Exam 6: CompTIA CySA+ Certification Exam (CS0-002)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/294
Play
Full screen (f)
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)
1
A company wants to take advantage of cloud benefits while retaining control of and maintaining compliance with all its security policy obligations. Based on the non-functional requirements, which of the following should the company use?
A) Hybrid cloud, as use is restricted to trusted customers
B) IaaS, as the cloud provider has a minimal level of security responsibility
C) PaaS, as the cloud customer has the most security responsibility
D) SaaS, as the cloud provider has less security responsibility
A) Hybrid cloud, as use is restricted to trusted customers
B) IaaS, as the cloud provider has a minimal level of security responsibility
C) PaaS, as the cloud customer has the most security responsibility
D) SaaS, as the cloud provider has less security responsibility
IaaS, as the cloud provider has a minimal level of security responsibility
2
A business is demanding faster IT services turnaround from its IT groups. The current lead time between request and delivery is three weeks for a task that would take a competitor two days. An architect is asked to develop a solution to reduce the lead time of the request while ensuring adherence to the company policies. Which of the following is the BEST approach to achieve the stated objective?
A) Document the desired state, complete a root cause analysis, and execute the flow.
B) Revise the schedule, implement a waterfall methodology, and flatten the network.
C) Identify deficiencies, optimize change management, and automate the workflow.
D) Follow the company policies, execute the flow, and document results.
A) Document the desired state, complete a root cause analysis, and execute the flow.
B) Revise the schedule, implement a waterfall methodology, and flatten the network.
C) Identify deficiencies, optimize change management, and automate the workflow.
D) Follow the company policies, execute the flow, and document results.
Document the desired state, complete a root cause analysis, and execute the flow.
3
Which of the following is the BEST way to ensure accounts in a cloud environment are disabled as soon as they no longer need to be active?
A) Have the user contact the cloud systems administrator to disable the account when it is no longer needed.
B) When users leave the company, ensure an account disablement request is initiated and will be fulfilled in less than four hours.
C) Have accounts checked by the cloud systems administrator once per day to ensure active accounts are still valid.
D) Reboot directory services servers once a day to ensure all account disablement requests are committed.
A) Have the user contact the cloud systems administrator to disable the account when it is no longer needed.
B) When users leave the company, ensure an account disablement request is initiated and will be fulfilled in less than four hours.
C) Have accounts checked by the cloud systems administrator once per day to ensure active accounts are still valid.
D) Reboot directory services servers once a day to ensure all account disablement requests are committed.
Have the user contact the cloud systems administrator to disable the account when it is no longer needed.
4
A cloud engineer is using a hosted service for aggregating the logs for all the servers in a public cloud environment. Each server is configured via syslog to send its logs to a central location. A new version of the application was recently deployed, and the SaaS server now stops processing logs at noon each day. In reviewing the system logs, the engineer notices the size of the logs has increased by 50% each day. Which of the following is the MOST likely reason the logs are not being published after noon?
A) The logging directory does not have sufficient storage space.
B) The syslog service is not running on the servers.
C) The data limit has been exceeded at the SaaS provider.
D) There is a cloud service provider outage.
A) The logging directory does not have sufficient storage space.
B) The syslog service is not running on the servers.
C) The data limit has been exceeded at the SaaS provider.
D) There is a cloud service provider outage.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
5
A customer wants a cloud systems administrator to adjust the backup schedule after month-end to ensure the data can be restored as fast as possible while minimizing the time needed to perform the backup. Which of the following backup types should be scheduled?
A) Synthetic full
B) Incremental
C) Differential
D) Full
A) Synthetic full
B) Incremental
C) Differential
D) Full

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
6
A system's application servers need to be patched. The requirements for maintenance work are as follows: System downtime is not allowed. The application server in use must be in the sane patch status. System performance must be maintained during patching work. Testing after patching must be done before the application server is in use. If any trouble occurs, recover the previous version in ten minutes. Which of the following methodologies should be selected?
A) Rolling update
B) Patching directly
C) Blue-green deployment
D) Three staging environments
A) Rolling update
B) Patching directly
C) Blue-green deployment
D) Three staging environments

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
7
A company wants to leverage a SaaS provider for its back-office services, and security is paramount. Which of the following solutions should a cloud engineer deploy to BEST meet the security requirements?
A) Firewall
B) IPS/IDS
C) Proxy gateway
D) CASB
A) Firewall
B) IPS/IDS
C) Proxy gateway
D) CASB

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
8
A new SaaS timecard application that is being tested will be used by all employees at a large corporation. The following process was used to test the application: 1. Three users from each site used the application for three weeks. 2. The new application was used side by side with the existing application. 3. The outputs of the old and new applications were compared side by side. Which of the following requirements did the testing plan confirm? (Select two.)
A) High availability
B) Performance
C) Connectivity
D) Data integrity
E) Sizing
F) Security
A) High availability
B) Performance
C) Connectivity
D) Data integrity
E) Sizing
F) Security

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
9
A technician receives a report of system utilization: 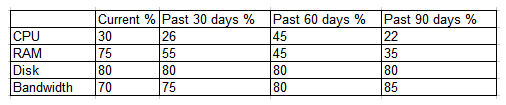 Which of the following additional resources should the technician add FIRST given the trend data shown above?
Which of the following additional resources should the technician add FIRST given the trend data shown above?
A) CPU
B) Disk
C) Bandwidth
D) RAM
 Which of the following additional resources should the technician add FIRST given the trend data shown above?
Which of the following additional resources should the technician add FIRST given the trend data shown above?A) CPU
B) Disk
C) Bandwidth
D) RAM

