Deck 4: Administration of Symantec ProxySG 6.7
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/138
Play
Full screen (f)
Deck 4: Administration of Symantec ProxySG 6.7
1
Which channel does Endpoint Prevent protect using Device Control?
A) Bluetooth
B) USB storage
C) CD/DVD
D) Network card
A) Bluetooth
B) USB storage
C) CD/DVD
D) Network card
USB storage
2
Which statement accurately describes where Optical Character Recognition (OCR) components must be installed?
A) The OCR engine must be installed on detection server other than the Enforce server.
B) The OCR server software must be installed on one or more dedicated (non-detection) Linux servers.
C) The OCR engine must be directly on the Enforce server.
D) The OCR server software must be installed on one or more dedicated (non-detection) Windows servers.
A) The OCR engine must be installed on detection server other than the Enforce server.
B) The OCR server software must be installed on one or more dedicated (non-detection) Linux servers.
C) The OCR engine must be directly on the Enforce server.
D) The OCR server software must be installed on one or more dedicated (non-detection) Windows servers.
The OCR engine must be directly on the Enforce server.
3
How should a DLP administrator exclude a custom endpoint application named "custom_app.exe" from being monitoring by Application File Access Control?
A) Add "custom_app.exe" to the "Application Whitelist" on all Endpoint servers.
B) Add "custom_app.exe" Application Monitoring Configuration and de-select all its channel options.
C) Add "custom_app_.exe" as a filename exception to the Endpoint Prevent policy.
D) Add "custom_app.exe" to the "Program Exclusion List" in the agent configuration settings.
A) Add "custom_app.exe" to the "Application Whitelist" on all Endpoint servers.
B) Add "custom_app.exe" Application Monitoring Configuration and de-select all its channel options.
C) Add "custom_app_.exe" as a filename exception to the Endpoint Prevent policy.
D) Add "custom_app.exe" to the "Program Exclusion List" in the agent configuration settings.
Add "custom_app.exe" to the "Application Whitelist" on all Endpoint servers.
4
Which two detection technology options run on the DLP agent? (Choose two.)
A) Optical Character Recognition (OCR)
B) Described Content Matching (DCM)
C) Directory Group Matching (DGM)
D) Form Recognition
E) Indexed Document Matching (IDM)
A) Optical Character Recognition (OCR)
B) Described Content Matching (DCM)
C) Directory Group Matching (DGM)
D) Form Recognition
E) Indexed Document Matching (IDM)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
5
Which product is able to replace a confidential document residing on a file share with a marker file explaining why the document was removed?
A) Network Discover
B) Cloud Service for Email
C) Endpoint Prevent
D) Network Protect
A) Network Discover
B) Cloud Service for Email
C) Endpoint Prevent
D) Network Protect

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
6
Under the "System Overview" in the Enforce management console, the status of a Network Monitor detection server is shown as "Running Selected." The Network Monitor server's event logs indicate that the packet capture and filereader processes are crashing. What is a possible cause for the Network Monitor server being in this state?
A) There is insufficient disk space on the Network Monitor server.
B) The Network Monitor server's certificate is corrupt or missing.
C) The Network Monitor server's license file has expired.
D) The Enforce and Network Monitor servers are running different versions of DLP.
A) There is insufficient disk space on the Network Monitor server.
B) The Network Monitor server's certificate is corrupt or missing.
C) The Network Monitor server's license file has expired.
D) The Enforce and Network Monitor servers are running different versions of DLP.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
7
Which action should a DLP administrator take to secure communications between an on-premises Enforce server and detection servers hosted in the Cloud?
A) Use the built-in Symantec DLP certificate for the Enforce Server, and use the "sslkeytool" utility to create certificates for the detection servers.
B) Use the built-in Symantec DLP certificate for both the Enforce server and the hosted detection servers.
C) Set up a Virtual Private Network (VPN) for the Enforce server and the hosted detection servers.
D) Use the "sslkeytool" utility to create certificates for the Enforce server and the hosted detection servers.
A) Use the built-in Symantec DLP certificate for the Enforce Server, and use the "sslkeytool" utility to create certificates for the detection servers.
B) Use the built-in Symantec DLP certificate for both the Enforce server and the hosted detection servers.
C) Set up a Virtual Private Network (VPN) for the Enforce server and the hosted detection servers.
D) Use the "sslkeytool" utility to create certificates for the Enforce server and the hosted detection servers.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
8
When managing an Endpoint Discover scan, a DLP administrator notices some endpoint computers are NOT completing their scans. When does the DLP agent stop scanning?
A) When the agent sends a report within the "Scan Idle Timeout" period
B) When the endpoint computer is rebooted and the agent is started
C) When the agent is unable to send a status report within the "Scan Idle Timeout" period
D) When the agent sends a report immediately after the "Scan Idle Timeout" period
A) When the agent sends a report within the "Scan Idle Timeout" period
B) When the endpoint computer is rebooted and the agent is started
C) When the agent is unable to send a status report within the "Scan Idle Timeout" period
D) When the agent sends a report immediately after the "Scan Idle Timeout" period

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
9
A compliance officer needs to understand how the company is complying with its data security policies over time. Which report should be compliance officer generate to obtain the compliance information?
A) Policy report, filtered on date and summarized by policy
B) Policy Trend report, summarized by policy, then quarter
C) Policy report, filtered on quarter and summarized by policy
D) Policy Trend report, summarized by policy, then severity
A) Policy report, filtered on date and summarized by policy
B) Policy Trend report, summarized by policy, then quarter
C) Policy report, filtered on quarter and summarized by policy
D) Policy Trend report, summarized by policy, then severity

