Deck 15: Dicision Making Models and Knowledge Management
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/47
Play
Full screen (f)
Deck 15: Dicision Making Models and Knowledge Management
1
Which of the following statements about technology and knowledge management is most true?
A) Technology can facilitate knowledge management.
B) Knowledge management can facilitate technology.
C) Technology is required in knowledge management systems.
D) Knowledge management systems do not include technology.
A) Technology can facilitate knowledge management.
B) Knowledge management can facilitate technology.
C) Technology is required in knowledge management systems.
D) Knowledge management systems do not include technology.
A
2
Which element of Steps for Better Thinking focuses on choosing and implementing solutions?
A) Foundation.
B) Identifying.
C) Envisioning.
D) Prioritizing.
A) Foundation.
B) Identifying.
C) Envisioning.
D) Prioritizing.
D
3
Newspapers are easier to read than textbooks, illustrating which of the following causes of information overload?
A) Information characteristics.
B) Information technology.
C) Task parameters.
D) Organizational design.
A) Information characteristics.
B) Information technology.
C) Task parameters.
D) Organizational design.
A
4
Which element of Steps for Better Thinking focuses on interpreting and organizing information?
A) Exploring.
B) Identifying.
C) Envisioning.
D) Prioritizing.
A) Exploring.
B) Identifying.
C) Envisioning.
D) Prioritizing.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
5
Every year, David promises himself to file his taxes as soon as possible. But, inevitably, he waits until the last minute. David's behavior is an example of:
A) Satisficing.
B) Bounded rationality.
C) Relapse error.
D) Information overload.
A) Satisficing.
B) Bounded rationality.
C) Relapse error.
D) Information overload.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
6
Denise had memorized rules about making adjusting entries in the accounting information system. She continued to use those rules, even when they failed to produce the best outcome possible. Her behavior is an example of:
A) Satisficing.
B) Bounded rationality.
C) Relapse error.
D) Information overload.
A) Satisficing.
B) Bounded rationality.
C) Relapse error.
D) Information overload.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
7
When a person has to make a decision quickly, ___ may cause information overload.
A) Personal factors.
B) Information parameters.
C) Task and process parameters.
D) Information technology.
A) Personal factors.
B) Information parameters.
C) Task and process parameters.
D) Information technology.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
8
Mike was auditing the accounting information system of FBN Corporation. He wanted to select a sample of transactions to verify; rather than considering all the possible choices, he used a sampling method he found easiest in school. Mike's behavior is an example of:
A) Satisficing.
B) Bounded rationality.
C) Relapse error.
D) Information overload.
A) Satisficing.
B) Bounded rationality.
C) Relapse error.
D) Information overload.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
9
Which element of Steps for Better Thinking focuses on acquiring background knowledge and skills?
A) Foundation.
B) Identifying.
C) Exploring.
D) Prioritizing.
A) Foundation.
B) Identifying.
C) Exploring.
D) Prioritizing.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
10
Phil, a corporate controller, was preparing a comprehensive presentation of his firm's financial statements for the board of directors. He suspected some members of the board would experience information overload. Which of the following countermeasures could Phil employ most effectively to reduce information overload for his audience?
A) Create small, self-contained tasks.
B) Improve personal time management skills.
C) Define decision rules.
D) Use graphs and visual aides.
A) Create small, self-contained tasks.
B) Improve personal time management skills.
C) Define decision rules.
D) Use graphs and visual aides.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
11
Information overload can be caused by all of the following except:
A) Information design.
B) Information technology.
C) Organizational design.
D) Information characteristics.
A) Information design.
B) Information technology.
C) Organizational design.
D) Information characteristics.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
12
___ can cause information overload simply by increasing the amount of available information.
A) Organizational design.
B) Process parameters.
C) Information characteristics.
D) Information technology.
A) Organizational design.
B) Process parameters.
C) Information characteristics.
D) Information technology.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
13
Working in groups frequently leads to information overload because of:
A) Information technology.
B) Organizational design.
C) Task parameters.
D) Personal factors.
A) Information technology.
B) Organizational design.
C) Task parameters.
D) Personal factors.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
14
Peter created an online database for his company's computer network. If anyone inside the firm can search the database without entering a user name or password, it is fulfilling which objective of knowledge management?
A) To improve knowledge access.
B) To create knowledge repositories.
C) To cause a shift in organizational culture.
D) To manage knowledge as an asset.
A) To improve knowledge access.
