Exam 3: EC-Council Information Security Manager (E|ISM)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/131
Play
Full screen (f)
Exam 3: EC-Council Information Security Manager (E|ISM)
1
After passively scanning the network of Department of Defense (DoD), you switch over to active scanning to identify live hosts on their network. DoD is a large organization and should respond to any number of scans. You start an ICMP ping sweep by sending an IP packet to the broadcast address. Only five hosts respond to your ICMP pings; definitely not the number of hosts you were expecting. Why did this ping sweep only produce a few responses?
A) Only IBM AS/400 will reply to this scan
B) Only Windows systems will reply to this scan
C) A switched network will not respond to packets sent to the broadcast address
D) Only Unix and Unix-like systems will reply to this scan
A) Only IBM AS/400 will reply to this scan
B) Only Windows systems will reply to this scan
C) A switched network will not respond to packets sent to the broadcast address
D) Only Unix and Unix-like systems will reply to this scan
D
2
In a virtual test environment, Michael is testing the strength and security of BGP using multiple routers to mimic the backbone of the Internet. This project will help him write his doctoral thesis on "bringing down the Internet". Without sniffing the traffic between the routers, Michael sends millions of RESET packets to the routers in an attempt to shut one or all of them down. After a few hours, one of the routers finally shuts itself down. What will the other routers communicate between themselves?
A) The change in the routing fabric to bypass the affected router
B) More RESET packets to the affected router to get it to power back up
C) RESTART packets to the affected router to get it to power back up
D) STOP packets to all other routers warning of where the attack originated
A) The change in the routing fabric to bypass the affected router
B) More RESET packets to the affected router to get it to power back up
C) RESTART packets to the affected router to get it to power back up
D) STOP packets to all other routers warning of where the attack originated
A
3
A small law firm located in the Midwest has possibly been breached by a computer hacker looking to obtain information on their clientele. The law firm does not have any on-site IT employees, but wants to search for evidence of the breach themselves to prevent any possible media attention. Why would this not be recommended?
A) Searching for evidence themselves would not have any ill effects
B) Searching could possibly crash the machine or device
C) Searching creates cache files, which would hinder the investigation
D) Searching can change date/time stamps
A) Searching for evidence themselves would not have any ill effects
B) Searching could possibly crash the machine or device
C) Searching creates cache files, which would hinder the investigation
D) Searching can change date/time stamps
D
4
How many possible sequence number combinations are there in TCP/IP protocol?
A) 1 billion
B) 320 billion
C) 4 billion
D) 32 million
A) 1 billion
B) 320 billion
C) 4 billion
D) 32 million

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
5
Julia is a senior security analyst for Berber Consulting group. She is currently working on a contract for a small accounting firm in Florid a. They have given her permission to perform social engineering attacks on the company to see if their in-house training did any good. Julia calls the main number for the accounting firm and talks to the receptionist. Julia says that she is an IT technician from the company's main office in Iowa. She states that she needs the receptionist's network username and password to troubleshoot a problem they are having. Julia says that Bill Hammond, the CEO of the company, requested this information. After hearing the name of the CEO, the receptionist gave Julia all the information she asked for. What principal of social engineering did Julia use?
A) Social Validation
B) Scarcity
C) Friendship/Liking
D) Reciprocation
A) Social Validation
B) Scarcity
C) Friendship/Liking
D) Reciprocation

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
6
If a PDA is seized in an investigation while the device is turned on, what would be the proper procedure?
A) Keep the device powered on
B) Turn off the device immediately
C) Remove the battery immediately
D) Remove any memory cards immediately
A) Keep the device powered on
B) Turn off the device immediately
C) Remove the battery immediately
D) Remove any memory cards immediately

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
7
You are the security analyst working for a private company out of France. Your current assignment is to obtain credit card information from a Swiss bank owned by that company. After initial reconnaissance, you discover that the bank security defenses are very strong and would take too long to penetrate. You decide to get the information by monitoring the traffic between the bank and one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of FTP packets traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What tool could you use to get this information?
A) Airsnort
B) Snort
C) Ettercap
D) RaidSniff
A) Airsnort
B) Snort
C) Ettercap
D) RaidSniff