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
10
Which two actions are available for a "Network Prevent: Remove HTTP/HTTPS content" response rule when the content is unable to be removed? (Choose two.)
A) Allow the content to be posted
B) Remove the content through FlexResponse
C) Block the content before posting
D) Encrypt the content before posting
E) Redirect the content to an alternative destination
A) Allow the content to be posted
B) Remove the content through FlexResponse
C) Block the content before posting
D) Encrypt the content before posting
E) Redirect the content to an alternative destination

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
11
Which option correctly describes the two-tier installation type for Symantec DLP?
A) Install the Oracle database on the host, and install the Enforce server and a detection server on a second host.
B) Install the Oracle database on a local physical host, and install the Enforce server and detection servers on virtual hosts in the Cloud.
C) Install the Oracle database and a detection server in the same host, and install the Enforce server on a second host.
D) Install the Oracle database and Enforce server on the same host, and install detection servers on separate hosts.
A) Install the Oracle database on the host, and install the Enforce server and a detection server on a second host.
B) Install the Oracle database on a local physical host, and install the Enforce server and detection servers on virtual hosts in the Cloud.
C) Install the Oracle database and a detection server in the same host, and install the Enforce server on a second host.
D) Install the Oracle database and Enforce server on the same host, and install detection servers on separate hosts.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
12
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a "copy to USB device" operation?
A) Add a "Limit Incident Data Retention" response rule with "Retain Original Message" option selected.
B) Modify the agent config.db to include the file
C) Modify the "Endpoint_Retain_Files.int" setting in the Endpoint server configuration
D) Modify the agent configuration and select the option "Retain Original Files"
A) Add a "Limit Incident Data Retention" response rule with "Retain Original Message" option selected.
B) Modify the agent config.db to include the file
C) Modify the "Endpoint_Retain_Files.int" setting in the Endpoint server configuration
D) Modify the agent configuration and select the option "Retain Original Files"

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
13
What is the correct configuration for "BoxMonitor.Channels" that will allow the server to start as a Network Monitor server?
A) Packet Capture, Span Port
B) Packet Capture, Network Tap
C) Packet Capture, Copy Rule
D) Packet capture, Network Monitor
A) Packet Capture, Span Port
B) Packet Capture, Network Tap
C) Packet Capture, Copy Rule
D) Packet capture, Network Monitor

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
14
Which detection server is available from Symantec as a hardware appliance?
A) Network Prevent for Email
B) Network Discover
C) Network Monitor
D) Network Prevent for Web
A) Network Prevent for Email
B) Network Discover
C) Network Monitor
D) Network Prevent for Web

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
15
What detection server type requires a minimum of two physical network interface cards?
A) Network Prevent for Web
B) Network Prevent for Email
C) Network Monitor
D) Cloud Detection Service (CDS)
A) Network Prevent for Web
B) Network Prevent for Email
C) Network Monitor
D) Cloud Detection Service (CDS)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
16
What detection server is used for Network Discover, Network Protect, and Cloud Storage?
A) Network Protect Storage Discover
B) Network Discover/Cloud Storage Discover
C) Network Prevent/Cloud Detection Service
D) Network Protect/Cloud Detection Service
A) Network Protect Storage Discover
B) Network Discover/Cloud Storage Discover
C) Network Prevent/Cloud Detection Service
D) Network Protect/Cloud Detection Service

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
17
A DLP administrator has enabled and successfully tested custom attribute lookups for incident data based on the Active Directory LDAP plugin. The Chief Information Security Officer (CISO) has attempted to generate a User Risk Summary report, but the report is empty. The DLP administrator confirms the Cisco's role has the "User Reporting" privilege enabled, but User Risk reporting is still not working. What is the probable reason that the User Risk Summary report is blank?
A) Only DLP administrators are permitted to access and view data for high risk users.
B) The Enforce server has insufficient permissions for importing user attributes.
C) User attribute data must be configured separately from incident data attributes.
D) User attributes have been incorrectly mapped to Active Directory accounts.
A) Only DLP administrators are permitted to access and view data for high risk users.
B) The Enforce server has insufficient permissions for importing user attributes.
C) User attribute data must be configured separately from incident data attributes.
D) User attributes have been incorrectly mapped to Active Directory accounts.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
18
Which two locations can Symantec DLP scan and perform Information Centric Encryption (ICE) actions on? (Choose two.)
A) Exchange
B) Jiveon
C) File store
D) SharePoint
E) Confluence
A) Exchange
B) Jiveon
C) File store
D) SharePoint
E) Confluence

