Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/107
Play
Full screen (f)
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004
1
A cloud systems administrator needs to migrate several corporate applications to a public cloud provider and decommission the internal hosting environment. This migration must be completed by the end of the month. Because these applications are internally developed to meet specific business accounting needs, the administrator cannot use an alternative application. Which of the following BEST describes the approach the administrator should use?
A) Hybrid deployment
B) Phased migration
C) Lift and shift
D) Rip and replace
A) Hybrid deployment
B) Phased migration
C) Lift and shift
D) Rip and replace
Lift and shift
2
A contract that defines the quality and performance metrics that are agreeable to both parties is called an:
A) SOP.
B) SOA.
C) SOW.
D) SLA.
A) SOP.
B) SOA.
C) SOW.
D) SLA.
SLA.
3
Volume, variety, velocity, and veracity are the four characteristics of:
A) machine learning.
B) Big Data.
C) microservice design.
D) blockchain.
E) object storage.
A) machine learning.
B) Big Data.
C) microservice design.
D) blockchain.
E) object storage.
Big Data.
4
A mobile application development team requires frequent software updates for a major launch of a customer-facing application. The business requirement is to be first-to-market on a new feature that leverages third-party-hosted services. Which of the following is the BEST approach to use for speed and efficiency?
A) Proprietary code solution
B) Application programming interface
C) Regression testing
D) Production load testing
A) Proprietary code solution
B) Application programming interface
C) Regression testing
D) Production load testing

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
5
An organization wants to migrate a locally hosted application to a PaaS model. The application currently runs on a 15-year-old operating system and cannot be upgraded. Which of the following should the organization perform to ensure the application will be supported in the cloud?
A) Risk register
B) Feasibility study
C) Benchmarks
D) Baseline
A) Risk register
B) Feasibility study
C) Benchmarks
D) Baseline

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
6
A business analyst is drafting a risk assessment. Which of the following components should be included in the draft? (Choose two.)
A) Asset management
B) Database type
C) Encryption algorithms
D) Certificate name
E) Asset inventory
F) Data classification
A) Asset management
B) Database type
C) Encryption algorithms
D) Certificate name
E) Asset inventory
F) Data classification

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
7
A SaaS provider specifies in a user agreement that the customer agrees that any misuse of the service will be the responsibility of the customer. Which of the following risk response methods was applied?
A) Acceptance
B) Avoidance
C) Transference
D) Mitigation
A) Acceptance
B) Avoidance
C) Transference
D) Mitigation

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
8
A developer is leveraging a public cloud service provider to provision servers using the templates created by the company's cloud engineer. Which of the following does this BEST describe?
A) Subscription services
B) Containerization
C) User self-service
D) Autonomous environments
A) Subscription services
B) Containerization
C) User self-service
D) Autonomous environments

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
9
A cloud administrator suggested using spot instances to reduce cloud costs for part of a new cloud infrastructure. Which of the following conditions must be addressed by the application that will run on these instances?
A) The application needs to store data in a database.
B) There is a restriction for distributed network communications.
C) The application needs to handle unpredictable instance termination.
D) Resource-intensive compute loads will be forbidden.
A) The application needs to store data in a database.
B) There is a restriction for distributed network communications.
C) The application needs to handle unpredictable instance termination.
D) Resource-intensive compute loads will be forbidden.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following services would restrict connectivity to cloud resources?
A) Security lists
B) Firewall
C) VPN
D) Intrusion detection system
A) Security lists
B) Firewall
C) VPN
D) Intrusion detection system