B) To create knowledge repositories.
C) To cause a shift in organizational culture.
D) To manage knowledge as an asset.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
15
The organization of intellectual resources and information systems within a business environment is often referred to as:
A) A decision making model.
B) Knowledge management.
C) The accounting information system.
D) Systems analysis and design.
A) A decision making model.
B) Knowledge management.
C) The accounting information system.
D) Systems analysis and design.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
16
Phil, a corporate controller, was preparing a comprehensive presentation of his firm's financial statements for the board of directors. He suspected some members of the board would experience information overload, so he wanted to focus on creating value-added information as a strategy for reducing it. Which of the following is the best example of value-added information in this context?
A) An explanation of the company's inventory cost flow assumption (FIFO, LIFO).
B) The difference between the direct and indirect methods of computing cash flow from operations.
C) The percentage change in this year's net income compared to last year's.
D) A list of steps in the accounting cycle.
A) An explanation of the company's inventory cost flow assumption (FIFO, LIFO).
B) The difference between the direct and indirect methods of computing cash flow from operations.
C) The percentage change in this year's net income compared to last year's.
D) A list of steps in the accounting cycle.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
17
The first step in creating a knowledge management system is:
A) Define business goals.
B) Create an appropriate organizational culture.
C) Perform a knowledge audit.
D) Create a mental model.
A) Define business goals.
B) Create an appropriate organizational culture.
C) Perform a knowledge audit.
D) Create a mental model.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
18
Knowledge management is the process through which organizations generate value from what kind(s) of assets: (i) monetary, (ii) intellectual, (iii) knowledge-based.
A) i and ii only.
B) ii and iii only.
C) i and iii only.
D) i, ii and iii.
A) i and ii only.
B) ii and iii only.
C) i and iii only.
D) i, ii and iii.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
19
Which element of Steps for Better Thinking focuses on finding relevant information and acknowledging uncertainties?
A) Foundation.
B) Identifying.
C) Envisioning.
D) Prioritizing.
A) Foundation.
B) Identifying.
C) Envisioning.
D) Prioritizing.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
20
Which of the following is the least appropriate business goal for a knowledge management system?
A) Improving customer service.
B) Justifying employee layoffs.
C) Enhancing competitive advantage.
D) Developing employee-training plans.
A) Improving customer service.
B) Justifying employee layoffs.
C) Enhancing competitive advantage.
D) Developing employee-training plans.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
21
Decision makers can avoid information overload caused by organizational design by:
A) Using information technology.
B) Working alone.
C) Satisficing.
D) Avoiding relapse errors.
A) Using information technology.
B) Working alone.
C) Satisficing.
D) Avoiding relapse errors.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
22
Mike had recently finished his accounting degree, and was considering which professional journals he should subscribe to in his career. He purchased ten different journals and read the first article in each one, then made his decision. His behavior is an example of:
A) Limited information search strategies.
B) Arbitrary information analysis.
C) Suboptimal decisions.
D) Strenuous personal situations.
A) Limited information search strategies.
B) Arbitrary information analysis.
C) Suboptimal decisions.
D) Strenuous personal situations.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
23
Satisficing, bounded rationality and relapse errors
A group of accounting students was discussing which elective courses they should take as part of their degree; several comments from their conversation appear below. Place an "X" in the appropriate column to indicate whether each comment most clearly demonstrates satisficing, bounded rationality or relapse errors.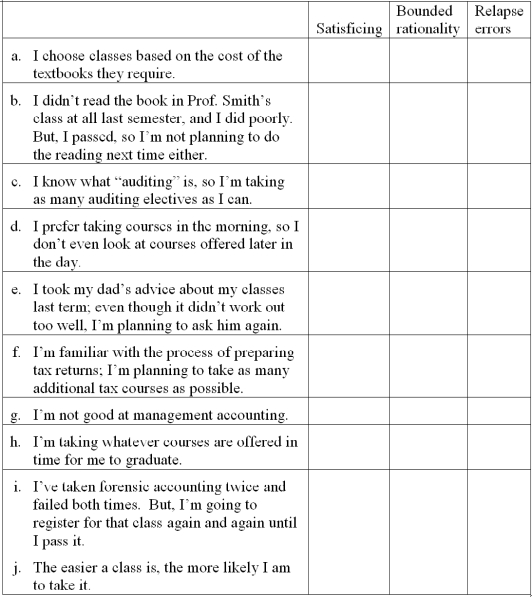
A group of accounting students was discussing which elective courses they should take as part of their degree; several comments from their conversation appear below. Place an "X" in the appropriate column to indicate whether each comment most clearly demonstrates satisficing, bounded rationality or relapse errors.


Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
24
Each year, employees in the accounting department of TCB Corporation discuss the upcoming year's budget with their department manager. Those discussions best fulfill which objective of knowledge management systems?
A) Creating a knowledge repository.
B) Improving knowledge access.
C) Enhancing the knowledge environment.
D) Managing knowledge as an asset.
A) Creating a knowledge repository.
B) Improving knowledge access.
C) Enhancing the knowledge environment.
D) Managing knowledge as an asset.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
25
Mike had recently finished his accounting degree, and was considering which professional journals he should subscribe to in his career. He purchased two journals and read all the articles in each one, then made his decision. His behavior is an example of:
A) Limited information search strategies.
B) Arbitrary information analysis.
C) Suboptimal decisions.
D) Strenuous personal situations.
A) Limited information search strategies.
B) Arbitrary information analysis.
C) Suboptimal decisions.
D) Strenuous personal situations.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following could be accurately described as a decision model: (i) debit and credit rules, (ii) weighted rating software technique.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
27
Steps for Better Thinking
Indicate which level of Steps for Better Thinking is described by each of the following items.
_________
a. Acquire background knowledge and skills
_________
b. Choose and implement solutions.
_________
c. Deal with limitations to the solution.
_________
d. Identify the problem, relevant information and uncertainties.
_________
e. Interpret and organize the information.
Indicate which level of Steps for Better Thinking is described by each of the following items.
_________
a. Acquire background knowledge and skills
_________
b. Choose and implement solutions.
_________
c. Deal with limitations to the solution.
_________
d. Identify the problem, relevant information and uncertainties.
_________
e. Interpret and organize the information.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
28
Knowledge management systems
Place an "X" in the appropriate column to indicate whether each of the following independent statements about knowledge management is true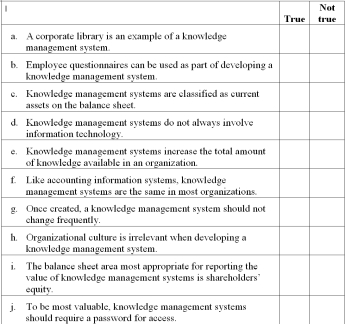
Place an "X" in the appropriate column to indicate whether each of the following independent statements about knowledge management is true


Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
29
Betsy and Molly had identified three business goals for their company's knowledge management system. Their supervisor asked them which goal was most important. Betsy and Molly would use the ___ level of Steps for Better Thinking to answer the supervisor's question.
A) Foundation.
B) Identifying.
C) Exploring.
D) Prioritizing.
A) Foundation.
B) Identifying.
C) Exploring.
D) Prioritizing.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
30
One step in creating a knowledge management system involves creating an appropriate organizational culture. Learning about the elements of corporate culture would be an activity in which part of Steps for Better Thinking?
A) Foundation.
B) Identifying.
C) Exploring.
D) Prioritizing.
A) Foundation.
B) Identifying.
C) Exploring.
D) Prioritizing.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
31
Steps for Better Thinking comprises four steps after its foundation level. Which of the following is most representative of Level Three?
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
32
Mike had recently finished his accounting degree, and was considering which professional journals he should subscribe to in his career. He purchased several journals and read all the articles in each one right after finishing the CPA exam, then made his decision. His behavior is an example of:
A) Limited information search strategies.
B) Arbitrary information analysis.
C) Suboptimal decisions.
D) Strenuous personal situations.
A) Limited information search strategies.
B) Arbitrary information analysis.
C) Suboptimal decisions.
D) Strenuous personal situations.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
33
Matt needed to estimate uncollectible receivables as part of a financial statement audit. According to Steps for Better Thinking, which of the following should Matt do first?
A) Calculate the estimate.
B) Exclude years where sales were unusually high or unusually low.
C) Graph the net sales and bad debt expense for the last several years.
D) Review the concepts associated with the estimation in an accounting textbook.
A) Calculate the estimate.
B) Exclude years where sales were unusually high or unusually low.
C) Graph the net sales and bad debt expense for the last several years.
D) Review the concepts associated with the estimation in an accounting textbook.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
34
Steps for Better Thinking comprise four steps after its foundation level. Which of the following is most representative of Level One?