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
19
What is Application Detection Configuration?
A) The Cloud Detection Service (CDS) process that tells Enforce a policy has been violated
B) The Data Loss Prevention (DLP) policy which has been pushed into Cloud Detection Service (CDC) for files in transit to or residing in Cloud apps
C) The terminology describing the Data Loss Prevention (DLP) process within the CloudSOC administration portal
D) The setting configured within the user interface (UI) that determines whether CloudSOC should send a file to Cloud Detection Service (CDS) for analysis.
A) The Cloud Detection Service (CDS) process that tells Enforce a policy has been violated
B) The Data Loss Prevention (DLP) policy which has been pushed into Cloud Detection Service (CDC) for files in transit to or residing in Cloud apps
C) The terminology describing the Data Loss Prevention (DLP) process within the CloudSOC administration portal
D) The setting configured within the user interface (UI) that determines whether CloudSOC should send a file to Cloud Detection Service (CDS) for analysis.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
20
A DLP administrator has performed a test deployment of the DLP 15.0 Endpoint agent and now wants to uninstall the agent. However, the administrator no longer remembers the uninstall password. What should the administrator do to work around the password problem?
A) Apply a new global agent uninstall password in the Enforce management console.
B) Manually delete all the Endpoint agent files from the test computer and install a new agent package.
C) Replace the PGPsdk.dll file on the agent's assigned Endpoint server with a copy from a different Endpoint server Replace the PGPsdk.dll file on the agent's assigned Endpoint server with a copy from a different Endpoint server
D) Use the UninstallPwdGenerator to create an UninstallPasswordKey . Use the UninstallPwdGenerator to create an UninstallPasswordKey .
A) Apply a new global agent uninstall password in the Enforce management console.
B) Manually delete all the Endpoint agent files from the test computer and install a new agent package.
C) Replace the PGPsdk.dll file on the agent's assigned Endpoint server with a copy from a different Endpoint server Replace the PGPsdk.dll file on the agent's assigned Endpoint server with a copy from a different Endpoint server
D) Use the UninstallPwdGenerator to create an UninstallPasswordKey . Use the UninstallPwdGenerator to create an UninstallPasswordKey .

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
21
What is the Symantec recommended order for stopping Symantec DLP services on a Windows Enforce server?
A) Vontu Notifier, Vontu Incident Persister, Vontu Update, Vontu Manager, Vontu Monitor Controller
B) Vontu Update, Vontu Notifier, Vontu Manager, Vontu Incident Persister, Vontu Monitor Controller
C) Vontu Incident Persister, Vontu Update, Vontu Notifier, Vontu Monitor Controller, Vontu Manager.
D) Vontu Monitor Controller, Vontu Incident Persister, Vontu Manager, Vontu Notifier, Vontu Update.
A) Vontu Notifier, Vontu Incident Persister, Vontu Update, Vontu Manager, Vontu Monitor Controller
B) Vontu Update, Vontu Notifier, Vontu Manager, Vontu Incident Persister, Vontu Monitor Controller
C) Vontu Incident Persister, Vontu Update, Vontu Notifier, Vontu Monitor Controller, Vontu Manager.
D) Vontu Monitor Controller, Vontu Incident Persister, Vontu Manager, Vontu Notifier, Vontu Update.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
22
What detection technology supports partial contents matching?
A) Indexed Document Matching (IDM)
B) Described Content Matching (DCM)
C) Exact Data Matching (EDM)
D) Optical Character Recognition (OCR)
A) Indexed Document Matching (IDM)
B) Described Content Matching (DCM)
C) Exact Data Matching (EDM)
D) Optical Character Recognition (OCR)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
23
Which two detection servers are available as virtual appliances? (Choose two.)
A) Network Monitor
B) Network Prevent for Web
C) Network Discover
D) Network Prevent for Email
E) Optical Character Recognition (OCR)
A) Network Monitor
B) Network Prevent for Web
C) Network Discover
D) Network Prevent for Email
E) Optical Character Recognition (OCR)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
24
Refer to the exhibit. Which type of Endpoint response rule is shown? 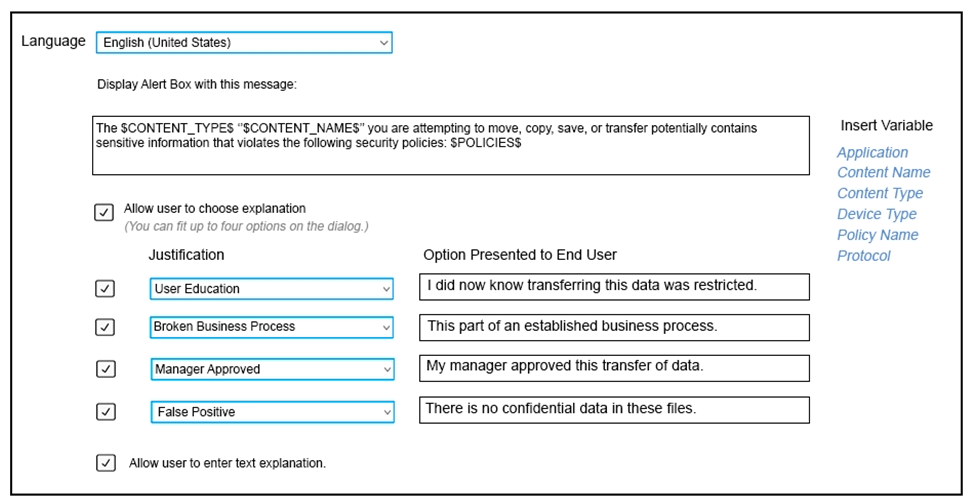
A) Endpoint Prevent: User Notification
B) Endpoint Prevent: Block
C) Endpoint Prevent: Notify
D) Endpoint Prevent: User Cancel

A) Endpoint Prevent: User Notification
B) Endpoint Prevent: Block
C) Endpoint Prevent: Notify
D) Endpoint Prevent: User Cancel

