Exam 16: CompTIA Security+ 2021
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/129
Play
Full screen (f)
Exam 16: CompTIA Security+ 2021
1
A network administrator has been asked to install an IDS to improve the security posture of an organization. Which of the following control types is an IDS?
A) Corrective
B) Physical
C) Detective
D) Administrative
A) Corrective
B) Physical
C) Detective
D) Administrative
Detective
2
A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the company's data?
A) Containerization
B) Geofencing
C) Full-disk encryption
D) Remote wipe
A) Containerization
B) Geofencing
C) Full-disk encryption
D) Remote wipe
Full-disk encryption
3
An organization is developing an authentication service for use at the entry and exit ports of country borders. The service will use data feeds obtained from passport systems, passenger manifests, and high-definition video feeds from CCTV systems that are located at the ports. The service will incorporate machine-learning techniques to eliminate biometric enrollment processes while still allowing authorities to identify passengers with increasing accuracy over time. The more frequently passengers travel, the more accurately the service will identify them. Which of the following biometrics will MOST likely be used, without the need for enrollment? (Choose two.)
A) Voice
B) Gait
C) Vein
D) Facial
E) Retina
F) Fingerprint
A) Voice
B) Gait
C) Vein
D) Facial
E) Retina
F) Fingerprint
Gait
Facial
Facial
4
Which of the following should be put in place when negotiating with a new vendor about the timeliness of the response to a significant outage or incident?
A) MOU
B) MTTR
C) SLA
D) NDA
A) MOU
B) MTTR
C) SLA
D) NDA

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
5
An organization needs to implement more stringent controls over administrator/root credentials and service accounts. Requirements for the project include: Check-in/checkout of credentials The ability to use but not know the password Automated password changes Logging of access to credentials Which of the following solutions would meet the requirements?
A) OAuth 2.0
B) Secure Enclave
C) A privileged access management system
D) An OpenID Connect authentication system
A) OAuth 2.0
B) Secure Enclave
C) A privileged access management system
D) An OpenID Connect authentication system

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
6
A security analyst is reviewing a new website that will soon be made publicly available. The analyst sees the following in the URL: http://dev-site.comptia.org/home/show.php?sessionID=77276554&loc=us The analyst then sends an internal user a link to the new website for testing purposes, and when the user clicks the link, the analyst is able to browse the website with the following URL: http://dev-site.comptia.org/home/show.php?sessionID=98988475&loc=us Which of the following application attacks is being tested?
A) Pass-the-hash
B) Session replay
C) Object deference
D) Cross-site request forgery
A) Pass-the-hash
B) Session replay
C) Object deference
D) Cross-site request forgery

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
7
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
A) Monitoring large data transfer transactions in the firewall logs
B) Developing mandatory training to educate employees about the removable media policy
C) Implementing a group policy to block user access to system files
D) Blocking removable-media devices and write capabilities using a host-based security tool
A) Monitoring large data transfer transactions in the firewall logs
B) Developing mandatory training to educate employees about the removable media policy
C) Implementing a group policy to block user access to system files
D) Blocking removable-media devices and write capabilities using a host-based security tool

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
8
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events: 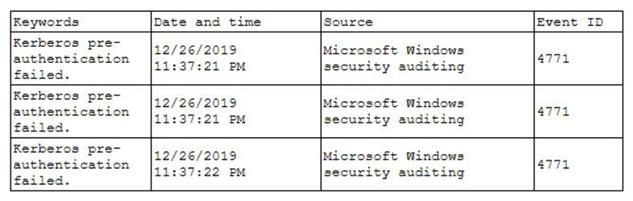 To better understand what is going on, the analyst runs a command and receives the following output:
To better understand what is going on, the analyst runs a command and receives the following output: 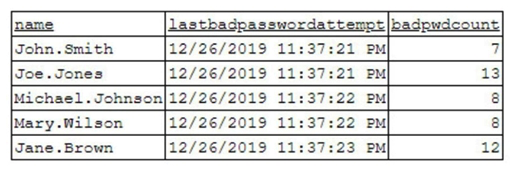 Based on the analyst's findings, which of the following attacks is being executed?
Based on the analyst's findings, which of the following attacks is being executed?
A) Credential harvesting
B) Keylogger
C) Brute-force
D) Spraying
 To better understand what is going on, the analyst runs a command and receives the following output:
To better understand what is going on, the analyst runs a command and receives the following output:  Based on the analyst's findings, which of the following attacks is being executed?
Based on the analyst's findings, which of the following attacks is being executed?A) Credential harvesting
B) Keylogger
C) Brute-force
D) Spraying