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
10
A company purchased a SaaS CRM application. The signed SLA meets year-round performance requirements. Three months after deployment, customers start reporting a slow application response time. System availability, connectivity, and proper functionality still meet the SLA. Which of the following is MOST likely the reason for the poor response time?
A) Incorrect business requirements are invalidating the testing results.
B) Bandwidth restrictions are causing poor performance.
C) The application version is causing compatibility issues.
D) Inadequate documentation is affecting the user interface.
A) Incorrect business requirements are invalidating the testing results.
B) Bandwidth restrictions are causing poor performance.
C) The application version is causing compatibility issues.
D) Inadequate documentation is affecting the user interface.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
11
A cloud administrator is looking at business requirements that specify the data available at the disaster recovery site must not be more than 24 hours old. Which of the following metrics correctly relates to these requirements?
A) RTO
B) MTBF
C) MTTR
D) RPO
A) RTO
B) MTBF
C) MTTR
D) RPO

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
12
A storage administrator must choose the best replication methodology for storage. The datacenters are on opposite sides of the country. The RPO is 24 hours. Replication and customer access use the same connections. Replication should not impact customer access during the day. Which of the following solutions would BEST meet these requirements?
A) Asynchronous
B) Regional
C) Multiregional
D) Synchronous
A) Asynchronous
B) Regional
C) Multiregional
D) Synchronous

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
13
Before doing a change on a VM, a systems administrator wants to ensure there is an easy and fast way to rollback if needed. The change and testing should take approximately two hours. Which of the following is the EASIEST way to meet this requirement?
A) Create a snapshot on the hypervisor.
B) Make an on-demand, incremental backup to a VTL.
C) Make an on-demand, full backup to a secondary location.
D) Create a snapshot on a remote storage array.
A) Create a snapshot on the hypervisor.
B) Make an on-demand, incremental backup to a VTL.
C) Make an on-demand, full backup to a secondary location.
D) Create a snapshot on a remote storage array.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
14
A company has deployed a four-node cluster in a COLO environment with server configurations listed below. The company wants to ensure there is 50% overhead for failover and redundancy. There are currently eight VMs running within the cluster with four vCPUs x32GB each. The company wants to better utilize its resources within the cluster without compromising failover and redundancy. 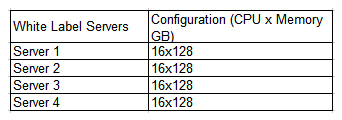 Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?
Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?
A) Ensure hyperthreading is being utilized with physical server CPUs.
B) Ensure dynamic resource allocation is being utilized.
C) Overcommit memory, and the systems will allocate resources as required.
D) Set hard limits for VM resources and turn on hyperthreading.
 Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?
Given the information above, which of the following should a cloud administrator do to BEST accommodate failover and redundancy requirements?A) Ensure hyperthreading is being utilized with physical server CPUs.
B) Ensure dynamic resource allocation is being utilized.
C) Overcommit memory, and the systems will allocate resources as required.
D) Set hard limits for VM resources and turn on hyperthreading.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
15
A cloud architect created a new delivery controller for a large VM farm to scale up according to organizational needs. The old and new delivery controllers now form a cluster. However, the new delivery controller returns an error when entering the license code. Which of the following is the MOST likely cause?
A) A firewall is blocking the port on the license server.
B) The existing license is for a lower version.
C) The existing license is not supported for clusters.
D) The existing license has expired.
A) A firewall is blocking the port on the license server.
B) The existing license is for a lower version.
C) The existing license is not supported for clusters.
D) The existing license has expired.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
16
When designing a new private cloud platform, a cloud engineer wants to make sure the new hypervisor can be configured as fast as possible by cloning the OS from the other hypervisor. The engineer does not want to use local drives for the hypervisors. Which of the following storage types would BEST suit the engineer's needs?
A) CAS
B) NAS
C) DAS
D) SAN
A) CAS
B) NAS
C) DAS
D) SAN

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
17
A courier company has virtualized its packing software application. The CSA needs to confirm the deployment is utilizing the correct amount of CPU per virtual instance. After confirming the deployment requirements, the CSA should log into the cloud services portal to ensure that:
A) the VMs with the most CPU cores available have been selected.
B) smaller VMs are being selected to reduce the total deployment cost.
C) the deployment is utilizing the recommended amount of CPUs per VM.
D) the alarms on CPU utilization have been enabled.
A) the VMs with the most CPU cores available have been selected.
B) smaller VMs are being selected to reduce the total deployment cost.
C) the deployment is utilizing the recommended amount of CPUs per VM.
D) the alarms on CPU utilization have been enabled.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
18
A cloud implementation engineer successfully created a new VM. However, the engineer notices the new VM is not accessible from another network. A ping test works from another VM on the same subnet. Which of the following is the MOST likely problem?
A) Incorrect subnet
B) Incorrect host IP address
C) Incorrect VLAN
D) Incorrect gateway
A) Incorrect subnet
B) Incorrect host IP address
C) Incorrect VLAN
D) Incorrect gateway

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
19
A new browser version has been deployed to all users at a company. After the deployment, users report that they can no longer access the company's secure time-card system, which is hosted by a SaaS provider. A technician investigates and discovers a security error is received upon opening the site. If the browser is rolled back to the older version, the site is accessible again. Which of the following is the MOST likely cause of the security error users are seeing?
A) SSL certificate expiration on the SaaS load balancers
B) Federation issues between the SaaS provider and the company
C) Obsolete security technologies implemented on the SaaS servers
D) Unencrypted communications between the users and the application
A) SSL certificate expiration on the SaaS load balancers
B) Federation issues between the SaaS provider and the company
C) Obsolete security technologies implemented on the SaaS servers
D) Unencrypted communications between the users and the application

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
20
A new application with availability SLA requirements of 99.99% has been deployed in a cloud. For a test spanning a month, which of the following unavailability times would mean the test was successful? (Select TWO).
A) 1 minute
B) 4 minutes
C) 10 minutes
D) 30 minutes
E) 60 minutes
A) 1 minute
B) 4 minutes
C) 10 minutes
D) 30 minutes
E) 60 minutes

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
21
A private cloud customer is considering using the public cloud to accommodate the peak utilization workload. Which of the following would be considered the ideal scaling solution?
A) Cloud bursting
B) Load balancing
C) Horizontal scaling
D) Vertical scaling
A) Cloud bursting
B) Load balancing
C) Horizontal scaling
D) Vertical scaling

