Deck 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/75
Play
Full screen (f)
Deck 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)
1
Which two action types are performed by Cisco ESA message filters? (Choose two.)
A) non-final actions
B) filter actions
C) discard actions
D) final actions
E) quarantine actions
A) non-final actions
B) filter actions
C) discard actions
D) final actions
E) quarantine actions
non-final actions
final actions
final actions
2
Which benefit does enabling external spam quarantine on Cisco SMA provide?
A) ability to back up spam quarantine from multiple Cisco ESAs to one central console
B) access to the spam quarantine interface on which a user can release, duplicate, or delete
C) ability to scan messages by using two engines to increase a catch rate
D) ability to consolidate spam quarantine data from multiple Cisco ESA to one central console
A) ability to back up spam quarantine from multiple Cisco ESAs to one central console
B) access to the spam quarantine interface on which a user can release, duplicate, or delete
C) ability to scan messages by using two engines to increase a catch rate
D) ability to consolidate spam quarantine data from multiple Cisco ESA to one central console
ability to consolidate spam quarantine data from multiple Cisco ESA to one central console
3
When email authentication is configured on Cisco ESA, which two key types should be selected on the signing profile? (Choose two.)
A) DKIM
B) Public Keys
C) Domain Keys
D) Symmetric Keys
E) Private Keys
A) DKIM
B) Public Keys
C) Domain Keys
D) Symmetric Keys
E) Private Keys
DKIM
Domain Keys
Domain Keys
4
An administrator is trying to enable centralized PVO but receives the error, "Unable to proceed with Centralized Policy, Virus and Outbreak Quarantines configuration as esa1 in Cluster has content filters / DLP actions available at a level different from the cluster level." What is the cause of this error?
A) Content filters are configured at the machine-level on esa1.
B) DLP is configured at the cluster-level on esa2.
C) DLP is configured at the domain-level on esa1.
D) DLP is not configured on host1.
A) Content filters are configured at the machine-level on esa1.
B) DLP is configured at the cluster-level on esa2.
C) DLP is configured at the domain-level on esa1.
D) DLP is not configured on host1.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
5
Which suboption must be selected when LDAP is configured for Spam Quarantine End-User Authentication?
A) Designate as the active query
B) Update Frequency
C) Server Priority
D) Entity ID
A) Designate as the active query
B) Update Frequency
C) Server Priority
D) Entity ID

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
6
What are two phases of the Cisco ESA email pipeline? (Choose two.)
A) reject
B) workqueue
C) action
D) delivery
E) quarantine
A) reject
B) workqueue
C) action
D) delivery
E) quarantine

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
7
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
A) NetFlow
B) geolocation-based filtering
C) heuristic-based filtering
D) senderbase reputation filtering
E) content disarm and reconstruction
A) NetFlow
B) geolocation-based filtering
C) heuristic-based filtering
D) senderbase reputation filtering
E) content disarm and reconstruction

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
8
Email encryption is configured on a Cisco ESA that uses CRES. Which action is taken on a message when CRES is unavailable?
A) It is requeued.
B) It is sent in clear text.
C) It is dropped and an error message is sent to the sender.
D) It is encrypted by a Cisco encryption appliance.
A) It is requeued.
B) It is sent in clear text.
C) It is dropped and an error message is sent to the sender.
D) It is encrypted by a Cisco encryption appliance.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
9
Which two actions are configured on the Cisco ESA to query LDAP servers? (Choose two.)
A) accept
B) relay
C) delay
D) route
E) reject
A) accept
B) relay
C) delay
D) route
E) reject

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
10
How does the graymail safe unsubscribe feature function?
A) It strips the malicious content of the URI before unsubscribing.
B) It checks the URI reputation and category and allows the content filter to take an action on it.
C) It redirects the end user who clicks the unsubscribe button to a sandbox environment to allow a safe unsubscribe.
D) It checks the reputation of the URI and performs the unsubscribe process on behalf of the end user.
A) It strips the malicious content of the URI before unsubscribing.
B) It checks the URI reputation and category and allows the content filter to take an action on it.
C) It redirects the end user who clicks the unsubscribe button to a sandbox environment to allow a safe unsubscribe.
D) It checks the reputation of the URI and performs the unsubscribe process on behalf of the end user.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
11
Which two statements about configuring message filters within the Cisco ESA are true? (Choose two.)
A) The filters command executed from the CLI is used to configure the message filters. The filters command executed from the CLI is used to configure the message filters.
B) Message filters configuration within the web user interface is located within Incoming Content Filters . Message filters configuration within the web user interface is located within Incoming Content Filters .
C) The filterconfig command executed from the CLI is used to configure message filters. filterconfig command executed from the CLI is used to configure message filters.
D) Message filters can be configured only from the CLI.
E) Message filters can be configured only from the web user interface.
A) The filters command executed from the CLI is used to configure the message filters. The filters command executed from the CLI is used to configure the message filters.
B) Message filters configuration within the web user interface is located within Incoming Content Filters . Message filters configuration within the web user interface is located within Incoming Content Filters .
C) The filterconfig command executed from the CLI is used to configure message filters. filterconfig command executed from the CLI is used to configure message filters.
D) Message filters can be configured only from the CLI.
E) Message filters can be configured only from the web user interface.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
12
Which action is a valid fallback when a client certificate is unavailable during SMTP authentication on Cisco ESA?
A) LDAP Query
B) SMTP AUTH
C) SMTP TLS
D) LDAP BIND
A) LDAP Query
B) SMTP AUTH
C) SMTP TLS
D) LDAP BIND