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
9
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message: 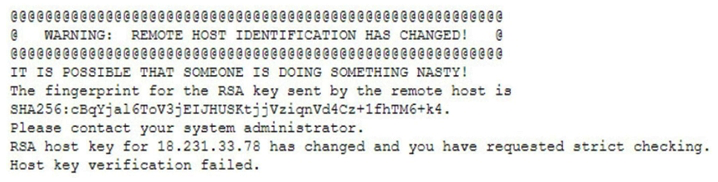 Which of the following network attacks is the researcher MOST likely experiencing?
Which of the following network attacks is the researcher MOST likely experiencing?
A) MAC cloning
B) Evil twin
C) Man-in-the-middle
D) ARP poisoning
 Which of the following network attacks is the researcher MOST likely experiencing?
Which of the following network attacks is the researcher MOST likely experiencing?A) MAC cloning
B) Evil twin
C) Man-in-the-middle
D) ARP poisoning

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
10
A RAT that was used to compromise an organization's banking credentials was found on a user's computer. The RAT evaded antivirus detection. It was installed by a user who has local administrator rights to the system as part of a remote management tool set. Which of the following recommendations would BEST prevent this from reoccurring?
A) Create a new acceptable use policy.
B) Segment the network into trusted and untrusted zones.
C) Enforce application whitelisting.
D) Implement DLP at the network boundary.
A) Create a new acceptable use policy.
B) Segment the network into trusted and untrusted zones.
C) Enforce application whitelisting.
D) Implement DLP at the network boundary.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
11
Which of the following will MOST likely adversely impact the operations of unpatched traditional programmable-logic controllers, running a back-end LAMP server and OT systems with human-management interfaces that are accessible over the Internet via a web interface? (Choose two.)
A) Cross-site scripting
B) Data exfiltration
C) Poor system logging
D) Weak encryption
E) SQL injection
F) Server-side request forgery
A) Cross-site scripting
B) Data exfiltration
C) Poor system logging
D) Weak encryption
E) SQL injection
F) Server-side request forgery

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
12
The CSIRT is reviewing the lessons learned from a recent incident. A worm was able to spread unhindered throughout the network and infect a large number of computers and servers. Which of the following recommendations would be BEST to mitigate the impacts of a similar incident in the future?
A) Install a NIDS device at the boundary.
B) Segment the network with firewalls.
C) Update all antivirus signatures daily.
D) Implement application blacklisting.
A) Install a NIDS device at the boundary.
B) Segment the network with firewalls.
C) Update all antivirus signatures daily.
D) Implement application blacklisting.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
13
A small company that does not have security staff wants to improve its security posture. Which of the following would BEST assist the company?
A) MSSP
B) SOAR
C) IaaS
D) PaaS
A) MSSP
B) SOAR
C) IaaS
D) PaaS

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
14
A security auditor is reviewing vulnerability scan data provided by an internal security team. Which of the following BEST indicates that valid credentials were used?
A) The scan results show open ports, protocols, and services exposed on the target host
B) The scan enumerated software versions of installed programs
C) The scan produced a list of vulnerabilities on the target host
D) The scan identified expired SSL certificates
A) The scan results show open ports, protocols, and services exposed on the target host
B) The scan enumerated software versions of installed programs
C) The scan produced a list of vulnerabilities on the target host
D) The scan identified expired SSL certificates

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
15
Several employees return to work the day after attending an industry trade show. That same day, the security manager notices several malware alerts coming from each of the employee's workstations. The security manager investigates but finds no signs of an attack on the perimeter firewall or the NIDS. Which of the following is MOST likely causing the malware alerts?
A) A worm that has propagated itself across the intranet, which was initiated by presentation media
B) A fileless virus that is contained on a vCard that is attempting to execute an attack
C) A Trojan that has passed through and executed malicious code on the hosts
D) A USB flash drive that is trying to run malicious code but is being blocked by the host firewall
A) A worm that has propagated itself across the intranet, which was initiated by presentation media
B) A fileless virus that is contained on a vCard that is attempting to execute an attack
C) A Trojan that has passed through and executed malicious code on the hosts
D) A USB flash drive that is trying to run malicious code but is being blocked by the host firewall

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
A) SSAE SOC 2
B) PCI DSS
C) GDPR
D) ISO 31000
A) SSAE SOC 2
B) PCI DSS
C) GDPR
D) ISO 31000

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
17
A security administrator suspects an employee has been emailing proprietary information to a competitor. Company policy requires the administrator to capture an exact copy of the employee's hard disk. Which of the following should the administrator use?
A) dd
B) chmod
C) dnsenum
D) logger
A) dd
B) chmod
C) dnsenum
D) logger

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
18
A network administrator needs to build out a new datacenter, with a focus on resiliency and uptime. Which of the following would BEST meet this objective? (Choose two.)
A) Dual power supply
B) Off-site backups
C) Automatic OS upgrades
D) NIC teaming
E) Scheduled penetration testing
F) Network-attached storage
A) Dual power supply
B) Off-site backups
C) Automatic OS upgrades
D) NIC teaming
E) Scheduled penetration testing
F) Network-attached storage

