Exam 10: CompTIA Network+
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/829
Play
Full screen (f)
Exam 10: CompTIA Network+
1
A network engineer is configuring wireless access for guests at an organization. Access to other areas in the organization should not be accessible to guests. Which of the following represents the MOST secure method to configure guest access to the wireless network?
A) Guests should log into a separate wireless network using a captive portal
B) Guests should log into the current wireless network using credentials obtained upon entering the facility
C) The existing wireless network should be configured to allow guest access
D) An additional wireless network should be configured to allow guest access
A) Guests should log into a separate wireless network using a captive portal
B) Guests should log into the current wireless network using credentials obtained upon entering the facility
C) The existing wireless network should be configured to allow guest access
D) An additional wireless network should be configured to allow guest access
Guests should log into a separate wireless network using a captive portal
2
A technician has racked a new access switch and has run multimode fiber to a new location. After installing an extended-range 10Gb SFP in the core switch, the technician installed a 10Gb SFP in the access switch and connected the port to the new extension with a fiber jumper. However, the link does not display, and the technician cannot see light emitting from the core switch. Which of the following solutions is MOST likely to resolve the problem?
A) Swap the fiber pairs in one of the SFPs
B) Replace the jumpers with single-mode fiber
C) Set the correct MTU on the new interface
D) Install an optic that matches the fiber type
A) Swap the fiber pairs in one of the SFPs
B) Replace the jumpers with single-mode fiber
C) Set the correct MTU on the new interface
D) Install an optic that matches the fiber type
Replace the jumpers with single-mode fiber
3
A technician attempts to replace a switch with a new one of similar model from the same vendor. When the technician moves the fiber and SFP plug, the switch does not completely boot up. Considering that the config files are the same, which of the following is the MOST likely cause of the failure?
A) Damaged fiber
B) Corrupted operating system
C) VLAN mismatch
D) Bad port
A) Damaged fiber
B) Corrupted operating system
C) VLAN mismatch
D) Bad port
Corrupted operating system
4
The server team has just installed an application across three different servers. They are asking that all requests to the application are spread evenly across the three servers. Which of the following should the network team implement to fulfil the request?
A) Proxy server
B) UTM appliance
C) Content filter
D) Load balancer
A) Proxy server
B) UTM appliance
C) Content filter
D) Load balancer

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
5
A network technician is troubleshooting an issue and has established a theory of probable cause. Which of the following steps should the network technician take NEXT?
A) Test the possible solution
B) Question the users
C) Determine what has changed
D) Document the theory
A) Test the possible solution
B) Question the users
C) Determine what has changed
D) Document the theory

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
6
A technician wants to prevent an unauthorized host from connecting to the network via Ethernet. Which of the following is a Layer 2 access control the technician should implement?
A) Access control lists
B) Captive portal
C) WPA2
D) Port security
A) Access control lists
B) Captive portal
C) WPA2
D) Port security

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following provides the ability to deploy consistent access point configurations from a central location?
A) Wireless controller
B) AAA server
C) WiFi-protected setup
D) Proxy server
E) VPN concentrator
A) Wireless controller
B) AAA server
C) WiFi-protected setup
D) Proxy server
E) VPN concentrator

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
8
A UTM is deployed on the external edge of the main corporate office. The office connects to the WAN port of the edge router. The edge router at the main office connects to the remote offices using GRE IPSec tunnels. A network administrator notices that a worm that was not detected by the UTM has spread from the remote sites into the corporate network. The UTM currently has traffic rules applied that should block the port used by the worm. Which of the following steps would MOST likely correct this issue?
A) Move the UTM onto the LAN side of the network
B) Enable TLS inspection on the UTM
C) Enable stateful inspection on the UTM
D) Configure the UTM to deny encrypted files from being transferred
A) Move the UTM onto the LAN side of the network
B) Enable TLS inspection on the UTM
C) Enable stateful inspection on the UTM
D) Configure the UTM to deny encrypted files from being transferred

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
9
A network technician is troubleshooting wireless network issues in a crowded office complex and suspects there is interference from nearby wireless networks. Which of the following should the technician perform to discover possible interference?
A) Site survey
B) Vulnerability scanning
C) Wardriving
D) Checking logical diagram
E) Bandwidth test
A) Site survey
B) Vulnerability scanning
C) Wardriving
D) Checking logical diagram
E) Bandwidth test