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
11
Which of the following are the main advantages of using ML/AI for data analytics in the cloud as opposed to on premises? (Choose two.)
A) Cloud providers offer enhanced technical support.
B) Elasticity allows access to a large pool of compute resources.
C) The shared responsibility model offers greater security.
D) AI enables DevOps to build applications easier and faster.
E) A pay-as-you-go approach allows the company to save money.
F) ML enables DevOps to build applications easier and faster.
A) Cloud providers offer enhanced technical support.
B) Elasticity allows access to a large pool of compute resources.
C) The shared responsibility model offers greater security.
D) AI enables DevOps to build applications easier and faster.
E) A pay-as-you-go approach allows the company to save money.
F) ML enables DevOps to build applications easier and faster.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
12
A cloud administrator for an ISP identified a vulnerability in the software that controls all the firewall rules for a geographic area. To ensure the software upgrade is properly tested, approved, and applied, which of the following processes should the administrator follow?
A) Configuration management
B) Incident management
C) Resource management
D) Change management
A) Configuration management
B) Incident management
C) Resource management
D) Change management

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
13
Which of the following models provides the SMALLEST amount of technical overhead?
A) SaaS
B) PaaS
C) MaaS
D) IaaS
A) SaaS
B) PaaS
C) MaaS
D) IaaS

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following is commonly used to forecast market trends?
A) Serverless computing
B) Data warehouse
C) Machine learning
D) Accelerated computing
A) Serverless computing
B) Data warehouse
C) Machine learning
D) Accelerated computing

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
15
A human resources department is considering a SaaS-based human resources portal and requires a risk analysis. Which of the following are requirements to consider? (Choose two.)
A) Support
B) Threats
C) Chargebacks
D) Vulnerabilities
E) Maintenance
F) Gap analysis
A) Support
B) Threats
C) Chargebacks
D) Vulnerabilities
E) Maintenance
F) Gap analysis

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
16
A project manager must inform the Chief Information Officer (CIO) of the additional resources necessary to migrate services to the cloud successfully. Which of the following cloud assessments would be MOST appropriate to use for the recommendation?
A) Feasibility study
B) Gap analysis
C) Future requirements
D) Baseline report
A) Feasibility study
B) Gap analysis
C) Future requirements
D) Baseline report

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
17
A small online retailer is looking for a solution to handle the high load on its servers during the holiday season. The retailer is not currently ready to move its IT operations completely to the cloud. Which of the following will BEST fit these requirements?
A) Elasticity
B) Scalability
C) Bursting
D) Self-service
A) Elasticity
B) Scalability
C) Bursting
D) Self-service

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
18
A company has been running tests on a newly developed algorithm to increase the responsiveness of the application. The company's monthly bills for the testing have been much higher than expected. Which of the following documents should the company examine FIRST?
A) Memory report
B) Compute report
C) Network report
D) Storage report
A) Memory report
B) Compute report
C) Network report
D) Storage report

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
19
A company is in its second year of a three-year agreement with a cloud vendor. After the initial phase of the cloud migration, resource consumption has stabilized. Which of the following would help the company reduce the cost of infrastructure?
A) Reserved instances
B) Pay-as-you-go
C) Spot instances
D) Bring your own license
A) Reserved instances
B) Pay-as-you-go
C) Spot instances
D) Bring your own license

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
20
A company is moving to the cloud and wants to enhance the provisioning of compute, storage, security, and networking. Which of the following will be leveraged?
A) Infrastructure as code
B) Infrastructure templates
C) Infrastructure orchestration
D) Infrastructure automation
A) Infrastructure as code
B) Infrastructure templates
C) Infrastructure orchestration
D) Infrastructure automation

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
21
An organization's servers are experiencing performance degradation from oversubscription of memory in the virtual environment and exhausted physical RAM. Which of the following cloud computing characteristics would BEST address the issue?
A) Availability
B) Elasticity
C) Pay-as-you-go
D) Self-service
A) Availability
B) Elasticity
C) Pay-as-you-go
D) Self-service

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
22
A small business is engaged with a cloud provider to migrate from on-premises CRM software. The contract includes fixed costs associated with the product. Which of the following variable costs must be considered?
A) Time to market
B) Operating expenditure fees
C) BYOL costs
D) Human capital
A) Time to market
B) Operating expenditure fees
C) BYOL costs
D) Human capital

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following technologies would help a game company prepare its cloud infrastructure to support a global distribution workload of a newly released online game? (Choose two.)
A) Auto-scaling
B) VDI
C) Data portability
D) CDN
E) Templates
F) Blockchain
A) Auto-scaling
B) VDI
C) Data portability
D) CDN
E) Templates
F) Blockchain

