Deck 2: Basic Communication on the Internet: Email
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/150
Play
Full screen (f)
Deck 2: Basic Communication on the Internet: Email
1
An email with a Subject line beginning with "Fw" indicates that the message has been forwarded.
True
2
When you send an email message, the message is sent to a mail server.
True
3
A message can be queued, or temporarily held with other messages.
True
4
The CRAM-SPAM law was the first U.S. federal government effort to legislate controls on spam.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
5
Email is considered private, and therefore safe to use as a medium for discussing sensitive information.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
6
After uploading a file to SkyDrive, you can add comments to it, but you cannot rename the file.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
7
Thanks to improved technology, email attachments no longer contain viruses.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
8
POP (or POP3) is an extensively used protocol for handling incoming email messages.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
9
Thunderbird is Microsoft's open source email project.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
10
The IMAP protocol specifies how to encode nontext data, such as graphics and sound, in an email so that it can travel over the Internet.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
11
In Hotmail, if you want to forward the message to several people, type their addresses, separated by periods.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
12
In Hotmail, when you delete a message or folder, you are simply moving it to the Deleted folder.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
13
The term "NetManners" refers to the set of commonly accepted rules that represent proper behavior on a network.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
14
"UCE" is another term for spam.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
15
When you delete an email message that contains an attached file, you also delete the file that is attached to the message.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
16
In an email message, it is common to see a special mark preceding each line of a quoted message.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
17
Bcc email recipients are unaware of other Bcc recipients.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
18
A signature is not optional when sending an email.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
19
"Detaching a file" is the phrase often used for saving an email attachment to your computer.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
20
When you don't need a message any longer, you can delete it by opening the message and then clicking the Recycle link on the Hotmail menu bar.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
21
____ are rules that determine how the Internet handles message packets flowing on it.
A) Mores
B) Protocols
C) Servers
D) Codes
A) Mores
B) Protocols
C) Servers
D) Codes

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
22
To save an attached file in Hotmail using Firefox, click the attached file's Upload link in the message header, click the Save File option button in the dialog box that opens, and then click the OK button. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
23
In Windows Live Mail, when you receive new mail, messages that you haven't opened yet are displayed with a(n) closed envelope icon next to them. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
24
An email sender's local network sends the message to the sender's mail ____.
A) portal
B) server
C) modem
D) satellite
A) portal
B) server
C) modem
D) satellite

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
25
Most email programs offer you two options for replying to a message that you have received: Reply or Reply All. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
26
An email user's account name is also known as their domain name. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
27
"Email" is short for ____.
A) encoded mail
B) ethernet mail
C) electronic mail
D) none of the above
A) encoded mail
B) ethernet mail
C) electronic mail
D) none of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
28
The sender uses an email program ____ to enter the recipient's email address, compose the email message, attach optional files, and send the message.
A) on a computer
B) on a Web browser
C) either a. or b.
D) neither a. nor b.
A) on a computer
B) on a Web browser
C) either a. or b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
29
Some email programs let you define and use a(n) queue to move incoming mail into a specific folder. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
30
A(n) emoticon is a group of keyboard characters that when viewed together represent a human expression. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
31
____ handles outgoing email messages, determining the paths an email message takes on the Internet.
A) POP
B) SMTP
C) IMAP
D) MIME
A) POP
B) SMTP
C) IMAP
D) MIME

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
32
When you jump a message, you are sending a copy of the message, including any attachments, to one or more recipients who were not included in the original message. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
33
To reply to a message, click the Reply link on the Hotmail menu bar to reply only to the sender. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
34
In an email, the message body contains the actual message content. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
35
Thunderbird is the companion email program for Mozilla Firefox. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
36
You cannot attach more than one file to an email message. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
37
When sending business correspondence, use a(n) semicolon to introduce a list of items or an explanation. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
38
Protocols are rules that determine how the Internet handles message packets flowing on it. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
39
The full email address of the main recipient should be entered into the Cc line of a message header. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
40
When sending business correspondence, use a(n) comma to indicate a brief pause in a sentence, or to join or separate sentence parts. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
41
A ____ contains information about the message.
A) salutation
B) message header
C) message body
D) signature
A) salutation
B) message header
C) message body
D) signature

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
42
When you send along a complex document or graphic as part of your email, you send it along as a(n) ____.
A) tag
B) attachment
C) protocol
D) wrapper
A) tag
B) attachment
C) protocol
D) wrapper

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
43
The ____ contains the actual message content.
A) salutation
B) message header
C) message body
D) signature
A) salutation
B) message header
C) message body
D) signature

