Deck 14: Computer Crime and Information Technology Security
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/58
Play
Full screen (f)
Deck 14: Computer Crime and Information Technology Security
1
"Any illegal act for which knowledge of computer technology is used to commit the offense" is the United States Department of Justice definition of:
A) An intrusion.
B) Information manipulation.
C) Information theft.
D) Computer fraud.
A) An intrusion.
B) Information manipulation.
C) Information theft.
D) Computer fraud.
D
2
According to Carter's taxonomy of computer crime, which of the following best describes the computer as a target?
A) Using the computer to further a criminal end.
B) Focusing on the system or its data.
C) Not required, but related to the criminal act.
D) New versions of traditional crimes.
A) Using the computer to further a criminal end.
B) Focusing on the system or its data.
C) Not required, but related to the criminal act.
D) New versions of traditional crimes.
B
3
The COBIT framework can be used to strengthen internal controls against computer crime by helping information systems professionals: (i) identify risk, (ii) assign responsibility, (iii) designate authority.
A) i and ii only.
B) i and iii only.
C) ii and iii only.
D) i, ii and iii.
A) i and ii only.
B) i and iii only.
C) ii and iii only.
D) i, ii and iii.
D
4
A hacker launches a denial of service attack against an information system, then demands money to stop it. The hacker's actions are an example of:
A) Extortion.
B) Malicious software.
C) Intrusion.
D) Information theft.
A) Extortion.
B) Malicious software.
C) Intrusion.
D) Information theft.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
5
An unhappy employee introduces a virus that will shut down a company's information system if his name no longer appears in the payroll database. The employee's action is an example of which element of Carter's taxonomy?
A) Target.
B) Instrumentality.
C) Incidental.
D) Associated.
A) Target.
B) Instrumentality.
C) Incidental.
D) Associated.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
6
According to Carter's taxonomy of computer crime, which of the following best describes the computer as an instrumentality?
A) Using the computer to further a criminal end.
B) Focusing on the system or its data.
C) Not required, but related to the criminal act.
D) New versions of traditional crimes.
A) Using the computer to further a criminal end.
B) Focusing on the system or its data.
C) Not required, but related to the criminal act.
D) New versions of traditional crimes.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
7
A customer's bank account should be credited with $10.532 interest. The bank's information system is most exposed to which of the following risks/threats?
A) Extortion.
B) Information manipulation.
C) Information theft.
D) Disclosure of confidential information.
A) Extortion.
B) Information manipulation.
C) Information theft.
D) Disclosure of confidential information.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
8
According to Carter's taxonomy of computer crime, which of the following best describes the computer as incidental?
A) Using the computer to further a criminal end.
B) Focusing on the system or its data.
C) Not required, but related to the criminal act.
D) New versions of traditional crimes.
A) Using the computer to further a criminal end.
B) Focusing on the system or its data.
C) Not required, but related to the criminal act.
D) New versions of traditional crimes.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
9
As a form of internal control, fingerprint scans are most likely to prevent:
A) Intrusions.
B) Computer fraud.
C) Service interruptions.
D) Errors.
A) Intrusions.
B) Computer fraud.
C) Service interruptions.
D) Errors.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following is not part of the IT control taxonomy presented in the text?
A) Physical.
B) Technical.
C) Administrative.
D) Financial.
A) Physical.
B) Technical.
C) Administrative.
D) Financial.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
11
A bank teller steals money from the vault and covers up the theft by making a journal entry in the accounting information system. The teller's actions are an example of which element of Carter's taxonomy?
A) Target.
B) Instrumentality.
C) Incidental.
D) Associated.
A) Target.
B) Instrumentality.
C) Incidental.
D) Associated.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
12
All of the following are business risks and threats related to computer crime except:
A) Disclosure of confidential information.
B) Conflict of interest.
C) Extortion.
D) Denial of service attacks.
A) Disclosure of confidential information.
B) Conflict of interest.
C) Extortion.
D) Denial of service attacks.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
13
A terrorist posts a threatening message on a web site. The post is an example of which element of Carter's taxonomy?
A) Target.
B) Instrumentality.
C) Incidental.
D) Associated.
A) Target.
B) Instrumentality.
C) Incidental.
D) Associated.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following is not an element of the CIA triad?
A) Data integrity.
B) Confidentiality.
C) Accessibility.
D) Competence.
A) Data integrity.
B) Confidentiality.
C) Accessibility.
D) Competence.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
15
An attempt to gain access to a network or a system by bypassing security controls is referred to as a(n):
A) Denial of service attack.
B) Web site defacement.
C) Intrusion.
D) Error.
A) Denial of service attack.
B) Web site defacement.
C) Intrusion.
D) Error.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
16
Which type of computer criminal is most closely associated with spamming, phishing, extortion and other profitable branches of computer crime?
A) Corporate spies.
B) Organized crime.
C) Script kiddies.
D) Terrorists.
A) Corporate spies.
B) Organized crime.
C) Script kiddies.
D) Terrorists.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
17
Computer hackers driven by financial gain are called:
A) Script kiddies.
B) Cyber-criminals.
C) Insiders.
D) Corporate spies.
A) Script kiddies.
B) Cyber-criminals.
C) Insiders.
D) Corporate spies.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
18
According to the COBIT framework, information that is "relevant and pertinent to the business process and is delivered in a timely, correct, consistent and usable manner" meets the ___ criterion.
A) Integrity.
B) Availability.
C) Effectiveness.
D) Compliance.
A) Integrity.
B) Availability.
C) Effectiveness.
D) Compliance.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
19
The COBIT framework can be used to strengthen internal controls against computer crime by:
A) Helping information systems professionals identify and assess risk.
B) Listing the internal controls every organization should implement.
C) Requiring a SAS 70 audit.
D) Specifying which encryption method is most secure.
A) Helping information systems professionals identify and assess risk.
B) Listing the internal controls every organization should implement.
C) Requiring a SAS 70 audit.
D) Specifying which encryption method is most secure.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
20
According to the COBIT framework, information that is "accurate and complete and is in accordance with business values and expectations" meets the ___ criterion.
A) Accuracy.
B) Completeness.
C) Integrity.
D) Reliability.
A) Accuracy.
B) Completeness.
C) Integrity.
D) Reliability.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
21
As a business risk, extortion can be preceded by: (i) information theft, (ii) error, (iii) malicious software.
A) i and ii only.
B) i and iii only.
C) ii and iii only.
D) i, ii and iii.
A) i and ii only.
B) i and iii only.
C) ii and iii only.
D) i, ii and iii.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
22
As an administrative security control, a well-written conflict of interest policy would be most helpful in punishing which category of computer criminal?
A) Organized crime.
B) Terrorists.
C) Hackers.
D) Fraudsters.
A) Organized crime.
B) Terrorists.
C) Hackers.
D) Fraudsters.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
23
An organization experiencing a denial of service attack is most likely failing to fulfill which of COBIT's information criteria?
A) Confidentiality.
B) Availability.
C) Compliance.
D) Integrity.
A) Confidentiality.
B) Availability.
C) Compliance.
D) Integrity.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
24
On a monthly basis, internal auditors review an organization's information security policy over a specific group of physical computer assets. The review is an example of a(n):
A) Physical security control.
B) Technical security control.
C) Administrative security control.
D) Sarbanes-Oxley security control.
A) Physical security control.
B) Technical security control.
C) Administrative security control.
D) Sarbanes-Oxley security control.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
25
According to the COBIT accountability framework, the scope of corporate governance accountability and the scope of information governance accountability differ based on (i) the presence of disclosure, (ii) the stakeholders involved.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
26
A company installs video surveillance outside the room that houses its central computer servers. The video system is an example of a(n):
A) Physical control.
B) Technical control.
C) Administrative control.
D) Data control.
A) Physical control.
B) Technical control.
C) Administrative control.