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
25
What detection method utilizes Data Identifiers?
A) Indexed Document Matching (IDM)
B) Described Content Matching (DCM)
C) Directory Group Matching (DGM)
D) Exact Data Matching (EDM)
A) Indexed Document Matching (IDM)
B) Described Content Matching (DCM)
C) Directory Group Matching (DGM)
D) Exact Data Matching (EDM)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
26
A DLP administrator has added several approved endpoint devices as exceptions to an Endpoint Prevent policy that blocks the transfer of sensitive data. However, data transfers to these devices are still being blocked. What is the first action an administrator should take to enable data transfers to the approved endpoint devices?
A) Disable and re-enable the Endpoint Prevent policy to activate the changes
B) Double-check that the correct device ID or class has been entered for each device
C) Verify Application File Access Control (AFAC) is configured to monitor the specific application
D) Edit the exception rule to ensure that the "Match On" option is set to "Attachments"
A) Disable and re-enable the Endpoint Prevent policy to activate the changes
B) Double-check that the correct device ID or class has been entered for each device
C) Verify Application File Access Control (AFAC) is configured to monitor the specific application
D) Edit the exception rule to ensure that the "Match On" option is set to "Attachments"

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
27
What is the default fallback option for the Endpoint Prevent Encrypt response rule?
A) Block
B) User Cancel
C) Encrypt
D) Notify
A) Block
B) User Cancel
C) Encrypt
D) Notify

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
28
A DLP administrator is checking the System Overview in the Enforce management console, and all of the detection servers are showing as "unknown". The Vontu services are up and running on the detection servers. Thousands of .IDC files are building up in the Incidents directory on the detection servers. There is good network connectivity between the detection servers and the Enforce server when testing with the telnet command. How should the administrator bring the detection servers to a running state in the Enforce management console?
A) Restart the Vontu Update Service on the Enforce server
B) Ensure the Vontu Monitor Controller service is running in the Enforce server
C) Delete all of the .BAD files in the Incidents folder on the Enforce server
D) Restart the Vontu Monitor Service on all the affected detection servers
A) Restart the Vontu Update Service on the Enforce server
B) Ensure the Vontu Monitor Controller service is running in the Enforce server
C) Delete all of the .BAD files in the Incidents folder on the Enforce server
D) Restart the Vontu Monitor Service on all the affected detection servers

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
29
Why would an administrator set the Similarity Threshold to zero when testing and tuning a Vector Machine Learning (VML) profile?
A) To capture the matches to the Positive set
B) To capture the matches to the Negative set
C) To see the false negatives only
D) To see the entire range of potential matches
A) To capture the matches to the Positive set
B) To capture the matches to the Negative set
C) To see the false negatives only
D) To see the entire range of potential matches

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
30
Why is it important for an administrator to utilize the grid scan feature?
A) To distribute the scan workload across multiple network discover servers
B) To distribute the scan workload across the cloud servers
C) To distribute the scan workload across multiple endpoint servers
D) To distribute the scan workload across multiple detection servers
A) To distribute the scan workload across multiple network discover servers
B) To distribute the scan workload across the cloud servers
C) To distribute the scan workload across multiple endpoint servers
D) To distribute the scan workload across multiple detection servers

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
31
How do Cloud Detection Service and the Enforce server communicate with each other?
A) Enforce initiates communication with Cloud Detection Service, which is expecting connections on port 8100.
B) Cloud Detection Service initiates communication with Enforce, which is expecting connections on port 443.
C) Cloud Detection Service initiates communication with Enforce, which is expecting connections on port 1443.
D) Enforce initiates communication with Cloud Detection Service, which is expecting connections on port 443.
A) Enforce initiates communication with Cloud Detection Service, which is expecting connections on port 8100.
B) Cloud Detection Service initiates communication with Enforce, which is expecting connections on port 443.
C) Cloud Detection Service initiates communication with Enforce, which is expecting connections on port 1443.
D) Enforce initiates communication with Cloud Detection Service, which is expecting connections on port 443.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
32
A company needs to secure the content of all Mergers and Acquisitions Agreements However, the standard text included in all company literature needs to be excluded. How should the company ensure that this standard text is excluded from detection?
A) Create a Whitelisted.txt file after creating the Vector Machine Learning (VML) profile. Create a Whitelisted.txt file after creating the Vector Machine Learning (VML) profile.
B) Create a Whitelisted.txt file after creating the Exact Data Matching (EDM) profile file after creating the Exact Data Matching (EDM) profile
C) Create a Whitelisted.txt file before creating the Indexed Document Matching (IDM) profile file before creating the Indexed Document Matching (IDM) profile
D) Create a Whitelisted.txt file before creating the Exact Data Matching (EDM) profile file before creating the Exact Data Matching (EDM) profile
A) Create a Whitelisted.txt file after creating the Vector Machine Learning (VML) profile. Create a Whitelisted.txt file after creating the Vector Machine Learning (VML) profile.
B) Create a Whitelisted.txt file after creating the Exact Data Matching (EDM) profile file after creating the Exact Data Matching (EDM) profile
C) Create a Whitelisted.txt file before creating the Indexed Document Matching (IDM) profile file before creating the Indexed Document Matching (IDM) profile
D) Create a Whitelisted.txt file before creating the Exact Data Matching (EDM) profile file before creating the Exact Data Matching (EDM) profile

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
33
Which two Infrastructure-as-a-Service providers are supported for hosting Cloud Prevent for Office 365? (Choose two.)
A) Any customer-hosted private cloud
B) Amazon Web Services
C) AT&T
D) Verizon
E) Rackspace
A) Any customer-hosted private cloud
B) Amazon Web Services
C) AT&T
D) Verizon
E) Rackspace