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
24
An online retailer wants to ensure its inventory for the holiday season is correct. The company does not have a large IT infrastructure or staff to collect and analyze sales information, customer analytics, marketing information, or trends. Which of the following cloud services will help the company analyze these metrics without a large investment in human capital?
A) Containerization
B) Big Data
C) Microservices
D) Blockchain
A) Containerization
B) Big Data
C) Microservices
D) Blockchain

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
25
A vendor stipulates it will provide incident response within two hours of a severity level A incident. Which of the following does this describe?
A) Maintenance agreement
B) Managed service agreement
C) Operating level agreement
D) Service level agreement
A) Maintenance agreement
B) Managed service agreement
C) Operating level agreement
D) Service level agreement

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
26
A company's finance team is reporting increased cloud costs against the allocated cloud budget. Which of the following is the BEST approach to match some of the cloud operating costs with the appropriate departments?
A) Right-sizing
B) Scaling
C) Chargeback
D) Showback
A) Right-sizing
B) Scaling
C) Chargeback
D) Showback

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
27
A company migrated all of its infrastructure to the cloud. The cloud security team must review the security post-migration. Which of the following is the MOST appropriate task for the cloud security team to perform?
A) Risk register
B) Threat assessment
C) Application scan
D) Vulnerability scan
A) Risk register
B) Threat assessment
C) Application scan
D) Vulnerability scan

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
28
A company is required to move its human resources application to the cloud to reduce capital expenses. The IT team does a feasibility analysis and learns the application requires legacy infrastructure and cannot be moved to the cloud. Which of the following is the MOST appropriate cloud migration approach for the company?
A) Lift and shift
B) Hybrid
C) Rip and replace
D) In-place upgrade
A) Lift and shift
B) Hybrid
C) Rip and replace
D) In-place upgrade

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
29
A company deploys a data management capability that reduces RPO. Which of the following BEST describes the capability needed?
A) Locality
B) Replication
C) Portability
D) Archiving
A) Locality
B) Replication
C) Portability
D) Archiving

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
30
A company wants to migrate mission-critical applications to the cloud. In order for technicians to build, decommission, and perform other routine functions, which of the following cloud characteristics would BEST satisfy this business requirement?
A) Self-service
B) Elasticity
C) Broad network access
D) Availability
A) Self-service
B) Elasticity
C) Broad network access
D) Availability

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following is the cloud storage technology that would allow a company with 12 nearly identical servers to have the SMALLEST storage footprint?
A) Capacity on demand
B) Compression
C) Software-defined storage
D) Deduplication
A) Capacity on demand
B) Compression
C) Software-defined storage
D) Deduplication

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
32
After performing an initial assessment of a cloud-hosted architecture, a department wants to gain the support of upper management. Which of the following should be presented to management?
A) Project charter
B) Feasibility study
C) Managed services
D) Pilot
A) Project charter
B) Feasibility study
C) Managed services
D) Pilot

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the following are true about the use of machine learning in a cloud environment? (Choose two).
A) Specialized machine learning algorithms can be deployed to optimize results for specific scenarios.
B) Machine learning can just be hosted in the cloud for managed services.
C) Just one type of cloud storage is available in the cloud for machine learning workloads.
D) Machine learning can leverage processes in a cloud environment through the use of cloud storage and auto-scaling.
E) Machine learning requires a specialized IT team to create the machine learning models from scratch.
F) Using machine learning solutions in the cloud removes the data-gathering step from the learning process.
A) Specialized machine learning algorithms can be deployed to optimize results for specific scenarios.
B) Machine learning can just be hosted in the cloud for managed services.
C) Just one type of cloud storage is available in the cloud for machine learning workloads.
D) Machine learning can leverage processes in a cloud environment through the use of cloud storage and auto-scaling.
E) Machine learning requires a specialized IT team to create the machine learning models from scratch.
F) Using machine learning solutions in the cloud removes the data-gathering step from the learning process.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
34
A cloud systems administrator needs to log in to a remote Linux server that is hosted in a public cloud. Which of the following protocols will the administrator MOST likely use?
A) HTTPS
B) RDP
C) Secure Shell
D) Virtual network computing
A) HTTPS
B) RDP
C) Secure Shell
D) Virtual network computing