D) Data control.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
27
A hacker extracts clients' social security numbers from a company's information system, then offers to sell the numbers back to the company to prevent their disclosure. The hacker's actions are an example of:
A) Disclosure of confidential information.
B) Extortion.
C) Information manipulation.
D) Service interruption.
A) Disclosure of confidential information.
B) Extortion.
C) Information manipulation.
D) Service interruption.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
28
Information systems professionals would most likely consult with legal professionals for advice regarding which of COBIT's information criteria?
A) Availability.
B) Compliance.
C) Reliability.
D) Integrity.
A) Availability.
B) Compliance.
C) Reliability.
D) Integrity.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
29
In MRT Corporation, users must say a specific phrase to gain access to information systems. The system identifies both the phrase and the user's voice before allowing access. MRT's system is an example of a(n):
A) Physical security control.
B) Technical security control.
C) Administrative security control.
D) Computer fraud control.
A) Physical security control.
B) Technical security control.
C) Administrative security control.
D) Computer fraud control.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
30
Which type of computer control is most likely to prevent the threat of system intrusions?
A) Physical.
B) Technical.
C) Administrative.
D) Biomechanical.
A) Physical.
B) Technical.
C) Administrative.
D) Biomechanical.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
31
According to the COBIT accountability framework, which of the following stakeholder groups should create disclosures regarding information governance controls?
A) The board of directors.
B) Internal auditors.
C) External auditors.
D) IT and information security management.
A) The board of directors.
B) Internal auditors.
C) External auditors.
D) IT and information security management.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
32
Errors are most likely to lead to which of the following business risks/threats?
A) Service interruptions and delays.
B) Disclosure of confidential information.
C) Intrusions.
D) Information manipulation.
A) Service interruptions and delays.
B) Disclosure of confidential information.
C) Intrusions.
D) Information manipulation.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
33
Corporate spies are most closely associated with which of the following business risks?
A) Malicious software.
B) Information theft.
C) Web site defacements.
D) Computer fraud.
A) Malicious software.
B) Information theft.
C) Web site defacements.
D) Computer fraud.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
34
Extortion is an example of: (i) a computer-associated crime, (ii) computer as incidental to a crime?
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
35
A well-developed information security policy will enhance internal control by helping to fulfill which of COBIT's information criteria?
A) Effectiveness.
B) Efficiency.
C) Confidentiality.
D) Accuracy.
A) Effectiveness.
B) Efficiency.
C) Confidentiality.
D) Accuracy.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
36
The main difference between hackers and cyber-criminals is:
A) Their motivation.
B) Their knowledge.
C) Their relationship to the organization.
D) Their techniques.
A) Their motivation.
B) Their knowledge.
C) Their relationship to the organization.
D) Their techniques.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
37
Which type of computer criminal is least sophisticated in terms of computer knowledge?
A) Hackers.
B) Corporate spies.
C) Cyber-criminals.
D) Script kiddies.
A) Hackers.
B) Corporate spies.
C) Cyber-criminals.
D) Script kiddies.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
38
Administrative security controls can be used to prevent problems with (i) confidentiality, (ii) data integrity, (iii) availability.
A) i and ii only.
B) ii and iii only.
C) i and iii only.
D) i, ii and iii.
A) i and ii only.
B) ii and iii only.
C) i and iii only.
D) i, ii and iii.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
39
Web site defacements are an example of: (i) computer as a crime target, (ii) computer as an instrumentality?
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.
A) i only.
B) ii only.
C) Both i and ii.
D) Neither i nor ii.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
40
A computer criminal initiates a denial of service attack designed to shut down a country's air traffic control system. The computer criminal is best described as a(n):
A) Hacker.
B) Corporate spy.
C) Insider.
D) Terrorist.
A) Hacker.
B) Corporate spy.
C) Insider.
D) Terrorist.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
41
The following scenario applies to Questions:
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
Which of the following internal controls would be most effective in preventing Calvin from carrying out the tabloid's request?
A) Conflict of interest policy.
B) Intrusion detection system.