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
10
A technician is installing a new wireless badging system on a hospital network. The requirements of the badging system are for it to have its own SSID and low power levels. The badging system has to cover 99.9% of the hospital. Which of the following is the BEST action to take to meet the system requirements?
A) Install additional WAPs
B) Install external antennas
C) Move the WAPs closer to the more populated area
D) Change the antenna types
A) Install additional WAPs
B) Install external antennas
C) Move the WAPs closer to the more populated area
D) Change the antenna types

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
11
A network administrator has been given a network of 172.16.85.0/21 and wants to know the usable range of IP addresses on that subnet. Which of the following indicates the correct IP address range?
A) 172.16.80.0-172.16.85.254
B) 172.16.80.0-172.16.88.255
C) 172.16.80.1-172.16.87.254
D) 172.16.80.1-172.16.85.255
A) 172.16.80.0-172.16.85.254
B) 172.16.80.0-172.16.88.255
C) 172.16.80.1-172.16.87.254
D) 172.16.80.1-172.16.85.255

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
12
A network technician has discovered a rogue access point placed under an empty cubicle desk. Which of the following should the technician perform to ensure another cannot be placed on the network?
A) Disable unused ports on switches
B) Enable DHCP guard to detect rogue servers
C) Configure WPA2 on all access points
D) Use TACACS+ authentication
A) Disable unused ports on switches
B) Enable DHCP guard to detect rogue servers
C) Configure WPA2 on all access points
D) Use TACACS+ authentication

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
13
A company has hundreds of nodes on a single subnet and has decided to implement VLANs. Which of the following BEST describes the benefit of this approach?
A) It segments broadcast domains in the network infrastructure
B) It provides a faster port to all servers
C) It provides multiple collision domains on one switchport
D) It provides multiple broadcast domains within a single collision domain
A) It segments broadcast domains in the network infrastructure
B) It provides a faster port to all servers
C) It provides multiple collision domains on one switchport
D) It provides multiple broadcast domains within a single collision domain

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
14
A junior network technician is setting up a new email server on the company network. Which of the following default ports should the technician ensure is open on the firewall so the new email server can relay email?
A) 23
B) 25
C) 110
D) 143
A) 23
B) 25
C) 110
D) 143

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
15
According to the OSI model, at which of the following layers is data encapsulated into a packet?
A) Layer 2
B) Layer 3
C) Layer 4
D) Layer 5
E) Layer 6
A) Layer 2
B) Layer 3
C) Layer 4
D) Layer 5
E) Layer 6

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following WAN technologies is MOST preferred when developing a VoIP system with 23 concurrent channels?
A) DSL
B) POTS
C) T1
D) DOCSIS
A) DSL
B) POTS
C) T1
D) DOCSIS

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
17
A penetration tester has been tasked with reconnaissance to determine which ports are open on the network. Which of the following tasks should be done FIRST? (Choose two.)
A) Network scan
B) Banner grab
C) Tracert
D) DHCP server check
E) Brute-force attack
A) Network scan
B) Banner grab
C) Tracert
D) DHCP server check
E) Brute-force attack

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
18
Which of the following is a vulnerable system designed to detect and log unauthorized access?
A) SIEM
B) Honeypot
C) DMZ
D) Proxy server
A) SIEM
B) Honeypot
C) DMZ
D) Proxy server

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
19
A network technician is configuring a wireless network at a branch office. Users at this office work with large files and must be able to access their files on the server quickly. Which of the following 802.11 standards provides the MOST bandwidth?
A) a
B) ac
C) g
D) n
A) a
B) ac
C) g
D) n

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
20
Users are reporting Internet connectivity issues. The network administrator wants to determine if the issues are internal to the company network or if there is an issue with the ISP. Which of the following tools should be used to BEST determine where the outage is occurring?
A) traceroute
B) ping
C) nslookup
D) netstat
A) traceroute
B) ping
C) nslookup
D) netstat

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
21
The backup server connects to a NAS device using block-level storage over Ethernet. The performance is very slow, however, and the network technician suspects the performance issues are network related. Which of the following should the technician do to improve performance?
A) Utilize UDP to eliminate packet overhead
B) Turn off MDIX settings on the NAS and server switchports
C) Enable jumbo frames on the NAS and server
D) Encapsulate the storage traffic in a GRE tunnel
A) Utilize UDP to eliminate packet overhead
B) Turn off MDIX settings on the NAS and server switchports
C) Enable jumbo frames on the NAS and server
D) Encapsulate the storage traffic in a GRE tunnel

