Exam 4: Network and Internet Security
Exam 1: Introduction to the World of Computers100 Questions
Exam 2: A Closer Look at Hardware and Software100 Questions
Exam 3: The Internet and the World Wide Web100 Questions
Exam 4: Network and Internet Security100 Questions
Exam 5: Computer Security and Privacy100 Questions
Exam 6: Intellectual Property Rights and Ethics100 Questions
Exam 7: Health, Access and the Environment100 Questions
Exam 8: Emerging Technologies100 Questions
Select questions type
Antispam programs are used to detect and remove any viruses or worms that find their way onto your computer.
Free
(True/False)
4.7/5  (43)
(43)
Correct Answer:
False
In businesses, access control systems are often integrated into a comprehensive ____________________ system designed to manage users' access to enterprise systems.
Free
(Short Answer)
4.8/5  (32)
(32)
Correct Answer:
IDM
What is war driving?
Free
(Essay)
4.8/5  (32)
(32)
Correct Answer:
Unauthorized use of a Wi-Fi network is called war driving or Wi-Fi piggybacking, depending on the location of the hacker at the time. War driving typically involves driving in a car with a portable computer looking for unsecured Wi-Fi networks to connect to.
Botnets are a major security threat since criminals are increasingly creating botnets to use for computer sabotage.
(True/False)
4.8/5  (22)
(22)
Packetsniffing systems determine whether or not the person attempting access is actually who he or she claims to be. _________________________
(True/False)
4.9/5  (34)
(34)
Possessed knowledge access systems use physical objects for identification purposes and are frequently used to access facilities and computer systems.
(True/False)
4.8/5  (33)
(33)
A computer ____ spreads by creating copies of its code and sending those copies to other computers via a network.
(Multiple Choice)
4.7/5  (35)
(35)
A(n)____________________ access system is an identification system that requires the individual requesting access to provide information that only the authorized user is supposed to know.
(Short Answer)
4.9/5  (35)
(35)
To avoid the need to obtain the recipient's public key before sending that person an encrypted e-mail, proprietary encrypted e-mail can be used. _________________________
(True/False)
4.9/5  (44)
(44)
Like a computer virus, a computer worm infects other computer files to replicate itself.
(True/False)
4.9/5  (34)
(34)
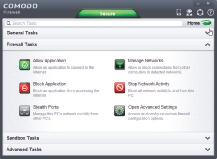 A(n)____________________, such as the one shown in the accompanying figure, is a security system that essentially creates a barrier between a computer or a network and the Internet in order to protect against unauthorized access.
A(n)____________________, such as the one shown in the accompanying figure, is a security system that essentially creates a barrier between a computer or a network and the Internet in order to protect against unauthorized access.
(Short Answer)
4.8/5  (44)
(44)
____ is a type of scam that uses spoofed domain names to obtain personal information for use in fraudulent activities.
(Multiple Choice)
4.8/5  (35)
(35)
While two-factor authentication systems are common in the United States, they are not widely used in other countries.
(True/False)
4.9/5  (33)
(33)
USB security keys are also called USB security tokens . _________________________
(True/False)
4.7/5  (33)
(33)
A computer that is controlled by a hacker or other computer criminal is referred to as a ____.
(Multiple Choice)
4.8/5  (39)
(39)
Strong passwords are passwords that are at least eight characters long. _________________________
(True/False)
4.7/5  (40)
(40)
A relatively new type of scam involves posting fake job listings on job search sites to elicit personal information (such as Social Security numbers)from job seekers.
(True/False)
4.8/5  (27)
(27)
____ is a generic term that refers to any type of malicious software.
(Multiple Choice)
4.9/5  (37)
(37)
Increasingly, computers and hard drives are ____________________; that is, encrypting all data automatically and invisibly to the user.
(Short Answer)
4.7/5  (30)
(30)
Showing 1 - 20 of 100
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)