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
22
A company security policy mandates education and training for new employees. The policy must outline acceptable use policies for SaaS applications. Given these requirements, which of the following security controls is BEST suited?
A) Preventive
B) Detective
C) Corrective
D) Physical
A) Preventive
B) Detective
C) Corrective
D) Physical

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
23
After deploying new VMs, the systems administrator notices it is not possible to connect to them using network credentials; however, local accounts work. After logging in, the administrator notices the NTP servers are not set. Which of the following is MOST likely causing this issue?
A) Directory services requires the use of NTP servers.
B) The VMs are insufficiently licensed.
C) There is a directory services outage.
D) There is a time synchronization issue.
A) Directory services requires the use of NTP servers.
B) The VMs are insufficiently licensed.
C) There is a directory services outage.
D) There is a time synchronization issue.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
24
After deploying multiple copies of database servers, data scrambling is started on them to anonymize user data. A few minutes later, the systems administrator receives multiple complaints regarding the performance of other VMs. CPU and memory have been eliminated as possible bottlenecks. Which of the following should be verified NEXT as a possible bottleneck?
A) Storage array
B) Database drivers
C) Hardware load balancer
D) Internet connection speed
A) Storage array
B) Database drivers
C) Hardware load balancer
D) Internet connection speed

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
25
A new private cloud platform is being deployed by an engineer. SLA requirements state that any clusters should have a baseline redundancy sufficient to handle the failure of at least two hosts. The engineer records the following metrics after the deployment: 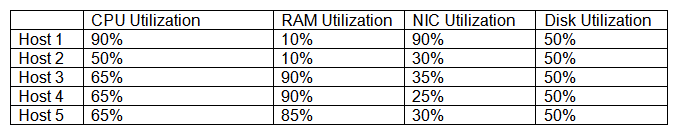 Which of the following metrics is MOST likely to represent a violation of SLA?
Which of the following metrics is MOST likely to represent a violation of SLA?
A) RAM utilization
B) NIC utilization
C) CPU utilization
D) Disk utilization
 Which of the following metrics is MOST likely to represent a violation of SLA?
Which of the following metrics is MOST likely to represent a violation of SLA?A) RAM utilization
B) NIC utilization
C) CPU utilization
D) Disk utilization

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
26
A cloud service administrator is consuming PaaS services and is performing baseline configuration tests. Which of the following is part of the PaaS consumer's responsibility with respect to the baseline confirmation tests?
A) Application versions
B) CPU utilization
C) RAM utilization
D) Operating system versions
A) Application versions
B) CPU utilization
C) RAM utilization
D) Operating system versions

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
27
A cloud administrator is tasked with ensuring redundancy and high availability of an IaaS cloud platform environment. The administrator is given the following requirements: Two web servers must share the same configurations and service client connections evenly. Two database servers must share data and configurations, with only one being used at a time. Given the above, which of the following should the administrator propose to BEST meet these requirements? (Select TWO).
A) The web server should be configured with a round-robin DNS with a CNAME record.
B) The web server should be configured with a load balancer with a virtual IP address.
C) The database server should be configured as an active-active cluster.
D) The database server should be configured as an active-passive cluster.
E) The availability aspect of the request does not currently exist in the IaaS cloud platform.
F) The redundancy aspect of the request does not currently exist in the IaaS cloud platform.
A) The web server should be configured with a round-robin DNS with a CNAME record.
B) The web server should be configured with a load balancer with a virtual IP address.
C) The database server should be configured as an active-active cluster.
D) The database server should be configured as an active-passive cluster.
E) The availability aspect of the request does not currently exist in the IaaS cloud platform.
F) The redundancy aspect of the request does not currently exist in the IaaS cloud platform.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
28
A cloud administrator is managing two private cloud environments. In cloud A, the disaster recovery solution has an SLA for RPO of five minutes and RTO of one hour. In cloud B, the disaster recovery solution has an SLA for RPO of one hour and RTO of 24 hours. A new customer's application requires that, in case of a disaster, no more than 15 minutes of data can be lost, and it should be fully recovered within one day. Which of the following would be the BEST approach to this application?
A) Tell the customer cloud A is the best solution
B) Put it in cloud B and ask the customer to create snapshots every 15 minutes
C) Both cloud A and cloud B would suit the customer's needs
D) Change the cloud B disaster recovery solution so RPO will be 15 minutes
A) Tell the customer cloud A is the best solution
B) Put it in cloud B and ask the customer to create snapshots every 15 minutes
C) Both cloud A and cloud B would suit the customer's needs
D) Change the cloud B disaster recovery solution so RPO will be 15 minutes

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
29
A cloud service provider wants to offer hardened virtual server images for provisioning purposes. This will enable users to use only the operating system services that are allowed by the provider. Which of the following tasks are MOST appropriate for the hardening process? (Select TWO).
A) Disable automatic updates.
B) Disable the command prompt.
C) Disable unneeded ports and services.
D) Disable the local administrator account.
E) Disable the remote desktop connection.
F) Disable complex passwords.
A) Disable automatic updates.
B) Disable the command prompt.
C) Disable unneeded ports and services.
D) Disable the local administrator account.
E) Disable the remote desktop connection.
F) Disable complex passwords.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
30
A public cloud provider recently updated one of its services to provide a new type of application load balancer. The cloud administrator is tasked with building out a proof-of-concept using this new service type. The administrator sets out to update the scripts and notices the cloud provider does not list the load balancer as an available option type for deploying this service. Which of the following is the MOST likely reason?
A) The administrator can deploy the new load balancer via the cloud provider's web console.
B) The administrator needs to update the version of the CLI tool.
C) The administrator needs to write a new script function to call this service.
D) The administrator is not using the correct cloud provider account.
A) The administrator can deploy the new load balancer via the cloud provider's web console.
B) The administrator needs to update the version of the CLI tool.
C) The administrator needs to write a new script function to call this service.
D) The administrator is not using the correct cloud provider account.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following would be appropriate when considering inbound access security for a web-based SaaS solution?
A) Antivirus/anti-malware
B) IPSec
C) Firewall
D) Obfuscation
A) Antivirus/anti-malware
B) IPSec
C) Firewall
D) Obfuscation

