Deck 7: Criminal Intelligence and Surveillance Operations
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/53
Play
Full screen (f)
Deck 7: Criminal Intelligence and Surveillance Operations
1
Which best describes the goal of the RISS projects?
A)To ensure a systematic method for data collection and target selection
B)To provide tactical intelligence information to guide decision making
C)To create a nationwide,strategic plan for intelligence collation
D)To aid state and local law enforcement agencies in sharing criminal intelligence
A)To ensure a systematic method for data collection and target selection
B)To provide tactical intelligence information to guide decision making
C)To create a nationwide,strategic plan for intelligence collation
D)To aid state and local law enforcement agencies in sharing criminal intelligence
D
2
What is the final stage of the intelligence process?
A)Analysis
B)Flowcharting
C)Dissemination of information
D)Data collection
A)Analysis
B)Flowcharting
C)Dissemination of information
D)Data collection
C
3
A technique designed to show relationships between individuals and organizations,using a graphical visual design is called:
A)link analysis.
B)flowcharting.
C)visualization.
D)diagramming.
A)link analysis.
B)flowcharting.
C)visualization.
D)diagramming.
A
4
The purpose of _____ is to make fragmented information flow in a logical sequence and make it purposeful to the user.
A)data collection
B)analysis
C)target selection
D)dissemination
A)data collection
B)analysis
C)target selection
D)dissemination

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
5
Which of the following tactics is most successful both in the prevention of terrorism and in the prevention of other illegal activities?
A)Imposing harsher punishments
B)Increasing security at every level of society
C)Decreasing emergency response times
D)Increasing and improving intelligence gathering efforts
A)Imposing harsher punishments
B)Increasing security at every level of society
C)Decreasing emergency response times
D)Increasing and improving intelligence gathering efforts

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
6
Which best explains the utility of an investigation target?
A) The value or worth of the investigation's findings if successful
B)The amount of money the state will save by prosecuting the criminal
C)The length of sentence the criminal will probably receive
D)The heinousness of the criminal's activities
A) The value or worth of the investigation's findings if successful
B)The amount of money the state will save by prosecuting the criminal
C)The length of sentence the criminal will probably receive
D)The heinousness of the criminal's activities

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
7
Satellite surveillance refers to the use of:
A)moonlight on clear nights.
B)the positions of stars and the tracking of criminal suspects.
C)starlight scopes.
D)GPS technology.
A)moonlight on clear nights.
B)the positions of stars and the tracking of criminal suspects.
C)starlight scopes.
D)GPS technology.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
8
Which of the following is LEAST likely to be a valid surveillance activity?
A)Electronic eavesdropping
B)Examination of subject/suspects garbage
C)Use of lineup
D)Robot (automatic)cameras
A)Electronic eavesdropping
B)Examination of subject/suspects garbage
C)Use of lineup
D)Robot (automatic)cameras

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
9
Which is the first step in the intelligence gathering process?
A)Target selection
B)Collection
C)Dissemination
D)Collation and analysis
A)Target selection
B)Collection
C)Dissemination
D)Collation and analysis

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following is true regarding the nature of the criminal intelligence function?
A)The patrol division is especially useful in conducting covert intelligence activities.
B)Overt intelligence collection is more commonly done during undercover operations.
C)Typically,the role of intelligence personnel is to receive information from line personnel,not to deliver information to them.
D) Covert methods include the use of surveillance equipment,undercover officers,and informants.
A)The patrol division is especially useful in conducting covert intelligence activities.
B)Overt intelligence collection is more commonly done during undercover operations.
C)Typically,the role of intelligence personnel is to receive information from line personnel,not to deliver information to them.
D) Covert methods include the use of surveillance equipment,undercover officers,and informants.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
11
How are criminal and intelligence functions different?
A)Intelligence personnel tend to use deductive logic while criminal personnel tend to use inductive logic.
B)Criminal investigations tend to be proactive in nature while intelligence ones are reactive.
C) Intelligence files generally are closed while criminal files generally are open.
D)Criminal personnel are staff functions while intelligence personnel are line functions.
A)Intelligence personnel tend to use deductive logic while criminal personnel tend to use inductive logic.
B)Criminal investigations tend to be proactive in nature while intelligence ones are reactive.
C) Intelligence files generally are closed while criminal files generally are open.
D)Criminal personnel are staff functions while intelligence personnel are line functions.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
12
Which best describes the collation process?
A)Listing the names of criminals in various crimes
B)Providing information to different agencies
C)Comparing data by designing charts in sequence
D)Deleting data that is not relevant to the objective
A)Listing the names of criminals in various crimes
B)Providing information to different agencies
C)Comparing data by designing charts in sequence
D)Deleting data that is not relevant to the objective

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
13
Which type of intelligence provides investigators with a tool for long-range planning?
A)Tactical
B)Strategic
C)Distance
D)Future
A)Tactical
B)Strategic
C)Distance
D)Future

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
14
Surveillance is a process that allows investigators to:
A)make arrests.
B)work undercover.
C)pay an informant by using secret funds.
D) observe a suspect without arousing his/her suspicions.
A)make arrests.
B)work undercover.
C)pay an informant by using secret funds.
D) observe a suspect without arousing his/her suspicions.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
15
Which of the following is a method of surveillance?
A)Fixed surveillance
B)Foot surveillance
C)Vehicle surveillance
D) All of the above.
A)Fixed surveillance
B)Foot surveillance
C)Vehicle surveillance
D) All of the above.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
16
A technique that demonstrates a chain of events or activities over a period of time is called:
A)link analysis.
B)flowcharting.
C)streaming.
D)diagramming.
A)link analysis.
B)flowcharting.
C)streaming.
D)diagramming.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
17
The public rejection of electronic eavesdropping most likely originates in:
A)a fear of disclosure of hidden crimes.
B)aversion to an invasion of privacy.
C)a lack of knowledge of electronics.
D)the opinion that it is a "dirty business."
A)a fear of disclosure of hidden crimes.
B)aversion to an invasion of privacy.
C)a lack of knowledge of electronics.
D)the opinion that it is a "dirty business."

