Deck 16: Cybersecurity
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/99
Play
Full screen (f)
Deck 16: Cybersecurity
1
The terms "hacker" and "attacker" are used to refer to
A) programmers with malicious intentions that pose a risk to a company.
B) analysts with ulterior motives.
C) managers whose behavior poses a risk to the company.
D) executives who treat the company's assets as their own.
A) programmers with malicious intentions that pose a risk to a company.
B) analysts with ulterior motives.
C) managers whose behavior poses a risk to the company.
D) executives who treat the company's assets as their own.
programmers with malicious intentions that pose a risk to a company.
2
Cybersecurity encompasses
A) actions by programmers with malicious intentions that pose a risk to a company.
B) the measures a company takes to protect a computer or system against unauthorized access or attacks.
C) actions taken by managers which pose a risk to the company.
D) actions by executives who treat the company's assets as their own.
A) actions by programmers with malicious intentions that pose a risk to a company.
B) the measures a company takes to protect a computer or system against unauthorized access or attacks.
C) actions taken by managers which pose a risk to the company.
D) actions by executives who treat the company's assets as their own.
the measures a company takes to protect a computer or system against unauthorized access or attacks.
3
Colonial Pipeline, which provides almost 50% of the fuel for the East Coast, is an example of an attack of
A) chaos and destruction.
B) financial data breach.
C) ransomware.
D) reconnaissance.
A) chaos and destruction.
B) financial data breach.
C) ransomware.
D) reconnaissance.
ransomware.
4
Florida Water Supply, a water treatment facility, is an example of being hacked to
A) obtain financial data.
B) create a denial of service.
C) obtain customer information.
D) cause chaos and destruction.
A) obtain financial data.
B) create a denial of service.
C) obtain customer information.
D) cause chaos and destruction.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
5
Equifax, a credit reporting agency, was victim to
A) a financial data breach.
B) ransomware.
C) reconnaissance.
D) chaos and destruction.
A) a financial data breach.
B) ransomware.
C) reconnaissance.
D) chaos and destruction.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
6
At larger companies, the cybersecurity program is usually the responsibility of a dedicated executive leader. This could include the
A) Chief Executive Officer.
B) Chief Information Officer.
C) Chief Marketing Officer.
D) Chief Operating Officer.
A) Chief Executive Officer.
B) Chief Information Officer.
C) Chief Marketing Officer.
D) Chief Operating Officer.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
7
At larger companies, the cybersecurity program is usually the responsibility of a dedicated executive leader. This could include the
A) Chief Executive Officer.
B) Chief Marketing Officer.
C) Chief Technology Officer.
D) Chief Operating Officer.
A) Chief Executive Officer.
B) Chief Marketing Officer.
C) Chief Technology Officer.
D) Chief Operating Officer.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
8
At larger companies, the cybersecurity program is usually the responsibility of a dedicated executive leader. This could include the
A) Chief Executive Officer.
B) Chief Marketing Officer.
C) Chief Operating Officer.
D) Chief Information Security Officer.
A) Chief Executive Officer.
B) Chief Marketing Officer.
C) Chief Operating Officer.
D) Chief Information Security Officer.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
9
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
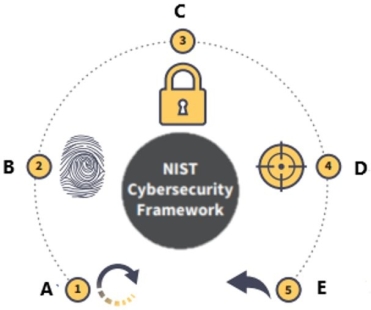 What is function A?
What is function A?
A) Recover
B) Identify
C) Protect
D) Detect
 What is function A?
What is function A?A) Recover
B) Identify
C) Protect
D) Detect

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
10
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
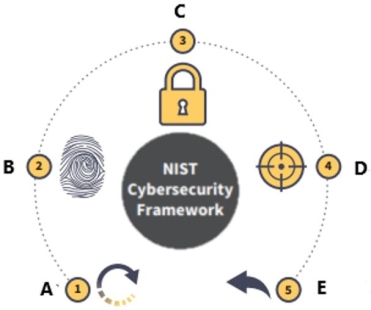 What is function B?
What is function B?
A) Recover
B) Identify
C) Protect
D) Detect
 What is function B?
What is function B?A) Recover
B) Identify
C) Protect
D) Detect

