Exam 13: AWS Certified SysOps Administrator (SOA-C01)
Exam 1: AWS Certified Advanced Networking - Specialty (ANS-C00)397 Questions
Exam 2: AWS Certified Alexa Skill Builder - Specialty68 Questions
Exam 3: AWS Certified Cloud Practitioner (CLF-C01)803 Questions
Exam 4: AWS Certified Data Analytics - Specialty (DAS-C01)135 Questions
Exam 5: AWS Certified Database - Specialty156 Questions
Exam 6: AWS Certified Developer Associate (DVA-C01)470 Questions
Exam 7: AWS Certified Machine Learning - Specialty (MLS-C01)159 Questions
Exam 8: AWS Certified Security - Specialty (SCS-C01)295 Questions
Exam 9: AWS Certified Solutions Architect - Associate SAA-C02596 Questions
Exam 10: AWS Certified Solutions Architect - Professional (SAP-C01)871 Questions
Exam 11: AWS Certified SysOps Administrator - Associate (SOA-C02)54 Questions
Exam 12: AWS DevOps Engineer - Professional (DOP-C01)610 Questions
Exam 13: AWS Certified SysOps Administrator (SOA-C01)976 Questions
Select questions type
A user is measuring the CPU utilization of a private data center machine every minute. The machine provides the aggregate of data every hour, such as Sum of data", "Min value", "Max value, and "Number of Data points". The user wants to send these values to CloudWatch. How can the user achieve this?
(Multiple Choice)
4.8/5  (37)
(37)
Application developers are reporting Access Denied errors when trying to list the contents of an Amazon S3 bucket by using the IAM user " arn:aws:iam::111111111111:user/application ". The following S3 bucket policy is in use: 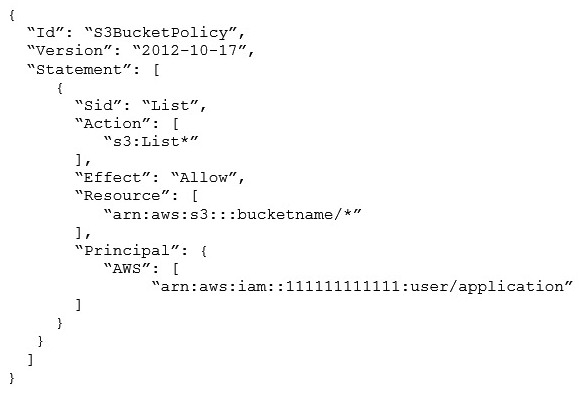 How should a SysOps Administrator modify the S3 bucket policy to fix the issue?
How should a SysOps Administrator modify the S3 bucket policy to fix the issue?
(Multiple Choice)
4.8/5  (36)
(36)
An ecommerce company uses an Amazon ElastiCache for Memcached cluster for in-memory caching of popular product queries on the shopping site. When viewing recent Amazon CloudWatch metrics data for the ElastiCache cluster, the sysops administrator notices a large number of evictions. Which of the following actions will reduce these evictions? (Choose two.)
(Multiple Choice)
4.9/5  (34)
(34)
An application running on Amazon EC2 instances in an Auto Scaling group across multiple Availability Zones was deployed using an AWS CloudFormation template. The SysOps team has patched the Amazon Machine Image (AMI) version and must update all the EC2 instances to use the new AMI. How can the SysOps Administrator use CloudFormation to apply the new AMI while maintaining a minimum level of active instances to ensure service continuity?
(Multiple Choice)
4.9/5  (41)
(41)
Which of the following services can receive an alert from CloudWatch?
(Multiple Choice)
4.8/5  (33)
(33)
A company wants to launch a group of Amazon EC2 instances that need to communicate with each other with the lowest possible latency. Which combination of actions should a SysOps administrator take when launching these instances? (Choose two.)
(Multiple Choice)
4.8/5  (31)
(31)
An organization is generating digital policy files which are required by the admins for verification. Once the files are verified they may not be required in the future unless there is some compliance issue. If the organization wants to save them in a cost effective way, which is the best possible solution?