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
44
The software that requests mail delivery from the mail server to an Internet device is known as mail ____ software.
A) server
B) user
C) client
D) box
A) server
B) user
C) client
D) box

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
45
A file that has been attached to an email message will be received by those recipients in the ____ line(s) of the message header.
A) To only
B) To and Cc only
C) To, Cc, and Bcc
D) Bcc only
A) To only
B) To and Cc only
C) To, Cc, and Bcc
D) Bcc only

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
46
A ____ might appear at the bottom of an email message and contain standard information about the sender.
A) salutation
B) message header
C) message body
D) signature
A) salutation
B) message header
C) message body
D) signature

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
47
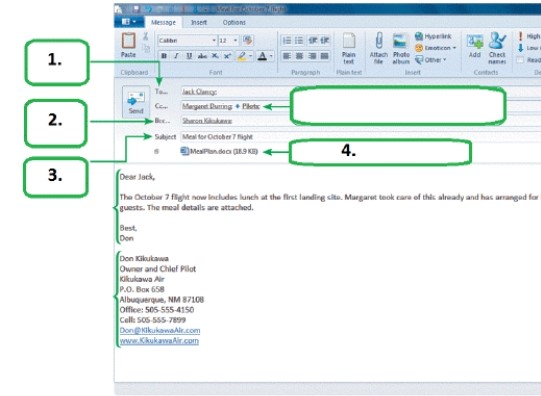
In the figure above, the area labeled "3" indicates the ____.
A) message's primary recipients
B) attachment filename and size
C) message topic
D) recipients receiving a blind courtesy copy

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
48
A(n) ____ name usually identifies one person's email account on a mail server.
A) domain
B) Web
C) IP
D) user
A) domain
B) Web
C) IP
D) user

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
49

In the figure above, the area labeled "1" indicates the ____.
A) message's primary recipients
B) attachment filename and size
C) message topic
D) recipients receiving a blind courtesy copy

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
50

In the figure above, the area labeled "2" indicates the ____.
A) message's primary recipients
B) attachment filename and size
C) message topic
D) recipients receiving a blind courtesy copy

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
51

In the figure above, the area labeled "4" indicates the ____.
A) message's primary recipients
B) attachment filename and size
C) message topic
D) recipients receiving a blind courtesy copy

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
52
Some mail servers will reject messages with too many recipients (usually ____ or more).
A) 25
B) 50
C) 10
D) 100
A) 25
B) 50
C) 10
D) 100

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
53
MIME stands for Multipurpose Internet Mail ____.
A) Entities
B) Extensions
C) Envelopes
D) Encryption
A) Entities
B) Extensions
C) Envelopes
D) Encryption

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
54
When sending an email to multiple recipients, separate the addresses with a ____.
A) comma
B) semicolon
C) either a. or b.
D) neither a. nor b.
A) comma
B) semicolon
C) either a. or b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
55
The ____ protocol specifies how to encode nontext data, such as graphics or sound, so it can travel over the Internet.
A) POP
B) MIME
C) SMTP
D) IMAP
A) POP
B) MIME
C) SMTP
D) IMAP

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
56
All of the following are typical parts of an email message EXCEPT ____.
A) salutation
B) message header
C) message body
D) signature
A) salutation
B) message header
C) message body
D) signature

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
57
A single email address that can represent several email addresses is called a ____.
A) category
B) group
C) either a. or b.
D) neither a. nor b.
A) category
B) group
C) either a. or b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
58
A(n) ____ file is a file you can view but cannot change.
A) read-only
B) locked
C) shared
D) attach-only
A) read-only
B) locked
C) shared
D) attach-only

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
59
To route an email message to someone, you must identify that person by his or her user name, and by their ____.
A) passphrase
B) domain name
C) IP address
D) time zone
A) passphrase
B) domain name
C) IP address
D) time zone

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
60
Most organizations have ____.
A) a single mail server to manage the email they send and receive
B) one mail server for email received and one mail server for email sent
C) multiple mail servers for email coming in, and only one mail server for outgoing mail
D) none of the above
A) a single mail server to manage the email they send and receive
B) one mail server for email received and one mail server for email sent
C) multiple mail servers for email coming in, and only one mail server for outgoing mail
D) none of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
61
If your email program does not provide filters, you can filter the messages ____ by reading them and moving them to the appropriate folders.
A) automatically
B) manually
C) randomly
D) Web-style
A) automatically
B) manually
C) randomly
D) Web-style