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
8
As a security analyst, you setup a false survey website that will require users to create a username and a strong password. You send the link to all the employees of the company. What information will you be able to gather?
A) The IP address of the employees' computers
B) Bank account numbers and the corresponding routing numbers
C) The employees network usernames and passwords
D) The MAC address of the employees' computers
A) The IP address of the employees' computers
B) Bank account numbers and the corresponding routing numbers
C) The employees network usernames and passwords
D) The MAC address of the employees' computers

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
9
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
A) Computers on his wired network
B) Satellite television
C) 2.4Ghz Cordless phones
D) CB radio
A) Computers on his wired network
B) Satellite television
C) 2.4Ghz Cordless phones
D) CB radio

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
10
What feature of Decryption Collection allows an investigator to crack a password as quickly as possible?
A) Cracks every password in 10 minutes
B) Distribute processing over 16 or fewer computers
C) Support for Encrypted File System
D) Support for MD5 hash verification
A) Cracks every password in 10 minutes
B) Distribute processing over 16 or fewer computers
C) Support for Encrypted File System
D) Support for MD5 hash verification

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
11
How many bits is Source Port Number in TCP Header packet?
A) 16
B) 32
C) 48
D) 64
A) 16
B) 32
C) 48
D) 64

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
12
Your company's network just finished going through a SAS 70 audit. This audit reported that overall, your network is secure, but there are some areas that needs improvement. The major area was SNMP security. The audit company recommended turning off SNMP, but that is not an option since you have so many remote nodes to keep track of. What step could you take to help secure SNMP on your network?
A) Block all internal MAC address from using SNMP
B) Block access to UDP port 171
C) Block access to TCP port 171
D) Change the default community string names
A) Block all internal MAC address from using SNMP
B) Block access to UDP port 171
C) Block access to TCP port 171
D) Change the default community string names

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
13
When making the preliminary investigations in a sexual harassment case, how many investigators are you recommended having?
A) One
B) Two
C) Three
D) Four
A) One
B) Two
C) Three
D) Four

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
14
Harold wants to set up a firewall on his network but is not sure which one would be the most appropriate. He knows he needs to allow FTP traffic to one of the servers on his network, but he wants to only allow FTP-PUT. Which firewall would be most appropriate for Harold? needs?
A) Circuit-level proxy firewall
B) Packet filtering firewall
C) Application-level proxy firewall
D) Data link layer firewall
A) Circuit-level proxy firewall
B) Packet filtering firewall
C) Application-level proxy firewall
D) Data link layer firewall

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
15
Daryl, a computer forensics investigator, has just arrived at the house of an alleged computer hacker. Daryl takes pictures and tags all computer and peripheral equipment found in the house. Daryl packs all the items found in his van and takes them back to his lab for further examination. At his lab, Michael his assistant helps him with the investigation. Since Michael is still in training, Daryl supervises all of his work very carefully. Michael is not quite sure about the procedures to copy all the data off the computer and peripheral devices. How many data acquisition tools should Michael use when creating copies of the evidence for the investigation?
A) Two
B) One
C) Three
D) Four
A) Two
B) One
C) Three
D) Four

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
16
What does ICMP Type 3/Code 13 mean?
A) Host Unreachable
B) Administratively Blocked
C) Port Unreachable
D) Protocol Unreachable
A) Host Unreachable
B) Administratively Blocked
C) Port Unreachable
D) Protocol Unreachable

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
17
In the following directory listing, 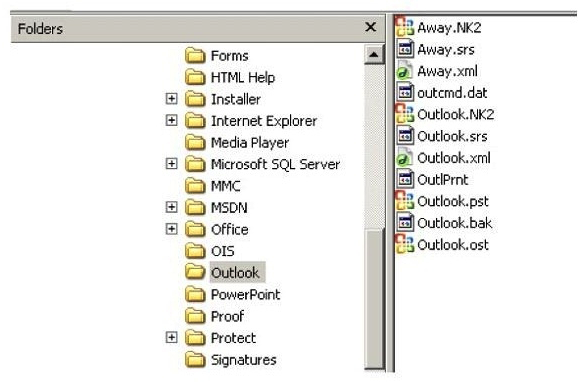 Which file should be used to restore archived email messages for someone using Microsoft Outlook?
Which file should be used to restore archived email messages for someone using Microsoft Outlook?
A) Outlook bak
B) Outlook ost
C) Outlook NK2
D) Outlook pst
 Which file should be used to restore archived email messages for someone using Microsoft Outlook?
Which file should be used to restore archived email messages for someone using Microsoft Outlook?A) Outlook bak
B) Outlook ost
C) Outlook NK2
D) Outlook pst