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
19
Which of the following cloud models provides clients with servers, storage, and networks but nothing else?
A) SaaS
B) PaaS
C) IaaS
D) DaaS
A) SaaS
B) PaaS
C) IaaS
D) DaaS

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
20
A network engineer needs to build a solution that will allow guests at the company's headquarters to access the Internet via WiFi. This solution should not allow access to the internal corporate network, but it should require guests to sign off on the acceptable use policy before accessing the Internet. Which of the following should the engineer employ to meet these requirements?
A) Implement open PSK on the APs
B) Deploy a WAF
C) Configure WIPS on the APs
D) Install a captive portal
A) Implement open PSK on the APs
B) Deploy a WAF
C) Configure WIPS on the APs
D) Install a captive portal

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
21
A recently discovered zero-day exploit utilizes an unknown vulnerability in the SMB network protocol to rapidly infect computers. Once infected, computers are encrypted and held for ransom. Which of the following would BEST prevent this attack from reoccurring?
A) Configure the perimeter firewall to deny inbound external connections to SMB ports.
B) Ensure endpoint detection and response systems are alerting on suspicious SMB connections.
C) Deny unauthenticated users access to shared network folders.
D) Verify computers are set to install monthly operating system, updates automatically.
A) Configure the perimeter firewall to deny inbound external connections to SMB ports.
B) Ensure endpoint detection and response systems are alerting on suspicious SMB connections.
C) Deny unauthenticated users access to shared network folders.
D) Verify computers are set to install monthly operating system, updates automatically.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
22
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
A) A script kiddie
B) Shadow IT
C) Hacktivism
D) White-hat
A) A script kiddie
B) Shadow IT
C) Hacktivism
D) White-hat

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
23
A user contacts the help desk to report the following: Two days ago, a pop-up browser window prompted the user for a name and password after connecting to the corporate wireless SSID. This had never happened before, but the user entered the information as requested. The user was able to access the Internet but had trouble accessing the department share until the next day. The user is now getting notifications from the bank about unauthorized transactions. Which of the following attack vectors was MOST likely used in this scenario?
A) Rogue access point
B) Evil twin
C) DNS poisoning
D) ARP poisoning
A) Rogue access point
B) Evil twin
C) DNS poisoning
D) ARP poisoning

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
24
A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory. Which of the following is the analyst doing?
A) A packet capture
B) A user behavior analysis
C) Threat hunting
D) Credentialed vulnerability scanning
A) A packet capture
B) A user behavior analysis
C) Threat hunting
D) Credentialed vulnerability scanning

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
25
An organization with a low tolerance for user inconvenience wants to protect laptop hard drives against loss or data theft. Which of the following would be the MOST acceptable?
A) SED
B) HSM
C) DLP
D) TPM
A) SED
B) HSM
C) DLP
D) TPM

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
26
An employee has been charged with fraud and is suspected of using corporate assets. As authorities collect evidence, and to preserve the admissibility of the evidence, which of the following forensic techniques should be used?
A) Order of volatility
B) Data recovery
C) Chain of custody
D) Non-repudiation
A) Order of volatility
B) Data recovery
C) Chain of custody
D) Non-repudiation

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
27
An analyst needs to identify the applications a user was running and the files that were open before the user's computer was shut off by holding down the power button. Which of the following would MOST likely contain that information?
A) NGFW
B) Pagefile
C) NetFlow
D) RAM
A) NGFW
B) Pagefile
C) NetFlow
D) RAM

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
28
A university with remote campuses, which all use different service providers, loses Internet connectivity across all locations. After a few minutes, Internet and VoIP services are restored, only to go offline again at random intervals, typically within four minutes of services being restored. Outages continue throughout the day, impacting all inbound and outbound connections and services. Services that are limited to the local LAN or WiFi network are not impacted, but all WAN and VoIP services are affected. Later that day, the edge-router manufacturer releases a CVE outlining the ability of an attacker to exploit the SIP protocol handling on devices, leading to resource exhaustion and system reloads. Which of the following BEST describe this type of attack? (Choose two.)
A) DoS
B) SSL stripping
C) Memory leak
D) Race condition
E) Shimming
F) Refactoring
A) DoS
B) SSL stripping
C) Memory leak
D) Race condition
E) Shimming
F) Refactoring

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following is the purpose of a risk register?
A) To define the level or risk using probability and likelihood
B) To register the risk with the required regulatory agencies
C) To identify the risk, the risk owner, and the risk measures
D) To formally log the type of risk mitigation strategy the organization is using
A) To define the level or risk using probability and likelihood
B) To register the risk with the required regulatory agencies
C) To identify the risk, the risk owner, and the risk measures
D) To formally log the type of risk mitigation strategy the organization is using