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
62
If you are using email for a business communication, your ____ usually contains your name, title, and your company's name.
A) closing
B) e-envelope
C) mail server
D) signature file
A) closing
B) e-envelope
C) mail server
D) signature file

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
63
When using the "Reply All" option, your message will automatically be sent to ____ recipients of the original message.
A) To only
B) To and Cc only
C) To, Cc, and Bcc
D) CC only
A) To only
B) To and Cc only
C) To, Cc, and Bcc
D) CC only

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
64
If you are in the midst of composing an email message, but want to save it and finish it later, you can store your email in your program's ____ folder.
A) Buffer
B) Inbox
C) Drafts
D) Queue
A) Buffer
B) Inbox
C) Drafts
D) Queue

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
65
The email address someone@mail.com is the same as the email address ____.
A) somebody@mail.com
B) someone@maildotcom
C) Someone@mail.org
D) Someone@mail.com
A) somebody@mail.com
B) someone@maildotcom
C) Someone@mail.org
D) Someone@mail.com

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
66
All of the following are email acronyms noted in the text EXCEPT ____.
A) btw
B) imho
C) wth
D) atm
A) btw
B) imho
C) wth
D) atm

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
67
A group of keyboard characters that, viewed together, represent a human expression is known as a(n) ____.
A) e-doodle
B) Web face
C) emoticon
D) Nettitude
A) e-doodle
B) Web face
C) emoticon
D) Nettitude

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
68
The following are generally accepted rules for email messages EXCEPT ____.
A) avoid writing messages in all capital letters
B) don't overuse formatting and graphics
C) always forward new information about viruses and hoaxes
D) use caution when attempting sarcasm or humor in your messages
A) avoid writing messages in all capital letters
B) don't overuse formatting and graphics
C) always forward new information about viruses and hoaxes
D) use caution when attempting sarcasm or humor in your messages

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
69
In your address book, you can assign each entry a unique ____ so it is easier to address your email messages.
A) tag
B) moniker
C) nickname
D) domain name
A) tag
B) moniker
C) nickname
D) domain name

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
70
Software that only detects and eliminates malicious code is called a(n) ____ program.
A) sniffer
B) antivirus
C) cracker
D) watchdog
A) sniffer
B) antivirus
C) cracker
D) watchdog

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
71
Email attachments can contain malicious programs called ____.
A) bugs
B) wyrms
C) hackers
D) viruses
A) bugs
B) wyrms
C) hackers
D) viruses

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
72
A virus ____ is a sequence of characters that is always present in a particular virus.
A) signature
B) pattern
C) definition
D) all of the above
A) signature
B) pattern
C) definition
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
73
Mozilla's email program is called ____.
A) Thunderbird
B) Opera
C) Apache
D) Outlook Express
A) Thunderbird
B) Opera
C) Apache
D) Outlook Express

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
74
If you receive an email message from a sender that you don't recognize and the message contains an attached file, you should ____.
A) contact the local police so they can run a trace on the email
B) only open the file in the evenings, when malicious code is less virulent
C) immediately delete the email and reboot the computer
D) avoid opening the file until you are sure that it doesn't contain a virus
A) contact the local police so they can run a trace on the email
B) only open the file in the evenings, when malicious code is less virulent
C) immediately delete the email and reboot the computer
D) avoid opening the file until you are sure that it doesn't contain a virus

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
75
Some email programs let you use a(n) ____ to move incoming mail to a specific folder or to delete it automatically based on the content of the message.
A) router
B) baffle
C) filter
D) protocol
A) router
B) baffle
C) filter
D) protocol

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
76
The term ____ refers to a set of commonly accepted rules for proper behavior on a network.
A) netiquette
B) mores
C) e-manners
D) E-mily Post
A) netiquette
B) mores
C) e-manners
D) E-mily Post

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
77
A ____ message is a copy of the sender's original message with your inserted comments.
A) drafted
B) volley
C) quoted
D) plagiarized
A) drafted
B) volley
C) quoted
D) plagiarized

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
78
Another term for junk mail is ____.
A) slop
B) clutter
C) ramen
D) spam
A) slop
B) clutter
C) ramen
D) spam

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
79
The email acronym "iow" stands for "____."
A) inbox/outbox/work
B) in other words
C) in or win
D) in one word
A) inbox/outbox/work
B) in other words
C) in or win
D) in one word

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
80
When you ____ a message, a copy of the original message is sent to the new recipient(s) without the original sender's knowledge.
A) forward
B) reply to
C) draft
D) filter
A) forward
B) reply to
C) draft
D) filter

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck