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
34
Which detection method depends on "training sets"?
A) Form Recognition
B) Vector Machine Learning (VML)
C) Index Document Matching (IDM)
D) Exact Data Matching (EDM)
A) Form Recognition
B) Vector Machine Learning (VML)
C) Index Document Matching (IDM)
D) Exact Data Matching (EDM)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
35
Which service encrypts the message when using a Modify SMTP Message response rule?
A) Network Monitor server
B) SMTP Prevent
C) Enforce server
D) Encryption Gateway
A) Network Monitor server
B) SMTP Prevent
C) Enforce server
D) Encryption Gateway

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
36
Which two Network Discover/Cloud Storage targets apply Information Centric Encryption as policy response rules?
A) Microsoft Exchange
B) Windows File System
C) SQL Databases
D) Microsoft SharePoint
E) Network File System (NFS)
A) Microsoft Exchange
B) Windows File System
C) SQL Databases
D) Microsoft SharePoint
E) Network File System (NFS)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
37
Which two automated response rules will be active in policies that include Exact Data Matching (EDM) detection rule? (Choose two.)
A) Endpoint Discover: Quarantine File
B) All: Send Email Notification
C) Endpoint Prevent: User Cancel
D) Endpoint Prevent: Block
E) Network Protect: Quarantine File
A) Endpoint Discover: Quarantine File
B) All: Send Email Notification
C) Endpoint Prevent: User Cancel
D) Endpoint Prevent: Block
E) Network Protect: Quarantine File

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
38
What should an incident responder select in the Enforce management console to remediate multiple incidents simultaneously?
A) Smart Response on the Incident page
B) Automated Response on the Incident Snapshot page
C) Smart Response on an Incident List report
D) Automated Response on an Incident List report
A) Smart Response on the Incident page
B) Automated Response on the Incident Snapshot page
C) Smart Response on an Incident List report
D) Automated Response on an Incident List report

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
39
Where in the Enforce management console can a DLP administrator change the "UI.NO_SCAN.int" setting to disable the "Inspecting data" pop-up?
A) Advanced Server Settings from the Endpoint Server Configuration
B) Advanced Monitoring from the Agent Configuration
C) Advanced Agent Settings from the Agent Configuration
D) Application Monitoring from the Agent Configuration
A) Advanced Server Settings from the Endpoint Server Configuration
B) Advanced Monitoring from the Agent Configuration
C) Advanced Agent Settings from the Agent Configuration
D) Application Monitoring from the Agent Configuration

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
40
Which two components can perform a file system scan of a workstation? (Choose two.)
A) Endpoint Server
B) DLP Agent
C) Network Prevent for Web Server
D) Discover Server
E) Enforce Server
A) Endpoint Server
B) DLP Agent
C) Network Prevent for Web Server
D) Discover Server
E) Enforce Server

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
41
What are two reasons an administrator should utilize a manual configuration to determine the endpoint location? (Choose two.)
A) To specify Wi-Fi SSID names
B) To specify an IP address or range
C) To specify the endpoint server
D) To specify domain names
E) To specify network card status (ON/OFF)
A) To specify Wi-Fi SSID names
B) To specify an IP address or range
C) To specify the endpoint server
D) To specify domain names
E) To specify network card status (ON/OFF)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
42
Refer to the exhibit. 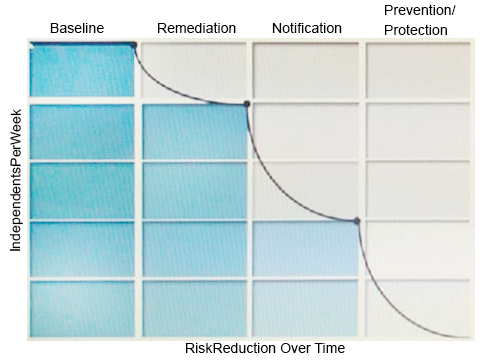 What activity should occur during the baseline phase, according to the risk reduction model?
What activity should occur during the baseline phase, according to the risk reduction model?
A) Define and build the incident response team
B) Monitor incidents and tune the policy to reduce false positives
C) Establish business metrics and begin sending reports to business unit stakeholders
D) Test policies to ensure that blocking actions minimize business process disruptions
 What activity should occur during the baseline phase, according to the risk reduction model?
What activity should occur during the baseline phase, according to the risk reduction model?A) Define and build the incident response team
B) Monitor incidents and tune the policy to reduce false positives
C) Establish business metrics and begin sending reports to business unit stakeholders
D) Test policies to ensure that blocking actions minimize business process disruptions

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
43
A DLP administrator determines that the \ SymantecDLP\Protect\Incidents folder on the Enforce server contains. BAD files dated today, while other. IDC files are flowing in and out of the \Incidents directory. Only .IDC files larger than 1MB are turning to .BAD files. What could be causing only incident data smaller than 1MB to persist while incidents larger than 1MB change to .BAD files?
A) A corrupted policy was deployed.
B) The Enforce server's hard drive is out of space.
C) A detection server has excessive filereader restarts.
D) Tablespace is almost full.
A) A corrupted policy was deployed.
B) The Enforce server's hard drive is out of space.
C) A detection server has excessive filereader restarts.
D) Tablespace is almost full.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
44
What detection technology supports partial contents matching?
A) Indexed Document Matching (IDM)
B) Described Content Matching (DCM)
C) Exact Data Matching (DCM)
D) Optical Character Recognition (OCR)
A) Indexed Document Matching (IDM)
B) Described Content Matching (DCM)
C) Exact Data Matching (DCM)
D) Optical Character Recognition (OCR)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
45
Which two detection technology options ONLY run on a detection server? (Choose two.)
A) Form Recognition
B) Indexed Document Matching (IDM)
C) Described Content Matching (DCM)
D) Exact Data Matching (EDM)
E) Vector Machine Learning (VML)
A) Form Recognition
B) Indexed Document Matching (IDM)
C) Described Content Matching (DCM)
D) Exact Data Matching (EDM)
E) Vector Machine Learning (VML)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
46
A DLP administrator needs to remove an agent its associated events from an Endpoint server. Which Agent Task should the administrator perform to disable the agent's visibility in the Enforce management console?
A) Delete action from the Agent Health dashboard
B) Delete action from the Agent List page
C) Disable action from Symantec Management Console
D) Change Endpoint Server action from the Agent Overview page
A) Delete action from the Agent Health dashboard
B) Delete action from the Agent List page
C) Disable action from Symantec Management Console
D) Change Endpoint Server action from the Agent Overview page