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
18
When needing to search for a website that is no longer present on the Internet today but was online few years back, what site can be used to view the website collection of pages?
A) Proxify.net
B) Dnsstuff.com
C) Samspade.org
D) Archive.org
A) Proxify.net
B) Dnsstuff.com
C) Samspade.org
D) Archive.org

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
19
What is the smallest physical storage unit on a hard drive?
A) Track
B) Cluster
C) Sector
D) Platter
A) Track
B) Cluster
C) Sector
D) Platter

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
20
After attending a CEH security seminar, you make a list of changes you would like to perform on your network to increase its security. One of the first things you change is to switch the RestrictAnonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server. Using Userinfo tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
A) RestrictAnonymous must be set to "10" for complete security
B) RestrictAnonymous must be set to "3" for complete security
C) RestrictAnonymous must be set to "2" for complete security
D) There is no way to always prevent an anonymous null session from establishing
A) RestrictAnonymous must be set to "10" for complete security
B) RestrictAnonymous must be set to "3" for complete security
C) RestrictAnonymous must be set to "2" for complete security
D) There is no way to always prevent an anonymous null session from establishing

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
21
You are a security analyst performing reconnaissance on a company you will be carrying out a penetration test for. You conduct a search for IT jobs on Dice.com and find the following information for an open position: 7+ years experience in Windows Server environment 5+ years experience in Exchange 2000/2003 environment Experience with Cisco Pix Firewall, Linksys 1376 router, Oracle 11i and MYOB v3.4 Accounting software are required MCSA desired, MCSE, CEH preferred No Unix/Linux Experience needed What is this information posted on the job website considered?
A) Social engineering exploit
B) Competitive exploit
C) Information vulnerability
D) Trade secret
A) Social engineering exploit
B) Competitive exploit
C) Information vulnerability
D) Trade secret

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
22
Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the company PBX system be called?
A) Phreaking
B) Squatting
C) Crunching
D) Pretexting
A) Phreaking
B) Squatting
C) Crunching
D) Pretexting

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
23
When is it appropriate to use computer forensics?
A) If copyright and intellectual property theft/misuse has occurred
B) If employees do not care for their boss management techniques
C) If sales drop off for no apparent reason for an extended period of time
D) If a financial institution is burglarized by robbers
A) If copyright and intellectual property theft/misuse has occurred
B) If employees do not care for their boss management techniques
C) If sales drop off for no apparent reason for an extended period of time
D) If a financial institution is burglarized by robbers

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
24
What is the first step taken in an investigation for laboratory forensic staff members?
A) Packaging the electronic evidence
B) Securing and evaluating the electronic crime scene
C) Conducting preliminary interviews
D) Transporting the electronic evidence
A) Packaging the electronic evidence
B) Securing and evaluating the electronic crime scene
C) Conducting preliminary interviews
D) Transporting the electronic evidence

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
25
What encryption technology is used on Blackberry devices Password Keeper?
A) 3DES
B) AES
C) Blowfish
D) RC5
A) 3DES
B) AES
C) Blowfish
D) RC5

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
26
Why is it a good idea to perform a penetration test from the inside?
A) It is never a good idea to perform a penetration test from the inside
B) Because 70% of attacks are from inside the organization
C) To attack a network from a hacker's perspective
D) It is easier to hack from the inside
A) It is never a good idea to perform a penetration test from the inside
B) Because 70% of attacks are from inside the organization
C) To attack a network from a hacker's perspective
D) It is easier to hack from the inside

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
27
In the following email header, where did the email first originate from? 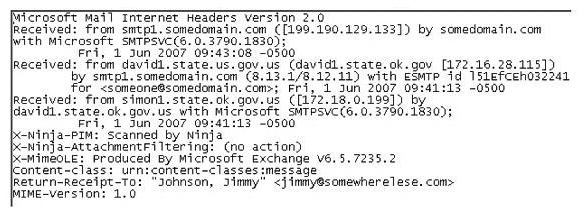
A) Somedomain.com
B) Smtp1.somedomain.com
C) Simon1.state.ok.gov.us
D) David1.state.ok.gov.us

