Patrick visits his teenage daughter's social media page and discovers several offensive posts about one of her classmates. After speaking with his daughter, Patrick learns that several other girls in her class are upset with the classmate and have been posting, texting and e-mailing others about the girl. What is the best way for Patrick to help his daughter understand cyberbullying?
A) He should advise his daughter to ignore the posts, texts and c-mails.
B) He should explain to his daughter that she is participating in the bullying by accepting others' posts, texts and c-mails.
C) He should explain to his daughter that the Internet embraces freedom of speech, and anyone is allowed to write anything.
D) He should advise his daughter to delete all the posts, texts and c-mails she has received, as well as any new ones that appear.












































































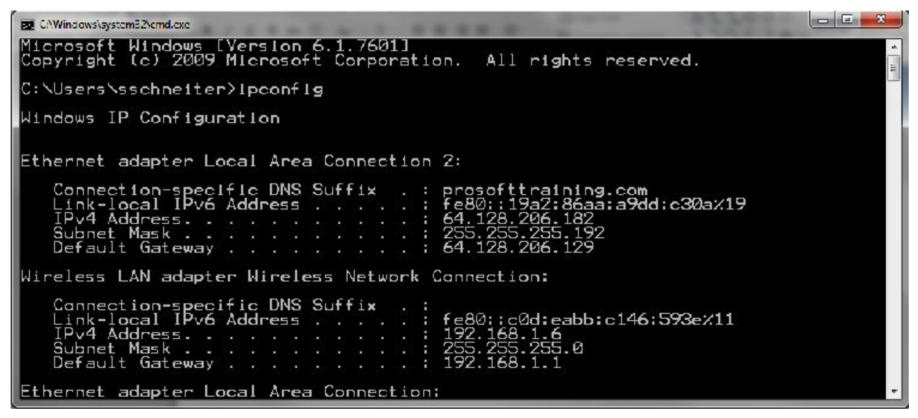 What does the Default Gateway identify?
What does the Default Gateway identify?
