Exam 6: EC-Council Certified Security Analyst
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/24
Play
Full screen (f)
Exam 6: EC-Council Certified Security Analyst
1
Lee has established a new startup where they develop android applications. In order to meet memory requirements of the company, Lee has hired a Cloud Service Provider, who offered memory space along with virtual systems. Lee was dissatisfied with their service and wanted to move to another CSP, but was denied as a part of the contract, which reads that the user cannot switch to another CSP. What is this condition called?
A) Virtualization
B) Lock-in
C) Resource Isolation
D) Lock-up
A) Virtualization
B) Lock-in
C) Resource Isolation
D) Lock-up
B
2
Jason is a penetration tester, and after completing the initial penetration test, he wanted to create a final penetration test report that consists of all activities performed throughout the penetration testing process. Before creating the final penetration testing report, which of the following reports should Jason prepare in order to verify if any crucial information is missed from the report?
A) Activity report
B) Host report
C) User report
D) Draft report
A) Activity report
B) Host report
C) User report
D) Draft report
A
3
A penetration tester at Trinity Ltd. is performing IoT device testing. As part of this process, he is checking the IoT devices for open ports using port scanners such as Nmap. After identifying the open ports, he started using automated tools to check each open port for any exploitable vulnerabilities. Identify the IoT security issues the penetration tester is trying to uncover?
A) Insecure software/firmware
B) Lack of transport encryption
C) Insecure network services
D) Insufficient security configurability
A) Insecure software/firmware
B) Lack of transport encryption
C) Insecure network services
D) Insufficient security configurability
D
4
James, a research scholar, received an email informing that someone is trying to access his Google account from an unknown device. When he opened his email message, it looked like a standard Google notification instructing him to click the link below to take further steps. This link was redirected to a malicious webpage where he was tricked to provide Google account credentials. James observed that the URL began with www.translate.google.com giving a legitimate appearance. In the above scenario, identify the type of attack being performed on James' email account?
A) SMiShing
B) Dumpster diving
C) Phishing
D) Vishing
A) SMiShing
B) Dumpster diving
C) Phishing
D) Vishing

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
5
Identify the PRGA from the following screenshot: 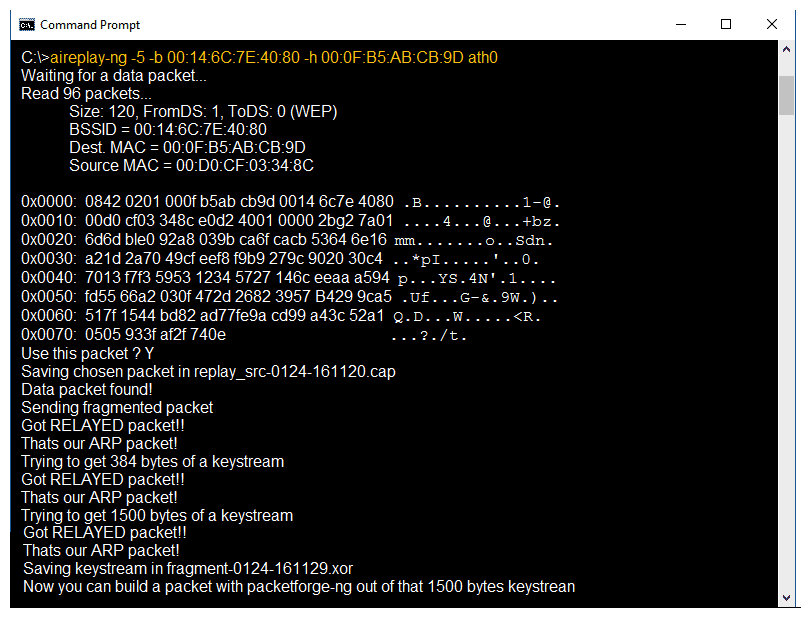
A) replay_src-0124-161120.cap
B) fragment-0124-161129.xor
C) 0505 933f af2f 740e
D) 0842 0201 000f b5ab cd9d 0014 6c7e 4080

A) replay_src-0124-161120.cap
B) fragment-0124-161129.xor
C) 0505 933f af2f 740e
D) 0842 0201 000f b5ab cd9d 0014 6c7e 4080

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
6
Henderson has completed the pen testing tasks. He is now compiling the final report for the client. Henderson needs to include the result of scanning that revealed a SQL injection vulnerability and different SQL queries that he used to bypass web application authentication. In which section of the pen testing report, should Henderson include this information?
A) General opinion section
B) Methodology section
C) Comprehensive technical report section
D) Executive summary section
A) General opinion section
B) Methodology section
C) Comprehensive technical report section
D) Executive summary section