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
30
An organization is developing a plan in the event of a complete loss of critical systems and data. Which of the following plans is the organization MOST likely developing?
A) Incident response
B) Communications
C) Disaster recovery
D) Data retention
A) Incident response
B) Communications
C) Disaster recovery
D) Data retention

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
31
A company provides mobile devices to its users to permit access to email and enterprise applications. The company recently started allowing users to select from several different vendors and device models. When configuring the MDM, which of the following is a key security implication of this heterogeneous device approach?
A) The most common set of MDM configurations will become the effective set of enterprise mobile security controls.
B) All devices will need to support SCEP-based enrollment; therefore, the heterogeneity of the chosen architecture may unnecessarily expose private keys to adversaries.
C) Certain devices are inherently less secure than others, so compensatory controls will be needed to address the delta between device vendors.
D) MDMs typically will not support heterogeneous deployment environments, so multiple MDMs will need to be installed and configured.
A) The most common set of MDM configurations will become the effective set of enterprise mobile security controls.
B) All devices will need to support SCEP-based enrollment; therefore, the heterogeneity of the chosen architecture may unnecessarily expose private keys to adversaries.
C) Certain devices are inherently less secure than others, so compensatory controls will be needed to address the delta between device vendors.
D) MDMs typically will not support heterogeneous deployment environments, so multiple MDMs will need to be installed and configured.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
32
To secure an application after a large data breach, an e-commerce site will be resetting all users' credentials. Which of the following will BEST ensure the site's users are not compromised after the reset?
A) A password reuse policy
B) Account lockout after three failed attempts
C) Encrypted credentials in transit
D) A geofencing policy based on login history
A) A password reuse policy
B) Account lockout after three failed attempts
C) Encrypted credentials in transit
D) A geofencing policy based on login history

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
33
Joe, an employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm Joe's identity before sending him the prize. Which of the following BEST describes this type of email?
A) Spear phishing
B) Whaling
C) Phishing
D) Vishing
A) Spear phishing
B) Whaling
C) Phishing
D) Vishing

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
34
A Chief Security Officer (CSO) is concerned about the amount of PII that is stored locally on each salesperson's laptop. The sales department has a higher-than-average rate of lost equipment. Which of the following recommendations would BEST address the CSO's concern?
A) Deploy an MDM solution.
B) Implement managed FDE.
C) Replace all hard drives with SEDs.
D) Install DLP agents on each laptop.
A) Deploy an MDM solution.
B) Implement managed FDE.
C) Replace all hard drives with SEDs.
D) Install DLP agents on each laptop.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
35
In which of the following common use cases would steganography be employed?
A) Obfuscation
B) Integrity
C) Non-repudiation
D) Blockchain
A) Obfuscation
B) Integrity
C) Non-repudiation
D) Blockchain

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
36
A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform?
A) PCI DSS
B) ISO 22301
C) ISO 27001
D) NIST CSF
A) PCI DSS
B) ISO 22301
C) ISO 27001
D) NIST CSF

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
37
An organization wants to implement a third factor to an existing multifactor authentication. The organization already uses a smart card and password. Which of the following would meet the organization's needs for a third factor?
A) Date of birth
B) Fingerprints
C) PIN
D) TPM
A) Date of birth
B) Fingerprints
C) PIN
D) TPM

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following refers to applications and systems that are used within an organization without consent or approval?
A) Shadow IT
B) OSINT
C) Dark web
D) Insider threats
A) Shadow IT
B) OSINT
C) Dark web
D) Insider threats

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
39
In which of the following situations would it be BEST to use a detective control type for mitigation?
A) A company implemented a network load balancer to ensure 99.999% availability of its web application.
B) A company designed a backup solution to increase the chances of restoring services in case of a natural disaster.
C) A company purchased an application-level firewall to isolate traffic between the accounting department and the information technology department.
D) A company purchased an IPS system, but after reviewing the requirements, the appliance was supposed to monitor, not block, any traffic.
E) A company purchased liability insurance for flood protection on all capital assets.
A) A company implemented a network load balancer to ensure 99.999% availability of its web application.
B) A company designed a backup solution to increase the chances of restoring services in case of a natural disaster.
C) A company purchased an application-level firewall to isolate traffic between the accounting department and the information technology department.
D) A company purchased an IPS system, but after reviewing the requirements, the appliance was supposed to monitor, not block, any traffic.
E) A company purchased liability insurance for flood protection on all capital assets.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
40
Which of the following would MOST likely support the integrity of a voting machine?
A) Asymmetric encryption
B) Blockchain
C) Transport Layer Security
D) Perfect forward secrecy
A) Asymmetric encryption
B) Blockchain
C) Transport Layer Security
D) Perfect forward secrecy