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
13
An analyst creates a new content dictionary to use with Forged Email Detection. Which entry will be added into the dictionary?
A) mycompany.com
B) Alpha Beta
C) ^Alpha\ Beta$
D) Alpha.Beta@mycompany.com
A) mycompany.com
B) Alpha Beta
C) ^Alpha\ Beta$
D) Alpha.Beta@mycompany.com

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
14
Which method enables an engineer to deliver a flagged message to a specific virtual gateway address in the most flexible way?
A) Set up the interface group with the flag.
B) Issue the altsrchost command. Issue the altsrchost command.
C) Map the envelope sender address to the host.
D) Apply a filter on the message.
A) Set up the interface group with the flag.
B) Issue the altsrchost command. Issue the altsrchost command.
C) Map the envelope sender address to the host.
D) Apply a filter on the message.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
15
Which two query types are available when an LDAP profile is configured? (Choose two.)
A) proxy consolidation
B) user
C) recursive
D) group
E) routing
A) proxy consolidation
B) user
C) recursive
D) group
E) routing

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
16
Which feature utilizes sensor information obtained from Talos intelligence to filter email servers connecting into the Cisco ESA?
A) SenderBase Reputation Filtering
B) Connection Reputation Filtering
C) Talos Reputation Filtering
D) SpamCop Reputation Filtering
A) SenderBase Reputation Filtering
B) Connection Reputation Filtering
C) Talos Reputation Filtering
D) SpamCop Reputation Filtering

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
17
What is the order of virus scanning when multilayer antivirus scanning is configured?
A) The default engine scans for viruses first and the McAfee engine scans for viruses second.
B) The Sophos engine scans for viruses first and the McAfee engine scans for viruses second.
C) The McAfee engine scans for viruses first and the default engine scans for viruses second.
D) The McAfee engine scans for viruses first and the Sophos engine scans for viruses second.
A) The default engine scans for viruses first and the McAfee engine scans for viruses second.
B) The Sophos engine scans for viruses first and the McAfee engine scans for viruses second.
C) The McAfee engine scans for viruses first and the default engine scans for viruses second.
D) The McAfee engine scans for viruses first and the Sophos engine scans for viruses second.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
18
Which SMTP extension does Cisco ESA support for email security?
A) ETRN
B) UTF8SMTP
C) PIPELINING
D) STARTTLS
A) ETRN
B) UTF8SMTP
C) PIPELINING
D) STARTTLS

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
19
Which two steps configure Forged Email Detection? (Choose two.)
A) Configure a content dictionary with executive email addresses.
B) Configure a filter to use the Forged Email Detection rule and dictionary.
C) Configure a filter to check the Header From value against the Forged Email Detection dictionary.
D) Enable Forged Email Detection on the Security Services page.
E) Configure a content dictionary with friendly names.
A) Configure a content dictionary with executive email addresses.
B) Configure a filter to use the Forged Email Detection rule and dictionary.
C) Configure a filter to check the Header From value against the Forged Email Detection dictionary.
D) Enable Forged Email Detection on the Security Services page.
E) Configure a content dictionary with friendly names.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
20
Which two factors must be considered when message filter processing is configured? (Choose two.)
A) message-filter order
B) lateral processing
C) structure of the combined packet
D) mail policies
E) MIME structure of the message
A) message-filter order
B) lateral processing
C) structure of the combined packet
D) mail policies
E) MIME structure of the message

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
21
What is a valid content filter action?
A) decrypt on delivery
B) quarantine
C) skip antispam
D) archive
A) decrypt on delivery
B) quarantine
C) skip antispam
D) archive

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
22
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
A) redirect
B) return
C) drop
D) delay
E) abandon
A) redirect
B) return
C) drop
D) delay
E) abandon

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
23
Which action must be taken before a custom quarantine that is being used can be deleted?
A) Delete the quarantine that is assigned to a filter.
B) Delete the quarantine that is not assigned to a filter.
C) Delete only the unused quarantine.
D) Remove the quarantine from the message action of a filter.
A) Delete the quarantine that is assigned to a filter.
B) Delete the quarantine that is not assigned to a filter.
C) Delete only the unused quarantine.
D) Remove the quarantine from the message action of a filter.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
24
Which two components form the graymail management solution in Cisco ESA? (Choose two.)
A) cloud-based unsubscribe service
B) uniform unsubscription management interface for end users
C) secure subscribe option for end users
D) integrated graymail scanning engine
E) improved mail efficacy
A) cloud-based unsubscribe service
B) uniform unsubscription management interface for end users
C) secure subscribe option for end users
D) integrated graymail scanning engine
E) improved mail efficacy