A) Somedomain.com
B) Smtp1.somedomain.com
C) Simon1.state.ok.gov.us
D) David1.state.ok.gov.us

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
28
Why is it still possible to recover files that have been emptied from the Recycle Bin on a Windows computer?
A) The data is still present until the original location of the file is used
B) The data is moved to the Restore directory and is kept there indefinitely
C) The data will reside in the L2 cache on a Windows computer until it is manually deleted
D) It is not possible to recover data that has been emptied from the Recycle Bin
A) The data is still present until the original location of the file is used
B) The data is moved to the Restore directory and is kept there indefinitely
C) The data will reside in the L2 cache on a Windows computer until it is manually deleted
D) It is not possible to recover data that has been emptied from the Recycle Bin

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
29
Which program is the bootloader when Windows XP starts up?
A) KERNEL.EXE
B) NTLDR
C) LOADER
D) LILO
A) KERNEL.EXE
B) NTLDR
C) LOADER
D) LILO

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
30
This type of testimony is presented by someone who does the actual fieldwork and does not offer a view in court.
A) Civil litigation testimony
B) Expert testimony
C) Victim advocate testimony
D) Technical testimony
A) Civil litigation testimony
B) Expert testimony
C) Victim advocate testimony
D) Technical testimony

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
31
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
A) Copyright
B) Design patent
C) Trademark
D) Utility patent
A) Copyright
B) Design patent
C) Trademark
D) Utility patent

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
32
Using Linux to carry out a forensics investigation, what would the following command accomplish? dd if=/usr/home/partition.image of=/dev/sdb2 bs=4096 conv=notrunc,noerror
A) Search for disk errors within an image file
B) Backup a disk to an image file
C) Copy a partition to an image file
D) Restore a disk from an image file
A) Search for disk errors within an image file
B) Backup a disk to an image file
C) Copy a partition to an image file
D) Restore a disk from an image file

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
33
What type of equipment would a forensics investigator store in a StrongHold bag?
A) PDAPDA?
B) Backup tapes
C) Hard drives
D) Wireless cards
A) PDAPDA?
B) Backup tapes
C) Hard drives
D) Wireless cards

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
34
While presenting his case to the court, Simon calls many witnesses to the stand to testify. Simon decides to call Hillary Taft, a lay witness, to the stand. Since Hillary is a lay witness, what field would she be considered an expert in?
A) Technical material related to forensics
B) No particular field
C) Judging the character of defendants/victims
D) Legal issues
A) Technical material related to forensics
B) No particular field
C) Judging the character of defendants/victims
D) Legal issues

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
35
When carrying out a forensics investigation, why should you never delete a partition on a dynamic disk?
A) All virtual memory will be deleted
B) The wrong partition may be set to active
C) This action can corrupt the disk
D) The computer will be set in a constant reboot state
A) All virtual memory will be deleted
B) The wrong partition may be set to active
C) This action can corrupt the disk
D) The computer will be set in a constant reboot state

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
36
When marking evidence that has been collected with the aa/ddmmyy/nnnn/zz format, what does the nnn denote?
A) The year the evidence was taken
B) The sequence number for the parts of the same exhibit
C) The initials of the forensics analyst
D) The sequential number of the exhibits seized
A) The year the evidence was taken
B) The sequence number for the parts of the same exhibit
C) The initials of the forensics analyst
D) The sequential number of the exhibits seized

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
37
The following is a log file screenshot from a default installation of IIS 6.0. 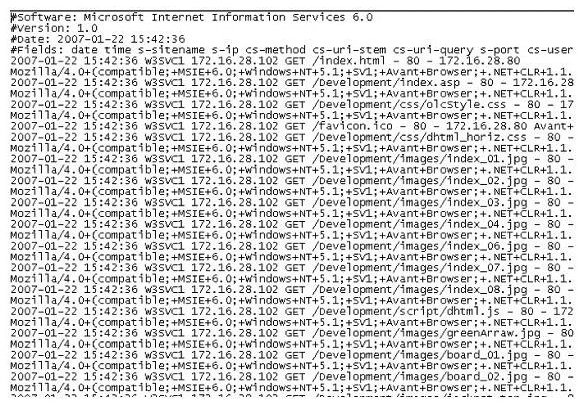 What time standard is used by IIS as seen in the screenshot?
What time standard is used by IIS as seen in the screenshot?
A) UTC
B) GMT
C) TAI
D) UT
 What time standard is used by IIS as seen in the screenshot?
What time standard is used by IIS as seen in the screenshot?A) UTC
B) GMT
C) TAI
D) UT

