Deck 7: Operating System Scheduling and Deadlock Prevention: a Comprehensive Guide
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/33
Play
Full screen (f)
Deck 7: Operating System Scheduling and Deadlock Prevention: a Comprehensive Guide
1
Deadlock can occur ________.
A) only between two or more threads
B) only on multiprogrammed systems
C) only if resource sharing is allowed
D) none of the above
A) only between two or more threads
B) only on multiprogrammed systems
C) only if resource sharing is allowed
D) none of the above
D
2
Which of the following is not a major area of deadlock research?
A) prevention
B) avoidance
C) recovery
D) none of the above
A) prevention
B) avoidance
C) recovery
D) none of the above
D
3
If a process is given the task of waiting for an event to occur, and if the system includes no provision for signaling that event, then we have ________.
A) one-process deadlock
B) starvation
C) mutual exclusion
D) circular wait
A) one-process deadlock
B) starvation
C) mutual exclusion
D) circular wait
A
4
Most deadlocks in operating systems develop because of the normal contention for _________ .
A) dedicated resources
B) processors
C) main memory
D) device drivers
A) dedicated resources
B) processors
C) main memory
D) device drivers

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
5
________ is characteristic of deadlocked systems.
A) Starvation
B) Circular waiting
C) Saturation
D) Aging
A) Starvation
B) Circular waiting
C) Saturation
D) Aging

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
6
To avoid deadlock in spooling systems, a system can ________.
A) provide considerably more space for spooling files than is likely to be needed
B) restrain the input spoolers so that they do not accept additional print jobs when the spooling files approach some saturation threshold
C) allow printing to begin before the job is completed so that a full, or nearly full, spooling file can begin emptying while a job is still executing
D) all of the above
A) provide considerably more space for spooling files than is likely to be needed
B) restrain the input spoolers so that they do not accept additional print jobs when the spooling files approach some saturation threshold
C) allow printing to begin before the job is completed so that a full, or nearly full, spooling file can begin emptying while a job is still executing
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
7
The solution to the Dining Philosophers problem must ________.
A) prevent deadlock
B) prevent starvation
C) ensure mutual exclusion
D) all of the above
A) prevent deadlock
B) prevent starvation
C) ensure mutual exclusion
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
8
________ is a technique that prevents indefinite postponement.
A) Monitors
B) Mutual exclusion
C) Aging
D) Preemption
A) Monitors
B) Mutual exclusion
C) Aging
D) Preemption

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
9
Code that may be changed but is reinitialized each time it is used is said to be ________ .
A) serially reusable
B) reentrant
C) static
D) shared
A) serially reusable
B) reentrant
C) static
D) shared

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
10
________ code is not modified as it executes and may be shared by several processes simultaneously.
A) Preemptible
B) Dynamic
C) Reentrant
D) Serially reusable
A) Preemptible
B) Dynamic
C) Reentrant
D) Serially reusable

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
11
________ resources are the kinds that tend to become involved in deadlocks.
A) Preemptible
B) Serially reusable
C) Reentrant
D) all of the above
A) Preemptible
B) Serially reusable
C) Reentrant
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following is not a condition necessary for deadlock to exist?
A) wait-for condition
B) mutual-exclusion condition
C) circular-wait condition
D) indefinite-postponement condition
A) wait-for condition
B) mutual-exclusion condition
C) circular-wait condition
D) indefinite-postponement condition

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
13
_______ conditions a system to remove any possibility of deadlocks occurring.
A) Deadlock avoidance
B) Deadlock prevention
C) Deadlock detection
D) Deadlock recovery
A) Deadlock avoidance
B) Deadlock prevention
C) Deadlock detection
D) Deadlock recovery

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
14
________ imposes less stringent conditions than deadlock prevention in an attempt to get better resource utilization while stopping deadlock from occurring.
A) Deadlock avoidance
B) Deadlock detection
C) Deadlock recovery
D) both a and c
A) Deadlock avoidance
B) Deadlock detection
C) Deadlock recovery
D) both a and c

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
15
The strategy of denying the "wait-for" condition ________.
A) prevents deadlock from occurring
B) is commonly implemented
C) leads to poor resource utilization
D) both a and c
A) prevents deadlock from occurring
B) is commonly implemented
C) leads to poor resource utilization
D) both a and c

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
16
The strategy of denying the "no-preemption" condition could lead to ________.
A) indefinite postponement
B) loss of work
C) poor resource utilization
D) both a and b
A) indefinite postponement
B) loss of work
C) poor resource utilization
D) both a and b

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
17
The strategy of denying the "circular-wait" condition ________.
A) is a deadlock prevention technique that promotes portability
B) creates a linear ordering of resources
C) maximizes resource utilization
D) none of the above
A) is a deadlock prevention technique that promotes portability
B) creates a linear ordering of resources
C) maximizes resource utilization
D) none of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
18
The system is said to be in an unsafe state if ________.
A) the operating system cannot guarantee that all current processes can complete their work within a finite time
B) the system is deadlocked
C) a thread is indefinitely postponed
D) mutual exclusion has been violated
A) the operating system cannot guarantee that all current processes can complete their work within a finite time
B) the system is deadlocked
C) a thread is indefinitely postponed
D) mutual exclusion has been violated

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
19
Dijkstra's Banker's Algorithm requires the system to maintain ________ for each process.
A) a count of the system's total resources
B) the maximum resources that can be requested
C) the current loan
D) both b and c
A) a count of the system's total resources
B) the maximum resources that can be requested
C) the current loan
D) both b and c

