Deck 9: Cybersecurity: Network and Host Protection
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/19
Play
Full screen (f)
Deck 9: Cybersecurity: Network and Host Protection
1
I am trying to reach a web server, www.chicago.edu. The response message from the DNS server tells my computer the _____.
A) domain name of the www.chicago.edu server
B) IP address of the www.chicago.edu server
C) IP address of the DNS root server
D) IP address of the DNS authority server
E) MAC address of the www.chicago.edu server
A) domain name of the www.chicago.edu server
B) IP address of the www.chicago.edu server
C) IP address of the DNS root server
D) IP address of the DNS authority server
E) MAC address of the www.chicago.edu server
B
2
Which command is issued to obtain the IP address of a domain name, "www.sdsu.edu", as in the figure?

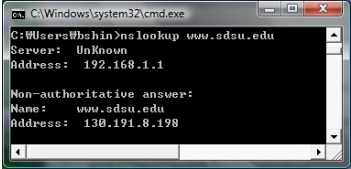
A) C:>ipconfig /flushdns www.sdsu.edu
B) C:>ipconfig /displaydns
C) C:>nslookup www.sdsu.edu
D) C:>netstat -n
E) C:>ipconfig /all


A) C:>ipconfig /flushdns www.sdsu.edu
B) C:>ipconfig /displaydns
C) C:>nslookup www.sdsu.edu
D) C:>netstat -n
E) C:>ipconfig /all
C
3
The uniform resource locator (URL) field includes information on:
A) protocol + DNS authority server
B) protocol + domain name
C) domain name + DNS authority server
D) domain name + HTTP server
E) domain name + ISP router address
A) protocol + DNS authority server
B) protocol + domain name
C) domain name + DNS authority server
D) domain name + HTTP server
E) domain name + ISP router address
B
4
The authoritative server concept applies to the _________ protocol.
A) DHCP
B) HTTP
C) SMTP
D) DNS
E) FTP
A) DHCP
B) HTTP
C) SMTP
D) DNS
E) FTP

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
5
The 'root' and 'authority' server concepts are relevant to the _________ protocol.
A) DHCP
B) HTTP
C) SMTP
D) DNS
E) FTP
A) DHCP
B) HTTP
C) SMTP
D) DNS
E) FTP

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
6
The statement, "127.0.0.1 localhost", should be in included in the _________ file of a computer.
A) DHCP
B) HTTP
C) SMTP
D) DNS
E) FTP
A) DHCP
B) HTTP
C) SMTP
D) DNS
E) FTP

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following filtering rules is considered a 'complete' rule on a firewall?
A) If source IP = 172.16.x.x to 172.31.x.x or 192.168.x.x.
B) If TCP destination port = 21.
C) If HTML message contains 'sex' or 'entertainment'.
D) If destination IP = 161.154.23.59 and TCP port = 25.
E) None of the above
A) If source IP = 172.16.x.x to 172.31.x.x or 192.168.x.x.
B) If TCP destination port = 21.
C) If HTML message contains 'sex' or 'entertainment'.
D) If destination IP = 161.154.23.59 and TCP port = 25.
E) None of the above

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
8
Which of the following filtering rules of the firewall is considered a stateful rule ?
A) If source IP = 172.16.x.x to 172.31.x.x or 192.168.x.x, then drop the packet.
B) If TCP destination port = 21, then drop the packet.
C) If the URL = www.darkspace.xxx, then drop the packet.
D) If destination IP = 161.154.23.59 and TCP port = 80, then pass the packet.
E) If the source and destination sockets of an arriving packet match those of a session established, then pass the packet.
A) If source IP = 172.16.x.x to 172.31.x.x or 192.168.x.x, then drop the packet.
B) If TCP destination port = 21, then drop the packet.
C) If the URL = www.darkspace.xxx, then drop the packet.
D) If destination IP = 161.154.23.59 and TCP port = 80, then pass the packet.
E) If the source and destination sockets of an arriving packet match those of a session established, then pass the packet.