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
18
Which illegal activities are the LEAST to be the targets of an intelligence operation?
A)Drug trafficking
B)Sexual Assault,vandalism,and theft
C)Pornography,prostitution,and gambling
D)Fraud and extortion
A)Drug trafficking
B)Sexual Assault,vandalism,and theft
C)Pornography,prostitution,and gambling
D)Fraud and extortion

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
19
The "core area" of police intelligence process is:
A)review.
B)analysis-interpretation.
C)dissemination.
D)collection.
A)review.
B)analysis-interpretation.
C)dissemination.
D)collection.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
20
Information should NOT be gathered about which of the following organizations?
A)Organizations that advocate the use of violence to affect the government
B)Organizations that possess chemical weapons for unlawful purposes
C)Organizations that have unusual political views but do not present a clear and present danger
D)Organizations that finance violent or unlawful activity.
A)Organizations that advocate the use of violence to affect the government
B)Organizations that possess chemical weapons for unlawful purposes
C)Organizations that have unusual political views but do not present a clear and present danger
D)Organizations that finance violent or unlawful activity.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
21
Each state in the United States is its own RISS region.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
22
Event flow analysis is the most commonly used method of investigating drug kingpins.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
23
_____ intelligence provides the investigator with a tool for long-range planning.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
24
The collection gathering stage of the intelligence process is the final stage and is where the process most likely breaks down.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
25
Intelligence operations should not be used to gather information about people solely because of their political views.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
26
The leapfrogging technique is used for following persons under surveillance who are either on foot or in vehicles.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
27
The U.S.Supreme Court has ruled that law enforcement officers may constitutionally break and enter to install listening devices.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
28
Intelligence files should never be purged.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
29
The U.S.Supreme Court has established that eavesdropping and other forms of audio surveillance may be conducted in public places without a warrant.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
30
The single or "one-man surveillance" is the most difficult because the suspect must be kept in view at all times and close contact is required by the officer.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
31
A device that electronically signals the location of automobiles,or other objects to which it is affixed,is known as a bumper beeper and its use has been prohibited by the courts.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
32
_____information collection includes personal interaction with people,many of whom are witnesses,victims,and even suspects.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
33
The dissemination stage of the intelligence process is the process that most commonly breaks down.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
34
The RISS projects are funded on a yearly basis by the United States Congress.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
35
Whenever possible,the surveillance car should be occupied by more than one officer.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
36
Covert information collection is the most common form of intelligence collection and includes a process known as intelligence gathering.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
37
To make sense out of the multitudes of information,a process known as data description and integration is used.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
38
A flowchart illustrates an activity at a single point in time.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
39
______information collection methods include the use of surveillance equipment,undercover officers,and informants.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
40
The primary purpose of the RISS projects is to provide the means to share criminal intelligence among member agencies.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
41
You have been working with a local police department that makes use of their aviation unit's helicopter to conduct thermal imaging operations in seeking out drugs in your community.Discuss and determine why you would choose to ask this organization for assistance with locating marijuana growing in your community.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
42
_______ files are criminal information developed for the purpose of making an arrest and gaining a conviction in a court of law.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
43
_____ intelligence targets criminal activity considered to be of immediate importance to the investigator.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
44
_____ is the secret or clandestine collecting and evaluation of information about crime and criminals not normally available to investigators.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
45
_____ analysis is a technique designed to show relationships between individuals and organizations,using a graphical visual design.
*Link
*Link

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
46
_____ is the stage of intelligence process in which information is shared with other law enforcement agencies.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
47
Matching
Locate the correct matches from Column 1 to Column 2
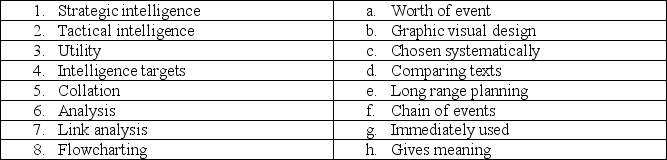
Locate the correct matches from Column 1 to Column 2


Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
48
You are preparing to conduct a surveillance operation and will need to be prepared.Determine what information you should have or attempt to obtain prior to conducting the actual surveillance.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
49
The surveillance operation can produce a great deal of needed information for the investigator.Discuss what detailed information can accomplish for the investigator.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
50
Your textbook identifies many items that surveillance officers should possess within their "Surveillance Kit Checklist." Identify a minimum of five of these items.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
51
Intelligence files are ______ files.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
52
_____ demonstrates a chain of events or activities over a period of time.

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck
54
Match between columns

Unlock Deck
Unlock for access to all 53 flashcards in this deck.
Unlock Deck
k this deck


