Exam 14: Databases and Database Management Systems
Exam 1: Introduction to the World of Computers90 Questions
Exam 2: The System Unit: Processing and Memory91 Questions
Exam 3: Storage90 Questions
Exam 4: Input and Output90 Questions
Exam 5: System Software: Operating Systems and Utility91 Questions
Exam 6: Application Software89 Questions
Exam 7: Computer Networks89 Questions
Exam 8: The Internet and the World Wide Web87 Questions
Exam 9: Network and Internet Security90 Questions
Exam 10: Multimedia and the Web79 Questions
Exam 11: E-Commerce88 Questions
Exam 12: Information Systems and System Development75 Questions
Exam 13: Program Development and Programming Languages73 Questions
Exam 14: Databases and Database Management Systems72 Questions
Exam 15: Computer Security and Privacy88 Questions
Exam 16: Intellectual Property Rights, Ethics, Health, Acccess and the Environment80 Questions
Select questions type
____ is a growing concern because of the vast amounts of personal data stored in databases today and the many breaches that have occurred in the recent past.
Free
(Multiple Choice)
4.8/5  (37)
(37)
Correct Answer:
A
In a typical client-server database application, the client is called the ____.
Free
(Multiple Choice)
4.9/5  (34)
(34)
Correct Answer:
D
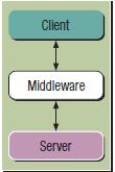 -The accompanying figure shows an n-tier database model.
-The accompanying figure shows an n-tier database model.
Free
(True/False)
4.9/5  (39)
(39)
Correct Answer:
True
Most DBMSs come bundled with a set of tools to perform a variety of necessary tasks, such as building user interfaces, creating forms and reports, and interfacing with query languages and ____ for complex applications.
(Multiple Choice)
4.8/5  (20)
(20)
The ____ contains all data definitions for a database, including table structures, security information, relationships between the tables in the database, and so on.
(Multiple Choice)
4.9/5  (36)
(36)
In ____________________ organization, the order of the records is physically based on the content of the key field.
(Short Answer)
4.9/5  (32)
(32)
Virtually all DBMSs include a ____ for easy data input, modification, and retrieval.
(Multiple Choice)
4.9/5  (33)
(33)
To create a query, users can either type a query using SQL or, more commonly, use the query tools built into the DBMS (such as a query design screen or query ____) to create a query object.
(Multiple Choice)
4.8/5  (36)
(36)
____ create the actual database, based on the design generated by the database designer, and get it ready for data entry.
(Multiple Choice)
4.8/5  (36)
(36)
In ASPs, the code to tie the database to the Web site is typically written in JavaScript or ____.
(Multiple Choice)
4.7/5  (39)
(39)
One of the properties that can be assigned to a field is a(n) ____ to specify the format (such as letters, numbers, or symbols) that must be entered into a field.
(Multiple Choice)
4.9/5  (29)
(29)
____________________ databases are located on a PC and are designed to be accessed by one user.
(Short Answer)
4.9/5  (34)
(34)
Views need to be designed to extract the needed information in as efficient a manner as possible.
(True/False)
4.9/5  (33)
(33)
In ____, the table field involved in the changes is locked until the changes to that field have been completed.
(Multiple Choice)
4.8/5  (31)
(31)
With a(n) ____________________, the data is separated into several databases, each of which is stored on a different computer that may be in different physical locations from one another but that are connected via a network.
(Essay)
4.8/5  (42)
(42)
Middleware for Web database applications is commonly written as ____-short sections of code written in a programming or scripting language that are executed by another program.
(Multiple Choice)
4.9/5  (37)
(37)
To protect against data loss caused by a database failure, accidental deletion, or other problem that renders the main copy of a database unusable, stringent backup procedures should be implemented.
(True/False)
4.8/5  (35)
(35)
Showing 1 - 20 of 72
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)