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
35
Marge was creating an Access database to serve as her company's knowledge management system. Which of the following field types is she least likely to use in completing her task?
A) Memo.
B) Currency.
C) Text.
D) Date/time.
A) Memo.
B) Currency.
C) Text.
D) Date/time.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
36
A student creates an online knowledge management system for evaluating professors at her university. Her system fulfills all the objectives of a knowledge management system except:
A) Creating a knowledge repository.
B) Improving knowledge access.
C) Enhancing the knowledge environment.
D) Managing knowledge as an asset.
A) Creating a knowledge repository.
B) Improving knowledge access.
C) Enhancing the knowledge environment.
D) Managing knowledge as an asset.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following would precede the identifying phase of Steps for Better Thinking: (i) obtaining a college degree, (ii) reading the newspaper.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
38
Steps for Better Thinking comprise four steps after its foundation level. Which of the following is most representative of Level Two?
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
39
Matt needed to estimate uncollectible receivables as part of a financial statement audit. According to Steps for Better Thinking, which of the following should Matt do second?
A) Review the concepts associated with the estimation in an accounting textbook.
B) Graph the net sales and bad debt expense for the last several years.
C) Exclude years where sales were unusually high or unusually low.
D) Calculate the estimate.
A) Review the concepts associated with the estimation in an accounting textbook.
B) Graph the net sales and bad debt expense for the last several years.
C) Exclude years where sales were unusually high or unusually low.
D) Calculate the estimate.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
40
Steps for Better Thinking comprises four steps after its foundation level. Which of the following is most representative of Level Four?
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.
A) Creating a plan to train employees on the new system.
B) Deciding between a view-driven system and an event-driven system.
C) Grouping information obtained through employee interviews into several categories.
D) Recognizing the need for a new accounting information system.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
41
Visual map
Part of creating a knowledge management system is creating a visual map of its ideas. Create a visual map that depicts at least three major ideas related to internal control in accounting information systems.
Part of creating a knowledge management system is creating a visual map of its ideas. Create a visual map that depicts at least three major ideas related to internal control in accounting information systems.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
42
The following scenario applies to Questions:
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Kay has come to you for advice regarding this situation. To help her, explain your personal strategy for making decisions and managing knowledge.
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Kay has come to you for advice regarding this situation. To help her, explain your personal strategy for making decisions and managing knowledge.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
43
The following scenario applies to Questions:
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Assume Kay has the background information and skills she needs to solve the problem. Use the first three levels of Steps for Better Thinking to advise Kay on how to proceed.
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Assume Kay has the background information and skills she needs to solve the problem. Use the first three levels of Steps for Better Thinking to advise Kay on how to proceed.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
44
Steps for Better Thinking
Arnold and Robin were trying to develop a strong internal control system for their company's acquisition/payment process. Suggest an appropriate question they should ask at each level of the Steps for Better Thinking framework.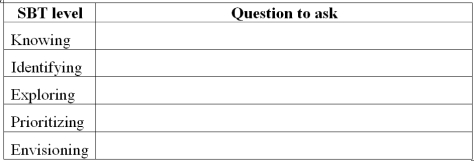
Arnold and Robin were trying to develop a strong internal control system for their company's acquisition/payment process. Suggest an appropriate question they should ask at each level of the Steps for Better Thinking framework.


Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
45
The following scenario applies to Questions:
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Kay has decided to create a knowledge management system for her client. Use the four objectives of knowledge management systems discussed in the text to explain to Kay's client what such a system will accomplish.
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Kay has decided to create a knowledge management system for her client. Use the four objectives of knowledge management systems discussed in the text to explain to Kay's client what such a system will accomplish.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
46
The following scenario applies to Questions:
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Kay is experiencing information overload. The text identified five common sources of information overload; explain which of the five are related to Kay's specific situation.
Kay was frustrated. She was auditing a new client for the first time, but the client's accounting information system was in complete disarray. The client, a multi-national corporation, had boxes and filing cabinets full of paper forms in at least three languages. She had been working very long days with her other clients, too. She needed to come up with a plan for making sense of the documents before she could proceed with any of the audit tasks.
Kay is experiencing information overload. The text identified five common sources of information overload; explain which of the five are related to Kay's specific situation.

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck
48
Match between columns

Unlock Deck
Unlock for access to all 47 flashcards in this deck.
Unlock Deck
k this deck