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
32
After scheduled network maintenance, users report that an externally hosted web application is particularly slow to load. Small items on the page load such as text documents and markup, but larger multimedia files do not load. Which of the following is the MOST likely cause of the reported issues?
A) Incorrect MTU in the network segment
B) Misconfiguration of QoS settings
C) Incorrect VLAN for the affected PCs
D) Excessive latency on the local LAN segment
A) Incorrect MTU in the network segment
B) Misconfiguration of QoS settings
C) Incorrect VLAN for the affected PCs
D) Excessive latency on the local LAN segment

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
33
During peak times, users are unable to access their online wealth management applications in a timely fashion. The online banking application resides in a community cloud environment. Which of the following explains how the cloud systems administrator should start to resolve this issue?
A) Access the cloud services portal and ensure memory ballooning is enabled.
B) Access the cloud services portal and ensure there is adequate disk space available.
C) Access the cloud services portal and ensure all users are accessing it through the same web service.
D) Access the cloud services portal and ensure the ACLs are set correctly for the user community.
A) Access the cloud services portal and ensure memory ballooning is enabled.
B) Access the cloud services portal and ensure there is adequate disk space available.
C) Access the cloud services portal and ensure all users are accessing it through the same web service.
D) Access the cloud services portal and ensure the ACLs are set correctly for the user community.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
34
Joe, a systems administrator, deployed a computer and storage for a system and took it to the application team. The next day, the application team claimed the database was slow. The deployment request, result, and current utilization data are shown below. 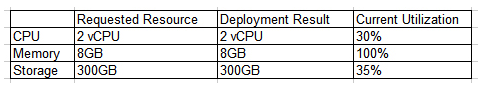 Which of the following descriptions of the situation is correct?
Which of the following descriptions of the situation is correct?
A) The deployment was done with the wrong memory configuration.
B) The deployment was unsuccessful due to the cloud failure.
C) The deployment was successful, but the capacity planning was inaccurate.
D) The deployment was done with the wrong storage parameter.
 Which of the following descriptions of the situation is correct?
Which of the following descriptions of the situation is correct?A) The deployment was done with the wrong memory configuration.
B) The deployment was unsuccessful due to the cloud failure.
C) The deployment was successful, but the capacity planning was inaccurate.
D) The deployment was done with the wrong storage parameter.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
35
A technician is configuring a new web application to be highly available. The technician has configured multiple web servers in different availability zones at a public cloud provider. The application requires users to be directed to the same server each time they visit. Which of the following network components is MOST likely to accomplish this?
A) Network firewall
B) Intrusion prevention system
C) Global load balancer
D) Virtual private network
A) Network firewall
B) Intrusion prevention system
C) Global load balancer
D) Virtual private network

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
36
An organization is replacing its internal human resources system with a SaaS-based application. The solution is multi-tenant, and the organization wants to ensure ubiquitous access while preventing password replay attacks. Which of the following would BEST help to mitigate the risk?
A) Implement destination resources authentication.
B) Require and implement two-factor authentication.
C) Remove administrator privileges from users' laptops.
D) Combine network authentication and physical security in one card/token.
A) Implement destination resources authentication.
B) Require and implement two-factor authentication.
C) Remove administrator privileges from users' laptops.
D) Combine network authentication and physical security in one card/token.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
37
A VM was deleted by mistake today at 11:05 a.m. Below are the backups currently available for the VM: 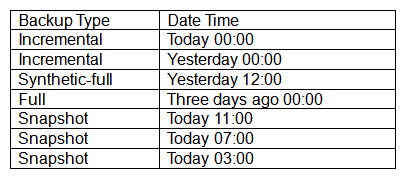 Crash-consistent restore is acceptable. Which of the following backups should be chosen?
Crash-consistent restore is acceptable. Which of the following backups should be chosen?
A) Snapshot from today at 11:00
B) Full from three days ago at 00:00
C) Incremental from today at 00:00
D) Synthetic-full from yesterday at 12:00
 Crash-consistent restore is acceptable. Which of the following backups should be chosen?
Crash-consistent restore is acceptable. Which of the following backups should be chosen?A) Snapshot from today at 11:00
B) Full from three days ago at 00:00
C) Incremental from today at 00:00
D) Synthetic-full from yesterday at 12:00

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
38
A cloud administrator is analyzing usage trends for a website housed within an IaaS cloud platform. The administrator notices that traffic and visitors to the site quadrupled from the normal baseline during the holiday season. The environment has a load balancer that uses standardized VMs to host the applications. Given this scenario, which of the following would be the MOST efficient, provide no downtime, and address the temporary spike in traffic?
A) Implement an upward vertical scaling solution.
B) Implement a downward vertical scaling solution.
C) Implement an inward horizontal scaling solution.
D) Implement an outward horizontal scaling solution.
A) Implement an upward vertical scaling solution.
B) Implement a downward vertical scaling solution.
C) Implement an inward horizontal scaling solution.
D) Implement an outward horizontal scaling solution.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
39
A cloud administrator is configuring a bastion host. The bastion host will be used to administer systems in the cloud remotely from the administrator's on-premises desktop. The administrator is given the following requirements: Ensure port 22 is open on the host and only allow the public IP of the on-premises router/firewall. Ensure port 3389 is open on the host and only allow the public IP of the on-premises router/firewall. Harden these services with PKI (where applicable). Given this scenario, which of the following should the administrator utilize to BEST address these requirements? (Select THREE).
A) RDP protocol from the desktop to the bastion host
B) Telnet protocol from the desktop to the bastion host
C) SSH protocol from the desktop to the bastion host
D) MD5 and RC4 with a signed certificate
E) RSA and AES with a signed certificate
F) Blowfish and SHA-1 with a signed certificate
G) VNC protocol from the desktop to the bastion host
A) RDP protocol from the desktop to the bastion host
B) Telnet protocol from the desktop to the bastion host
C) SSH protocol from the desktop to the bastion host
D) MD5 and RC4 with a signed certificate
E) RSA and AES with a signed certificate
F) Blowfish and SHA-1 with a signed certificate
G) VNC protocol from the desktop to the bastion host