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
25
Which two certificate authority lists are available in Cisco ESA? (Choose two.)
A) default
B) system
C) user
D) custom
E) demo
A) default
B) system
C) user
D) custom
E) demo

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
26
What is the default port to deliver emails from the Cisco ESA to the Cisco SMA using the centralized Spam Quarantine?
A) 8025
B) 6443
C) 6025
D) 8443
A) 8025
B) 6443
C) 6025
D) 8443

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
27
Which attack is mitigated by using Bounce Verification?
A) spoof
B) denial of service
C) eavesdropping
D) smurf
A) spoof
B) denial of service
C) eavesdropping
D) smurf

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
28
Which two features are applied to either incoming or outgoing mail policies? (Choose two.)
A) Indication of Compromise
B) application filtering
C) outbreak filters
D) sender reputation filtering
E) antivirus
A) Indication of Compromise
B) application filtering
C) outbreak filters
D) sender reputation filtering
E) antivirus

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
29
Which feature must be configured before an administrator can use the outbreak filter for nonviral threats?
A) quarantine threat level
B) antispam
C) data loss prevention
D) antivirus
A) quarantine threat level
B) antispam
C) data loss prevention
D) antivirus

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
30
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
A) Enable outbreak filters.
B) Enable email relay.
C) Enable antispam scanning.
D) Enable port bouncing.
E) Enable antivirus scanning.
A) Enable outbreak filters.
B) Enable email relay.
C) Enable antispam scanning.
D) Enable port bouncing.
E) Enable antivirus scanning.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
31
Which two steps are needed to disable local spam quarantine before external quarantine is enabled? (Choose two.)
A) Uncheck the Enable Spam Quarantine check box. Uncheck the Enable Spam Quarantine check box.
B) Select Monitor and click Spam Quarantine . Select Monitor and click Spam Quarantine .
C) Check the External Safelist/Blocklist check box. Check the External Safelist/Blocklist
D) Select External Spam Quarantine and click on Configure . External Spam Quarantine and click on Configure
E) Select Security Services and click Spam Quarantine . Security Services
A) Uncheck the Enable Spam Quarantine check box. Uncheck the Enable Spam Quarantine check box.
B) Select Monitor and click Spam Quarantine . Select Monitor and click Spam Quarantine .
C) Check the External Safelist/Blocklist check box. Check the External Safelist/Blocklist
D) Select External Spam Quarantine and click on Configure . External Spam Quarantine and click on Configure
E) Select Security Services and click Spam Quarantine . Security Services

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
32
Which process is skipped when an email is received from safedomain.com, which is on the safelist?
A) message filter
B) antivirus scanning
C) outbreak filter
D) antispam scanning
A) message filter
B) antivirus scanning
C) outbreak filter
D) antispam scanning

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
33
When the Cisco ESA is configured to perform antivirus scanning, what is the default timeout value?
A) 30 seconds
B) 90 seconds
C) 60 seconds
D) 120 seconds
A) 30 seconds
B) 90 seconds
C) 60 seconds
D) 120 seconds

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
34
What are two primary components of content filters? (Choose two.)
A) conditions
B) subject
C) content
D) actions
E) policies
A) conditions
B) subject
C) content
D) actions
E) policies

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
35
When virtual gateways are configured, which two distinct attributes are allocated to each virtual gateway address? (Choose two.)
A) domain
B) IP address
C) DNS server address
D) DHCP server address
E) external spam quarantine
A) domain
B) IP address
C) DNS server address
D) DHCP server address
E) external spam quarantine

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
36
When DKIM signing is configured, which DNS record must be updated to load the DKIM public signing key?
A) AAAA record
B) PTR record
C) TXT record
D) MX record
A) AAAA record
B) PTR record
C) TXT record
D) MX record

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
37
Which global setting is configured under Cisco ESA Scan Behavior?
A) minimum attachment size to scan
B) attachment scanning timeout
C) actions for unscannable messages due to attachment type
D) minimum depth of attachment recursion to scan
A) minimum attachment size to scan
B) attachment scanning timeout
C) actions for unscannable messages due to attachment type
D) minimum depth of attachment recursion to scan

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
38
Which type of attack is prevented by configuring file reputation filtering and file analysis features?
A) denial of service
B) zero-day
C) backscatter
D) phishing
A) denial of service
B) zero-day
C) backscatter
D) phishing

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
39
What is the maximum message size that can be configured for encryption on the Cisco ESA?
A) 20 MB
B) 25 MB
C) 15 MB
D) 30 MB
A) 20 MB
B) 25 MB
C) 15 MB
D) 30 MB

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
40
What is the default HTTPS port when configuring spam quarantine on Cisco ESA?
A) 83
B) 82
C) 443
D) 80
A) 83
B) 82
C) 443
D) 80