C) Employee bonding.
D) Data access controls.
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
Which of the following internal controls would be most effective in preventing Calvin from carrying out the tabloid's request?
A) Conflict of interest policy.
B) Intrusion detection system.
C) Employee bonding.
D) Data access controls.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
42
Computer crime taxonomy: Fill in each blank below with a word or phrase based on Carter's taxonomy of computer crime.
a. Target: This category is comprised of computer crimes where the criminal targets ______. The objective of these crimes is to impact the ______ of data stored on the computer.
b. Instrumentality: Computer as the instrumentality of the crime uses the computer to ______. The computer is used to ______.
c. Incidental: This type of computer crime encompasses crimes where the computer is not ______ but is ______. The use of computer ______ and may make the crime more difficult to ______.
d. Associated: The simple ______ of computers, and notably the growth of the Internet, has generated ______of ______. In these cases, technological growth essentially creates ______ and new ways of ______.
a. Target: This category is comprised of computer crimes where the criminal targets ______. The objective of these crimes is to impact the ______ of data stored on the computer.
b. Instrumentality: Computer as the instrumentality of the crime uses the computer to ______. The computer is used to ______.
c. Incidental: This type of computer crime encompasses crimes where the computer is not ______ but is ______. The use of computer ______ and may make the crime more difficult to ______.
d. Associated: The simple ______ of computers, and notably the growth of the Internet, has generated ______of ______. In these cases, technological growth essentially creates ______ and new ways of ______.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
43
The following scenario applies to Questions:
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
If Calvin carries out the tabloid's request, RRI's information system will fail to meet which of COBIT's information criteria?
A) Effectiveness and efficiency.
B) Confidentiality and compliance.
C) Compliance and effectiveness.
D) Confidentiality and efficiency.
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
If Calvin carries out the tabloid's request, RRI's information system will fail to meet which of COBIT's information criteria?
A) Effectiveness and efficiency.
B) Confidentiality and compliance.
C) Compliance and effectiveness.
D) Confidentiality and efficiency.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
44
Carter identified four categories of computer crime. Explain which categories are most appropriate for Tim's action.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
45
COBIT's accountability framework can enhance internal control by assigning responsibility and designating authority for various tasks related to information systems security. Which of the following groups is most suited to develop technical security controls?
A) Board of directors.
B) External auditors.
C) Audit committee.
D) Information security management.
A) Board of directors.
B) External auditors.
C) Audit committee.
D) Information security management.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
46
COBIT accountability framework
Indicate one group from COBIT's accountability framework that applies to each item below. Some groups may be repeated.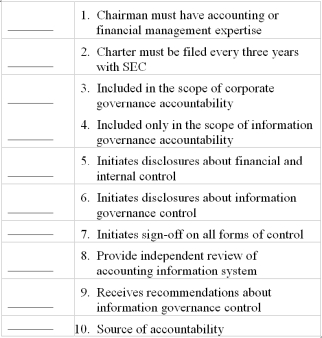
Indicate one group from COBIT's accountability framework that applies to each item below. Some groups may be repeated.


Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
47
List the seven information criteria associated with the COBIT framework. Which criteria will be compromised if Tim activates the program?

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
48
The following scenario applies to Questions:
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
Assuming Calvin accepts the offer, he could be described as all of the following except:
A) Cyber-criminal.
B) Corporate spy.
C) Organized crime.
D) Hacker.
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
Assuming Calvin accepts the offer, he could be described as all of the following except:
A) Cyber-criminal.
B) Corporate spy.
C) Organized crime.