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
35
A company wants to process a batch job in a faster, cost-effective manner. Which of the following is the BEST solution?
A) Implement right-sizing.
B) Increase CPU usage.
C) Utilize spot instances.
D) Add storage.
A) Implement right-sizing.
B) Increase CPU usage.
C) Utilize spot instances.
D) Add storage.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
36
Which of the following cloud principles will help manage the risk of a network breach?
A) Shared responsibility
B) Self-service
C) Availability
D) Elasticity
A) Shared responsibility
B) Self-service
C) Availability
D) Elasticity

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
37
A business analysis team is reviewing a report to try to determine the costs for a cloud application. The report does not allow separating costs by application. Which of the following should the team use to BEST report on the costs of the specific cloud application?
A) Right-sizing
B) Content management
C) Optimization
D) Resource tagging
A) Right-sizing
B) Content management
C) Optimization
D) Resource tagging

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
38
A company is migrating its e-commerce platform to a cloud service provider. The e-commerce site has a significant number of images. Which of the following is the BEST storage type for storing the images?
A) Object
B) Cold
C) File
D) Block
A) Object
B) Cold
C) File
D) Block

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
39
A company has a perpetual license for a database application. Which of the following is the MOST cost-effective option when moving to the cloud?
A) Fixed
B) Subscription
C) EULA
D) BYOL
A) Fixed
B) Subscription
C) EULA
D) BYOL

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
40
Which of the following types of risk is MOST likely to be associated with moving all data to one cloud provider?
A) Vendor lock-in
B) Data portability
C) Network connectivity
D) Data sovereignty
A) Vendor lock-in
B) Data portability
C) Network connectivity
D) Data sovereignty

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following should be considered to ensure the availability of data that is accessed across multiple sites? (Choose two.)
A) Auto-scaling
B) Geo-redundancy
C) Backup
D) Provisioning
E) Locality
F) Zones
A) Auto-scaling
B) Geo-redundancy
C) Backup
D) Provisioning
E) Locality
F) Zones

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
42
Which of the following is a benefit of microservice applications in a cloud environment?
A) Microservices are dependent on external shared databases found on cloud solutions.
B) Federation is a mandatory component for an optimized microservice deployment.
C) The architecture of microservice applications allows the use of auto-scaling.
D) Microservice applications use orchestration solutions to update components in each service.
A) Microservices are dependent on external shared databases found on cloud solutions.
B) Federation is a mandatory component for an optimized microservice deployment.
C) The architecture of microservice applications allows the use of auto-scaling.
D) Microservice applications use orchestration solutions to update components in each service.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
43
Which of the following results from implementing a proprietary SaaS solution when an organization does not ensure the solution adopts open standards? (Choose two.)
A) Vendor lock-in
B) Inability to enforce the SLA
C) Lack of technical support
D) Higher ongoing operational expenditure
E) Integration issues
F) Higher initial capital expenditure
A) Vendor lock-in
B) Inability to enforce the SLA
C) Lack of technical support
D) Higher ongoing operational expenditure
E) Integration issues
F) Higher initial capital expenditure

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
44
Which of the following security concerns is BEST addressed by moving systems to the cloud?
A) Availability
B) Authentication
C) Confidentiality
D) Integrity
A) Availability
B) Authentication
C) Confidentiality
D) Integrity

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
45
When designing a new cloud-enabled application, an organization that is considering RTO and RPO is MOST likely concerned about:
A) redundancy.
B) load balancing.
C) disaster recovery.
D) high availability.
A) redundancy.
B) load balancing.
C) disaster recovery.
D) high availability.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following is an example of multifactor authentication?
A) A password policy that requires both upper and lowercase letters
B) A short message service (SMS) message sent to a phone and an access PIN
C) Encryption of cached password information and a challenge question
D) A password that expires after 90 days and a PIN
A) A password policy that requires both upper and lowercase letters
B) A short message service (SMS) message sent to a phone and an access PIN
C) Encryption of cached password information and a challenge question
D) A password that expires after 90 days and a PIN