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
41
A document that appears to be malicious has been discovered in an email that was sent to a company's Chief Financial Officer (CFO). Which of the following would be BEST to allow a security analyst to gather information and confirm it is a malicious document without executing any code it may contain?
A) Open the document on an air-gapped network.
B) View the document's metadata for origin clues.
C) Search for matching file hashes on malware websites.
D) Detonate the document in an analysis sandbox.
A) Open the document on an air-gapped network.
B) View the document's metadata for origin clues.
C) Search for matching file hashes on malware websites.
D) Detonate the document in an analysis sandbox.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
42
An organization has a growing workforce that is mostly driven by additions to the sales department. Each newly hired salesperson relies on a mobile device to conduct business. The Chief Information Officer (CIO) is wondering if the organization may need to scale down just as quickly as it scaled up. The CIO is also concerned about the organization's security and customer privacy. Which of the following would be BEST to address the CIO's concerns?
A) Disallow new hires from using mobile devices for six months.
B) Select four devices for the sales department to use in a CYOD model.
C) Implement BYOD for the sales department while leveraging the MDM.
D) Deploy mobile devices using the COPE methodology.
A) Disallow new hires from using mobile devices for six months.
B) Select four devices for the sales department to use in a CYOD model.
C) Implement BYOD for the sales department while leveraging the MDM.
D) Deploy mobile devices using the COPE methodology.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
43
A cybersecurity administrator has a reduced team and needs to operate an on-premises network and security infrastructure efficiently. To help with the situation, the administrator decides to hire a service provider. Which of the following should the administrator use?
A) SDP
B) AAA
C) IaaS
D) MSSP
E) Microservices
A) SDP
B) AAA
C) IaaS
D) MSSP
E) Microservices

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
44
A public relations team will be taking a group of guests on a tour through the facility of a large e-commerce company. The day before the tour, the company sends out an email to employees to ensure all whiteboards are cleaned and all desks are cleared. The company is MOST likely trying to protect against:
A) loss of proprietary information.
B) damage to the company's reputation.
C) social engineering.
D) credential exposure.
A) loss of proprietary information.
B) damage to the company's reputation.
C) social engineering.
D) credential exposure.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
45
Which of the following ISO standards is certified for privacy?
A) ISO 9001
B) ISO 27002
C) ISO 27701
D) ISO 31000
A) ISO 9001
B) ISO 27002
C) ISO 27701
D) ISO 31000

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
46
A security analyst is performing a forensic investigation involving compromised account credentials. Using the Event Viewer, the analyst was able to detect the following message: "Special privileges assigned to new logon." Several of these messages did not have a valid logon associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
A) Pass-the-hash
B) Buffer overflow
C) Cross-site scripting
D) Session replay
A) Pass-the-hash
B) Buffer overflow
C) Cross-site scripting
D) Session replay

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
47
The manager who is responsible for a data set has asked a security engineer to apply encryption to the data on a hard disk. The security engineer is an example of a:
A) data controller.
B) data owner.
C) data custodian.
D) data processor.
A) data controller.
B) data owner.
C) data custodian.
D) data processor.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
48
A security assessment determines DES and 3DES are still being used on recently deployed production servers. Which of the following did the assessment identify?
A) Unsecure protocols
B) Default settings
C) Open permissions
D) Weak encryption
A) Unsecure protocols
B) Default settings
C) Open permissions
D) Weak encryption

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
49
A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants to ensure it does not happen again. Which of the following should the IT administrator do FIRST after recovery?
A) Scan the NAS for residual or dormant malware and take new daily backups that are tested on a frequent basis.
B) Restrict administrative privileges and patch all systems and applications.
C) Rebuild all workstations and install new antivirus software.
D) Implement application whitelisting and perform user application hardening.
A) Scan the NAS for residual or dormant malware and take new daily backups that are tested on a frequent basis.
B) Restrict administrative privileges and patch all systems and applications.
C) Rebuild all workstations and install new antivirus software.
D) Implement application whitelisting and perform user application hardening.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
50
An organization is concerned that its hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities?
A) hping3 -S comptia.org -p 80
B) nc -l -v comptia.org -p 80
C) nmap comptia.org -p 80 -sV
D) nslookup -port=80 comptia.org
A) hping3 -S comptia.org -p 80
B) nc -l -v comptia.org -p 80
C) nmap comptia.org -p 80 -sV
D) nslookup -port=80 comptia.org