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
11
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
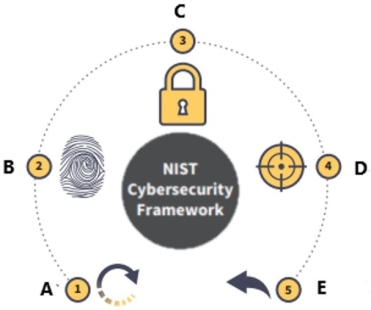 What is function C?
What is function C?
A) Recover
B) Identify
C) Protect
D) Detect
 What is function C?
What is function C?A) Recover
B) Identify
C) Protect
D) Detect

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
12
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
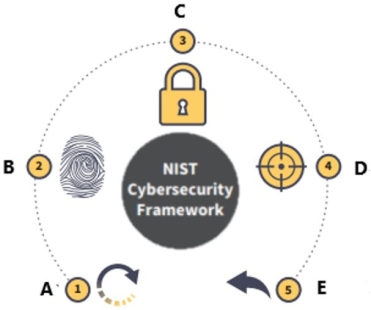 What is function D?
What is function D?
A) Recover
B) Identify
C) Protect
D) Detect
 What is function D?
What is function D?A) Recover
B) Identify
C) Protect
D) Detect

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
13
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is displayed below.
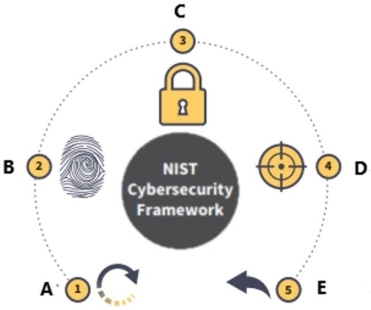 What is function E?
What is function E?
A) Respond
B) Identify
C) Protect
D) Detect
 What is function E?
What is function E?A) Respond
B) Identify
C) Protect
D) Detect

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
14
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is
A) a list of cybersecurity risks companies may face.
B) a catalog of security control baselines for business.
C) a checklist for Information Technology professionals.
D) a list of entry level cybersecurity jobs for Accounting professionals.
A) a list of cybersecurity risks companies may face.
B) a catalog of security control baselines for business.
C) a checklist for Information Technology professionals.
D) a list of entry level cybersecurity jobs for Accounting professionals.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
15
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into
A) 53 chapters.
B) 5 sections.
C) 18 control families.
D) 27 volumes.
A) 53 chapters.
B) 5 sections.
C) 18 control families.
D) 27 volumes.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
16
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). One of the control families is Access Control. What ID does Access Control family use?
A) AT
B) AN
C) AL
D) AC
A) AT
B) AN
C) AL
D) AC

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
17
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). One of the control families is Awareness and Training. What ID does Awareness and Training family use?
A) AT
B) AN
C) AL
D) AC
A) AT
B) AN
C) AL
D) AC

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
18
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Security Assessment and Authorization. What ID does Security Assessment and Authorization family use?
A) SA
B) CA
C) AA
D) AS
A) SA
B) CA
C) AA
D) AS

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
19
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Configuration Management. What ID does Configuration Management family use?
A) CO
B) MC
C) CM
D) CP
A) CO
B) MC
C) CM
D) CP

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
20
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Maintenance. What ID does Maintenance family use?
A) MT
B) AM
C) MN
D) MA
A) MT
B) AM
C) MN
D) MA

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
21
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Physical and Environmental Protection. What ID does Physical and Environmental Protection family use?
A) PE
B) PP
C) PH
D) PY
A) PE
B) PP
C) PH
D) PY

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
22
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is Personal Security. What ID does Personal Security family use?
A) PR
B) PS
C) PE
D) SE
A) PR
B) PS
C) PE
D) SE

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
23
The National Institute of Standards and Technology (NIST) has published Security and Privacy Controls for Federal Information Systems and Organizations (NIST-800-53). The NIST-800-53 document is divided into 18 control families. One of the control families is System and Information Integrity. What ID does System and Information Integrity family use?
A) SY
B) SS
C) SI
D) SN
A) SY
B) SS
C) SI
D) SN

