Deck 6: DevNet Associate (DEVASC)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/134
Play
Full screen (f)
Deck 6: DevNet Associate (DEVASC)
1
What are two advantages of version control software? (Choose two.)
A) It supports tracking and comparison of changes in binary format files.
B) It allows new team members to access the current code and history.
C) It supports comparisons between revisions of source code files.
D) It provides wiki collaboration software for documentation.
E) It allows old versions of packaged applications to be hosted on the Internet.
A) It supports tracking and comparison of changes in binary format files.
B) It allows new team members to access the current code and history.
C) It supports comparisons between revisions of source code files.
D) It provides wiki collaboration software for documentation.
E) It allows old versions of packaged applications to be hosted on the Internet.
It supports tracking and comparison of changes in binary format files.
It allows new team members to access the current code and history.
It allows new team members to access the current code and history.
2
Refer to the exhibit. 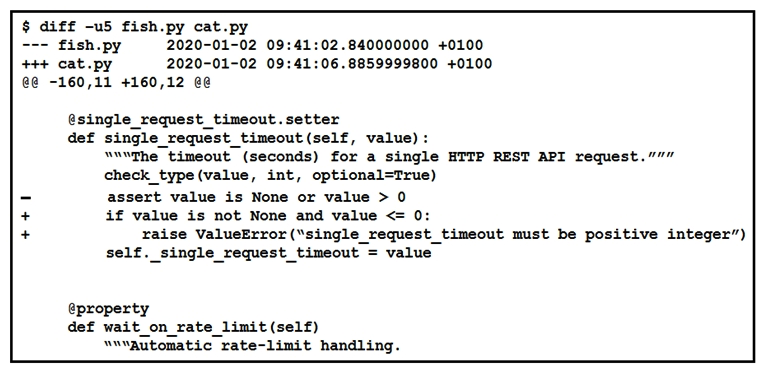 The output of a unified diff when comparing two versions of a Python script is shown. Which two " single_request_timeout() " functions are defined in fish.py and cat.py? (Choose two.)
The output of a unified diff when comparing two versions of a Python script is shown. Which two " single_request_timeout() " functions are defined in fish.py and cat.py? (Choose two.)
A)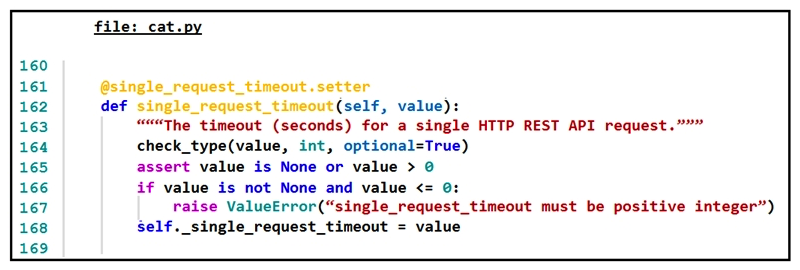
B)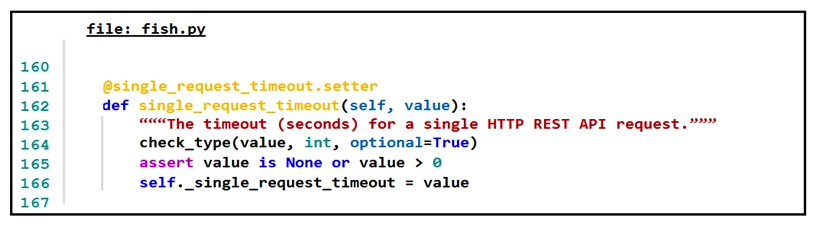
C)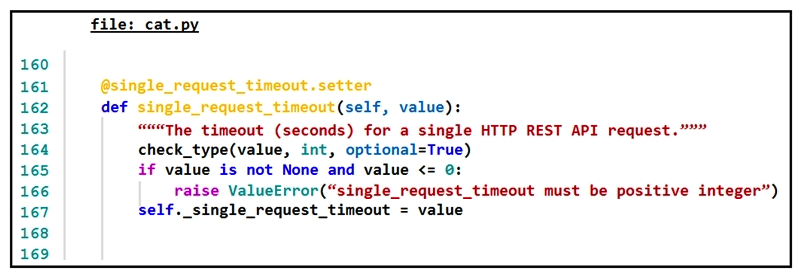
D)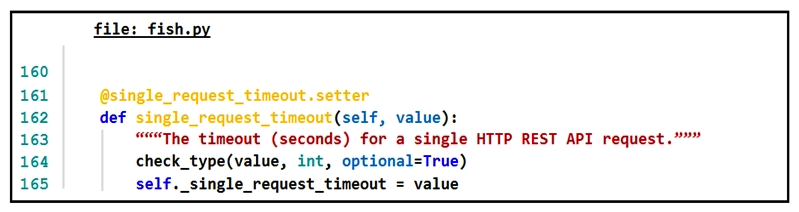
E)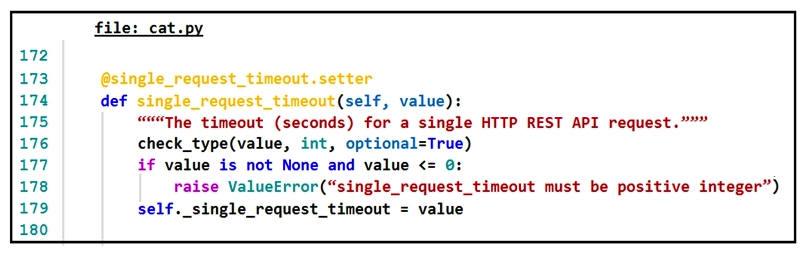
 The output of a unified diff when comparing two versions of a Python script is shown. Which two " single_request_timeout() " functions are defined in fish.py and cat.py? (Choose two.)
The output of a unified diff when comparing two versions of a Python script is shown. Which two " single_request_timeout() " functions are defined in fish.py and cat.py? (Choose two.)A)

B)

C)

D)

E)



3
Which statement describes the benefit of using functions in programming?
A) Functions ensure that a developer understands the inner logic contained before using them as part of a script or application.
B) Functions create the implementation of secret and encrypted algorithms.
C) Functions allow problems to be split into simpler, smaller groups, and reduce code repetition, which makes the code easier to read.
D) Functions store mutable values within a script or application.
A) Functions ensure that a developer understands the inner logic contained before using them as part of a script or application.
B) Functions create the implementation of secret and encrypted algorithms.
C) Functions allow problems to be split into simpler, smaller groups, and reduce code repetition, which makes the code easier to read.
D) Functions store mutable values within a script or application.
Functions allow problems to be split into simpler, smaller groups, and reduce code repetition, which makes the code easier to read.
4
Which two statements describe the advantages of using a version control system? (Choose two.)
A) It allows for branching and merging so that different tasks are worked on in isolation before they are merged into a feature or master branch.
B) It provides tooling to automate application builds and infrastructure provisioning.
C) It allows multiple engineers to work against the same code and configuration files and manage differences and conflicts.
D) It provides a system to track User Stories and allocate to backlogs.
E) It allows developers to write effective unit tests.
A) It allows for branching and merging so that different tasks are worked on in isolation before they are merged into a feature or master branch.
B) It provides tooling to automate application builds and infrastructure provisioning.
C) It allows multiple engineers to work against the same code and configuration files and manage differences and conflicts.
D) It provides a system to track User Stories and allocate to backlogs.
E) It allows developers to write effective unit tests.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
5
Which description of a default gateway is true?
A) It is a security feature that denies certain traffic.
B) It is a device that receives IP packets that have no explicit next-hop in the routing table.
C) It is a feature that translates between public and private addresses.
D) It is a device that receives Layer 2 frames with an unknown destination address.
A) It is a security feature that denies certain traffic.
B) It is a device that receives IP packets that have no explicit next-hop in the routing table.
C) It is a feature that translates between public and private addresses.
D) It is a device that receives Layer 2 frames with an unknown destination address.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
6
Which two elements are foundational principles of DevOps? (Choose two.)
A) organizing cross-functional teams over organizational silos
B) designing applications as microservices
C) encouraging containers for the deployment of applications
D) automating over documenting
E) optimizing the cost of infrastructures
A) organizing cross-functional teams over organizational silos
B) designing applications as microservices
C) encouraging containers for the deployment of applications
D) automating over documenting
E) optimizing the cost of infrastructures