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
38
In handling computer-related incidents, which IT role should be responsible for recovery, containment, and prevention to constituents?
A) Security Administrator
B) Network Administrator
C) Director of Information Technology
D) Director of Administration
A) Security Administrator
B) Network Administrator
C) Director of Information Technology
D) Director of Administration

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
39
What will the following command accomplish in Linux? fdisk /dev/hda
A) Partition the hard drive
B) Format the hard drive
C) Delete all files under the /dev/hda folder
D) Fill the disk with zeros
A) Partition the hard drive
B) Format the hard drive
C) Delete all files under the /dev/hda folder
D) Fill the disk with zeros

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
40
All Blackberry email is eventually sent and received through what proprietary RIM-operated mechanism?
A) Blackberry Message Center
B) Microsoft Exchange
C) Blackberry WAP gateway
D) Blackberry WEP gateway
A) Blackberry Message Center
B) Microsoft Exchange
C) Blackberry WAP gateway
D) Blackberry WEP gateway

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
41
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd. 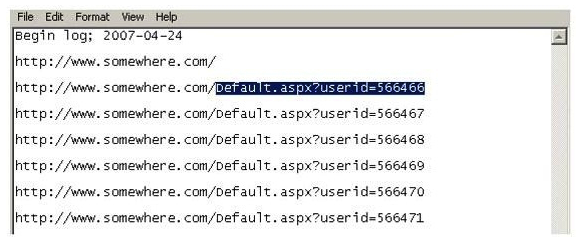 From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
A) Parameter tampering
B) Cross site scripting
C) SQL injection
D) Cookie Poisoning
 From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?A) Parameter tampering
B) Cross site scripting
C) SQL injection
D) Cookie Poisoning

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
42
What will the following Linux command accomplish? dd if=/dev/mem of=/home/sam/mem.bin bs=1024
A) Copy the master boot record to a file
B) Copy the contents of the system folder to a file
C) Copy the running memory to a file
D) Copy the memory dump file to an image file
A) Copy the master boot record to a file
B) Copy the contents of the system folder to a file
C) Copy the running memory to a file
D) Copy the memory dump file to an image file

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
43
Harold is finishing up a report on a case of network intrusion, corporate spying, and embezzlement that he has been working on for over six months. He is trying to find the right term to use in his report to describe network-enabled spying. What term should Harold use?
A) Spycrack
B) Spynet
C) Netspionage
D) Hackspionage
A) Spycrack
B) Spynet
C) Netspionage
D) Hackspionage

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
44
Paraben Lockdown device uses which operating system to write hard drive data?
A) Mac OS
B) Red Hat
C) Unix
D) Windows
A) Mac OS
B) Red Hat
C) Unix
D) Windows

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
45
Why would you need to find out the gateway of a device when investigating a wireless attack?
A) The gateway will be the IP of the proxy server used by the attacker to launch the attack
B) The gateway will be the IP of the attacker computer
C) The gateway will be the IP used to manage the RADIUS server
D) The gateway will be the IP used to manage the access point
A) The gateway will be the IP of the proxy server used by the attacker to launch the attack
B) The gateway will be the IP of the attacker computer
C) The gateway will be the IP used to manage the RADIUS server
D) The gateway will be the IP used to manage the access point

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
46
What must be obtained before an investigation is carried out at a location?
A) Search warrant
B) Subpoena
C) Habeas corpus
D) Modus operandi
A) Search warrant
B) Subpoena
C) Habeas corpus
D) Modus operandi

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
47
What type of attack sends spoofed UDP packets (instead of ping packets) with a fake source address to the IP broadcast address of a large network?
A) Fraggle
B) Smurf scan
C) SYN flood
D) Teardrop
A) Fraggle
B) Smurf scan
C) SYN flood
D) Teardrop

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
48
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
A) Text semagram
B) Visual semagram
C) Grill cipher
D) Visual cipher
A) Text semagram
B) Visual semagram
C) Grill cipher
D) Visual cipher