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
47
Before conducting a cloud migration, a compliance team requires confirmation that sensitive data will remain close to their users. Which of the following will meet this requirement during the cloud design phase?
A) Data locality
B) Data classification
C) Data certification
D) Data validation
A) Data locality
B) Data classification
C) Data certification
D) Data validation

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
48
Which of the following can be used to achieve automation, environment consistency, and standardization of computer resources in a cloud environment?
A) Content management system
B) Automation
C) Service-oriented architecture
D) Infrastructure as code
A) Content management system
B) Automation
C) Service-oriented architecture
D) Infrastructure as code

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
49
Which of the following BEST explains the concept of RTOs for restoring servers to operational use?
A) To reduce the amount of data loss that can occur in the event of a server failure
B) To ensure the restored server is available and operational within a given window of time
C) To ensure the data on the restored server is current within a given window of time
D) To reduce the amount of time a particular server is unavailable and offline
A) To reduce the amount of data loss that can occur in the event of a server failure
B) To ensure the restored server is available and operational within a given window of time
C) To ensure the data on the restored server is current within a given window of time
D) To reduce the amount of time a particular server is unavailable and offline

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
50
An incident response team requires documentation for an email phishing campaign against a company's email server. Which of the following is the BEST resource to use to start the investigation?
A) Audit and system logs
B) Change management procedures
C) Departmental policies
D) Standard operating procedures
A) Audit and system logs
B) Change management procedures
C) Departmental policies
D) Standard operating procedures

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
51
Which of the following storage types will BEST allow data to be backed up and retained for long periods of time?
A) Solid state storage
B) Block storage
C) Object storage
D) File storage
A) Solid state storage
B) Block storage
C) Object storage
D) File storage

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following metrics defines how much data loss a company can tolerate?
A) RTO
B) TCO
C) MTTR
D) ROI
E) RPO
A) RTO
B) TCO
C) MTTR
D) ROI
E) RPO

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
53
For security reasons, a cloud service that can be accessed from anywhere would make BEST use of:
A) replication.
B) multifactor authentication.
C) single sign-on.
D) data locality
A) replication.
B) multifactor authentication.
C) single sign-on.
D) data locality

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following would be expected from a security consultant who has been hired to investigate a data breach of a private cloud instance?
A) Incident report
B) Application scan results
C) Request for information
D) Risk register
A) Incident report
B) Application scan results
C) Request for information
D) Risk register

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following are aspects of cloud data availability? (Choose two.)
A) Resource tagging
B) Data sovereignty
C) Locality
D) Zones
E) Geo-redundancy
F) Auto-scaling
A) Resource tagging
B) Data sovereignty
C) Locality
D) Zones
E) Geo-redundancy
F) Auto-scaling

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
56
Which of the following would help a company avoid failure of a cloud project due to a lack of adherence of the company's operations and business processes to a cloud solution?
A) Cloud managed services
B) Company baseline
C) Proof of value
D) Industry benchmarks
A) Cloud managed services
B) Company baseline
C) Proof of value
D) Industry benchmarks

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
57
Which of the following is the BEST approach to optimize data security in an IaaS migration of data to the cloud?
A) Review the risk register.
B) Perform a vulnerability scan
C) Perform server hardening.
D) Configure encryption in transit.
A) Review the risk register.
B) Perform a vulnerability scan
C) Perform server hardening.
D) Configure encryption in transit.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
58
A startup company wants to use a CRM application to manage its sales and support organizations. The company does not have any IT staff. Which of the following cloud computing models is MOST appropriate for this company to use?
A) CaaS
B) PaaS
C) IaaS
D) SaaS
A) CaaS
B) PaaS
C) IaaS
D) SaaS