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
40
A cloud administrator has finished building a virtual server template in a public cloud environment. The administrator is now cloning six servers from that template. Each server is configured with one private IP address and one public IP address. After starting the server instances, the cloud administrator notices that two of the servers do not have a public IP address. Which of the following is the MOST likely cause?
A) The maximum number of public IP addresses has already been reached.
B) The two servers are not attached to the correct public subnet.
C) There is no Internet gateway configured in the cloud environment.
D) The two servers do not have enough virtual network adapters attached.
A) The maximum number of public IP addresses has already been reached.
B) The two servers are not attached to the correct public subnet.
C) There is no Internet gateway configured in the cloud environment.
D) The two servers do not have enough virtual network adapters attached.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
41
A consultant is helping a gaming-as-a-service company set up a new cloud. The company recently bought several graphic card that need to be added to the servers. Which of the following should the consultant suggest as the MOST cost effective?
A) Private
B) Public
C) Community
D) SaaS
A) Private
B) Public
C) Community
D) SaaS

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
42
A CSA needs to bring a client's public cloud site online at another location in the same region after a disaster. The RPO is eight hours, and the RTO is four hours. Which of the following is the BEST way to accomplish this goal?
A) Restore the site at the new location within six hours by using backups from the failed public cloud site from eight hours earlier. Switch users from the failed site to the online regional public cloud site.
B) Restore the site at the new location within two hours by using backups from the failed public cloud site from two hours earlier. Switch users from the failed site to the online regional public cloud site.
C) Restore the site at the new location within eight hours by using backups from the failed public cloud site from six hours earlier. Switch users from the failed site to the online regional public cloud site.
D) Restore the site at the new location within four and half hours by using backups from the failed public cloud site from a half hour earlier. Switch users from the failed site to the online regional public cloud site.
A) Restore the site at the new location within six hours by using backups from the failed public cloud site from eight hours earlier. Switch users from the failed site to the online regional public cloud site.
B) Restore the site at the new location within two hours by using backups from the failed public cloud site from two hours earlier. Switch users from the failed site to the online regional public cloud site.
C) Restore the site at the new location within eight hours by using backups from the failed public cloud site from six hours earlier. Switch users from the failed site to the online regional public cloud site.
D) Restore the site at the new location within four and half hours by using backups from the failed public cloud site from a half hour earlier. Switch users from the failed site to the online regional public cloud site.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
43
A cloud administrator is given a requirement to maintain a copy of all system logs for seven years. All servers are deployed in a public cloud provider's environment. Which of the following is the MOST cost-efficient solution for retaining these logs?
A) Create a long-term storage repository at the cloud provider. Have all logs copied to the cloud storage device.
B) Schedule a nightly job on each server to archive all logs. Copy them to a compressed drive on the server.
C) Configure SMTP services on each server and schedule a nightly job to email the logs to the cloud administrator team's email account.
D) Configure a nightly job on each server to copy all logs to a single server. Schedule a job on the server to archive those logs into a compressed drive.
A) Create a long-term storage repository at the cloud provider. Have all logs copied to the cloud storage device.
B) Schedule a nightly job on each server to archive all logs. Copy them to a compressed drive on the server.
C) Configure SMTP services on each server and schedule a nightly job to email the logs to the cloud administrator team's email account.
D) Configure a nightly job on each server to copy all logs to a single server. Schedule a job on the server to archive those logs into a compressed drive.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
44
A cloud administrator has configured a connection between two virtual private cloud environments at a public cloud provider that are each in different accounts. The administrator has configured the accounts correctly so they can connect to each other's resources. Both cloud environments have policies that allow anyone from 0.0.0.0/0 on TCP port 22. The following table shows the network configuration information: 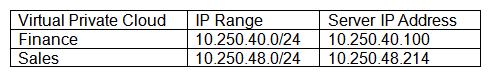 However, the administrator is unable to establish an SSH connection from a server in 10.250.40.100 to 10.250.48.214. Which of the following is the MOST likely issue?
However, the administrator is unable to establish an SSH connection from a server in 10.250.40.100 to 10.250.48.214. Which of the following is the MOST likely issue?
A) The network ACL is not configured to allow SSH access.
B) The IP configuration on one of the servers is incorrect.
C) The administrator does not have sufficient credentials.
D) The routing tables have not been updated correctly.
 However, the administrator is unable to establish an SSH connection from a server in 10.250.40.100 to 10.250.48.214. Which of the following is the MOST likely issue?
However, the administrator is unable to establish an SSH connection from a server in 10.250.40.100 to 10.250.48.214. Which of the following is the MOST likely issue?A) The network ACL is not configured to allow SSH access.
B) The IP configuration on one of the servers is incorrect.
C) The administrator does not have sufficient credentials.
D) The routing tables have not been updated correctly.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
45
A cloud provider is increasingly discovering hard-to-find issues within the growing infrastructure. The provider has all the basic necessary tools implemented to collect and store data regarding the environment. To allow the cloud provider to focus on relevant events, which of the following is the MOST appropriate technique to build intelligence?
A) Event correlation
B) Event collection
C) Event alerts
D) Event-based workflows
A) Event correlation
B) Event collection
C) Event alerts
D) Event-based workflows

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
46
A cloud provider wants to automate the installation of standard applications and services as part of the PaaS environment. The provider generates scripts for installation and configuration, taking into account the values provided by the users as input. The scripts need to be run automatically as part of the provisioning process and reused later for other purposes. Which of the following would help the provider do this?
A) Provisioning
B) Orchestration
C) Self-service portal
D) Baselines
A) Provisioning
B) Orchestration
C) Self-service portal
D) Baselines