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
41
Which antispam feature is utilized to give end users control to allow emails that are spam to be delivered to their inbox, overriding any spam verdict and action on the Cisco ESA?
A) end user allow list
B) end user spam quarantine access
C) end user passthrough list
D) end user safelist
A) end user allow list
B) end user spam quarantine access
C) end user passthrough list
D) end user safelist

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
42
What is a benefit of implementing URL filtering on the Cisco ESA?
A) removes threats from malicious URLs
B) blacklists spam
C) provides URL reputation protection
D) enhances reputation against malicious URLs
A) removes threats from malicious URLs
B) blacklists spam
C) provides URL reputation protection
D) enhances reputation against malicious URLs

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
43
An administrator identifies that, over the past week, the Cisco ESA is receiving many emails from certain senders and domains which are being consistently quarantined. The administrator wants to ensure that these senders and domain are unable to send anymore emails. Which feature on Cisco ESA should be used to achieve this?
A) incoming mail policies
B) safelist
C) blocklist
D) S/MIME Sending Profile
A) incoming mail policies
B) safelist
C) blocklist
D) S/MIME Sending Profile

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
44
What is the default behavior of any listener for TLS communication?
A) preferred-verify
B) off
C) preferred
D) required
A) preferred-verify
B) off
C) preferred
D) required

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
45
A Cisco ESA administrator has several mail policies configured. While testing policy match using a specific sender, the email was not matching the expected policy. What is the reason of this?
A) The "From" header is checked against all policies in a top-down fashion.
B) The message header with the highest priority is checked against each policy in a top-down fashion.
C) The "To" header is checked against all policies in a top-down fashion.
D) The message header with the highest priority is checked against the Default policy in a top-down fashion.
A) The "From" header is checked against all policies in a top-down fashion.
B) The message header with the highest priority is checked against each policy in a top-down fashion.
C) The "To" header is checked against all policies in a top-down fashion.
D) The message header with the highest priority is checked against the Default policy in a top-down fashion.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
46
Which type of query must be configured when setting up the Spam Quarantine while merging notifications?
A) Spam Quarantine Alias Routing Query
B) Spam Quarantine Alias Consolidation Query
C) Spam Quarantine Alias Authentication Query
D) Spam Quarantine Alias Masquerading Query
A) Spam Quarantine Alias Routing Query
B) Spam Quarantine Alias Consolidation Query
C) Spam Quarantine Alias Authentication Query
D) Spam Quarantine Alias Masquerading Query

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
47
When URL logging is configured on a Cisco ESA, which feature must be enabled first?
A) antivirus
B) antispam
C) virus outbreak filter
D) senderbase reputation filter
A) antivirus
B) antispam
C) virus outbreak filter
D) senderbase reputation filter

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
48
Which two are configured in the DMARC verification profile? (Choose two.)
A) name of the verification profile
B) minimum number of signatures to verify
C) ESA listeners to use the verification profile
D) message action into an incoming or outgoing content filter
E) message action to take when the policy is reject/quarantine
A) name of the verification profile
B) minimum number of signatures to verify
C) ESA listeners to use the verification profile
D) message action into an incoming or outgoing content filter
E) message action to take when the policy is reject/quarantine

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
49
Which scenario prevents a message from being sent to the quarantine as an action in the scan behavior on Cisco ESA?
A) A policy quarantine is missing.
B) More than one email pipeline is defined.
C) The "modify the message subject" is already set.
D) The "add custom header" action is performed first.
A) A policy quarantine is missing.
B) More than one email pipeline is defined.
C) The "modify the message subject" is already set.
D) The "add custom header" action is performed first.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
50
An administrator is managing multiple Cisco ESA devices and wants to view the quarantine emails from all devices in a central location. How is this accomplished?
A) Disable the VOF feature before sending SPAM to the external quarantine.
B) Configure a mail policy to determine whether the message is sent to the local or external quarantine.
C) Disable the local quarantine before sending SPAM to the external quarantine.
D) Configure a user policy to determine whether the message is sent to the local or external quarantine.
A) Disable the VOF feature before sending SPAM to the external quarantine.
B) Configure a mail policy to determine whether the message is sent to the local or external quarantine.
C) Disable the local quarantine before sending SPAM to the external quarantine.
D) Configure a user policy to determine whether the message is sent to the local or external quarantine.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
51
A Cisco ESA administrator was notified that a user was not receiving emails from a specific domain. After reviewing the mail logs, the sender had a negative sender-based reputation score. What should the administrator do to allow inbound email from that specific domain?
A) Create a new inbound mail policy with a message filter that overrides Talos.
B) Ask the user to add the sender to the email application's allow list.
C) Modify the firewall to allow emails from the domain.
D) Add the domain into the allow list.
A) Create a new inbound mail policy with a message filter that overrides Talos.
B) Ask the user to add the sender to the email application's allow list.
C) Modify the firewall to allow emails from the domain.
D) Add the domain into the allow list.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
52
What must be configured to allow the Cisco ESA to encrypt an email using the Cisco Registered Envelope Service?
A) provisioned email encryption profile
B) message encryption from a content filter that select "Message Encryption" over TLS
C) message encryption from the mail flow policies with "CRES" selected
D) content filter to forward the email to the Cisco Registered Envelope server
A) provisioned email encryption profile
B) message encryption from a content filter that select "Message Encryption" over TLS
C) message encryption from the mail flow policies with "CRES" selected
D) content filter to forward the email to the Cisco Registered Envelope server

