Exam 3: Check Point Certified Security Expert - R80
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
You have a Gateway is running with 2 cores. You plan to add a second gateway to build a cluster and used a device with 4 cores. How many cores can be used in a Cluster for Firewall-kernel on the new device?
(Multiple Choice)
4.9/5  (46)
(46)
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret the administrator found that the check box to enable pre-shared secret and cannot be enabled. Why does it not allow him to specify the pre-shared secret?
(Multiple Choice)
4.9/5  (47)
(47)
Which utility allows you to configure the DHCP service on Gaia from the command line?
(Multiple Choice)
4.8/5  (38)
(38)
What are the different command sources that allow you to communicate with the API server?
(Multiple Choice)
4.9/5  (40)
(40)
Is the first packet of an UDP session is rejected by a rule definition from within a security policy (not including the clean up rule), what message is send back through the kernel?
(Multiple Choice)
4.9/5  (37)
(37)
What is the command to check the status of the SmartEvent Correlation Unit?
(Multiple Choice)
4.8/5  (43)
(43)
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.) 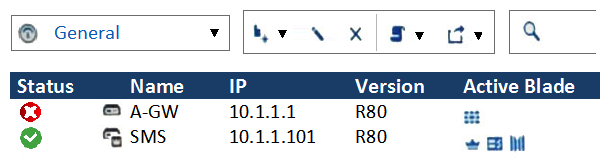
(Multiple Choice)
4.9/5  (38)
(38)
What needs to be configured if the NAT property 'Translate destination or client side' is not enabled in Global Properties?
(Multiple Choice)
4.9/5  (37)
(37)
The back end database for Check Point R80 Management uses:
(Multiple Choice)
4.9/5  (41)
(41)
SandBlast Mobile identifies threats in mobile devices by using on-device, network, and cloud-based algorithms and has four dedicated components that constantly work together to protect mobile devices and their data. Which component is NOT part of the SandBlast Mobile solution?
(Multiple Choice)
4.8/5  (35)
(35)
Check Point recommends configuring Disk Space Management parameters to delete old log entries when available disk space is less than or equal to?
(Multiple Choice)
4.8/5  (38)
(38)
Which of the SecureXL templates are enabled by default on Security Gateway?
(Multiple Choice)
4.8/5  (31)
(31)
Steve is a Cyber Security Engineer working for Global Bank with a large scale deployment of Check Point Enterprise Appliances. Steve's manager, Diana, asks him to provide firewall connection table details from one of the firewalls for which he is responsible. Which of these commands may impact performance briefly and should not be used during heavy traffic times of day?
(Multiple Choice)
4.7/5  (38)
(38)
In a Client to Server scenario, which represents that the packet has already checked against the tables and the Rule Base?
(Multiple Choice)
4.8/5  (33)
(33)
Hit Count is a feature to track the number of connections that each rule matches, which one is not benefit of Hit Count.
(Multiple Choice)
4.9/5  (31)
(31)
Fill in the blanks: Gaia can be configured using the ______ or _____ .
(Multiple Choice)
4.7/5  (38)
(38)
Showing 121 - 140 of 340
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)