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
49
What type of attack sends SYN requests to a target system with spoofed IP addresses?
A) SYN flood
B) Ping of death
C) Cross site scripting
D) Land
A) SYN flood
B) Ping of death
C) Cross site scripting
D) Land

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
50
While looking through the IIS log file of a web server, you find the following entries: 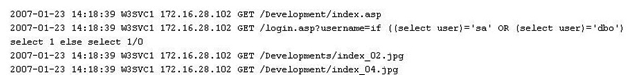 What is evident from this log file?
What is evident from this log file?
A) Web bugs
B) Cross site scripting
C) Hidden fields
D) SQL injection is possible
 What is evident from this log file?
What is evident from this log file?A) Web bugs
B) Cross site scripting
C) Hidden fields
D) SQL injection is possible

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
51
What feature of Windows is the following command trying to utilize? 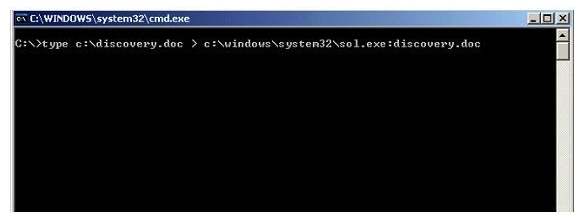
A) White space
B) AFS
C) ADS
D) Slack file

A) White space
B) AFS
C) ADS
D) Slack file

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
52
What stage of the incident handling process involves reporting events?
A) Containment
B) Follow-up
C) Identification
D) Recovery
A) Containment
B) Follow-up
C) Identification
D) Recovery

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
53
What is the CIDR from the following screenshot? 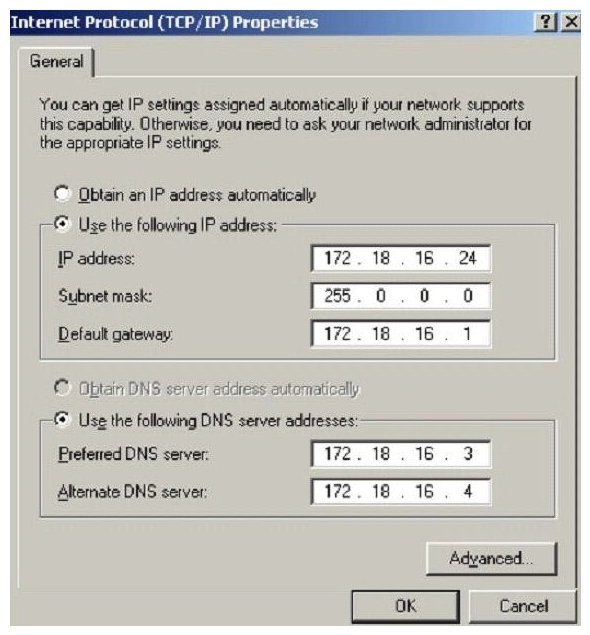
A) /24A./24A./24
B) /32 B./32 B./32
C) /16 C./16 C./16
D) /8D./8D./8

A) /24A./24A./24
B) /32 B./32 B./32
C) /16 C./16 C./16
D) /8D./8D./8

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
54
When a router receives an update for its routing table, what is the metric value change to that path?
A) Increased by 2
B) Decreased by 1
C) Increased by 1
D) Decreased by 2
A) Increased by 2
B) Decreased by 1
C) Increased by 1
D) Decreased by 2

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
55
When investigating a computer forensics case where Microsoft Exchange and Blackberry Enterprise server are used, where would investigator need to search to find email sent from a Blackberry device?
A) RIM Messaging center
B) Blackberry Enterprise server
C) Microsoft Exchange server
D) Blackberry desktop redirector
A) RIM Messaging center
B) Blackberry Enterprise server
C) Microsoft Exchange server
D) Blackberry desktop redirector

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
56
During an investigation, an employee was found to have deleted harassing emails that were sent to someone else. The company was using Microsoft Exchange and had message tracking enabled. Where could the investigator search to find the message tracking log file on the Exchange server?
A) C:\Program Files\Exchsrvr\servername.log
B) D:\Exchsrvr\Message Tracking\servername.log
C) C:\Exchsrvr\Message Tracking\servername.log
D) C:\Program Files\Microsoft Exchange\srvr\servername.log
A) C:\Program Files\Exchsrvr\servername.log
B) D:\Exchsrvr\Message Tracking\servername.log
C) C:\Exchsrvr\Message Tracking\servername.log
D) C:\Program Files\Microsoft Exchange\srvr\servername.log