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following reflects the correct sequence of the three steps of the cyber-kill chain?
A) Gather information about the network, access the network, disrupt the network
B) Access the network, gather information about the network, disrupt the network
C) Access the network, disrupt the network, gather information about the network
D) Disrupt the network, gather information about the network, access the network
A) Gather information about the network, access the network, disrupt the network
B) Access the network, gather information about the network, disrupt the network
C) Access the network, disrupt the network, gather information about the network
D) Disrupt the network, gather information about the network, access the network

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
25
What step do reconnaissance attacks correspond to in the cyber-kill chain?
A) Steal passwords
B) Gather information about the network
C) Access the network
D) Disrupt the network
A) Steal passwords
B) Gather information about the network
C) Access the network
D) Disrupt the network

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
26
Cybercriminals look for vulnerabilities in the network, through either a ________, who exposes valuable information or a ________ in the network.
A) person, company
B) company, person
C) person, technical weak point
D) company, technical weak point
A) person, company
B) company, person
C) person, technical weak point
D) company, technical weak point

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
27
What two categories do cyberattacks fall into?
A) Conceptual attack, theoretical attack
B) Conceptual attack, logical attack
C) Physical attack, conceptual attack
D) Physical attack, logical attack
A) Conceptual attack, theoretical attack
B) Conceptual attack, logical attack
C) Physical attack, conceptual attack
D) Physical attack, logical attack

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
28
Attackers us these three types of attacks to plan, enter, and damage a victim's network:
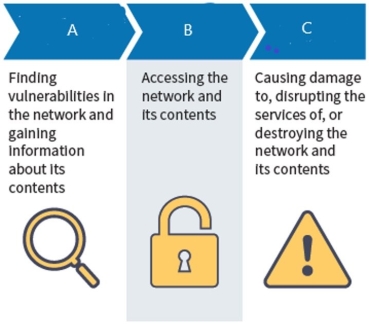 What type of attack is A?
What type of attack is A?
A) Reconnaissance attack
B) Access attack
C) Disruptive attack
D) Translucent attack
 What type of attack is A?
What type of attack is A?A) Reconnaissance attack
B) Access attack
C) Disruptive attack
D) Translucent attack

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
29
Attackers us these three types of attacks to plan, enter, and damage a victim's network:
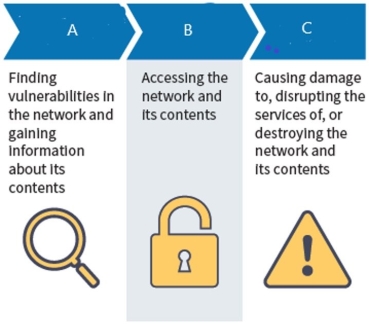 What type of attack is B?
What type of attack is B?
A) Reconnaissance attack
B) Access attack
C) Disruptive attack
D) Translucent attack
 What type of attack is B?
What type of attack is B?A) Reconnaissance attack
B) Access attack
C) Disruptive attack
D) Translucent attack

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
30
Attackers us these three types of attacks to plan, enter, and damage a victim's network:
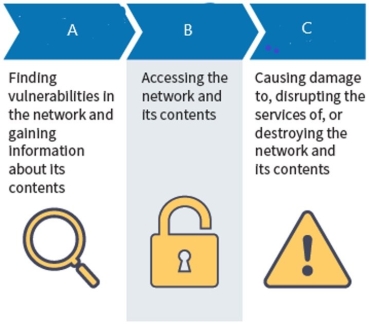 What type of attack is C?
What type of attack is C?
A) Reconnaissance attack
B) Access attack
C) Disruptive attack
D) Translucent attack
 What type of attack is C?
What type of attack is C?A) Reconnaissance attack
B) Access attack
C) Disruptive attack
D) Translucent attack

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the physical reconnaissance attacks is a deceptive request designed to trick victims into sharing private information?
A) Email phishing
B) Dumpster diving
C) Eavesdropping
D) Malware
A) Email phishing
B) Dumpster diving
C) Eavesdropping
D) Malware

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the physical reconnaissance attacks is looking through someone else's physical trash?
A) Phishing
B) Dumpster diving
C) Eavesdropping
D) Malware
A) Phishing
B) Dumpster diving
C) Eavesdropping
D) Malware

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the physical reconnaissance attacks is the unauthorized interception of communication?
A) Phishing
B) Dumpster diving
C) Eavesdropping
D) Malware
A) Phishing
B) Dumpster diving
C) Eavesdropping
D) Malware