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
7
When a Cisco IOS XE networking device is configured using RESTCONF, what is the default data-encoding method?
A) JSON
B) YAML
C) XML
D) x-form-encoding
A) JSON
B) YAML
C) XML
D) x-form-encoding

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
8
In DNS, which record specifies an alias that refers to another name that ultimately resolves to an IP address?
A) CNAME
B) NS
C) AAA
D) SOA
A) CNAME
B) NS
C) AAA
D) SOA

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
9
Which device is a system that monitors and controls incoming and outgoing network traffic based on predetermined security roles?
A) router
B) switch
C) load balancer
D) firewall
A) router
B) switch
C) load balancer
D) firewall

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
10
Refer to the exhibit.  A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
A) only outbound connections between 3000 and 5000 are possible
B) port 3000
C) any port between 3000 and 5000
D) port 5000
 A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?A) only outbound connections between 3000 and 5000 are possible
B) port 3000
C) any port between 3000 and 5000
D) port 5000

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
11
Refer to the exhibit. 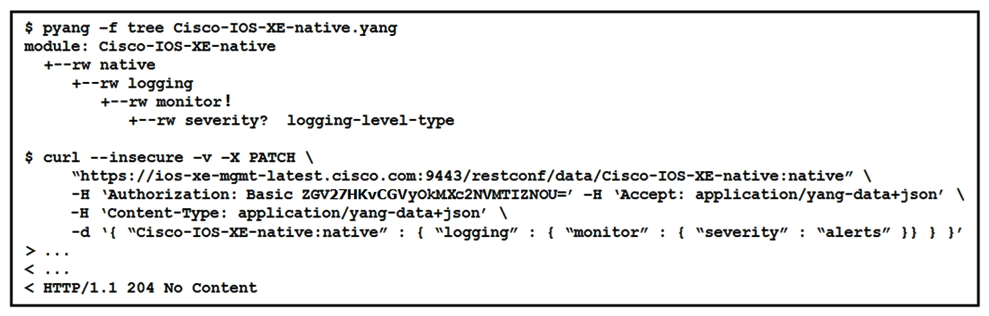 The definition of the YANG module and a RESTCONF query sent to a Cisco IOS XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?
The definition of the YANG module and a RESTCONF query sent to a Cisco IOS XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?
A) The query retrieved the logging severity level.
B) The query updated the logging severity level or created it if not present on the device.
C) The query failed at retrieving the logging severity level.
D) The query failed to set the logging severity level due to an invalid path.
 The definition of the YANG module and a RESTCONF query sent to a Cisco IOS XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?
The definition of the YANG module and a RESTCONF query sent to a Cisco IOS XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?A) The query retrieved the logging severity level.
B) The query updated the logging severity level or created it if not present on the device.
C) The query failed at retrieving the logging severity level.
D) The query failed to set the logging severity level due to an invalid path.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
12
What is the purpose of the Cisco VIRL software tool?
A) to verify configurations against compliance standards
B) to automate API workflows
C) to simulate and model networks
D) to test performance of an application
A) to verify configurations against compliance standards
B) to automate API workflows
C) to simulate and model networks
D) to test performance of an application

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
13
Which CI/CD tool is an automation tool used to build, test, and deploy software?
A) Git
B) Gradle
C) Nagios
D) Jenkins
A) Git
B) Gradle
C) Nagios
D) Jenkins

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
14
Refer to the exhibit. 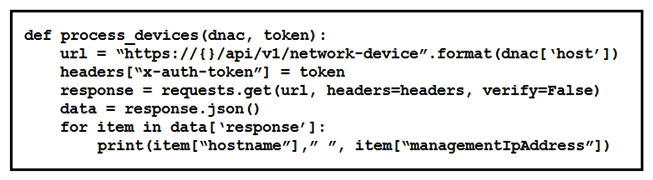 What is the function of the Python script?
What is the function of the Python script?
A) Loop through the returned list of network devices and, for each device, print the device name and management IP address.
B) Count and print the total number of available devices.
C) For each device that is returned, display the device type and associated management IP address.
D) Iterate over a list of network devices and write all device names and management IP addresses to an output file.
 What is the function of the Python script?
What is the function of the Python script?A) Loop through the returned list of network devices and, for each device, print the device name and management IP address.
B) Count and print the total number of available devices.
C) For each device that is returned, display the device type and associated management IP address.
D) Iterate over a list of network devices and write all device names and management IP addresses to an output file.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
15
Refer to the exhibit. 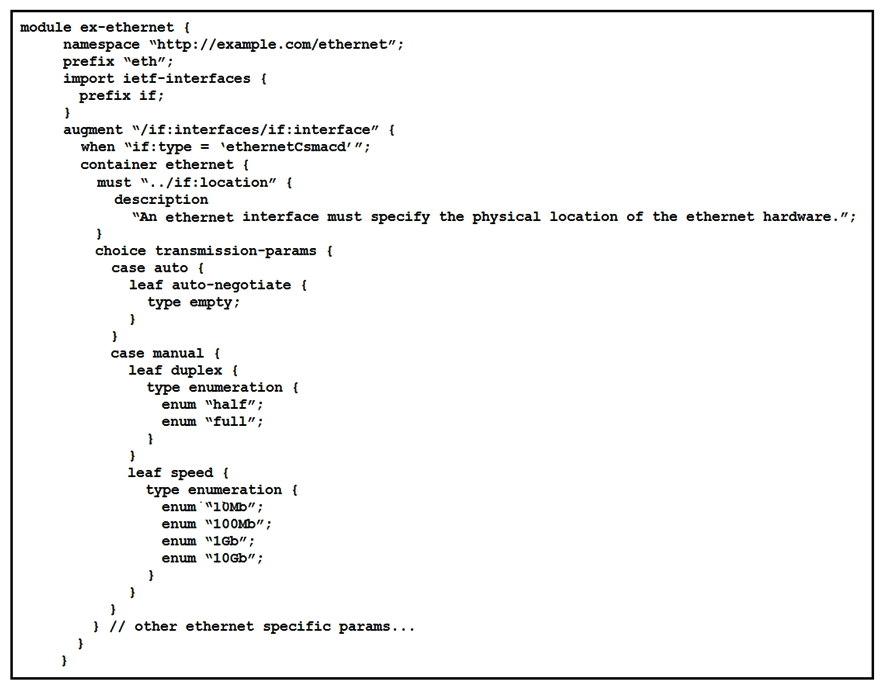 What is represented in this YANG module?
What is represented in this YANG module?
A) interface management
B) BGP
C) OpenFlow
D) topology
 What is represented in this YANG module?
What is represented in this YANG module?A) interface management
B) BGP
C) OpenFlow
D) topology

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
16
Which product provides network controller-level management features?
A) Cisco ISE
B) Cisco DNA Center
C) Cisco UCS Manager
D) Cisco NX-OS
A) Cisco ISE
B) Cisco DNA Center
C) Cisco UCS Manager
D) Cisco NX-OS

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
17
Which two statements are true about Cisco UCS Manager, Cisco UCS Director, or Cisco Intersight APIs? (Choose two.)
A) UCS Manager uses JSON to encode API interactions and utilizes Base64-encoded credentials in the HTTP header for authentication.
B) UCS Director API interactions can be XML- or JSON-encoded and require an API key in the HTTP header for authentication.
C) Cisco Intersight uses XML to encode API interactions and requires an API key pair for authentication.
D) UCS Manager API interactions are XML-encoded and require a cookie in the method for authentication.
E) Cisco Intersight API interactions can be encoded in XML or JSON and require an API key in the HTTP header for authentication.
A) UCS Manager uses JSON to encode API interactions and utilizes Base64-encoded credentials in the HTTP header for authentication.
B) UCS Director API interactions can be XML- or JSON-encoded and require an API key in the HTTP header for authentication.
C) Cisco Intersight uses XML to encode API interactions and requires an API key pair for authentication.
D) UCS Manager API interactions are XML-encoded and require a cookie in the method for authentication.
E) Cisco Intersight API interactions can be encoded in XML or JSON and require an API key in the HTTP header for authentication.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
18
What is the purpose of a MAC address?
A) to uniquely identify a switch in a LAN
B) to uniquely identify a router in a LAN
C) to uniquely identify a network interface in a LAN
D) to uniquely identify a device on the Internet
A) to uniquely identify a switch in a LAN
B) to uniquely identify a router in a LAN
C) to uniquely identify a network interface in a LAN
D) to uniquely identify a device on the Internet

