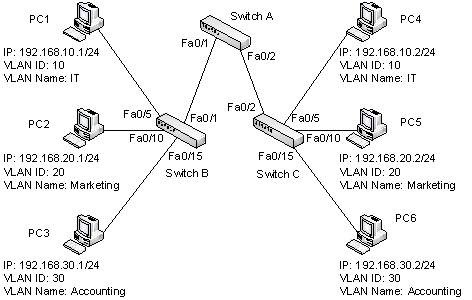 AT LEAST how many ports of Switch B should be configured as an access port?
AT LEAST how many ports of Switch B should be configured as an access port?
A) 2
B) 3
C) 4
D) 6
E) 9
 AT LEAST how many ports of Switch B should be configured as an access port?
AT LEAST how many ports of Switch B should be configured as an access port?A) 2
B) 3
C) 4
D) 6
E) 9

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
21
When switches are interconnected in a hierarchical topology, switches in this layer can be configured so that unauthorized computers (or other host types) are prevented from joining the network.
A) trunk layer
B) access layer
C) core layer
D) distribution layer
E) root layer
A) trunk layer
B) access layer
C) core layer
D) distribution layer
E) root layer

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
22
Choose a CORRECT statement on VLANs.
A) Layer 2 switches can forward frames across different VLANs.
B) With VLANs, cut-through switching should be used to minimize transmission delays.
C) VLAN tagging information is added to the Ethernet frame by host computers.
D) A host can be attached to a trunk port of a switch for data transmissions.
E) A switch port may be either an access or a trunk port, but not both at the same time.
A) Layer 2 switches can forward frames across different VLANs.
B) With VLANs, cut-through switching should be used to minimize transmission delays.
C) VLAN tagging information is added to the Ethernet frame by host computers.
D) A host can be attached to a trunk port of a switch for data transmissions.
E) A switch port may be either an access or a trunk port, but not both at the same time.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
23
Bridge Protocol Data Unit (BPDU) carries information relevant to (the) _________.
A) link aggregation
B) VLAN configuration
C) VLAN tagging
D) inter-VLAN routing
E) redundant path identification
A) link aggregation
B) VLAN configuration
C) VLAN tagging
D) inter-VLAN routing
E) redundant path identification

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
24
Refer to the figure below. 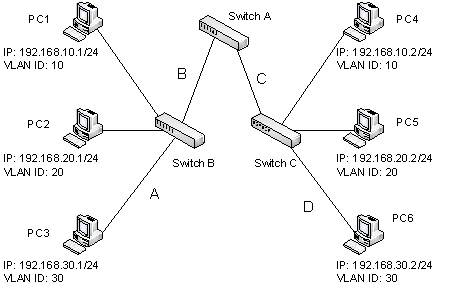 Which physical links should carry tagged Ethernet frames when PC3 and PC6 communicate?
Which physical links should carry tagged Ethernet frames when PC3 and PC6 communicate?
A) A, B, C, and D
B) A and D only
C) B and C only
D) A, B, and C
E) B,C, and D
 Which physical links should carry tagged Ethernet frames when PC3 and PC6 communicate?
Which physical links should carry tagged Ethernet frames when PC3 and PC6 communicate?A) A, B, C, and D
B) A and D only
C) B and C only
D) A, B, and C
E) B,C, and D

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck