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
7
A user unknowingly installed a fake malicious banking app in his Android mobile. This app includes a configuration file that consists of phone numbers of the bank. When the user makes a call to the bank, he is automatically redirected to the number being used by the attacker. The attacker impersonates as a banking official. Also, the app allows the attacker to call the user, then the app displays fake caller ID on the user's mobile resembling call from a legitimate bank. Identify the attack being performed on the Android mobile user?
A) Tailgating
B) SMiShing
C) Vishing
D) Eavesdropping
A) Tailgating
B) SMiShing
C) Vishing
D) Eavesdropping

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
8
Karen is a Network engineer at ITSec, a reputed MNC based in Philadelphia, USA. She wants to retrieve the DNS records from the publicly available servers. She searched using Google for the providers DNS Information and found the following sites: http://www.dnsstuff.com https://dnsquery.org Through these sites she got the DNS records information as she wished. What information is contained in DNS records?
A) Information about the DNS logs.
B) Information about local MAC addresses.
C) Information such as mail server extensions, IP addresses etc.
D) Information about the database servers and its services.
A) Information about the DNS logs.
B) Information about local MAC addresses.
C) Information such as mail server extensions, IP addresses etc.
D) Information about the database servers and its services.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
9
Stanley, a pen tester needs to perform various tests to detect SQL injection vulnerabilities. He has to make a list of all input fields whose values could be used in crafting a SQL query. This includes the hidden fields of POST requests and then test them separately, attempting to interfere with the query and cause an error to generate as a result. In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
A) Dynamic Testing
B) Static Testing
C) Function Testing
D) Source Code Testing
A) Dynamic Testing
B) Static Testing
C) Function Testing
D) Source Code Testing

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
10
Tom is a networking manager in XYZ Inc. He and his team were assigned the task to store and update the confidential files present on a remote server using Network File System (NFS) client-server application protocol. Since the files are confidential, Tom was asked to perform this operation in a secured manner by limiting the access only to his team. As per the instructions provided to him, to use NFS securely, he employed the process of limiting the superuser access privileges only to his team by using authentication based on the team personnel identity. Identify the method employed by Tom for securing access controls in NFS?
A) Root Squashing
B) nosuid
C) noexec
D) Suid
A) Root Squashing
B) nosuid
C) noexec
D) Suid

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
11
Michael, a penetration tester of Rolatac Pvt. Ltd., has completed his initial penetration testing and now he needs to create a penetration testing report for company's client, management, and top officials for their reference. For this, he created a report providing a detailed summary of the complete penetration testing process of the project that he has undergone, its outcomes, and recommendations for future testing and exploitation. In the above scenario, which type of penetration testing report has Michael prepared?
A) Host report
B) Activity report
C) User report
D) Executive report
A) Host report
B) Activity report
C) User report
D) Executive report

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
12
Rebecca, a security analyst, was auditing the network in her organization. During the scan, she found a service running on a remote host, which helped her to enumerate information related to user accounts, network interfaces, network routing and TCP connections. Which among the following services allowed Rebecca to enumerate the information?
A) NTP
B) SNMP
C) SMPT
D) SMB
A) NTP
B) SNMP
C) SMPT
D) SMB

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
13
Veronica, a penetration tester at a top MNC company, is trying to breach the company's database as a part of SQLi penetration testing. She began to use the SQLi techniques to test the database security level. She inserted new database commands into the SQL statement and appended a SQL Server EXECUTE command to the vulnerable SQL statements. Which of the following SQLi techniques was used to attack the database?
A) Function call injection
B) File inclusion
C) Buffer Overflow
D) Code injection
A) Function call injection
B) File inclusion
C) Buffer Overflow
D) Code injection

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
14
Steven is performing a wireless network audit. As part of the engagement, he is trying to crack a WPA-PSK key. Steven has captured enough packets to run aircrack-ng and discover the key, but aircrack-ng did not yield any result, as there were no authentication packets in the capture. Which of the following commands should Steven use to generate authentication packets?
A) aireplay-ng --deauth 11 -a AA:BB:CC:DD:EE:FF
B) airmon-ng start eth0
C) airodump-ng --write capture eth0
D) aircrack-ng.exe -a 2 -w capture.cap
A) aireplay-ng --deauth 11 -a AA:BB:CC:DD:EE:FF
B) airmon-ng start eth0
C) airodump-ng --write capture eth0
D) aircrack-ng.exe -a 2 -w capture.cap

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
15
An organization hosted a website to provide services to its customers. A visitor of this website has reported a complaint to the organization that they are getting an error message with code 502 when they are trying to access the website. This issue was forwarded to the IT department in the organization. The IT department identified the reason behind the error and started resolving the issue by checking whether the server is overloaded, whether the name resolution is working properly, whether the firewall is configured properly, etc. Identify the error message corresponding to code 502 that the visitors obtained when they tried to access the organization's website?
A) Bad request
B) Forbidden
C) Internal error
D) Bad gateway
A) Bad request
B) Forbidden
C) Internal error
D) Bad gateway