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
47
A DLP administrator has enabled and successfully tested custom attribute lookups for incident data based on the Active Directory LDAP plugin. The Chief Information Security Officer (CISO) has attempted to generate a User Risk Summary report, but the report is empty. The DLP administrator confirms the Cisco's role has the "User Reporting" privilege enabled, but User Risk reporting is still not working. What is the probable reason that the User Risk Summary report is blank?
A) Only DLP administrators are permitted to access and view data for high risk users.
B) The Enforce server has insufficient permissions for importing user attributes.
C) User attribute data must be configured separately from incident data attributed.
D) User attributes have been incorrectly mapped to Active Directory accounts.
A) Only DLP administrators are permitted to access and view data for high risk users.
B) The Enforce server has insufficient permissions for importing user attributes.
C) User attribute data must be configured separately from incident data attributed.
D) User attributes have been incorrectly mapped to Active Directory accounts.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
48
What is required on the Enforce server to communicate with the Symantec DLP database?
A) Port 8082 should be opened
B) CryptoMasterKey.properties file
C) Symbolic links to .dbf files
D) SQL*Plus Client
A) Port 8082 should be opened
B) CryptoMasterKey.properties file
C) Symbolic links to .dbf files
D) SQL*Plus Client

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
49
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a "cope to USB device" operation?
A) Add a "Limit Incident Data Retention" response rule with "retain Original Message" option selected.
B) Modify the agent config.db to include the file
C) Modify the "Endpoint_Retain_Files.int" setting in the Endpoint server configuration
D) Modify the agent configuration and select the option "retain Original Files"
A) Add a "Limit Incident Data Retention" response rule with "retain Original Message" option selected.
B) Modify the agent config.db to include the file
C) Modify the "Endpoint_Retain_Files.int" setting in the Endpoint server configuration
D) Modify the agent configuration and select the option "retain Original Files"

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
50
Where should an administrator set the debug levels for an Endpoint Agent?
A) Setting the log level within the Agent List
B) Advanced configuration within the Agent settings
C) Setting the log level within the Agent Overview
D) Advanced server settings within the Endpoint server
A) Setting the log level within the Agent List
B) Advanced configuration within the Agent settings
C) Setting the log level within the Agent Overview
D) Advanced server settings within the Endpoint server

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
51
Which two DLP products support the new Optical Character Recognition (OCR) engine in Symantec DLP 15.0? (Choose two.)
A) Endpoint Prevent
B) Cloud Service for Email
C) Network Prevent for Email
D) Network Discover
E) Cloud Detection Service
A) Endpoint Prevent
B) Cloud Service for Email
C) Network Prevent for Email
D) Network Discover
E) Cloud Detection Service

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
52
What detection technology supports partial row matching?
A) Vector Machine Learning (VML)
B) Indexed Document Matching (IDM)
C) Described Content Matching (DCM)
D) Exact Data Matching (EDM)
A) Vector Machine Learning (VML)
B) Indexed Document Matching (IDM)
C) Described Content Matching (DCM)
D) Exact Data Matching (EDM)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
53
A company needs to implement Data Owner Exception so that incidents are avoided when employees send or receive their own personal information. What detection method should the company use?
A) Indexed Document Matching (IDM)
B) Vector Machine Learning (VML)
C) Exact Data Matching (EDM)
D) Described Content Matching (DCM)
A) Indexed Document Matching (IDM)
B) Vector Machine Learning (VML)
C) Exact Data Matching (EDM)
D) Described Content Matching (DCM)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
54
Which server target uses the "Automated Incident Remediation Tracking" feature in Symantec DLP?
A) Exchange
B) File System
C) Lotus Notes
D) SharePoint
A) Exchange
B) File System
C) Lotus Notes
D) SharePoint

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
55
What is the correct order for data in motion when a customer has integrated their CloudSOC and DLP solutions?
A) User > CloudSOC Gatelet > DLP Cloud Detection Service > Application
B) User > Enforce > Application
C) User > Enforce > CloudSOC > Application
D) User > CloudSOC Gatelet > Enforce > Application
A) User > CloudSOC Gatelet > DLP Cloud Detection Service > Application
B) User > Enforce > Application
C) User > Enforce > CloudSOC > Application
D) User > CloudSOC Gatelet > Enforce > Application

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
56
Which two factors are common sources of data leakage where the main actor is well-meaning insider? (Choose two.)
A) An absence of a trained incident response team
B) A disgruntled employee for a job with a competitor
C) Merger and Acquisition activities
D) Lack of training and awareness
E) Broken business processes
A) An absence of a trained incident response team
B) A disgruntled employee for a job with a competitor
C) Merger and Acquisition activities
D) Lack of training and awareness
E) Broken business processes

