Deck 6: Internet Security
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/150
Play
Full screen (f)
Deck 6: Internet Security
1
A port scan tests whether a computer's various ports are open, closed, or stealth.
True
2
ActiveX technology was developed by Microsoft.
True
3
Physical security includes protecting assets using physical means.
True
4
Computers hijacked without the owner's knowledge are often called spammers.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
5
Computer security experts generally classify computer security threats into three categories: secrecy, integrity, and necessity.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
6
In a brute force attack, a cracker uses a program to enter character combinations until the system accepts a user name and password.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
7
The process of using a key to reverse encrypted text is called cryptography.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
8
A client certificate authenticates a Web site so site visitors can be confident in the identity of the Web server.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
9
Malware is short for malfunctioning freeware.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
10
DoS attacks can happen on mobile networks.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
11
A digital ID is most often used by people using social networks, such as Facebook, to verify their posts.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
12
Public-key encryption is also called symmetric encryption.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
13
You can purchase a digital signature from a certificate authority site.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
14
A bulkhead is a software program or hardware device that controls access between two networks.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
15
Software that gathers personal information about the user's behavior or the user's computer without their knowledge is called infoware.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
16
A counterstrike is a procedure that recognizes, reduces, or eliminates a threat.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
17
The text recommends having your Social Security number printed on your checks.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
18
The latest, most secure form of SSL certificate is known as SSL-EV.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
19
A Trojan horse is a potentially harmful program hidden inside another program.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
20
A DoS filter can help defend against DoS attacks.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
21
Most firewalls are installed to prevent traffic from entering the network. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
22
The use of spyware is always illegal. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
23
Many viruses can send you an email that includes the name of someone you know in the message's From line, a tactic called phishing. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
24
A(n) identity manager stores user name and password information in encrypted form on a computer. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
25
Encrypted information is called cipher text. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
26
A talented computer programmer who uses his skills to commit illegal acts is sometimes known as a(n) snacker. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
27
The use of nonphysical security techniques to protect data stored on computers is sometimes called computer security. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
28
When an "@" symbol appears in a URL, all characters that precede the symbol are ignored. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
29
Computer security is the use of ____ security techniques to protect data stored on computers.
A) physical
B) port
C) logical
D) encrypted
A) physical
B) port
C) logical
D) encrypted

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
30
A(n) packet sniffer examines the structure of the data elements that flow through a network. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
31
The combination of user login plus password is called multifactor authentication. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
32
When the user loads the Web page that contains the code shown in the figure above, the browser downloads the ____ file from the DoubleClick server.
A) clear GIF
B) clear JPG
C) clear widget
D) clear screensaver
A) clear GIF
B) clear JPG
C) clear widget
D) clear screensaver

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
33
A Web phish is a small, hidden graphic on a Web page or email message that works with a cookie to obtain information about the person viewing the page or email message. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
34
Asymmetric encryption uses a public and a private key to exchange encrypted messages. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
35
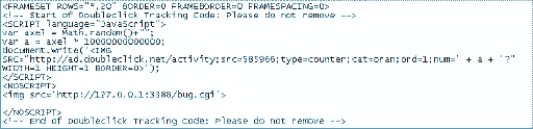
The figure above shows a(n) ____ page that contains a Web bug.
A) HTTPS page
B) User History page
C) HTML page
D) FTP page

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
36
The location of the clear GIF shown in the figure above is a URL for DoubleClick, a division of ____ that develops tools for Internet marketing and advertising.
A) Yahoo!
B) Google
C) Microsoft
D) Apple
A) Yahoo!
B) Google
C) Microsoft
D) Apple

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
37
A(n) certificate authority authenticates the certificate holder's identity and issues digital certificates. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
38
A digital logo is a digital pattern containing copyright information that is inserted into a digital image, animation, or audio or video file. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
39
Java, JavaScript, and ActiveX programs are all considered proactive content. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
40
There are two types of security: ____ and ____.
A) physical, logical
B) client, server
C) active, passive
D) internal, external
A) physical, logical
B) client, server
C) active, passive
D) internal, external

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
41
A(n) ____ is a formula or set of steps to solve a particular problem.
A) thought process
B) steganograph
C) key
D) algorithm
A) thought process
B) steganograph
C) key
D) algorithm

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
42
Email ____ involves a virus sending you an email that includes the name of someone you know in the message's From line.
A) scamming
B) spamming
C) spoofing
D) goofing
A) scamming
B) spamming
C) spoofing
D) goofing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
43
All characters that precede a(n) "____" symbol in a URL are ignored by a Web server.
A) @
B) /
C) _
D) %
A) @
B) /
C) _
D) %