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
53
What occurs when configuring separate incoming mail policies?
A) message splintering
B) message exceptions
C) message detachment
D) message aggregation
A) message splintering
B) message exceptions
C) message detachment
D) message aggregation

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
54
An engineer is testing mail flow on a new Cisco ESA and notices that messages for domain abc.com are stuck in the delivery queue. Upon further investigation, the engineer notices that the messages pending delivery are destined for 192.168.1.11, when they should instead be routed to 192.168.1.10. What configuration change needed to address this issue?
A) Add an address list for domain abc.com.
B) Modify Destination Controls entry for the domain abc.com.
C) Modify the SMTP route for the domain and change the IP address to 192.168.1.10.
D) Modify the Routing Tables and add a route for IP address to 192.168.1.10.
A) Add an address list for domain abc.com.
B) Modify Destination Controls entry for the domain abc.com.
C) Modify the SMTP route for the domain and change the IP address to 192.168.1.10.
D) Modify the Routing Tables and add a route for IP address to 192.168.1.10.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
55
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
A) Show the SLBL cache on the CLI.
B) Monitor Incoming/Outgoing Listener.
C) Export the SLBL to a .csv file.
D) Debug the mail flow policy.
A) Show the SLBL cache on the CLI.
B) Monitor Incoming/Outgoing Listener.
C) Export the SLBL to a .csv file.
D) Debug the mail flow policy.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
56
Which setting affects the aggressiveness of spam detection?
A) protection level
B) spam threshold
C) spam timeout
D) maximum depth of recursion scan
A) protection level
B) spam threshold
C) spam timeout
D) maximum depth of recursion scan

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
57
A network administrator is modifying an outgoing mail policy to enable domain protection for the organization. A DNS entry is created that has the public key. Which two headers will be used as matching criteria in the outgoing mail policy? (Choose two.)
A) message-ID
B) sender
C) URL reputation
D) from
E) mail-from
A) message-ID
B) sender
C) URL reputation
D) from
E) mail-from

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
58
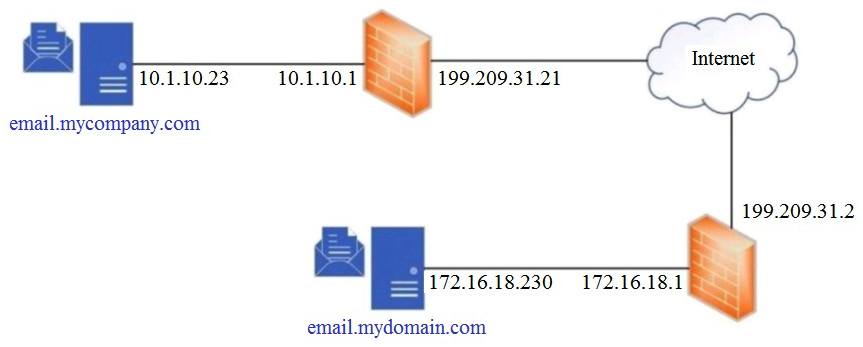 Refer to the exhibit. Which SPF record is valid for mycompany.com?
Refer to the exhibit. Which SPF record is valid for mycompany.com?A) v=spf1 a mx ip4:199.209.31.2 -all
B) v=spf1 a mx ip4:10.1.10.23 -all
C) v=spf1 a mx ip4:199.209.31.21 -all
D) v=spf1 a mx ip4:172.16.18.230 -all

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
59
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
A) Enabling the End-User Safelist/Blocklist feature
B) Spam Quarantine External Authentication Query
C) Spam Quarantine End-User Authentication Query
D) Spam Quarantine Alias Consolidation Query
A) Enabling the End-User Safelist/Blocklist feature
B) Spam Quarantine External Authentication Query
C) Spam Quarantine End-User Authentication Query
D) Spam Quarantine Alias Consolidation Query