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
22
A network technician is working on a proposal for email migration from an on-premises email system to a vendor-hosted email in the cloud. The technician needs to explain to management what type of cloud model will be utilized with the cloud-hosted email. Which of the following cloud models should the technician identify in the proposal?
A) IaaS
B) PaaS
C) SaaS
D) MaaS
A) IaaS
B) PaaS
C) SaaS
D) MaaS

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
23
A technician discovers that multiple switches require a major update. Which of the following policies should be followed?
A) Change management policy
B) Remote access policy
C) Acceptable use policy
D) Memorandum of understanding
A) Change management policy
B) Remote access policy
C) Acceptable use policy
D) Memorandum of understanding

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following devices should a network administrator configure on the outermost part of the network?
A) Media converter
B) Switch
C) Modem
D) Firewall
A) Media converter
B) Switch
C) Modem
D) Firewall

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
25
Based on networks 10.8.16.0/22 and 10.8.31.0/21, which of the following is the BEST summarized CIDR notation?
A) 10.8.0.0/16
B) 10.8.0.0/19
C) 10.8.0.0/20
D) 10.0.0.0/24
A) 10.8.0.0/16
B) 10.8.0.0/19
C) 10.8.0.0/20
D) 10.0.0.0/24

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
26
A network administrator is setting up a web-based application that needs to be continually accessible to the end users. Which of the following concepts would BEST ensure this requirement?
A) High availability
B) Snapshots
C) NIC teaming
D) Cold site
A) High availability
B) Snapshots
C) NIC teaming
D) Cold site

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
27
A technician is setting up a direct connection between two older PCs so they can communicate but not be on the corporate network. The technician does not have access to a spare switch but does have spare Cat 6 cables, RJ-45 plugs, and a crimping tool. The technician cuts off one end of the cable. Which of the following should the technician do to make a crossover cable before crimping the new plug?
A) Reverse the wires leading to pins 1 and 2
B) Reverse the wires leading to pins 1 and 3
C) Reverse the wires leading to pins 2 and 3
D) Reverse the wires leading to pins 2 and 4
A) Reverse the wires leading to pins 1 and 2
B) Reverse the wires leading to pins 1 and 3
C) Reverse the wires leading to pins 2 and 3
D) Reverse the wires leading to pins 2 and 4

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
28
A network engineer wants to segment the network into multiple broadcast domains. Which of the following devices would allow for communication between the segments?
A) Layer 2 switch
B) Layer 3 switch
C) Bridge
D) Load balancer
A) Layer 2 switch
B) Layer 3 switch
C) Bridge
D) Load balancer

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
29
Client PCs are unable to receive addressing information from a newly configured interface on a router. Which of the following should be added to allow the clients to connect?
A) DHCP lease time
B) IP helper
C) TTL
D) DNS record type
A) DHCP lease time
B) IP helper
C) TTL
D) DNS record type

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
30
A network engineer is designing a new network for a remote site. The remote site consists of ten desktop computers, ten VoIP phones, and two network printers. In addition, two of the desktop computers at the remote site will be used by managers who should be on a separate network from the other eight computers. Which of the following represents the BEST configuration for the remote site?
A) One router connected to one 24-port switch configured with three VLANS; one for the manager's computers and printer, one for the other computers and printer, and one for the VoIP phones
B) Two routers with each router connected to a 12-port switch, with a firewall connected to the switch connected to the manager's desktop computers, VoIP phones, and printer
C) One router connected to one 12-port switch configured for the manager's computers, phones, and printer, and one 12-port switch configured for the other computers, VoIP phones, and printer
D) One router connected to one 24-port switch configured with two VLANS; one for the manager's computers, VoIP phones, and printer, and one for the other computers, VoIP phones, and printer
A) One router connected to one 24-port switch configured with three VLANS; one for the manager's computers and printer, one for the other computers and printer, and one for the VoIP phones
B) Two routers with each router connected to a 12-port switch, with a firewall connected to the switch connected to the manager's desktop computers, VoIP phones, and printer
C) One router connected to one 12-port switch configured for the manager's computers, phones, and printer, and one 12-port switch configured for the other computers, VoIP phones, and printer
D) One router connected to one 24-port switch configured with two VLANS; one for the manager's computers, VoIP phones, and printer, and one for the other computers, VoIP phones, and printer

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
31
A technician is trying to determine the IP address of a customer's router. The customer has an IP address of 192.168.1.55/24. Which of the following is the address of the customer's router?
A) 192.168.0.55
B) 192.168.1.0
C) 192.168.1.1
D) 192.168.5.5
E) 255.255.255.0
A) 192.168.0.55
B) 192.168.1.0
C) 192.168.1.1
D) 192.168.5.5
E) 255.255.255.0