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
34
What is a company's best defense against phishing attacks?
A) Only allow email from certified businesses
B) Shut down email
C) Monitor employee's email
D) Train employees to recognize and report red flags
A) Only allow email from certified businesses
B) Shut down email
C) Monitor employee's email
D) Train employees to recognize and report red flags

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
35
What is an incorrect sender address red flag?
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
36
What is a vague salutation red flag?
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
37
A company's best defense against phishing attacks is to train employees to recognize and report red flags. The correct definition of a poor grammar or spelling red flag is
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
38
What is an urgency red flag?
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
39
What is an unusual links red flag?
A) Hovering over a link in the email shows the actual link is not the same as the displayed text.
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"
A) Hovering over a link in the email shows the actual link is not the same as the displayed text.
B) Addressing the email to a generic recipient
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
40
What is a surveys red flag?
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Asking for personal information in a survey instead of taking you to a company portal to input information directly in the corporate system
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) Asking for personal information in a survey instead of taking you to a company portal to input information directly in the corporate system
C) Including grammar or spelling mistakes
D) Using words like "suspended", "security concerns," and "immediately"

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
41
What is encryption?
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) A standard network protocol that allows users to transfer files between the company network and outside parties
C) The process of using an algorithm to encode a plaintext message and converting it to something that is seemingly meaningless
D) Asking for personal information in a survey instead of taking you to a company portal to input information directly in the corporate system
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) A standard network protocol that allows users to transfer files between the company network and outside parties
C) The process of using an algorithm to encode a plaintext message and converting it to something that is seemingly meaningless
D) Asking for personal information in a survey instead of taking you to a company portal to input information directly in the corporate system

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
42
What is file transfer protocol (FTP)?
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) A standard network protocol that allows users to transfer files between the company network and outside parties
C) The process of using an algorithm to encode a plaintext message and converting it to something that is seemingly meaningless
D) Asking for personal information in a survey instead of taking you to a company portal to input information directly in the corporate system
A) Sending from obscure domains that are designed to look similar to legitimate domains
B) A standard network protocol that allows users to transfer files between the company network and outside parties
C) The process of using an algorithm to encode a plaintext message and converting it to something that is seemingly meaningless
D) Asking for personal information in a survey instead of taking you to a company portal to input information directly in the corporate system

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
43
The purpose of a ________, also called an IP probe, is to identify which hosts are active in the network by sending a communication to each IP address to see if there is a response packet.
A) ping sweep
B) port scan
C) computer scan
D) network sweep
A) ping sweep
B) port scan
C) computer scan
D) network sweep

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
44
For hackers to narrow their results, they use ________, which indicates which ports are open and sending or receiving data on the network.
A) ping sweep
B) port scans
C) computer scan
D) network sweep
A) ping sweep
B) port scans
C) computer scan
D) network sweep

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
45
What is it called when a company performs sweeps and scans to detect and classify loopholes in their infrastructure?
A) Vulnerability scans
B) Penetration tests
C) Patches
D) Upgrades
A) Vulnerability scans
B) Penetration tests
C) Patches
D) Upgrades

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
46
What is it called when a company attempts to hack their own systems?
A) Vulnerability scans
B) Penetration tests
C) Patches
D) Upgrades
A) Vulnerability scans
B) Penetration tests
C) Patches
D) Upgrades

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
47
What does a company apply to ensure that systems are running up-to-date security when they are available?
A) Vulnerability scans
B) Penetration tests
C) Patches
D) Upgrades
A) Vulnerability scans
B) Penetration tests
C) Patches
D) Upgrades

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
48
Physical access attacks
A) result in access to either hardware or people.
B) seek unauthorized access to a system by either exploiting a network vulnerability or attempting to use force to get through network security.
C) result in access to customers or vendors.
D) seek unauthorized access to employee records on the network.
A) result in access to either hardware or people.
B) seek unauthorized access to a system by either exploiting a network vulnerability or attempting to use force to get through network security.
C) result in access to customers or vendors.
D) seek unauthorized access to employee records on the network.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
49
________ are the biggest weakness in a company's internal control environment.
A) Networks
B) Humans
C) Systems
D) Routers
A) Networks
B) Humans
C) Systems
D) Routers