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
20
Consider the following system state:
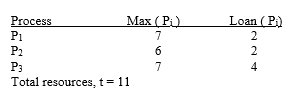 The system will be in a safe state if ________.
The system will be in a safe state if ________.
A) process P1 is allocated one additional resource
B) process P2 is allocated two additional resources
C) process P3 is allocated three additional resources
D) process P2 is allocated one additional resource
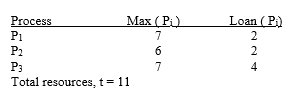 The system will be in a safe state if ________.
The system will be in a safe state if ________.A) process P1 is allocated one additional resource
B) process P2 is allocated two additional resources
C) process P3 is allocated three additional resources
D) process P2 is allocated one additional resource

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
21
An unsafe state implies ________.
A) the existence of deadlock
B) that deadlock will eventually occur
C) that some unfortunate sequence of events might lead to a deadlock
D) none of the above
A) the existence of deadlock
B) that deadlock will eventually occur
C) that some unfortunate sequence of events might lead to a deadlock
D) none of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
22
Consider the following system state:
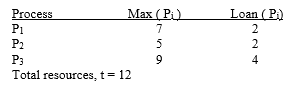 The system will enter an unsafe state if ________.
The system will enter an unsafe state if ________.
A) process P1 is allocated one additional resource
B) process P2 is allocated two additional resources
C) process P3 is allocated three additional resources
D) process P2 is allocated one additional resource
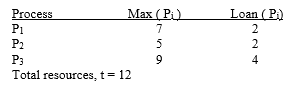 The system will enter an unsafe state if ________.
The system will enter an unsafe state if ________.A) process P1 is allocated one additional resource
B) process P2 is allocated two additional resources
C) process P3 is allocated three additional resources
D) process P2 is allocated one additional resource

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
23
In the Banker's Algorithm, resource requests that would result in ________ are repeatedly denied until they can eventually be satisfied.
A) indefinite postponement
B) holding resources while waiting for others
C) unsafe states
D) all of the above
A) indefinite postponement
B) holding resources while waiting for others
C) unsafe states
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
24
________ is a weakness of the Banker's Algorithm.
A) Allowing the population of processes to vary over time
B) Enabling processes to hold their resources indefinitely
C) Requiring that processes state their maximum needs in advance
D) Enabling the number of resources to fluctuate
A) Allowing the population of processes to vary over time
B) Enabling processes to hold their resources indefinitely
C) Requiring that processes state their maximum needs in advance
D) Enabling the number of resources to fluctuate

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
25
The Banker's Algorithm ________.
A) can provide better resource utilization than deadlock prevention
B) incurs little overhead
C) is appropriate for real-time systems
D) facilitates applications programming
A) can provide better resource utilization than deadlock prevention
B) incurs little overhead
C) is appropriate for real-time systems
D) facilitates applications programming

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
26
________ is the process of determining that a deadlock exists and identifying the processes and resources involved in the deadlock.
A) Deadlock avoidance
B) Deadlock detection
C) Deadlock recovery
D) Deadlock prevention
A) Deadlock avoidance
B) Deadlock detection
C) Deadlock recovery
D) Deadlock prevention

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
27
In a resource-allocation graph, ________ represent processes and ________ represent resources.
A) circles, squares
B) arrows, circles
C) squares, circles
D) arrows, squares
A) circles, squares
B) arrows, circles
C) squares, circles
D) arrows, squares

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
28
In a resource-allocation graph, an arrow points from a ________ to a ________ to indicate that the system has allocated a specific resource of a specific type to the process.
A) square, large circle
B) square, small circle
C) large circle, square
D) small circle, square
A) square, large circle
B) square, small circle
C) large circle, square
D) small circle, square

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
29
If a graph can be reduced by all its processes, then ________.
A) there is no deadlock
B) indefinite postponement cannot occur
C) the system is in an unsafe state
D) none of the above
A) there is no deadlock
B) indefinite postponement cannot occur
C) the system is in an unsafe state
D) none of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
30
To ensure that data in a database remains in a consistent state when deadlocked processes are terminated, database systems typically perform resource allocations using ________.
A) checkpoints
B) rollback
C) aging
D) transactions
A) checkpoints
B) rollback
C) aging
D) transactions

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following complicates deadlock recovery?
A) It may not be clear that the system has become deadlocked.
B) Most systems do not provide the means to suspend a process indefinitely.
C) The deadlock could involve many processes.
D) all of the above
A) It may not be clear that the system has become deadlocked.
B) Most systems do not provide the means to suspend a process indefinitely.
C) The deadlock could involve many processes.
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
32
Many of today's personal computer systems ignore deadlock because ________.
A) the processor time required to check for deadlocks can significantly reduce system performance
B) they do not perform many concurrent operations that could lead to deadlock
C) the number of resources that operating systems must manage is decreasing dramatically
D) all of the above
A) the processor time required to check for deadlocks can significantly reduce system performance
B) they do not perform many concurrent operations that could lead to deadlock
C) the number of resources that operating systems must manage is decreasing dramatically
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
33
Deadlock will continue to be an important area of research in current and future systems because ________.
A) large-scale systems are becoming more oriented toward asynchronous parallel operations
B) small, portable devices, for which users cannot rely on an administrator to detect and rid a system of deadlock, are becoming more prevalent
C) there is an increasing tendency of operating systems designers to view data as a resource that must be managed carefully
D) all of the above
A) large-scale systems are becoming more oriented toward asynchronous parallel operations
B) small, portable devices, for which users cannot rely on an administrator to detect and rid a system of deadlock, are becoming more prevalent
C) there is an increasing tendency of operating systems designers to view data as a resource that must be managed carefully
D) all of the above

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck