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
51
During an incident response, a security analyst observes the following log entry on the web server:  Which of the following BEST describes the type of attack the analyst is experiencing?
Which of the following BEST describes the type of attack the analyst is experiencing?
A) SQL injection
B) Cross-site scripting
C) Pass-the-hash
D) Directory traversal
 Which of the following BEST describes the type of attack the analyst is experiencing?
Which of the following BEST describes the type of attack the analyst is experiencing?A) SQL injection
B) Cross-site scripting
C) Pass-the-hash
D) Directory traversal

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following would be the BEST method for creating a detailed diagram of wireless access points and hotspots?
A) Footprinting
B) White-box testing
C) A drone/UAV
D) Pivoting
A) Footprinting
B) White-box testing
C) A drone/UAV
D) Pivoting

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
53
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be BEST to help the organization's executives determine their next course of action?
A) An incident response plan
B) A communications plan
C) A disaster recovery plan
D) A business continuity plan
A) An incident response plan
B) A communications plan
C) A disaster recovery plan
D) A business continuity plan

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
54
After entering a username and password, an administrator must draw a gesture on a touch screen. Which of the following demonstrates what the administrator is providing?
A) Multifactor authentication
B) Something you can do
C) Biometrics
D) Two-factor authentication
A) Multifactor authentication
B) Something you can do
C) Biometrics
D) Two-factor authentication

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
55
A security analyst is running a vulnerability scan to check for missing patches during a suspected security incident. During which of the following phases of the response process is this activity MOST likely occurring?
A) Containment
B) Identification
C) Recovery
D) Preparation
A) Containment
B) Identification
C) Recovery
D) Preparation

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
56
A network administrator would like to configure a site-to-site VPN utilizing IPsec. The administrator wants the tunnel to be established with data integrity, encryption, authentication, and anti-replay functions. Which of the following should the administrator use when configuring the VPN?
A) AH
B) EDR
C) ESP
D) DNSSEC
A) AH
B) EDR
C) ESP
D) DNSSEC

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
57
A company has limited storage space available and an online presence that cannot be down for more than four hours. Which of the following backup methodologies should the company implement to allow for the FASTEST database restore time in the event of a failure, while being mindful of the limited available storage space?
A) Implement full tape backups every Sunday at 8:00 p.m. and perform nightly tape rotations.
B) Implement differential backups every Sunday at 8:00 p.m. and nightly incremental backups at 8:00 p.m.
C) Implement nightly full backups every Sunday at 8:00 p.m.
D) Implement full backups every Sunday at 8:00 p.m. and nightly differential backups at 8:00 p.m.
A) Implement full tape backups every Sunday at 8:00 p.m. and perform nightly tape rotations.
B) Implement differential backups every Sunday at 8:00 p.m. and nightly incremental backups at 8:00 p.m.
C) Implement nightly full backups every Sunday at 8:00 p.m.
D) Implement full backups every Sunday at 8:00 p.m. and nightly differential backups at 8:00 p.m.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
58
Under GDPR, which of the following is MOST responsible for the protection of privacy and website user rights?
A) The data protection officer
B) The data processor
C) The data owner
D) The data controller
A) The data protection officer
B) The data processor
C) The data owner
D) The data controller

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
59
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Choose two.)
A) Something you know
B) Something you have
C) Somewhere you are
D) Someone you know
E) Something you are
F) Something you can do
A) Something you know
B) Something you have
C) Somewhere you are
D) Someone you know
E) Something you are
F) Something you can do

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
60
Which of the following describes the BEST approach for deploying application patches?
A) Apply the patches to systems in a testing environment, then to systems in a staging environment, and finally to production systems.
B) Test the patches in a staging environment, develop against them in the development environment, and then apply them to the production systems.
C) Test the patches in a test environment, apply them to the production systems, and then apply them to a staging environment.
D) Apply the patches to the production systems, apply them in a staging environment, and then test all of them in a testing environment.
A) Apply the patches to systems in a testing environment, then to systems in a staging environment, and finally to production systems.
B) Test the patches in a staging environment, develop against them in the development environment, and then apply them to the production systems.
C) Test the patches in a test environment, apply them to the production systems, and then apply them to a staging environment.
D) Apply the patches to the production systems, apply them in a staging environment, and then test all of them in a testing environment.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
61
A company uses wireless for all laptops and keeps a very detailed record of its assets, along with a comprehensive list of devices that are authorized to be on the wireless network. The Chief Information Officer (CIO) is concerned about a script kiddie potentially using an unauthorized device to brute force the wireless PSK and obtain access to the internal network. Which of the following should the company implement to BEST prevent this from occurring?
A) A BPDU guard
B) WPA-EAP
C) IP filtering
D) A WIDS
A) A BPDU guard
B) WPA-EAP
C) IP filtering
D) A WIDS

