Exam 4: Programs and Apps
Exam 1: Introducing Today S Technologies199 Questions
Exam 2: Connecting and Communicating Online200 Questions
Exam 3: Computers and Mobile Devices200 Questions
Exam 4: Programs and Apps200 Questions
Exam 5: Digital Security Ethics and Privacy200 Questions
Exam 6: Computing Components200 Questions
Exam 7: Input and Output200 Questions
Exam 8: Digital Storage197 Questions
Exam 9: Operating Systems200 Questions
Exam 10: Communicating Digital Content200 Questions
Exam 11: Building Solutions199 Questions
Exam 12: Working in the Enterprise200 Questions
Exam 13: Focus on Web Development74 Questions
Exam 14: Practice Test for Mindtap9 Questions
Select questions type
COGNITIVE ASSESSMENT Which of the following are valid steps toward virus protection?
(Multiple Choice)
4.9/5  (34)
(34)
Some shareware developers render their software useless if no payment is received after the trial period expires.
(True/False)
4.8/5  (42)
(42)
Which of the following is a collection of individual programs sold as a unit?
(Multiple Choice)
4.7/5  (34)
(34)
Which of the following describes a potentially damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without the user's knowledge or permission?
(Multiple Choice)
4.9/5  (30)
(30)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Integrated in most mobile devices
Responses:
chat room
software suite
photo editing
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (32)
(32)
 In the accompanying figure, 12 point and 28 point are measurements of which of the following?
In the accompanying figure, 12 point and 28 point are measurements of which of the following?
(Multiple Choice)
4.8/5  (29)
(29)
In a database, each row, called a(n)____________________, contains data about a given person, product, object, or event.
(Short Answer)
4.9/5  (35)
(35)
Which of the following is a utility that detects and protects a computer from unauthorized intrusions?
(Multiple Choice)
4.7/5  (41)
(41)
Simone is aware that there are a variety of security tools available for her new computer, but she is not entirely sure which kinds of products she needs for which situations. She asks you for some advice. Simone is plagued by junk email that offers her products she does not want, promotes business opportunities that are irrelevant to her, and sometimes advertises offensive material to her. Which kind of security tool do you tell her she needs?
(Multiple Choice)
4.8/5  (36)
(36)
Which kind of program attempts to locate a file on your computer or mobile device based on criteria you specify?
(Multiple Choice)
4.8/5  (30)
(30)
COGNITIVE ASSESSMENT If you follow the advice of your instructor and use CBT to learn about programming languages, how would you learn?
(Multiple Choice)
4.8/5  (37)
(37)
To cut involves removing a portion of a document and storing it in a temporary storage location, called a(n)____________________.
(Short Answer)
4.9/5  (32)
(32)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Keeps track of changes made to websites
Responses:
discussion forum
photo editing
personal firewall
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (27)
(27)
Video editing software allows professionals to modify a segment of a video, called a clip.
(True/False)
4.8/5  (38)
(38)
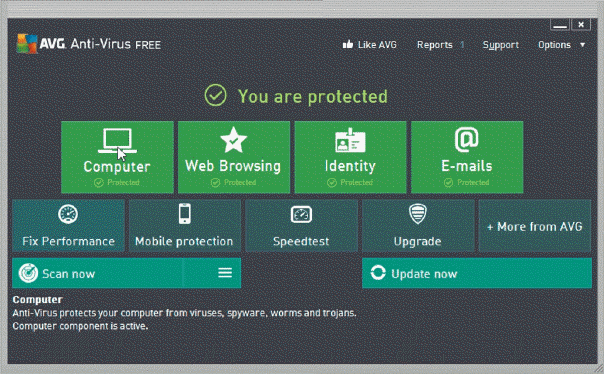 As shown in the accompanying figure, which of the following kinds of program protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files?
As shown in the accompanying figure, which of the following kinds of program protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files?
(Multiple Choice)
4.9/5  (40)
(40)
____________________ is copyrighted software that is distributed at no cost for a trial period.
(Short Answer)
4.9/5  (41)
(41)
____________________ software is an application that helps you organize your calendar, keep track of contacts, and share this information with other devices or users.
(Short Answer)
4.8/5  (28)
(28)
Which of the following kinds of malware is a malicious mobile app that uses a variety of fraudulent schemes to charge unsuspecting users for premium messaging services?
(Multiple Choice)
4.8/5  (39)
(39)
Showing 21 - 40 of 200
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)