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
57
What technique is used by JPEGs for compression?
A) ZIP
B) TCD
C) DCT
D) TIFF-8
A) ZIP
B) TCD
C) DCT
D) TIFF-8

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
58
Before performing a logical or physical search of a drive in Encase, what must be added to the program?
A) File signatures
B) Keywords
C) Hash sets
D) Bookmarks
A) File signatures
B) Keywords
C) Hash sets
D) Bookmarks

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
59
When reviewing web logs, you see an entry for resource not found in the HTTP status code field. What is the actual error code that you would see in the log for resource not found?
A) 202
B) 404
C) 606
D) 999
A) 202
B) 404
C) 606
D) 999

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
60
How many times can data be written to a DVD+R disk?
A) Twice
B) Once
C) Zero
D) Infinite
A) Twice
B) Once
C) Zero
D) Infinite

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
61
When should an MD5 hash check be performed when processing evidence?
A) After the evidence examination has been completed
B) On an hourly basis during the evidence examination
C) Before and after evidence examination
D) Before the evidence examination has been completed
A) After the evidence examination has been completed
B) On an hourly basis during the evidence examination
C) Before and after evidence examination
D) Before the evidence examination has been completed

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
62
Why should you never power on a computer that you need to acquire digital evidence from?
A) When the computer boots up, files are written to the computer rendering the data nclean
B) When the computer boots up, the system cache is cleared which could destroy evidence
C) When the computer boots up, data in the memory buffer is cleared which could destroy evidence
D) Powering on a computer has no affect when needing to acquire digital evidence from it
A) When the computer boots up, files are written to the computer rendering the data nclean
B) When the computer boots up, the system cache is cleared which could destroy evidence
C) When the computer boots up, data in the memory buffer is cleared which could destroy evidence
D) Powering on a computer has no affect when needing to acquire digital evidence from it

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
63
A stakeholder is a person or group:
A) Vested in the success and/or failure of a project or initiative regardless of budget implications.
B) Vested in the success and/or failure of a project or initiative and is tied to the project budget.
C) That has budget authority.
D) That will ultimately use the system.
A) Vested in the success and/or failure of a project or initiative regardless of budget implications.
B) Vested in the success and/or failure of a project or initiative and is tied to the project budget.
C) That has budget authority.
D) That will ultimately use the system.

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
64
What method of copying should always be performed first before carrying out an investigation?
A) Parity-bit copy
B) Bit-stream copy
C) MS-DOS disc copy
D) System level copy
A) Parity-bit copy
B) Bit-stream copy
C) MS-DOS disc copy
D) System level copy

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
65
Preparing an image drive to copy files to is the first step in Linux forensics. For this purpose, what would the following command accomplish? dcfldd if=/dev/zero of=/dev/hda bs=4096 conv=noerror, sync
A) Fill the disk with zeros
B) Low-level format
C) Fill the disk with 4096 zeros
D) Copy files from the master disk to the slave disk on the secondary IDE controller
A) Fill the disk with zeros
B) Low-level format
C) Fill the disk with 4096 zeros
D) Copy files from the master disk to the slave disk on the secondary IDE controller

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
66
Travis, a computer forensics investigator, is finishing up a case he has been working on for over a month involving copyright infringement and embezzlement. His last task is to prepare an investigative report for the president of the company he has been working for. Travis must submit a hard copy and an electronic copy to this president. In what electronic format should Travis send this report?
A) TIFF-8
B) DOC
C) WPD
D) PDF
A) TIFF-8
B) DOC
C) WPD
D) PDF

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
67
John is working as a computer forensics investigator for a consulting firm in Canada. He is called to seize a computer at a local web caf purportedly used as a botnet server. John thoroughly scans the computer and finds nothing that would lead him to think the computer was a botnet server. John decides to scan the virtual memory of the computer to possibly find something he had missed. What information will the virtual memory scan produce?
A) It contains the times and dates of when the system was last patched
B) It is not necessary to scan the virtual memory of a computer
C) It contains the times and dates of all the system files
D) Hidden running processes
A) It contains the times and dates of when the system was last patched
B) It is not necessary to scan the virtual memory of a computer
C) It contains the times and dates of all the system files
D) Hidden running processes

