Exam 5: Digital Security Ethics and Privacy
Exam 1: Introducing Todays Technologies180 Questions
Exam 2: Connecting and Communicating Online181 Questions
Exam 3: Computers and Mobile Devices181 Questions
Exam 4: Programs and Apps181 Questions
Exam 5: Digital Security Ethics and Privacy181 Questions
Exam 6: Computing Components181 Questions
Exam 7: Input and Output181 Questions
Exam 8: Digital Storage178 Questions
Exam 9: Operating Systems181 Questions
Exam 10: Communicating Digital Content181 Questions
Exam 11: Building Solutions180 Questions
Exam 12: Working in the Enterprise181 Questions
Exam 13: Focus on Web Development66 Questions
Exam 14: Practice Test for Mindtap9 Questions
Select questions type
A(n) ____________________ is a program or set of instructions in a program that allow users to bypass security controls when accessing a program, computer, or network.
Free
(Short Answer)
4.8/5  (30)
(30)
Correct Answer:
back door
Biometric objects are entirely foolproof.
Free
(True/False)
4.9/5  (45)
(45)
Correct Answer:
False
Combating cybercrime is not one of the FBI's top priorities.
Free
(True/False)
4.8/5  (34)
(34)
Correct Answer:
False
What type of software restricts access to specified websites?
(Multiple Choice)
4.9/5  (37)
(37)
A(n) ____________________ control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer.
(Short Answer)
4.9/5  (32)
(32)
Any illegal act involving a computer generally is referred to as a computer crime.
(True/False)
4.9/5  (31)
(31)
To promote a better understanding of software piracy problems and, if necessary, to take legal action, a number of major worldwide software companies formed the BSA.
(True/False)
4.9/5  (38)
(38)
Any device that connects to the Internet is susceptible to mobile malware.
(True/False)
4.8/5  (36)
(36)
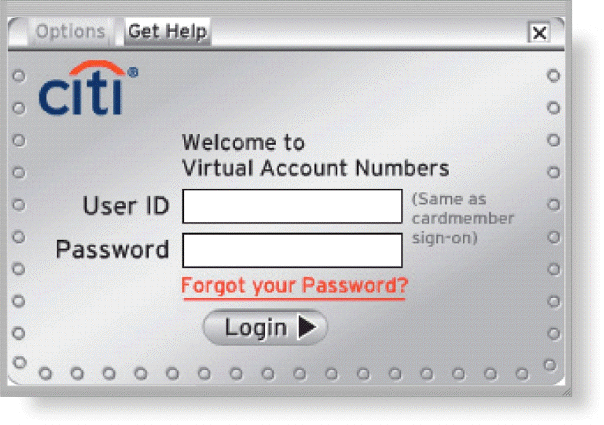 Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
(Multiple Choice)
4.9/5  (41)
(41)
Computer viruses, worms, Trojan horses, and rootkits are classified as which of the following?
(Multiple Choice)
4.8/5  (37)
(37)
Passwords and passphrases that are more than four characters, contain uppercase and lowercase letters, numbers, and special characters are the most secure.
(True/False)
5.0/5  (34)
(34)
Content filtering opponents argue that banning any materials violates constitutional guarantees of free speech and personal rights.
(True/False)
4.8/5  (24)
(24)
Which of the following does your new smartphone use to unlock the device?
(Multiple Choice)
4.8/5  (38)
(38)
A(n) ____________________ object is any item that must be carried to gain access to a computer or computer facility.
(Short Answer)
4.8/5  (36)
(36)
Which of the following categories are the rights to which creators are entitled for their work?
(Multiple Choice)
4.7/5  (25)
(25)
Which of the following is not a security product developer?
(Multiple Choice)
4.8/5  (28)
(28)
Showing 1 - 20 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)