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
57
A software company wants to protect its source code, including new source code created between scheduled indexing runs. Which detection method should the company use to meet this requirement?
A) Exact Data Matching (EDM)
B) Described Content Matching (DCM)
C) Vector Machine Learning (VML)
D) Indexed Document Matching (IDM)
A) Exact Data Matching (EDM)
B) Described Content Matching (DCM)
C) Vector Machine Learning (VML)
D) Indexed Document Matching (IDM)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
58
Which tool must a DLP administrator run to certify the database prior to upgrading DLP?
A) Lob_Tablespace Reclamation Tool
B) Upgrade Readiness Tool
C) SymDiag
D) EnforceMigrationUtility
A) Lob_Tablespace Reclamation Tool
B) Upgrade Readiness Tool
C) SymDiag
D) EnforceMigrationUtility

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
59
Which two technologies should an organization utilize for integration with the Network Prevent products? (choose two.)
A) Network Tap
B) Network Firewall
C) Proxy Server
D) Mail Transfer Agent
E) Encryption Appliance
A) Network Tap
B) Network Firewall
C) Proxy Server
D) Mail Transfer Agent
E) Encryption Appliance

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
60
Which Network Prevent action takes place when the Network Incident list shows the message is "Modified"?
A) Remove attachments from an email
B) Obfuscate text in the body of an email
C) Add one or more SMTP headers to an email
D) Modify content from the body of an email
A) Remove attachments from an email
B) Obfuscate text in the body of an email
C) Add one or more SMTP headers to an email
D) Modify content from the body of an email

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
61
When configuring remote logging, where are the logs redirected?
A) The primary control center
B) Symantec System Incident Manager (SSIM)
C) Application Eventlog
D) syslog
A) The primary control center
B) Symantec System Incident Manager (SSIM)
C) Application Eventlog
D) syslog

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
62
A DLP administrator is testing Network Prevent for Web functionality. When the administrator posts a small test file to a cloud storage website, no new incidents are reported. What should the administrator do to allow incidents to be generated against this file?
A) Change the "Ignore requests Smaller Than" value to 1
B) Add the filename to the Inspect Content Type field
C) Change the "PacketCapture.DISCARD_HTTP_GET" value to "false"
D) Uncheck trial mode under the ICAP tab
A) Change the "Ignore requests Smaller Than" value to 1
B) Add the filename to the Inspect Content Type field
C) Change the "PacketCapture.DISCARD_HTTP_GET" value to "false"
D) Uncheck trial mode under the ICAP tab

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
63
Which action is available for use in both Smart Response and Automated Response rules?
A) Log to a Syslog Server
B) Limit incident data retention
C) Modify SMTP message
D) Block email message
A) Log to a Syslog Server
B) Limit incident data retention
C) Modify SMTP message
D) Block email message

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
64
Which option is an accurate use case for Information Centric Encryption (ICE)?
A) The ICE utility encrypts files matching DLP policy being copied from network share through use of encryption keys.
B) The ICE utility encrypts files matching DLP policy being copied to removable storage through use of encryption keys.
C) The ICE utility encrypts files matching DLP policy being copied to removable storage on an endpoint use of certificates.
D) The ICE utility encrypts files matching DLP policy being copied from network share through use of certificates
A) The ICE utility encrypts files matching DLP policy being copied from network share through use of encryption keys.
B) The ICE utility encrypts files matching DLP policy being copied to removable storage through use of encryption keys.
C) The ICE utility encrypts files matching DLP policy being copied to removable storage on an endpoint use of certificates.
D) The ICE utility encrypts files matching DLP policy being copied from network share through use of certificates

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
65
Having received a targeted attack from a spoofed email domain, a company wants to take advantage of DKIM validation for inbound mail. The messaging administrator has enabled sender authentication and DKIM validation and now needs to configure a content filtering policy to quarantine any messages that fail. Which condition should be met for the content filtering policy to fire?
A) The envelope sender email address contains "dkim=fail".
B) The message header contains "dkim=fail".
C) The file metadata MIME type is "dkim=fail".
D) The text in the subject, body, or attachments contains "dkim=fail".
A) The envelope sender email address contains "dkim=fail".
B) The message header contains "dkim=fail".
C) The file metadata MIME type is "dkim=fail".
D) The text in the subject, body, or attachments contains "dkim=fail".

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
66
An organization has an extremely large LDAP database. What is done in Symantec Messaging Gateway 10.5 that will help prevent mail from backing up in the system during the initial directory building process?
A) reduce the length of time that logs and quarantine items are kept in the database
B) configure the control center to download the complete directory of users each night
C) the appliance fails open during the initial phase of deployment to prevent email from backing up during the initial directory building process
D) preload the directory data cache
A) reduce the length of time that logs and quarantine items are kept in the database
B) configure the control center to download the complete directory of users each night
C) the appliance fails open during the initial phase of deployment to prevent email from backing up during the initial directory building process
D) preload the directory data cache

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
67
An administrator is unable to log in to the Enforce management console as "sysadmin". Symantec DLP is configured to use Active Directory authentication. The administrator is a member of two roles: "sysadmin" and "remediator." How should the administrator log in to the Enforce console with the "sysadmin" role?
A) sysadmin\username
B) sysadmin\username@domain
C) domain\username
D) username\sysadmin
A) sysadmin\username
B) sysadmin\username@domain
C) domain\username
D) username\sysadmin