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
50
What is accidental tailgating?
A) Unauthorized users are aware that there is a tailgater.
B) The authorized user is aware of the other person and blocks entry to the tailgater.
C) Authorized users are unaware that there is a tailgater.
D) The authorized user is aware of the other person but may politely hold the door for the tailgater.
A) Unauthorized users are aware that there is a tailgater.
B) The authorized user is aware of the other person and blocks entry to the tailgater.
C) Authorized users are unaware that there is a tailgater.
D) The authorized user is aware of the other person but may politely hold the door for the tailgater.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
51
What is polite tailgating?
A) Unauthorized users are aware that there is a tailgater.
B) The authorized user is aware of the other person and blocks entry to the tailgater.
C) Authorized users are unaware that there is a tailgater.
D) The authorized user is aware of the other person but may politely hold the door for the tailgater.
A) Unauthorized users are aware that there is a tailgater.
B) The authorized user is aware of the other person and blocks entry to the tailgater.
C) Authorized users are unaware that there is a tailgater.
D) The authorized user is aware of the other person but may politely hold the door for the tailgater.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
52
Logical access attacks
A) result in access to either hardware or people.
B) seek unauthorized access to a system by either exploiting a network vulnerability or attempting to use force to get through network security.
C) result in access to customers or vendors.
D) seek unauthorized access to employee records on the network.
A) result in access to either hardware or people.
B) seek unauthorized access to a system by either exploiting a network vulnerability or attempting to use force to get through network security.
C) result in access to customers or vendors.
D) seek unauthorized access to employee records on the network.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
53
An attacker force access to the network by attempting many passwords or phrases until finding the correct one. What type of attack is being described?
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following logical access attacks is a brute-force attack?
A) An attacker forces access to the network by attempting many passwords or phrases until finding the correct one.
B) An attacker attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties.
C) An attacker disguises their identity and impersonates a legitimate computer on the network.
D) An attacker follows an authorized user into the system.
A) An attacker forces access to the network by attempting many passwords or phrases until finding the correct one.
B) An attacker attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties.
C) An attacker disguises their identity and impersonates a legitimate computer on the network.
D) An attacker follows an authorized user into the system.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
55
What type of logical access attack attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties?
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
56
Which of the following describes an on-path attack?
A) An on-path attack is when the attacker forces access to the network by attempting many passwords or phrases until finding the correct one.
B) An on-path attack is when the attacker attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties.
C) An on-path attack is when the attacker disguises their identity and impersonates a legitimate computer on the network.
D) An on-path attack is when the attacker follows an authorized user into the system.
A) An on-path attack is when the attacker forces access to the network by attempting many passwords or phrases until finding the correct one.
B) An on-path attack is when the attacker attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties.
C) An on-path attack is when the attacker disguises their identity and impersonates a legitimate computer on the network.
D) An on-path attack is when the attacker follows an authorized user into the system.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
57
What type of logical access attack disguises the source identity and impersonates a legitimate computer on the network?
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
58
Which of the following logical access attacks describes IP spoofing?
A) IP spoofing is when the attacker forces access to the network by attempting many passwords or phrases until finding the correct one.
B) IP spoofing is when the attacker attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties.
C) IP spoofing is when the attacker disguises their identity and impersonates a legitimate computer on the network.
D) IP spoofing is when the attacker follows an authorized user into the system.
A) IP spoofing is when the attacker forces access to the network by attempting many passwords or phrases until finding the correct one.
B) IP spoofing is when the attacker attempts to gain access to an on-going communication between two endpoints by pretending to be each of the parties.
C) IP spoofing is when the attacker disguises their identity and impersonates a legitimate computer on the network.
D) IP spoofing is when the attacker follows an authorized user into the system.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
59
NIST provides explicit guidelines that companies can require for password strength. What is the NIST recommended length?
A) 2 - 6 characters
B) 18 - 32 characters
C) 4 - 8 characters
D) 8 - 64 characters
A) 2 - 6 characters
B) 18 - 32 characters
C) 4 - 8 characters
D) 8 - 64 characters

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
60
NIST provides explicit guidelines that companies can require for password strength. What does NIST recommend for character types?
A) Mixture of letters, numbers, and special characters
B) Numbers only
C) Mixture of numbers and letters
D) Letters only
A) Mixture of letters, numbers, and special characters
B) Numbers only
C) Mixture of numbers and letters
D) Letters only