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
32
A network technician receives a call from a user who is experiencing network connectivity issues. The network technician questions the user and learns the user brought in a personal wired router to use multiple computers and connect to the network. Which of the following has the user MOST likely introduced to the network?
A) Rogue DHCP server
B) Evil twin
C) VLAN mismatch
D) Honeypot
A) Rogue DHCP server
B) Evil twin
C) VLAN mismatch
D) Honeypot

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
33
A network technician wants to remotely and securely access the desktop of a Linux workstation. The desktop is running remote control software without encryption. Which of the following should the technician use to secure the connection?
A) SSH in tunnel mode
B) RDP set to console connection
C) EAP-PEAP
D) SFTP
A) SSH in tunnel mode
B) RDP set to console connection
C) EAP-PEAP
D) SFTP

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
34
A technician is troubleshooting a point-to-point fiber-optic connection. The technician is at a remote site and has no connectivity to the main site. The technician confirms the switch and the send-and-receive light levels are within acceptable range. Both fiber SFPs are confirmed as working. Which of the following should the technician use to reveal the location of the fault?
A) OTDR
B) Light meter
C) Tone generator
D) CSU/DSU
A) OTDR
B) Light meter
C) Tone generator
D) CSU/DSU

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
35
A technician is connecting a router directly to a PC using the G1/0/1 interface. Without the use of auto-sensing ports, which of the following cables should be used?
A) Straight-through
B) Console
C) Rollover
D) Crossover
A) Straight-through
B) Console
C) Rollover
D) Crossover

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
36
A Chief Information Officer (CIO) wants to move some IT services to a cloud service offering. However, the network administrator still wants to be able to control some parts of the cloud service's networking components. Which of the following should be leveraged to complete this task?
A) IaaS
B) PaaS
C) SaaS
D) DaaS
A) IaaS
B) PaaS
C) SaaS
D) DaaS

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
37
A network technician is able to connect the switches between two offices, but the offices cannot communicate with each other, as each office uses a different IP addressing scheme. Which of the following devices needs to be installed between the switches to allow communication?
A) Bridge
B) Access point
C) Router
D) Range extender
A) Bridge
B) Access point
C) Router
D) Range extender

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
38
A network technician notices the site-to-site VPN and Internet connection have not come back up at a branch office after a recent power outage. Which of the following is an out-of-band method the technician would MOST likely utilize to check the branch office's router status?
A) Use a modem to console into the router
B) Walk a user through troubleshooting the connection
C) Travel to the branch office
D) Hire a contractor to go on-site
A) Use a modem to console into the router
B) Walk a user through troubleshooting the connection
C) Travel to the branch office
D) Hire a contractor to go on-site

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following should current network performance be compared against to determine network anomalies?
A) Baseline
B) Traffic analysis
C) Packet capture
D) Logs
A) Baseline
B) Traffic analysis
C) Packet capture
D) Logs

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
40
A technician is diagnosing an issue with a new T1 connection. The router is configured, the cable is connected, but the T1 is down. To verify the configuration of the router, which of the following tools should the technician use?
A) Loopback adapter
B) Cable tester
C) Tone generator
D) Multimeter
A) Loopback adapter
B) Cable tester
C) Tone generator
D) Multimeter

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
41
A network technician is connecting two switches together. Which of the following protocols should the technician use to increase speed and fault tolerance?
A) SIP
B) BGP
C) LACP
D) LLDP
A) SIP
B) BGP
C) LACP
D) LLDP

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
42
A disgruntled employee executes a man-in-the-middle attack on the company network. Layer 2 traffic destined for the gateway is redirected to the employee's computer. This type of attack is an example of:
A) ARP cache poisoning
B) IP spoofing
C) amplified DNS attack
D) evil twin
A) ARP cache poisoning
B) IP spoofing
C) amplified DNS attack
D) evil twin

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
43
A company has a web-based application that is used by many different departments. The company has experienced some overload of resources on the database server. The network administrator implements a network device in between the servers and the database. Which of the following BEST describes the purpose of this device?
A) Content filtering and network analysis
B) Load balancing and providing high availability
C) Port sniffing and protocol analysis
D) Clustering and NIC teaming
A) Content filtering and network analysis
B) Load balancing and providing high availability
C) Port sniffing and protocol analysis
D) Clustering and NIC teaming