D) Hacker.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
49
The textbook identified eleven specific business risks/threats associated with information technology. Discuss three that apply in this situation.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
50
Computer crime taxonomy, computer criminals and internal controls
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 7.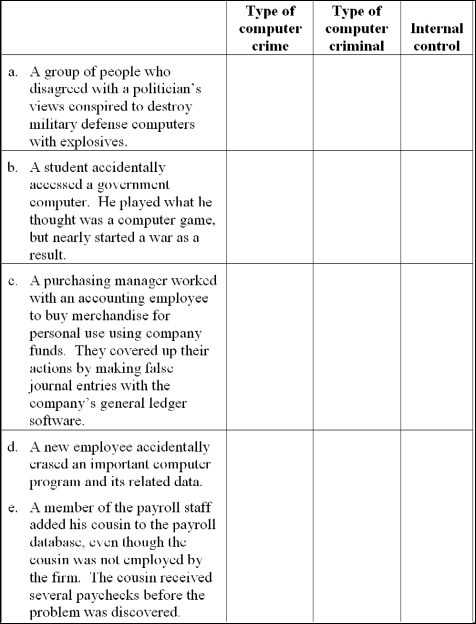
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 7.


Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
51
The textbook discussed seven types of computer criminals. Explain which types most clearly describe Tim based on the above situation.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
52
The following scenario applies to Questions:
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
If Calvin accepts the offer, the crime he commits will most likely involve computers as:
A) Targets.
B) Instrumentalities.
C) Incidental.
D) Associated.
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
If Calvin accepts the offer, the crime he commits will most likely involve computers as:
A) Targets.
B) Instrumentalities.
C) Incidental.
D) Associated.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
53
An unhappy employee has installed a logic bomb in an organization's information system. If the bomb is activated, which of COBIT's information criteria is most likely to be compromised?
A) Compliance.
B) Confidentiality.
C) Efficiency.
D) Integrity.
A) Compliance.
B) Confidentiality.
C) Efficiency.
D) Integrity.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
54
Types of computer criminals
Identify the type of computer criminal described in each of the following cases.
Identify the type of computer criminal described in each of the following cases.


Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
55
COBIT's accountability framework can enhance internal control by assigning responsibility and designating authority for various tasks related to information systems security. Which of the following groups is ultimately responsible for developing and maintaining a strong internal control system?
A) Board of directors.
B) Management.
C) External auditors.
D) Internal auditors.
A) Board of directors.
B) Management.
C) External auditors.
D) Internal auditors.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
56
Which type of internal control is most closely associated with COBIT's "compliance" information criterion?
A) Physical.
B) Confidentiality.
C) Administrative.
D) Availability.
A) Physical.
B) Confidentiality.
C) Administrative.
D) Availability.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
57
The following scenario applies to Questions:
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
Based on the description above, RRI is exposed to all of the following risks except:
A) Disclosure of confidential information.
B) Intrusion.
C) Extortion.
D) Malicious software.
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
Based on the description above, RRI is exposed to all of the following risks except:
A) Disclosure of confidential information.
B) Intrusion.
C) Extortion.
D) Malicious software.

Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck
58
Computer crime taxonomy, computer criminals and internal controls
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 8.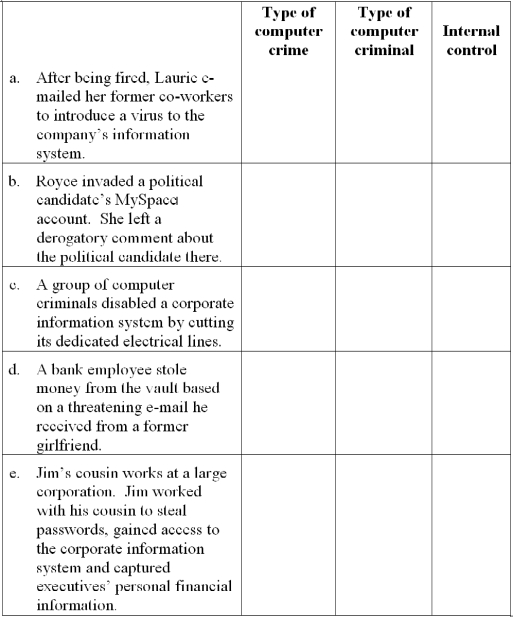
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 8.


Unlock Deck
Unlock for access to all 58 flashcards in this deck.
Unlock Deck
k this deck