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
61
NIST provides explicit guidelines that companies can require for password strength. What is the NIST recommendation for resetting a password?
A) Reset your password every month.
B) Only reset your password if you know it has been compromised.
C) Reset your password every six months.
D) Never reset your password.
A) Reset your password every month.
B) Only reset your password if you know it has been compromised.
C) Reset your password every six months.
D) Never reset your password.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
62
NIST provides explicit guidelines that companies can require for password strength. What does NIST recommend for password construction?
A) Combine multiple common words in a password.
B) Reuse previous passwords so you remember them.
C) Avoid dictionary words.
D) Use your name as the password.
A) Combine multiple common words in a password.
B) Reuse previous passwords so you remember them.
C) Avoid dictionary words.
D) Use your name as the password.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
63
On-path attacks, which were once known as man-in-the-middle attacks, attempt to gain access to an ongoing communication between two endpoints. Which of the following is the definition of eavesdropping?
A) The hacker is actively communicating with the server.
B) The hacker is passively injected into the connection.
C) The hacker is actively injected into the connection.
D) The hacker is only listening to or intercepting the communication.
A) The hacker is actively communicating with the server.
B) The hacker is passively injected into the connection.
C) The hacker is actively injected into the connection.
D) The hacker is only listening to or intercepting the communication.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
64
Match the cybersecurity threat to the following control activity:
-Ensure that the information system enforces minimum password complexity of specified case sensitivity, character numbers, and mix of uppercase and lowercase letters, including minimum requirements for each type.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
-Ensure that the information system enforces minimum password complexity of specified case sensitivity, character numbers, and mix of uppercase and lowercase letters, including minimum requirements for each type.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
65
Match the cybersecurity threat to the following control activity:
-Enforce a specified number of changed characters when new passwords are created.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
-Enforce a specified number of changed characters when new passwords are created.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
66
Match the cybersecurity threat to the following control activity:
-Prohibit password reuse for a specified number of generations.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
-Prohibit password reuse for a specified number of generations.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
67
Match the cybersecurity threat to the following control activity:
-Review and update the baseline configuration of the information system using a company-defined frequency.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
-Review and update the baseline configuration of the information system using a company-defined frequency.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
68
Match the cybersecurity threat to the following control activity:
-Review and update the baseline configuration of the information system as an integral part of information system component installations and upgrades.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
-Review and update the baseline configuration of the information system as an integral part of information system component installations and upgrades.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
69
Match the cybersecurity threat to the following control activity:
-Ensure that the information system uniquely identifies and authenticates devices before establishing a connection.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating
-Ensure that the information system uniquely identifies and authenticates devices before establishing a connection.
A) Brute-force attack
B) On-path attack
C) IP spoofing
D) Tailgating

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
70
What is an attack that prohibits users from using resources such as computers, websites, servers, or an entire network called?
A) Denial-of-service attack
B) Malware attack
C) Virus attack
D) Logic bomb attack
A) Denial-of-service attack
B) Malware attack
C) Virus attack
D) Logic bomb attack

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
71
What is a Denial-of-service attack?
A) An attack that prohibits users from using resources such as computers, websites, servers, or an entire network
B) An attack that uses destructive programs to take down a system
C) An attack that is disguised as benign software but carries malicious code that may be activated via a logic bomb
D) An attack that is a piece of malicious code that is programmed into a system and remains dormant until certain conditions are met
A) An attack that prohibits users from using resources such as computers, websites, servers, or an entire network
B) An attack that uses destructive programs to take down a system
C) An attack that is disguised as benign software but carries malicious code that may be activated via a logic bomb
D) An attack that is a piece of malicious code that is programmed into a system and remains dormant until certain conditions are met

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
72
What is a Botnet attack?
A) An attack that creates a virus that cause a variety of problems
B) An attack that is disguised as benign software but carries malicious code that may be activated via a logic bomb
C) An attack that uses computers infected with malware that function like robots
D) An attack that uses multiple machines or IP addresses to force the target to shut down
A) An attack that creates a virus that cause a variety of problems
B) An attack that is disguised as benign software but carries malicious code that may be activated via a logic bomb
C) An attack that uses computers infected with malware that function like robots
D) An attack that uses multiple machines or IP addresses to force the target to shut down