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
62
A security engineer is reviewing log files after a third party discovered usernames and passwords for the organization's accounts. The engineer sees there was a change in the IP address for a vendor website one week earlier. This change lasted eight hours. Which of the following attacks was MOST likely used?
A) Man-in-the-middle
B) Spear phishing
C) Evil twin
D) DNS poisoning
A) Man-in-the-middle
B) Spear phishing
C) Evil twin
D) DNS poisoning

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
63
Which of the following are requirements that must be configured for PCI DSS compliance? (Choose two.)
A) Testing security systems and processes regularly
B) Installing and maintaining a web proxy to protect cardholder data
C) Assigning a unique ID to each person with computer access
D) Encrypting transmission of cardholder data across private networks
E) Benchmarking security awareness training for contractors
F) Using vendor-supplied default passwords for system passwords
A) Testing security systems and processes regularly
B) Installing and maintaining a web proxy to protect cardholder data
C) Assigning a unique ID to each person with computer access
D) Encrypting transmission of cardholder data across private networks
E) Benchmarking security awareness training for contractors
F) Using vendor-supplied default passwords for system passwords

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
64
A Chief Information Security Officer (CISO) is concerned about the organization's ability to continue business operations in the event of a prolonged DDoS attack on its local datacenter that consumes database resources. Which of the following will the CISO MOST likely recommend to mitigate this risk?
A) Upgrade the bandwidth available into the datacenter.
B) Implement a hot-site failover location.
C) Switch to a complete SaaS offering to customers.
D) Implement a challenge response test on all end-user queries.
A) Upgrade the bandwidth available into the datacenter.
B) Implement a hot-site failover location.
C) Switch to a complete SaaS offering to customers.
D) Implement a challenge response test on all end-user queries.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
65
A network administrator is setting up wireless access points in all the conference rooms and wants to authenticate devices using PKI. Which of the following should the administrator configure?
A) A captive portal
B) PSK
C) 802.1X
D) WPS
A) A captive portal
B) PSK
C) 802.1X
D) WPS

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
66
A company is designing the layout of a new datacenter so it will have an optimal environmental temperature. Which of the following must be included? (Choose two.)
A) An air gap
B) A cold aisle
C) Removable doors
D) A hot aisle
E) An IoT thermostat
F) A humidity monitor
A) An air gap
B) A cold aisle
C) Removable doors
D) A hot aisle
E) An IoT thermostat
F) A humidity monitor

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
67
Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario?
A) Watering-hole attack
B) Credential harvesting
C) Hybrid warfare
D) Pharming
A) Watering-hole attack
B) Credential harvesting
C) Hybrid warfare
D) Pharming

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
68
An organization has hired a security analyst to perform a penetration test. The analyst captures 1Gb worth of inbound network traffic to the server and transfers the pcap back to the machine for analysis. Which of the following tools should the analyst use to further review the pcap?
A) Nmap
B) cURL
C) Netcat
D) Wireshark
A) Nmap
B) cURL
C) Netcat
D) Wireshark

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
69
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements: The devices will be used internationally by staff who travel extensively. Occasional personal use is acceptable due to the travel requirements. Users must be able to install and configure sanctioned programs and productivity suites. The devices must be encrypted. The devices must be capable of operating in low-bandwidth environments. Which of the following would provide the GREATEST benefit to the security posture of the devices?
A) Configuring an always-on VPN
B) Implementing application whitelisting
C) Requiring web traffic to pass through the on-premises content filter
D) Setting the antivirus DAT update schedule to weekly
A) Configuring an always-on VPN
B) Implementing application whitelisting
C) Requiring web traffic to pass through the on-premises content filter
D) Setting the antivirus DAT update schedule to weekly

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
70
A security analyst has received an alert about PII being sent via email. The analyst's Chief Information Security Officer (CISO) has made it clear that PII must be handled with extreme care. From which of the following did the alert MOST likely originate?
A) S/MIME
B) DLP
C) IMAP
D) HIDS
A) S/MIME
B) DLP
C) IMAP
D) HIDS

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
71
A company recently moved sensitive videos between on-premises, company-owned websites. The company then learned the videos had been uploaded and shared to the Internet. Which of the following would MOST likely allow the company to find the cause?
A) Checksums
B) Watermarks
C) Order of volatility
D) A log analysis
E) A right-to-audit clause
A) Checksums
B) Watermarks
C) Order of volatility
D) A log analysis
E) A right-to-audit clause

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
72
A vulnerability assessment report will include the CVSS score of the discovered vulnerabilities because the score allows the organization to better:
A) validate the vulnerability exists in the organization's network through penetration testing.
B) research the appropriate mitigation techniques in a vulnerability database.
C) find the software patches that are required to mitigate a vulnerability.
D) prioritize remediation of vulnerabilities based on the possible impact.
A) validate the vulnerability exists in the organization's network through penetration testing.
B) research the appropriate mitigation techniques in a vulnerability database.
C) find the software patches that are required to mitigate a vulnerability.
D) prioritize remediation of vulnerabilities based on the possible impact.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
73
A user received an SMS on a mobile phone that asked for bank details. Which of the following social-engineering techniques was used in this case?
A) SPIM
B) Vishing
C) Spear phishing
D) Smishing
A) SPIM
B) Vishing
C) Spear phishing
D) Smishing