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
19
A developer is reviewing a code that was written by a colleague. It runs fine, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code?
A) Refactor the code by removing any unnecessary tests.
B) Reverse engineer and rewrite the code logic.
C) Using functions, rewrite any pieces of code that are repeated.
D) Modify the code to use loops.
A) Refactor the code by removing any unnecessary tests.
B) Reverse engineer and rewrite the code logic.
C) Using functions, rewrite any pieces of code that are repeated.
D) Modify the code to use loops.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
20
Refer to the exhibit. 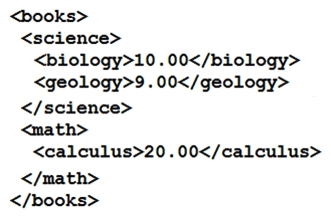 Which JSON is equivalent to the XML-encoded data?
Which JSON is equivalent to the XML-encoded data?
A)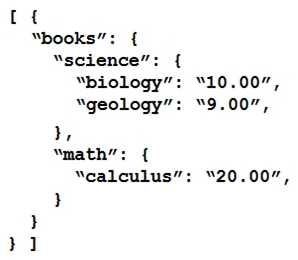
B)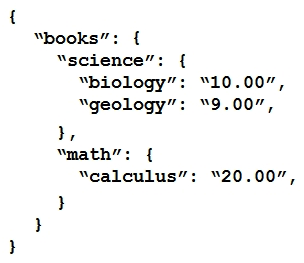
C)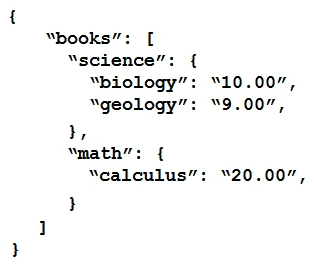
D)
 Which JSON is equivalent to the XML-encoded data?
Which JSON is equivalent to the XML-encoded data?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
21
Which principle is a value from the manifesto for Agile software development?
A) processes and tools over teams and interactions
B) detailed documentation over working software
C) adhering to a plan over responding to requirements
D) customer collaboration over contract negotiation
A) processes and tools over teams and interactions
B) detailed documentation over working software
C) adhering to a plan over responding to requirements
D) customer collaboration over contract negotiation

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
22
An application calls a REST API and expects a result set of more than 550 records, but each time the call is made, only 25 are returned. Which feature limits the amount of data that is returned by the API?
A) pagination
B) payload limit
C) service timeouts
D) rate limiting
A) pagination
B) payload limit
C) service timeouts
D) rate limiting

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
23
Refer to the exhibit. 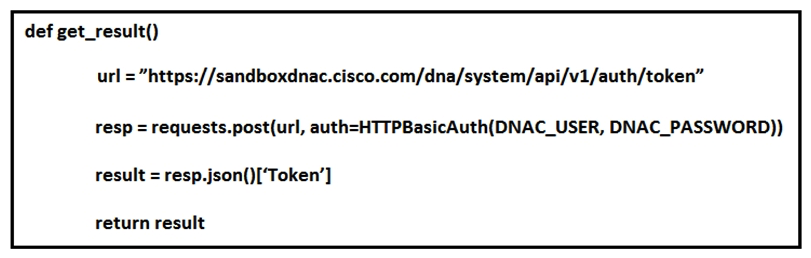 What does the Python function do?
What does the Python function do?
A) It returns HTTP Basic Authentication.
B) It returns DNAC user and password.
C) It reads a token from a local JSON file and posts the token to the DNAC URL.
D) It returns an authorization token.
 What does the Python function do?
What does the Python function do?A) It returns HTTP Basic Authentication.
B) It returns DNAC user and password.
C) It reads a token from a local JSON file and posts the token to the DNAC URL.
D) It returns an authorization token.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
24
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
A) 400
B) 403
C) 405
D) 429
A) 400
B) 403
C) 405
D) 429

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
25
Which statement about authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software is true?
A) No authentication is required.
B) OAuth must be used.
C) A token must be retrieved and the associated string must be embedded in the X-Auth-Token header.
D) Basic authentication must be used.
A) No authentication is required.
B) OAuth must be used.
C) A token must be retrieved and the associated string must be embedded in the X-Auth-Token header.
D) Basic authentication must be used.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
26
Which two concepts describe test-driven development? (Choose two.)
A) User acceptance testers develop the test requirements.
B) It enables code refactoring.
C) Tests are created when code is ready for release.
D) Implementation is driven by incremental testing of release candidates.
E) Write a test before writing code.
A) User acceptance testers develop the test requirements.
B) It enables code refactoring.
C) Tests are created when code is ready for release.
D) Implementation is driven by incremental testing of release candidates.
E) Write a test before writing code.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
27
In Python, which expression checks whether the script returns a success status code when the Requests library is used?
A) response.status_code == requests.codes.ok
B) response.code == requests.codes.ok
C) response.status_code == requests.ok
D) response.status_code != requests.codes.ok
A) response.status_code == requests.codes.ok
B) response.code == requests.codes.ok
C) response.status_code == requests.ok
D) response.status_code != requests.codes.ok

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
28
Package updates from a local server fail to download. However, the same updates work when a much slower external repository is used. Why are local updates failing?
A) The server is running out of disk space.
B) The Internet connection is too slow.
C) The Internet is down at the moment, which causes the local server to not be able to respond.
D) The update utility is trying to use a proxy to access the internal resource.
A) The server is running out of disk space.
B) The Internet connection is too slow.
C) The Internet is down at the moment, which causes the local server to not be able to respond.
D) The update utility is trying to use a proxy to access the internal resource.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
29
Which line is an example of the start of a chunk from a unified diff?
A) @@ -20191007T1200 +88,90 @@
B) @@ -88,10 +88,6 @@
C) @@ -90,88 +20191008T1349 @@
D) @@ -20191007T1200 +20191008T1349 @@
A) @@ -20191007T1200 +88,90 @@
B) @@ -88,10 +88,6 @@
C) @@ -90,88 +20191008T1349 @@
D) @@ -20191007T1200 +20191008T1349 @@

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
30
What is an advantage of using network programmability?
A) Manual configuration is faster.
B) No cloud abstraction occurs.
C) It removes CLI access for devices.
D) It provides for more scalable and replicable network provisioning.
A) Manual configuration is faster.
B) No cloud abstraction occurs.
C) It removes CLI access for devices.
D) It provides for more scalable and replicable network provisioning.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
31
What are two roles of an artifact repository in a CI/CD pipeline? (Choose two.)
A) stores files needed and generated during the build process
B) provides traceability, search, and management of binary files
C) is required for CI/CD pipelines executed on a public cloud infrastructure
D) allows for comparing and merging changes in the source code
E) is required for managing open source software
A) stores files needed and generated during the build process
B) provides traceability, search, and management of binary files
C) is required for CI/CD pipelines executed on a public cloud infrastructure
D) allows for comparing and merging changes in the source code
E) is required for managing open source software

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
32
Which two NETCONF operations cover the RESTCONF GET operation? (Choose two.)
A)
B)
C)
D)
E)
A)
B)
C)
D)
E)

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
33
Which two descriptions can be given to an application that is interacting with a webhook? (Choose two.)
A) receiver
B) transaction monitor
C) codec
D) processor
E) listener
A) receiver
B) transaction monitor
C) codec
D) processor
E) listener

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
34
What is the Git command to delete a local branch named "experiment" without a warning?
A) git branch -rm experiment
B) git branch -n experiment
C) git branch -f experiment
D) git branch -D experiment
A) git branch -rm experiment
B) git branch -n experiment
C) git branch -f experiment
D) git branch -D experiment