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
44
A network technician is diagnosing a time-out issue generated from an end user's web browser. The web browser issues standard HTTP get and post commands to interact with the website. Given this information, the technician would like to analyze the entire TCP handshake of the HTTP requests offline. Which of the following tools would allow the technician to view the handshake?
A) Packet analyzer
B) Port analyzer
C) SNMP traps
D) Spectrum analyzer
A) Packet analyzer
B) Port analyzer
C) SNMP traps
D) Spectrum analyzer

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
45
A customer cannot access a company's secure website. The company's network security is reviewing the firewall for the server and finds the following output: 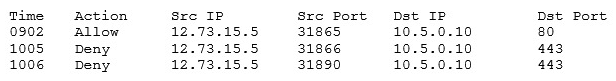 Which of the following changes should be made to allow all customers to access the company's secure website?
Which of the following changes should be made to allow all customers to access the company's secure website?
A) Allow any any 10.5.0.10 443
B) Allow any any 12.73.15.5 443
C) Allow 10.5.0.10 443 any any
D) Allow 10.5.0.10 any 10.5.0.10 80
 Which of the following changes should be made to allow all customers to access the company's secure website?
Which of the following changes should be made to allow all customers to access the company's secure website?A) Allow any any 10.5.0.10 443
B) Allow any any 12.73.15.5 443
C) Allow 10.5.0.10 443 any any
D) Allow 10.5.0.10 any 10.5.0.10 80

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following is used to classify network data for the purpose of providing QoS?
A) STP
B) VLANs
C) SIP
D) DSCP
A) STP
B) VLANs
C) SIP
D) DSCP

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
47
A company has contracted with an outside vendor to perform a service that will provide hardware, software, and procedures in case of a catastrophic failure of the primary datacenter. The Chief Information Officer (CIO) is concerned because this contract does not include a long-term strategy for extended outages. Which of the following should the CIO complete?
A) Disaster recovery plan
B) Business continuity plan
C) Service level agreement
D) First responder training
A) Disaster recovery plan
B) Business continuity plan
C) Service level agreement
D) First responder training

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
48
Which of the following is a reason why a business may be hesitant to move sensitive data to a SaaS cloud service?
A) Decreased performance of internal network
B) Loss of full control over data resources
C) Increased malware exposure
D) Incompatibility with the current network
A) Decreased performance of internal network
B) Loss of full control over data resources
C) Increased malware exposure
D) Incompatibility with the current network

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
49
A systems administrator has recently purchased and installed a large electronic signage screen for the company's parking garage. The screen's management software was installed on a server with a public IP address to allow remote management. The systems administrator is now troubleshooting an issue with the screen displaying unknown, random, and inappropriate messages. Which of the following is MOST effective in resolving this issue?
A) Changing the management software's default credentials
B) Disabling unnecessary services from the server and management software
C) Changing the management software's default port
D) Replacing the management software's self-signed certificate with a valid certificate
A) Changing the management software's default credentials
B) Disabling unnecessary services from the server and management software
C) Changing the management software's default port
D) Replacing the management software's self-signed certificate with a valid certificate

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
50
A technician is planning a remote-access strategy to manage routers and switches on a dedicated management network. The management network is segregated from the production network and uses site-to-site VPN connections. Some of the equipment does not support encryption. Which of the following should the technician choose that all the equipment would support?
A) Telnet
B) SSL
C) SSH
D) IPSec
A) Telnet
B) SSL
C) SSH
D) IPSec

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
51
A network technician has created a network that consists of a router, a firewall, a switch, and several PCs. Which of the following physical network topologies was created?
A) Star
B) Mesh
C) Ring
D) Bus
A) Star
B) Mesh
C) Ring
D) Bus

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
52
A computer lab on a campus network was recently reconfigured using recycled network cables. One of the 24 computers in the lab is unable to connect to the network after the upgrade. A network technician successfully uses the cable in question to connect directly to another computer. Which of the following is MOST likely the issue with the cable?
A) The cable is a crossover cable
B) The cable is a rollover cable
C) The cable has bent pins
D) The cable is a Cat 5 cable
A) The cable is a crossover cable
B) The cable is a rollover cable
C) The cable has bent pins
D) The cable is a Cat 5 cable

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
53
The process of attempting to exploit a weakness in a network after being given permission by the company is known as:
A) penetration testing
B) vulnerability scanning
C) reconnaissance
D) social engineering
A) penetration testing
B) vulnerability scanning
C) reconnaissance
D) social engineering