(Multiple Choice)
4.8/5  (37)
(37)
A SysOps administrator must monitor a fleet of Amazon EC2 Linux instances with the constraint that no agents be installed. The administrator chooses Amazon CloudWatch as the monitoring tool. Which metrics can be measured given the constraints? (Choose three.)
(Multiple Choice)
4.8/5  (27)
(27)
In EC2, what happens to the data in an instance store if an instance reboots (either intentionally or unintentionally)?
(Multiple Choice)
4.7/5  (42)
(42)
A company that hosts a multi-tier ecommerce web application on AWS has been alerted to suspicious application traffic. The architecture consists of Amazon EC2 instances deployed across multiple Availability Zones behind an Application Load Balancer (ALB). After examining the instance logs, a SysOps administrator determines that the suspicious traffic is an attempted SQL injection attack. What should the SysOps administrator do to prevent similar attacks?
(Multiple Choice)
4.7/5  (39)
(39)
A SysOps Administrator is running an auto-scaled application behind a Classic Load Balancer. Scaling out is triggered when the CPUUtilization instance metric is more than 75% across the Auto Scaling group. The Administrator noticed aggressive scaling out and after discussing with developers, an application memory leak is suspected causing aggressive garbage collection cycle. How can the Administrator troubleshoot the application without triggering the scaling process?
(Multiple Choice)
4.9/5  (27)
(27)
After launching a new Amazon EC2 instance from a Microsoft Windows 2012 Amazon Machine Image (AMI), the SysOps Administrator is unable to connect to the instance using Remote Desktop Protocol (RDP). The instance is also unreachable. As part of troubleshooting, the Administrator deploys a second instance from a different AMI using the same configuration and is able to connect to the instance. What should be the next logical step in troubleshooting the first instance?
(Multiple Choice)
4.9/5  (35)
(35)
A user has configured ELB with Auto Scaling. The user temporarily suspended the Auto Scaling terminate process. What might the Availability Zone Rebalancing process (AZRebalance) conse-quently cause during this period?
(Multiple Choice)
4.7/5  (45)
(45)
A company wants to track Amazon EC2 usage charges that are based on the value of a tag that is named Business-Unit. Company leaders instruct developers to update all EC2 resources with the tag. The developers notify the leaders that they have completed this task. Later that week, a finance team member checks Cost Explorer. The finance team member sees EC2 costs in the different accounts but cannot find the Business-Unit tag to filter by or group by. What is the MOST likely reason that the Business-Unit tag is absent?
(Multiple Choice)
4.8/5  (40)
(40)
A user has configured CloudWatch monitoring on an EBS backed EC2 instance. If the user has not attached any additional device, which of the below mentioned metrics will always show a 0 value?
(Multiple Choice)
4.8/5  (40)
(40)
A company needs to ensure that all IAM users rotate their passwords on a regular basis. Which action should be taken take to implement this?
(Multiple Choice)
4.8/5  (34)
(34)
You have set up Individual AWS accounts for each project. You have been asked to make sure your AWS Infrastructure costs do not exceed the budget set per project for each month. Which of the following approaches can help ensure that you do not exceed the budget each month?
(Multiple Choice)
4.9/5  (36)
(36)
A user has setup a custom application which generates a number in decimals. The user wants to track that number and setup the alarm whenever the number is above a certain limit. The application is sending the data to CloudWatch at regular intervals for this purpose. Which of the below mentioned statements is not true with respect to the above scenario?
(Multiple Choice)
4.9/5  (36)
(36)
The Security team at AnyCompany discovers that some employees have been using individual AWS accounts that are not under the control of AnyCompany. The team has requested that those individual accounts be linked to the central organization using AWS Organizations. Which action should a SysOps Administrator take to accomplish this?
(Multiple Choice)
4.8/5  (34)
(34)
Showing 781 - 800 of 976
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)