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
35
Refer to the exhibit. 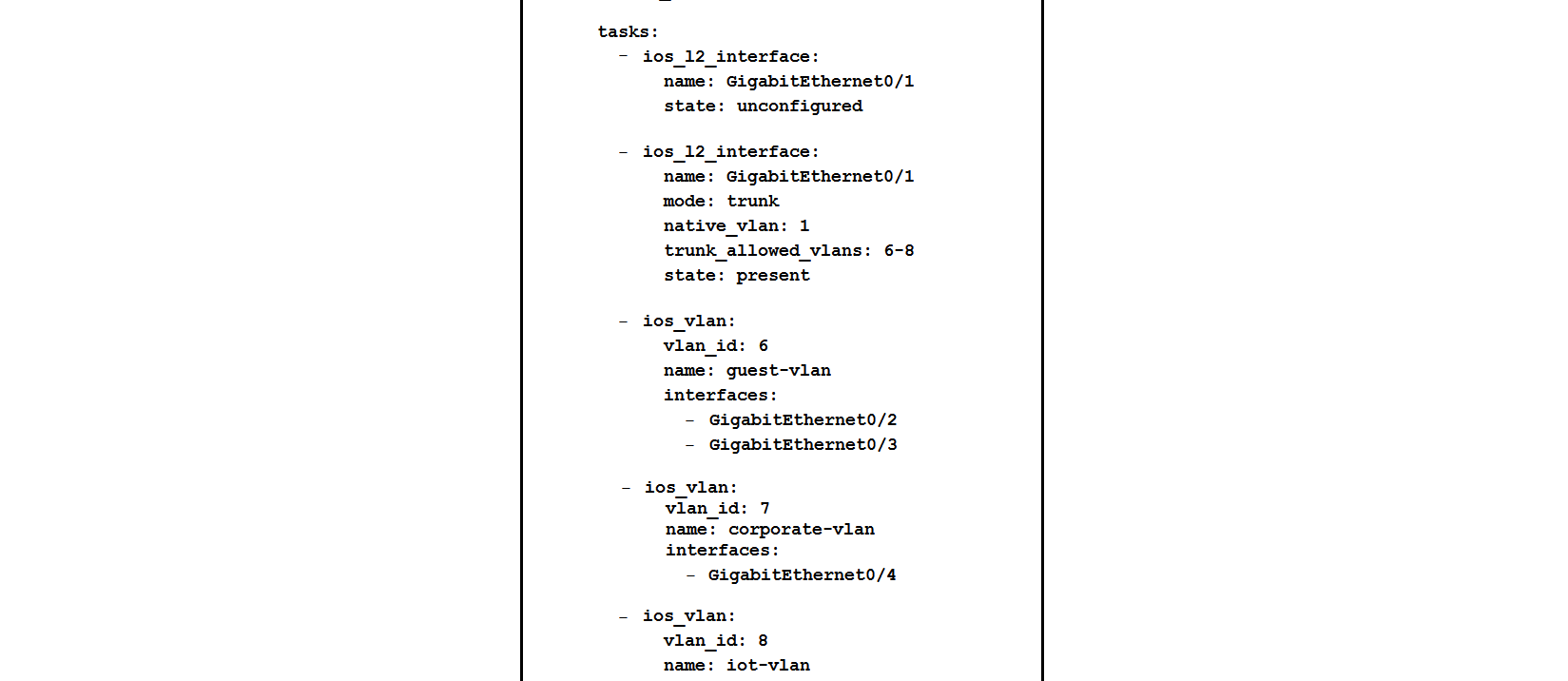 Which two statements describe the configuration of the switch after the Ansible script is run? (Choose two.)
Which two statements describe the configuration of the switch after the Ansible script is run? (Choose two.)
A) Traffic from ports 0/2 to 0/5 can flow on port 0/1 due to the trunk.
B) GigabitEthernet0/1 is left unconfigured.
C) GigabitEthernet0/2 and GigabitEthernet0/3 are access ports for VLAN 6.
D) Traffic can flow between ports 0/2 to 0/5 due to the trunk on port 0/1.
E) Traffic on ports 0/2 and 0/3 is connected to port 0/6.
 Which two statements describe the configuration of the switch after the Ansible script is run? (Choose two.)
Which two statements describe the configuration of the switch after the Ansible script is run? (Choose two.)A) Traffic from ports 0/2 to 0/5 can flow on port 0/1 due to the trunk.
B) GigabitEthernet0/1 is left unconfigured.
C) GigabitEthernet0/2 and GigabitEthernet0/3 are access ports for VLAN 6.
D) Traffic can flow between ports 0/2 to 0/5 due to the trunk on port 0/1.
E) Traffic on ports 0/2 and 0/3 is connected to port 0/6.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
36
Refer to the exhibit. 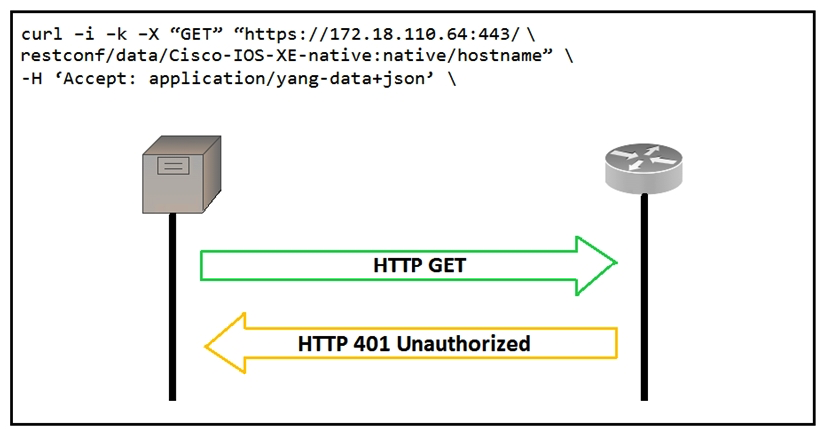 An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue?
An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue?
A) Remove the -H 'Accept: application/yang-data+json' HTTP header because it is not required. Remove the -H 'Accept: application/yang-data+json' HTTP header because it is not required.
B) Add - 'u cisco:cisco' in the end of the cURL command Add - 'u cisco:cisco' in the end of the cURL command
C) Change the request method from -X "GET" to -X "POST" Change the request method from -X "GET" to -X "POST"
D) Add Content-Type HTTP header with ' application/yang-data+json ' using -H 'Content-Type: application/yang-data+json' Add Content-Type HTTP header with ' application/yang-data+json ' using -H 'Content-Type: application/yang-data+json'
 An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue?
An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue?A) Remove the -H 'Accept: application/yang-data+json' HTTP header because it is not required. Remove the -H 'Accept: application/yang-data+json' HTTP header because it is not required.
B) Add - 'u cisco:cisco' in the end of the cURL command Add - 'u cisco:cisco' in the end of the cURL command
C) Change the request method from -X "GET" to -X "POST" Change the request method from -X "GET" to -X "POST"
D) Add Content-Type HTTP header with ' application/yang-data+json ' using -H 'Content-Type: application/yang-data+json' Add Content-Type HTTP header with ' application/yang-data+json ' using -H 'Content-Type: application/yang-data+json'