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
74
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has been given all the developer's documentation about the internal architecture. Which of the following BEST represents the type of testing that will occur?
A) Bug bounty
B) White-box
C) Black-box
D) Gray-box
A) Bug bounty
B) White-box
C) Black-box
D) Gray-box

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
75
The SOC is reviewing processes and procedures after a recent incident. The review indicates it took more than 30 minutes to determine that quarantining an infected host was the best course of action. This allowed the malware to spread to additional hosts before it was contained. Which of the following would be BEST to improve the incident response process?
A) Updating the playbooks with better decision points
B) Dividing the network into trusted and untrusted zones
C) Providing additional end-user training on acceptable use
D) Implementing manual quarantining of infected hosts
A) Updating the playbooks with better decision points
B) Dividing the network into trusted and untrusted zones
C) Providing additional end-user training on acceptable use
D) Implementing manual quarantining of infected hosts

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
76
A security incident may have occurred on the desktop PC of an organization's Chief Executive Officer (CEO). A duplicate copy of the CEO's hard drive must be stored securely to ensure appropriate forensic processes and the chain of custody are followed. Which of the following should be performed to accomplish this task?
A) Install a new hard drive in the CEO's PC, and then remove the old hard drive and place it in a tamper-evident bag.
B) Connect a write blocker to the hard drive. Then, leveraging a forensic workstation, utilize the dd command in a live Linux environment to create a duplicate copy. Connect a write blocker to the hard drive. Then, leveraging a forensic workstation, utilize the dd command in a live Linux environment to create a duplicate copy.
C) Remove the CEO's hard drive from the PC, connect to the forensic workstation, and copy all the contents onto a remote fileshare while the CEO watches.
D) Refrain from completing a forensic analysis of the CEO's hard drive until after the incident is confirmed; duplicating the hard drive at this stage could destroy evidence.
A) Install a new hard drive in the CEO's PC, and then remove the old hard drive and place it in a tamper-evident bag.
B) Connect a write blocker to the hard drive. Then, leveraging a forensic workstation, utilize the dd command in a live Linux environment to create a duplicate copy. Connect a write blocker to the hard drive. Then, leveraging a forensic workstation, utilize the dd command in a live Linux environment to create a duplicate copy.
C) Remove the CEO's hard drive from the PC, connect to the forensic workstation, and copy all the contents onto a remote fileshare while the CEO watches.
D) Refrain from completing a forensic analysis of the CEO's hard drive until after the incident is confirmed; duplicating the hard drive at this stage could destroy evidence.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
77
Which of the following will provide the BEST physical security countermeasures to stop intruders? (Choose two.)
A) Alarms
B) Signage
C) Lighting
D) Mantraps
E) Fencing
F) Sensors
A) Alarms
B) Signage
C) Lighting
D) Mantraps
E) Fencing
F) Sensors

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
78
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site. Upon investigation, a security analyst identifies the following: The legitimate website's IP address is 10.1.1.20 and eRecruit.local resolves to this IP. The forged website's IP address appears to be 10.2.12.99, based on NetFlow records. All three of the organization's DNS servers show the website correctly resolves to the legitimate IP. DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise. Which of the following MOST likely occurred?
A) A reverse proxy was used to redirect network traffic.
B) An SSL strip MITM attack was performed.
C) An attacker temporarily poisoned a name server.
D) An ARP poisoning attack was successfully executed.
A) A reverse proxy was used to redirect network traffic.
B) An SSL strip MITM attack was performed.
C) An attacker temporarily poisoned a name server.
D) An ARP poisoning attack was successfully executed.

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
79
A local coffee shop runs a small WiFi hotspot for its customers that utilizes WPA2-PSK. The coffee shop would like to stay current with security trends and wants to implement WPA3 to make its WiFi even more secure. Which of the following technologies will the coffee shop MOST likely use in place of PSK?
A) WEP
B) MSCHAP
C) WPS
D) SAE
A) WEP
B) MSCHAP
C) WPS
D) SAE

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck
80
Which of the following is a team of people dedicated to testing the effectiveness of organizational security programs by emulating the techniques of potential attackers?
A) Red team
B) White team
C) Blue team
D) Purple team
A) Red team
B) White team
C) Blue team
D) Purple team

Unlock Deck
Unlock for access to all 129 flashcards in this deck.
Unlock Deck
k this deck