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
60
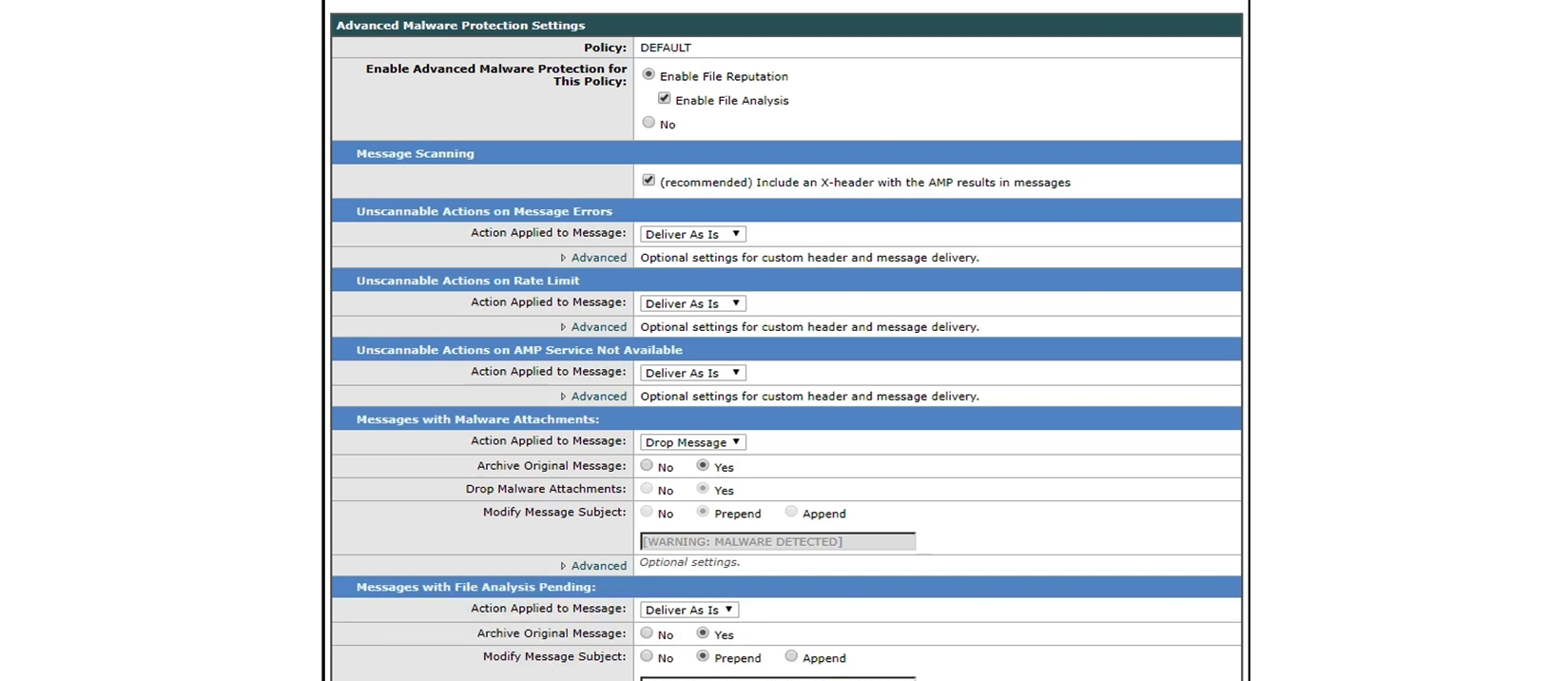 Refer to the exhibit. How should this configuration be modified to stop delivering Zero Day malware attacks?
Refer to the exhibit. How should this configuration be modified to stop delivering Zero Day malware attacks?A) Change Unscannable Action from Deliver As Is to Quarantine.
B) Change File Analysis Pending action from Deliver As Is to Quarantine.
C) Configure mailbox auto-remediation.
D) Apply Prepend on Modify Message Subject under Malware Attachments.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
61
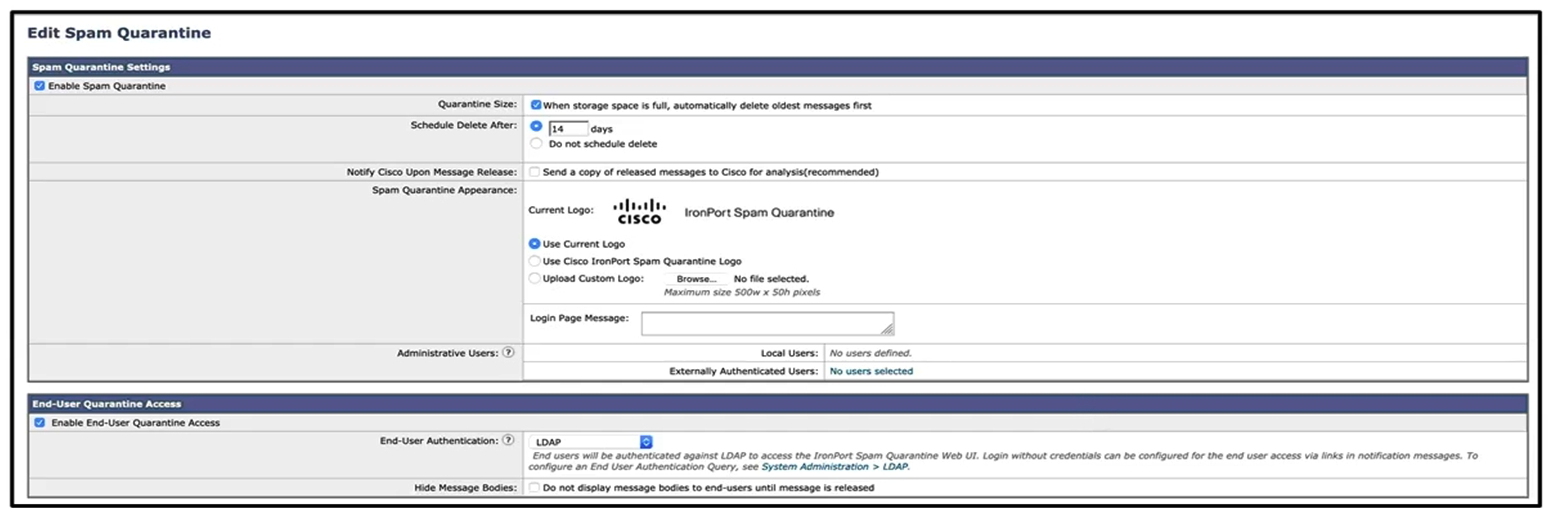
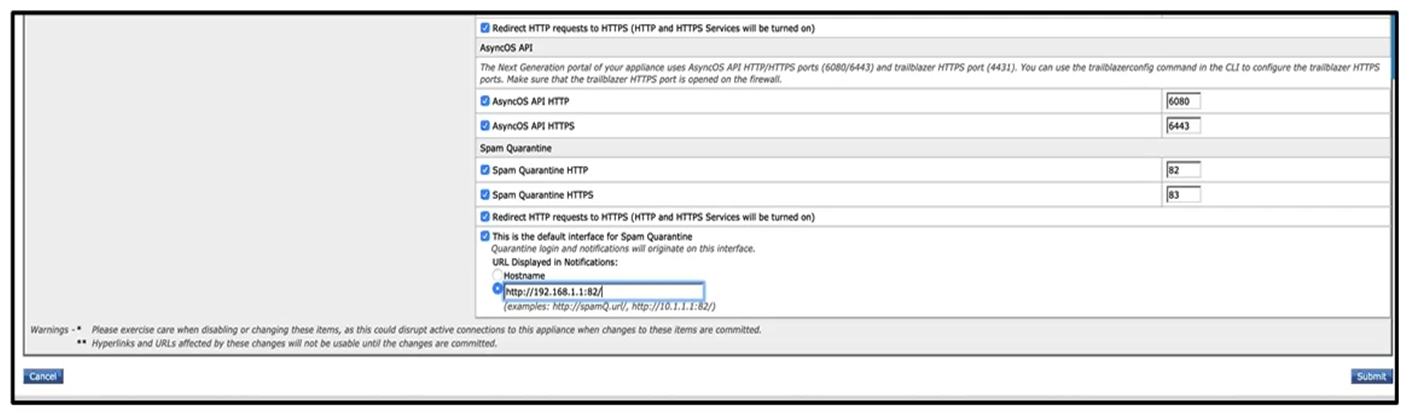 Refer to the exhibits. What must be done to enforce end user authentication before accessing quarantine?
Refer to the exhibits. What must be done to enforce end user authentication before accessing quarantine?A) Enable SPAM notification and use LDAP for authentication.
B) Enable SPAM Quarantine Notification and add the %quarantine_url% variable.
C) Change the end user quarantine access from None authentication to SAAS.
D) Change the end user quarantine access setting from None authentication to Mailbox.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
62
Which feature must be enabled first when URL logging is configured on a Cisco ESA?
A) antivirus
B) antispam
C) senderbase reputation filter
D) virus outbreak filter
A) antivirus
B) antispam
C) senderbase reputation filter
D) virus outbreak filter