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
37
Refer to the exhibit. 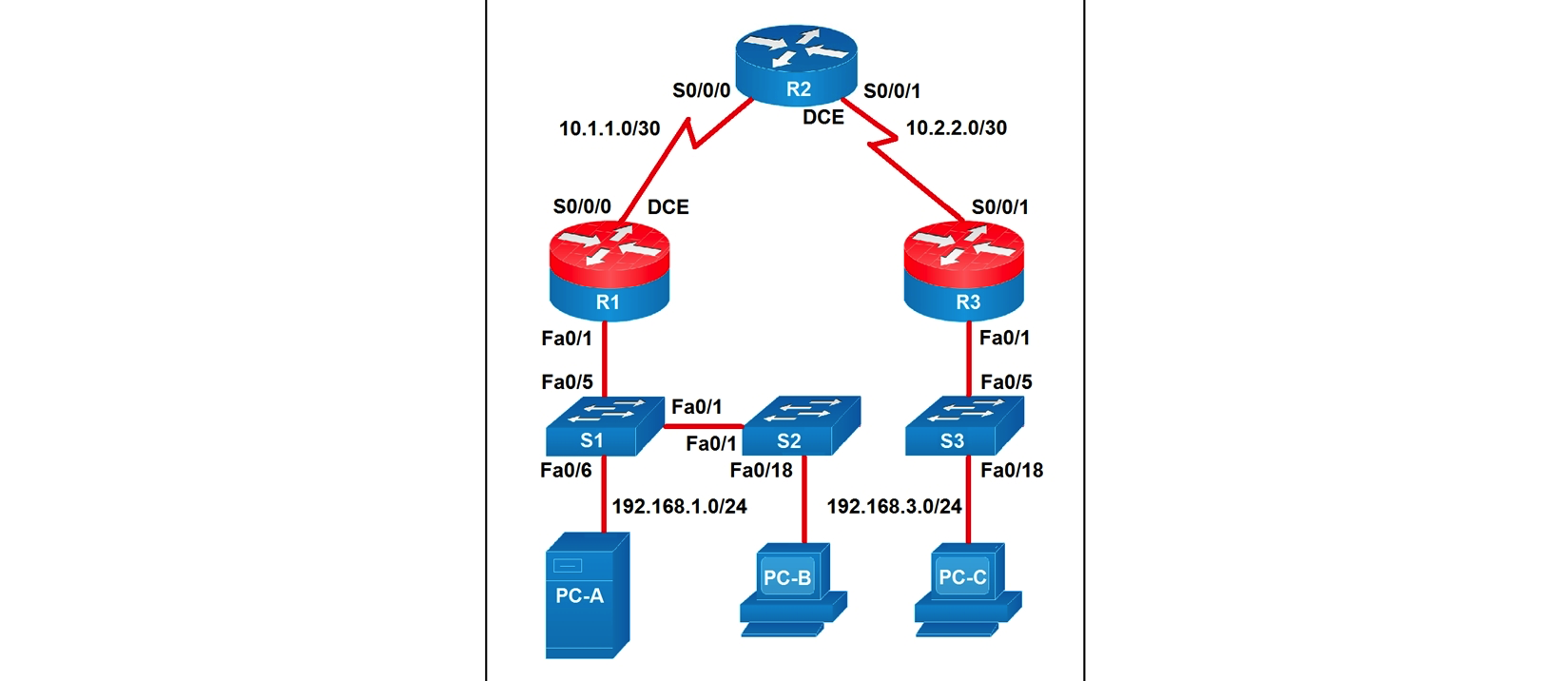 Which two statements about the network diagram are true? (Choose two.)
Which two statements about the network diagram are true? (Choose two.)
A) The subnet address of PC-B has 18 bits dedicated to the network portion.
B) One of the routers has two connected serial interfaces.
C) R1 and R3 are in the same subnet.
D) PC-A and PC-B are in the same subnet.
E) The subnet of PC-C can contain 256 hosts.
 Which two statements about the network diagram are true? (Choose two.)
Which two statements about the network diagram are true? (Choose two.)A) The subnet address of PC-B has 18 bits dedicated to the network portion.
B) One of the routers has two connected serial interfaces.
C) R1 and R3 are in the same subnet.
D) PC-A and PC-B are in the same subnet.
E) The subnet of PC-C can contain 256 hosts.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
38
Refer to the exhibits. 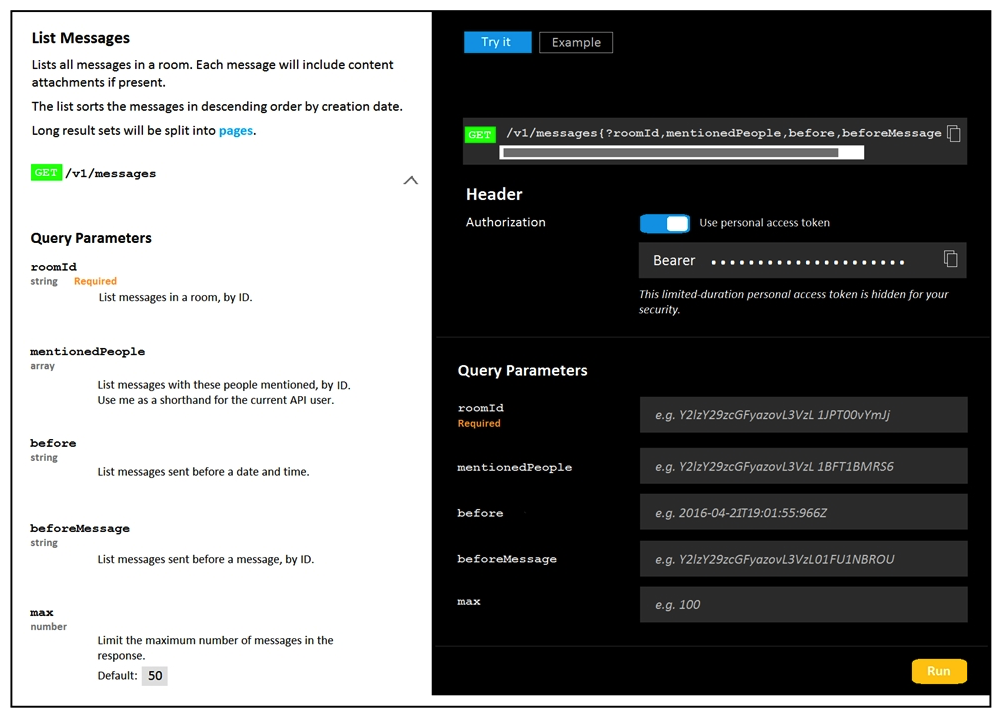
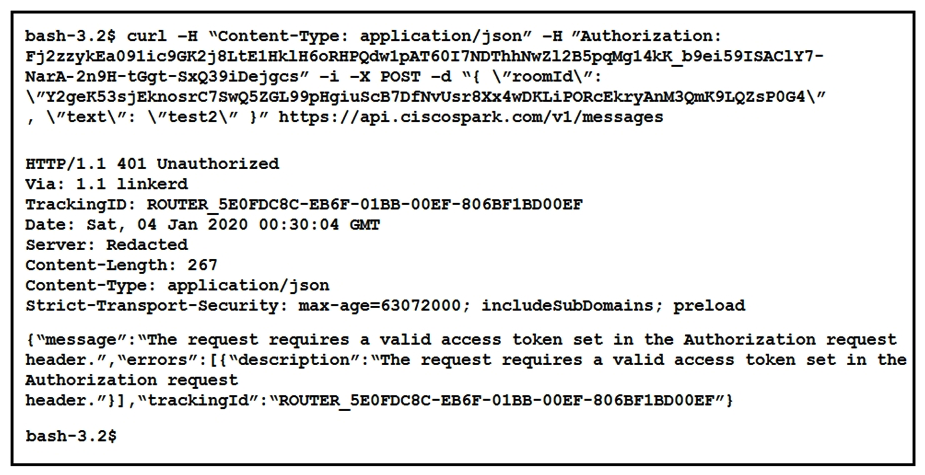 A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem?
A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem?
A) The authorization header is missing or incomplete.
B) The request body is missing or incomplete.
C) The API token specified is expired.
D) The user is not allowed to post messages from their account.

 A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem?
A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem?A) The authorization header is missing or incomplete.
B) The request body is missing or incomplete.
C) The API token specified is expired.
D) The user is not allowed to post messages from their account.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
39
Which two statements about JSON and XML are true? (Choose two.)
A) The syntax of JSON contains tags, elements, and attributes.
B) XML objects are collections of key-value pairs.
C) JSON objects are collections of key-value pairs.
D) JSON arrays are an unordered set of key-value pairs.
E) The syntax of XML contains tags, elements, and attributes.
A) The syntax of JSON contains tags, elements, and attributes.
B) XML objects are collections of key-value pairs.
C) JSON objects are collections of key-value pairs.
D) JSON arrays are an unordered set of key-value pairs.
E) The syntax of XML contains tags, elements, and attributes.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
40
Before which process is code review performed when version control is used?
A) checkout of code
B) merge of code
C) committing code
D) branching code
A) checkout of code
B) merge of code
C) committing code
D) branching code

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
41
On which network plane is routing protocol traffic handled?
A) management plane
B) data plane
C) authentication plane
D) control plane
A) management plane
B) data plane
C) authentication plane
D) control plane