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
73
What is a Distributed Denial-of-Service attack?
A) An attack that creates a virus that cause a variety of problems
B) An attack that is disguised as benign software but carries malicious code that may be activated via a logic bomb
C) An attack that uses computers infected with malware that function like robots
D) An attack that uses multiple machines or IP addresses to force the target to shut down
A) An attack that creates a virus that cause a variety of problems
B) An attack that is disguised as benign software but carries malicious code that may be activated via a logic bomb
C) An attack that uses computers infected with malware that function like robots
D) An attack that uses multiple machines or IP addresses to force the target to shut down

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
74
A business can protect itself from DoS and DDoS attacks by ensuring that ________, routers, and intrusion detection systems are up-to-date, are properly configured, and will automatically block the ports where fake requests enter the system.
A) firewalls
B) servers
C) websites
D) ecommerce sites
A) firewalls
B) servers
C) websites
D) ecommerce sites

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
75
A business can protect itself from DoS and DDoS attacks by ensuring that firewalls, ________, and intrusion detection systems are up-to-date, are properly configured, and will automatically block the ports where fake requests enter the system.
A) servers
B) routers
C) websites
D) ecommerce sites
A) servers
B) routers
C) websites
D) ecommerce sites

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
76
A business can protect itself from DoS and DDoS attacks by ensuring that firewalls, routers, and ________ are up-to-date, are properly configured, and will automatically block the ports where fake requests enter the system.
A) servers
B) websites
C) intrusion detection systems
D) ecommerce sites
A) servers
B) websites
C) intrusion detection systems
D) ecommerce sites

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
77
Which of the following is an example of a Denial-of-Service internal control?
A) Manage capacity, bandwidth, or other redundancy to limit the effects of an attack.
B) Employ malicious code protection mechanisms at information system entry and exit points.
C) Configure malicious code detection to perform periodic scans of the information system, block malicious code, quarantine malicious code, and notify the administrator.
D) Monitor the information systems to detect attacks and indicators of potential attacks, including unauthorized local, network, and remote connections.
A) Manage capacity, bandwidth, or other redundancy to limit the effects of an attack.
B) Employ malicious code protection mechanisms at information system entry and exit points.
C) Configure malicious code detection to perform periodic scans of the information system, block malicious code, quarantine malicious code, and notify the administrator.
D) Monitor the information systems to detect attacks and indicators of potential attacks, including unauthorized local, network, and remote connections.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
78
Which of the following is an example of a Denial-of-Service internal control?
A) Employ malicious code protection mechanisms at information system entry and exit points.
B) Employ monitoring tools to detect indicators of attacks against, or launched from, the system.
C) Configure malicious code detection to perform periodic scans of the information system, block malicious code, quarantine malicious code, and notify the administrator.
D) Monitor the information systems to detect attacks and indicators of potential attacks, including unauthorized local, network, and remote connections.
A) Employ malicious code protection mechanisms at information system entry and exit points.
B) Employ monitoring tools to detect indicators of attacks against, or launched from, the system.
C) Configure malicious code detection to perform periodic scans of the information system, block malicious code, quarantine malicious code, and notify the administrator.
D) Monitor the information systems to detect attacks and indicators of potential attacks, including unauthorized local, network, and remote connections.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
79
Which of the following is an example of a Denial-of-Service internal control?
A) Employ malicious code protection mechanisms at information system entry and exit points.
B) Configure malicious code detection to perform periodic scans of the information system, block malicious code, quarantine malicious code, and notify the administrator.
C) Monitor system resources to determine if sufficient resources exist to prevent effective attacks.
D) Monitor the information systems to detect attacks and indicators of potential attacks, including unauthorized local, network, and remote connections.
A) Employ malicious code protection mechanisms at information system entry and exit points.
B) Configure malicious code detection to perform periodic scans of the information system, block malicious code, quarantine malicious code, and notify the administrator.
C) Monitor system resources to determine if sufficient resources exist to prevent effective attacks.
D) Monitor the information systems to detect attacks and indicators of potential attacks, including unauthorized local, network, and remote connections.

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck
80
What is an attack that uses destructive programs to take down a system called?
A) Denial-of-service attack
B) Malware attack
C) Virus attack
D) Logic bomb attack
A) Denial-of-service attack
B) Malware attack
C) Virus attack
D) Logic bomb attack

Unlock Deck
Unlock for access to all 99 flashcards in this deck.
Unlock Deck
k this deck