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
68
Why would an administrator set the Similarity Threshold to s=zero when testing and tuning a Vector Machine Learning (VML) profile?
A) To capture the matches to the Positive set
B) To capture the matches to the negative set
C) To see the false negatives only
D) To see the entire range of potential matches
A) To capture the matches to the Positive set
B) To capture the matches to the negative set
C) To see the false negatives only
D) To see the entire range of potential matches

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
69
What is an advantage of Symantec Content Encryption over TLS encryption?
A) Ensures compliance with government-mandated regulations
B) TLS encryption provides better security than content encryption.
C) May be implemented without requiring SSL certificates for each scanner
D) Ensures secure end-to-end delivery of sensitive messages
A) Ensures compliance with government-mandated regulations
B) TLS encryption provides better security than content encryption.
C) May be implemented without requiring SSL certificates for each scanner
D) Ensures secure end-to-end delivery of sensitive messages

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
70
An organization wants to restrict employees to copy files only a specific set of USB thumb drives owned by the organization. Which detection method should the organization use to meet this requirement?
A) Exact Data Matching (EDM)
B) Indexed Document Matching (IDM)
C) Described Content Matching (DCM)
D) Vector Machine Learning (VML)
A) Exact Data Matching (EDM)
B) Indexed Document Matching (IDM)
C) Described Content Matching (DCM)
D) Vector Machine Learning (VML)

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
71
Which command is used to collect the configuration and log files from the command line interface (CLI)?
A) diagnostics
B) mallog
C) collect-logs
D) cc-config
A) diagnostics
B) mallog
C) collect-logs
D) cc-config

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
72
Which two functions of Symantec Messaging Gateway 10.5 can use information retrieved from a directory data source? (Select two.)
A) masquerading
B) routing
C) annotation
D) reputation
E) authentication
A) masquerading
B) routing
C) annotation
D) reputation
E) authentication

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
73
How does enabling and configuring sender authentication options in Symantec Messaging Gateway 10.5 help to protect against spam?
A) by protecting against messages sent from trusted partners
B) by protecting against messages sent using a Sendmail MTA
C) by protecting against messages with a forged message ID
D) by protecting against messages with forged sender domains
A) by protecting against messages sent from trusted partners
B) by protecting against messages sent using a Sendmail MTA
C) by protecting against messages with a forged message ID
D) by protecting against messages with forged sender domains

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
74
Which log would an administrator access to determine why an email was deleted by the scanner?
A) Update.log
B) Message Audit logs
C) Admin Audit logs
D) Messaginglog.log
A) Update.log
B) Message Audit logs
C) Admin Audit logs
D) Messaginglog.log

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
75
Which command allows the administrator to track messages from the command line interface (CLI)?
A) track message
B) monitor
C) malquery
D) message query
A) track message
B) monitor
C) malquery
D) message query

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
76
Which logs will help an administrator determine why antispam rules have failed to update?
A) Antispam Update logs
B) LiveUpdate logs
C) Conduit logs
D) Appliance syslog
A) Antispam Update logs
B) LiveUpdate logs
C) Conduit logs
D) Appliance syslog

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
77
Which two tasks can an end-user perform while logged in to the Control Center when authentication and address resolution are enabled? (Select two.)
A) configure personal suspect spam scoring
B) configure personal Good and Bad Sender lists
C) configure personal language preferences
D) configure personal content filtering policies
E) configure personal email digest preferences
A) configure personal suspect spam scoring
B) configure personal Good and Bad Sender lists
C) configure personal language preferences
D) configure personal content filtering policies
E) configure personal email digest preferences

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
78
Symantec Messaging Gateway 10.5 includes a policy-based encryption feature. How is this new feature licensed?
A) The license is included with Symantec Protection Suite.
B) The license is included with Symantec Messaging Gateway 10.5.
C) The license is included with Symantec Content Encryption.
D) The license is available with a PGP Universal license.
A) The license is included with Symantec Protection Suite.
B) The license is included with Symantec Messaging Gateway 10.5.
C) The license is included with Symantec Content Encryption.
D) The license is available with a PGP Universal license.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
79
A DLP administrator is attempting to add a new Network Discover detection server from the Enforce management console. However, the only available options are Network Monitor and Endpoint servers. What should the administrator do to make the Network Discover option available?
A) Restart the Symantec DLP Controller service
B) Apply a new software license file from the Enforce console
C) Install a new Network Discover detection server
D) Restart the Vontu Monitor Service
A) Restart the Symantec DLP Controller service
B) Apply a new software license file from the Enforce console
C) Install a new Network Discover detection server
D) Restart the Vontu Monitor Service

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck
80
A DLP administrator created a new agent configuration for an Endpoint server. However, the endpoint agents fail to receive the new configuration. What is one possible reason that the agent fails to receive the new configuration?
A) The new agent configuration was saved but not applied to any endpoint groups.
B) The new agent configuration was copied and modified from the default agent configuration.
C) The default agent configuration must be disabled before the new configuration can take effect.
D) The Endpoint server needs to be recycled so that the new agent configuration can take effect.
A) The new agent configuration was saved but not applied to any endpoint groups.
B) The new agent configuration was copied and modified from the default agent configuration.
C) The default agent configuration must be disabled before the new configuration can take effect.
D) The Endpoint server needs to be recycled so that the new agent configuration can take effect.

Unlock Deck
Unlock for access to all 138 flashcards in this deck.
Unlock Deck
k this deck