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
54
A company recently upgraded all of its printers to networked multifunction devices. Users can print to the new devices, but they would also like the ability to scan and fax files from their computers. Which of the following should the technician update to allow this functionality?
A) Device software
B) Printer drivers
C) Printer firmware
D) NIC drivers
A) Device software
B) Printer drivers
C) Printer firmware
D) NIC drivers

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following protocols do MOST MITM attacks utilize?
A) ARP
B) SIP
C) FTP
D) SCP
A) ARP
B) SIP
C) FTP
D) SCP

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
56
An administrator is moving to a new office. There will be several network runs through the ceiling area of the office. Which of the following is the BEST to utilize in these areas?
A) Single-mode fiber-optic cabling
B) Cat 5e-rated cabling
C) Cat 6-rated cabling
D) Plenum-rated cabling
A) Single-mode fiber-optic cabling
B) Cat 5e-rated cabling
C) Cat 6-rated cabling
D) Plenum-rated cabling

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
57
Which of the following MUST be implemented to share metrics between routing protocols within the same router?
A) Routing loop
B) Routing table
C) Route redistribution
D) Dynamic routes
A) Routing loop
B) Routing table
C) Route redistribution
D) Dynamic routes

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
58
An ISP technician gets a call from a business that just changed equipment but can no longer connect to the Internet. The technician checks the ARP table on the ISP switch, and there is no corresponding MAC address present. Instead, the entry is "Incomplete". Which of the following could cause this condition?
A) VLAN mismatch
B) Duplex/Speed mismatch
C) Duplicate IP address
D) TX/RX reverse
A) VLAN mismatch
B) Duplex/Speed mismatch
C) Duplicate IP address
D) TX/RX reverse

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
59
A network technician receives a spool of Cat 6a cable and is asked to build several cables for a new set of Ethernet runs between devices. Which of the following tools are MOST likely needed to complete the task? (Choose three.)
A) Wire stripper
B) Cable crimper
C) RJ-11 connectors
D) RJ-45 connectors
E) Multimeter
F) Punchdown tool
G) Tone generator
A) Wire stripper
B) Cable crimper
C) RJ-11 connectors
D) RJ-45 connectors
E) Multimeter
F) Punchdown tool
G) Tone generator

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
60
A technician is investigating a server performance issue. The technician has gathered the server utilization statistics. Which of the following should the technician use to determine which statistics are not in the normal range?
A) Baseline review
B) Vulnerability scan
C) System life-cycle report
D) Archiving logs
A) Baseline review
B) Vulnerability scan
C) System life-cycle report
D) Archiving logs

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
61
Which of the following BEST describes the differences between VLAN hopping and session hijacking?
A) VLAN hopping involves the unauthorized transition from one VLAN to another to gain additional access. Session hijacking involves overriding a user's web connection to execute commands
B) VLAN hopping is a brute force attack executed to gain additional access. Session hijacking involves physically disrupting a network connection
C) VLAN hopping involves overriding a user network connection to execute malicious commands. Session hijacking involves compromising a host to elevate privileges
D) VLAN hopping is the act of exploiting poor VLAN tagging. Session hijacking is a web-based attack aimed at privilege escalation
A) VLAN hopping involves the unauthorized transition from one VLAN to another to gain additional access. Session hijacking involves overriding a user's web connection to execute commands
B) VLAN hopping is a brute force attack executed to gain additional access. Session hijacking involves physically disrupting a network connection
C) VLAN hopping involves overriding a user network connection to execute malicious commands. Session hijacking involves compromising a host to elevate privileges
D) VLAN hopping is the act of exploiting poor VLAN tagging. Session hijacking is a web-based attack aimed at privilege escalation

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
62
Which of the following communication media can carry many voice, data, and video channels simultaneously over multiple frequencies?
A) Broadband
B) Baseband
C) Analog modem
D) CSMA
A) Broadband
B) Baseband
C) Analog modem
D) CSMA

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
63
Which of the following protocols can be both connection-oriented and connectionless?
A) 20 FTP
B) 53 DNS
C) 67 DHCP
D) 80 HTTP
A) 20 FTP
B) 53 DNS
C) 67 DHCP
D) 80 HTTP

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
64
An employee wishes to use a personal cell phone for work-related purposes, including storage of sensitive company data, during long business trips. Which of the following is needed to protect BOTH the employee and the company?
A) An NDA ensuring work data stored on the personal phone remains confidential
B) An AUP covering how a personal phone may be used for work matters
C) A consent to monitoring policy covering company audits of the personal phone
D) Real-time remote monitoring of the phone's activity and usage
A) An NDA ensuring work data stored on the personal phone remains confidential
B) An AUP covering how a personal phone may be used for work matters
C) A consent to monitoring policy covering company audits of the personal phone
D) Real-time remote monitoring of the phone's activity and usage