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
16
You are working on a pen testing assignment. Your client has asked for a document that shows them the detailed progress of the pen testing. Which document is the client asking for?
A) Scope of work (SOW) document
B) Rule of engagement with signatures of both the parties
C) Project plan with work breakdown structure
D) Engagement log
A) Scope of work (SOW) document
B) Rule of engagement with signatures of both the parties
C) Project plan with work breakdown structure
D) Engagement log

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
17
HDC Networks Ltd. is a leading security services company. Matthew works as a penetrating tester with this firm. He was asked to gather information about the target company. Matthew begins with social engineering by following the steps:
A) Secretly observes the target to gain critical information II. Looks at employee's password or PIN code with the help of binoculars or a low-power telescope Based on the above description, identify the information gathering technique.
B) Phishing
C) Shoulder surfing
D) Tailgating
E) Dumpster diving
A) Secretly observes the target to gain critical information II. Looks at employee's password or PIN code with the help of binoculars or a low-power telescope Based on the above description, identify the information gathering technique.
B) Phishing
C) Shoulder surfing
D) Tailgating
E) Dumpster diving

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
18
Richard, a penetration tester was asked to assess a web application. During the assessment, he discovered a file upload field where users can upload their profile pictures. While scanning the page for vulnerabilities, Richard found a file upload exploit on the website. Richard wants to test the web application by uploading a malicious PHP shell, but the web page denied the file upload. Trying to get around the security, Richard added the ' jpg ' extension to the end of the file. The new file name ended with '.php. jpg '. He then used the Burp suite tool and removed the ' jpg '' extension from the request while uploading the file. This enabled him to successfully upload the PHP shell. Which of the following techniques has Richard implemented to upload the PHP shell?
A) Session stealing
B) Cookie tampering
C) Cross site scripting
D) Parameter tampering
A) Session stealing
B) Cookie tampering
C) Cross site scripting
D) Parameter tampering

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
19
Ross performs security test on his company's network assets and creates a detailed report of all the findings. In his report, he clearly explains the methodological approach that he has followed in finding the loopholes in the network. However, his report does not mention about the security gaps that can be exploited or the amount of damage that may result from the successful exploitation of the loopholes. The report does not even mention about the remediation steps that are to be taken to secure the network. What is the type of test that Ross has performed?
A) Penetration testing
B) Vulnerability assessment
C) Risk assessment
D) Security audit
A) Penetration testing
B) Vulnerability assessment
C) Risk assessment
D) Security audit

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
20
Recently, Jacob was assigned a project to test the perimeter security of one of a client. As part of the project, Jacob wants to test whether or not a particular port on the firewall is open or closed. He used the hping utility with the following syntax: #hping -S -c 1 -p -t What response will indicate the particular port is allowed in the firewall?
A) Host Unreachable
B) TTL Exceeded
C) No Response
D) ICMP Port Unreachable
A) Host Unreachable
B) TTL Exceeded
C) No Response
D) ICMP Port Unreachable

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
21
Gibson, a security analyst at MileTech Solutions, is performing cloud penetration testing. As part of this process, he needs to check for any governance and compliance issues against cloud services. Which of the following documents helps Gibson in checking whether the CSP is regularly audited and certified for compliance issues?
A) Service level agreement
B) Data use agreement
C) ROE agreement
D) Nondisclosure agreement
A) Service level agreement
B) Data use agreement
C) ROE agreement
D) Nondisclosure agreement

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
22
An anonymity network is a series of?
A) Covert government networks
B) Virtual networks tunnels
C) Government networks in Tora
D) War driving maps
A) Covert government networks
B) Virtual networks tunnels
C) Government networks in Tora
D) War driving maps

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following reports should you as an IT auditor use to check on compliance with a service level agreement's requirement for uptime?
A) Systems logs
B) Hardware error reports
C) Availability reports
D) Utilization reports
A) Systems logs
B) Hardware error reports
C) Availability reports
D) Utilization reports

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
24
A recent audit has identified a few control exceptions and is recommending the implementation of technology and processes to address the finding. Which of the following is the MOST likely reason for the organization to reject the implementation of the recommended technology and processes?
A) The organization has purchased cyber insurance
B) The risk tolerance of the organization permits this risk
C) The CIO of the organization disagrees with the finding
D) The auditors have not followed proper auditing processes
A) The organization has purchased cyber insurance
B) The risk tolerance of the organization permits this risk
C) The CIO of the organization disagrees with the finding
D) The auditors have not followed proper auditing processes

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck