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
42
Refer to the exhibits. 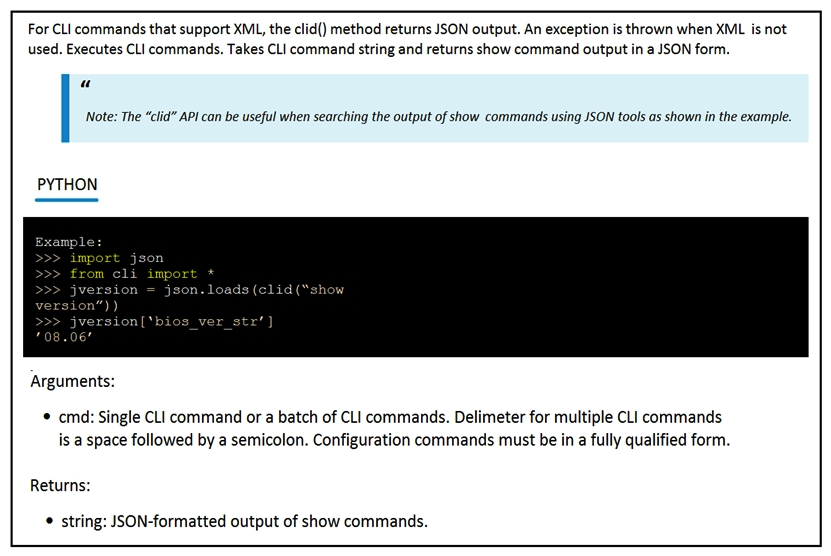
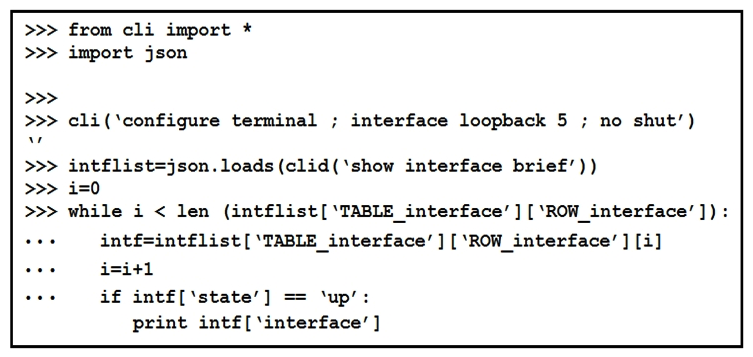 The Python interpreter and the Cisco Python SDK are available by default in the Cisco NX-OS Software. The SDK documentation shows how the clid() API can be used when working with JSON and XML. What are two effects of running the script? (Choose two.)
The Python interpreter and the Cisco Python SDK are available by default in the Cisco NX-OS Software. The SDK documentation shows how the clid() API can be used when working with JSON and XML. What are two effects of running the script? (Choose two.)
A) configure interface loopback 5
B) show details for the TABLE interface
C) issue shutdown on interface loopback 5
D) show only the interfaces in the up status
E) show only the interfaces in admin shut status

 The Python interpreter and the Cisco Python SDK are available by default in the Cisco NX-OS Software. The SDK documentation shows how the clid() API can be used when working with JSON and XML. What are two effects of running the script? (Choose two.)
The Python interpreter and the Cisco Python SDK are available by default in the Cisco NX-OS Software. The SDK documentation shows how the clid() API can be used when working with JSON and XML. What are two effects of running the script? (Choose two.)A) configure interface loopback 5
B) show details for the TABLE interface
C) issue shutdown on interface loopback 5
D) show only the interfaces in the up status
E) show only the interfaces in admin shut status

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
43
What are two security benefits of a Docker-based application? (Choose two.)
A) natively secures access to secrets that are used by the running application
B) guarantees container images are secured and free of vulnerabilities
C) easier to patch because Docker containers include only dependencies that the application requires
D) prevents information leakage that can occur when unhandled exceptions are returned in HTTP responses
E) allows for separation of applications that traditionally run on the same host
A) natively secures access to secrets that are used by the running application
B) guarantees container images are secured and free of vulnerabilities
C) easier to patch because Docker containers include only dependencies that the application requires
D) prevents information leakage that can occur when unhandled exceptions are returned in HTTP responses
E) allows for separation of applications that traditionally run on the same host

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
44
Refer to the exhibit. 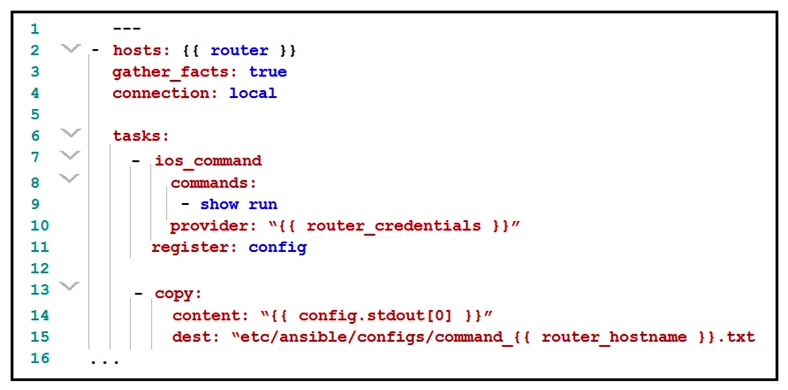 What is the effect of this Ansible playbook on an IOS router?
What is the effect of this Ansible playbook on an IOS router?
A) A new running configuration is pushed to the IOS router.
B) The start-up configuration of the IOS router is copied to a local folder.
C) The current running configuration of the IOS router is backed up.
D) A new start-up configuration is copied to the IOS router.
 What is the effect of this Ansible playbook on an IOS router?
What is the effect of this Ansible playbook on an IOS router?A) A new running configuration is pushed to the IOS router.
B) The start-up configuration of the IOS router is copied to a local folder.
C) The current running configuration of the IOS router is backed up.
D) A new start-up configuration is copied to the IOS router.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
45
What is the outcome of executing this command? git clone ssh:/john@example.com/path/to/my-project.git
A) creates a local copy of a repository called "my-project"
B) initiates a new Git repository called "my-project"
C) creates a copy of a branch called "my-project"
D) creates a new branch called "my-project"
A) creates a local copy of a repository called "my-project"
B) initiates a new Git repository called "my-project"
C) creates a copy of a branch called "my-project"
D) creates a new branch called "my-project"

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
46
What should a CI/CD pipeline aim to achieve?
A) to require minimal manual interaction
B) to allow manual testing before deployment
C) to support new deployments on a fixed monthly schedule
D) to provide a documented process for feedback
A) to require minimal manual interaction
B) to allow manual testing before deployment
C) to support new deployments on a fixed monthly schedule
D) to provide a documented process for feedback

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
47
Which platform has an API that can be used to obtain a list of vulnerable software on user devices?
A) Cisco Umbrella
B) Cisco Firepower
C) Cisco Identity Services Engine
D) Cisco Advanced Malware Protection
A) Cisco Umbrella
B) Cisco Firepower
C) Cisco Identity Services Engine
D) Cisco Advanced Malware Protection

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
48
What is an example of a network interface hardware address?
A) workstation name
B) IP address
C) domain name
D) MAC address
A) workstation name
B) IP address
C) domain name
D) MAC address

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
49
Which two statements describe the traits of an asynchronous API call? (Choose two.)
A) Code execution blocks or waits for the call to an API to return.
B) A callback function typically is used to process the response from an API call.
C) A call to an API does not block the code, but rather it allows application processing to continue.
D) The end user can experience latency or performance lag while waiting for the API call to return.
E) The order in which API calls return can be guaranteed.
A) Code execution blocks or waits for the call to an API to return.
B) A callback function typically is used to process the response from an API call.
C) A call to an API does not block the code, but rather it allows application processing to continue.
D) The end user can experience latency or performance lag while waiting for the API call to return.
E) The order in which API calls return can be guaranteed.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
50
Refer to the exhibit. 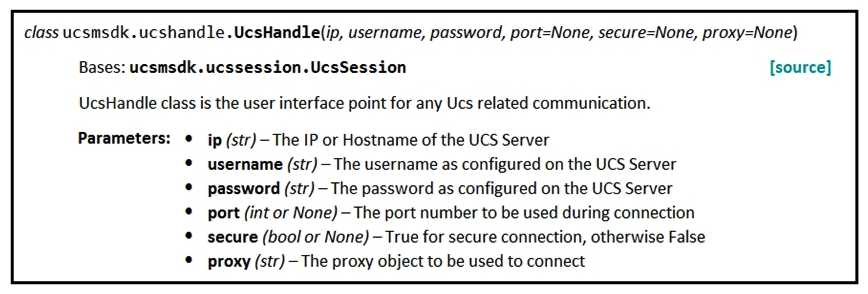 Given the API documentation for the UCS SDK Python class, UcsHandle, which code snippet creates a handle instance?
Given the API documentation for the UCS SDK Python class, UcsHandle, which code snippet creates a handle instance?
A)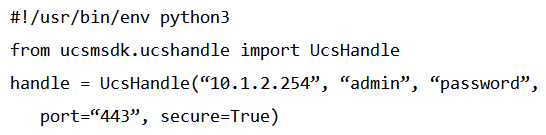
B)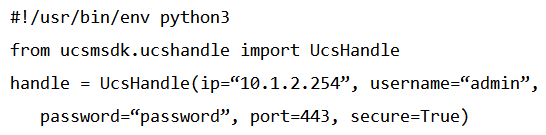
C)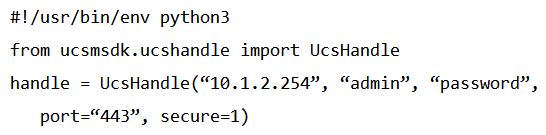
D)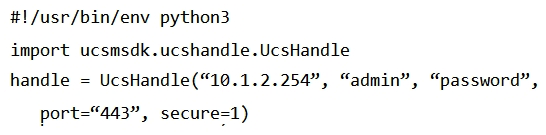
 Given the API documentation for the UCS SDK Python class, UcsHandle, which code snippet creates a handle instance?
Given the API documentation for the UCS SDK Python class, UcsHandle, which code snippet creates a handle instance?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
51
Which mechanism is used to consume a RESTful API design when large amounts of data are returned?
A) data sets
B) scrolling
C) pagination
D) blobs
A) data sets
B) scrolling
C) pagination
D) blobs