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following stores transactions in a distributed ledger of which all users have a copy?
A) Big Data
B) Blockchain
C) Machine learning
D) Artificial intelligence
A) Big Data
B) Blockchain
C) Machine learning
D) Artificial intelligence

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
60
A company wants to deploy an application in a public cloud. Which of the following service models gives the MOST responsibility to the provider?
A) PaaS
B) IaaS
C) BPaaS
D) SaaS
A) PaaS
B) IaaS
C) BPaaS
D) SaaS

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
61
Which of the following deployment models includes application components on a company's network as well as on the Internet?
A) Private
B) Public
C) Community
D) Hybrid
A) Private
B) Public
C) Community
D) Hybrid

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
62
A network team establishes a new connection to an IaaS CSP that is more efficient and has networking costs that are 25% less than previous monthly expenditures. The bill outlines the following costs: Storage: $10000 Compute: $12000 Network: $7000 Which of the following will be the total cloud expenditure for the following month?
A) $26000
B) $26250
C) $27250
D) $29000
A) $26000
B) $26250
C) $27250
D) $29000

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
63
A business analyst is reviewing a software upgrade plan. The plan mentions the term "hash" value. Which of the following BEST represents what this term implies?
A) Non-repudiation of data
B) Integrity of data
C) Confidentiality of data
D) Availability of data
A) Non-repudiation of data
B) Integrity of data
C) Confidentiality of data
D) Availability of data

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
64
A Chief Information Officer (CIO) wants to identify two business units to be pilots for a new cloud project. A business analyst who was recently assigned to this project will be selecting a cloud provider. Which of the following should the business analyst do FIRST?
A) Conduct a feasibility study of the environment.
B) Conduct a benchmark of all major systems.
C) Draw a matrix diagram of the capabilities of the cloud providers.
D) Gather business and technical requirements for key stakeholders.
A) Conduct a feasibility study of the environment.
B) Conduct a benchmark of all major systems.
C) Draw a matrix diagram of the capabilities of the cloud providers.
D) Gather business and technical requirements for key stakeholders.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
65
A manufacturing company is selecting applications for a cloud migration. The company's main concern relates to the ERP system, which needs to receive data from multiple industrial systems to generate the executive reports. Which of the following will provide the details needed for the company's decision regarding the cloud migration?
A) Standard operating procedures
B) Feasibility studies
C) Statement of work
D) Benchmarks
A) Standard operating procedures
B) Feasibility studies
C) Statement of work
D) Benchmarks

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
66
An architect recently discovered new opportunities the cloud can provide to the company. A business analyst is currently working with the architect to document the business use-case scenarios. Which of the following should be the architect's NEXT step?
A) Initialize a PoC.
B) Conduct a feasibility study.
C) Perform a gap analysis.
D) Gather cloud requirements.
A) Initialize a PoC.
B) Conduct a feasibility study.
C) Perform a gap analysis.
D) Gather cloud requirements.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
67
Which of the following allows for the management of network policies from a central portal while maintaining a hardware-agnostic approach?
A) Virtual private network
B) Software-defined network
C) Load balancing
D) Direct Connect
A) Virtual private network
B) Software-defined network
C) Load balancing
D) Direct Connect

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
68
A company is evaluating the capital expenditure necessary to modernize its on-premises datacenter. Management has directed that 50% of capital expenditure be reallocated to operating expenditure. Which of the following cloud characteristics applies?
A) BYOL
B) Billing chargeback
C) Pay-as-you-go
D) High availability
A) BYOL
B) Billing chargeback
C) Pay-as-you-go
D) High availability

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
69
A company would like to improve its current DR plan with an emphasis on high availability. Which of the following metrics should the company focus on?
A) MTTR
B) RTO
C) QoS
D) RPO
A) MTTR
B) RTO
C) QoS
D) RPO

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
70
Which of the following cloud migration methods would take full advantage of the cloud computing model?
A) Rip and replace
B) Lift and shift
C) Phased
D) Hybrid
A) Rip and replace
B) Lift and shift
C) Phased
D) Hybrid