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
9
Which filtering rule of a firewall is more likely a 'stateful' rule than the others?
A) If source IP = 172.16.x.x to 172.31.x.x or 192.168.x.x, then drop the packet.
B) If TCP destination port = 21, then allow the packet.
C) If HTML message contains 'sex' or 'entertainment', then drop the packet.
D) If destination IP = 161.154.23.59 and TCP port = 25, then allow the packet.
E) If source=192.168.1.34, dest.=163.43.24.11, source port=1075, dest. port=21, then allow the packet.
A) If source IP = 172.16.x.x to 172.31.x.x or 192.168.x.x, then drop the packet.
B) If TCP destination port = 21, then allow the packet.
C) If HTML message contains 'sex' or 'entertainment', then drop the packet.
D) If destination IP = 161.154.23.59 and TCP port = 25, then allow the packet.
E) If source=192.168.1.34, dest.=163.43.24.11, source port=1075, dest. port=21, then allow the packet.

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
10
Choose a CORRECT pairing between a security layer and its corresponding technical solution (remember to choose the most accurate one).
A) Application security -- Hardening intermediary devices
B) Data security -- Host-based firewall
C) Perimeter security -- DMZ (Demilitarized zone)
D) Host security -- Proxy server
E) Internal network security -- Server hardening
A) Application security -- Hardening intermediary devices
B) Data security -- Host-based firewall
C) Perimeter security -- DMZ (Demilitarized zone)
D) Host security -- Proxy server
E) Internal network security -- Server hardening

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
11
The following represent technical measures relevant to the host security layer EXCEPT:
A) Host-based intrusion detection
B) Proxy servers
C) Anti-virus protection
D) OS patch/security update management
E) Server hardening (e.g., authentication, and auditing)
A) Host-based intrusion detection
B) Proxy servers
C) Anti-virus protection
D) OS patch/security update management
E) Server hardening (e.g., authentication, and auditing)

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
12
Which CORRECTLY pairs a security layer and a technology solution?
A) data security - operating system patch management
B) application security - hardening intermediary devices
C) host security - subnetwork segmentations
D) internal network security - corporate-wide data encryption
E) perimeter security - access control list on border routers
A) data security - operating system patch management
B) application security - hardening intermediary devices
C) host security - subnetwork segmentations
D) internal network security - corporate-wide data encryption
E) perimeter security - access control list on border routers

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
13
The ____ packet filtering screens individual packets in isolation.
A) stateful
B) random
C) stateless
D) dynamic
E) independent
A) stateful
B) random
C) stateless
D) dynamic
E) independent

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
14
Which protocol information may be LEAST used by the firewall to filter packets?
A) IP (Internet protocol)
B) TCP (Transport control protocol)
C) UDP (User datagram protocol)
D) ICMP (Internet control message protocol)
E) ARP (Address resolution protocol)
A) IP (Internet protocol)
B) TCP (Transport control protocol)
C) UDP (User datagram protocol)
D) ICMP (Internet control message protocol)
E) ARP (Address resolution protocol)

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
15
The _____ is better positioned to conduct 'deep packet inspection'.
A) host computer firewall
B) application-aware/application layer firewall
C) stateless packet filtering firewall
D) stateful packet filtering firewall
E) access control list of a router
A) host computer firewall
B) application-aware/application layer firewall
C) stateless packet filtering firewall
D) stateful packet filtering firewall
E) access control list of a router

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following technologies is NOT used for authentication?
A) Password and passphrase
B) Digital signature and digital certificate
C) Biometric solution (e.g., face recognition).
D) Security token
E) Access control list
A) Password and passphrase
B) Digital signature and digital certificate
C) Biometric solution (e.g., face recognition).
D) Security token
E) Access control list

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
17
The intrusion detection and intrusion prevention systems are designed to enable/provide ______.
A) data confidentiality (privacy)
B) data integrity
C) data authentication
D) access control
E) spoofing detection
A) data confidentiality (privacy)
B) data integrity
C) data authentication
D) access control
E) spoofing detection

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
18
"If destination IP = 161.154.23.59 and TCP port = 25, then pass the packet" is a form of the _____ filtering rule.
A) stateful
B) random
C) stateless
D) dynamic
E) independent
A) stateful
B) random
C) stateless
D) dynamic
E) independent

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck
19
The analyst of cyber threat intelligence more likely uses ________ heavily for day-to-day tasks.
A) forward proxy server
B) anti-virus and anti-malware
C) honeypot
D) software defined network
E) security information and event management (SIEM)
A) forward proxy server
B) anti-virus and anti-malware
C) honeypot
D) software defined network
E) security information and event management (SIEM)

Unlock Deck
Unlock for access to all 19 flashcards in this deck.
Unlock Deck
k this deck