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
68
A picture file is recovered from a computer under investigation. During the investigation process, the file is enlarged 500% to get a better view of its contents. The picture quality is not degraded at all from this process. What kind of picture is this file. What kind of picture is this file?
A) Raster image
B) Vector image
C) Metafile image
D) Catalog image
A) Raster image
B) Vector image
C) Metafile image
D) Catalog image

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
69
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power required by small hard drives?
A) SD memory
B) CF memory
C) MMC memory
D) SM memory
A) SD memory
B) CF memory
C) MMC memory
D) SM memory

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
70
At what layer does a cross site scripting attack occur on?
A) Presentation
B) Application
C) Session
D) Data Link
A) Presentation
B) Application
C) Session
D) Data Link

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
71
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
A) NTOSKRNL.EXE
B) NTLDR
C) LSASS.EXE
D) NTDETECT.COM
A) NTOSKRNL.EXE
B) NTLDR
C) LSASS.EXE
D) NTDETECT.COM

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
72
A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size. What type of removable media could the investigator use?
A) Blu-Ray single-layer
B) HD-DVD
C) Blu-Ray dual-layer
D) DVD-18
A) Blu-Ray single-layer
B) HD-DVD
C) Blu-Ray dual-layer
D) DVD-18

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
73
How often must a company keep log files for them to be admissible in a court of law?
A) All log files are admissible in court no matter their frequency
B) Weekly
C) Monthly
D) Continuously
A) All log files are admissible in court no matter their frequency
B) Weekly
C) Monthly
D) Continuously

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
74
Jacob is a computer forensics investigator with over 10 years experience in investigations and has written over 50 articles on computer forensics. He has been called upon as a qualified witness to testify the accuracy and integrity of the technical log files gathered in an investigation into computer fraud. What is the term used for Jacob testimony in this case?
A) Justification
B) Authentication
C) Reiteration
D) Certification
A) Justification
B) Authentication
C) Reiteration
D) Certification

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
75
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?
A) Three
B) One
C) Two
D) Four
A) Three
B) One
C) Two
D) Four

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
76
Davidson Trucking is a small transportation company that has three local offices in Detroit Michigan. Ten female employees that work for the company have gone to an attorney reporting that male employees repeatedly harassed them and that management did nothing to stop the problem. Davidson has employee policies that outline all company guidelines, including awareness on harassment and how it will not be tolerated. When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company policy?
A) IT personnel
B) Employees themselves
C) Supervisors
D) Administrative assistant in charge of writing policies
A) IT personnel
B) Employees themselves
C) Supervisors
D) Administrative assistant in charge of writing policies

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
77
An on-site incident response team is called to investigate an alleged case of computer tampering within their company. Before proceeding with the investigation, the CEO informs them that the incident will be classified as low level. How long will the team have to respond to the incident?
A) One working day
B) Two working days
C) Immediately
D) Four hours
A) One working day
B) Two working days
C) Immediately
D) Four hours

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
78
What will the following command accomplish? dd if=/dev/xxx of=mbr.backup bs=512 count=1
A) Back up the master boot record
B) Restore the master boot record
C) Mount the master boot record on the first partition of the hard drive
D) Restore the first 512 bytes of the first partition of the hard drive
A) Back up the master boot record
B) Restore the master boot record
C) Mount the master boot record on the first partition of the hard drive
D) Restore the first 512 bytes of the first partition of the hard drive

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
79
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive? 22,164 cylinders/disk 80 heads/cylinder 63 sectors/track
A) 53.26 GB
B) 57.19 GB
C) 11.17 GB
D) 10 GB
A) 53.26 GB
B) 57.19 GB
C) 11.17 GB
D) 10 GB

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck
80
Which forensic investigating concept trails the whole incident from how the attack began to how the victim was affected?
A) Point-to-point
B) End-to-end
C) Thorough
D) Complete event analysis
A) Point-to-point
B) End-to-end
C) Thorough
D) Complete event analysis

Unlock Deck
Unlock for access to all 131 flashcards in this deck.
Unlock Deck
k this deck