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
47
IaaS users are reporting longer than expected wait times when accessing the virtual file repository. There are more than 2TB of free disk space, and vCPU and vRAM do not reach more than 75% utilization. In which of the following ways should the cloud systems administrator analyze this issue?
A) Access the cloud services portal and increase the amount of available disk space by 25%.
B) Access the cloud services portal and check the amount of CPU and RAM on the host machine.
C) Access the cloud services portal and look at the historical performance numbers.
D) Access the cloud services portal and check the security log for access denied requests.
A) Access the cloud services portal and increase the amount of available disk space by 25%.
B) Access the cloud services portal and check the amount of CPU and RAM on the host machine.
C) Access the cloud services portal and look at the historical performance numbers.
D) Access the cloud services portal and check the security log for access denied requests.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
48
A hospital is leveraging a third-party-hosted, SaaS-based EMRS for all its regional locations. The EMRS will consolidate all existent stand-alone regional systems. All regional systems managers are concerned about the new system availability. Which of the following should the new EMRS architect do to address the manager's concerns?
A) Analyze business requirements and design the new EMRS to run the most popular IaaS provider that meets the health industry's needs.
B) Analyze and communicate to regional managers that dual service providers will be used at all regional locations.
C) Analyze business requirements, and design and deploy client-to-site VPN for all regional hospital staff with two-factor authentication or a client certificate.
D) Analyze business requirements and deploy the SaaS EMRS within the hospital's headquarters and create a client-to-site VPN from each region.
A) Analyze business requirements and design the new EMRS to run the most popular IaaS provider that meets the health industry's needs.
B) Analyze and communicate to regional managers that dual service providers will be used at all regional locations.
C) Analyze business requirements, and design and deploy client-to-site VPN for all regional hospital staff with two-factor authentication or a client certificate.
D) Analyze business requirements and deploy the SaaS EMRS within the hospital's headquarters and create a client-to-site VPN from each region.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
49
A cloud administrator wants to apply patches in an isolated copy of the production virtual server to assess the impact. Which of the following activities would BEST achieve this objective?
A) Clustering
B) Snapshot
C) Image backup
D) Cloning
A) Clustering
B) Snapshot
C) Image backup
D) Cloning

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
50
As part of a nightly testing process, new version of an application is deployed to the set of web servers in the development environment. Which of the following is the BEST way to ensure the test environment is consistent with the previous night's test?
A) Clone the development web servers to the test environment.
B) Reprovision the web servers using predefined templates.
C) Undeploy the previous application and deploy the new version.
D) Revert to a previous state using configuration management tools.
A) Clone the development web servers to the test environment.
B) Reprovision the web servers using predefined templates.
C) Undeploy the previous application and deploy the new version.
D) Revert to a previous state using configuration management tools.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
51
A tenant has provisioned a new database server. It needs to add the database files in the exclusion list for security scanning, as it allows down the performance and locks the database file. Which of the following solutions must have this exclusion?
A) IPS
B) IDS
C) Antivirus
D) Firewall
A) IPS
B) IDS
C) Antivirus
D) Firewall

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
52
A company needs to meet the security requirements for PII. Which of the following cloud service models allows the company to have the MOST control to meet the security requirements?
A) SaaS
B) IaaS
C) PaaS
D) XaaS
A) SaaS
B) IaaS
C) PaaS
D) XaaS

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
53
An entertainment company with a very large movie library is moving all of its production systems to an IaaS cloud. The current lease is expiring in the next month, and the company made a last-minute decision not to renew the lease. Which of the following would be the MOST effective way to move all the data to the new cloud provider?
A) Perform an offline storage migration.
B) Perform an online storage migration.
C) Perform an offline VM migration.
D) Perform an online VM migration.
A) Perform an offline storage migration.
B) Perform an online storage migration.
C) Perform an offline VM migration.
D) Perform an online VM migration.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
54
The following three hosts are being put into a virtualization cluster for a new project initiative: 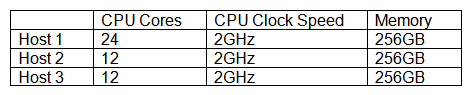 As more VMs are deployed to the cluster, which of the following virtualization technologies is MOST likely to report an error with this configuration?
As more VMs are deployed to the cluster, which of the following virtualization technologies is MOST likely to report an error with this configuration?
A) High availability
B) Ballooning
C) Memory overcommitment
D) Hyperthreading
 As more VMs are deployed to the cluster, which of the following virtualization technologies is MOST likely to report an error with this configuration?
As more VMs are deployed to the cluster, which of the following virtualization technologies is MOST likely to report an error with this configuration?A) High availability
B) Ballooning
C) Memory overcommitment
D) Hyperthreading

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
55
The CASB report indicates several unsanctioned SaaS applications are being used in an organization. Which of the following is the MOST likely cause?
A) VPN bypass
B) Shadow IT
C) Web proxy bypass
D) CAB approval
A) VPN bypass
B) Shadow IT
C) Web proxy bypass
D) CAB approval

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
56
A company uses SaaS and IaaS solutions from multiple cloud providers. Users report that this requires them to manage and remember multiple user accounts and passwords. Which of the following solutions should be implemented to fix this issue?
A) SSO
B) Federation
C) Password synchronization
D) Lowered password complexity
E) Multifactor authentication
A) SSO
B) Federation
C) Password synchronization
D) Lowered password complexity
E) Multifactor authentication

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
57
A company is deploying a new instant messaging app to allow for communications with external vendors. Each entity will host its own version of the application, but users must be able to talk between the companies. Which of the following security techniques would MOST likely be used to allow this to happen?
A) User synchronization
B) Password synchronization
C) Public federation
D) Multifactor authentication
A) User synchronization
B) Password synchronization
C) Public federation
D) Multifactor authentication