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
44
All of the following are categories of computer security threat EXCEPT ____.
A) secrecy
B) subterfuge
C) integrity
D) necessity
A) secrecy
B) subterfuge
C) integrity
D) necessity

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
45
If you click a link in a phishing email, you will likely be taken to ____.
A) a legitimate Web site, in which you can do business safely
B) a competitor's Web site (say, going to BarnesandNoble.com when you thought you were going to Amazon.com)
C) the phishing perpetrator's Web site
D) A Web site that is being targeted by a denial-of-service attack
A) a legitimate Web site, in which you can do business safely
B) a competitor's Web site (say, going to BarnesandNoble.com when you thought you were going to Amazon.com)
C) the phishing perpetrator's Web site
D) A Web site that is being targeted by a denial-of-service attack

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
46
Computers that have been "hijacked" and used to help a DDoS attack are known as ____.
A) droids
B) reluctants
C) phish
D) zombies
A) droids
B) reluctants
C) phish
D) zombies

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
47
According to the text, any act or object that endangers an asset is known as a(n) ____.
A) challenge
B) threat
C) opportunity
D) virus
A) challenge
B) threat
C) opportunity
D) virus

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
48
Referring to the figure above, the process of downloading a Web bug can identify ____.
A) your IP address
B) the Web site you last visited
C) information about your use of the site
D) all of the above
A) your IP address
B) the Web site you last visited
C) information about your use of the site
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
49
A ____ is a technologically skilled person who uses his or her skills to obtain unauthorized entry into computers.
A) zombie
B) cracker
C) script kiddie
D) whacker
A) zombie
B) cracker
C) script kiddie
D) whacker

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
50
A(n) ____ attack occurs when an attacker disrupts normal computer processing or denies processing entirely.
A) necessity
B) integrity
C) secrecy
D) man-in-the-middle
A) necessity
B) integrity
C) secrecy
D) man-in-the-middle

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
51
Unencrypted information is called ____.
A) plain text
B) a private key
C) cipher text
D) cryptography
A) plain text
B) a private key
C) cipher text
D) cryptography

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
52
Another term for a zombie is a(n) ____.
A) drone
B) bot
C) vampire
D) droid
A) drone
B) bot
C) vampire
D) droid

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
53
____ is a process that hides encrypted messages within different types of files.
A) Stegography
B) Stenography
C) Steganography
D) Stenagography
A) Stegography
B) Stenography
C) Steganography
D) Stenagography

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
54
A(n) ____ threat permits unauthorized data disclosure.
A) secrecy
B) integrity
C) necessity
D) none of the above
A) secrecy
B) integrity
C) necessity
D) none of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
55
A ____-bit key is considered a(n) ____ key.
A) 256, impervious
B) 128, weak
C) 128, strong
D) 64, strong
A) 256, impervious
B) 128, weak
C) 128, strong
D) 64, strong

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
56
A(n) ____ attack involves phony email messages that include links to spoofed Web sites.
A) DoS
B) DDoS
C) man-in-the-middle
D) phishing
A) DoS
B) DDoS
C) man-in-the-middle
D) phishing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
57
Email programs alert users when a link in an email message opens a Web page that is coded to a different ____ than the one displayed in the message.
A) sender name
B) URL
C) category of Web site
D) date
A) sender name
B) URL
C) category of Web site
D) date

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
58
____ encryption uses a single key that both the sender and receiver know.
A) Private-key
B) Public-key
C) Asymmetric
D) Man-in-the-Middle
A) Private-key
B) Public-key
C) Asymmetric
D) Man-in-the-Middle

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
59
APWG stands for ____ Working Group.
A) All-Protocol
B) Anti-Phishing
C) Autoplay
D) Auxiliary Port
A) All-Protocol
B) Anti-Phishing
C) Autoplay
D) Auxiliary Port

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
60
A digital ____ is a pattern containing copyright information that is inserted into a digital image, animation, or audio or video file.
A) Web bug
B) worm
C) watermark
D) stenograph
A) Web bug
B) worm
C) watermark
D) stenograph

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
61
A Web bug can ____.
A) identify your IP address
B) identify the last Web site you visited
C) both a. and b.
D) neither a. nor b.
A) identify your IP address
B) identify the last Web site you visited
C) both a. and b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
62
In the text, the term "applet" is associated with ____.
A) ActiveX
B) JavaScript
C) the Java programming language
D) none of the above
A) ActiveX
B) JavaScript
C) the Java programming language
D) none of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
63
The text recommended purchasing identity theft ____, which can help pay the expenses required to clear and restore your identity in case of a theft.
A) insurance
B) security
C) tracking
D) vaults
A) insurance
B) security
C) tracking
D) vaults