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
65
A small town is attempting to attract tourists who visit larger nearby cities. A network engineer is asked to implement a network encompassing the five-block town center and nearby businesses. The inclusion of smartphones and portable devices is crucial to the plan. Which of the following is the network engineer being asked to implement?
A) LAN
B) PAN
C) MAN
D) WAN
A) LAN
B) PAN
C) MAN
D) WAN

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
66
An office user cannot access local network drives but has full access to the Internet. A technician troubleshoots the issue and observes the following output of the ipconfig command: 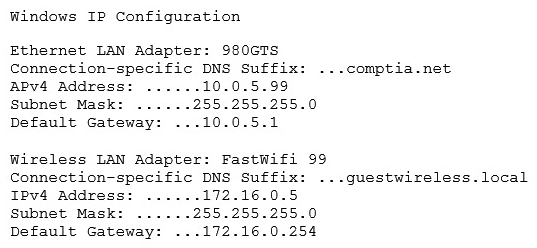 Which of the following would MOST likely allow the network drives to be accessed?
Which of the following would MOST likely allow the network drives to be accessed?
A) Update the WLAN adapter driver
B) Disable the WLAN adapter
C) Check the wireless DHCP configuration
D) Disable the LAN adapter
 Which of the following would MOST likely allow the network drives to be accessed?
Which of the following would MOST likely allow the network drives to be accessed?A) Update the WLAN adapter driver
B) Disable the WLAN adapter
C) Check the wireless DHCP configuration
D) Disable the LAN adapter

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
67
A network engineer arrives at work and discovers that many users are having problems when attempting to connect to the company network shared drives. The network operations center (NOC) technician just completed server upgrades the night before. To which of the following documents should the NOC technician refer to determine what potentially caused the connectivity problem?
A) Network maps
B) Cable management
C) Release notes
D) Change management
A) Network maps
B) Cable management
C) Release notes
D) Change management

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
68
Which of the following wireless connection types utilize MIMO on non-overlapping channels? (Choose two.)
A) 802.11a
B) 802.11ac
C) 802.11b
D) 802.11g
E) 802.11n
A) 802.11a
B) 802.11ac
C) 802.11b
D) 802.11g
E) 802.11n

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
69
A network technician is creating a new subnet for 488 host machines. The technician is told to use a class B address scheme when making the subnet and is instructed to leave as much room as possible for additional subnets of the same size. Which of the following subnets would fulfill these requirements?
A) 10.5.4.0/22
B) 10.233.2.0/23
C) 172.16.0.0/22
D) 172.18.0.0/23
E) 192.168.25.0/24
A) 10.5.4.0/22
B) 10.233.2.0/23
C) 172.16.0.0/22
D) 172.18.0.0/23
E) 192.168.25.0/24

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
70
An analyst is developing a proof of concept of a wireless-based attack as part of a penetration test against an organization's network. As part of the attack, the analyst launches a fake access point matching the SSID of the organization's guest access network. When a user connects to the fake access point, the analyst allows the traffic to flow through the access point to the legitimate site while the data traversing the network is logged for latest analysis and exploitation. Which of the following attacks has the analyst successfully performed in this scenario?
A) Bluesnarfing
B) Session hijacking
C) MAC spoofing
D) VLAN hopping
E) Man-in-the-middle
A) Bluesnarfing
B) Session hijacking
C) MAC spoofing
D) VLAN hopping
E) Man-in-the-middle

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
71
The security manager reports that individual systems involved in policy or security violations or incidents cannot be located quickly. The security manager notices the hostnames all appear to be randomly generated characters. Which of the following would BEST assist the security manager identifying systems involved in security incidents?
A) Enforce port security to require system authentication
B) Implement a standardized UNC
C) Label existing systems with current hostnames
D) Forward the DHCP logs to the security manager every day
A) Enforce port security to require system authentication
B) Implement a standardized UNC
C) Label existing systems with current hostnames
D) Forward the DHCP logs to the security manager every day

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
72
A forensic first responder arrives at the scene where an employee is suspected to have committed a computer-based crime. Which of the following should the first responder do FIRST?
A) Document the scene
B) Take pictures upon arrival
C) Secure the area
D) Implement chain of custody
A) Document the scene
B) Take pictures upon arrival
C) Secure the area
D) Implement chain of custody