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
58
A company has been migrating a significant number of its on-premises applications to various SaaS providers. The IT department has noticed the following: User account management has become challenging. User account compromises have increased. Accessing various SaaS applications is challenging. Which of the following should the IT security department implement to BEST resolve the issue? (Select THREE).
A) Single sign-on
B) Multifactor authentication
C) Network intrusion prevention system
D) Password synchronization
E) Federation
F) IPSec tunnel to the SaaS providers
G) VPN to SaaS providers
A) Single sign-on
B) Multifactor authentication
C) Network intrusion prevention system
D) Password synchronization
E) Federation
F) IPSec tunnel to the SaaS providers
G) VPN to SaaS providers

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
59
Ann, a technician, is using a saved workflow to deploy virtual servers. The script worked yesterday but is now returning an authentication error. Ann confirms that she can manually log in with her own account and create a virtual server. Which of the following is MOST likely causing the error?
A) Certificate misconfiguration
B) Account expiration
C) Federation issues
D) Encryption issues
A) Certificate misconfiguration
B) Account expiration
C) Federation issues
D) Encryption issues

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
60
A Type 1 hypervisor has the following specifications: RAM 128GB CPU 4 socket quad-core Storage 16TB Each VM must have 8GB RAM, 1 vCPU, and 512GB storage. Which of the following is the MAXIMUM number of VMs that can be hosted on this hypervisor?
A) 14
B) 15
C) 31
D) 32
A) 14
B) 15
C) 31
D) 32

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
61
While reviewing the auto-scaling events for a web application, a cloud engineer identified that the application upsized and downsized multiple times within the last hour. Which of the following should the cloud engineer do NEXT?
A) Add more systems into the scaling group.
B) Review the load balancer configuration settings.
C) Review auto-scaling policies to detect a misconfiguration.
D) Monitor auto-scaling events for the next 24 hours.
A) Add more systems into the scaling group.
B) Review the load balancer configuration settings.
C) Review auto-scaling policies to detect a misconfiguration.
D) Monitor auto-scaling events for the next 24 hours.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
62
A company has implemented a dual-region (Region 1 and Region 2) cloud strategy from its current CSP. Both regions have the same data in them. Region 2 is experiencing an outage. Which of the following is the BEST way to provide service to users in Region 2 during the outage while allowing access to the data?
A) Bring the backup instances online and provide Region 2 users access to their data.
B) Add more network bandwidth to Region 2.
C) Copy Region 1 data to a location in Region 3 and have users access their data.
D) Redirect users from Region 2 to Region 1.
A) Bring the backup instances online and provide Region 2 users access to their data.
B) Add more network bandwidth to Region 2.
C) Copy Region 1 data to a location in Region 3 and have users access their data.
D) Redirect users from Region 2 to Region 1.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
63
A SaaS customer reports that no one can access the application portal. After some troubleshooting, the cloud administrator finds a problem and provides a remedy by restarting the cluster. After documenting the solution, the support case is closed. Multiple tenants lose access to their hosts the following day. Which of the following troubleshooting steps did the administrator miss?
A) Identify the problem.
B) Establish a theory.
C) Verify full system functionality.
D) Test the theory.
E) Establish a plan of action.
A) Identify the problem.
B) Establish a theory.
C) Verify full system functionality.
D) Test the theory.
E) Establish a plan of action.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
64
Ann, a cloud administrator, is reporting on how the organization has adhered to its marketing of 99.99999% system availability SLA. Given this scenario, which of the following should Ann include in her report?
A) System clock time
B) System idle percentage
C) System response time
D) System uptime
A) System clock time
B) System idle percentage
C) System response time
D) System uptime

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
65
A pharmaceutical company is migrating its systems and infrastructure to the cloud. Due to security restrictions and regulatory policies, the company Chief Executive Officer (CEO) is concerned about moving this information to the cloud. Based on the CEO's concern, which of the following should the company do First?
A) Review compliance requirements.
B) Apply defined audit/compliance requirements.
C) Review company security policies.
D) Update the security tools to systems and services.
A) Review compliance requirements.
B) Apply defined audit/compliance requirements.
C) Review company security policies.
D) Update the security tools to systems and services.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
66
A mobile subscriber is experiencing random limited-service outages. Customers report being unable to make calls or browse. The service provider management console is not showing any alarms, errors, or critical logs, but does show a large number of connection request failures. Which of the following could be the problem?
A) Misconfigured federation
B) IP address limitations
C) SSO failure
D) Unavailable directory service
A) Misconfigured federation
B) IP address limitations
C) SSO failure
D) Unavailable directory service

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
67
Asynchronous data replication for a SaaS application occurs between Regions A and B. Users in Region A are reporting that the most current data for an insurance claims application is not available to them until after 11:30 a.m. The cloud administrator for this SaaS provider checks the network utilization and finds that only about 10% of the network bandwidth is being used. Which of the following describes how the cloud administrator could BEST resolve this issue?
A) Check the storage utilization logs in both regions.
B) Check the RAM utilization logs in both regions.
C) Check the CPU utilization logs in both regions.
D) Check the storage commit logs in both regions.
A) Check the storage utilization logs in both regions.
B) Check the RAM utilization logs in both regions.
C) Check the CPU utilization logs in both regions.
D) Check the storage commit logs in both regions.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
68
A company is subcontracting part of a large project to another company. Management wants to ensure that there is a secure way for employees from both companies to share data without exposing internal information to employees at the other company. Which of the following cloud models BEST serves this purpose?
A) Hybrid
B) Public
C) Private
D) Community
A) Hybrid
B) Public
C) Private
D) Community

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
69
Given the metric below: 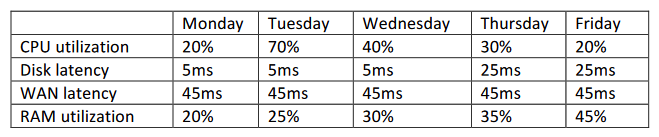 Using iSCSI storage reports across three datacenters, which of the following recorded metrics indicates an anomaly in the performance?
Using iSCSI storage reports across three datacenters, which of the following recorded metrics indicates an anomaly in the performance?
A) Disk latency
B) CPU utilization
C) WAN latency
D) RAM utilization
 Using iSCSI storage reports across three datacenters, which of the following recorded metrics indicates an anomaly in the performance?
Using iSCSI storage reports across three datacenters, which of the following recorded metrics indicates an anomaly in the performance?A) Disk latency
B) CPU utilization
C) WAN latency
D) RAM utilization