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
71
A business is experiencing an outage of a customer-facing e-commerce website after a SaaS-based CDN upgrade. The RTO is 5 minutes or less, but it has already been 10 minutes since the outage. After 15 minutes, the CDN recovers for the outage. The business loses $25000 in revenue per minute of the outage. Which of the following is the financial impact to the business?
A) $250000
B) $350000
C) $375000
D) $400000
A) $250000
B) $350000
C) $375000
D) $400000

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
72
Which of the following is true about the use of technologies such as JSON and XML for cloud data interchange and automation tasks?
A) It can cause cloud vendor lock-in
B) The company needs to define a specific programming language for cloud management.
C) The same message format can be used across different cloud platforms.
D) It is considered an unsafe format of communication.
A) It can cause cloud vendor lock-in
B) The company needs to define a specific programming language for cloud management.
C) The same message format can be used across different cloud platforms.
D) It is considered an unsafe format of communication.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
73
A company is planning to use cloud computing to extend the compute resources that will run a new resource-intensive application. A direct deployment to the cloud would cause unexpected billing. Which of the following must be generated while the application is running on-premises to predict the cloud budget for this project better?
A) Proof or concept
B) Benchmark
C) Baseline
D) Feasibility study
A) Proof or concept
B) Benchmark
C) Baseline
D) Feasibility study

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
74
An organization determines it cannot go forward with a cloud migration due to the risks involved. Which of the following types of risk response does this describe?
A) Acceptance
B) Transference
C) Avoidance
D) Mitigation
A) Acceptance
B) Transference
C) Avoidance
D) Mitigation

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
75
A business analyst is comparing utilization for a company's cloud servers on a financial expenditures report. The usage report is as follows: 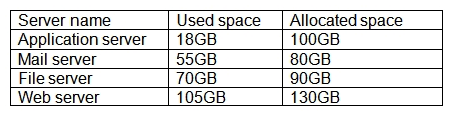 Which of the following instances represents the highest utilization?
Which of the following instances represents the highest utilization?
A) Mail server
B) Application server
C) File server
D) Web server
 Which of the following instances represents the highest utilization?
Which of the following instances represents the highest utilization?A) Mail server
B) Application server
C) File server
D) Web server

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
76
Which of the following strategies allows an organization to plan for cloud expenditures in a way that most closely aligns with the capital expenditure model?
A) Simplifying contract requirements
B) Implementing consolidated billing
C) Considering a BYOL policy
D) Using reserved cloud instances
A) Simplifying contract requirements
B) Implementing consolidated billing
C) Considering a BYOL policy
D) Using reserved cloud instances

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
77
A project manager is interested in the notification process a CSP follows after discovering a breach of customer data. Which of the following is MOST likely to provide the necessary information?
A) Communication plans
B) Incident response policy
C) Service level agreement
D) Access controls
A) Communication plans
B) Incident response policy
C) Service level agreement
D) Access controls

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
78
Which of the following allows an IP address to be referenced via an easily remembered name for a SaaS application?
A) DNS
B) CDN
C) VPN
D) WAN
A) DNS
B) CDN
C) VPN
D) WAN

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
79
Which of the following BEST describes the open-source licensing model for application software?
A) Software is free to use, but the source code is not available to modify.
B) Modifications to existing software are not allowed.
C) Code modifications must be submitted for approval.
D) Source code is readily available to view and use.
A) Software is free to use, but the source code is not available to modify.
B) Modifications to existing software are not allowed.
C) Code modifications must be submitted for approval.
D) Source code is readily available to view and use.

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck
80
A cloud administrator is reviewing the requirements for a SaaS application and estimates downtime will be very expensive for the organization. Which of the following should the administrator configure to minimize downtime? (Choose two.)
A) Continuous deployment
B) Right-sizing
C) Availability zones
D) Geo-redundancy
E) Hardening
F) Backups
A) Continuous deployment
B) Right-sizing
C) Availability zones
D) Geo-redundancy
E) Hardening
F) Backups

Unlock Deck
Unlock for access to all 107 flashcards in this deck.
Unlock Deck
k this deck