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
52
A function my_func() returns True when it executes normally. Which Python snippet tests ?
A)
B)
C)
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
53
Which two encoding formats do YANG interfaces support? (Choose two.)
A) XML
B) JSON
C) XHTML
D) BER
E) plain text
A) XML
B) JSON
C) XHTML
D) BER
E) plain text

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
54
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
A) clients receive responses with a task id for further processing
B) clients subscribe to a webhook for operation results
C) clients poll for the status of the execution of operations
D) clients can access the results immediately
A) clients receive responses with a task id for further processing
B) clients subscribe to a webhook for operation results
C) clients poll for the status of the execution of operations
D) clients can access the results immediately

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
55
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve a configuration statement using RESTCONF on a CSR 1000V?
A) Change the HTTP method to PUT.
B) Check the MIME types in the HTTP headers.
C) Change the transport protocol to HTTPS.
D) Check the authentication credentials.
A) Change the HTTP method to PUT.
B) Check the MIME types in the HTTP headers.
C) Change the transport protocol to HTTPS.
D) Check the authentication credentials.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
56
Which two items are Cisco DevNet resources? (Choose two.)
A) TAC Support
B) Software Research
C) API Documentation
D) Bitbucket
E) Sandbox
A) TAC Support
B) Software Research
C) API Documentation
D) Bitbucket
E) Sandbox

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
57
Refer to the exhibit.  What caused the error in this API request?
What caused the error in this API request?
A) The API resource does not support the POST operation.
B) The submitted JSON payload has a formatting issue.
C) The API resource does not support JSON format payloads.
D) The submitted JSON payload includes a field that is not supported by the API resource.
 What caused the error in this API request?
What caused the error in this API request?A) The API resource does not support the POST operation.
B) The submitted JSON payload has a formatting issue.
C) The API resource does not support JSON format payloads.
D) The submitted JSON payload includes a field that is not supported by the API resource.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
58
Refer to the exhibit. ![<strong>Refer to the exhibit. A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called vegetables. Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])</strong> A) {'color': 'green', 'items': ['kiwi', 'grape']} B) ['kiwi', 'grape'] C) lettuce D) kiwi](https://storage.examlex.com/C1178/11ec5360_da9e_5cac_8515_55cb191da145_C1178_00.jpg) A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called "vegetables". Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])
A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called "vegetables". Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])
A) {'color': 'green', 'items': ['kiwi', 'grape']}
B) ['kiwi', 'grape']
C) lettuce
D) kiwi
![<strong>Refer to the exhibit. A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called vegetables. Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])</strong> A) {'color': 'green', 'items': ['kiwi', 'grape']} B) ['kiwi', 'grape'] C) lettuce D) kiwi](https://storage.examlex.com/C1178/11ec5360_da9e_5cac_8515_55cb191da145_C1178_00.jpg) A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called "vegetables". Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])
A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called "vegetables". Using Python, which output is the result of this command? print(filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])A) {'color': 'green', 'items': ['kiwi', 'grape']}
B) ['kiwi', 'grape']
C) lettuce
D) kiwi

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
59
Which type of HTTP method is used by the Meraki and Webex Teams APIs to send webhook notifications?
A) HTTP POST
B) HTTP GET
C) HTTP HEAD
D) HTTP PUT
A) HTTP POST
B) HTTP GET
C) HTTP HEAD
D) HTTP PUT

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
60
Which REST architectural constraint indicates that no client context should be stored on the server between requests?
A) cacheable
B) stateless
C) uniform interface
D) client-server
A) cacheable
B) stateless
C) uniform interface
D) client-server

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
61
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports "communication administratively prohibited". What is the cause of this webserver access issue?
A) An access list along the path is blocking the traffic.
B) Users must authenticate on the webserver to access it.
C) A router along the path is overloaded and thus dropping traffic.
D) The traffic is not allowed to be translated with NAT and dropped.
A) An access list along the path is blocking the traffic.
B) Users must authenticate on the webserver to access it.
C) A router along the path is overloaded and thus dropping traffic.
D) The traffic is not allowed to be translated with NAT and dropped.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
62
While developing a real-time VoIP application on a Cisco Webex Teams platform, users report that their voice gets chopped or parts of the conversation drops out. Which network constraint is impacting the application?
A) jitter
B) capacity
C) delay
D) latency
A) jitter
B) capacity
C) delay
D) latency

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
63
Which service provides a directory lookup for IP addresses and host names?
A) DNS
B) NAT
C) SNMP
D) DHCP
A) DNS
B) NAT
C) SNMP
D) DHCP

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
64
A small company has 5 servers and 50 clients. What are two reasons an engineer should split this network into separate client and server subnets? (Choose two.)
A) Subnets will split domains to limit failures.
B) A router will limit the traffic types between the clients and servers.
C) Subnets provide more IP address space for clients and servers.
D) A router will bridge the traffic between clients and servers.
E) Internet access to the servers will be denied on the router.
A) Subnets will split domains to limit failures.
B) A router will limit the traffic types between the clients and servers.
C) Subnets provide more IP address space for clients and servers.
D) A router will bridge the traffic between clients and servers.
E) Internet access to the servers will be denied on the router.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
65
What is a benefit of organizing code into modules?
A) enables the code to be broken down into layers
B) improves collaboration of the development team
C) makes it easier to deal with large and complex systems
D) enables the inclusion of more programming languages in the code
A) enables the code to be broken down into layers
B) improves collaboration of the development team
C) makes it easier to deal with large and complex systems
D) enables the inclusion of more programming languages in the code

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
66
A local Docker alpine image has been created with an image ID of a391665405fe and tagged as "latest". Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host?
A) docker build -p 8080:80 alpine:latest
B) docker exec -p 8080:80 alpine:latest
C) docker start -p 8080:80 alpine:latest
D) docker run -p 8080:80 alpine:latest
A) docker build -p 8080:80 alpine:latest
B) docker exec -p 8080:80 alpine:latest
C) docker start -p 8080:80 alpine:latest
D) docker run -p 8080:80 alpine:latest

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
67
How does a developer create and switch to a new branch called "my-bug-fix" to develop a product fix?
A) git checkout -b my-bug-fix
B) git branch -b my-bug-fix
C) git branch my-bug-fix
D) git checkout my-bug-fix
A) git checkout -b my-bug-fix
B) git branch -b my-bug-fix
C) git branch my-bug-fix
D) git checkout my-bug-fix