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
63
An administrator has created a content filter to quarantine all messages that result in an SPF hardfail to review the messages and determine whether a trusted partner has accidentally misconfigured the DNS settings. The administrator sets the policy quarantine to release the messages after 24 hours, allowing time to review while not interrupting business. Which additional option should be used to help the end users be aware of the elevated risk of interacting with these messages?
A) Notify Recipient
B) Strip Attachments
C) Notify Sender
D) Modify Subject
A) Notify Recipient
B) Strip Attachments
C) Notify Sender
D) Modify Subject

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
64
Which two configurations are used on multiple LDAP servers to connect with Cisco ESA? (Choose two.)
A) load balancing
B) SLA monitor
C) active-standby
D) failover
E) active-active
A) load balancing
B) SLA monitor
C) active-standby
D) failover
E) active-active

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
65
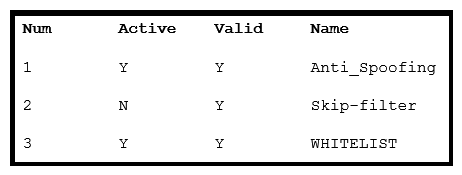 Refer to the exhibit. What is the correct order of commands to set filter 2 to active?
Refer to the exhibit. What is the correct order of commands to set filter 2 to active?A) filters-> edit-> 2-> Active
B) filters-> modify-> All-> Active
C) filters-> detail-> 2-> 1
D) filters-> set-> 2-> 1