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
64
If you believe that your computer is involved in a DoS attack, you should contact your ____ immediately.
A) network administrator
B) ISP
C) either a. or b.
D) neither a. nor b.
A) network administrator
B) ISP
C) either a. or b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
65
Virtual ports use numbers to isolate traffic by type; a computer has more than ____ virtual ports for different processes.
A) 650
B) 6,500
C) 65,000
D) 650,000
A) 650
B) 6,500
C) 65,000
D) 650,000

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
66
The Ad-Aware ad blocker was created by ____.
A) Java
B) McAfee
C) Microsoft
D) Lavasoft
A) Java
B) McAfee
C) Microsoft
D) Lavasoft

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
67
____ is a general category of software that includes advertisements to pay for the product for which it appears.
A) Adware
B) Spyware
C) Web bug-ware
D) Abandonware
A) Adware
B) Spyware
C) Web bug-ware
D) Abandonware

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
68
By setting your Internet security program or other program, such as ____, to remove cookies on a regular basis, you can eliminate cookies that store user data from your computer.
A) Spy-Kids
B) Ad-Aware
C) Bug-Aware
D) Cookie-Kids
A) Spy-Kids
B) Ad-Aware
C) Bug-Aware
D) Cookie-Kids

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
69
A(n) ____ is a self-replicating program usually hidden within another file and sent as an email attachment.
A) virus
B) Trojan horse
C) phish
D) worm
A) virus
B) Trojan horse
C) phish
D) worm

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
70
If you believe you are a victim of identity theft, you must act quickly to contact the ____ credit reporting agencies, every financial institution at which you have an account, and the issuer of every credit card you hold.
A) two
B) three
C) four
D) five
A) two
B) three
C) four
D) five

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
71
A Web bug is an example of spyware because ____.
A) it is small and unobtrusive
B) it involves the use and manipulation of cookies
C) the clear GIF and its actions are hidden from the user
D) the user is made explicitly aware of its presence and function
A) it is small and unobtrusive
B) it involves the use and manipulation of cookies
C) the clear GIF and its actions are hidden from the user
D) the user is made explicitly aware of its presence and function

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
72
DoubleClick is a division of ____.
A) Microsoft
B) Mozilla
C) Java
D) Google
A) Microsoft
B) Mozilla
C) Java
D) Google

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
73
All of the following are listed in the text as ways to avoid identity theft EXCEPT ____.
A) matching credit card receipts to monthly statements
B) keeping credit card, bank account, and investment account information together in a safe place
C) canceling and reopening credit card accounts once every three months
D) shredding all mail that contains any personal information
A) matching credit card receipts to monthly statements
B) keeping credit card, bank account, and investment account information together in a safe place
C) canceling and reopening credit card accounts once every three months
D) shredding all mail that contains any personal information

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
74
A(n) ____ is a small, hidden graphic on a Web page, designed to work in conjunction with a cookie to obtain information about the person viewing the page.
A) biscuit
B) Web bug
C) applet
D) no-see-um
A) biscuit
B) Web bug
C) applet
D) no-see-um

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
75
When a digital signature authenticates an ActiveX control's developer or source, it is called a(n) ____ ActiveX control.
A) safe
B) logical
C) signed
D) encrypted
A) safe
B) logical
C) signed
D) encrypted

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
76
A Java ____ is a program written in the Java programming language, could execute and consume a computer's resources.
A) apple
B) applet
C) cookie
D) widget
A) apple
B) applet
C) cookie
D) widget

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
77
Firewalls can be used on Web ____.
A) servers
B) clients
C) either a. or b.
D) neither a. nor b.
A) servers
B) clients
C) either a. or b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
78
____ components can make a Web page more useful by providing interactive elements like shipping calculators or mortgage payment tables.
A) Active content
B) Static
C) Clickstream
D) Graphic
A) Active content
B) Static
C) Clickstream
D) Graphic

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
79
If you are the victim of identity theft, file a police report with ____ law enforcement to document the theft, and keep a copy of the report.
A) local
B) UN
C) Internet
D) national
A) local
B) UN
C) Internet
D) national

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
80
The term "Web bug" is most associated with the term "____."
A) phishing
B) cookie
C) active content
D) adware
A) phishing
B) cookie
C) active content
D) adware

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck