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
70
A cloud administrator has deployed a new web application to a private cloud. The application platform consists of two web servers that communicate to a redundant database back end. The traffic to the web servers is directed by a load balancer appliance. The administrator connects to the website on each of the webservers individually and confirms they are able to log in. Which of the following aspects of the application has the administrator tested successfully?
A) Connectivity
B) Failover
C) Data Integrity
D) Performance
A) Connectivity
B) Failover
C) Data Integrity
D) Performance

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
71
A cloud application development team needs to consider the following requirements to the built in as part of the application's authentication process: - Customers should have the flexibility to use their own identity stores within the authentication process. - Customers should not be asked to provide the credentials repeatedly for different applications with different permission sets. Which of the following solutions would BEST help the team achieve the above business objectives? (Choose two.)
A) Certificates
B) Single sign-on
C) One-time passwords
D) Federation
E) Multifactor authentication
F) Hardware tokens
A) Certificates
B) Single sign-on
C) One-time passwords
D) Federation
E) Multifactor authentication
F) Hardware tokens

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
72
A cloud-based web proxy is blocking key sites that a business requires for operation. After validation, the sites are legitimate, and access is required for end users to complete their work. Which of the following is the BEST solution to allow access to the sites?
A) Instruct users to bypass the cloud-based web proxy.
B) Whitelist the URLs.
C) Blacklist the URLs.
D) Create a security group for those users and enforce MFA.
A) Instruct users to bypass the cloud-based web proxy.
B) Whitelist the URLs.
C) Blacklist the URLs.
D) Create a security group for those users and enforce MFA.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
73
A company is using storage-as-a-service from an IaaS provider for application services. The company has a mandate to protect personal information being stored on the cloud. The service provided includes encryption for in-transit data and requires a security solution for data-at-rest. Which of the following should be deployed to secure the personal information?
A) Implement data tokenization.
B) Implement hardware-based encryption.
C) Implement centralized key management.
D) Implement database-embedded encryption.
A) Implement data tokenization.
B) Implement hardware-based encryption.
C) Implement centralized key management.
D) Implement database-embedded encryption.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
74
It is taking an unusually long time for a financial division to run monthly reports on its SaaS-based, multitenant application. The cloud provider has grown exponentially, and more financial industry clients have moved their processing to the SaaS provider. Which of the following is the MOST probable cause of the issue?
A) The SSL certificate used by the SaaS provider has expired and is no longer valid.
B) Some of the new tenants are not from the financial industry and are causing data integrity issues.
C) The CSP did not keep up with the growth and the appropriate supporting infrastructure.
D) The licensing limit has been exceeded on the SaaS-based, multitenant application server.
A) The SSL certificate used by the SaaS provider has expired and is no longer valid.
B) Some of the new tenants are not from the financial industry and are causing data integrity issues.
C) The CSP did not keep up with the growth and the appropriate supporting infrastructure.
D) The licensing limit has been exceeded on the SaaS-based, multitenant application server.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
75
Based on demand, an IaaS provider wants to deploy a security application for its customers. Which of the following is the BEST technique for the IaaS provider to apply this to target systems?
A) Vendor application
B) Scripting
C) Orchestration
D) Custom programming
A) Vendor application
B) Scripting
C) Orchestration
D) Custom programming

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
76
A cloud administrator needs to configure multiple web servers to participate actively in workload processing. Which of the following will BEST help the administrator achieve this goal?
A) Deploy availability group and enable autoscaling.
B) Deploy availability group and enable load balancing.
C) Deploy a reverse proxy in the DMZ.
D) Deploy an HA group and make each website public.
A) Deploy availability group and enable autoscaling.
B) Deploy availability group and enable load balancing.
C) Deploy a reverse proxy in the DMZ.
D) Deploy an HA group and make each website public.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
77
A consultant is helping a gaming-as-a-service company set up a new cloud. The company recently bought several graphic cards that need to be added to the servers. Which of the following should the consultant suggest as the MOST cost effective?
A) Private
B) Public
C) Community
D) SaaS
A) Private
B) Public
C) Community
D) SaaS

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
78
A cloud technology vendor has released an update to its product. A company providing cloud services need to quickly adopt the update to provide support to its customers. Which of the following is the MOST efficient action to complete this task?
A) Use a virtualization tool to apply patches to cloud resources.
B) Use an automatic system restart to update the cloud resources.
C) Use an orchestration tool to automate updates across cloud resources.
D) Use custom scripts to distribute the release to the cloud resources.
A) Use a virtualization tool to apply patches to cloud resources.
B) Use an automatic system restart to update the cloud resources.
C) Use an orchestration tool to automate updates across cloud resources.
D) Use custom scripts to distribute the release to the cloud resources.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
79
Government agencies currently operate their own websites, each with its own directory services. There is a mandate to minimize IT administration. Which of the following should the cloud services architect choose to BEST meet this mandate?
A) Set up a direct VPN tunnel between the government sites.
B) Upgrade all stand-alone systems to use mobile technologies.
C) Upgrade the operating systems on all of the web servers.
D) Reengineer the identification and authorization process.
A) Set up a direct VPN tunnel between the government sites.
B) Upgrade all stand-alone systems to use mobile technologies.
C) Upgrade the operating systems on all of the web servers.
D) Reengineer the identification and authorization process.

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck
80
Upon discovery several SaaS applications are being utilized by users, and the InfoSec team needs to update a configuration file on all client machines. Which of the following file types is used to redirect users through a web proxy?
A) .dat
B) .tmp
C) .log
D) .pac
A) .dat
B) .tmp
C) .log
D) .pac

Unlock Deck
Unlock for access to all 294 flashcards in this deck.
Unlock Deck
k this deck