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
66
A company has deployed a new mandate that requires all emails sent externally from the Sales Department to be scanned by DLP for PCI-DSS compliance. A new DLP policy has been created on the Cisco ESA and needs to be assigned to a mail policy named 'Sales' that has yet to be created. Which mail policy should be created to accomplish this task?
A) Outgoing Mail Policy
B) Preliminary Mail Policy
C) Incoming Mail Flow Policy
D) Outgoing Mail Flow Policy
A) Outgoing Mail Policy
B) Preliminary Mail Policy
C) Incoming Mail Flow Policy
D) Outgoing Mail Flow Policy

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
67
Which component must be added to the content filter to trigger on failed SPF Verification or DKIM Authentication verdicts?
A) status
B) response
C) parameter
D) condition
A) status
B) response
C) parameter
D) condition

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
68
Which two Cisco ESA features are used to control email delivery based on the sender? (Choose two.)
A) incoming mail policies
B) spam quarantine
C) outbreak filter
D) safelists
E) blocklists
A) incoming mail policies
B) spam quarantine
C) outbreak filter
D) safelists
E) blocklists

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
69
An email containing a URL passes through the Cisco ESA that has content filtering disabled for all mail policies. The sender is sampleuser@test1.com, the recipients are testuser1@test2.com, testuser2@test2.com, testuser3@test2.com, and mailer1@test2.com. The subject of the email is Test Document395898847. An administrator wants to add a policy to ensure that the Cisco ESA evaluates the web reputation score before permitting this email. Which two criteria must be used by the administrator to achieve this? (Choose two.)
A) Subject contains "TestDocument"
B) Sender matches test1.com
C) Email body contains a URL
D) Date and time of email
E) Email does not match mailer1@test2.com
A) Subject contains "TestDocument"
B) Sender matches test1.com
C) Email body contains a URL
D) Date and time of email
E) Email does not match mailer1@test2.com

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
70
An administrator needs to configure Cisco ESA to ensure that emails are sent and authorized by the owner of the domain. Which two steps must be performed to accomplish this task? (Choose two.)
A) Generate keys.
B) Create signing profile.
C) Create Mx record.
D) Enable SPF verification.
E) Create DMARC profile.
A) Generate keys.
B) Create signing profile.
C) Create Mx record.
D) Enable SPF verification.
E) Create DMARC profile.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
71
Which two components must be configured to perform DLP scanning? (Choose two.)
A) Add a DLP policy on the Incoming Mail Policy.
B) Add a DLP policy to the DLP Policy Manager.
C) Enable a DLP policy on the Outgoing Mail Policy.
D) Enable a DLP policy on the DLP Policy Customizations.
E) Add a DLP policy to the Outgoing Content Filter.
A) Add a DLP policy on the Incoming Mail Policy.
B) Add a DLP policy to the DLP Policy Manager.
C) Enable a DLP policy on the Outgoing Mail Policy.
D) Enable a DLP policy on the DLP Policy Customizations.
E) Add a DLP policy to the Outgoing Content Filter.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
72
Users have been complaining of a higher volume of emails containing profanity. The network administrator will need to leverage dictionaries and create specific conditions to reduce the number of inappropriate emails. Which two filters should be configured to address this? (Choose two.)
A) message
B) spam
C) VOF
D) sender group
E) content
A) message
B) spam
C) VOF
D) sender group
E) content

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
73
A Cisco ESA administrator has noticed that new messages being sent to the Centralized Policy Quarantine are being released after one hour. Previously, they were being held for a day before being released. What was configured that caused this to occur?
A) The retention period was changed to one hour.
B) The threshold settings were set to override the clock settings.
C) The retention period was set to default.
D) The threshold settings were set to default.
A) The retention period was changed to one hour.
B) The threshold settings were set to override the clock settings.
C) The retention period was set to default.
D) The threshold settings were set to default.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
74
A recent engine update was pulled down for graymail and has caused the service to start crashing. It is critical to fix this as quickly as possible. What must be done to address this issue?
A) Roll back to a previous version of the engine from the Services Overview page.
B) Roll back to a previous version of the engine from the System Health page.
C) Download another update from the IMS and Graymail page.
D) Download another update from the Service Updates page.
A) Roll back to a previous version of the engine from the Services Overview page.
B) Roll back to a previous version of the engine from the System Health page.
C) Download another update from the IMS and Graymail page.
D) Download another update from the Service Updates page.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
75
A network administrator notices that there are a high number of queries to the LDAP server. The mail logs show an entry "550 Too many invalid recipients | Connection closed by foreign host." Which feature must be used to address this?
A) DHAP
B) SBRS
C) LDAP
D) SMTP
A) DHAP
B) SBRS
C) LDAP
D) SMTP

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck