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
73
A network technician has just configured NAC for connections using Cat 6 cables. However, none of the Windows clients can connect to the network. Which of the following components should the technician check on the Windows workstations? (Choose two.)
A) Start the Wired AutoConfig service in the Services console
B) Enable IEEE 802.1q Authentication in Network Interface Card Properties
C) Enable IEEE 802.1x Authentication in Network Interface Card Properties
D) Start the Wireless AutoConfig service in the Services console
E) Enable IEEE 802.3 Ethernet IPv6 in Network Interface Card Properties
A) Start the Wired AutoConfig service in the Services console
B) Enable IEEE 802.1q Authentication in Network Interface Card Properties
C) Enable IEEE 802.1x Authentication in Network Interface Card Properties
D) Start the Wireless AutoConfig service in the Services console
E) Enable IEEE 802.3 Ethernet IPv6 in Network Interface Card Properties

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
74
A network technician is building a network for a small office. The office currently has cable TV and now requires access to the Internet without adding any cabling other than what is already in place. Which of the following solutions should the technician install to meet these requirements?
A) DOCSIS modem
B) Wireless router
C) DSL modem
D) Access point
A) DOCSIS modem
B) Wireless router
C) DSL modem
D) Access point

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
75
A network administrator has a monitoring system in place that is currently polling hundreds of network devices at regular intervals. The continuous polling is causing high CPU utilization on the server. Which of the following tasks should the administrator perform to resolve the CPU issue while maintaining full monitoring capabilities?
A) Remove SNMP polling and configure SNMP traps on each network device
B) Remove SNMP polling and implement snmpwalk on each network device Remove SNMP polling and implement snmpwalk on each network device
C) Upgrade SNMP to the latest version to mitigate vulnerabilities
D) Modify SNMP polling to poll only during business hours
A) Remove SNMP polling and configure SNMP traps on each network device
B) Remove SNMP polling and implement snmpwalk on each network device Remove SNMP polling and implement snmpwalk on each network device
C) Upgrade SNMP to the latest version to mitigate vulnerabilities
D) Modify SNMP polling to poll only during business hours

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
76
Which of the following is a system of notation that uses base 16 rather than base 10?
A) Hex
B) Octal
C) Binary
D) CIDR
A) Hex
B) Octal
C) Binary
D) CIDR

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
77
A network administrator receives a call from the sales department requesting ports 20 and 21 be opened on the company's firewall to allow customers to retrieve a large file. Which of the following should the administrator perform BEFORE making the needed changes? (Choose two.)
A) Document the reason for the request
B) Scan the file for malware to protect the sales department's computers
C) Follow the company's approval process for the implementation
D) Install a TFTP server for the customers to use for the transfer
E) Create a honeypot to store the file on for the customers to use
F) Write the SLA for the sales department authorizing the change
A) Document the reason for the request
B) Scan the file for malware to protect the sales department's computers
C) Follow the company's approval process for the implementation
D) Install a TFTP server for the customers to use for the transfer
E) Create a honeypot to store the file on for the customers to use
F) Write the SLA for the sales department authorizing the change

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
78
Which of the following DNS records needs to be configured for SMTP traffic?
A) MX
B) CNAME
C) AAAA
D) PTR
A) MX
B) CNAME
C) AAAA
D) PTR

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
79
Users are reporting their network is extremely slow. The technician discovers pings to external host have excessive response times. However, internal pings to printers and other PCs have acceptable response times. Which of the following steps should the technician take NEXT?
A) Determine if any network equipment was replaced recently
B) Verify malware has not disabled the users' PC firewalls
C) Replace users' network cables with known-good network cables
D) Power cycle the web server
A) Determine if any network equipment was replaced recently
B) Verify malware has not disabled the users' PC firewalls
C) Replace users' network cables with known-good network cables
D) Power cycle the web server

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck
80
The IT manager at a small firm is in the process of renegotiating an SLA with the organization's ISP. As part of the agreement, the organization will agree to a dynamic bandwidth plan to provide 150Mbps of bandwidth. However, if the ISP determines that a host on the organization's internal network produces malicious traffic, the ISP reserves the right to reduce available bandwidth to 1.5 Mbps. Which of the following policies is being agreed to in the SLA?
A) Session hijacking
B) Blocking
C) Throttling
D) Data usage limits
E) Bandwidth quotas
A) Session hijacking
B) Blocking
C) Throttling
D) Data usage limits
E) Bandwidth quotas

Unlock Deck
Unlock for access to all 829 flashcards in this deck.
Unlock Deck
k this deck