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
68
A 401 HTTP response code is returned when calling a REST API. What is the error state identified by this response code?
A) The server cannot process the request as it has detected an issue in the request syntax or body.
B) The request has not been accepted because it requires authentication.
C) The sever accepted the request but the client is not authorized for this content.
D) The server cannot find the requested resource because the path specified is incorrect.
A) The server cannot process the request as it has detected an issue in the request syntax or body.
B) The request has not been accepted because it requires authentication.
C) The sever accepted the request but the client is not authorized for this content.
D) The server cannot find the requested resource because the path specified is incorrect.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
69
Refer to the exhibit. 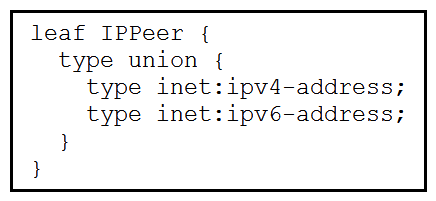 What is the value of the node defined by this YANG structure?
What is the value of the node defined by this YANG structure?
A)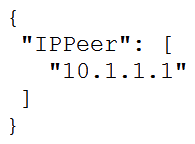
B)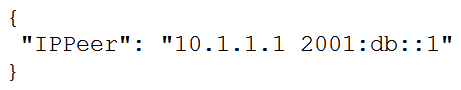
C)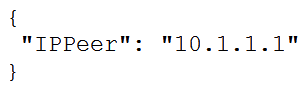
D)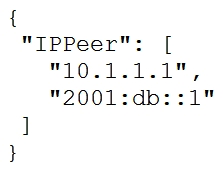
 What is the value of the node defined by this YANG structure?
What is the value of the node defined by this YANG structure?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
70
What is the function of an IP address in networking?
A) represents a network connection on specific devices
B) specifies the type of traffic that is allowed to roam on a network
C) specifies resource's location and the mechanism to retrieve it
D) represents the unique ID that is assigned to one host on a network
A) represents a network connection on specific devices
B) specifies the type of traffic that is allowed to roam on a network
C) specifies resource's location and the mechanism to retrieve it
D) represents the unique ID that is assigned to one host on a network

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
71
What is used in Layer 2 switches to direct packet transmission to the intended recipient?
A) MAC address
B) IPv6 address
C) spanning tree
D) IPv4 address
A) MAC address
B) IPv6 address
C) spanning tree
D) IPv4 address

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
72
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
A) multi-platform vendor abstraction
B) compiles to executables that run on network devices
C) designed to reflect networking concepts
D) directly maps to JavaScript
E) command line driven interface
A) multi-platform vendor abstraction
B) compiles to executables that run on network devices
C) designed to reflect networking concepts
D) directly maps to JavaScript
E) command line driven interface

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
73
What is the first development task in test-driven development?
A) Write code that implements a desired function.
B) Write a failing test case for a desired function.
C) Reverse engineer the code for a desired function.
D) Write a passing test case for existing code.
A) Write code that implements a desired function.
B) Write a failing test case for a desired function.
C) Reverse engineer the code for a desired function.
D) Write a passing test case for existing code.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
74
What is a benefit of using edge computing in an IoT implementation?
A) high speed in data processing
B) low network design complexity
C) low cost in network design
D) high availability for network components
A) high speed in data processing
B) low network design complexity
C) low cost in network design
D) high availability for network components

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
75
Where is an IP packet routed if the packet does not match any routes in the routing table?
A) firewall
B) load balancer
C) central switch
D) default gateway
A) firewall
B) load balancer
C) central switch
D) default gateway

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
76
What are two key capabilities of Cisco Finesse? (Choose two.)
A) Agents access Finesse from a browser without needing to install or configure anything on the client machine.
B) An OpenDNS utility is preconfigured and ready to use on Finesse.
C) Gadget containers provide a seamless experience in a single user interface.
D) Finesse automatically collects telemetry data.
E) Finesse includes an RPC API that enables the development of custom gadgets.
A) Agents access Finesse from a browser without needing to install or configure anything on the client machine.
B) An OpenDNS utility is preconfigured and ready to use on Finesse.
C) Gadget containers provide a seamless experience in a single user interface.
D) Finesse automatically collects telemetry data.
E) Finesse includes an RPC API that enables the development of custom gadgets.

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
77
After a project is migrated to a new codebase, the "old_project" directory must be deleted. This directory has multiple read-only flies, and it must be deleted recursively without prompting for confirmation. Which Bash command must be used?
A) rmdir -p old_project
B) rm -rf old_project
C) rm -r old_project
D) rmdir old_project
A) rmdir -p old_project
B) rm -rf old_project
C) rm -r old_project
D) rmdir old_project

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
78
What operation is performed with YANG model-driven programmability in NX-OS?
A) configure a device with native and OpenConfig-based models
B) bootstrap a device that has a factory-default configuration
C) send CLI commands to a device and retrieve output in JSON format
D) run Linux commands natively on the device
A) configure a device with native and OpenConfig-based models
B) bootstrap a device that has a factory-default configuration
C) send CLI commands to a device and retrieve output in JSON format
D) run Linux commands natively on the device

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
79
Refer to the exhibit. 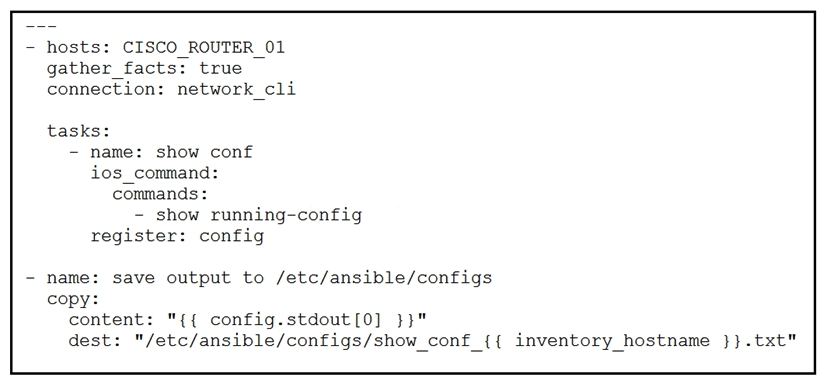 What is the result of executing this Ansible playbook?
What is the result of executing this Ansible playbook?
A) The playbook copies a new start-up configuration to CISCO_ROUTER_01
B) The playbook copies a new running configuration to CISCO_ROUTER_01
C) The playbook backs up the running configuration of CISCO_ROUTER_01
D) The playbook backs up the start-up configuration of CISCO_ROUTER_01
 What is the result of executing this Ansible playbook?
What is the result of executing this Ansible playbook?A) The playbook copies a new start-up configuration to CISCO_ROUTER_01
B) The playbook copies a new running configuration to CISCO_ROUTER_01
C) The playbook backs up the running configuration of CISCO_ROUTER_01
D) The playbook backs up the start-up configuration of CISCO_ROUTER_01

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck
80
Refer to the exhibit. 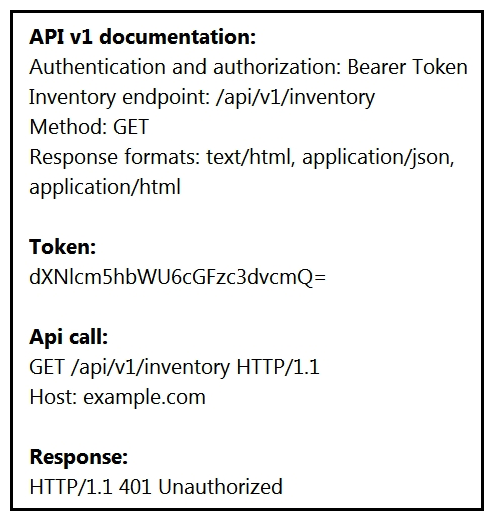 An API call is constructed to retrieve the inventory in XML formal by using the API. The response to the call is 401 Unauthorized. Which two headers must he added to the API call? (Choose two.)
An API call is constructed to retrieve the inventory in XML formal by using the API. The response to the call is 401 Unauthorized. Which two headers must he added to the API call? (Choose two.)
A) Bearer-Token: dXNlcm5hbWU6cGFzc3dvemQ=
B) Content-Type: application/xml
C) Authentication: Bearer dXNlcm5hbWU6cGFzc3dvemQ=
D) Accept: application/xml
E) Authorization: Bearer dXNlcm5hbWU6cGFzc3dvemQ=
 An API call is constructed to retrieve the inventory in XML formal by using the API. The response to the call is 401 Unauthorized. Which two headers must he added to the API call? (Choose two.)
An API call is constructed to retrieve the inventory in XML formal by using the API. The response to the call is 401 Unauthorized. Which two headers must he added to the API call? (Choose two.)A) Bearer-Token: dXNlcm5hbWU6cGFzc3dvemQ=
B) Content-Type: application/xml
C) Authentication: Bearer dXNlcm5hbWU6cGFzc3dvemQ=
D) Accept: application/xml
E) Authorization: Bearer dXNlcm5hbWU6cGFzc3dvemQ=

Unlock Deck
Unlock for access to all 134 flashcards in this deck.
Unlock Deck
k this deck


